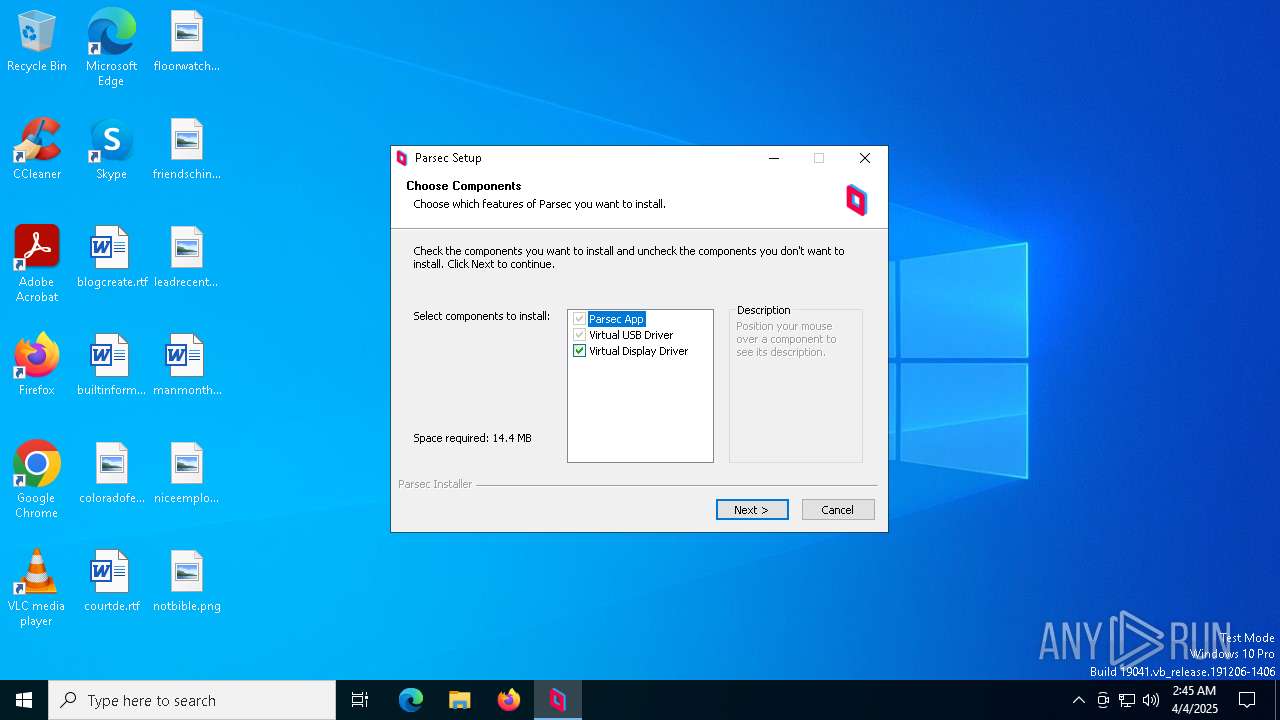
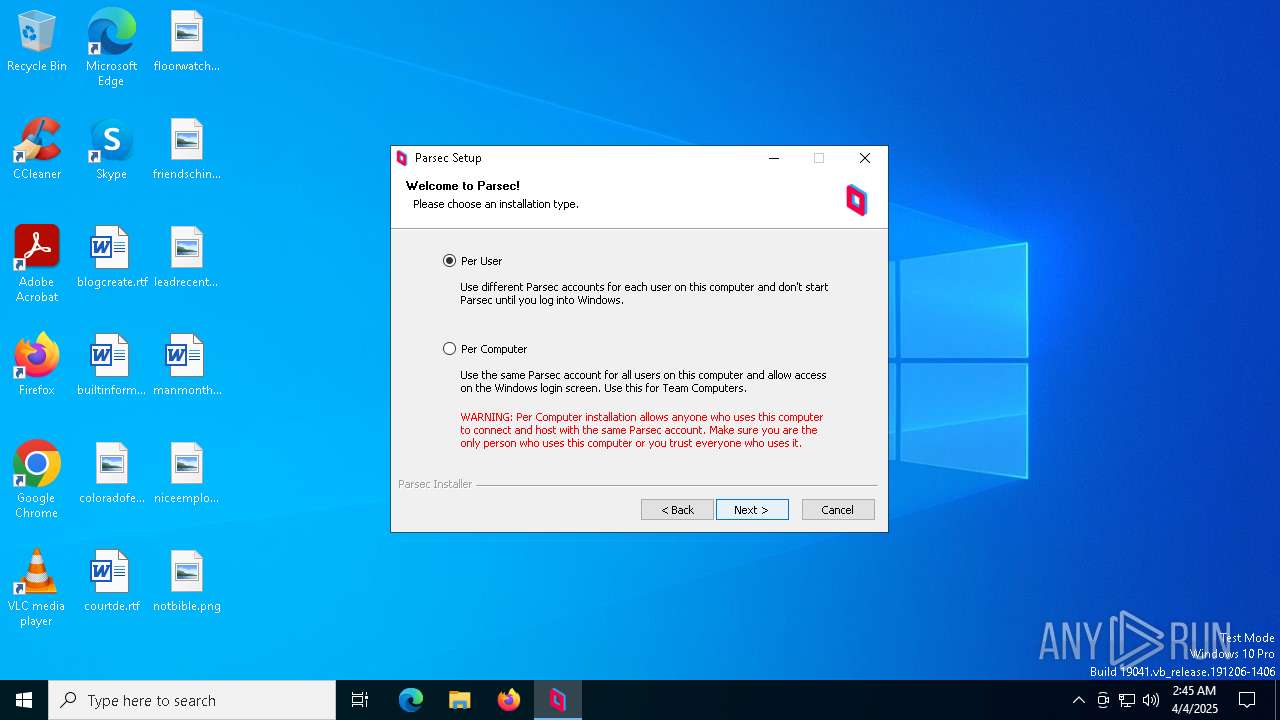
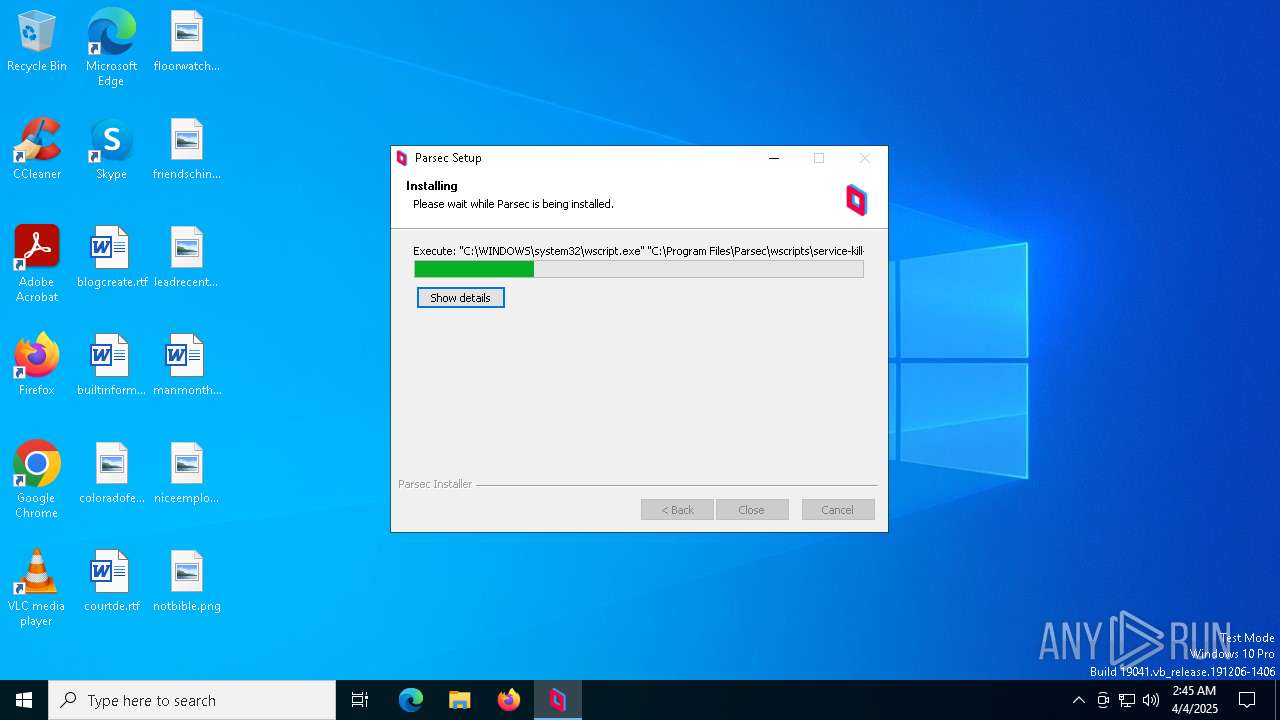
| File name: | parsec-windows.exe |
| Full analysis: | https://app.any.run/tasks/a3780929-a92c-4190-b85b-2e77ecf4729c |
| Verdict: | Malicious activity |
| Analysis date: | April 04, 2025, 02:44:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 0B9F6C9D89E9B427A469F34988B48F2C |
| SHA1: | DC29246551FB3BAAF77DCB3B926A2BF7E6FC567A |
| SHA256: | 206CD186AAA431D3975EB30F682B83851EF4F81125D2004F53B681117DA23EC6 |
| SSDEEP: | 98304:i8QkWrhYycq4DJLyPsYLhOtx+WVCj5VWMkV17LrQQSrLhdtjB2MzxuPhzAPHwZLM:23UUScD |
MALICIOUS
Executing a file with an untrusted certificate
- parsec-windows.exe (PID: 6004)
- parsec-windows.exe (PID: 812)
- pservice.exe (PID: 2096)
- parsecd.exe (PID: 7404)
- parsecd.exe (PID: 7336)
- parsecd.exe (PID: 7528)
Changes the autorun value in the registry
- nefconw.exe (PID: 3008)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- parsec-windows.exe (PID: 6004)
- parsec-vud.exe (PID: 4756)
- parsec-vdd.exe (PID: 1388)
There is functionality for taking screenshot (YARA)
- parsec-windows.exe (PID: 6004)
The process creates files with name similar to system file names
- parsec-windows.exe (PID: 6004)
- parsec-vud.exe (PID: 4756)
- parsec-vdd.exe (PID: 1388)
Executable content was dropped or overwritten
- parsec-windows.exe (PID: 6004)
- parsec-vud.exe (PID: 4756)
- drvinst.exe (PID: 1388)
- nefconw.exe (PID: 6324)
- drvinst.exe (PID: 4608)
- nefconw.exe (PID: 3008)
- parsec-vdd.exe (PID: 1388)
- drvinst.exe (PID: 840)
- nefconw.exe (PID: 1328)
- parsecd.exe (PID: 7336)
- parsecd.exe (PID: 7404)
The process executes VB scripts
- parsec-windows.exe (PID: 6004)
Windows service management via SC.EXE
- sc.exe (PID: 5344)
- sc.exe (PID: 6512)
- sc.exe (PID: 5956)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4024)
- wscript.exe (PID: 6656)
- wscript.exe (PID: 5436)
- wscript.exe (PID: 2316)
- wscript.exe (PID: 5156)
- wscript.exe (PID: 4448)
Uses TASKKILL.EXE to kill process
- wscript.exe (PID: 4024)
Stops a currently running service
- sc.exe (PID: 2516)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 5436)
- wscript.exe (PID: 5156)
- wscript.exe (PID: 4448)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- wscript.exe (PID: 5436)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 5244)
Creates a software uninstall entry
- parsec-windows.exe (PID: 6004)
- parsec-vud.exe (PID: 4756)
- parsec-vdd.exe (PID: 1388)
Creates a new Windows service
- sc.exe (PID: 4652)
Executes as Windows Service
- pservice.exe (PID: 2096)
- WUDFHost.exe (PID: 2516)
Starts CMD.EXE for commands execution
- parsec-vud.exe (PID: 4756)
- parsec-windows.exe (PID: 6004)
- parsec-vdd.exe (PID: 1388)
Drops a system driver (possible attempt to evade defenses)
- parsec-vud.exe (PID: 4756)
- nefconw.exe (PID: 6324)
- drvinst.exe (PID: 1388)
- drvinst.exe (PID: 4608)
- nefconw.exe (PID: 3008)
Executing commands from a ".bat" file
- parsec-vud.exe (PID: 4756)
- parsec-vdd.exe (PID: 1388)
Uses NETSH.EXE to add a firewall rule or allowed programs
- wscript.exe (PID: 4448)
Creates files in the driver directory
- drvinst.exe (PID: 1388)
- drvinst.exe (PID: 4608)
- drvinst.exe (PID: 840)
Creates or modifies Windows services
- drvinst.exe (PID: 3100)
- drvinst.exe (PID: 968)
- drvinst.exe (PID: 6268)
- drvinst.exe (PID: 7148)
Uses WEVTUTIL.EXE to remove publishers and event logs from the manifest
- parsec-vdd.exe (PID: 1388)
- wevtutil.exe (PID: 5156)
Reads security settings of Internet Explorer
- parsecd.exe (PID: 7336)
- parsecd.exe (PID: 7528)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- parsec-vdd.exe (PID: 1388)
- wevtutil.exe (PID: 7236)
Application launched itself
- parsecd.exe (PID: 7404)
INFO
Create files in a temporary directory
- parsec-windows.exe (PID: 6004)
- parsec-vud.exe (PID: 4756)
- nefconw.exe (PID: 6324)
- nefconw.exe (PID: 3008)
- parsec-vdd.exe (PID: 1388)
- nefconw.exe (PID: 1328)
Checks supported languages
- parsec-windows.exe (PID: 6004)
- pservice.exe (PID: 2096)
- nefconc.exe (PID: 1616)
- nefconw.exe (PID: 2040)
- nefconw.exe (PID: 6324)
- parsec-vud.exe (PID: 4756)
- drvinst.exe (PID: 1388)
- drvinst.exe (PID: 3100)
- nefconw.exe (PID: 3008)
- drvinst.exe (PID: 968)
- drvinst.exe (PID: 6268)
- drvinst.exe (PID: 4608)
- nefconw.exe (PID: 5436)
- parsec-vdd.exe (PID: 1388)
- drvinst.exe (PID: 840)
- nefconw.exe (PID: 1568)
- nefconw.exe (PID: 1328)
- parsecd.exe (PID: 7336)
- parsecd.exe (PID: 7404)
- drvinst.exe (PID: 7148)
- parsecd.exe (PID: 7528)
The sample compiled with english language support
- parsec-windows.exe (PID: 6004)
- parsec-vud.exe (PID: 4756)
- parsec-vdd.exe (PID: 1388)
- nefconw.exe (PID: 1328)
- drvinst.exe (PID: 840)
- parsecd.exe (PID: 7336)
- parsecd.exe (PID: 7404)
Reads the computer name
- parsec-windows.exe (PID: 6004)
- pservice.exe (PID: 2096)
- nefconw.exe (PID: 2040)
- drvinst.exe (PID: 1388)
- drvinst.exe (PID: 3100)
- nefconw.exe (PID: 6324)
- drvinst.exe (PID: 968)
- drvinst.exe (PID: 4608)
- drvinst.exe (PID: 6268)
- nefconw.exe (PID: 3008)
- nefconw.exe (PID: 5436)
- nefconw.exe (PID: 1568)
- drvinst.exe (PID: 840)
- nefconw.exe (PID: 1328)
- parsecd.exe (PID: 7336)
- parsecd.exe (PID: 7404)
- drvinst.exe (PID: 7148)
- parsecd.exe (PID: 7528)
Creates files in the program directory
- parsec-windows.exe (PID: 6004)
- parsec-vud.exe (PID: 4756)
- parsec-vdd.exe (PID: 1388)
- parsecd.exe (PID: 7336)
- parsecd.exe (PID: 7404)
- parsecd.exe (PID: 7528)
Reads the machine GUID from the registry
- drvinst.exe (PID: 1388)
- drvinst.exe (PID: 4608)
- drvinst.exe (PID: 840)
- parsecd.exe (PID: 7336)
- pservice.exe (PID: 2096)
- parsecd.exe (PID: 7404)
- parsecd.exe (PID: 7528)
Reads the software policy settings
- drvinst.exe (PID: 1388)
- drvinst.exe (PID: 4608)
- drvinst.exe (PID: 840)
- parsecd.exe (PID: 7336)
- pservice.exe (PID: 2096)
- parsecd.exe (PID: 7404)
- parsecd.exe (PID: 7528)
Reads the time zone
- runonce.exe (PID: 5156)
Reads security settings of Internet Explorer
- runonce.exe (PID: 5156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:55:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 184832 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 150.97.4.0 |
| ProductVersionNumber: | 150.97.4.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Parsec |
| FileVersion: | 150.97.4.0 |
| ProductName: | Parsec |
Total processes
204
Monitored processes
71
Malicious processes
14
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | "C:\Users\admin\Downloads\parsec-windows.exe" | C:\Users\admin\Downloads\parsec-windows.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Parsec Exit code: 3221226540 Version: 150.97.4.0 Modules
| |||||||||||||||
| 840 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{4710e3ba-e5c2-434e-85aa-492647effbd8}\mm.inf" "9" "484386e17" "0000000000000214" "WinSta0\Default" "0000000000000218" "208" "C:\Program Files\Parsec Virtual Display Driver\driver" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 928 | C:\WINDOWS\system32\cmd.exe /c ""C:\Program Files\Parsec Virtual Display Driver\vddinstall.bat"" | C:\Windows\SysWOW64\cmd.exe | — | parsec-vdd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | DrvInst.exe "8" "4" "C:\WINDOWS\System32\DriverStore\FileRepository\parsecvirtualds.inf_amd64_37113b1521fc4458\parsecvirtualds.inf" "0" "43799a85b" "0000000000000210" "WinSta0\Default" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | cmd /c "C:\Program Files\Parsec Virtual USB Adapter Driver\nefconc.exe" --find-hwid --hardware-id VUSBA | C:\Windows\SysWOW64\cmd.exe | — | parsec-vud.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1168 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
30 132
Read events
30 001
Write events
114
Delete events
17
Modification events
| (PID) Process: | (6004) parsec-windows.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Parsec.App.0 |
Value: | |||
| (PID) Process: | (6004) parsec-windows.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Parsec |
| Operation: | write | Name: | Comments |
Value: Parsec | |||
| (PID) Process: | (6004) parsec-windows.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Parsec |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Parsec\parsecd.exe | |||
| (PID) Process: | (6004) parsec-windows.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Parsec |
| Operation: | write | Name: | DisplayName |
Value: Parsec | |||
| (PID) Process: | (6004) parsec-windows.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Parsec |
| Operation: | write | Name: | DisplayVersion |
Value: 150-97d | |||
| (PID) Process: | (6004) parsec-windows.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Parsec |
| Operation: | write | Name: | EstimatedSize |
Value: 8414 | |||
| (PID) Process: | (6004) parsec-windows.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Parsec |
| Operation: | write | Name: | HelpLink |
Value: https://support.parsec.app | |||
| (PID) Process: | (6004) parsec-windows.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Parsec |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Parsec | |||
| (PID) Process: | (6004) parsec-windows.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Parsec |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (6004) parsec-windows.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Parsec |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
Executable files
40
Suspicious files
46
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6004 | parsec-windows.exe | C:\Program Files\Parsec\parsecd.exe | executable | |
MD5:3AD33F9CB1EFF184217E44C5970990E0 | SHA256:38011E713B4BE8577576062754CAD03E9899859488932AE4C9C83E5FBB5CB7D2 | |||
| 6004 | parsec-windows.exe | C:\Program Files\Parsec\wscripts\firewall-remove.vbs | text | |
MD5:5D4D70CDF36FCDAA292DA1DA9133320C | SHA256:75F1DECE4FDA689A907F6D74B513ADB0C1771C1B79EA71160179542C9C4AB2F0 | |||
| 6004 | parsec-windows.exe | C:\Program Files\Parsec\wscripts\legacy-cleanup.vbs | text | |
MD5:C78520C3162C1962F3164714B37EB4D0 | SHA256:DEA38BD553ABE93C689DE42D0220ADD18F9BE3E3D2FA53F97EB8649F586DF4F3 | |||
| 6004 | parsec-windows.exe | C:\Program Files\Parsec\vdd\parsec-vdd.exe | executable | |
MD5:4B9A3048286692A865187013B70F44E8 | SHA256:E23332448FDAF5AA017CB308DB5EF6855FAC526A7DED05D80C039404126D5362 | |||
| 6004 | parsec-windows.exe | C:\Program Files\Parsec\wscripts\firewall-add.vbs | text | |
MD5:882374285898F16B5F9FF44AFC1AE701 | SHA256:0BE5AA5CC6395A86878F56B131E13DB4908E48F06E892FF8F8CF9E2D3B6C8ABB | |||
| 6004 | parsec-windows.exe | C:\Program Files\Parsec\skel\parsecd-150-97d.dll | executable | |
MD5:983575B7678000A2DB45DD1673F946BD | SHA256:1902241E12ADBDF40ED4DAFC410CCBCF8E07FCE117D540DABBC2F75FF371F5BE | |||
| 6004 | parsec-windows.exe | C:\Program Files\Parsec\teams.exe | executable | |
MD5:FAA24223985ABFBF64E4DDCD43F062D3 | SHA256:6DC71B2E92B770DCFECA4A32C8F1787210311F731F1124754DF193EC22D5D13E | |||
| 6004 | parsec-windows.exe | C:\Program Files\Parsec\vusb\parsec-vud.exe | executable | |
MD5:FA2814C8CFF38B2F4737085C70154B8F | SHA256:F8DB024B61C36E5D45CA5B485BF855DBFE1D0523333158E873D7DEB4D86EC0E4 | |||
| 6004 | parsec-windows.exe | C:\Program Files\Parsec\pservice.exe | executable | |
MD5:C0FDABE612162A5CEE54773EFFE66625 | SHA256:CC62D22BF8A082621FA25FDEEE3150C17B09DBC09C9371E3DCDD6EC83967770C | |||
| 6004 | parsec-windows.exe | C:\Program Files\Parsec\skel\appdata.json | binary | |
MD5:C57289047FA04DA4A193C3C5C06DE960 | SHA256:4EF5DB1CEA63AF5102B1B445479CE61C5E017A9B633347251C70CBADC4BCBBC6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
36
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6048 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7404 | parsecd.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
6048 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7404 | parsecd.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAloEugzUPGt9OnVZ%2FPPgls%3D | unknown | — | — | whitelisted |
7404 | parsecd.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 20.197.71.89:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2800 | svchost.exe | 95.100.186.9:443 | go.microsoft.com | AKAMAI-AS | FR | whitelisted |
6048 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |