| File name: | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178 |
| Full analysis: | https://app.any.run/tasks/3aefc539-71b9-4baa-82cc-702c18794833 |
| Verdict: | Malicious activity |
| Analysis date: | July 31, 2024, 09:37:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C88056E5927B88CC685080634523FF54 |
| SHA1: | C0AC73B1EA92A2634F618720507A721DA326AD21 |
| SHA256: | 1FED7562FA2BE11233FCA458C3FD90012803F9016C947E2F7152EB75175CEF2C |
| SSDEEP: | 393216:IevIqJB2E1egqqJckiCSB3BTHmeHqASHgnLIyi7:ZyENiCSf1iKq |
MALICIOUS
Drops the executable file immediately after the start
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.exe (PID: 7020)
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.exe (PID: 6168)
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 3812)
- ps2pdf995.exe (PID: 6780)
- PS2Pdf995setup.exe (PID: 6832)
- pdf995s.exe (PID: 360)
- thinsetup.exe (PID: 3144)
- copy64.exe (PID: 3992)
- copy64.exe (PID: 2384)
- setup.exe (PID: 2456)
- copy64.exe (PID: 6500)
Registers / Runs the DLL via REGSVR32.EXE
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 3812)
Scans artifacts that could help determine the target
- Rpv.exe (PID: 5984)
- glver.exe (PID: 1964)
SUSPICIOUS
Reads security settings of Internet Explorer
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 7040)
- setup.exe (PID: 2456)
- Rpv.exe (PID: 5984)
- glver.exe (PID: 1964)
- e-mailer.exe (PID: 3188)
Executable content was dropped or overwritten
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.exe (PID: 7020)
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.exe (PID: 6168)
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 3812)
- ps2pdf995.exe (PID: 6780)
- PS2Pdf995setup.exe (PID: 6832)
- thinsetup.exe (PID: 3144)
- setup.exe (PID: 2456)
- pdf995s.exe (PID: 360)
- copy64.exe (PID: 3992)
- copy64.exe (PID: 2384)
- copy64.exe (PID: 6500)
Reads the date of Windows installation
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 7040)
Reads the Windows owner or organization settings
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 3812)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 6908)
- regsvr32.exe (PID: 6932)
- regsvr32.exe (PID: 6876)
- regsvr32.exe (PID: 6704)
- regsvr32.exe (PID: 6712)
- regsvr32.exe (PID: 1164)
- regsvr32.exe (PID: 7012)
- regsvr32.exe (PID: 5924)
- regsvr32.exe (PID: 2728)
- regsvr32.exe (PID: 4236)
- regsvr32.exe (PID: 5180)
- regsvr32.exe (PID: 1076)
- regsvr32.exe (PID: 6564)
- regsvr32.exe (PID: 6572)
- regsvr32.exe (PID: 6912)
- regsvr32.exe (PID: 6536)
- regsvr32.exe (PID: 4924)
- regsvr32.exe (PID: 1964)
- regsvr32.exe (PID: 3116)
- regsvr32.exe (PID: 3136)
- regsvr32.exe (PID: 236)
- regsvr32.exe (PID: 6504)
- regsvr32.exe (PID: 6764)
- regsvr32.exe (PID: 6616)
- regsvr32.exe (PID: 6304)
Process drops legitimate windows executable
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 3812)
- pdf995s.exe (PID: 360)
- thinsetup.exe (PID: 3144)
- setup.exe (PID: 2456)
Starts CMD.EXE for commands execution
- instpdf.exe (PID: 5044)
Executing commands from a ".bat" file
- instpdf.exe (PID: 5044)
Creates a software uninstall entry
- PS2Pdf995setup.exe (PID: 6832)
- setup.exe (PID: 2456)
Creates file in the systems drive root
- thinsetup.exe (PID: 3144)
Reads Microsoft Outlook installation path
- Rpv.exe (PID: 5984)
- glver.exe (PID: 1964)
- e-mailer.exe (PID: 3188)
Checks Windows Trust Settings
- Rpv.exe (PID: 5984)
- glver.exe (PID: 1964)
Reads Internet Explorer settings
- Rpv.exe (PID: 5984)
- glver.exe (PID: 1964)
- e-mailer.exe (PID: 3188)
There is functionality for sendig ICMP (YARA)
- e-mailer.exe (PID: 3188)
There is functionality for communication over UDP network (YARA)
- e-mailer.exe (PID: 3188)
Process requests binary or script from the Internet
- glver.exe (PID: 1964)
INFO
Checks supported languages
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 7040)
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.exe (PID: 7020)
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.exe (PID: 6168)
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 3812)
- instpdf.exe (PID: 5044)
- autosetup.exe (PID: 6884)
- PS2Pdf995setup.exe (PID: 6832)
- ps2pdf995.exe (PID: 6780)
- splash.exe (PID: 1344)
- thinsetup.exe (PID: 3144)
- setup.exe (PID: 2456)
- pdf995s.exe (PID: 360)
- copy64.exe (PID: 2384)
- copy64.exe (PID: 3992)
- copy64.exe (PID: 6500)
- xprights.exe (PID: 6892)
- Rpv.exe (PID: 5984)
- glver.exe (PID: 1964)
- e-mailer.exe (PID: 3188)
Create files in a temporary directory
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.exe (PID: 7020)
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.exe (PID: 6168)
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 3812)
- instpdf.exe (PID: 5044)
- ps2pdf995.exe (PID: 6780)
- pdf995s.exe (PID: 360)
- Rpv.exe (PID: 5984)
- glver.exe (PID: 1964)
- e-mailer.exe (PID: 3188)
Process checks computer location settings
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 7040)
Reads the computer name
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 7040)
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 3812)
- instpdf.exe (PID: 5044)
- ps2pdf995.exe (PID: 6780)
- splash.exe (PID: 1344)
- setup.exe (PID: 2456)
- pdf995s.exe (PID: 360)
- xprights.exe (PID: 6892)
- Rpv.exe (PID: 5984)
- glver.exe (PID: 1964)
- e-mailer.exe (PID: 3188)
Creates files in the program directory
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 3812)
- autosetup.exe (PID: 6884)
- PS2Pdf995setup.exe (PID: 6832)
- thinsetup.exe (PID: 3144)
- setup.exe (PID: 2456)
- xprights.exe (PID: 6892)
- instpdf.exe (PID: 5044)
Creates a software uninstall entry
- SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp (PID: 3812)
Reads mouse settings
- regsvr32.exe (PID: 1964)
- regsvr32.exe (PID: 1076)
- Rpv.exe (PID: 5984)
- e-mailer.exe (PID: 3188)
Creates files or folders in the user directory
- xcopy.exe (PID: 2340)
- xcopy.exe (PID: 2456)
- xcopy.exe (PID: 5084)
- xcopy.exe (PID: 6888)
- xcopy.exe (PID: 7032)
- xcopy.exe (PID: 3476)
- instpdf.exe (PID: 5044)
- xcopy.exe (PID: 6288)
- Rpv.exe (PID: 5984)
- glver.exe (PID: 1964)
- e-mailer.exe (PID: 3188)
Reads Microsoft Office registry keys
- setup.exe (PID: 2456)
Checks proxy server information
- Rpv.exe (PID: 5984)
- glver.exe (PID: 1964)
- e-mailer.exe (PID: 3188)
Process checks Internet Explorer phishing filters
- Rpv.exe (PID: 5984)
- e-mailer.exe (PID: 3188)
- glver.exe (PID: 1964)
Reads the software policy settings
- glver.exe (PID: 1964)
- Rpv.exe (PID: 5984)
Reads the machine GUID from the registry
- glver.exe (PID: 1964)
- Rpv.exe (PID: 5984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 41984 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaad0 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
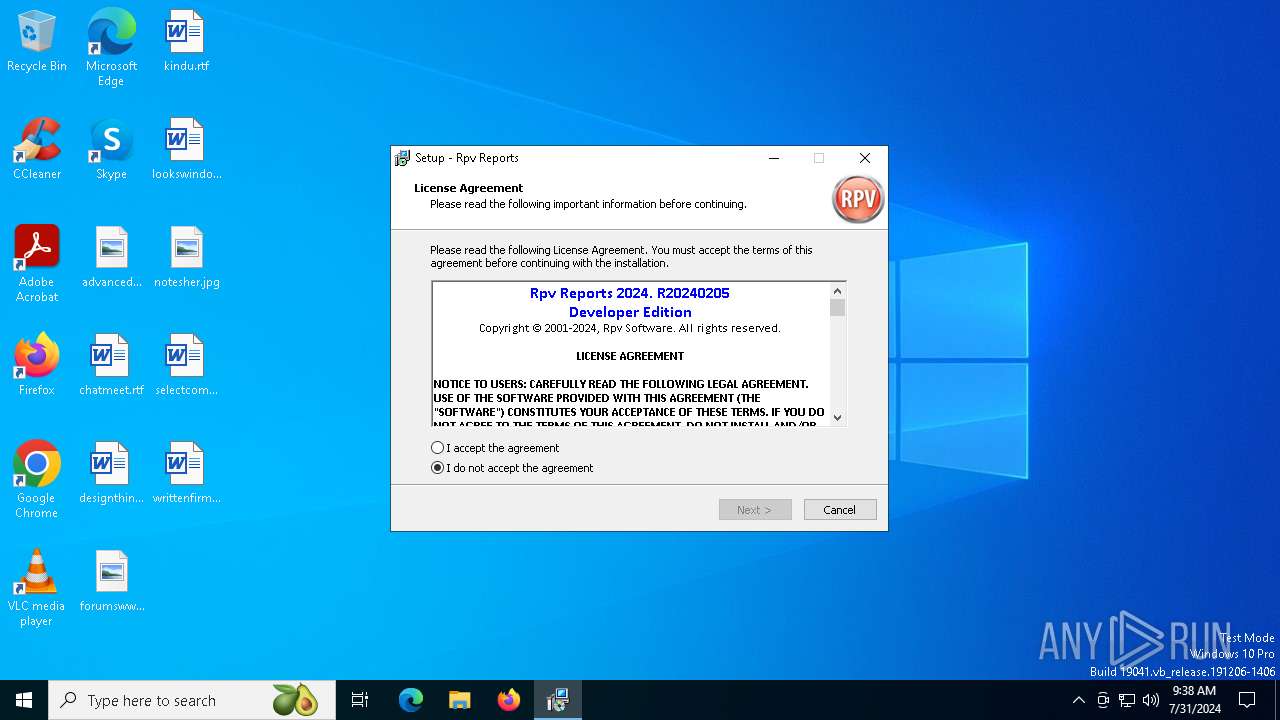
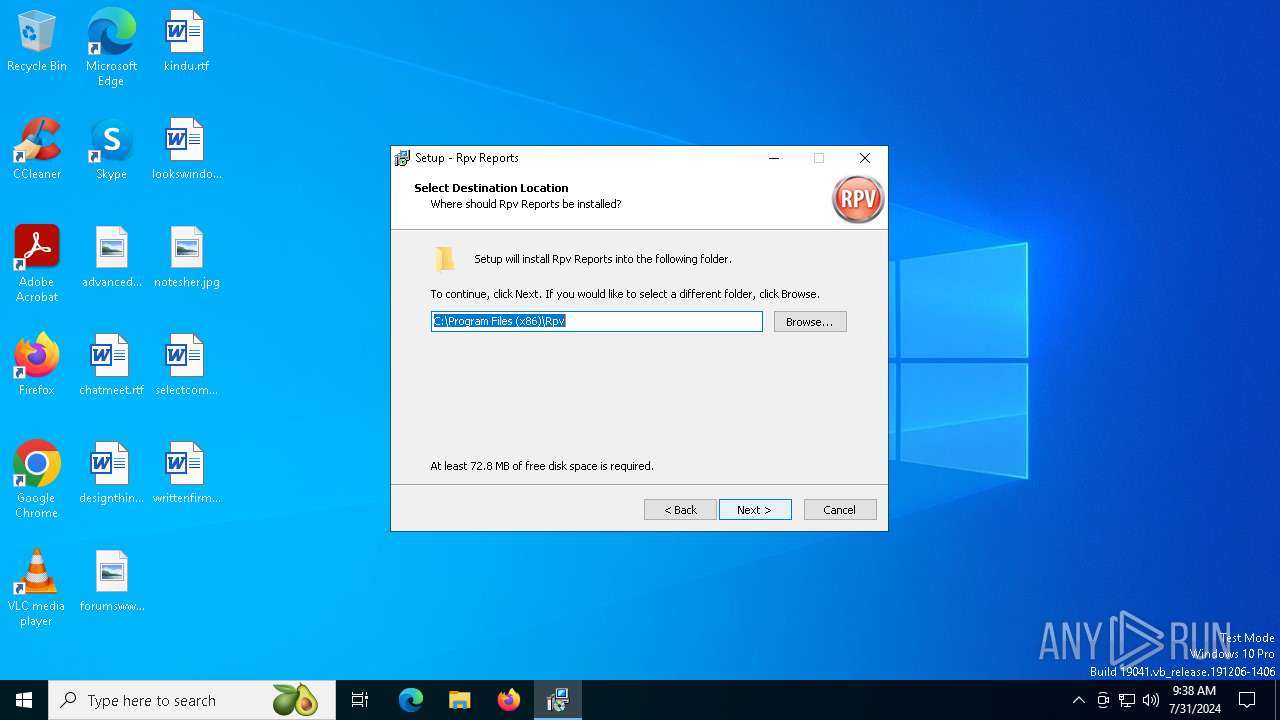
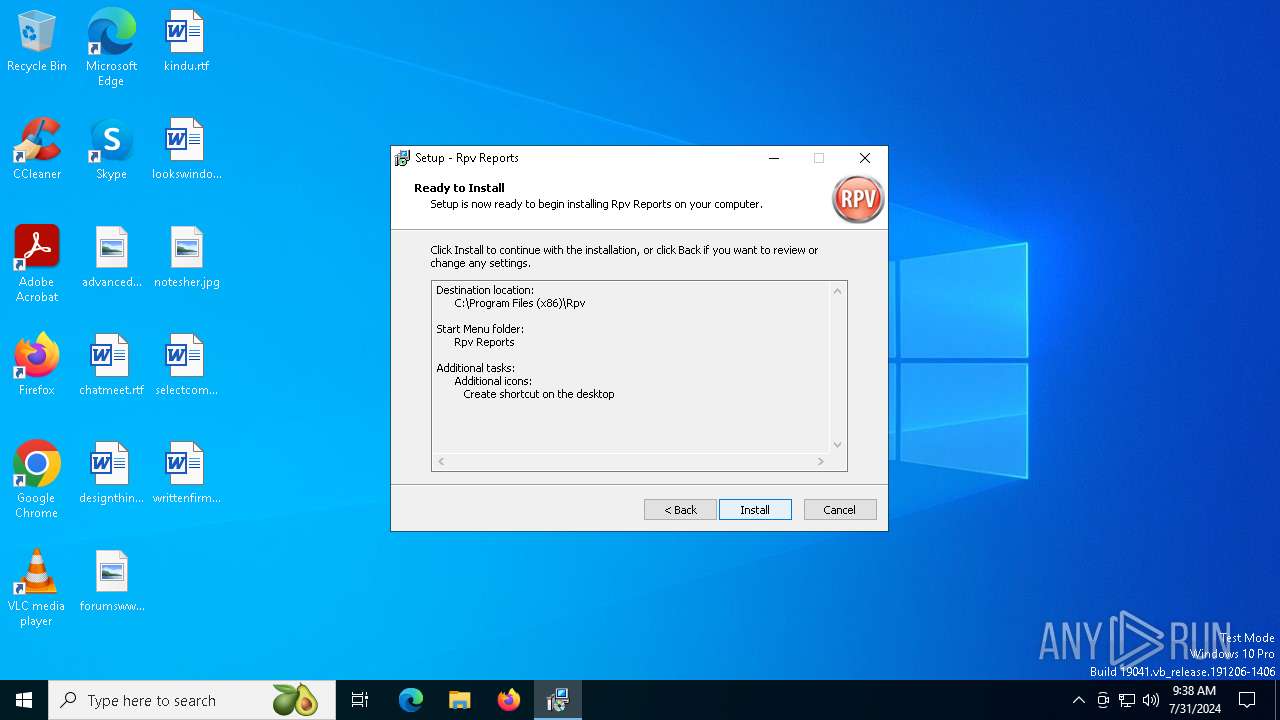
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Rpv Software |
| FileDescription: | Rpv Reports Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | Rpv Reports |
| ProductVersion: |
Total processes
185
Monitored processes
56
Malicious processes
19
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | C:\WINDOWS\system32\cmd.exe /c ""C:\Program Files (x86)\Rpv\appd.bat"" | C:\Windows\SysWOW64\cmd.exe | — | instpdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\WINDOWS\system32\mswinsck.OCX" | C:\Windows\SysWOW64\regsvr32.exe | — | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 360 | pdf995s.exe | C:\Program Files (x86)\Rpv\Pdf995\pdf995s.exe | autosetup.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1076 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\WINDOWS\system32\mscomctl.OCX" | C:\Windows\SysWOW64\regsvr32.exe | — | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files (x86)\Rpv\button10.ocx" | C:\Windows\SysWOW64\regsvr32.exe | — | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1344 | xcopy "pbms2021\*.*" "C:\Users\admin\AppData\Roaming\Rpv\Pbms\Pbms\*.*" /d /e /y | C:\Windows\SysWOW64\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1344 | .\pdf995\splash.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\pdf995\splash.exe | — | pdf995s.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1964 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\WINDOWS\system32\MSCOMCT2.OCX" | C:\Windows\SysWOW64\regsvr32.exe | — | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1964 | "C:\Program Files (x86)\Rpv\glver.exe" exe=rpv.exe&svk=X&serial=999999999999&roo=417665946&cma=demo&ver=R2024020&dte=20240731 | C:\Program Files (x86)\Rpv\glver.exe | Rpv.exe | ||||||||||||
User: admin Company: Rpv Software Integrity Level: MEDIUM Description: Rpv GLver Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2340 | xcopy "pbms2024\*.*" "C:\Users\admin\AppData\Roaming\Rpv\Pbms\Pbms2024\*.*" /d /e /y | C:\Windows\SysWOW64\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 922
Read events
15 059
Write events
605
Delete events
258
Modification events
| (PID) Process: | (3812) SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: E40E000014BB305F2DE3DA01 | |||
| (PID) Process: | (3812) SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: DC4E54CF52492D996C8E26CF21B7BA34BD542EE78FE74F60B8C95E2E5E963C92 | |||
| (PID) Process: | (3812) SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3812) SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files (x86)\Rpv\rpv.chm | |||
| (PID) Process: | (3812) SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 979387A8F46015104C77743CE5B75AE48FEB0738F3EA9B6A08E45B301A238608 | |||
| (PID) Process: | (3812) SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Roboto Black (TrueType) |
Value: Roboto-Black.ttf | |||
| (PID) Process: | (3812) SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Roboto Black Italic (TrueType) |
Value: Roboto-BlackItalic.ttf | |||
| (PID) Process: | (3812) SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Roboto Bold (TrueType) |
Value: Roboto-Bold.ttf | |||
| (PID) Process: | (3812) SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Roboto Bold Italic (TrueType) |
Value: Roboto-BoldItalic.ttf | |||
| (PID) Process: | (3812) SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Roboto Italic (TrueType) |
Value: Roboto-Italic.ttf | |||
Executable files
190
Suspicious files
101
Text files
1 095
Unknown types
81
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3812 | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | C:\Users\admin\AppData\Local\Temp\is-TPIE7.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 7020 | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.exe | C:\Users\admin\AppData\Local\Temp\is-776O6.tmp\SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | executable | |
MD5:1AFBD25DB5C9A90FE05309F7C4FBCF09 | SHA256:3BB0EE5569FE5453C6B3FA25AA517B925D4F8D1F7BA3475E58FA09C46290658C | |||
| 3812 | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | C:\Program Files (x86)\Rpv\rpv.chm | binary | |
MD5:8F208E2F568522965959C3DEC31DD68D | SHA256:5F279FCA25DFDC75DE88EC53E548F42292E0016C2DCF3F81EB18572068734129 | |||
| 3812 | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | C:\Program Files (x86)\Rpv\is-6UF31.tmp | binary | |
MD5:8F208E2F568522965959C3DEC31DD68D | SHA256:5F279FCA25DFDC75DE88EC53E548F42292E0016C2DCF3F81EB18572068734129 | |||
| 3812 | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | C:\Program Files (x86)\Rpv\is-9CIFV.tmp | text | |
MD5:01FBAAF40C58E26407743BCFAA5F9BE3 | SHA256:B58772FF7BFEA9572598F8DA28320FFA6B5AEE152755ED22F191BDEB91E32C8D | |||
| 3812 | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | C:\Program Files (x86)\Rpv\is-QKANF.tmp | executable | |
MD5:DB6F97815D221843048EFB36AD737CBC | SHA256:E93AB9B690396B18B3485FC674CC802D530145E472F2F6A88EF988F7CC0846C6 | |||
| 3812 | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | C:\Program Files (x86)\Rpv\is-8K8TP.tmp | text | |
MD5:98D62AE1DAE1C941E345D81F66742AA4 | SHA256:513C63B1C83A499F35635E14046B0707A156A27035D1F1CBBAE31C4C66D687AF | |||
| 3812 | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | C:\Program Files (x86)\Rpv\Internal tools\is-I3QHP.tmp | executable | |
MD5:F573585234DB54FAD0DF81976FEAA8DB | SHA256:5C5638890325D99075BF635EF64A84F0238AA200501C650B1864B610493E9460 | |||
| 3812 | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | C:\Program Files (x86)\Rpv\Svk | text | |
MD5:9A620BD52E66406EC798B6E1B038D86A | SHA256:EA530C2711E2680A718B5FA695AE3D97A8109B7A29FE50897A74E2A9F1BE8694 | |||
| 3812 | SecuriteInfo.com.Trojan.Win32.Agent.xbltbw.25187.23178.tmp | C:\Program Files (x86)\Rpv\unins000.exe | executable | |
MD5:DB6F97815D221843048EFB36AD737CBC | SHA256:E93AB9B690396B18B3485FC674CC802D530145E472F2F6A88EF988F7CC0846C6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
59
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6208 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5140 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5140 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6276 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5984 | Rpv.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
5984 | Rpv.exe | GET | 301 | 143.95.110.251:80 | http://www.rpvsoftware.com/add_reg7.php?serial=999999999999&email=nomail@nomail.com&name=noname&company=nocompany&svk=P&lic_name=noname&lic_company=nocompany&roo=417665946&st=1&date=20240731&ver=2024 | unknown | — | — | unknown |
5984 | Rpv.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
5984 | Rpv.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQDf7Nlo3DJkFjLrYhfHmCKC | unknown | — | — | whitelisted |
1964 | glver.exe | GET | 301 | 143.95.110.251:80 | http://rpvsoftware.com/latest_new.php?exe=rpv.exe&svk=X&serial=999999999999&roo=417665946&cma=demo&ver=R2024020&dte=20240731 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 184.86.251.16:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6208 | backgroundTaskHost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |