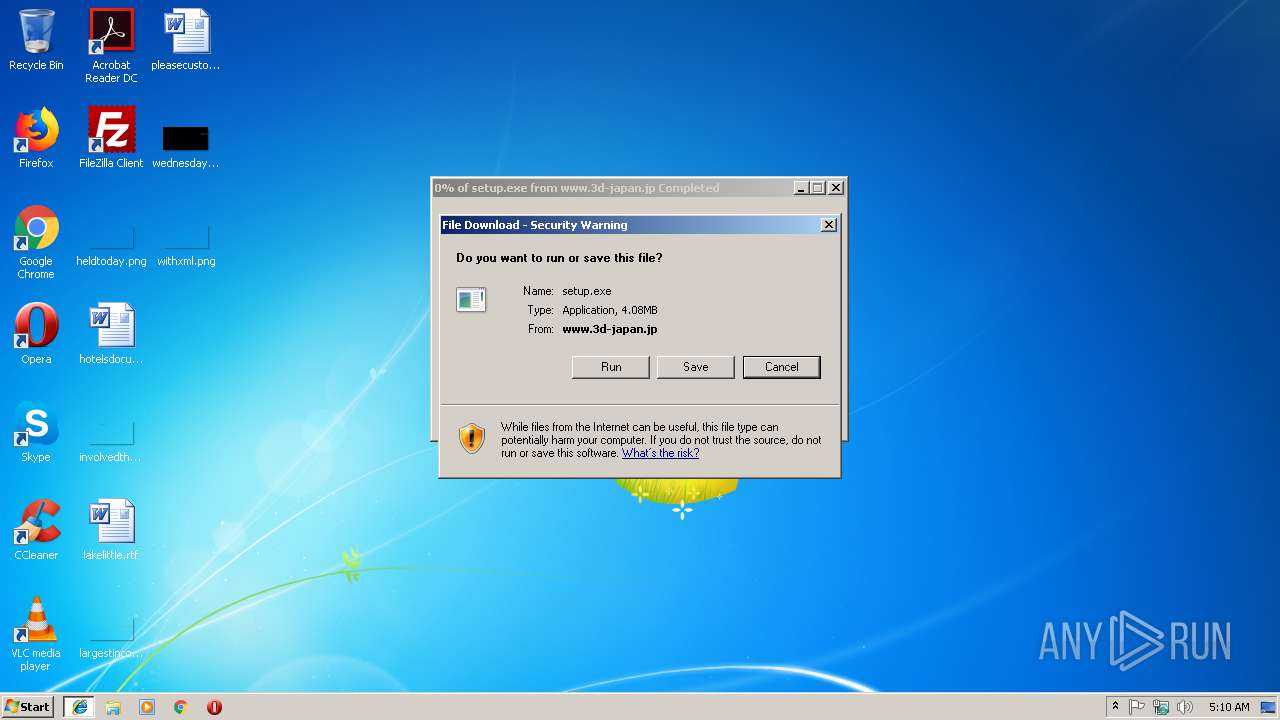
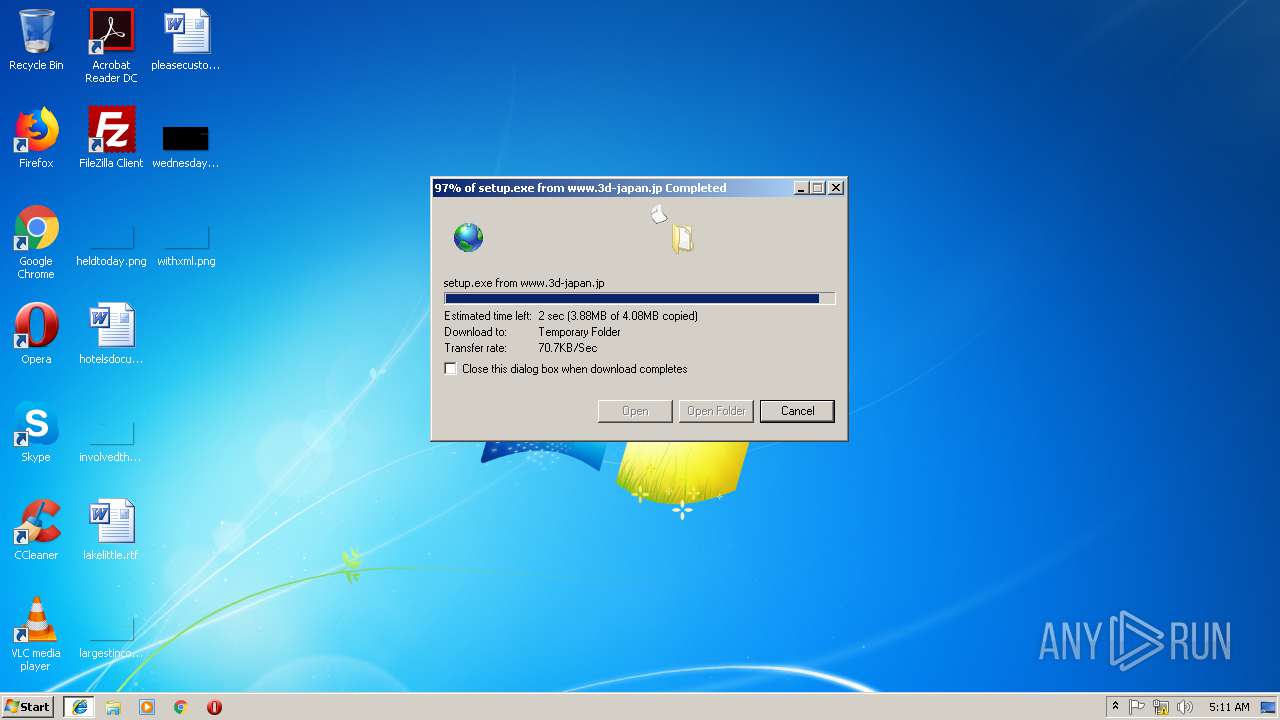
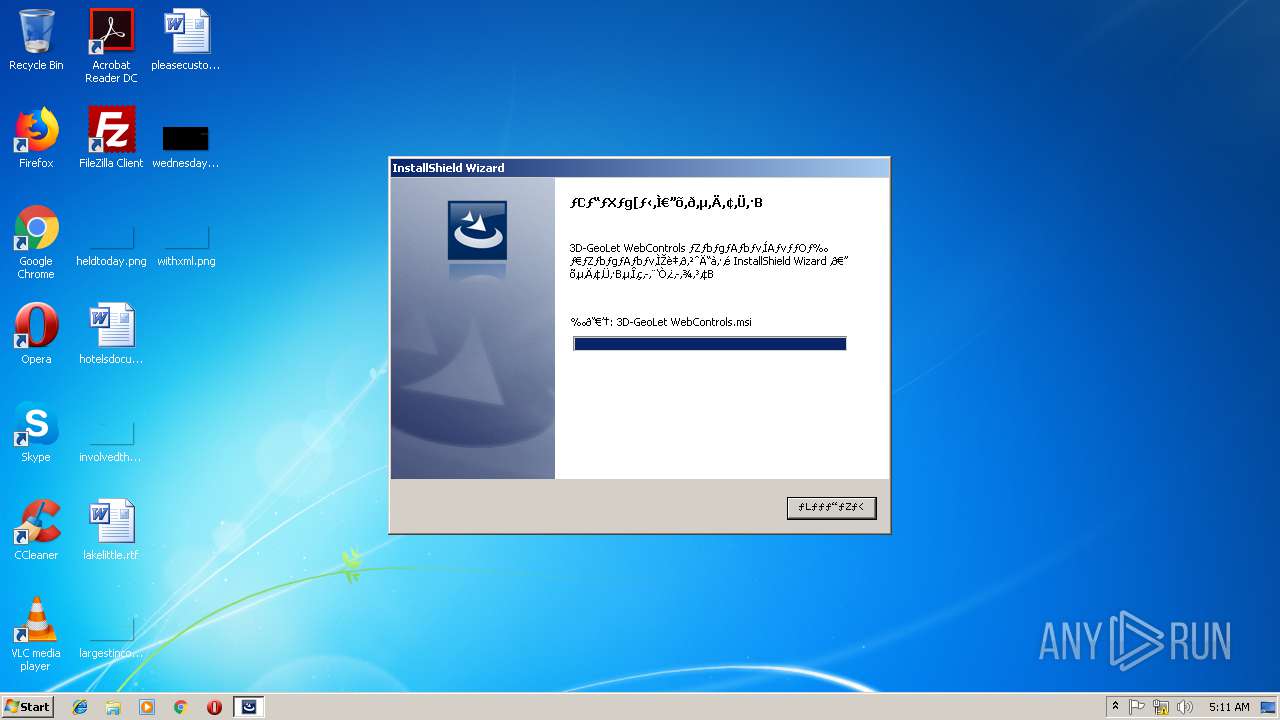
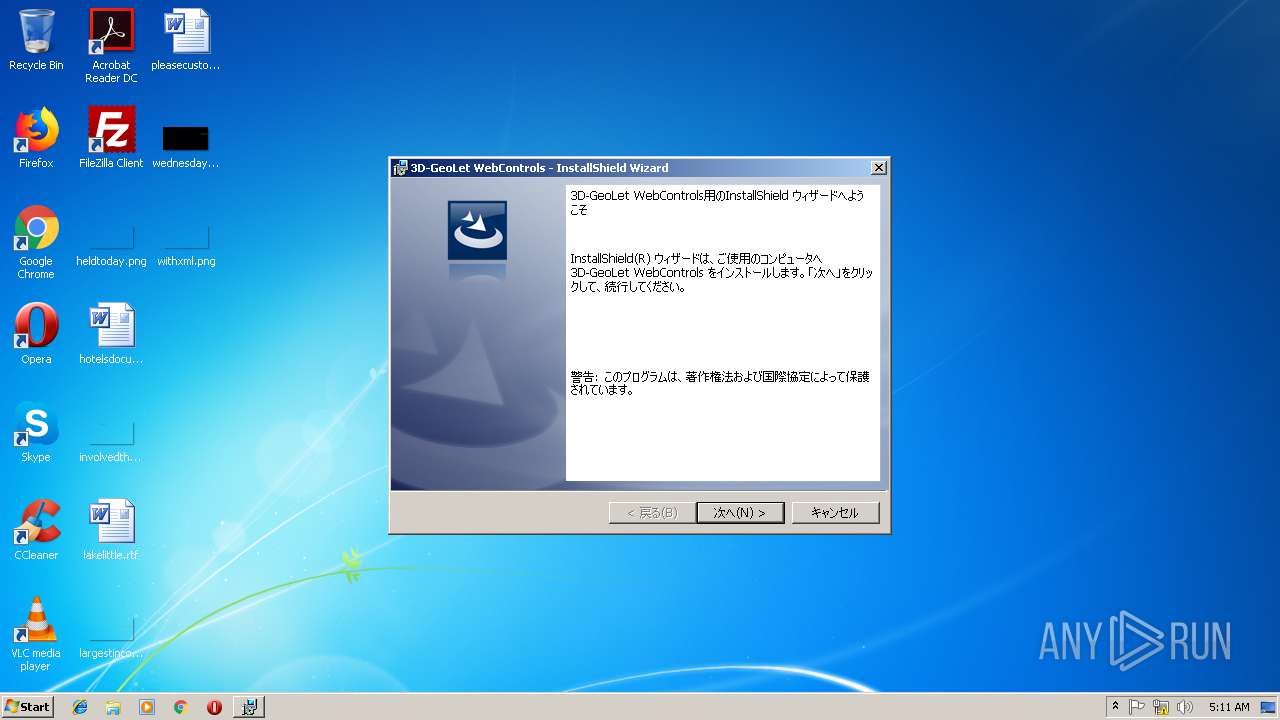
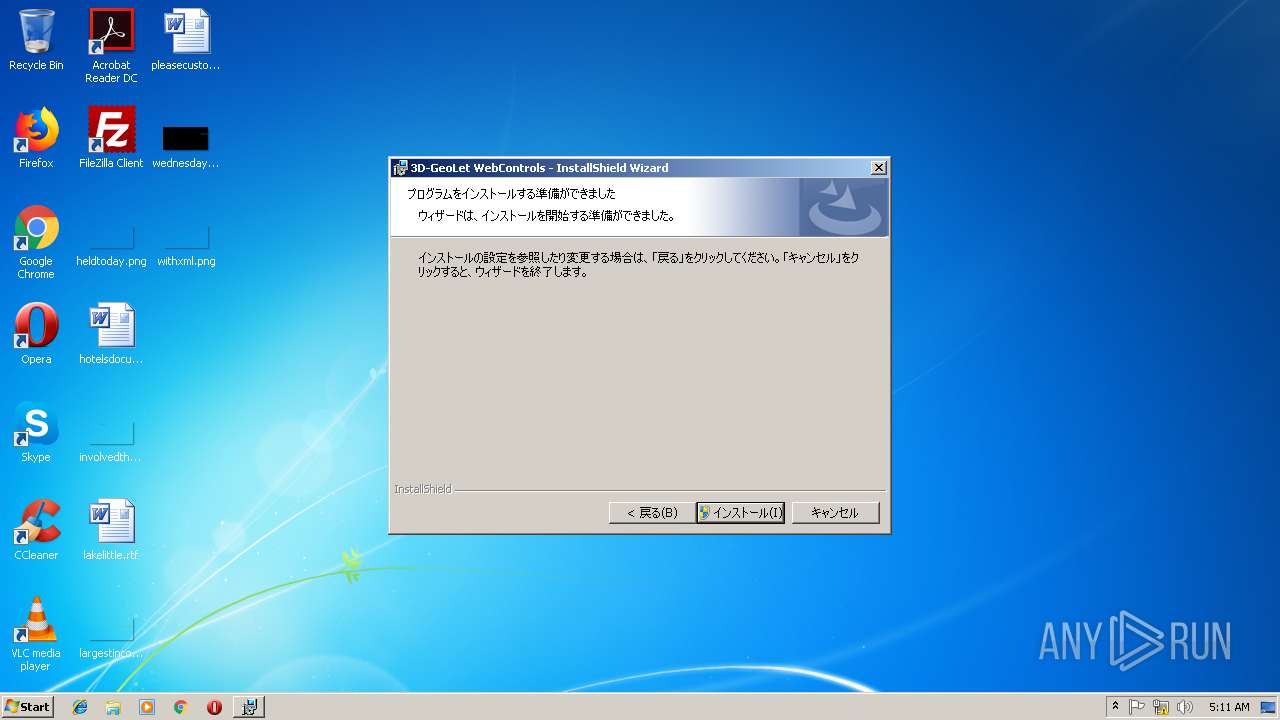
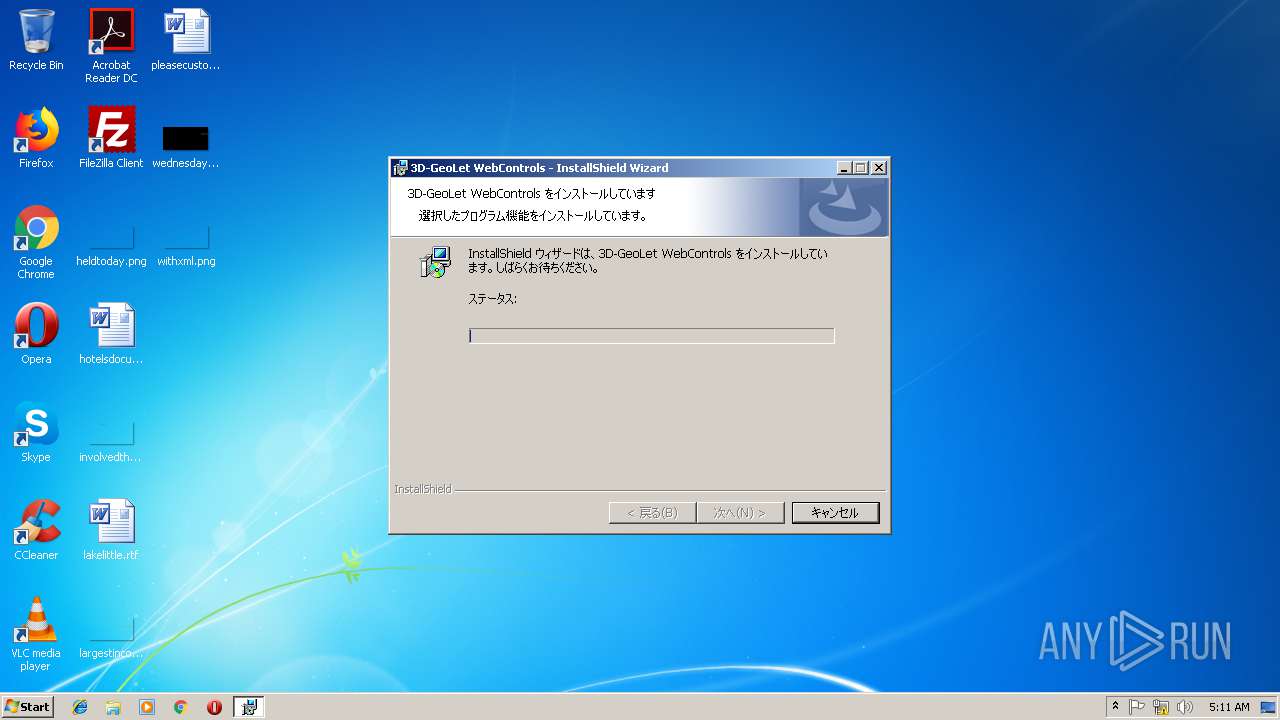
| URL: | http://www.3d-japan.jp/minamiizu/setup.exe |
| Full analysis: | https://app.any.run/tasks/526476d1-5b5f-40cb-a694-f71aae778c5d |
| Verdict: | Malicious activity |
| Analysis date: | February 19, 2019, 05:09:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 1067CE991C1D68D1717CFC39D9A83831 |
| SHA1: | 3479372631D57E3CD394F7863B985E6815D6BD9D |
| SHA256: | 206C14C913CA06E57531FD1DEDEAC2F10B5CDA4AC390CA58250CEA069B44C51C |
| SSDEEP: | 3:N1KJS4GI5LsEIJWAY4A:Cc4G0RP4A |
MALICIOUS
Application was dropped or rewritten from another process
- setup[1].exe (PID: 2784)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 3048)
- setup[1].exe (PID: 2784)
- iexplore.exe (PID: 2932)
- msiexec.exe (PID: 2320)
Starts Microsoft Installer
- setup[1].exe (PID: 2784)
Creates COM task schedule object
- msiexec.exe (PID: 2320)
INFO
Application launched itself
- iexplore.exe (PID: 2932)
- msiexec.exe (PID: 2320)
Changes internet zones settings
- iexplore.exe (PID: 2932)
Creates files in the user directory
- iexplore.exe (PID: 2932)
- iexplore.exe (PID: 3048)
Reads Internet Cache Settings
- iexplore.exe (PID: 3048)
Searches for installed software
- msiexec.exe (PID: 2320)
Low-level read access rights to disk partition
- vssvc.exe (PID: 2772)
Creates files in the program directory
- msiexec.exe (PID: 2320)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 2320)
Creates a software uninstall entry
- msiexec.exe (PID: 2320)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2320 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2772 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2784 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\setup[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\setup[1].exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2932 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3048 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2932 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3256 | MSIEXEC.EXE /i "C:\Users\admin\AppData\Local\Temp\{EECCC073-441C-40D0-90B9-CC9DAE18F975}\3D-GeoLet WebControls.msi" SETUPEXEDIR="C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59" | C:\Windows\system32\MSIEXEC.EXE | — | setup[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3576 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot18" "" "" "6792c44eb" "00000000" "00000060" "00000064" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3872 | C:\Windows\system32\MsiExec.exe -Embedding B69F8651858E3431DBE9BB4E0FC1C0B5 C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 455
Read events
891
Write events
1 548
Delete events
16
Modification events
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {9AE5A2CB-3404-11E9-91D7-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E30702000200130005000A0000001503 | |||
Executable files
37
Suspicious files
8
Text files
52
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2932 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2932 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2932 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA50FA3A010FA565A.TMP | — | |
MD5:— | SHA256:— | |||
| 2784 | setup[1].exe | C:\Users\admin\AppData\Local\Temp\~778D.tmp | — | |
MD5:— | SHA256:— | |||
| 2932 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE58B6DE5DE1186B6.TMP | — | |
MD5:— | SHA256:— | |||
| 2932 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{9AE5A2CB-3404-11E9-91D7-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 3256 | MSIEXEC.EXE | C:\Users\admin\AppData\Local\Temp\MSI8D19.tmp | — | |
MD5:— | SHA256:— | |||
| 2320 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3048 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012019021920190220\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2932 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012019021920190220\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
2
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2932 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2932 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3048 | iexplore.exe | 113.43.205.210:80 | www.3d-japan.jp | UCOM Corp. | JP | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www.3d-japan.jp |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3048 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3048 | iexplore.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |