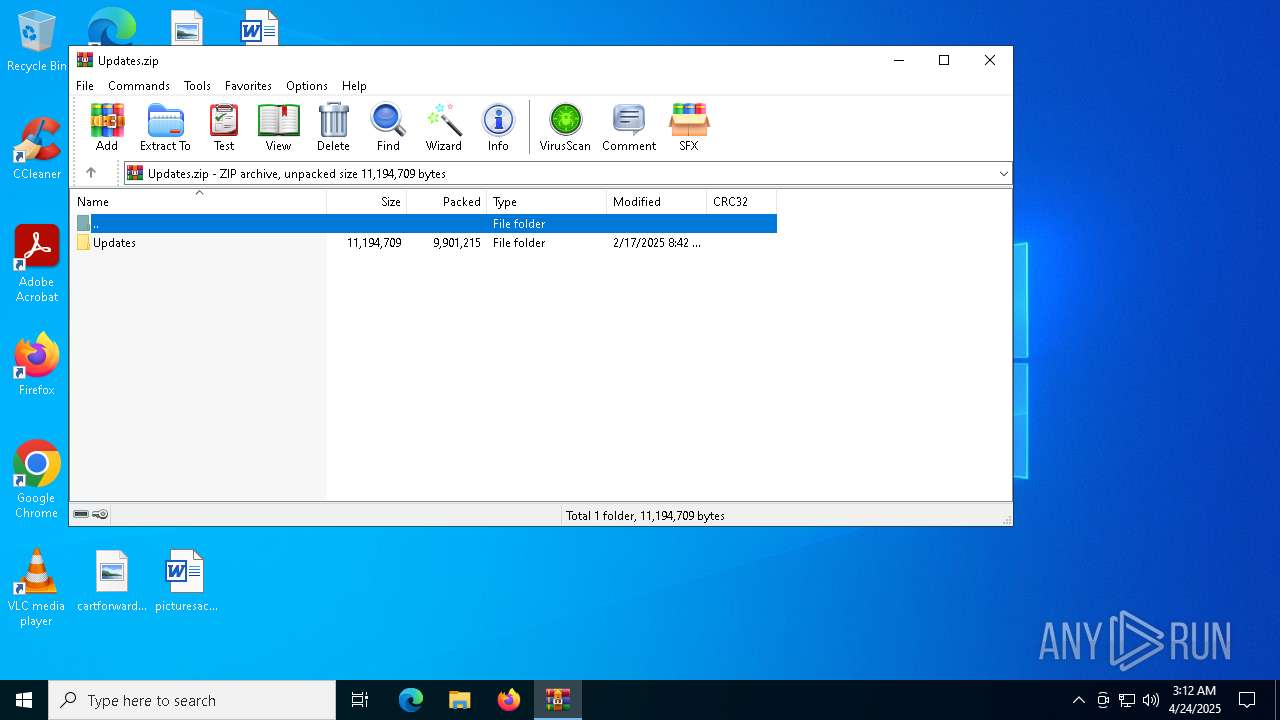
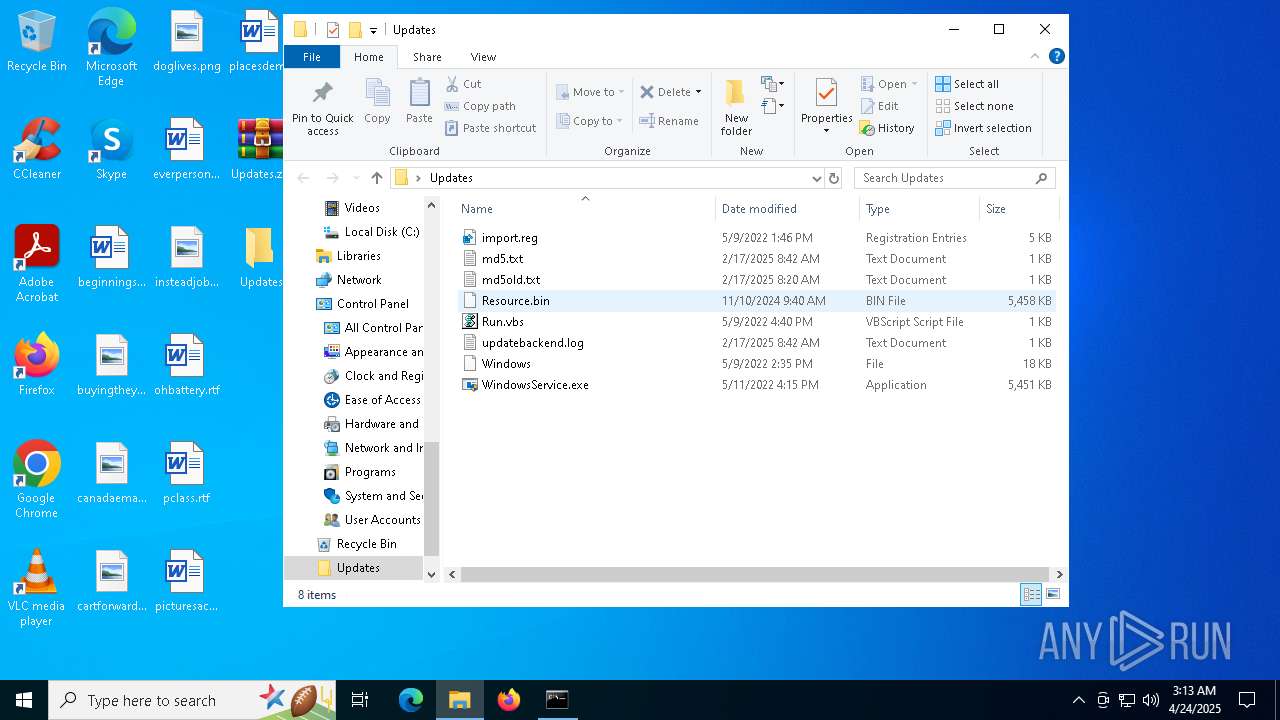
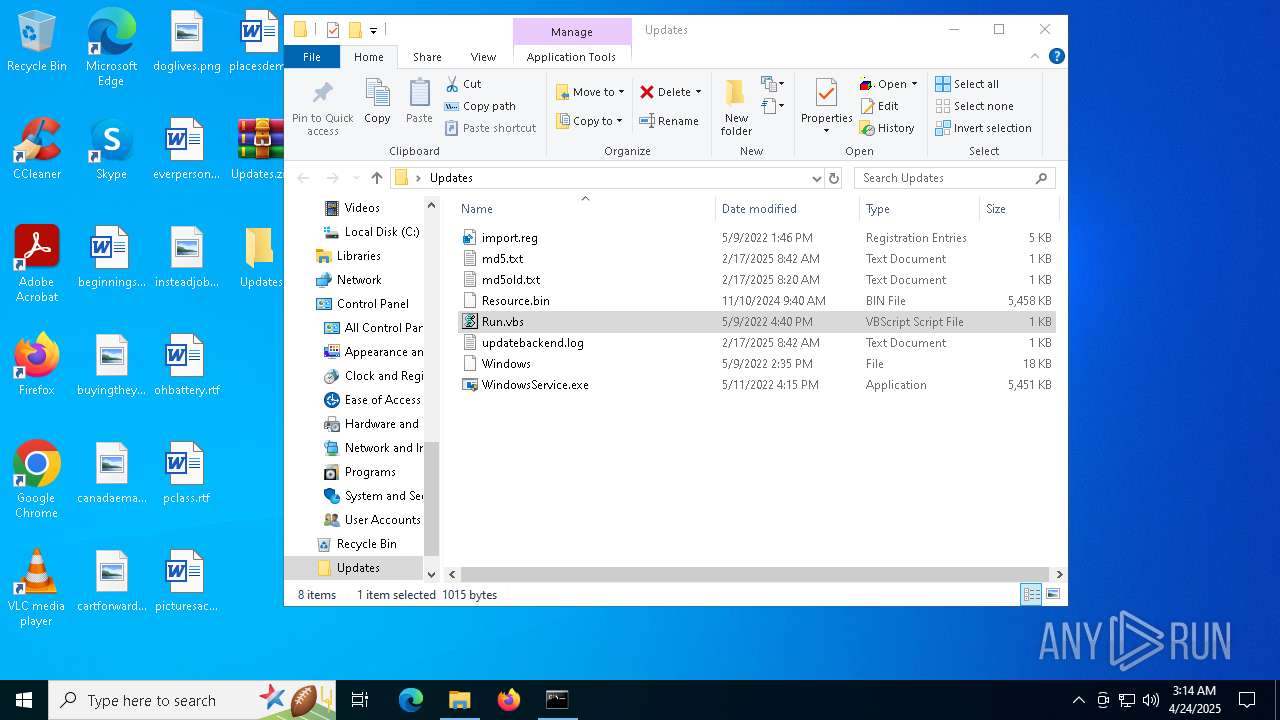
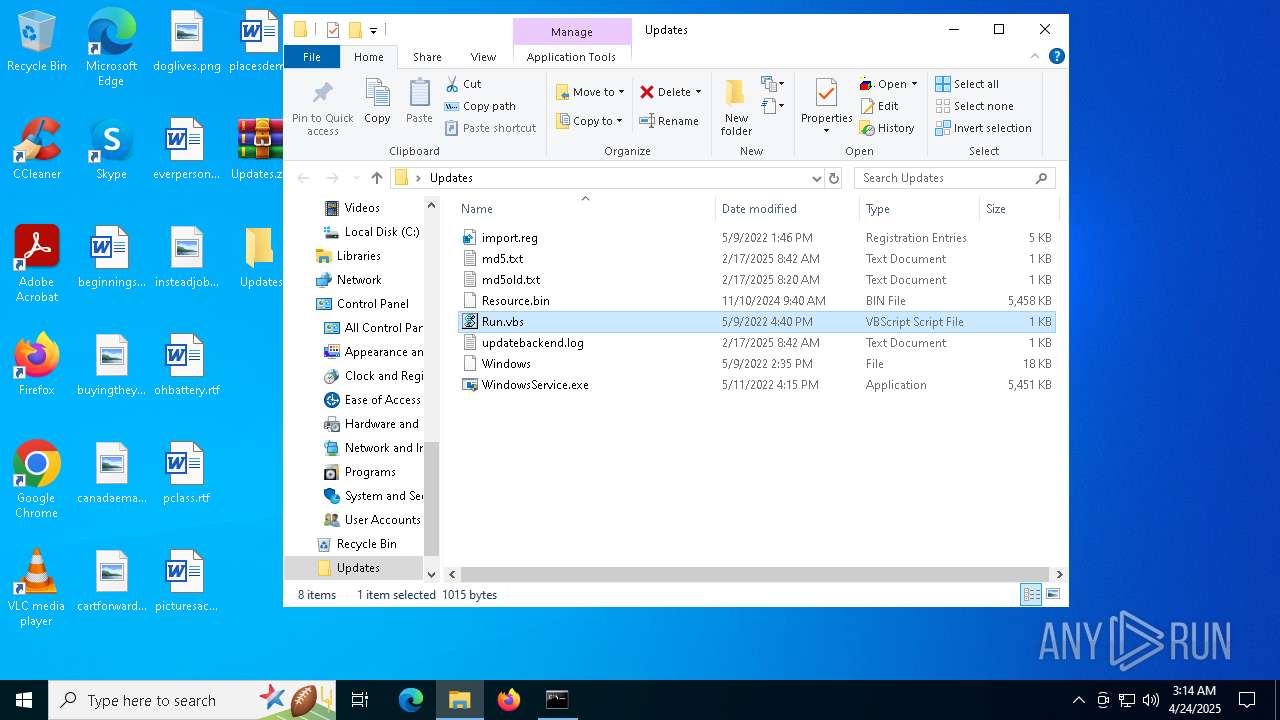
| File name: | Updates.zip |
| Full analysis: | https://app.any.run/tasks/a1e4cee5-4dec-4f26-a1d1-70e41c1c10a1 |
| Verdict: | Malicious activity |
| Analysis date: | April 24, 2025, 03:12:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 78777F171C8F705727B9C932D7A9C4AC |
| SHA1: | 949B0D8FC9B4AC710EA3527E595E71A0EC0D397E |
| SHA256: | 1FEB28CD830BA76B6272DB25A6ADC146DDD1E53C16C18A4A4998DC7F963E0B81 |
| SSDEEP: | 98304:w1dgaAc4YGG8tQQMidrVdXG4LwAJDFGD2Fj6Ar6p3xL1Qah7z91amW6hnfMsNGCT:kX1a9JQqTh9q6Ir0hNG |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7620)
Vulnerable driver has been detected
- WindowsService.exe (PID: 6620)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WindowsService.exe (PID: 6620)
Executable content was dropped or overwritten
- WindowsService.exe (PID: 6620)
Reads security settings of Internet Explorer
- WindowsService.exe (PID: 6620)
Connects to unusual port
- WindowsService.exe (PID: 6620)
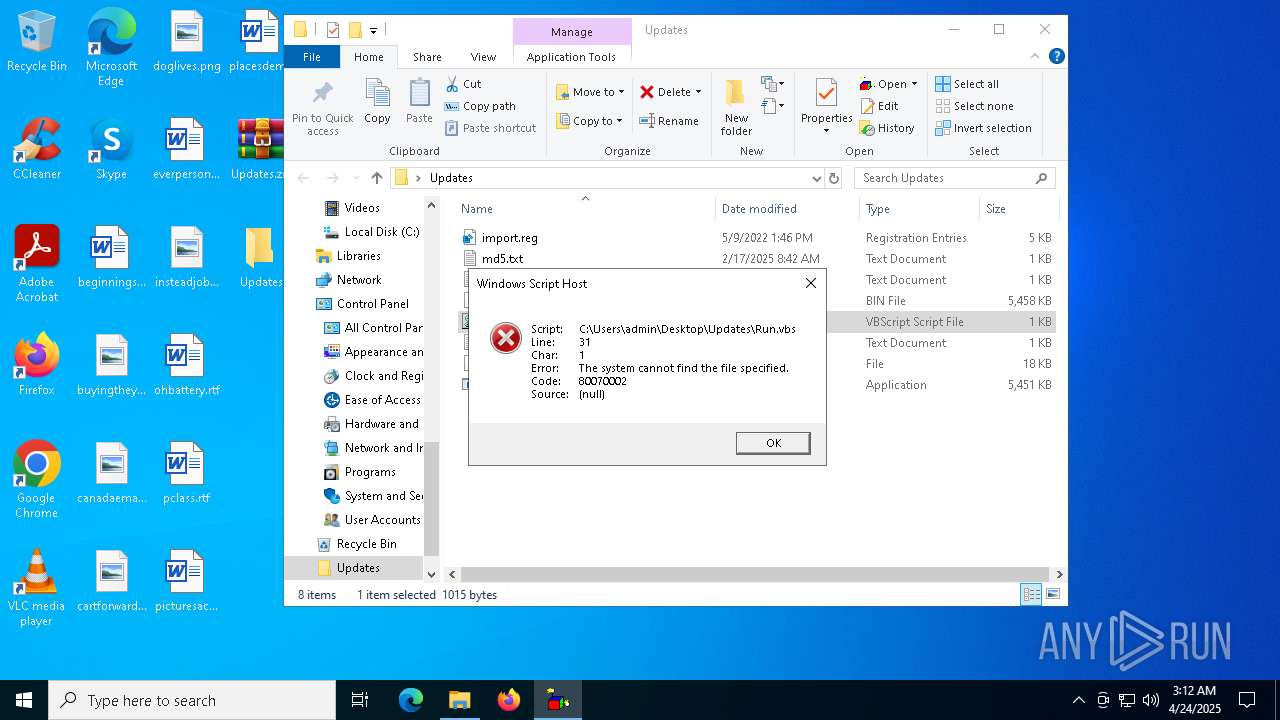
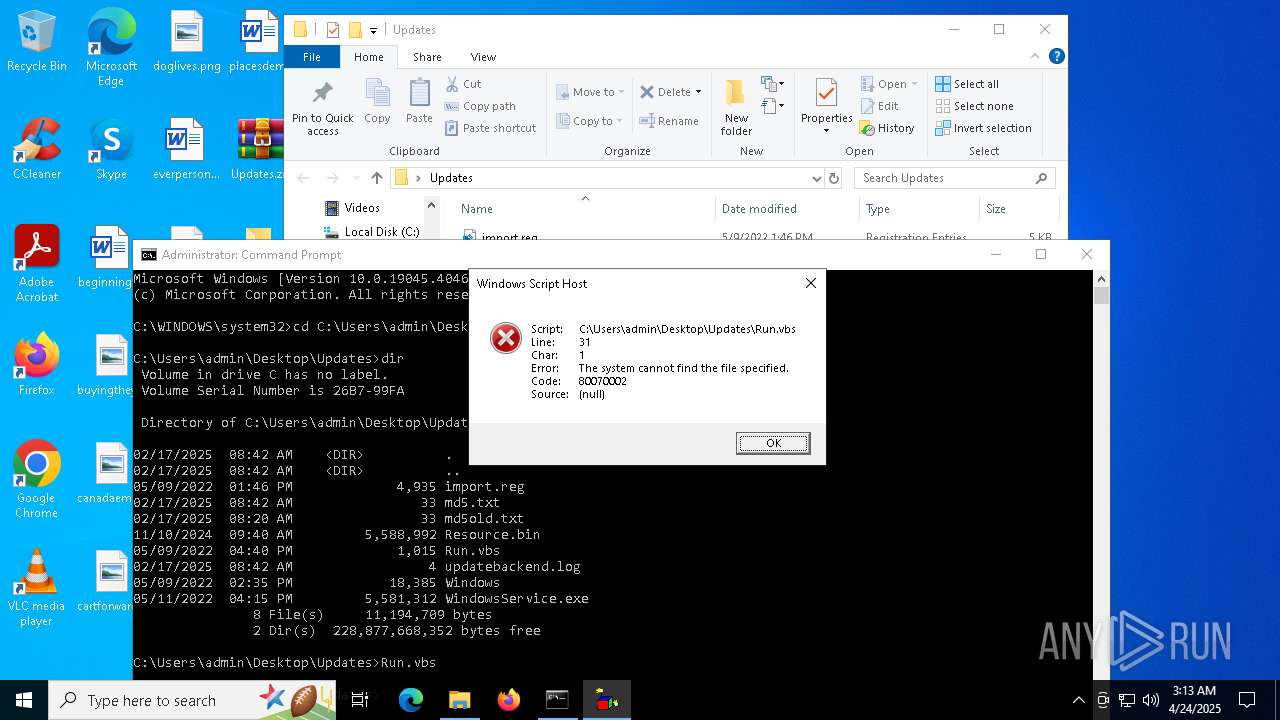
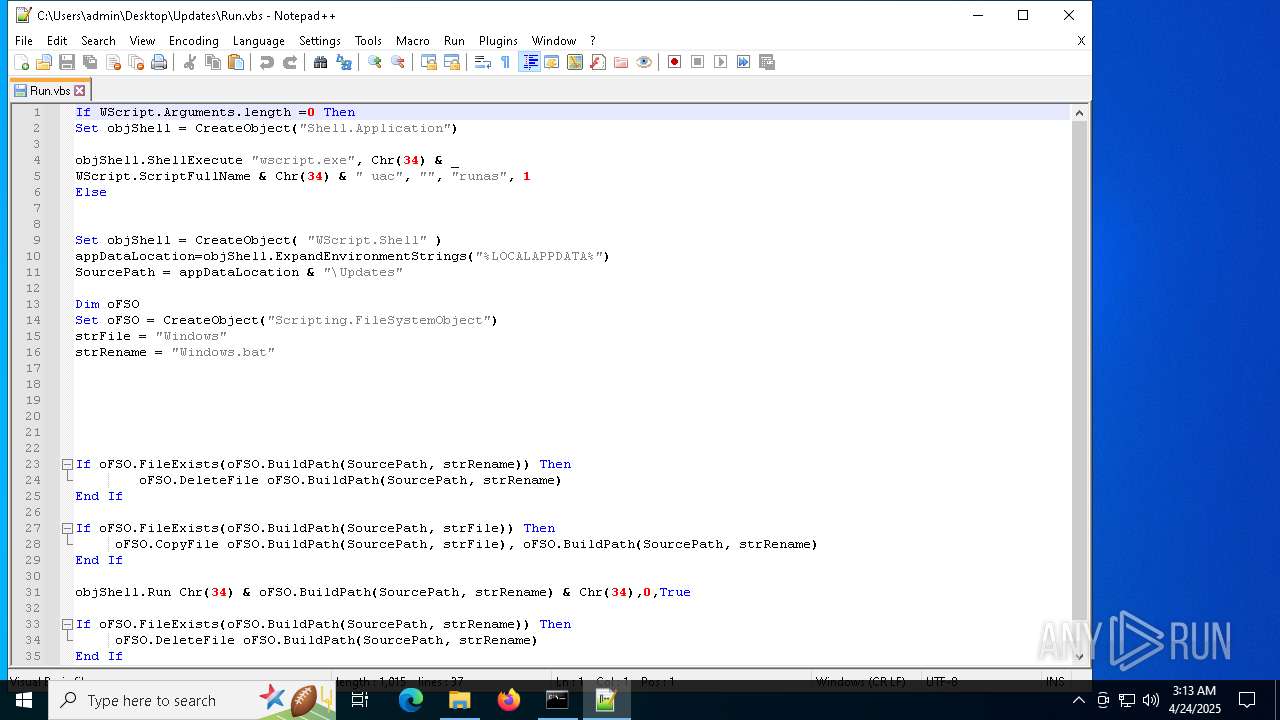
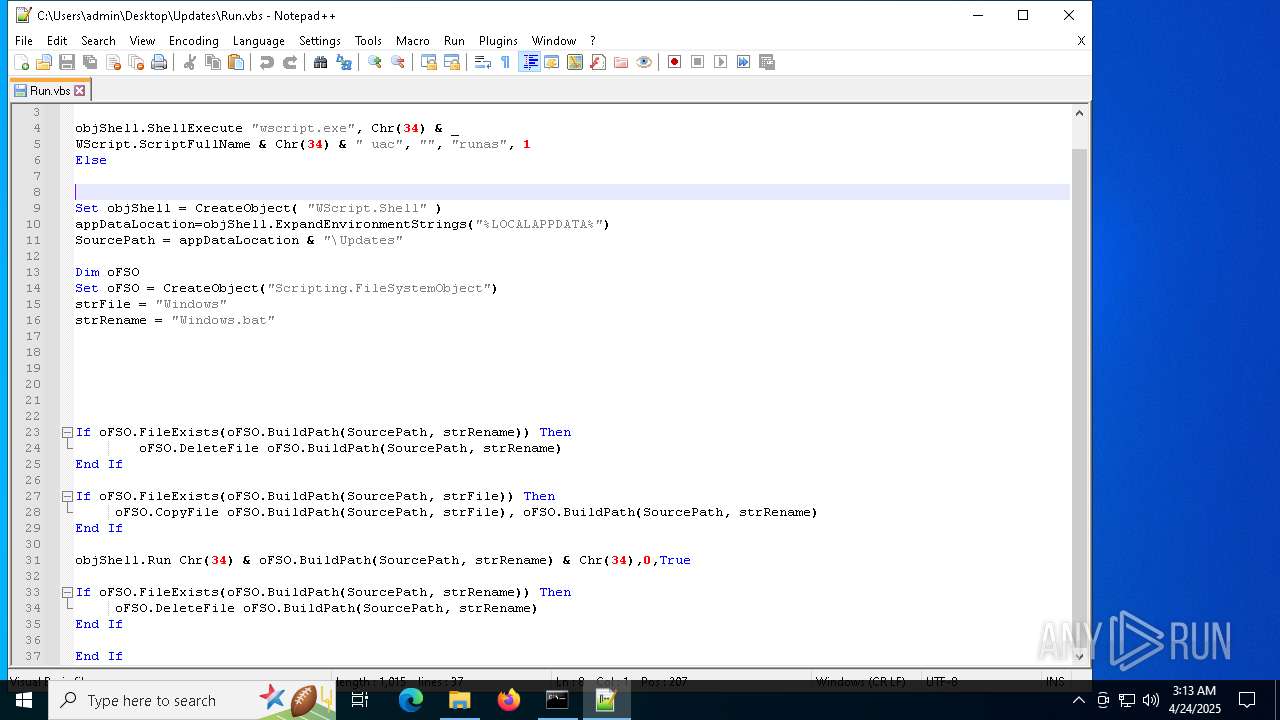
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 5680)
- wscript.exe (PID: 2240)
Application launched itself
- wscript.exe (PID: 5680)
- wscript.exe (PID: 2240)
The process executes VB scripts
- wscript.exe (PID: 5680)
- cmd.exe (PID: 7792)
- wscript.exe (PID: 2240)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5680)
- wscript.exe (PID: 4008)
- wscript.exe (PID: 2240)
- wscript.exe (PID: 5436)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 5436)
- wscript.exe (PID: 4008)
INFO
Reads the computer name
- WindowsService.exe (PID: 6620)
The sample compiled with japanese language support
- WindowsService.exe (PID: 6620)
Manual execution by a user
- WindowsService.exe (PID: 8156)
- WindowsService.exe (PID: 6620)
- wscript.exe (PID: 5680)
- cmd.exe (PID: 7792)
- notepad++.exe (PID: 7724)
- notepad.exe (PID: 2092)
- notepad.exe (PID: 5428)
Checks supported languages
- WindowsService.exe (PID: 6620)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7620)
Checks proxy server information
- WindowsService.exe (PID: 6620)
- slui.exe (PID: 7996)
VMProtect protector has been detected
- WindowsService.exe (PID: 6620)
Reads the software policy settings
- slui.exe (PID: 7848)
- slui.exe (PID: 7996)
Reads security settings of Internet Explorer
- notepad.exe (PID: 2092)
- notepad.exe (PID: 5428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:02:17 12:42:42 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Updates/ |
Total processes
153
Monitored processes
18
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2092 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Updates\md5.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\Updates\Run.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2384 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WindowsService.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4008 | "C:\Windows\System32\wscript.exe" "C:\Users\admin\Desktop\Updates\Run.vbs" uac | C:\Windows\System32\wscript.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5428 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Updates\md5old.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5436 | "C:\Windows\System32\wscript.exe" "C:\Users\admin\Desktop\Updates\Run.vbs" uac | C:\Windows\System32\wscript.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5680 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\Updates\Run.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6620 | "C:\Users\admin\Desktop\Updates\WindowsService.exe" | C:\Users\admin\Desktop\Updates\WindowsService.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 7620 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Updates.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
5 914
Read events
5 876
Write events
25
Delete events
13
Modification events
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Updates.zip | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
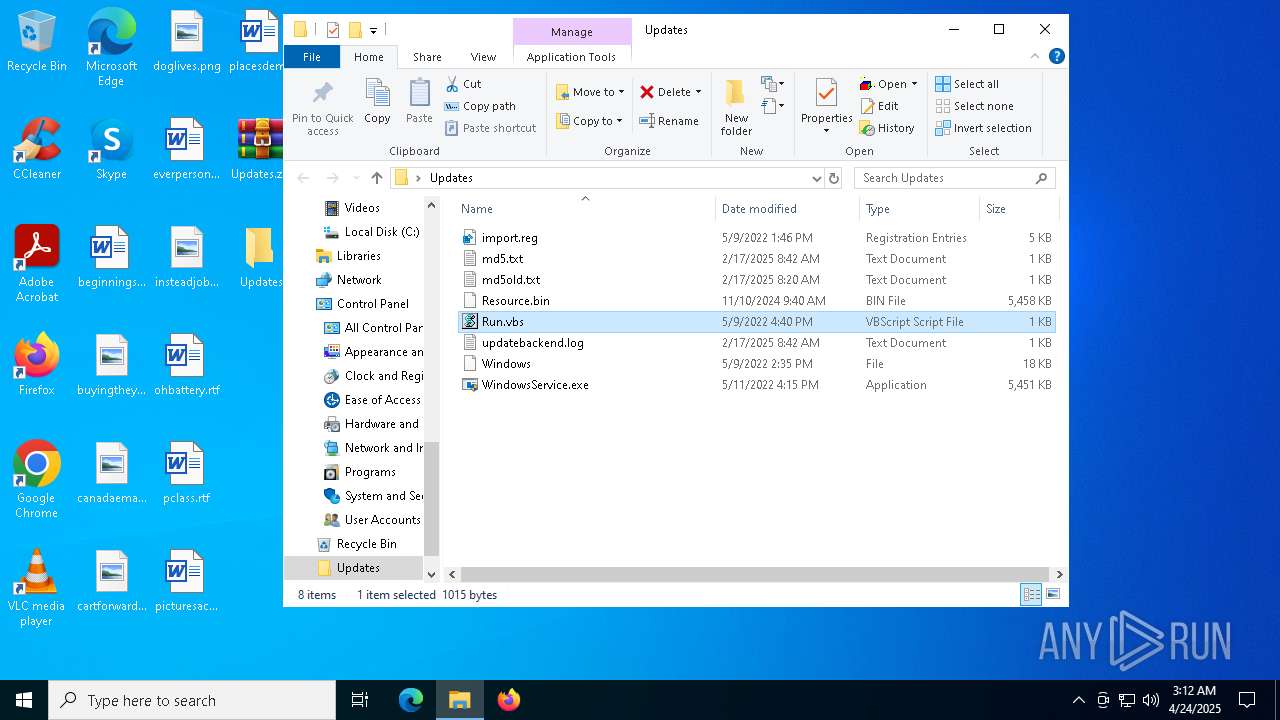
Executable files
2
Suspicious files
0
Text files
12
Unknown types
0
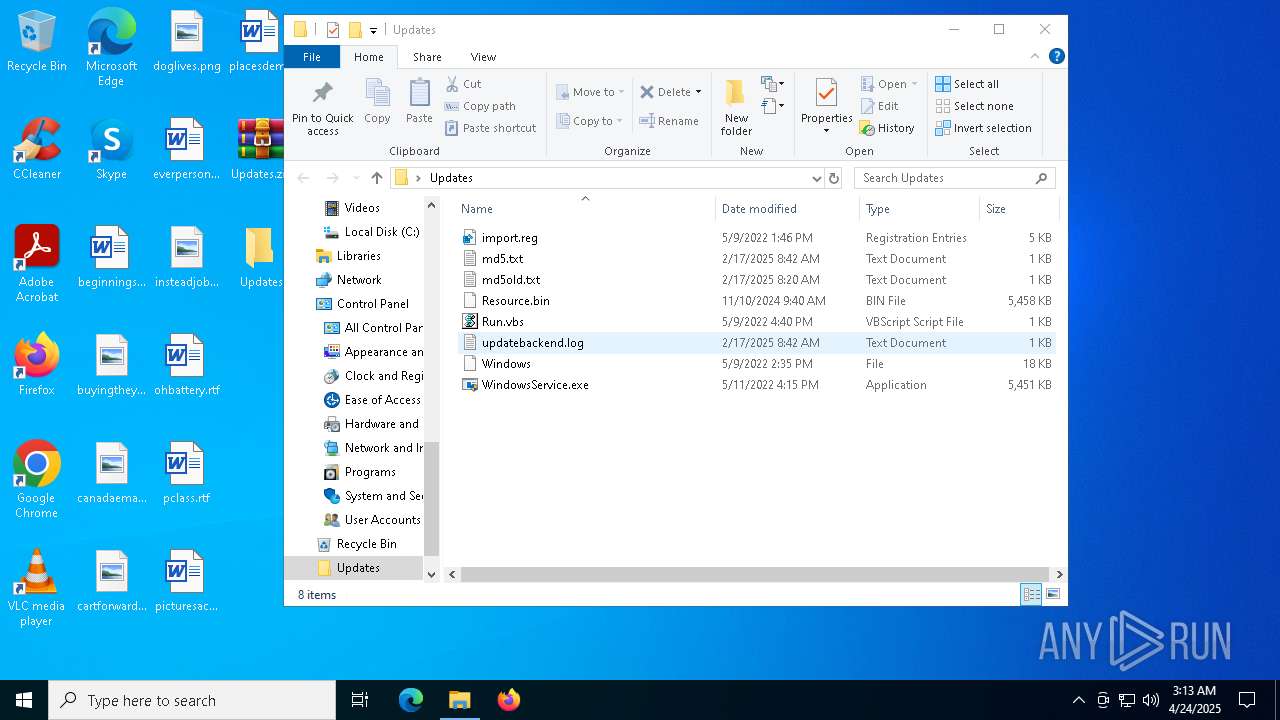
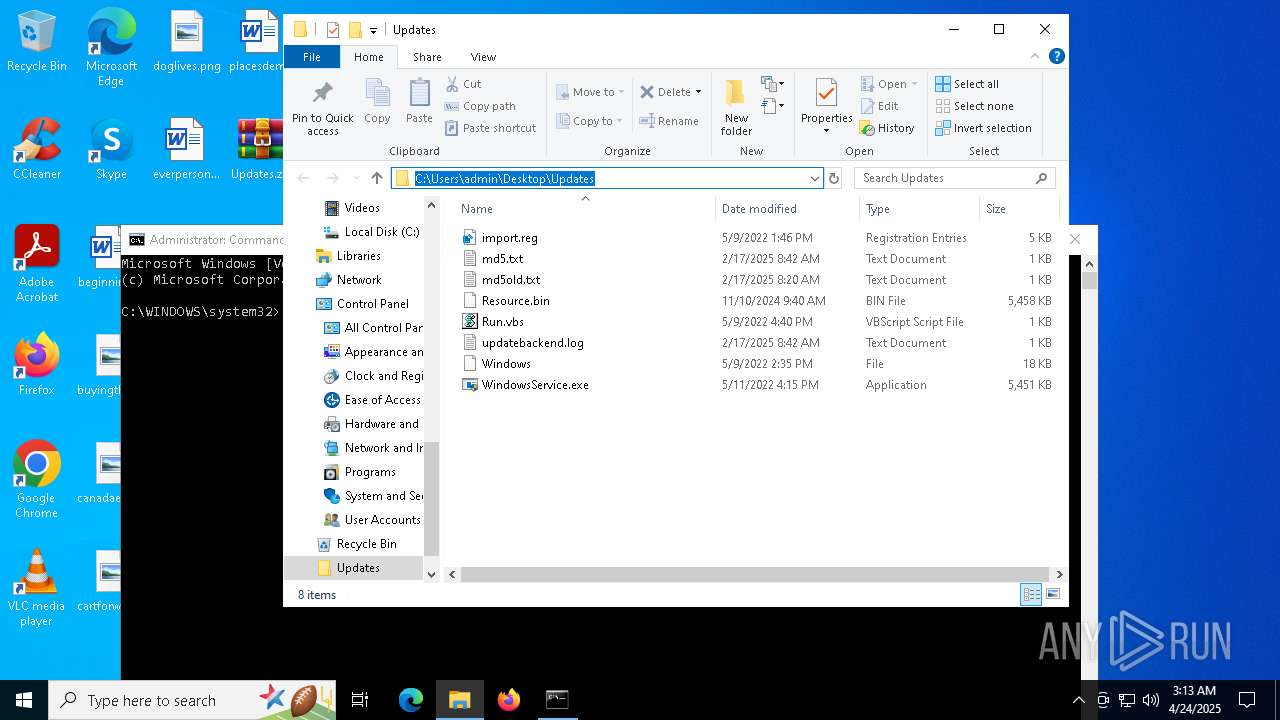
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
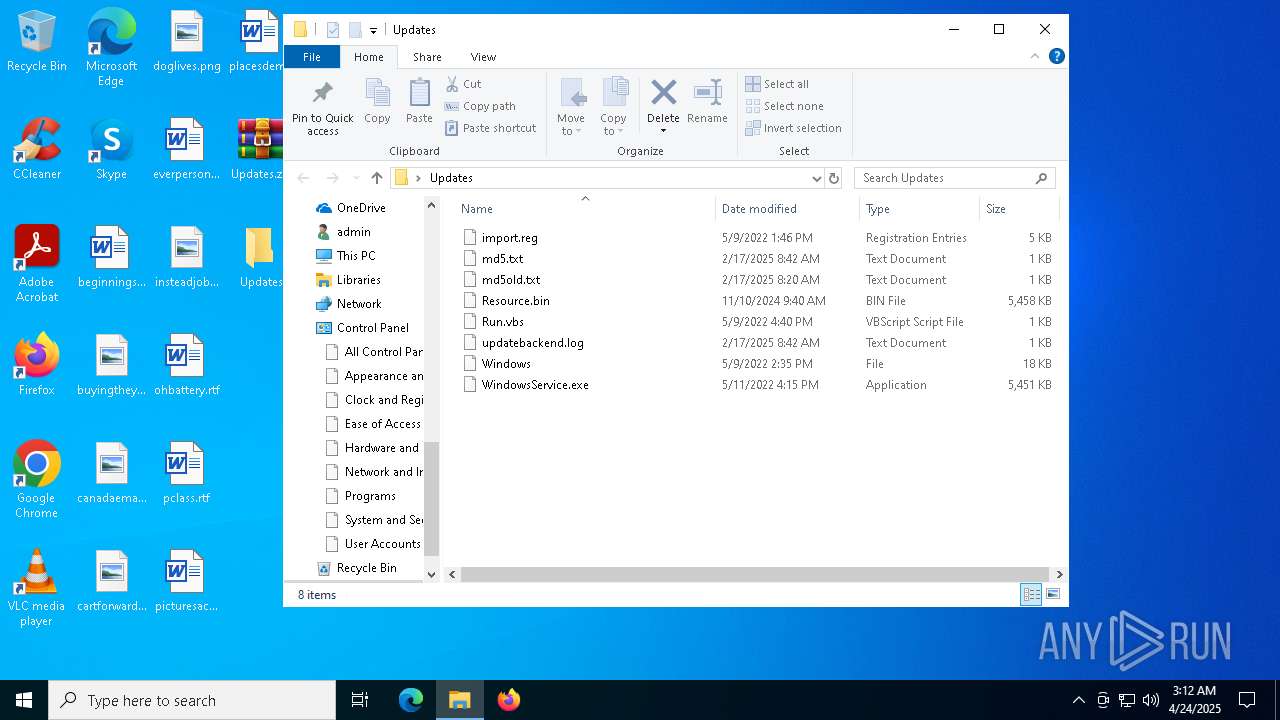
| 7620 | WinRAR.exe | C:\Users\admin\Desktop\Updates\Resource.bin | — | |
MD5:— | SHA256:— | |||
| 7620 | WinRAR.exe | C:\Users\admin\Desktop\Updates\updatebackend.log | text | |
MD5:146389F11F0E76CBC28CA267A34353A7 | SHA256:4DCD556F7A07C0C12FBE1BD911C3F5B857EBB09E57F4A0AC76CEECA171F3BC49 | |||
| 7724 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:FE22EC5755BC98988F9656F73B2E6FB8 | SHA256:F972C425CE176E960F6347F1CA2F64A8CE2B95A375C33A03E57538052BA0624D | |||
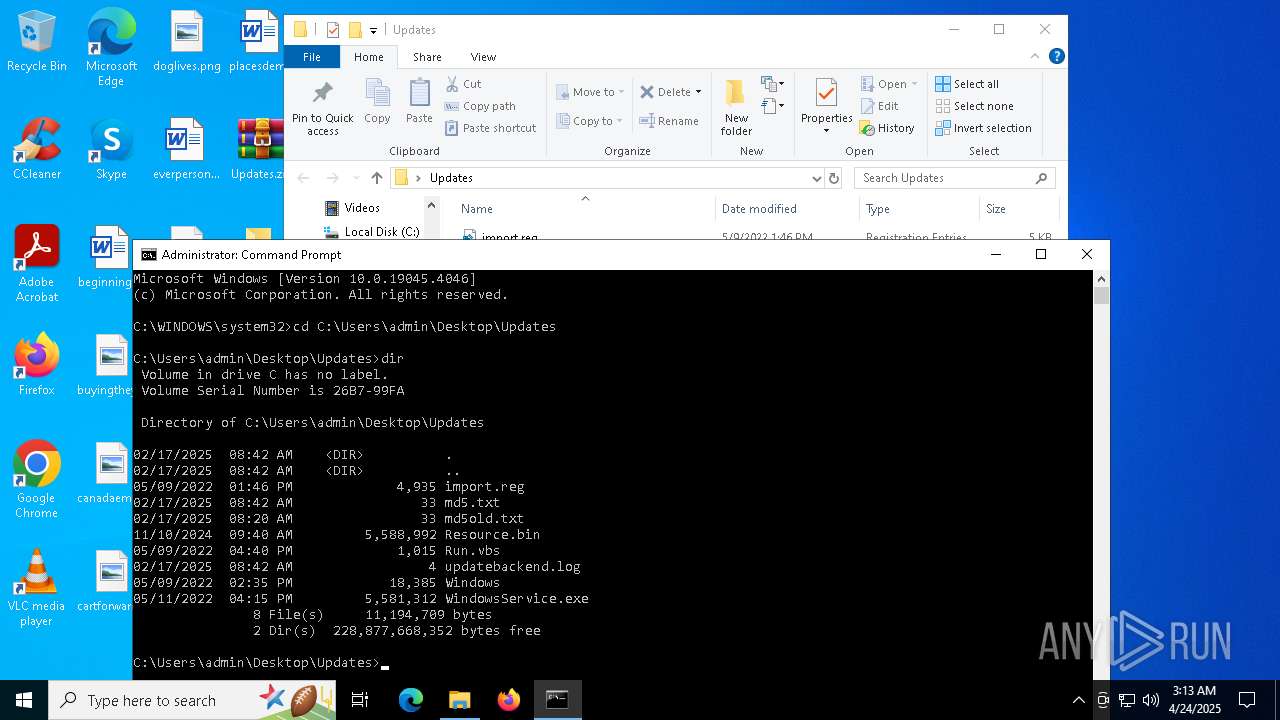
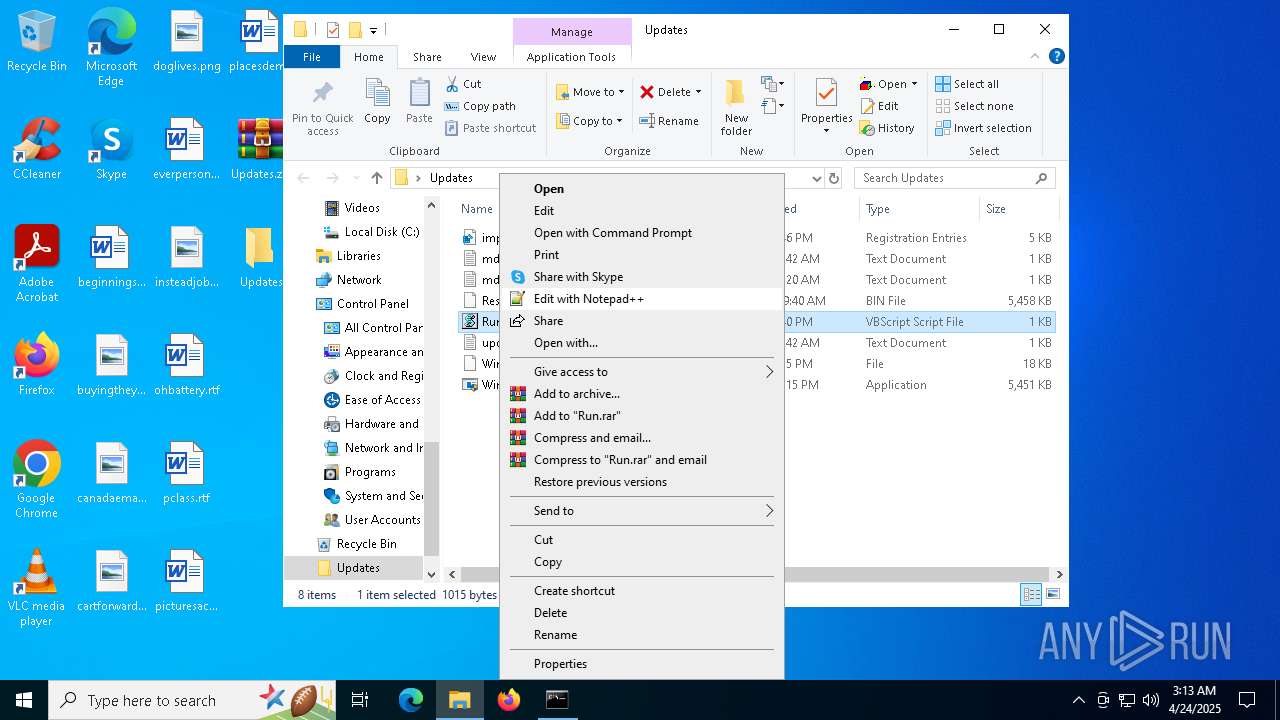
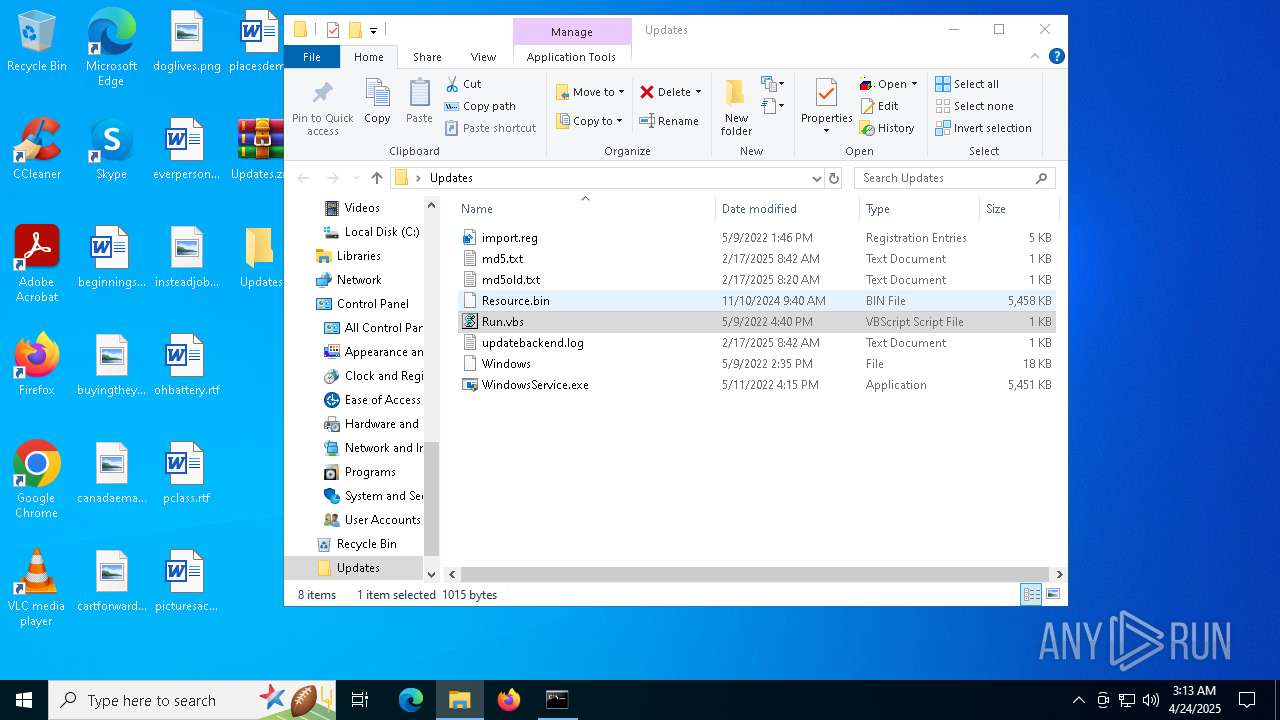
| 7620 | WinRAR.exe | C:\Users\admin\Desktop\Updates\WindowsService.exe | executable | |
MD5:1D7D93FA84BA7C5A5C8B1D62ACBB048D | SHA256:6D346056C766ED477967601425A4D162D15D429977910083C8A8BDD0D0C1C005 | |||
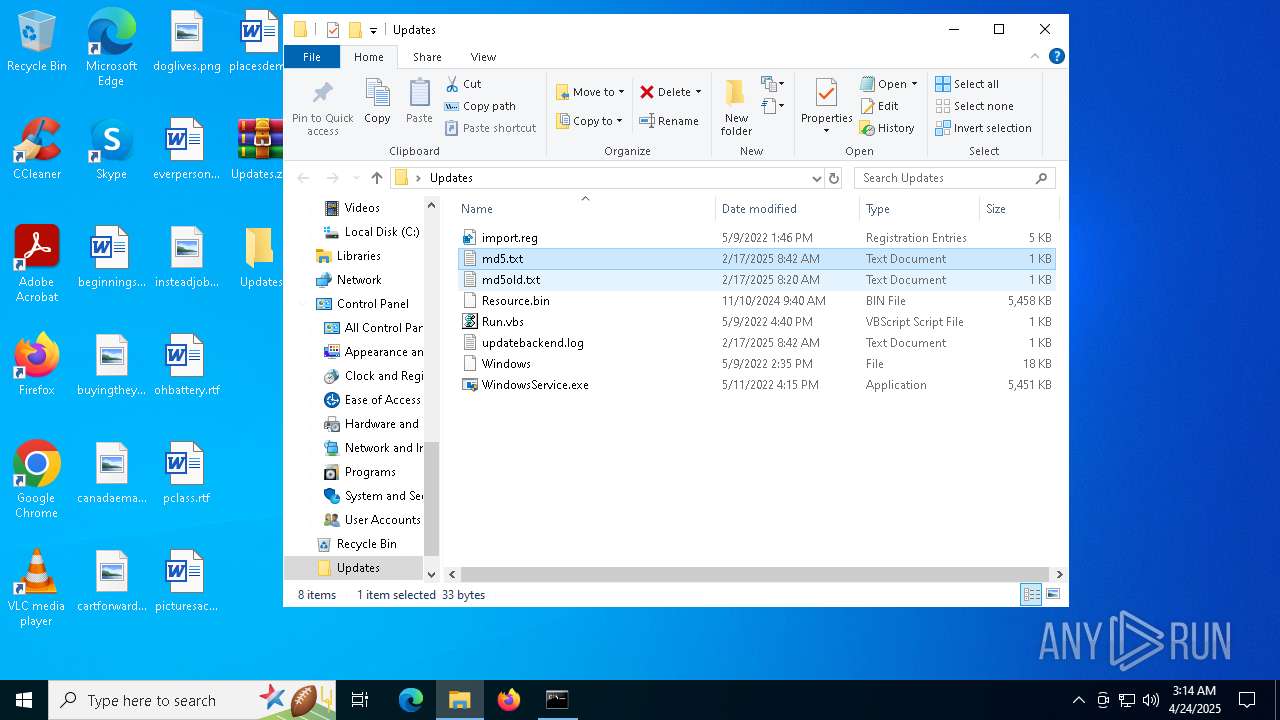
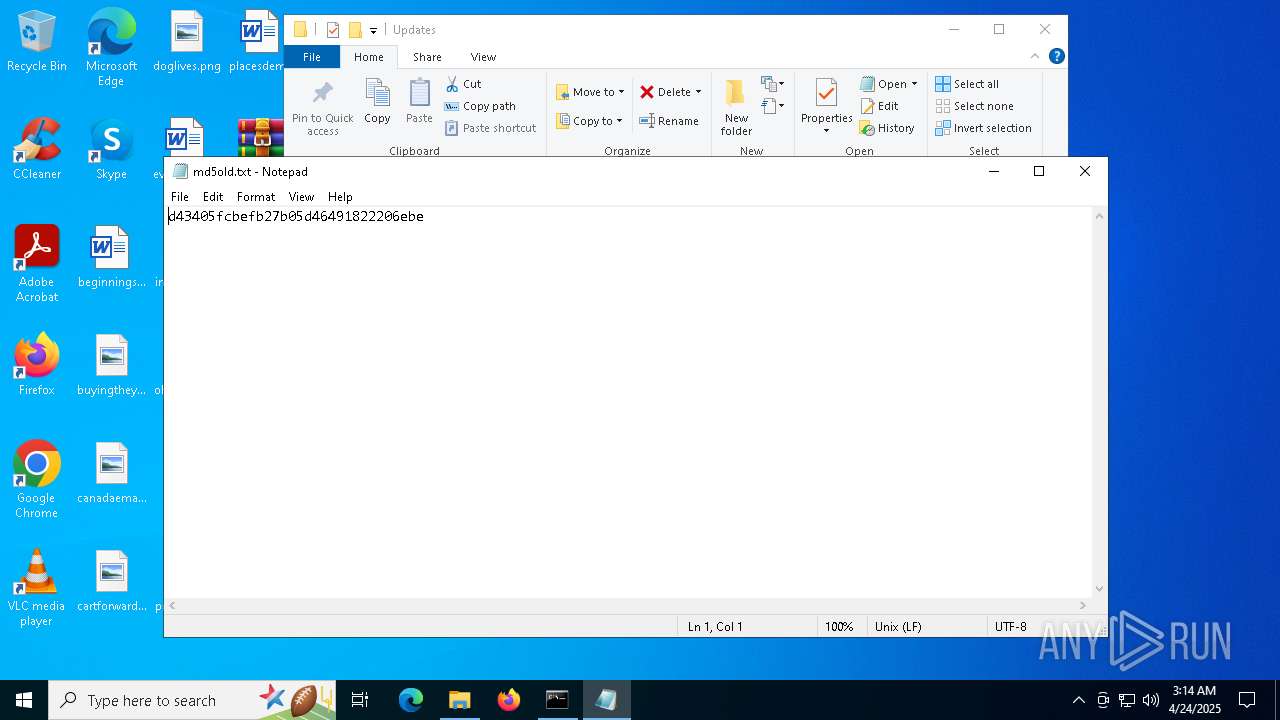
| 7620 | WinRAR.exe | C:\Users\admin\Desktop\Updates\md5old.txt | text | |
MD5:E8BC2231EC1E544601D2E7D0583D60A3 | SHA256:9B12A74329E1CCC577626482A94EE0F9CFBEFD81737645BD576E5E5CDD088A19 | |||
| 7620 | WinRAR.exe | C:\Users\admin\Desktop\Updates\Windows | text | |
MD5:BF520F8B27224F79EEBE30E6D6BC4DD7 | SHA256:614C0E2AB48512232A4C3C192CF05E6B8969A8DE74E6EE08989EC4A091FF2160 | |||
| 6620 | WindowsService.exe | C:\Windows\System32\WinRing0x64.sys | executable | |
MD5:0C0195C48B6B8582FA6F6373032118DA | SHA256:11BD2C9F9E2397C9A16E0990E4ED2CF0679498FE0FD418A3DFDAC60B5C160EE5 | |||
| 7724 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:F11D96162BC521F5CF49FFE6B6841C9B | SHA256:BE9AEAEAB5A2E4899BA7E582274BA592C1B9BAF688B340A754B8EF32B23CFA9C | |||
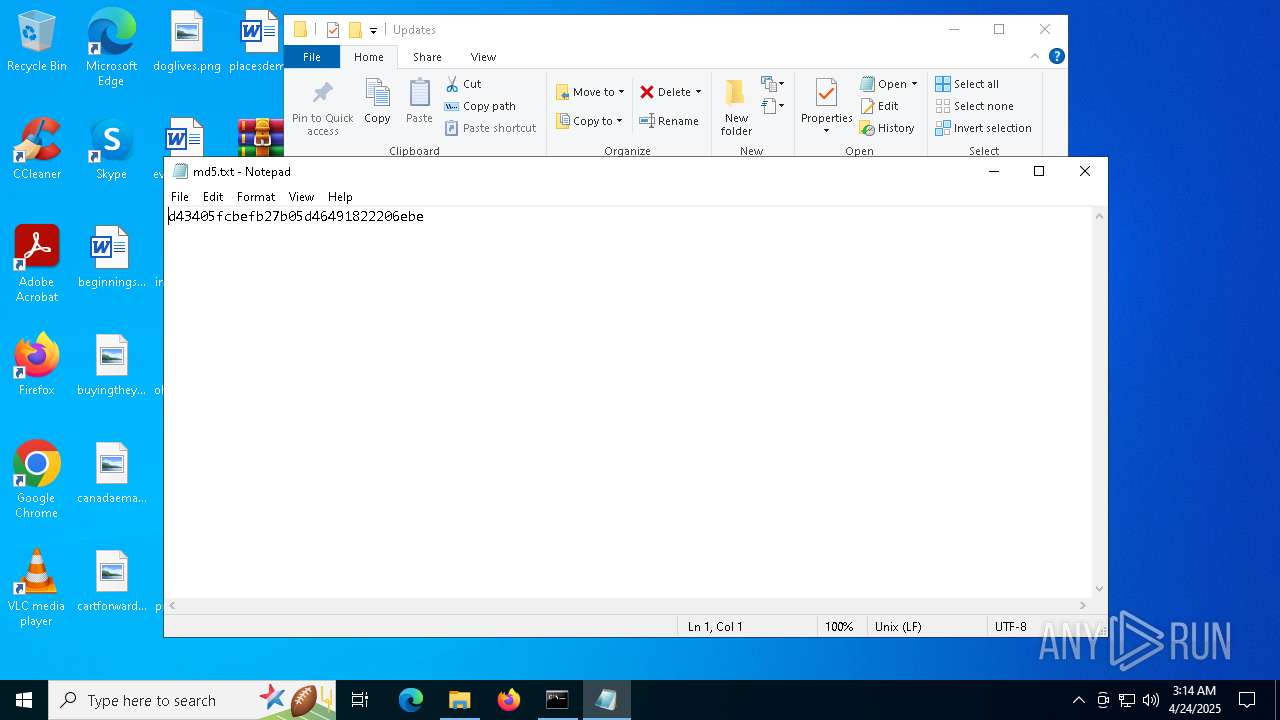
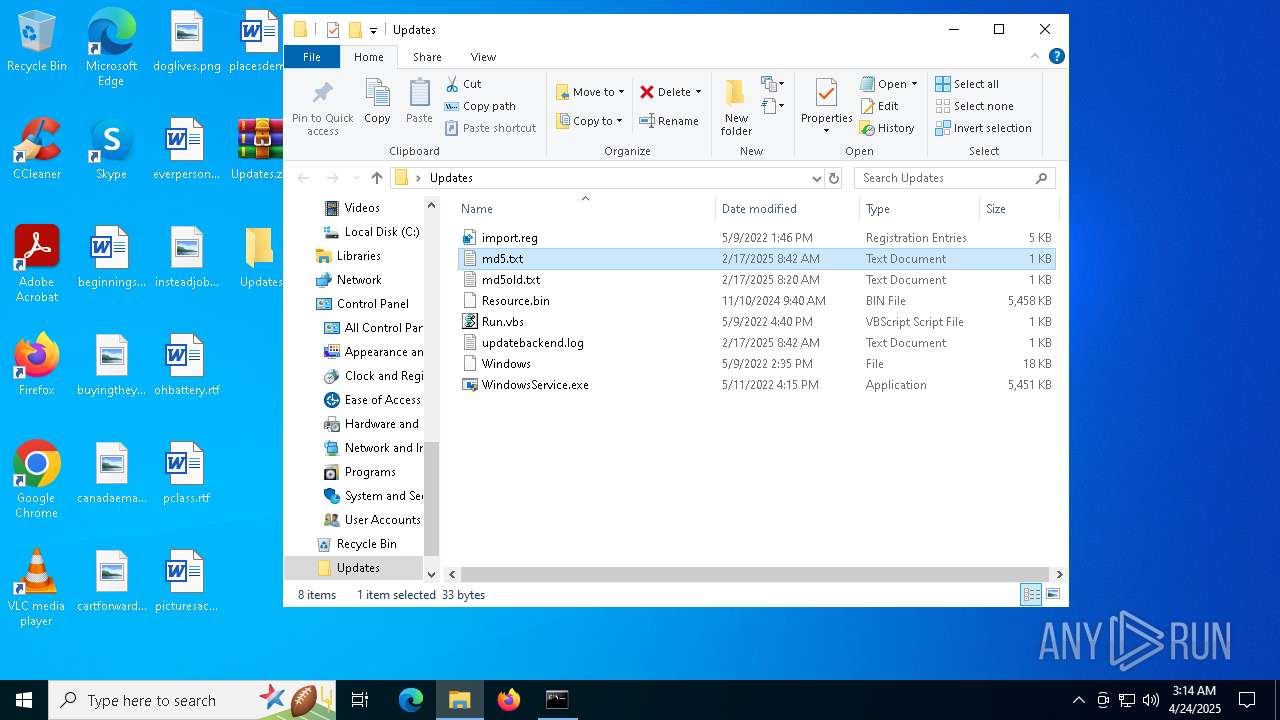
| 7620 | WinRAR.exe | C:\Users\admin\Desktop\Updates\md5.txt | text | |
MD5:E8BC2231EC1E544601D2E7D0583D60A3 | SHA256:9B12A74329E1CCC577626482A94EE0F9CFBEFD81737645BD576E5E5CDD088A19 | |||
| 7724 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\plugins\config\converter.ini | text | |
MD5:F70F579156C93B097E656CABA577A5C9 | SHA256:B926498A19CA95DC28964B7336E5847107DD3C0F52C85195C135D9DD6CA402D4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2 397
TCP/UDP connections
2 424
DNS requests
2 442
Threats
4 954
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6620 | WindowsService.exe | GET | 200 | 188.138.125.57:83 | http://www.google.com.4dgom8njcy7bapxk.service-windows.com:83/md5.txt | unknown | — | — | unknown |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6620 | WindowsService.exe | GET | 200 | 188.138.125.57:83 | http://www.google.com.4dgom8njcy7bapxk.service-windows.com:83/md5.txt | unknown | — | — | unknown |
6620 | WindowsService.exe | GET | 200 | 188.138.125.57:83 | http://www.google.com.4dgom8njcy7bapxk.service-windows.com:83/md5.txt | unknown | — | — | unknown |
6620 | WindowsService.exe | GET | 200 | 188.138.125.57:83 | http://www.google.com.4dgom8njcy7bapxk.service-windows.com:83/md5.txt | unknown | — | — | unknown |
6620 | WindowsService.exe | GET | 200 | 188.138.125.57:83 | http://www.google.com.4dgom8njcy7bapxk.service-windows.com:83/md5.txt | unknown | — | — | unknown |
6620 | WindowsService.exe | GET | 200 | 188.138.125.57:83 | http://www.google.com.4dgom8njcy7bapxk.service-windows.com:83/md5.txt | unknown | — | — | unknown |
6620 | WindowsService.exe | GET | 200 | 188.138.125.57:83 | http://www.google.com.4dgom8njcy7bapxk.service-windows.com:83/md5.txt | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2432 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.google.com.kzcp5i31snlyoqrj.service-windows.com |
| unknown |
www.google.com.4dgom8njcy7bapxk.service-windows.com |
| unknown |
www.google.com.s4vi6rn2btymfa81.service-windows.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain ( .service-windows .com) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain ( .service-windows .com) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain ( .service-windows .com) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain ( .service-windows .com) |