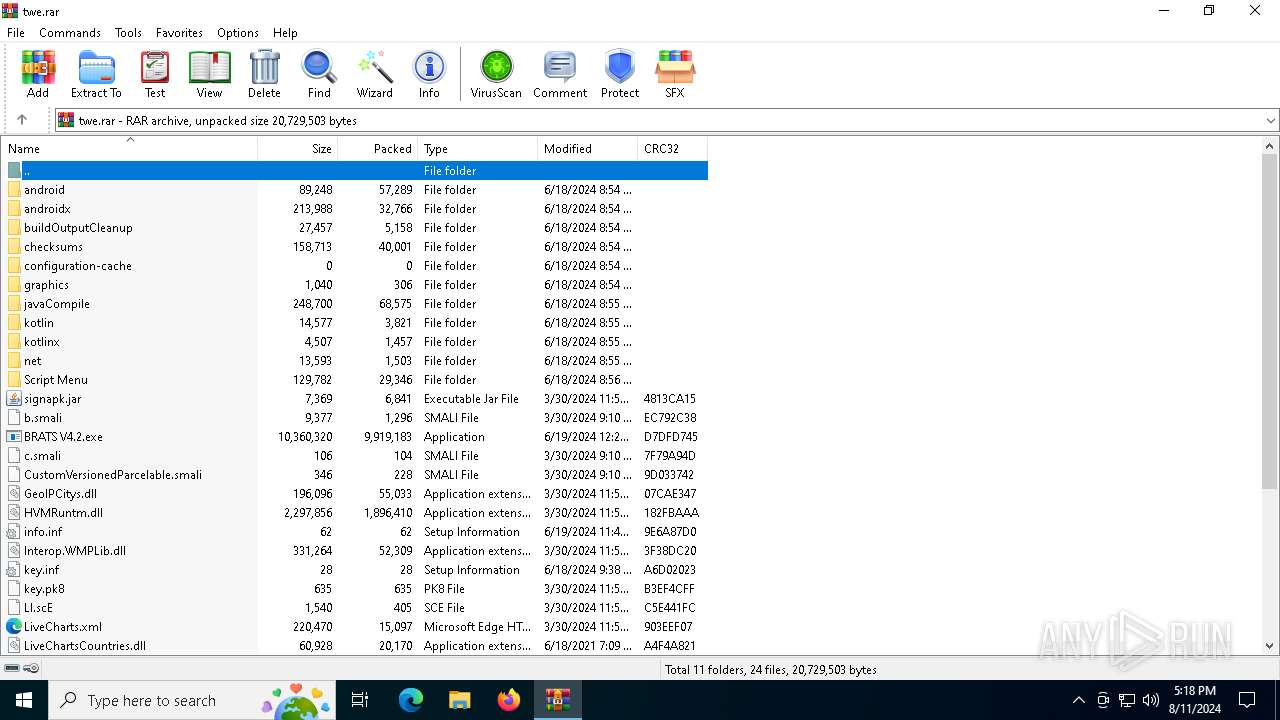
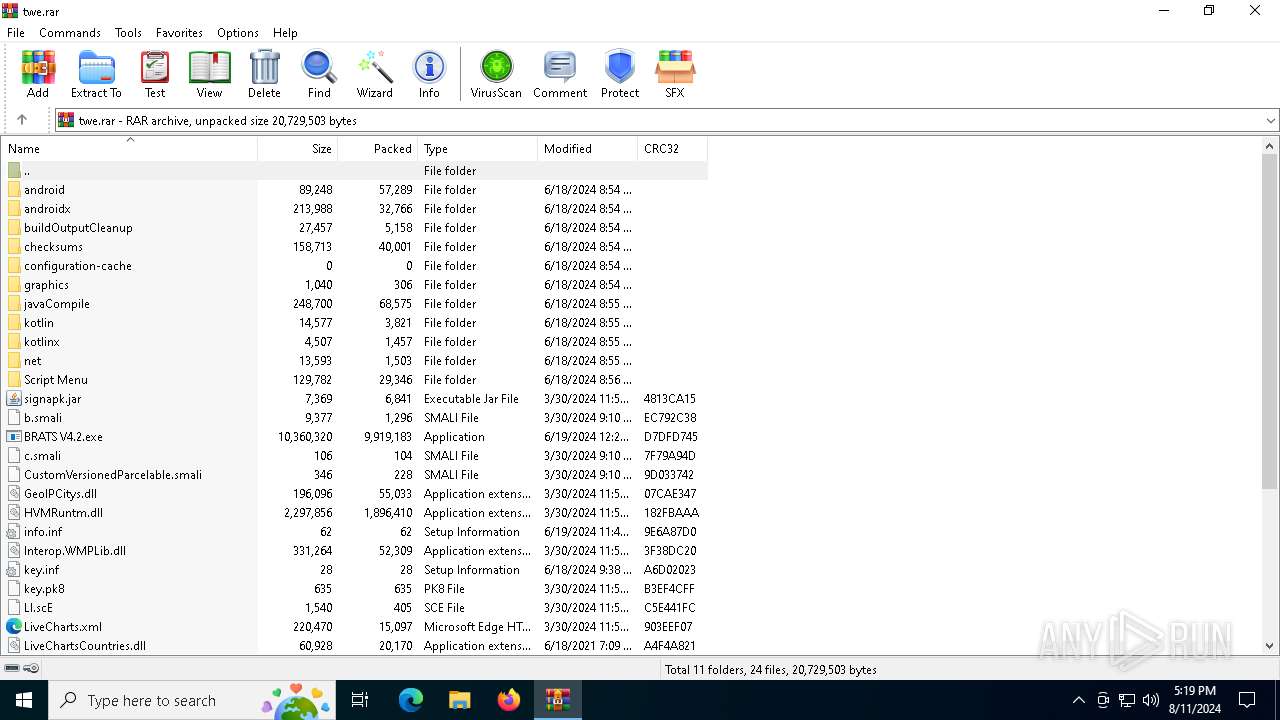
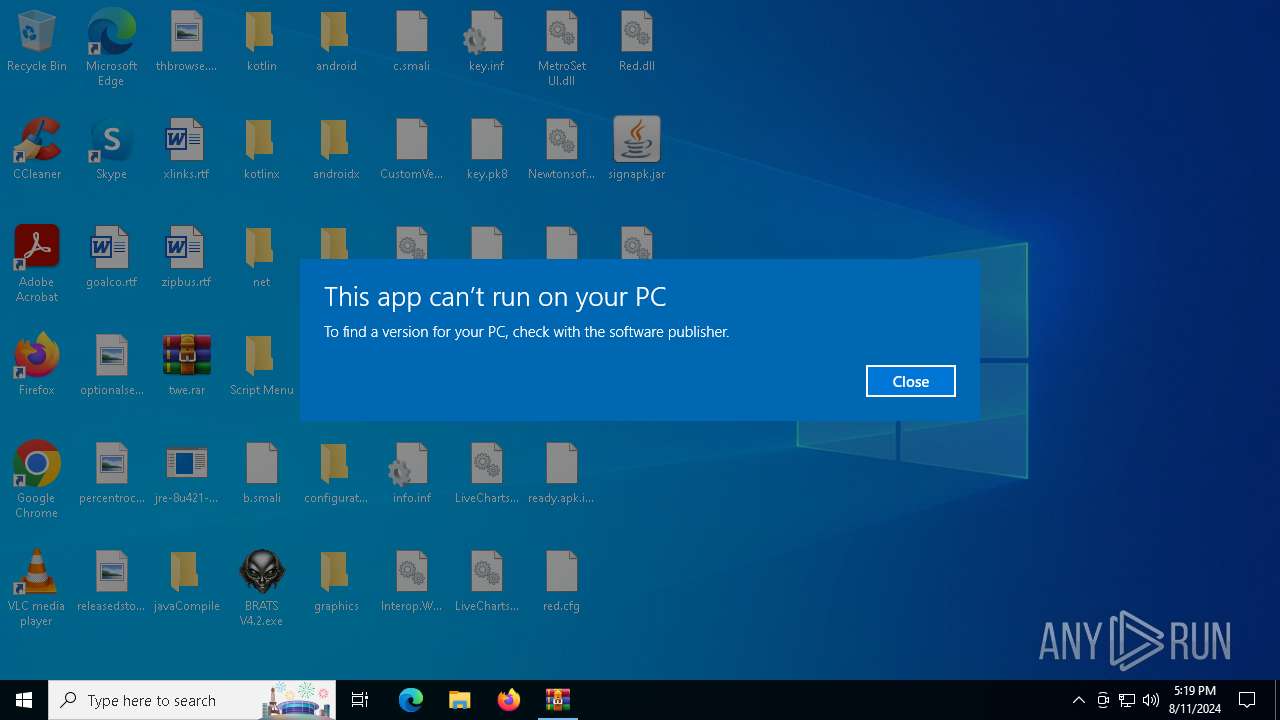
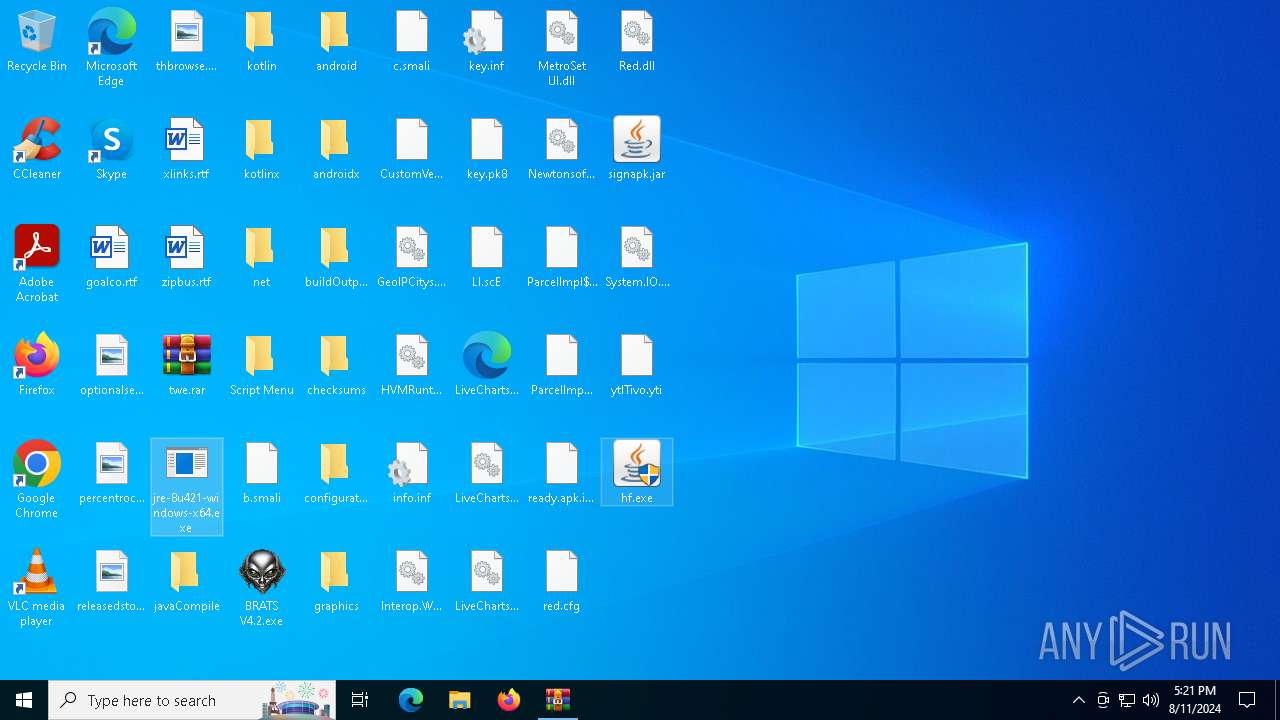
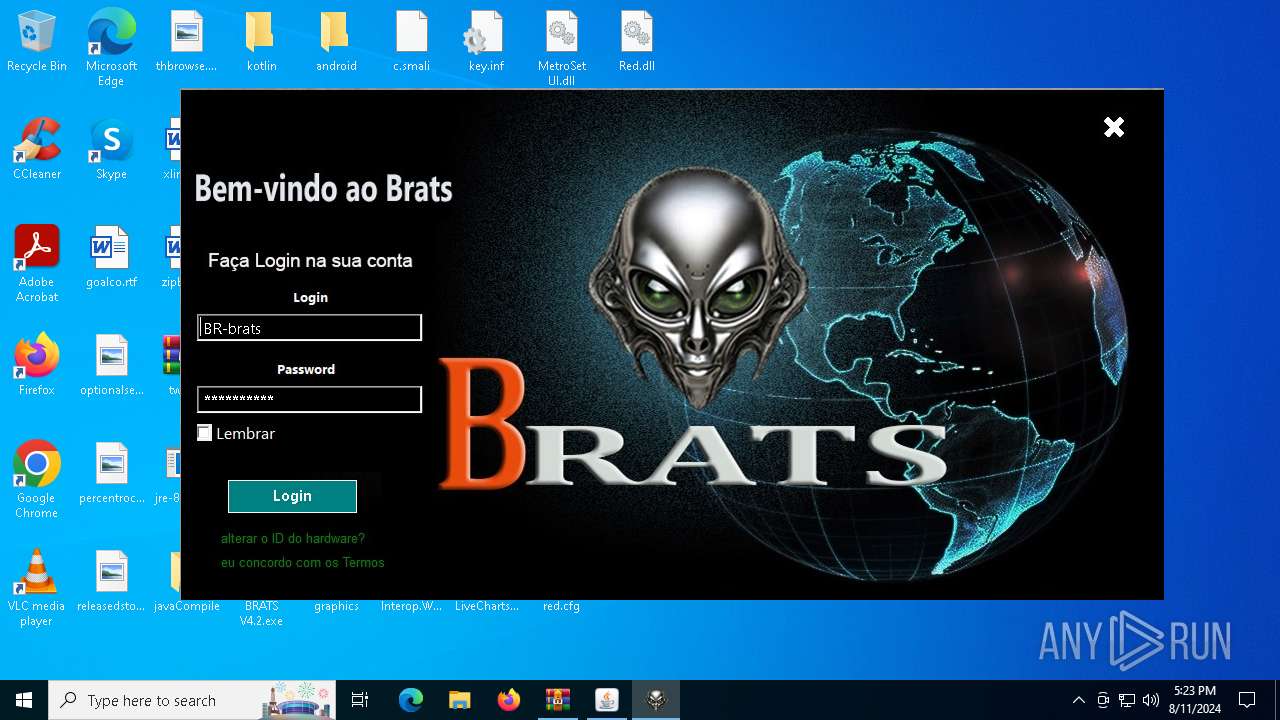
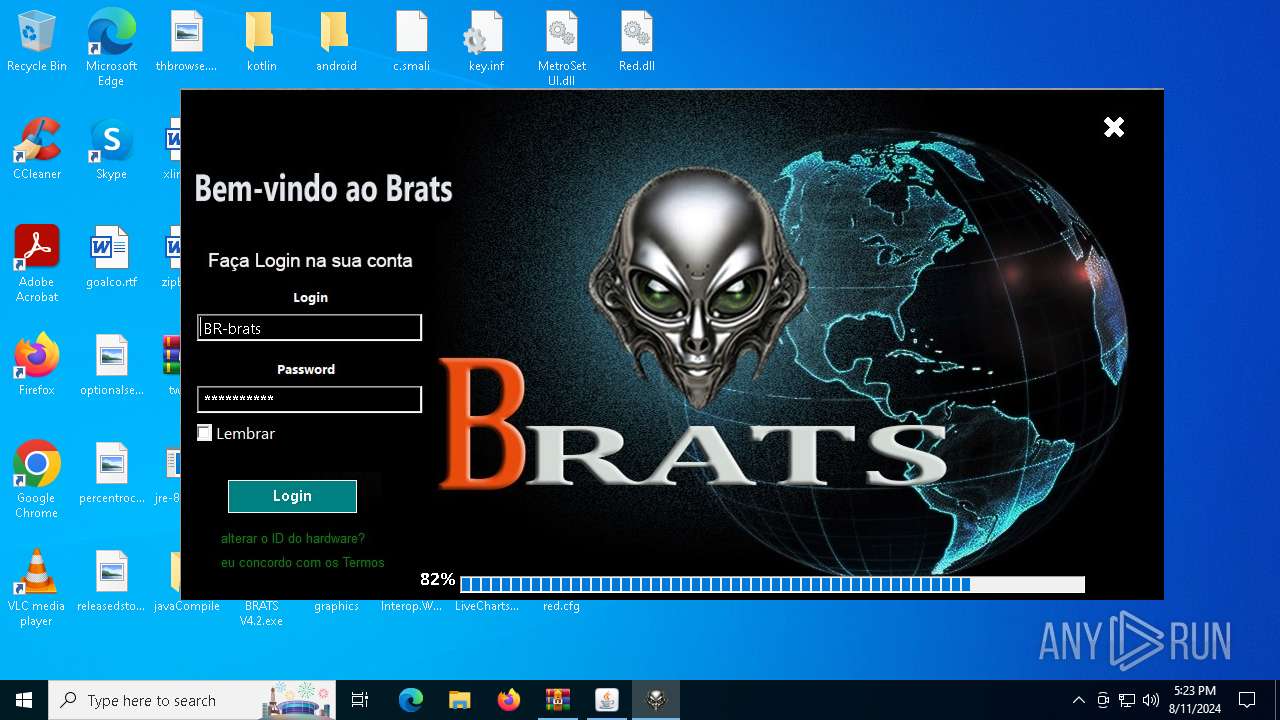
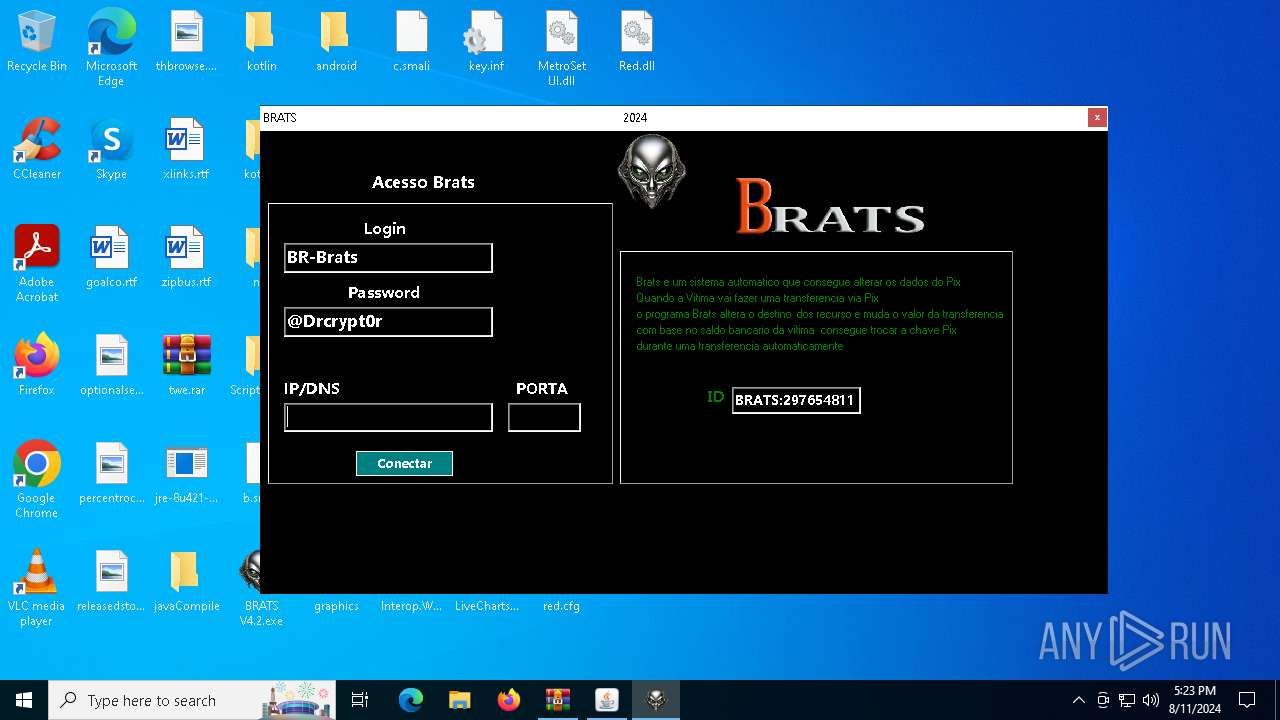
| File name: | twe.rar |
| Full analysis: | https://app.any.run/tasks/ea2b5f69-d6b4-4838-a3a3-b7cfa891a934 |
| Verdict: | Malicious activity |
| Analysis date: | August 11, 2024, 17:18:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 1DD147AD10AC9B591098E9122EA55766 |
| SHA1: | 53B2D5C0C5327E2F514B74902B8761080E6DA494 |
| SHA256: | 20727D0AEF43FA0EA2715227470F23C2A681BCCDD5EE836393D035A5D0CF2F0B |
| SSDEEP: | 98304:KDtBQn41HmcgKk+2OE+1NY6isE7S/CRu0wQ4Xx9aQXKCo7VqVKmcjH52GhwbOBr3:djNHjX6pIDdGlEFXcmTZNpbT |
MALICIOUS
Changes the autorun value in the registry
- msiexec.exe (PID: 6628)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6392)
- msiexec.exe (PID: 6628)
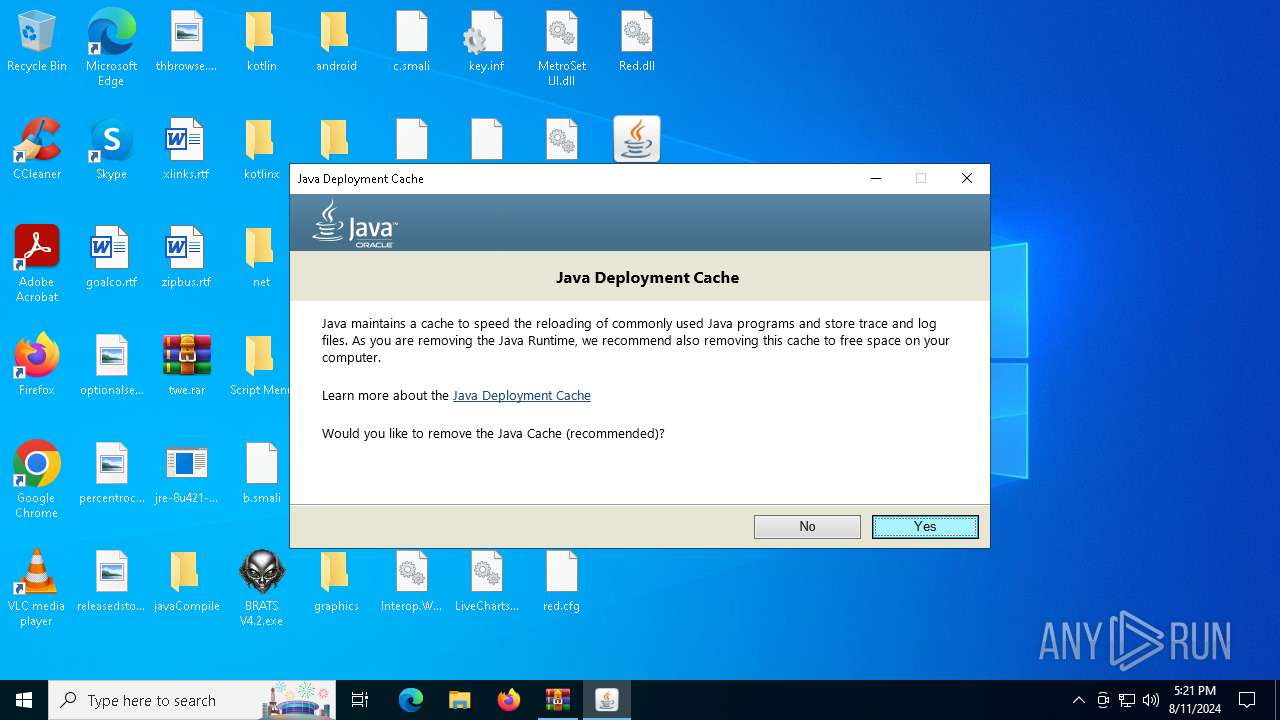
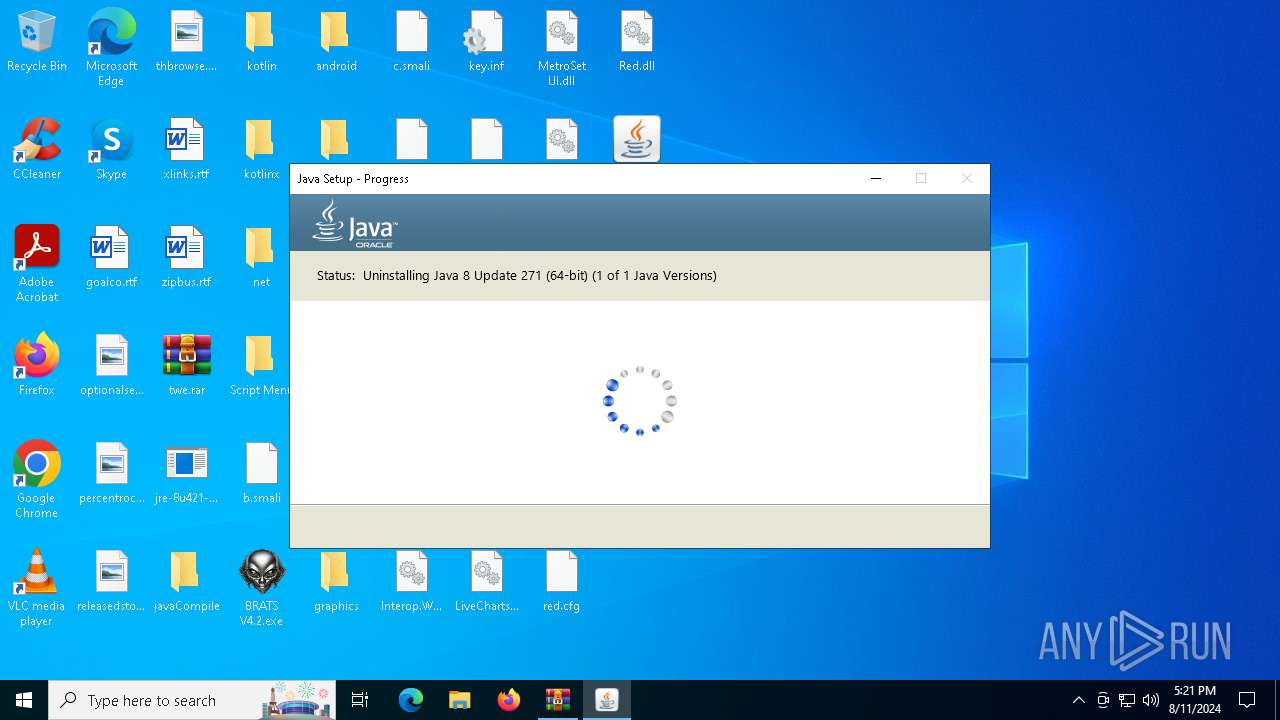
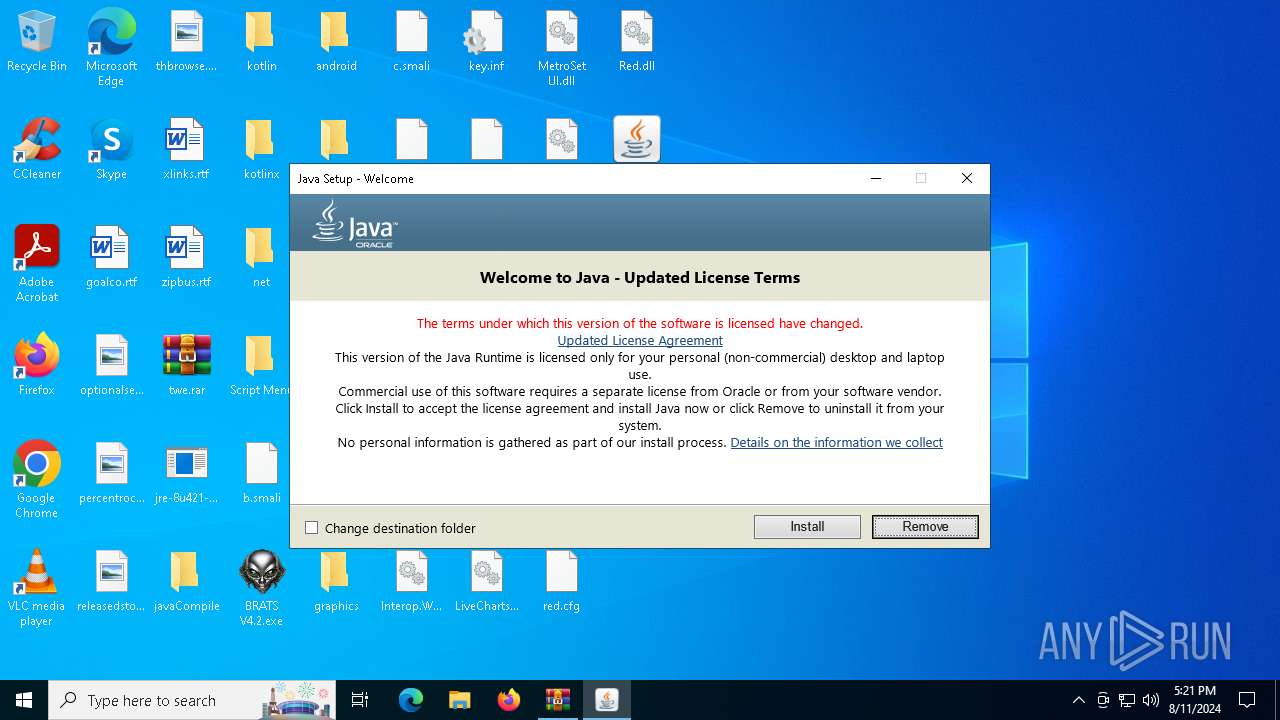
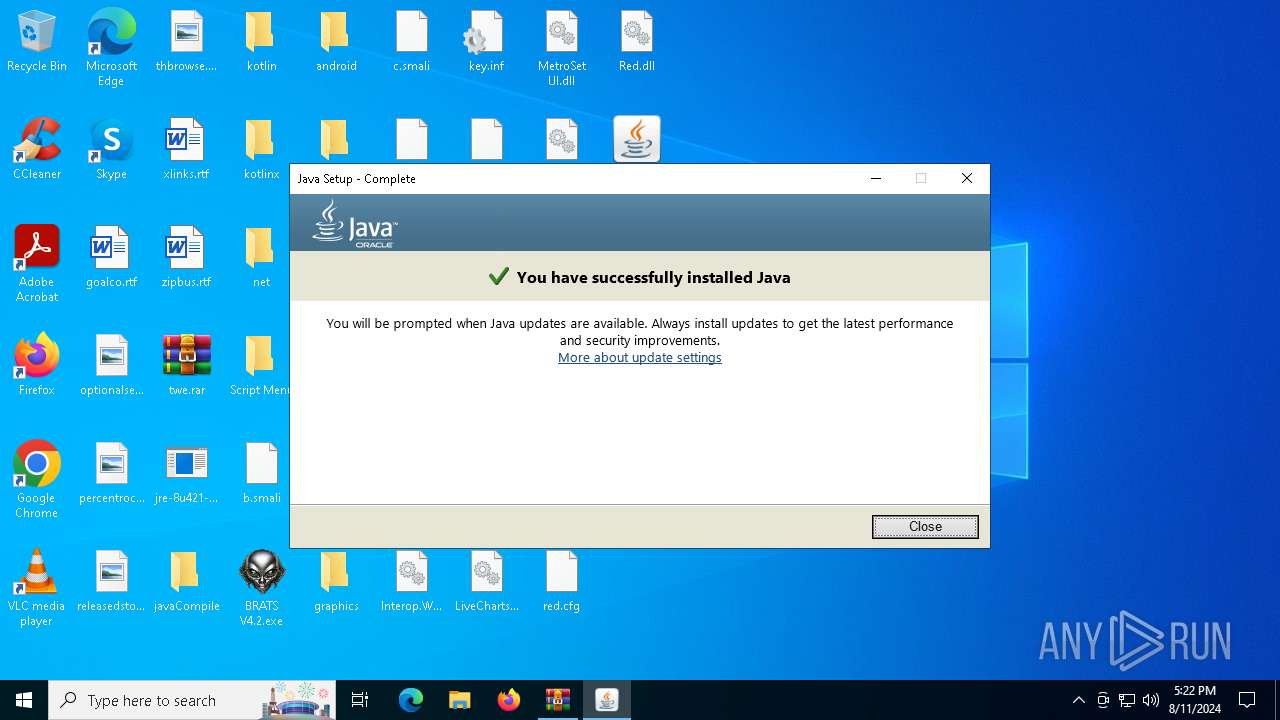
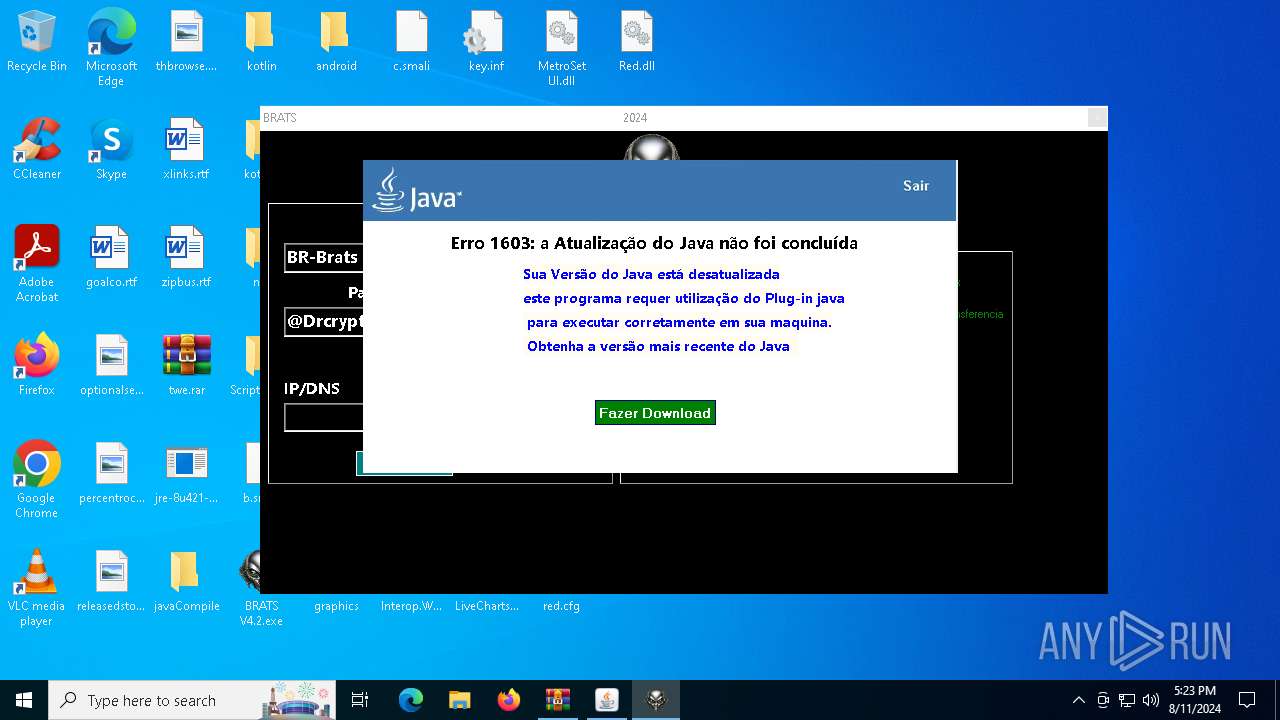
Checks for Java to be installed
- hf.exe (PID: 5048)
- msiexec.exe (PID: 6628)
- installer.exe (PID: 6160)
- ssvagent.exe (PID: 4020)
- jp2launcher.exe (PID: 236)
- jp2launcher.exe (PID: 5328)
- msiexec.exe (PID: 6196)
- hf.exe (PID: 4024)
- javaw.exe (PID: 6888)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6628)
Drops the executable file immediately after the start
- msiexec.exe (PID: 6628)
- installer.exe (PID: 6160)
- hf.exe (PID: 4024)
Reads security settings of Internet Explorer
- hf.exe (PID: 5048)
- hf.exe (PID: 4024)
- installer.exe (PID: 6160)
- jp2launcher.exe (PID: 236)
- jp2launcher.exe (PID: 5328)
Checks Windows Trust Settings
- hf.exe (PID: 5048)
- hf.exe (PID: 4024)
- msiexec.exe (PID: 6628)
Reads Microsoft Outlook installation path
- hf.exe (PID: 5048)
- hf.exe (PID: 4024)
Reads Internet Explorer settings
- hf.exe (PID: 5048)
- hf.exe (PID: 4024)
The process drops C-runtime libraries
- msiexec.exe (PID: 6628)
Reads Mozilla Firefox installation path
- MSIB77B.tmp (PID: 6556)
- installer.exe (PID: 6160)
Executable content was dropped or overwritten
- installer.exe (PID: 6160)
- hf.exe (PID: 4024)
Creates/Modifies COM task schedule object
- ssvagent.exe (PID: 4020)
- installer.exe (PID: 6160)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6392)
- msiexec.exe (PID: 6628)
Manual execution by a user
- hf.exe (PID: 5944)
- hf.exe (PID: 420)
- hf.exe (PID: 2524)
- hf.exe (PID: 6208)
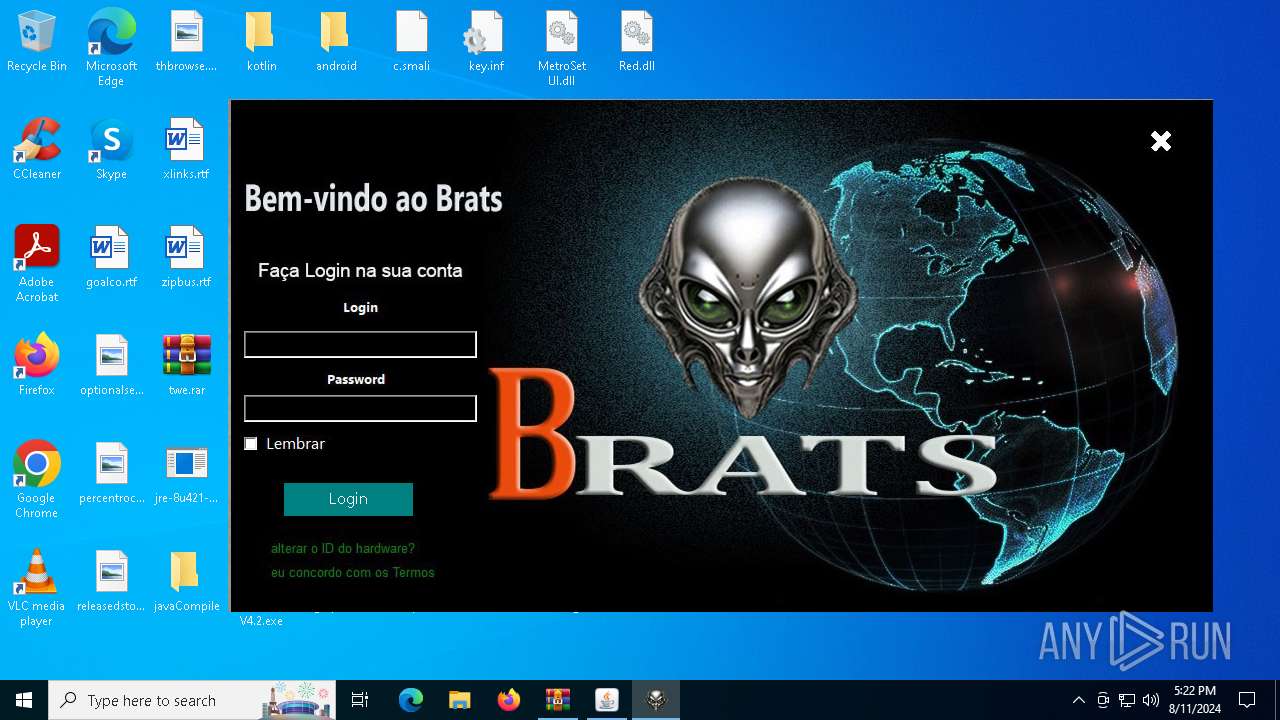
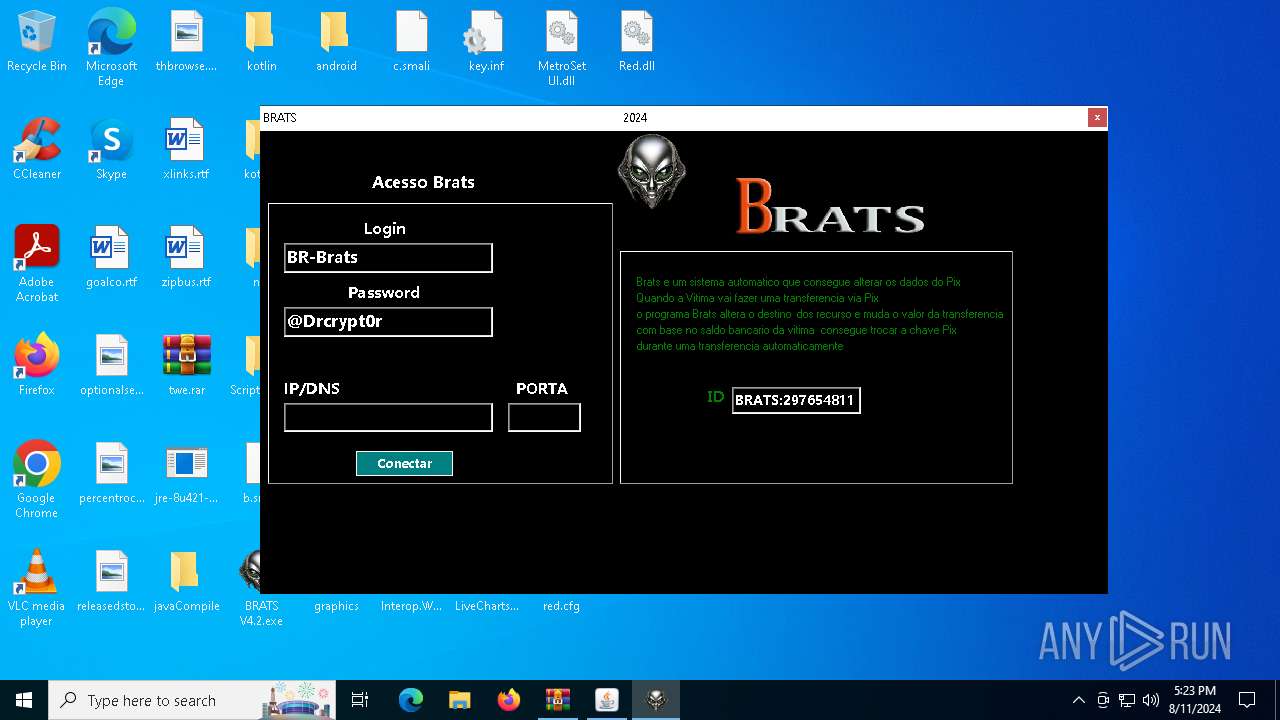
- BRATS V4.2.exe (PID: 7120)
Create files in a temporary directory
- hf.exe (PID: 420)
- MSIB77B.tmp (PID: 6556)
- hf.exe (PID: 6208)
- javaw.exe (PID: 4780)
- jp2launcher.exe (PID: 5328)
- jp2launcher.exe (PID: 236)
Checks supported languages
- hf.exe (PID: 5048)
- hf.exe (PID: 420)
- msiexec.exe (PID: 6628)
- MSIB77B.tmp (PID: 6556)
- msiexec.exe (PID: 5292)
- jaureg.exe (PID: 2852)
- hf.exe (PID: 6208)
- hf.exe (PID: 4024)
- msiexec.exe (PID: 5484)
- msiexec.exe (PID: 6632)
- installer.exe (PID: 6160)
- javaw.exe (PID: 4780)
- javaws.exe (PID: 2876)
- ssvagent.exe (PID: 4020)
- jp2launcher.exe (PID: 236)
- javaws.exe (PID: 4592)
- jp2launcher.exe (PID: 5328)
- msiexec.exe (PID: 6196)
- javaw.exe (PID: 6200)
- javaw.exe (PID: 6888)
- msiexec.exe (PID: 4344)
- msiexec.exe (PID: 6744)
- BRATS V4.2.exe (PID: 7120)
Reads the computer name
- hf.exe (PID: 420)
- hf.exe (PID: 5048)
- msiexec.exe (PID: 6628)
- msiexec.exe (PID: 5292)
- msiexec.exe (PID: 5484)
- hf.exe (PID: 6208)
- MSIB77B.tmp (PID: 6556)
- hf.exe (PID: 4024)
- msiexec.exe (PID: 6632)
- installer.exe (PID: 6160)
- javaws.exe (PID: 2876)
- jp2launcher.exe (PID: 236)
- javaws.exe (PID: 4592)
- jp2launcher.exe (PID: 5328)
- msiexec.exe (PID: 6196)
- javaw.exe (PID: 6888)
- msiexec.exe (PID: 4344)
- msiexec.exe (PID: 6744)
- javaw.exe (PID: 6200)
- BRATS V4.2.exe (PID: 7120)
Reads the machine GUID from the registry
- hf.exe (PID: 5048)
- hf.exe (PID: 4024)
- msiexec.exe (PID: 6628)
Reads Environment values
- hf.exe (PID: 5048)
- hf.exe (PID: 4024)
Creates files or folders in the user directory
- hf.exe (PID: 5048)
- hf.exe (PID: 4024)
- msiexec.exe (PID: 6628)
- jp2launcher.exe (PID: 236)
Reads CPU info
- msiexec.exe (PID: 6628)
Starts application with an unusual extension
- msiexec.exe (PID: 6628)
Checks proxy server information
- hf.exe (PID: 5048)
- hf.exe (PID: 4024)
- jp2launcher.exe (PID: 5328)
- jp2launcher.exe (PID: 236)
Reads the software policy settings
- hf.exe (PID: 5048)
- msiexec.exe (PID: 6628)
- hf.exe (PID: 4024)
Process checks Internet Explorer phishing filters
- hf.exe (PID: 5048)
- hf.exe (PID: 4024)
Application launched itself
- msiexec.exe (PID: 6628)
Creates files in the program directory
- javaw.exe (PID: 4780)
- installer.exe (PID: 6160)
Creates a software uninstall entry
- msiexec.exe (PID: 6628)
Reads Microsoft Office registry keys
- installer.exe (PID: 6160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
166
Monitored processes
28
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files\Java\jre1.8.0_421\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_421" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfNDIxXGxpYlxkZXBsb3kuamFyAC1EamF2YS5zZWN1cml0eS5wb2xpY3k9ZmlsZTpDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfNDIxXGxpYlxzZWN1cml0eVxqYXZhd3MucG9saWN5AC1EdHJ1c3RQcm94eT10cnVlAC1YdmVyaWZ5OnJlbW90ZQAtRGpubHB4LmhvbWU9QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzQyMVxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURzdW4uYXd0Lndhcm11cD10cnVlAC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF80MjFcbGliXGphdmF3cy5qYXI7QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzQyMVxsaWJcZGVwbG95LmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfNDIxXGxpYlxwbHVnaW4uamFyAC1EamF2YS5hd3QuaGVhZGxlc3M9dHJ1ZQAtRGpubHB4Lmp2bT1DOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfNDIxXGJpblxqYXZhdy5leGU= -ma LXdhaXQALWZpeAAtcGVybWlzc2lvbnMALXNpbGVudAAtbm90V2ViSmF2YQ== | C:\Program Files\Java\jre1.8.0_421\bin\jp2launcher.exe | — | javaws.exe | |||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.421.2.09 Modules
| |||||||||||||||
| 420 | "C:\Users\admin\Desktop\hf.exe" | C:\Users\admin\Desktop\hf.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.4210.9 Modules
| |||||||||||||||
| 1116 | "C:\Windows\SysWOW64\msiexec.exe" /x {4A03706F-666A-4037-7777-5F2748764D10} /qn | C:\Windows\SysWOW64\msiexec.exe | — | jaureg.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2524 | "C:\Users\admin\Desktop\hf.exe" | C:\Users\admin\Desktop\hf.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Platform SE binary Exit code: 3221226540 Version: 8.0.4210.9 Modules
| |||||||||||||||
| 2852 | "C:\Program Files (x86)\Common Files\Java\Java Update\jaureg.exe" -u auto-update | C:\Program Files (x86)\Common Files\Java\Java Update\jaureg.exe | MSIB77B.tmp | ||||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java Update Registration Exit code: 0 Version: 2.8.271.9 Modules
| |||||||||||||||
| 2876 | "C:\Program Files\Java\jre1.8.0_421\bin\javaws.exe" -wait -fix -permissions -silent | C:\Program Files\Java\jre1.8.0_421\bin\javaws.exe | installer.exe | ||||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.421.2.09 Modules
| |||||||||||||||
| 4020 | "C:\Program Files\Java\jre1.8.0_421\bin\ssvagent.exe" -doHKCUSSVSetup | C:\Program Files\Java\jre1.8.0_421\bin\ssvagent.exe | — | installer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 11.421.2.09 Modules
| |||||||||||||||
| 4024 | "C:\Users\admin\AppData\Local\Temp\jds1102515.tmp\hf.exe" | C:\Users\admin\AppData\Local\Temp\jds1102515.tmp\hf.exe | hf.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.4210.9 Modules
| |||||||||||||||
| 4088 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | jaureg.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4344 | C:\Windows\syswow64\MsiExec.exe -Embedding 12E3C53FB254EE530528FC4EE29AB902 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
51 501
Read events
24 403
Write events
12 579
Delete events
14 519
Modification events
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\twe.rar | |||
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
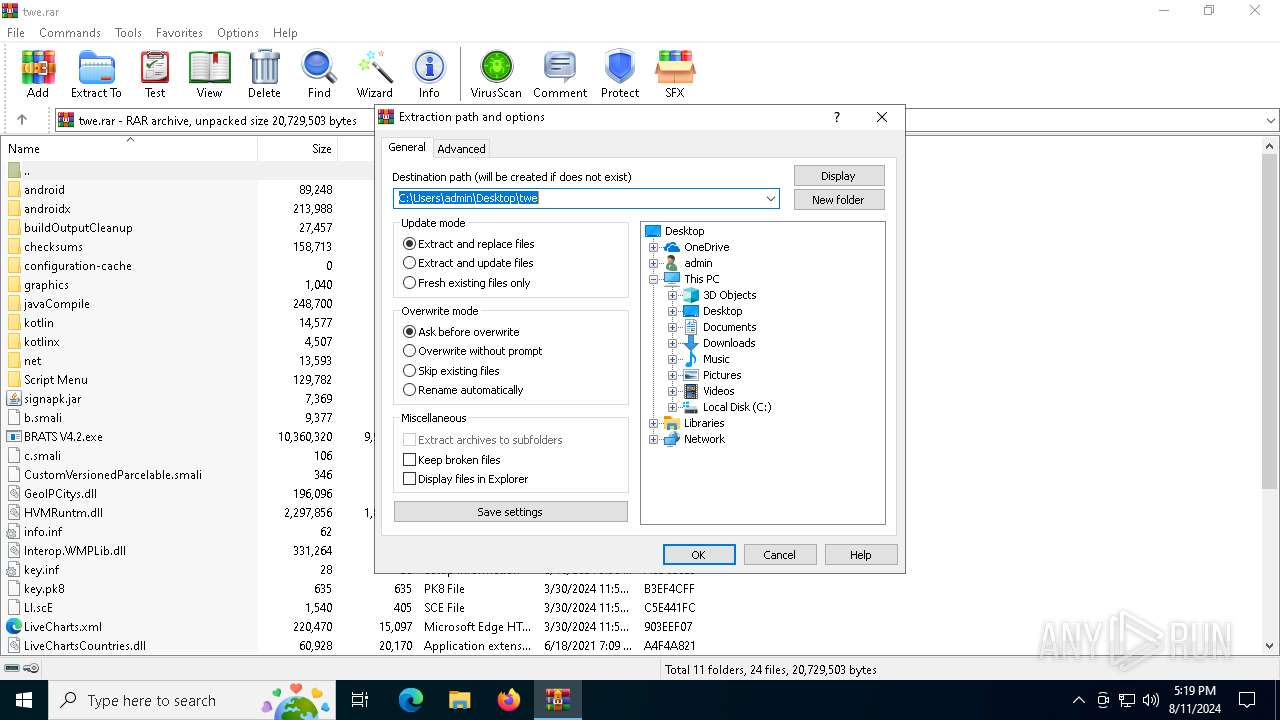
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (5048) hf.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft |
| Operation: | delete value | Name: | InstallStatus |
Value: | |||
Executable files
353
Suspicious files
138
Text files
288
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6392 | WinRAR.exe | C:\Users\admin\Desktop\kotlin\jvm\internal\IDxLambdaShape58S0000000_2_I1.smali | text | |
MD5:104DB889AC0063DEC3522591386F5F7B | SHA256:E859DFC71884323575BBFF171A8FA2928553E685367C32CACC2CB6E5AC4B3F0D | |||
| 6392 | WinRAR.exe | C:\Users\admin\Desktop\javaCompile\classAnalysis.bin | binary | |
MD5:1B216A899DD7F48DEFF5CEB24AF3F61B | SHA256:48804FE180688CB7B4C47CAE62A4C2D63EBA1AD73D8D2FF3B5F60849ABD58C3D | |||
| 6392 | WinRAR.exe | C:\Users\admin\Desktop\Script Menu\Add Timecode to all Media.cs | text | |
MD5:DCB8B90C1D24D0240ECEC7BDCC16BBA2 | SHA256:3407D353A949E51CADEF8A3C267C60A9AB6B466DD9C79D859276403ECAA099E7 | |||
| 6392 | WinRAR.exe | C:\Users\admin\Desktop\javaCompile\taskHistory.bin | binary | |
MD5:D22AD44936D2B2FAFA99EE87FD1C8262 | SHA256:954112F5A8B0F1FA71ADB5EB2AA28F754401DF645EEAC95B95B85FE4764E4EA2 | |||
| 6392 | WinRAR.exe | C:\Users\admin\Desktop\kotlinx\coroutines\android\AndroidDispatcherFactory.smali | text | |
MD5:0027E441B4EED066B89B0D51C30DB4D0 | SHA256:E86FDB3AB89F23EC76FAAC83C1C8C21E6A3B410914CB6E8FE722DF37F373A490 | |||
| 6392 | WinRAR.exe | C:\Users\admin\Desktop\kotlin\jvm\internal\IDxLambdaShape57S0000000_2_I0.smali | text | |
MD5:0CA13DF7A21D6DE5B86980D08AA4B0A8 | SHA256:B951CDD11A090AB69501A02A859CD8F8CD25E51CAD874A233A1D1D14E5BA0D63 | |||
| 6392 | WinRAR.exe | C:\Users\admin\Desktop\kotlin\jvm\internal\IDxLambdaShape55S0000000_2_I0.smali | text | |
MD5:9C72085961885946FA871A95D94C4AA7 | SHA256:6B091E950917510B9AAD1FBB64A24679FEFB3AD7DED09745AC73EFFC2038FB73 | |||
| 6392 | WinRAR.exe | C:\Users\admin\Desktop\Script Menu\Batch Render.cs | text | |
MD5:37BBAA26CFAB8777C893846E5007F2CF | SHA256:7028211EC01FEFBA1DBD9A6820BA1B34C3C1E67F89EB09F3BEBE9264F04B9B86 | |||
| 6392 | WinRAR.exe | C:\Users\admin\Desktop\kotlin\jvm\internal\IDxLambdaShape59S0000000_2_I1.smali | text | |
MD5:E2D12A28A7780B9F07EF7353349DC934 | SHA256:192DD5857B22C8BBDA6A6B848354E5E64D1D9927E5825C2606465166F4AF28B4 | |||
| 6392 | WinRAR.exe | C:\Users\admin\Desktop\Script Menu\Export Chapters.cs | text | |
MD5:F1A9DDFC2BA4CDF0334D680BD2F9E17D | SHA256:56A4650C6D9B2A3BDC3438272BEB608C92E33F6FE70E5DEF16FEEAAB44410E75 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
49
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6628 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
6628 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
6628 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAYOL4%2BeG4vlGNX%2BK2nPzLE%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6736 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1928 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5048 | hf.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEA2ypEAZl9ZmFI%2BR0FmZENI%3D | unknown | — | — | whitelisted |
5048 | hf.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
6784 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5388 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5244 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5388 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 2.23.209.154:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1928 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |