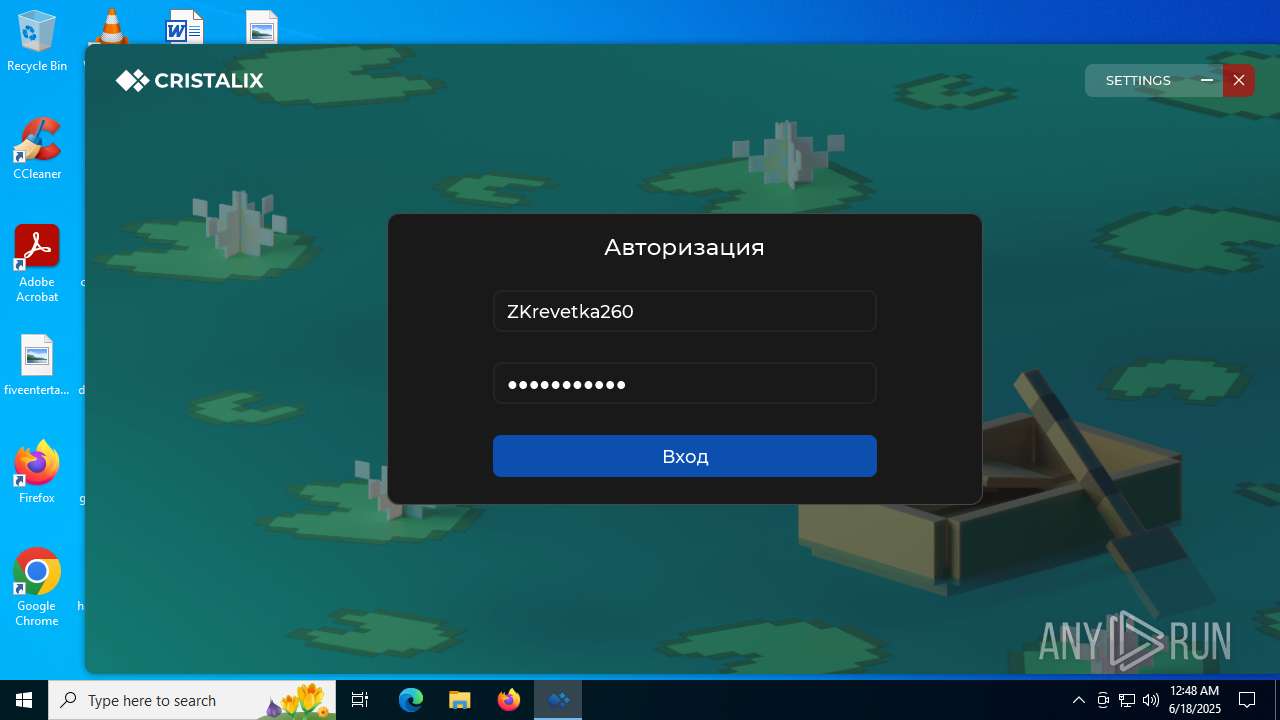
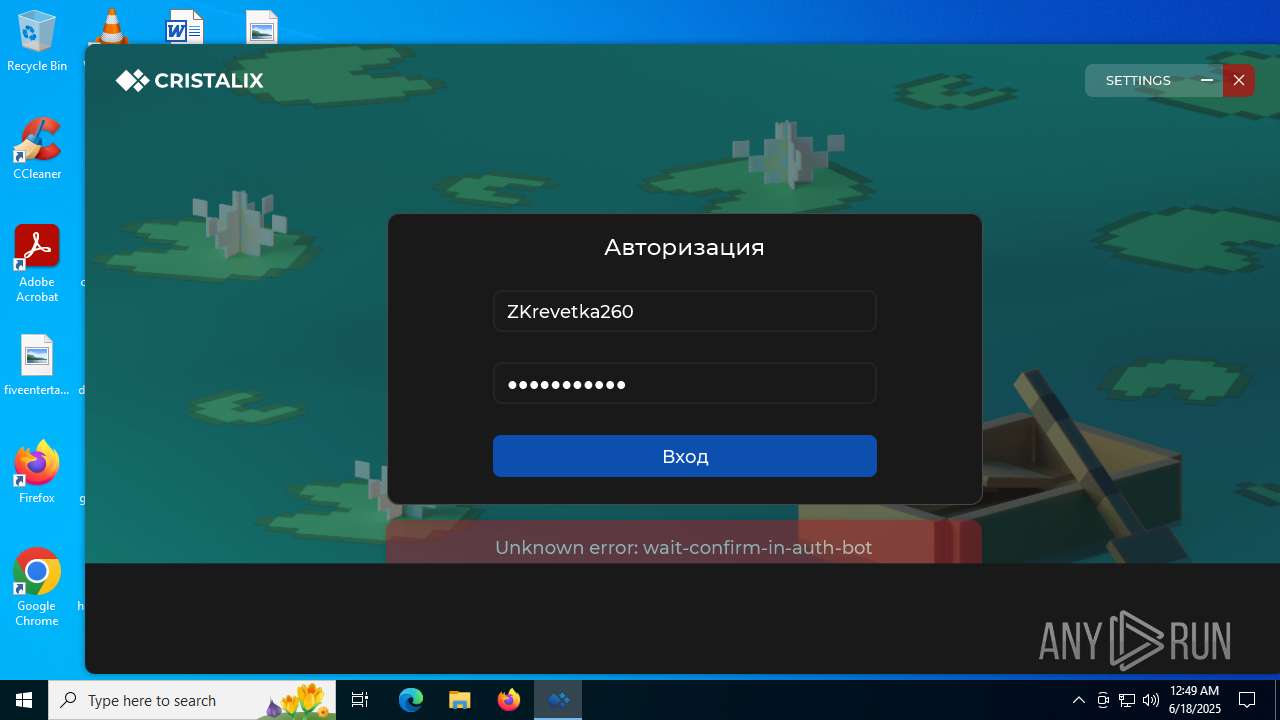
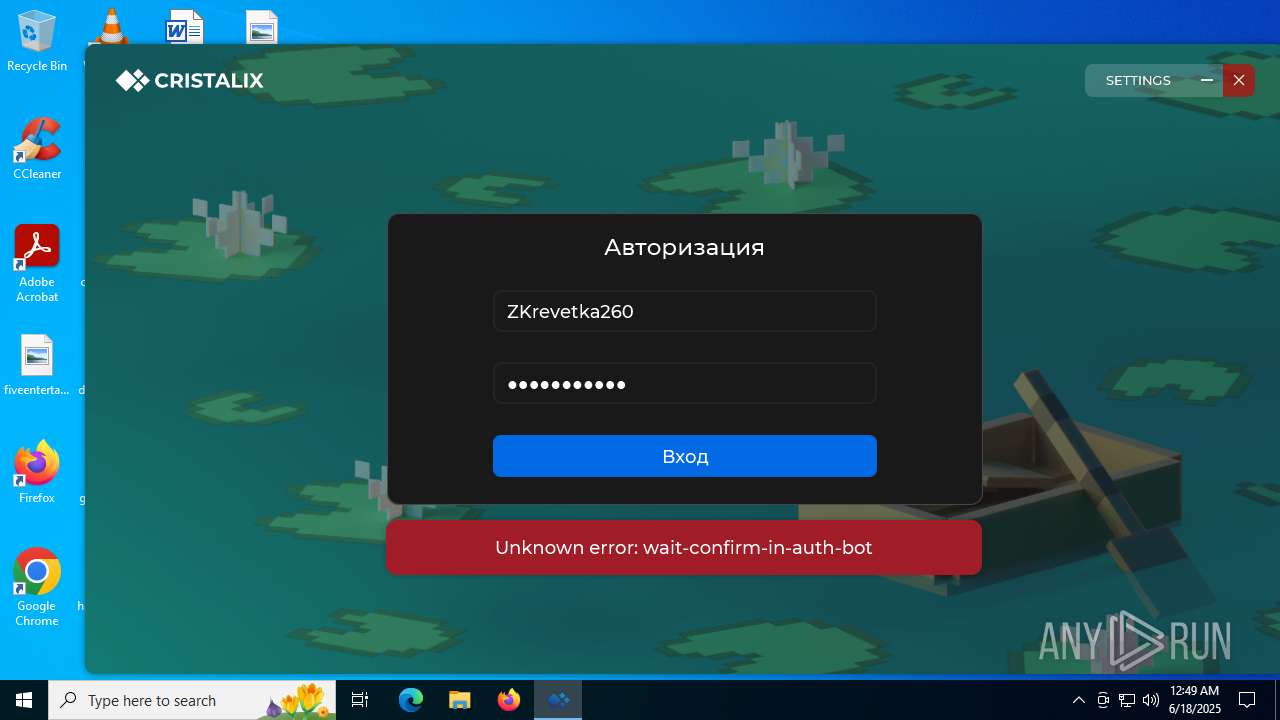
| File name: | Cristalix (1).exe |
| Full analysis: | https://app.any.run/tasks/1a3736fd-d7ca-4ee1-9308-75bf29205674 |
| Verdict: | Malicious activity |
| Analysis date: | June 18, 2025, 00:48:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive, with extra data prepended |
| MD5: | AD976BD32550E66CB82C81459D08B602 |
| SHA1: | F6CFE1D80CA681A846000A636EE72F7264B654AC |
| SHA256: | 203A34A75A3589121FB2BBCB81345B8CFC52A04D0ABB09018D949EE46FB058B0 |
| SSDEEP: | 98304:FMF7KcQdm/ohZISsV6MAAVGXbjrF6ODmhOL3l9bw5mUoh4SJZ2mk+Js58vRaQEl3:mqk59854sMDFq+Em |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks for Java to be installed
- Cristalix (1).exe (PID: 504)
Executable content was dropped or overwritten
- javaw.exe (PID: 6360)
There is functionality for taking screenshot (YARA)
- javaw.exe (PID: 6360)
The process drops C-runtime libraries
- javaw.exe (PID: 6360)
Process drops legitimate windows executable
- javaw.exe (PID: 6360)
Detected use of alternative data streams (AltDS)
- javaw.exe (PID: 6360)
INFO
The sample compiled with russian language support
- Cristalix (1).exe (PID: 504)
Create files in a temporary directory
- javaw.exe (PID: 6360)
Creates files in the program directory
- javaw.exe (PID: 6360)
Creates files or folders in the user directory
- javaw.exe (PID: 6360)
Checks supported languages
- javaw.exe (PID: 6360)
- Cristalix (1).exe (PID: 504)
Reads the computer name
- javaw.exe (PID: 6360)
The sample compiled with english language support
- javaw.exe (PID: 6360)
Reads the machine GUID from the registry
- javaw.exe (PID: 6360)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:09:19 06:58:07+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.32 |
| CodeSize: | 54784 |
| InitializedDataSize: | 107520 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x351d |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.1.0.0 |
| ProductVersionNumber: | 1.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Russian |
| CharacterSet: | Unicode |
| CompanyName: | Cristalix |
| FileDescription: | Cristalix Launcher |
| FileVersion: | 1.1.0.0 |
| InternalName: | Cristalix.exe |
| LegalCopyright: | Copyright (C) 2018-2022 Cristalix |
| OriginalFileName: | Cristalix.exe |
| ProductName: | Cristalix Launcher |
| ProductVersion: | 1.1.0.0 |
Total processes
139
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 504 | "C:\Users\admin\Desktop\Cristalix (1).exe" | C:\Users\admin\Desktop\Cristalix (1).exe | — | explorer.exe | |||||||||||
User: admin Company: Cristalix Integrity Level: MEDIUM Description: Cristalix Launcher Exit code: 0 Version: 1.1.0.0 Modules
| |||||||||||||||
| 2032 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6360 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -XX:MinHeapFreeRatio=5 -XX:MaxHeapFreeRatio=15 -jar "Cristalix (1).exe" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | Cristalix (1).exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Version: 8.0.2710.9 Modules
| |||||||||||||||
| 6460 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7000 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
868
Read events
868
Write events
0
Delete events
0
Modification events
Executable files
62
Suspicious files
493
Text files
127
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6360 | javaw.exe | C:\Users\admin\.cristalix\updates\24-jre-win-64\lib\modules | — | |
MD5:— | SHA256:— | |||
| 6360 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+JXF5145444697784564884.tmp | binary | |
MD5:ADE91F473255991F410F61857696434B | SHA256:C8289A870D238AA042BDFD09364FE6DEA524BCD1EA485341878D8C75A32AB444 | |||
| 6360 | javaw.exe | C:\Users\admin\.cristalix\updates\24-jre-win-64\conf\sound.properties | text | |
MD5:4F95242740BFB7B133B879597947A41E | SHA256:299C2360B6155EB28990EC49CD21753F97E43442FE8FAB03E04F3E213DF43A66 | |||
| 6360 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+JXF6580578887216718217.tmp | pi2 | |
MD5:C8B6E083AF3F94009801989C3739425E | SHA256:421F26B23E2BE6B98373D32ACD3CB2897B154D4BF0A77D26534CE476E4CBED53 | |||
| 6360 | javaw.exe | C:\Users\admin\.cristalix\updates\24-jre-win-64\conf\net.properties | text | |
MD5:1F251A36EB37913B696B5BE5595E1CD0 | SHA256:594BC40230A0BD7C441FE069989D66E534A6BAE2EE5910F9F4BF64E59B583256 | |||
| 6360 | javaw.exe | C:\Users\admin\.cristalix\updates\24-jre-win-64\conf\jaxp.properties | text | |
MD5:80F4A5F43C22B97BE120E0716974A029 | SHA256:D4F45052A100E5AEF02B6638A3B9C69B2BDD46155CEB58A52671E5D594C30100 | |||
| 6360 | javaw.exe | C:\Users\admin\.cristalix\updates\24-jre-win-64\conf\logging.properties | text | |
MD5:C4B74648F229C4B7E62A1061EE1DC3F0 | SHA256:8590633E1E8A7D88FFE74CC04189C5C61B1ED4703180CBC851DCD5575EFCCE74 | |||
| 6360 | javaw.exe | C:\Users\Public\desktop.ini:WinDeviceId | binary | |
MD5:F68716B1246697BB48D829A3833810A2 | SHA256:861DB123DB137665F864B9E2D05D909B081974C6C05BB01E977F1EA983C3CFC9 | |||
| 6360 | javaw.exe | C:\Users\admin\.cristalix\updates\24-jre-win-64\conf\jaxp-strict.properties.template | text | |
MD5:FD9C1610C84407BF676DC11322C522A7 | SHA256:3CC9B87633769414B22C24C97ECDED8A15DF630FE5AB12ABCA2398D88E31B32B | |||
| 6360 | javaw.exe | C:\Users\admin\.cristalix\updates\24-jre-win-64\bin\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:31990AAAB1AEEAE6BFF96EAF3809EDA9 | SHA256:D71714C34FABF8A93AE316A0D8679BB8CDC843F6128C9AFD42E18E0DE70B1A91 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
44
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4644 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2580 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2580 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
856 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6360 | javaw.exe | 95.181.182.182:443 | rucdn2.c7x.dev | EdgeCenter LLC | RU | malicious |
6360 | javaw.exe | 95.129.233.174:443 | rudynamiclnchr.c7x.dev | — | RU | unknown |
6360 | javaw.exe | 95.129.233.149:443 | rustaticlnchr.c7x.dev | — | RU | unknown |
6360 | javaw.exe | 95.129.233.178:443 | cristalix.gg | — | RU | unknown |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
rucdn2.c7x.dev |
| unknown |
rustorage.c7x.dev |
| unknown |
rudynamiclnchr.c7x.dev |
| unknown |
rustaticlnchr.c7x.dev |
| unknown |
ruwebdata.c7x.dev |
| unknown |
cristalix.gg |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |