| File name: | JRT_8.1.4.exe |
| Full analysis: | https://app.any.run/tasks/cdcd4589-af0f-4a82-8240-5613c0ad3957 |
| Verdict: | Malicious activity |
| Analysis date: | February 12, 2024, 23:57:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | E40542C4CC75E658A4615BFEFB308570 |
| SHA1: | 961A8C8C332494201E4F275FE1F50ABAE99140B3 |
| SHA256: | 2000ACF98EF0AC1A2D75C91586B5F30A2BC3ECE6E92388B324614C93A0645CF5 |
| SSDEEP: | 98304:ofPy7aaBPMFofjtZ7dvirsNhwx5SWAxVILeVnW7Hlr8AKpG7l6I3keTo7HUlmn1m:Agd |
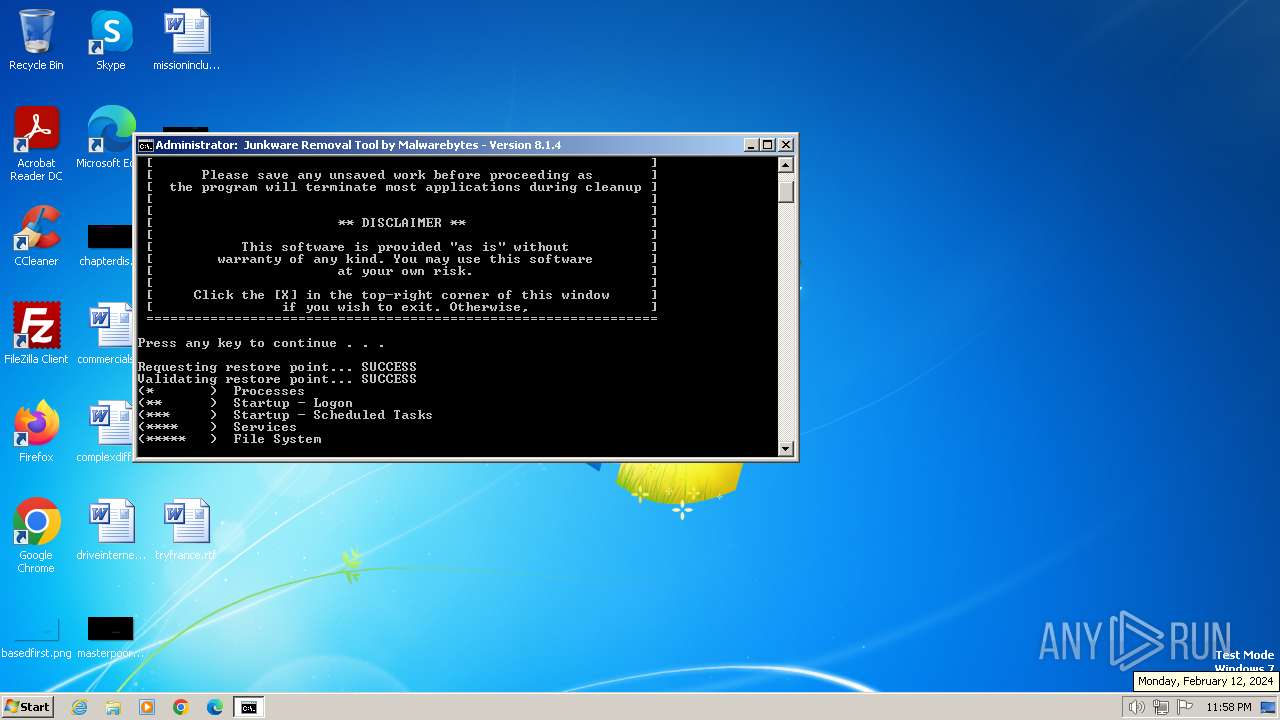
MALICIOUS
Drops the executable file immediately after the start
- JRT_8.1.4.exe (PID: 3772)
SUSPICIOUS
Reads the Internet Settings
- JRT_8.1.4.exe (PID: 3772)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2848)
- JRT_8.1.4.exe (PID: 3772)
Starts application with an unusual extension
- cmd.exe (PID: 2848)
Executing commands from a ".bat" file
- JRT_8.1.4.exe (PID: 3772)
Reads security settings of Internet Explorer
- JRT_8.1.4.exe (PID: 3772)
Application launched itself
- cmd.exe (PID: 2848)
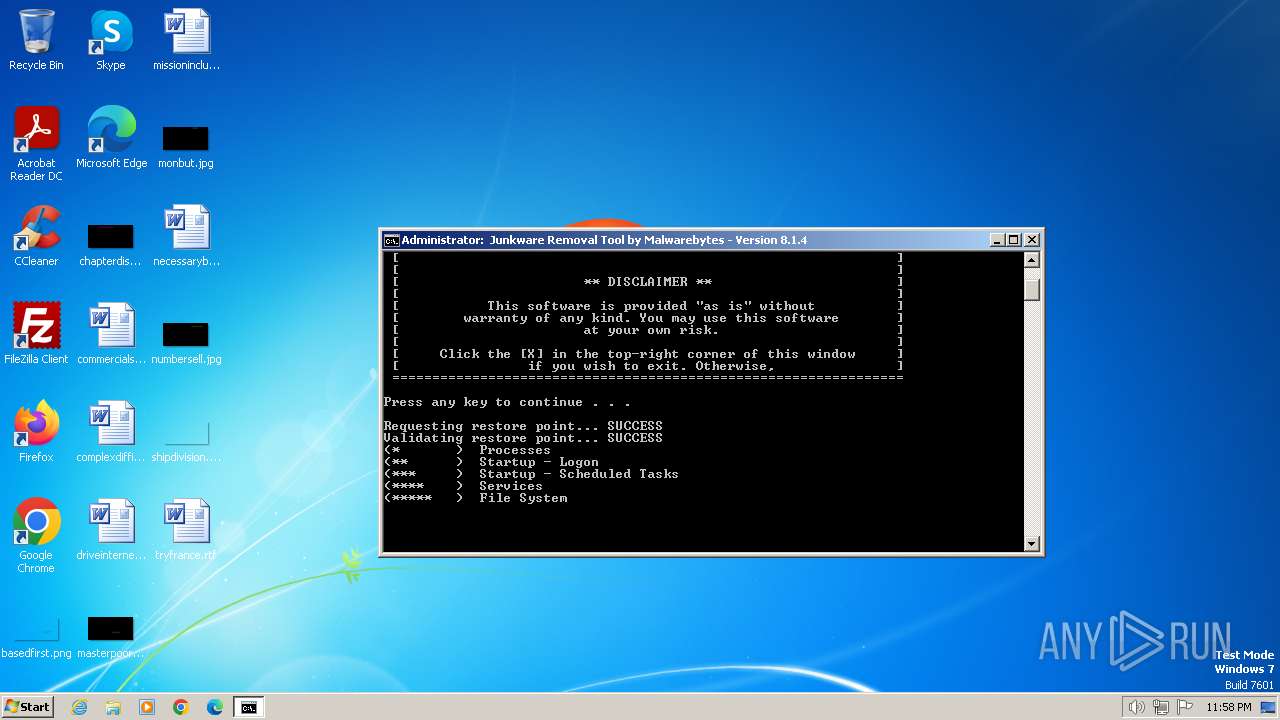
The executable file from the user directory is run by the CMD process
- WGET.DAT (PID: 2856)
- CreateRestorePoint.exe (PID: 2896)
- GREP.DAT (PID: 992)
- SED.DAT (PID: 2248)
- GREP.DAT (PID: 1840)
- GREP.DAT (PID: 2052)
- GREP.DAT (PID: 1636)
- SED.DAT (PID: 2584)
- SORT_.DAT (PID: 1216)
- GREP.DAT (PID: 920)
- GREP.DAT (PID: 3404)
- GREP.DAT (PID: 1020)
- GREP.DAT (PID: 2956)
- GREP.DAT (PID: 1124)
- GREP.DAT (PID: 1820)
- GREP.DAT (PID: 1736)
- GREP.DAT (PID: 3272)
- GREP.DAT (PID: 2828)
- GREP.DAT (PID: 1652)
- SED.DAT (PID: 2736)
- GREP.DAT (PID: 3456)
- GREP.DAT (PID: 3808)
- GREP.DAT (PID: 584)
- GREP.DAT (PID: 3440)
- GREP.DAT (PID: 2492)
- GREP.DAT (PID: 2740)
- GREP.DAT (PID: 3044)
- GREP.DAT (PID: 2228)
- GREP.DAT (PID: 3548)
- GREP.DAT (PID: 4036)
- GREP.DAT (PID: 1196)
- GREP.DAT (PID: 3748)
- GREP.DAT (PID: 3860)
- GREP.DAT (PID: 3452)
- GREP.DAT (PID: 3268)
- GREP.DAT (PID: 3284)
- GREP.DAT (PID: 4016)
- GREP.DAT (PID: 2044)
- GREP.DAT (PID: 3660)
- GREP.DAT (PID: 2328)
- GREP.DAT (PID: 3500)
- GREP.DAT (PID: 2692)
- GREP.DAT (PID: 864)
- GREP.DAT (PID: 1696)
- GREP.DAT (PID: 2860)
- GREP.DAT (PID: 1432)
- GREP.DAT (PID: 1388)
- GREP.DAT (PID: 4044)
- GREP.DAT (PID: 1860)
- GREP.DAT (PID: 2996)
- GREP.DAT (PID: 3364)
- GREP.DAT (PID: 2072)
Executable content was dropped or overwritten
- JRT_8.1.4.exe (PID: 3772)
Executes as Windows Service
- VSSVC.exe (PID: 3180)
Searches for installed software
- CreateRestorePoint.exe (PID: 2896)
Get information on the list of running processes
- cmd.exe (PID: 2848)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2848)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2848)
INFO
Create files in a temporary directory
- JRT_8.1.4.exe (PID: 3772)
Checks supported languages
- JRT_8.1.4.exe (PID: 3772)
- WGET.DAT (PID: 2856)
- CreateRestorePoint.exe (PID: 2896)
- GREP.DAT (PID: 1840)
- SED.DAT (PID: 2248)
- GREP.DAT (PID: 992)
- GREP.DAT (PID: 2052)
- GREP.DAT (PID: 1636)
- SED.DAT (PID: 2584)
- SORT_.DAT (PID: 1216)
- GREP.DAT (PID: 3404)
- GREP.DAT (PID: 920)
- GREP.DAT (PID: 1020)
- GREP.DAT (PID: 2956)
- GREP.DAT (PID: 1124)
- GREP.DAT (PID: 3272)
- GREP.DAT (PID: 1820)
- GREP.DAT (PID: 1736)
- GREP.DAT (PID: 2828)
Reads the computer name
- JRT_8.1.4.exe (PID: 3772)
- CreateRestorePoint.exe (PID: 2896)
- WGET.DAT (PID: 2856)
Reads the machine GUID from the registry
- WGET.DAT (PID: 2856)
- CreateRestorePoint.exe (PID: 2896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:06:27 07:06:38+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 70656 |
| InitializedDataSize: | 52224 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x11def |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.1.4.0 |
| ProductVersionNumber: | 8.1.4.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Malwarebytes |
| FileDescription: | Junkware Removal Tool |
| FileVersion: | 8.1.4 |
| ProductVersion: | 8.1.4 |
Total processes
173
Monitored processes
133
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | C:\Windows\system32\net1 session | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 124 | FC "C:\Users\admin\AppData\Local\Temp\jrt\TEMP\LOGON" "C:\Users\admin\AppData\Local\Temp\jrt\null" | C:\Windows\System32\fc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS 5 File Compare Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 128 | FC "C:\Users\admin\AppData\Local\Temp\jrt\TEMP\APPINIT_T" "C:\Users\admin\AppData\Local\Temp\jrt\null" | C:\Windows\System32\fc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS 5 File Compare Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 296 | FINDSTR /IG:"C:\Users\admin\AppData\Local\Temp\jrt\bl_appinit.cfg" "C:\Users\admin\AppData\Local\Temp\jrt\TEMP\APPINIT2" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 448 | FINDSTR /V "REG.EXE REG_MULTI_SZ" "C:\Users\admin\AppData\Local\Temp\jrt\TEMP\APPINIT" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 584 | "C:\Users\admin\AppData\Local\Temp\jrt\GREP.DAT" -i -v -x -f "C:\Users\admin\AppData\Local\Temp\jrt\wl_services.cfg" "C:\Users\admin\AppData\Local\Temp\jrt\TEMP\SERVICES2" | C:\Users\admin\AppData\Local\Temp\jrt\GREP.DAT | — | cmd.exe | |||||||||||
User: admin Company: GnuWin32 <http://gnuwin32.sourceforge.net> Integrity Level: HIGH Description: Grep: print lines matching a pattern Exit code: 0 Version: 2.5.4.3331 Modules
| |||||||||||||||
| 668 | FIND "x64" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 680 | TASKLIST /FO CSV /NH | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 864 | "C:\Users\admin\AppData\Local\Temp\jrt\GREP.DAT" -q "0.7A64656E67696E65.0" | C:\Users\admin\AppData\Local\Temp\jrt\GREP.DAT | cmd.exe | ||||||||||||
User: admin Company: GnuWin32 <http://gnuwin32.sourceforge.net> Integrity Level: HIGH Description: Grep: print lines matching a pattern Exit code: 1 Version: 2.5.4.3331 Modules
| |||||||||||||||
| 920 | "C:\Users\admin\AppData\Local\Temp\jrt\GREP.DAT" -i -P "^\w+_\w{2} browser plugin (?:loader|loader 64)$|^\w+ search scope monitor$|^\w+ EPM Support$|^\w+ AppIntegrator (?:32|64)-bit$|^ConduitFloatingPlugin_.*|^GoogleChromeAutoLaunch_.*|^SaferAutoLaunch_.*|^shopperz\d{5,}$|^groover\d{5,}$|^firstOffer\d{5,}$|^[a-z]{3,6}_[a-z]{2}_\d{2,9}$|^tmp[0-9A-F]{4}$|^updater\d{5}$|^[0-9a-f]{32}$|^\d{8}$|^[a-z]{1}utoauto$|^ ?maintance$|^ ?qqpctray$|^sun\d{1}$|^SimpleNoteApp\d{1,}$|^Advanced PC-?\s*(?:Fixer|Care).*" "C:\Users\admin\AppData\Local\Temp\jrt\TEMP\LOGON" | C:\Users\admin\AppData\Local\Temp\jrt\GREP.DAT | — | cmd.exe | |||||||||||
User: admin Company: GnuWin32 <http://gnuwin32.sourceforge.net> Integrity Level: HIGH Description: Grep: print lines matching a pattern Exit code: 1 Version: 2.5.4.3331 Modules
| |||||||||||||||
Total events
32 116
Read events
31 956
Write events
160
Delete events
0
Modification events
| (PID) Process: | (3772) JRT_8.1.4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3772) JRT_8.1.4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3772) JRT_8.1.4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3772) JRT_8.1.4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2896) CreateRestorePoint.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000E40981510F5EDA01500B00005C0B0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2896) CreateRestorePoint.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000E40981510F5EDA01500B00005C0B0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2896) CreateRestorePoint.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 75 | |||
| (PID) Process: | (2896) CreateRestorePoint.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000005ABA91510F5EDA01500B00005C0B0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2896) CreateRestorePoint.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000000E7F96510F5EDA01500B00003C090000E80300000100000000000000000000001798488ECC204A41BEF5BAA03C4497A80000000000000000 | |||
| (PID) Process: | (3180) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000001CA69D510F5EDA016C0C0000D8050000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
13
Suspicious files
1
Text files
57
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3772 | JRT_8.1.4.exe | C:\Users\admin\AppData\Local\Temp\jrt\clean_shortcut.vbs | text | |
MD5:FA73FE2C0D3C62E8732A71282E2E491C | SHA256:449B9F2DC6B67A6ECCF0FBE16FF91AF50EFB57E0978393A2C3F1B3FAFD1189D9 | |||
| 3772 | JRT_8.1.4.exe | C:\Users\admin\AppData\Local\Temp\jrt\jrtcurrentmd5 | text | |
MD5:36D3663C87C5B5E7A1093AFD56824A43 | SHA256:FB5A9A5C71A54D055C3A66FD0D1B404A04A6C5AD5E36CA571C7EC88C16701057 | |||
| 3772 | JRT_8.1.4.exe | C:\Users\admin\AppData\Local\Temp\jrt\nfo\NirCmd.chm | chm | |
MD5:66729EFE2819E71C060AF7FD49732C28 | SHA256:E050308C4A297F637A848109D719C65A62F6AB6ED0D854D026CC2DF257515D32 | |||
| 3772 | JRT_8.1.4.exe | C:\Users\admin\AppData\Local\Temp\jrt\get.bat | text | |
MD5:6142E0A5C78FA8B63993357AF48D7AB9 | SHA256:F793FA295E1598556A6B91EB73B68D825D5EDBCB0A764D9D58A570A6A4B5BF0F | |||
| 3772 | JRT_8.1.4.exe | C:\Users\admin\AppData\Local\Temp\jrt\bl_ffext.cfg | text | |
MD5:3E03ED48DAA500AC767092B38B8A5E28 | SHA256:47241BF6935755524E8FC3C781718630278C2AD1F1BA81790A35B5D4CBEA8DAB | |||
| 3772 | JRT_8.1.4.exe | C:\Users\admin\AppData\Local\Temp\jrt\bl_chrext.cfg | text | |
MD5:935ED2949D1ECEAC23C52564CBA49529 | SHA256:DBEDB3193DDA09AC6DF38A640A08BEE54041D020D46223AD7B3F297E4253360F | |||
| 3772 | JRT_8.1.4.exe | C:\Users\admin\AppData\Local\Temp\jrt\nfo\shortcut.txt | text | |
MD5:3A26827485C683AACD1E0194F34A0CFA | SHA256:094E2FA2C6DF5FEE039BA345067BA5B2C22E8C54CA4A8D7B35E86A91C1E8E320 | |||
| 3772 | JRT_8.1.4.exe | C:\Users\admin\AppData\Local\Temp\jrt\bl_appinit.cfg | text | |
MD5:CC6A968CCDA289BE7B69E039646D0BC9 | SHA256:95691814D105108152B96E41D0F0FF30462D0A060AF32431089C312604C235B6 | |||
| 3772 | JRT_8.1.4.exe | C:\Users\admin\AppData\Local\Temp\jrt\bl_chrstrg.cfg | text | |
MD5:EBDFDE9F11720DFC627933F37E8AE319 | SHA256:613DEC5AE47C9FCC4EFF4E50FE811FD41A9442796A57DBB0E63FBE36178C0663 | |||
| 3772 | JRT_8.1.4.exe | C:\Users\admin\AppData\Local\Temp\jrt\nfo\wget.txt | text | |
MD5:A541C96318F0FE10D90415E7B6A57080 | SHA256:1ACBF2A4A53DB8597CC3774B6D312F207AC2011FD4CEEECA9523452D016A9315 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2856 | WGET.DAT | GET | 301 | 65.9.66.107:80 | http://data-cdn.mbamupdates.com/v1/tools/jrt/jrtnewmd5 | unknown | html | 167 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2856 | WGET.DAT | 65.9.66.107:80 | data-cdn.mbamupdates.com | AMAZON-02 | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2856 | WGET.DAT | 65.9.66.107:443 | data-cdn.mbamupdates.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| whitelisted |
data-cdn.mbamupdates.com |
| whitelisted |
Threats
Process | Message |
|---|---|
GREP.DAT | Invalid parameter passed to C runtime function.
|
GREP.DAT | Invalid parameter passed to C runtime function.
|
GREP.DAT | Invalid parameter passed to C runtime function.
|
GREP.DAT | Invalid parameter passed to C runtime function.
|
GREP.DAT | Invalid parameter passed to C runtime function.
|
GREP.DAT | Invalid parameter passed to C runtime function.
|
GREP.DAT | Invalid parameter passed to C runtime function.
|
GREP.DAT | Invalid parameter passed to C runtime function.
|
GREP.DAT | Invalid parameter passed to C runtime function.
|
GREP.DAT | Invalid parameter passed to C runtime function.
|