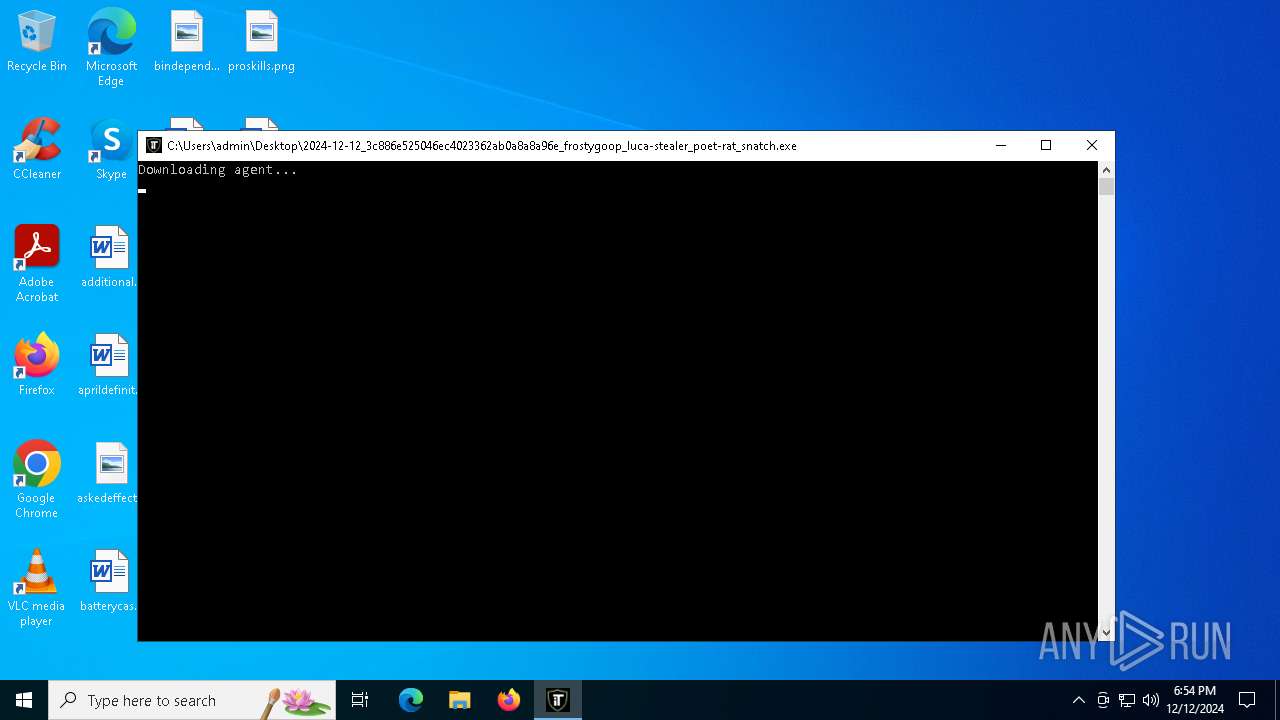
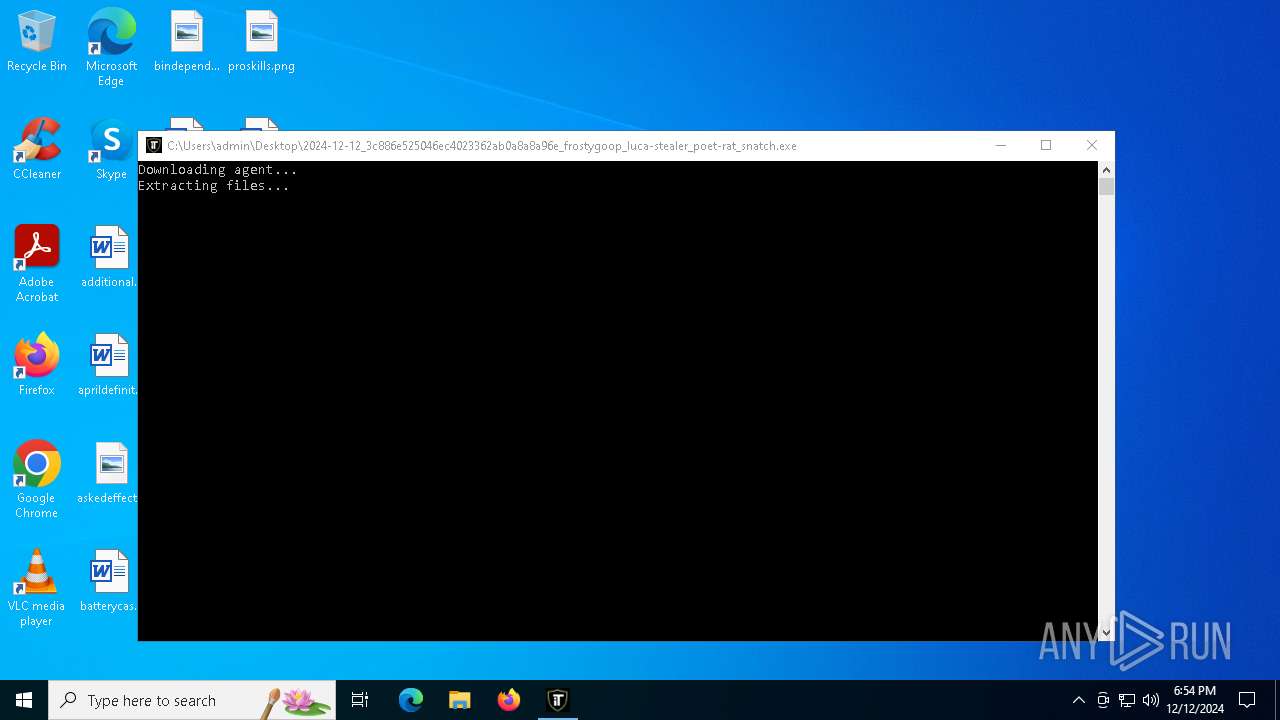
| File name: | 2024-12-12_3c886e525046ec4023362ab0a8a8a96e_frostygoop_luca-stealer_poet-rat_snatch |
| Full analysis: | https://app.any.run/tasks/c4c4a097-5e78-4c8c-80f6-e6d952febb09 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | December 12, 2024, 18:54:30 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64 (stripped to external PDB), for MS Windows, 7 sections |
| MD5: | 3C886E525046EC4023362AB0A8A8A96E |
| SHA1: | 9B43610B5B28FD3B573F7BD9073DC84B913BE909 |
| SHA256: | 205495309953CC878B28B5D5F9BC09D908CE8FC4170A98232C833D7C9687DC4F |
| SSDEEP: | 98304:Anz9OgdgXP7aOhkedjIz4ZSCxy1LYQau6q:c |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 2008)
- cmd.exe (PID: 3172)
- cmd.exe (PID: 640)
- cmd.exe (PID: 3992)
- net.exe (PID: 3780)
- net.exe (PID: 3032)
- cmd.exe (PID: 2572)
- net.exe (PID: 1988)
Bypass execution policy to execute commands
- powershell.exe (PID: 2224)
Changes powershell execution policy (Bypass)
- tacticalrmm.exe (PID: 3560)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 2224)
SUSPICIOUS
Executable content was dropped or overwritten
- 2024-12-12_3c886e525046ec4023362ab0a8a8a96e_frostygoop_luca-stealer_poet-rat_snatch.exe (PID: 4548)
- tacticalagent-v2.8.0-windows-amd64.exe (PID: 4864)
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 5268)
- tacticalrmm.exe (PID: 372)
- meshagent.exe (PID: 5992)
Reads the Windows owner or organization settings
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 5268)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3172)
- cmd.exe (PID: 3992)
Starts CMD.EXE for commands execution
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 5268)
Creates or modifies Windows services
- tacticalrmm.exe (PID: 5652)
- meshagent.exe (PID: 5992)
- tacticalrmm.exe (PID: 3560)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4392)
There is functionality for capture public ip (YARA)
- tacticalrmm.exe (PID: 372)
MeshAgent potential remote access (YARA)
- tacticalrmm.exe (PID: 372)
Executes as Windows Service
- MeshAgent.exe (PID: 4520)
- tacticalrmm.exe (PID: 3560)
Creates a software uninstall entry
- meshagent.exe (PID: 5992)
Searches for installed software
- tacticalrmm.exe (PID: 372)
- tacticalrmm.exe (PID: 3560)
Starts POWERSHELL.EXE for commands execution
- tacticalrmm.exe (PID: 3560)
The process executes Powershell scripts
- tacticalrmm.exe (PID: 3560)
The process hide an interactive prompt from the user
- tacticalrmm.exe (PID: 3560)
The process bypasses the loading of PowerShell profile settings
- tacticalrmm.exe (PID: 3560)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 2224)
Application launched itself
- tacticalrmm.exe (PID: 3560)
INFO
Checks supported languages
- 2024-12-12_3c886e525046ec4023362ab0a8a8a96e_frostygoop_luca-stealer_poet-rat_snatch.exe (PID: 4548)
- tacticalagent-v2.8.0-windows-amd64.exe (PID: 4864)
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 5268)
- tacticalrmm.exe (PID: 5652)
- tacticalrmm.exe (PID: 372)
- meshagent.exe (PID: 5992)
- MeshAgent.exe (PID: 4520)
- tacticalrmm.exe (PID: 3560)
The sample compiled with english language support
- 2024-12-12_3c886e525046ec4023362ab0a8a8a96e_frostygoop_luca-stealer_poet-rat_snatch.exe (PID: 4548)
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 5268)
- tacticalrmm.exe (PID: 372)
- meshagent.exe (PID: 5992)
Reads the computer name
- 2024-12-12_3c886e525046ec4023362ab0a8a8a96e_frostygoop_luca-stealer_poet-rat_snatch.exe (PID: 4548)
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 5268)
- tacticalrmm.exe (PID: 5652)
- meshagent.exe (PID: 5992)
- MeshAgent.exe (PID: 628)
- MeshAgent.exe (PID: 4520)
- tacticalrmm.exe (PID: 3560)
Reads the machine GUID from the registry
- 2024-12-12_3c886e525046ec4023362ab0a8a8a96e_frostygoop_luca-stealer_poet-rat_snatch.exe (PID: 4548)
- tacticalrmm.exe (PID: 5652)
- tacticalrmm.exe (PID: 372)
- tacticalrmm.exe (PID: 3560)
- tacticalrmm.exe (PID: 3488)
Creates files in the program directory
- 2024-12-12_3c886e525046ec4023362ab0a8a8a96e_frostygoop_luca-stealer_poet-rat_snatch.exe (PID: 4548)
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 5268)
- meshagent.exe (PID: 5992)
- MeshAgent.exe (PID: 4520)
- tacticalrmm.exe (PID: 372)
- tacticalrmm.exe (PID: 3560)
Reads the software policy settings
- 2024-12-12_3c886e525046ec4023362ab0a8a8a96e_frostygoop_luca-stealer_poet-rat_snatch.exe (PID: 4548)
- tacticalrmm.exe (PID: 372)
- tacticalrmm.exe (PID: 3560)
Create files in a temporary directory
- tacticalagent-v2.8.0-windows-amd64.exe (PID: 4864)
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 5268)
Application based on Golang
- 2024-12-12_3c886e525046ec4023362ab0a8a8a96e_frostygoop_luca-stealer_poet-rat_snatch.exe (PID: 4548)
- tacticalrmm.exe (PID: 372)
Creates a software uninstall entry
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 5268)
Reads Environment values
- tacticalrmm.exe (PID: 5652)
- tacticalrmm.exe (PID: 372)
Reads product name
- tacticalrmm.exe (PID: 5652)
- tacticalrmm.exe (PID: 372)
Drops encrypted VBS script (Microsoft Script Encoder)
- tacticalrmm.exe (PID: 3560)
The process uses the downloaded file
- powershell.exe (PID: 2224)
Drops encrypted JS script (Microsoft Script Encoder)
- tacticalrmm.exe (PID: 3560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 2520576 |
| InitializedDataSize: | 246784 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x66fe0 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 2.0.4.0 |
| ProductVersionNumber: | 2.0.4.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | AmidaWare LLC |
| FileDescription: | Tactical RMM Installer |
| FileVersion: | v2.0.4.0 |
| InternalName: | rmm.exe |
| LegalCopyright: | Copyright (c) 2022 AmidaWare LLC |
| OriginalFileName: | installer.go |
| ProductName: | Tactical RMM Installer |
| ProductVersion: | v2.0.4.0 |
Total processes
171
Monitored processes
46
Malicious processes
6
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 372 | "C:\Program Files\TacticalAgent\tacticalrmm.exe" -m install --api https://api.andvo.ru --client-id 1 --site-id 1 --agent-type workstation --auth 9542a8f8c22095f58aa4fecf581b66f40581f8bf0207b6afe759ede9e5b6411b | C:\Program Files\TacticalAgent\tacticalrmm.exe | 2024-12-12_3c886e525046ec4023362ab0a8a8a96e_frostygoop_luca-stealer_poet-rat_snatch.exe | ||||||||||||
User: admin Company: AmidaWare Inc Integrity Level: HIGH Description: Tactical RMM Agent Exit code: 0 Version: v2.8.0.0 Modules
| |||||||||||||||
| 628 | "C:\Program Files\Mesh Agent\MeshAgent.exe" -nodeid | C:\Program Files\Mesh Agent\MeshAgent.exe | — | tacticalrmm.exe | |||||||||||
User: admin Integrity Level: HIGH Description: MeshCentral Background Service Agent Exit code: 0 Version: 2022-Dec-2 11:42:16-0800 Modules
| |||||||||||||||
| 640 | "cmd.exe" /c net stop tacticalagent | C:\Windows\SysWOW64\cmd.exe | — | tacticalagent-v2.8.0-windows-amd64.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1304 | "C:\Program Files\Mesh Agent\MeshAgent.exe" -nodeid | C:\Program Files\Mesh Agent\MeshAgent.exe | — | tacticalrmm.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: MeshCentral Background Service Agent Exit code: 0 Version: 2022-Dec-2 11:42:16-0800 Modules
| |||||||||||||||
| 1804 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1988 | net start tacticalrmm | C:\Windows\SysWOW64\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
28 706
Read events
28 651
Write events
55
Delete events
0
Modification events
| (PID) Process: | (5268) tacticalagent-v2.8.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.2 | |||
| (PID) Process: | (5268) tacticalagent-v2.8.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\TacticalAgent | |||
| (PID) Process: | (5268) tacticalagent-v2.8.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\TacticalAgent\ | |||
| (PID) Process: | (5268) tacticalagent-v2.8.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: (Default) | |||
| (PID) Process: | (5268) tacticalagent-v2.8.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (5268) tacticalagent-v2.8.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: english | |||
| (PID) Process: | (5268) tacticalagent-v2.8.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | DisplayName |
Value: Tactical RMM Agent | |||
| (PID) Process: | (5268) tacticalagent-v2.8.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\TacticalAgent\tacticalrmm.exe | |||
| (PID) Process: | (5268) tacticalagent-v2.8.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\TacticalAgent\unins000.exe" | |||
| (PID) Process: | (5268) tacticalagent-v2.8.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Program Files\TacticalAgent\unins000.exe" /SILENT | |||
Executable files
9
Suspicious files
6
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5268 | tacticalagent-v2.8.0-windows-amd64.tmp | C:\Program Files\TacticalAgent\is-7SS2Q.tmp | executable | |
MD5:6CFBD2DA5F304A3B8972EAFE6FE4D191 | SHA256:AD29D4E9E01870FFBDB6F2498E6CE36A708E56DB2AD431BA2D80BF5A6CAAC069 | |||
| 5268 | tacticalagent-v2.8.0-windows-amd64.tmp | C:\Program Files\TacticalAgent\is-NFQ6A.tmp | executable | |
MD5:5E81857286E2795352225BE245FBD62B | SHA256:2624C22DA19E89717DCD522D22B21849A1C3F0EB781333DF85BE5FCD57597278 | |||
| 4548 | 2024-12-12_3c886e525046ec4023362ab0a8a8a96e_frostygoop_luca-stealer_poet-rat_snatch.exe | C:\ProgramData\TacticalRMM\tacticalagent-v2.8.0-windows-amd64.exe | executable | |
MD5:ED40540E7432BACAA08A6CD6A9F63004 | SHA256:D6C7BDAB07151678B713A02EFE7AD5281B194B0D5B538061BDAFDF2C4CA1FDAA | |||
| 5268 | tacticalagent-v2.8.0-windows-amd64.tmp | C:\Program Files\TacticalAgent\unins000.exe | executable | |
MD5:5E81857286E2795352225BE245FBD62B | SHA256:2624C22DA19E89717DCD522D22B21849A1C3F0EB781333DF85BE5FCD57597278 | |||
| 5268 | tacticalagent-v2.8.0-windows-amd64.tmp | C:\Program Files\TacticalAgent\unins000.dat | binary | |
MD5:0D9711E727C0551636A19AF1074AA5CD | SHA256:E97ADE5A12E4DF19EE71D6B1BFD9A173510EDBCBEB38523F8C718F517AEDC4DD | |||
| 5268 | tacticalagent-v2.8.0-windows-amd64.tmp | C:\Program Files\TacticalAgent\tacticalrmm.exe | executable | |
MD5:6CFBD2DA5F304A3B8972EAFE6FE4D191 | SHA256:AD29D4E9E01870FFBDB6F2498E6CE36A708E56DB2AD431BA2D80BF5A6CAAC069 | |||
| 5268 | tacticalagent-v2.8.0-windows-amd64.tmp | C:\Users\admin\AppData\Local\Temp\Setup Log 2024-12-12 #001.txt | text | |
MD5:951CD69FEE2F75DCAF56297BE77B0C4F | SHA256:EE68A81FF4DF6AB26FB3A04E434221F5B8E2148C3FAC40EE044D76E14FAF0EEE | |||
| 4520 | MeshAgent.exe | C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\SystemCertificates\My\Keys\EAA0AC7AD3E50B58E5FBBAA142C74D32DCE4DFAD | binary | |
MD5:5F27142BCD8772AF15C5961A2ABDD462 | SHA256:5FCF761059A0B22A5E85A315C0511CDF1935C21B9EB9C621D0514D4C76B5E715 | |||
| 372 | tacticalrmm.exe | C:\Program Files\TacticalAgent\meshagent.exe | executable | |
MD5:32E747EDA182352F2F1883979B8ECCAB | SHA256:2E94C1F68D529EDECEC9184EE10A3383153752FF57018585D7B491B1EBB6157C | |||
| 5992 | meshagent.exe | C:\Program Files\Mesh Agent\MeshAgent.exe | executable | |
MD5:32E747EDA182352F2F1883979B8ECCAB | SHA256:2E94C1F68D529EDECEC9184EE10A3383153752FF57018585D7B491B1EBB6157C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
54
DNS requests
18
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 302 | 140.82.121.3:443 | https://github.com/amidaware/rmmagent/releases/download/v2.8.0/tacticalagent-v2.8.0-windows-amd64.exe | unknown | — | — | unknown |
1356 | svchost.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1356 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 101 | 185.229.65.114:443 | https://api.andvo.ru/natsws | unknown | — | — | unknown |
— | — | GET | 101 | 185.229.65.114:443 | https://api.andvo.ru/natsws | unknown | — | — | unknown |
— | — | GET | 302 | 140.82.121.3:443 | https://github.com/amidaware/rmmagent/releases/download/v2.8.0/py3.11.9_amd64.zip | unknown | — | — | unknown |
— | — | GET | 302 | 140.82.121.3:443 | https://github.com/denoland/deno/releases/download/v1.44.4/deno-x86_64-pc-windows-msvc.zip | unknown | — | — | unknown |
— | — | GET | 302 | 140.82.121.3:443 | https://github.com/nushell/nushell/releases/download/0.93.0/nu-0.93.0-x86_64-windows-msvc-full.zip | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1356 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 104.126.37.171:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4548 | 2024-12-12_3c886e525046ec4023362ab0a8a8a96e_frostygoop_luca-stealer_poet-rat_snatch.exe | 140.82.121.3:443 | github.com | GITHUB | US | shared |
1356 | svchost.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4548 | 2024-12-12_3c886e525046ec4023362ab0a8a8a96e_frostygoop_luca-stealer_poet-rat_snatch.exe | 185.199.111.133:443 | objects.githubusercontent.com | FASTLY | US | shared |
4712 | MoUsoCoreWorker.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
github.com |
| shared |
crl.microsoft.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
www.microsoft.com |
| whitelisted |
api.andvo.ru |
| unknown |
mesh.andvo.ru |
| unknown |
icanhazip.tacticalrmm.io |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
— | — | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |