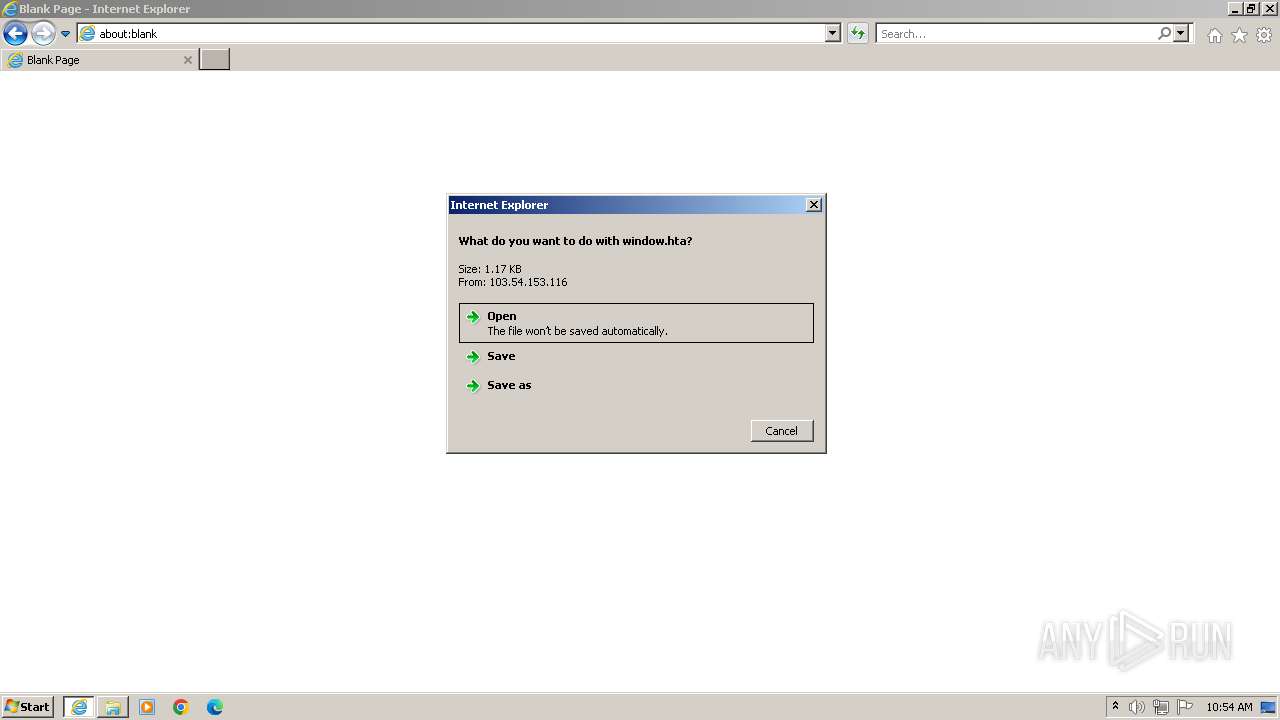
| download: | /window.hta |
| Full analysis: | https://app.any.run/tasks/79e247b3-5ea9-4672-9107-b166527389cd |
| Verdict: | Malicious activity |
| Analysis date: | June 04, 2024, 09:53:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, Unicode text, UTF-8 text, with CRLF line terminators |
| MD5: | 4D4BFC553118C8A52D3AE50EC794F9A4 |
| SHA1: | 815539B8BCE2F71C611574A1203979AD3BD38A66 |
| SHA256: | 2079D557BD97B6F3A34770A0B8488E1BC534FF6AC60038A4ED72CEA9D7E4FECC |
| SSDEEP: | 24:hPBCChyPzaFXp7QBJxAjWZmwB9+DomcXB7cCYMCQPIzAMf:tThCzG+fV70omcXB7cCPCUEXf |
MALICIOUS
EXPLOIT has been detected (SURICATA)
- mshta.exe (PID: 2624)
SUSPICIOUS
Reads the Internet Settings
- mshta.exe (PID: 2624)
Connects to the server without a host name
- mshta.exe (PID: 2624)
INFO
Application launched itself
- iexplore.exe (PID: 4036)
- iexplore.exe (PID: 3976)
Checks supported languages
- wmpnscfg.exe (PID: 1056)
Reads the computer name
- wmpnscfg.exe (PID: 1056)
Manual execution by a user
- explorer.exe (PID: 1864)
- wmpnscfg.exe (PID: 1056)
Checks proxy server information
- mshta.exe (PID: 2624)
Reads Internet Explorer settings
- mshta.exe (PID: 2624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
EXIF
HTML
| Viewport: | width=device-width, initial-scale=1.0 |
|---|---|
| Title: | Safe Page |
Total processes
42
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1116 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3976 CREDAT:333057 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1864 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2624 | C:\Windows\System32\mshta.exe -Embedding | C:\Windows\System32\mshta.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3976 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\window.hta.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4036 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3976 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
27 686
Read events
27 335
Write events
223
Delete events
128
Modification events
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 496896928 | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31110757 | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 797370678 | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31110757 | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
13
Text files
33
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:AD55BD80EE59AB8391FA9E5E43F56B30 | SHA256:1D0CEFA75DFDA6ED48F90F66719D2BDAFAFD5CC6BF81185F5069364D50AFD40E | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\V0WJWSDZ.txt | text | |
MD5:F26B23CBCB80506E8DC5EF31DABEDF25 | SHA256:023F492CC0347ABED02A56568F596AE3E302068E9432F47C63B612F83E11F290 | |||
| 3976 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:2338418CA51CBE49CE90F15A1E742A3B | SHA256:898B398E38DE8E91532FDBC13E788A732E12185EC10AF4772B4FE3BD34A749E2 | |||
| 3976 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:E4A6497C402DCDF41B5F7D0827824059 | SHA256:98FC52BEA0AC5A888ED498FE0CC68A85945C1579AC8F692BD6C059FECA2342C5 | |||
| 3976 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:C0EE139D946BF8543AC7EB41E535E7E7 | SHA256:736AEC954D31E3CE2F57AE39BFA76D606865694E655D6A5902D40A6C8B103BF5 | |||
| 3976 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3976 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\CTQ94SF7.txt | text | |
MD5:C629DA5675E0E267CF7C264B3A83235E | SHA256:57F8843BB1F6EF9488DD37259EBFFF2D51A5D5B43E4B143ACECE87ED8080643B | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_C0427F5F77D9B3A439FC620EDAAB6177 | binary | |
MD5:AD3111CE865B07DE4423CFD3B1564ABD | SHA256:FBEDE97EFC1AE7181A63BD55D1A86818B931D3BF6E5A879E69BB012BAA500ED1 | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\BPPX2Z9Z.txt | text | |
MD5:3EEB72215D505A6AE50CD000D6A4965A | SHA256:99BD3A9F26D47C24A1D277496BCA0DC15DE7C53C107EEAAEBC226392C50E6825 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
26
DNS requests
18
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3976 | iexplore.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8644b833ad892dd7 | unknown | — | — | unknown |
3976 | iexplore.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c21588876f974d24 | unknown | — | — | unknown |
1116 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | — | — | unknown |
3976 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
3976 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
3976 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
2624 | mshta.exe | GET | 200 | 103.54.153.116:80 | http://103.54.153.116/window.hta | unknown | — | — | unknown |
1116 | iexplore.exe | GET | 200 | 103.54.153.116:80 | http://103.54.153.116/window.hta | unknown | — | — | unknown |
3976 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | unknown |
1088 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f33259cc05673396 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3976 | iexplore.exe | 2.19.120.21:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3976 | iexplore.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
3976 | iexplore.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
3976 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1116 | iexplore.exe | 13.107.5.80:443 | api.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1116 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1116 | iexplore.exe | Potentially Bad Traffic | ET POLICY Possible HTA Application Download |
1116 | iexplore.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host HTA Request |
1116 | iexplore.exe | Attempted User Privilege Gain | ET WEB_CLIENT HTA File containing Wscript.Shell Call - Potential CVE-2017-0199 |
1116 | iexplore.exe | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
1116 | iexplore.exe | A Network Trojan was detected | LOADER [ANY.RUN] Gen.Powershell.Downloader Script Payload |
2624 | mshta.exe | Potentially Bad Traffic | ET POLICY Possible HTA Application Download |
2624 | mshta.exe | Attempted User Privilege Gain | ET EXPLOIT SUSPICIOUS Possible CVE-2017-0199 IE7/NoCookie/Referer HTA dl |
2624 | mshta.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host HTA Request |
2624 | mshta.exe | Attempted User Privilege Gain | ET WEB_CLIENT HTA File containing Wscript.Shell Call - Potential CVE-2017-0199 |
2624 | mshta.exe | A Network Trojan was detected | ET EXPLOIT MSXMLHTTP Download of HTA (Observed in CVE-2017-0199) |