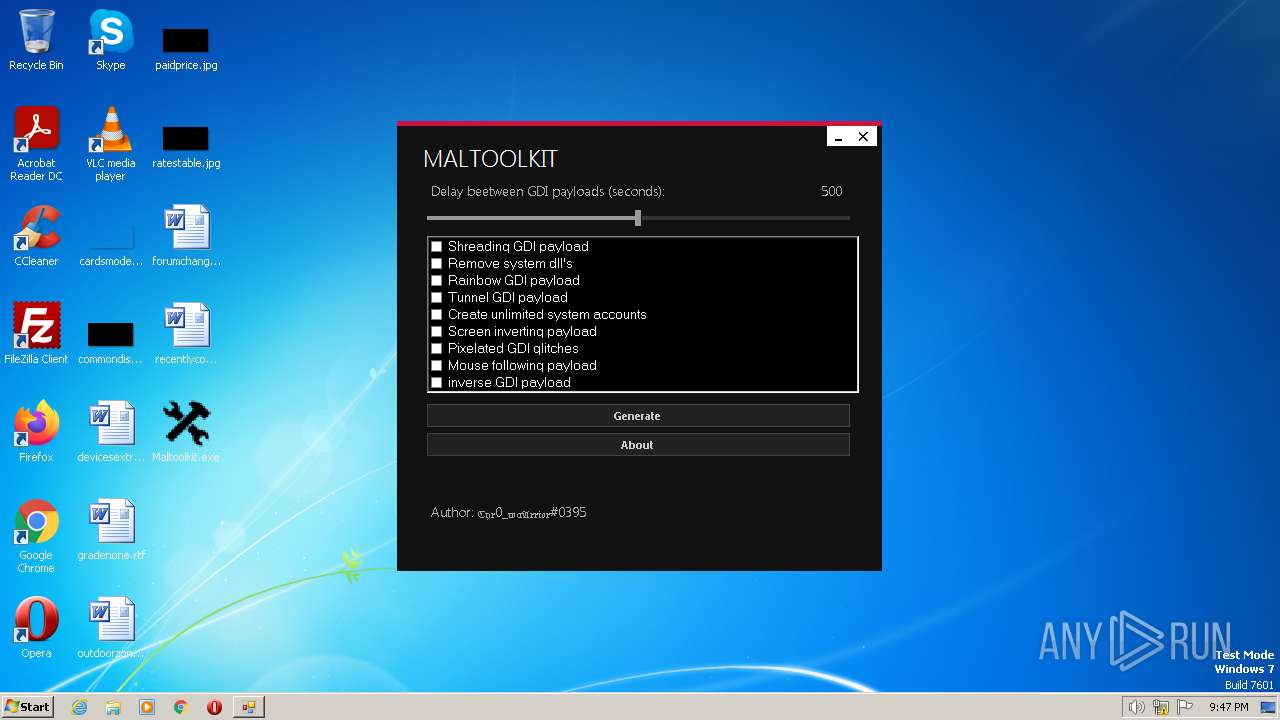
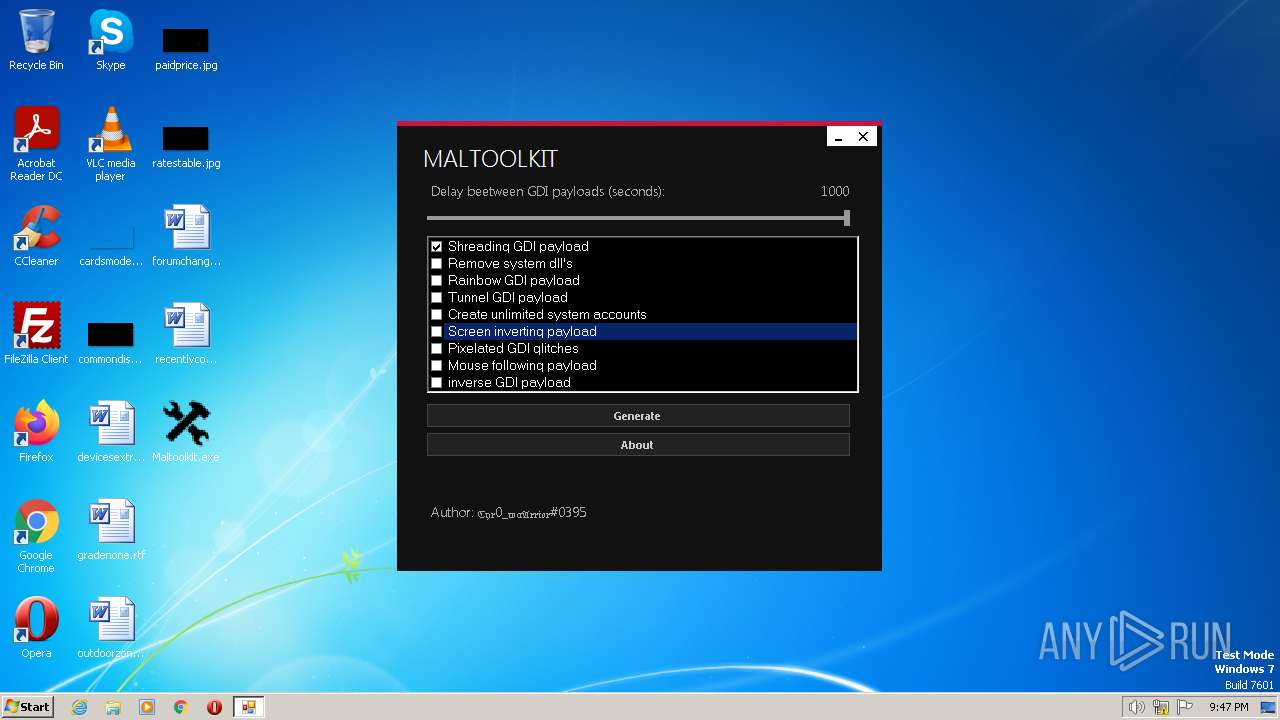
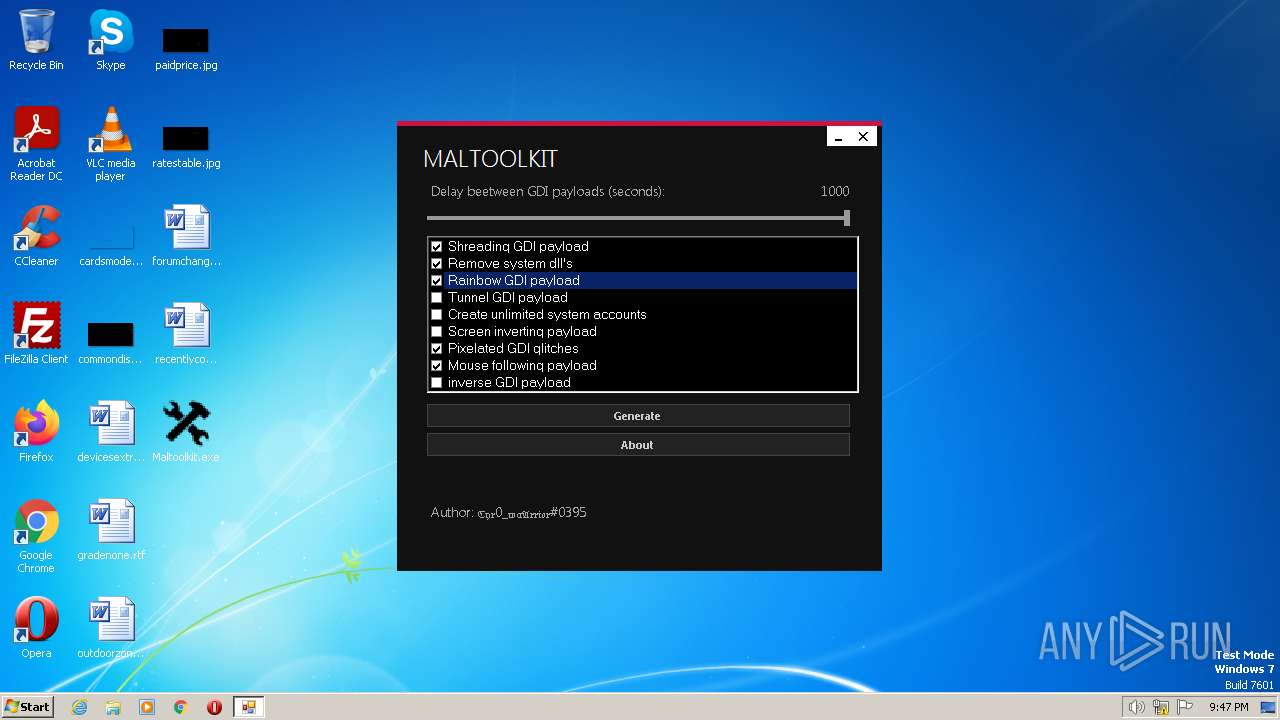
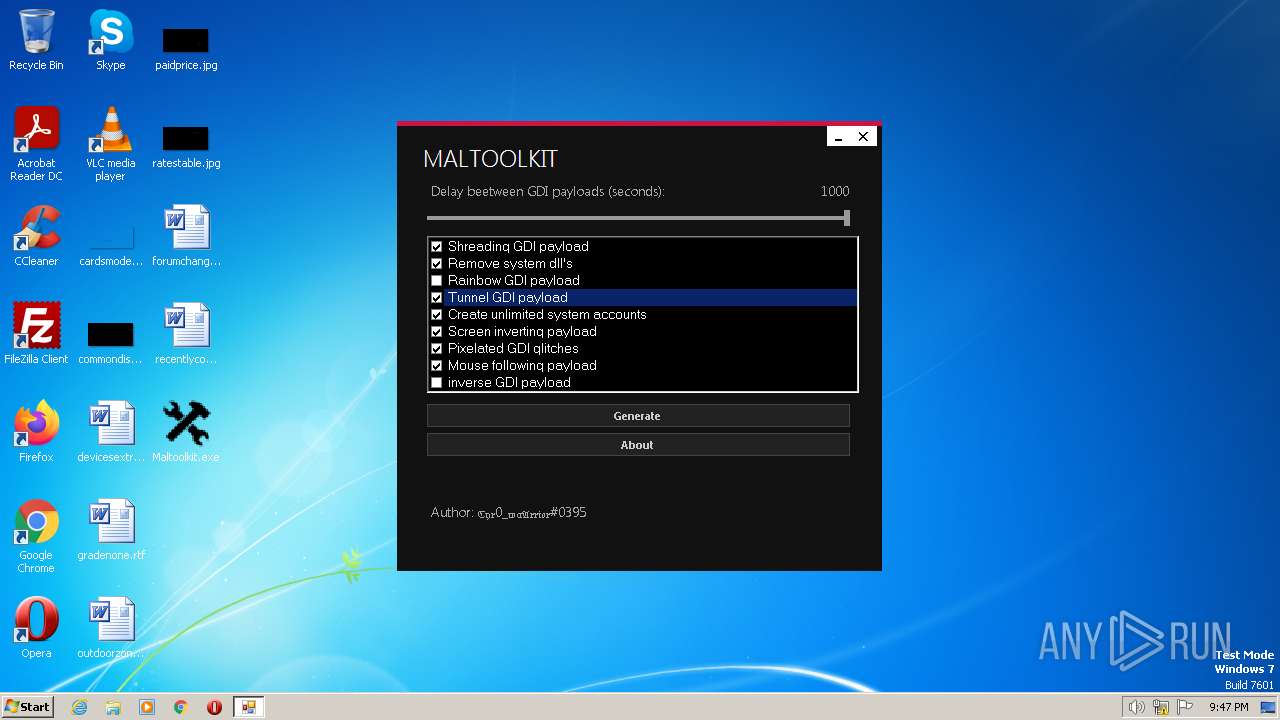
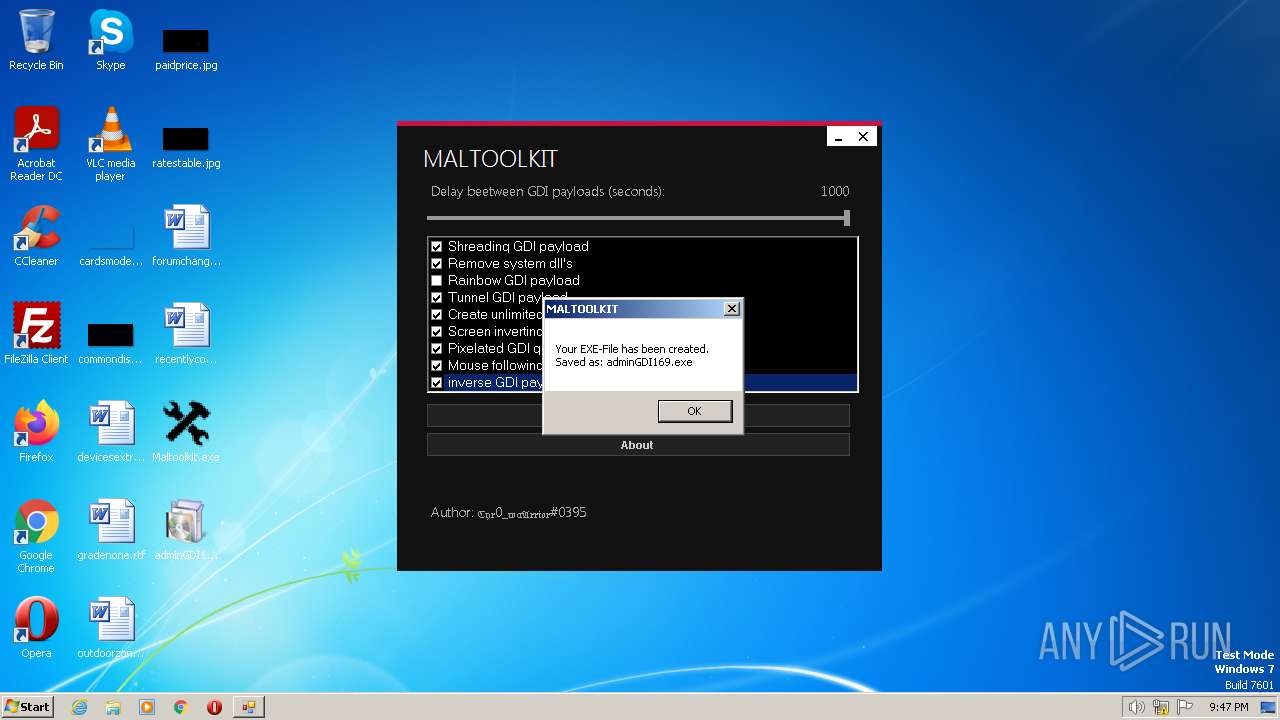
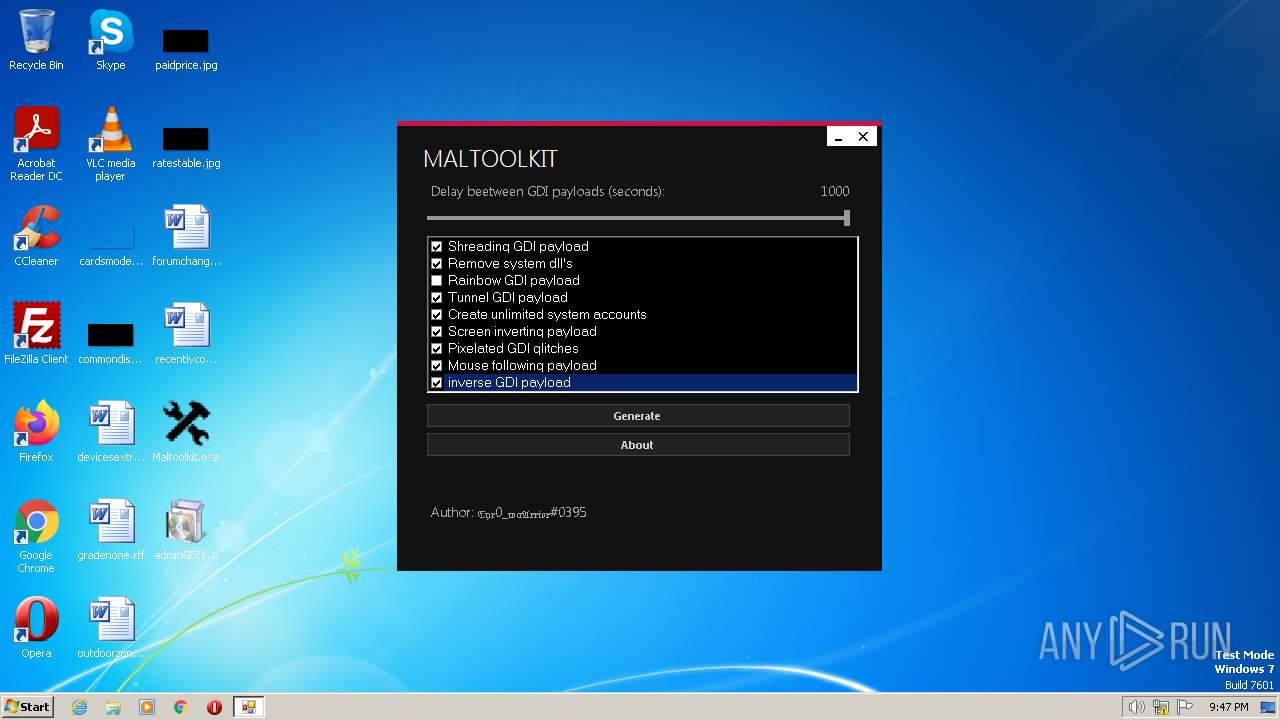
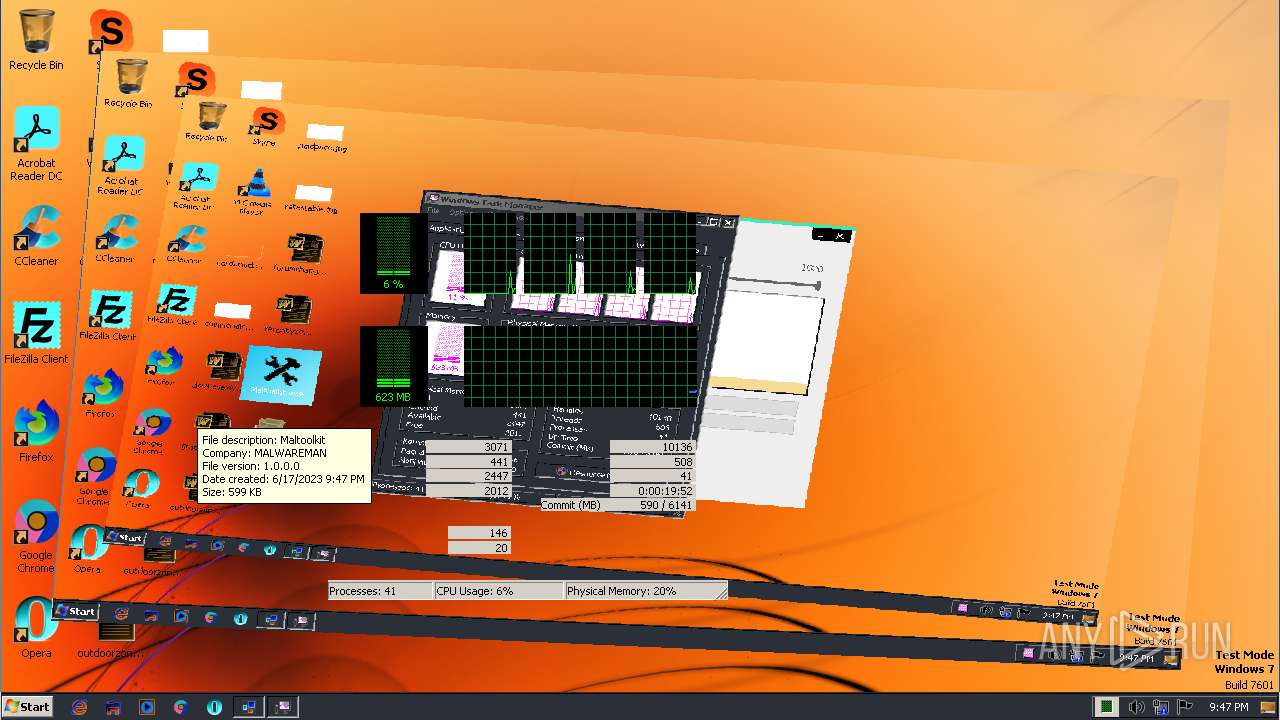
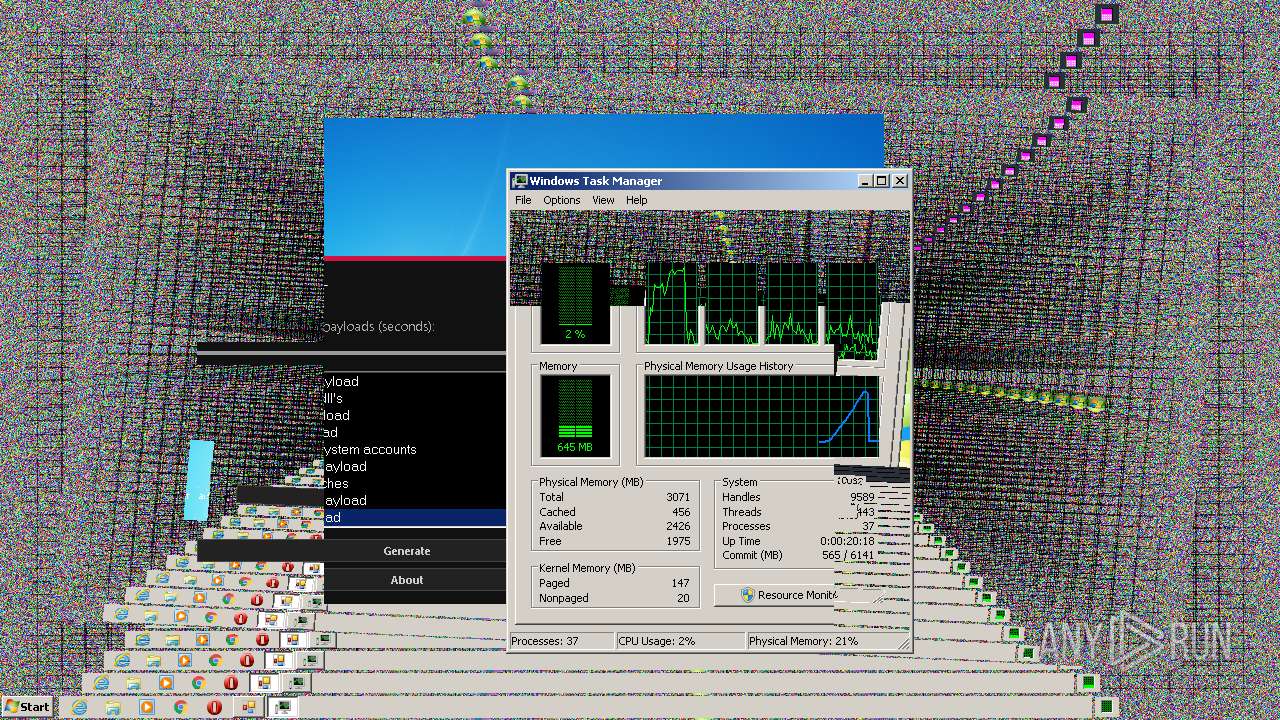
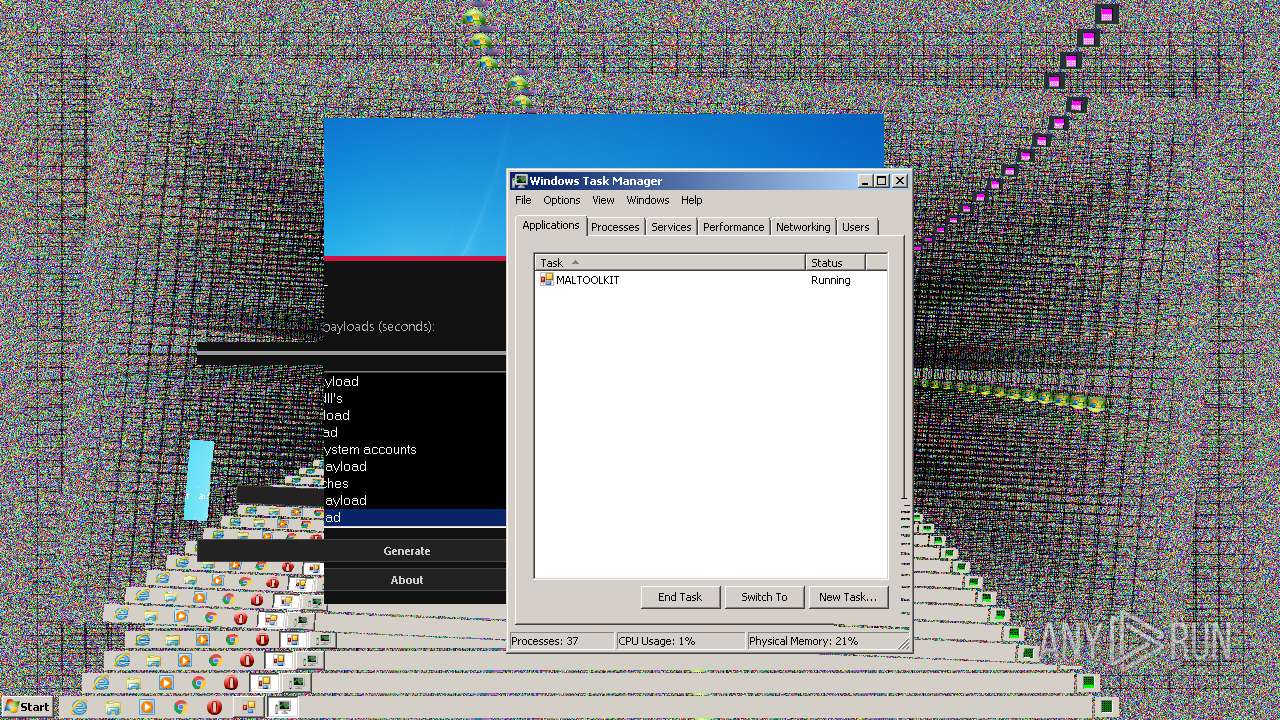
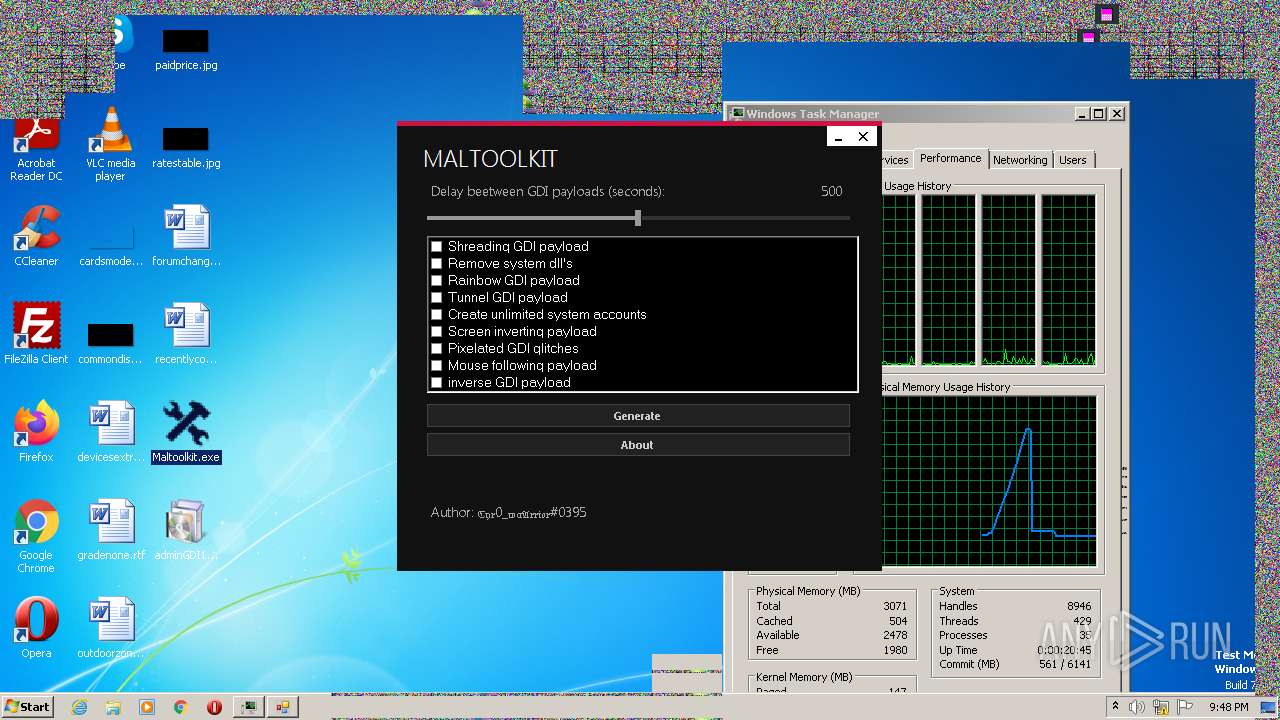
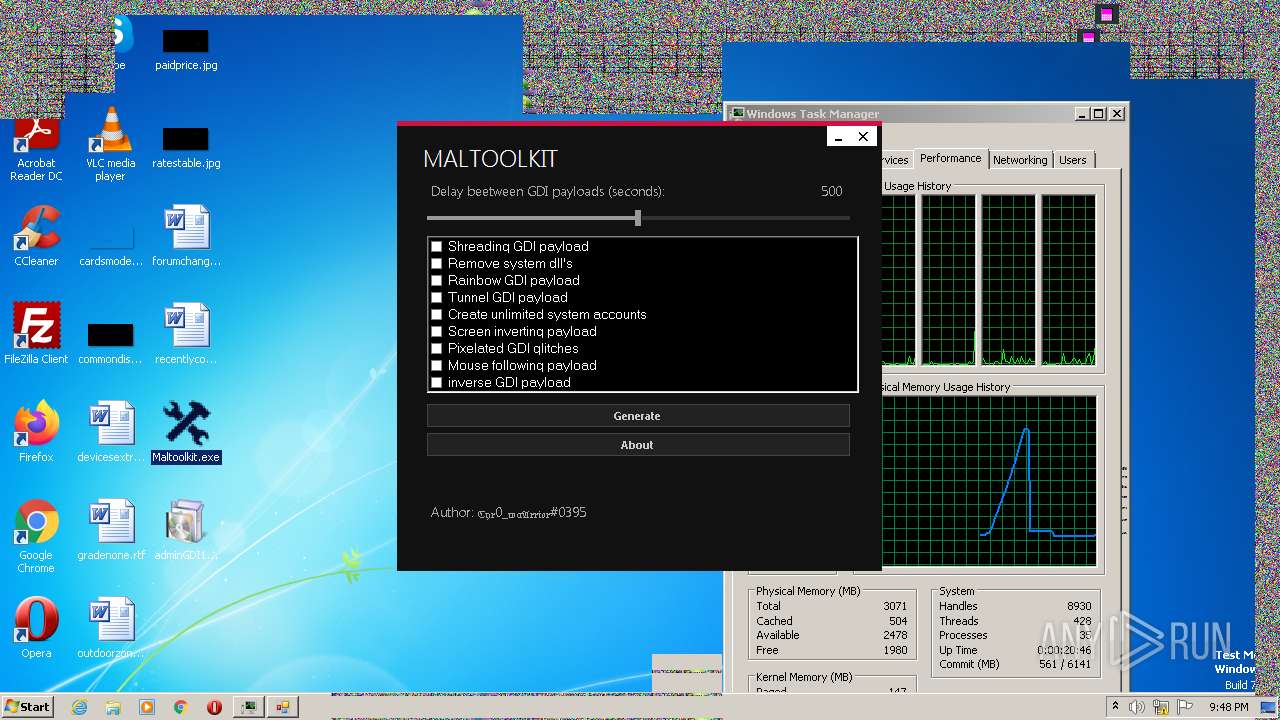
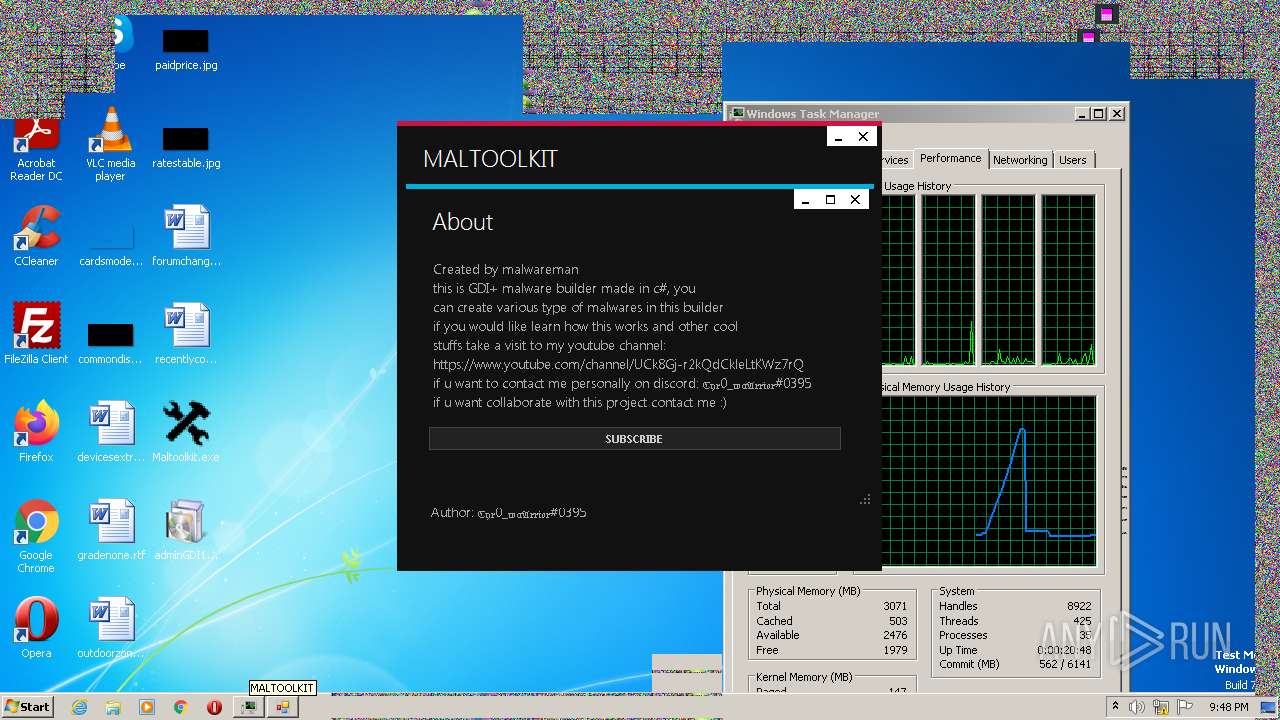
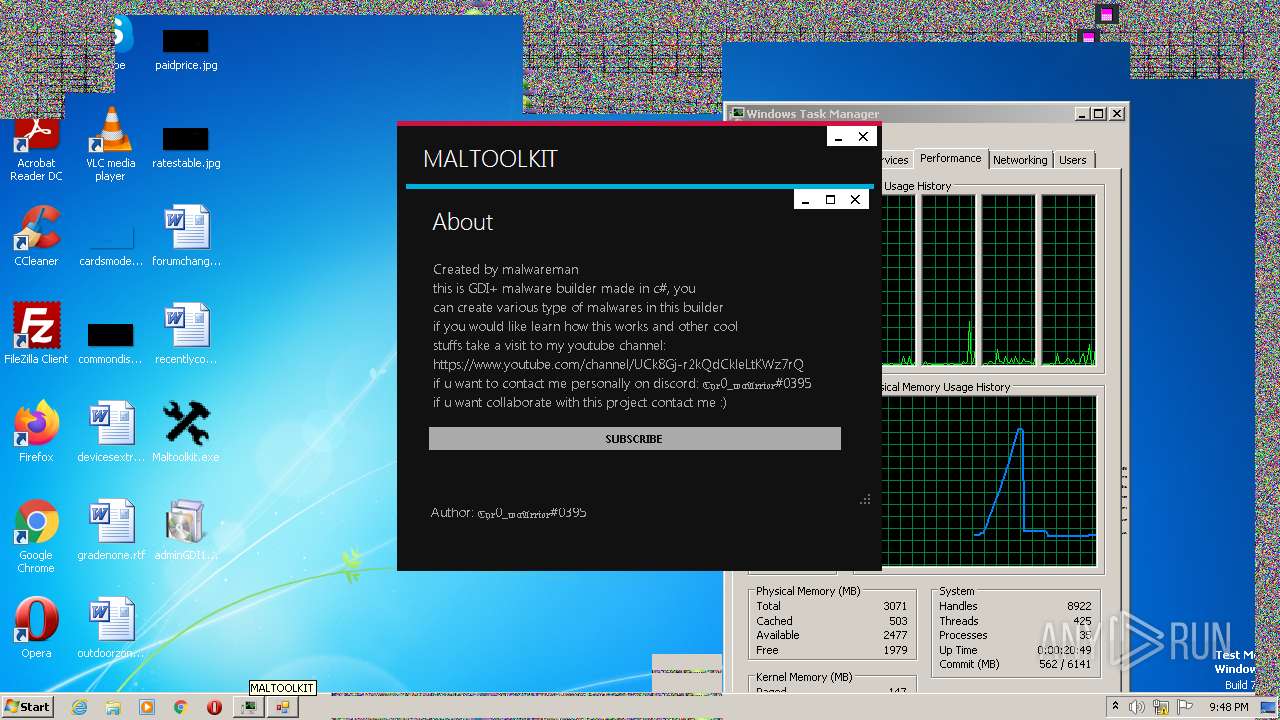
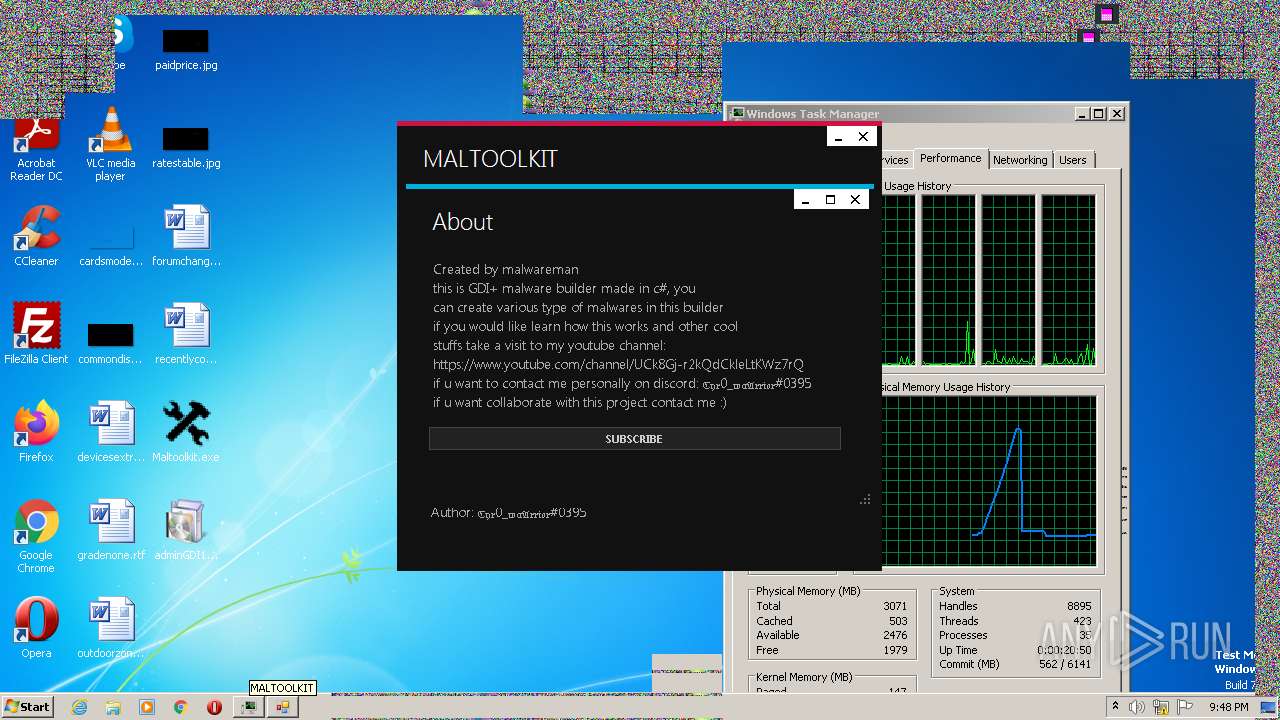
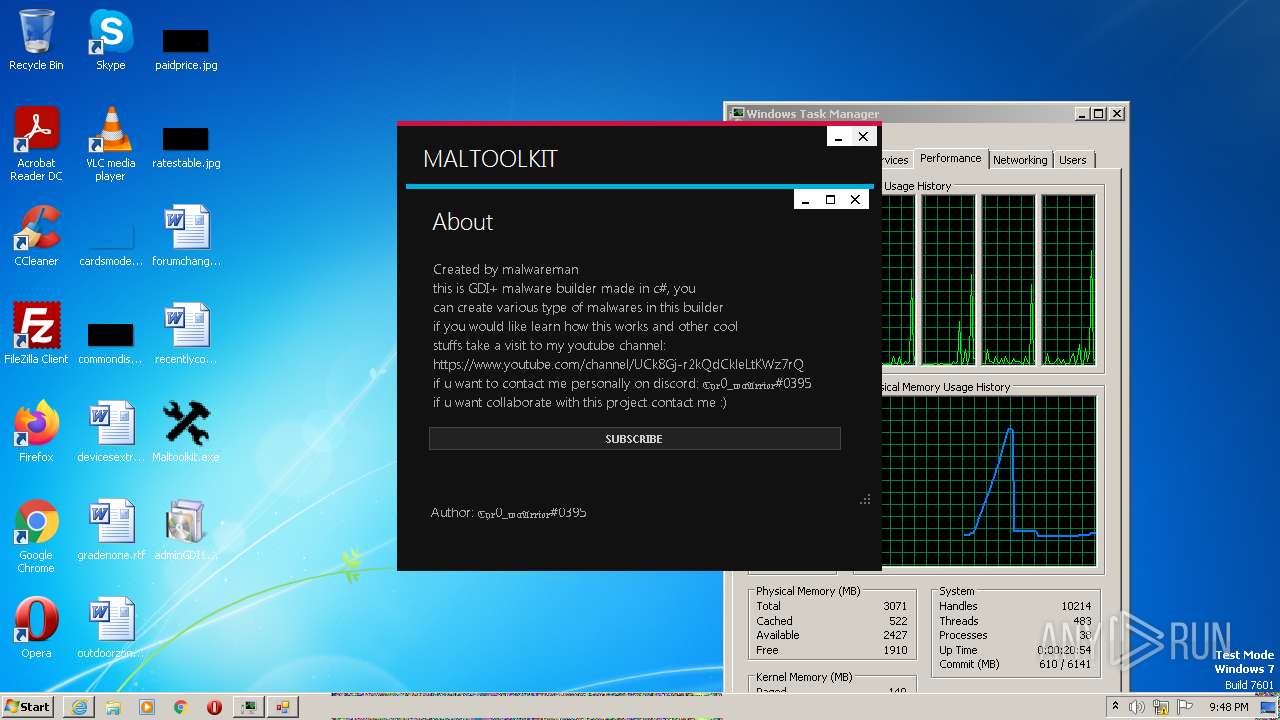
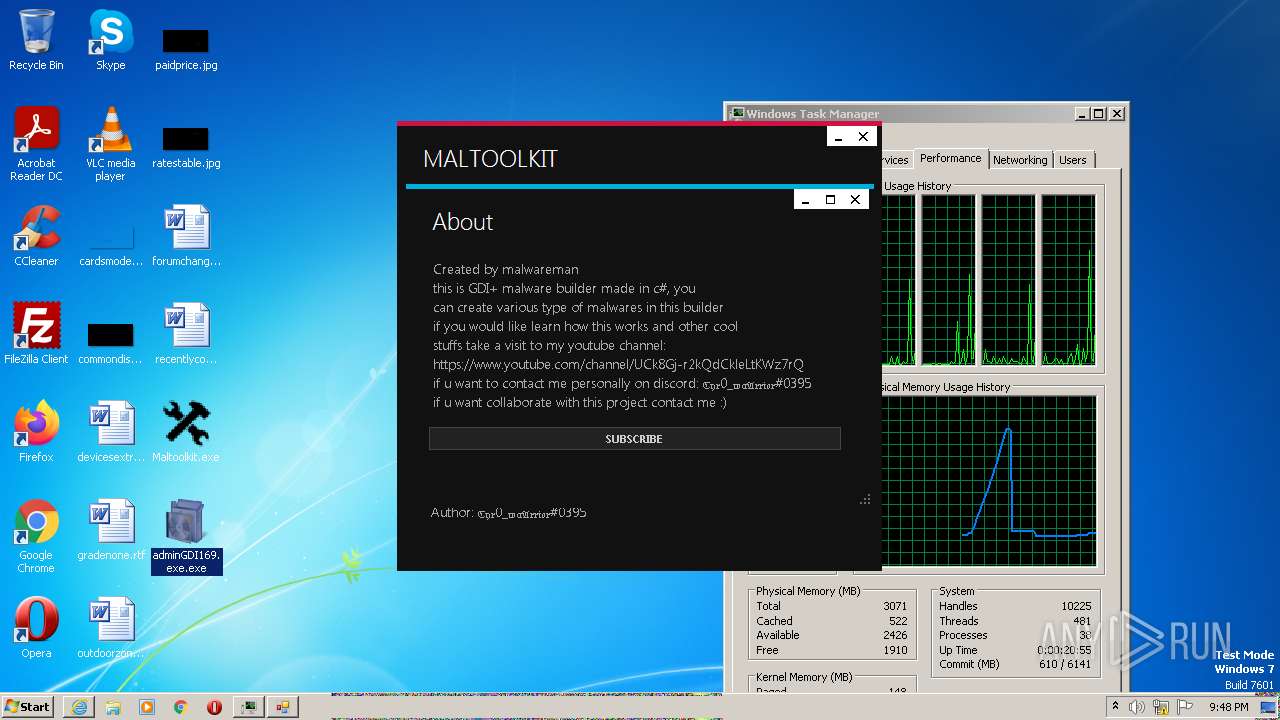
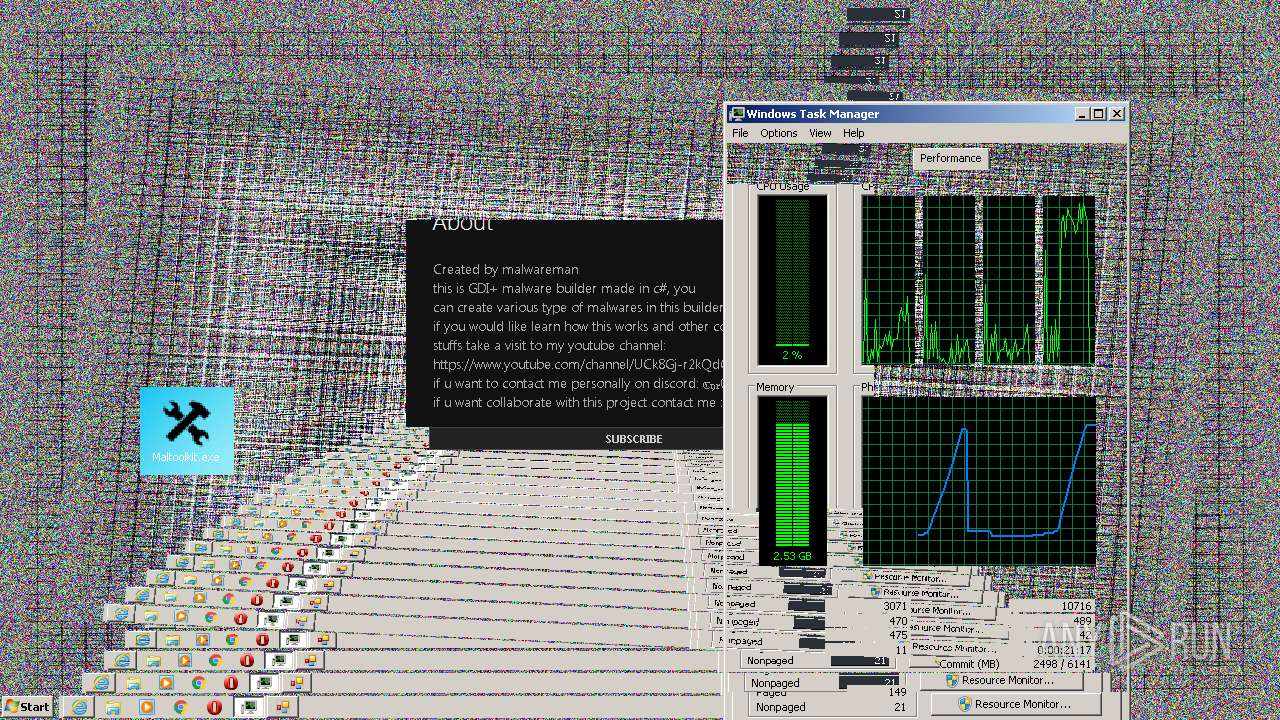
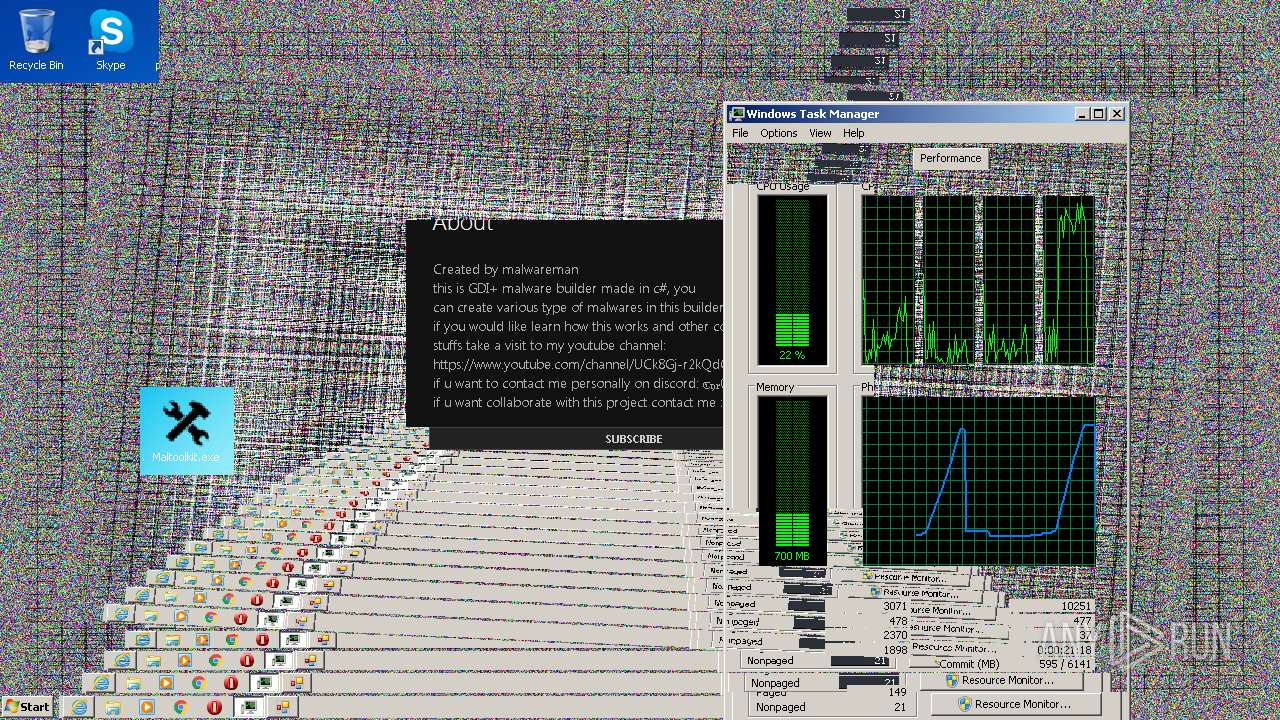
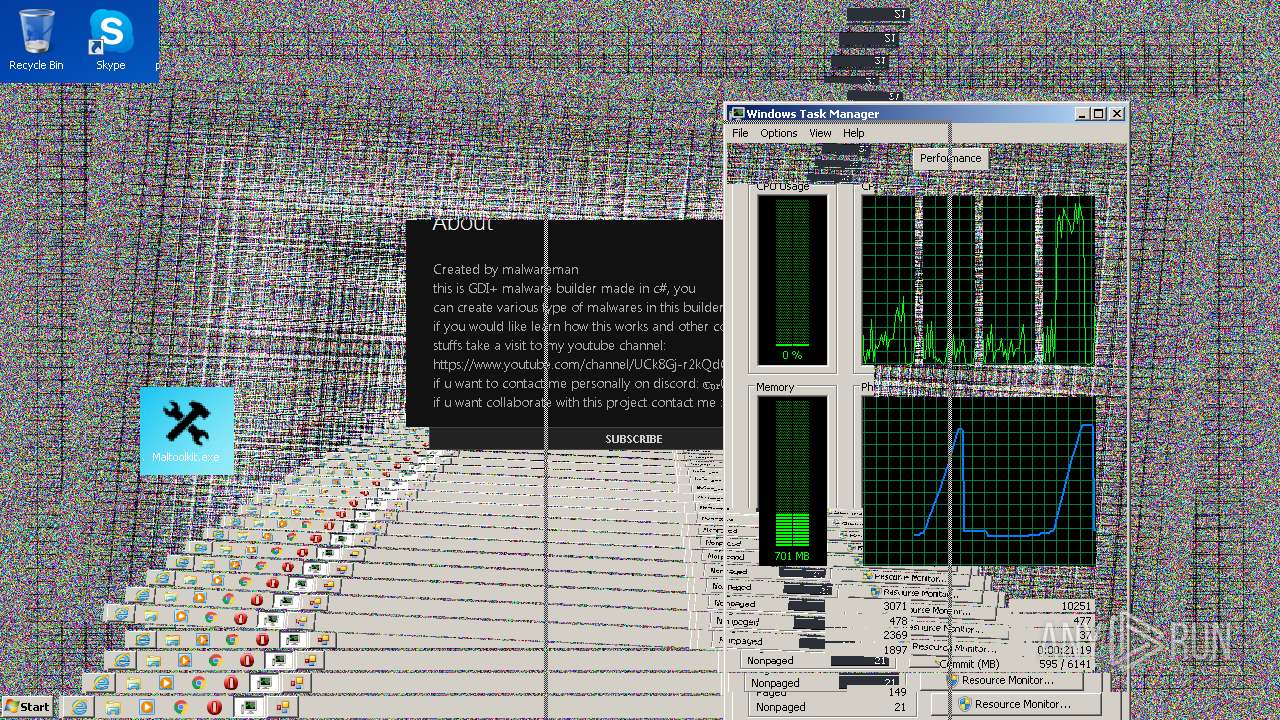
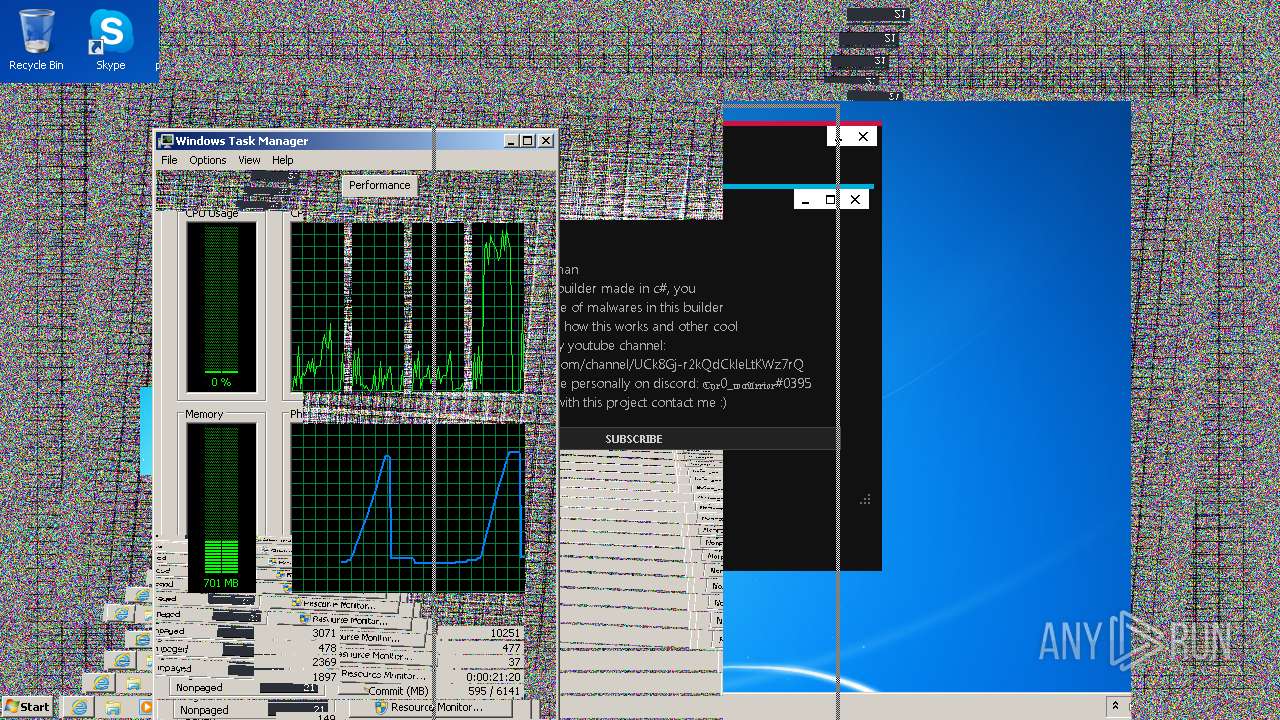
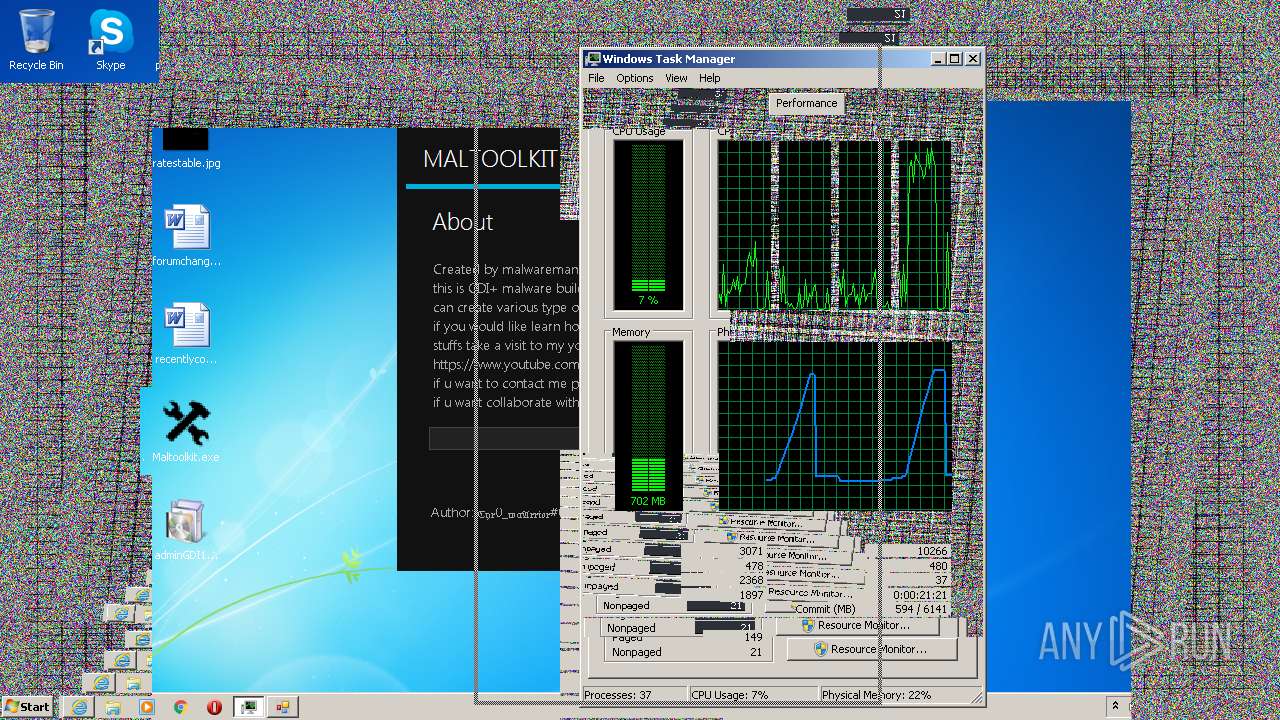
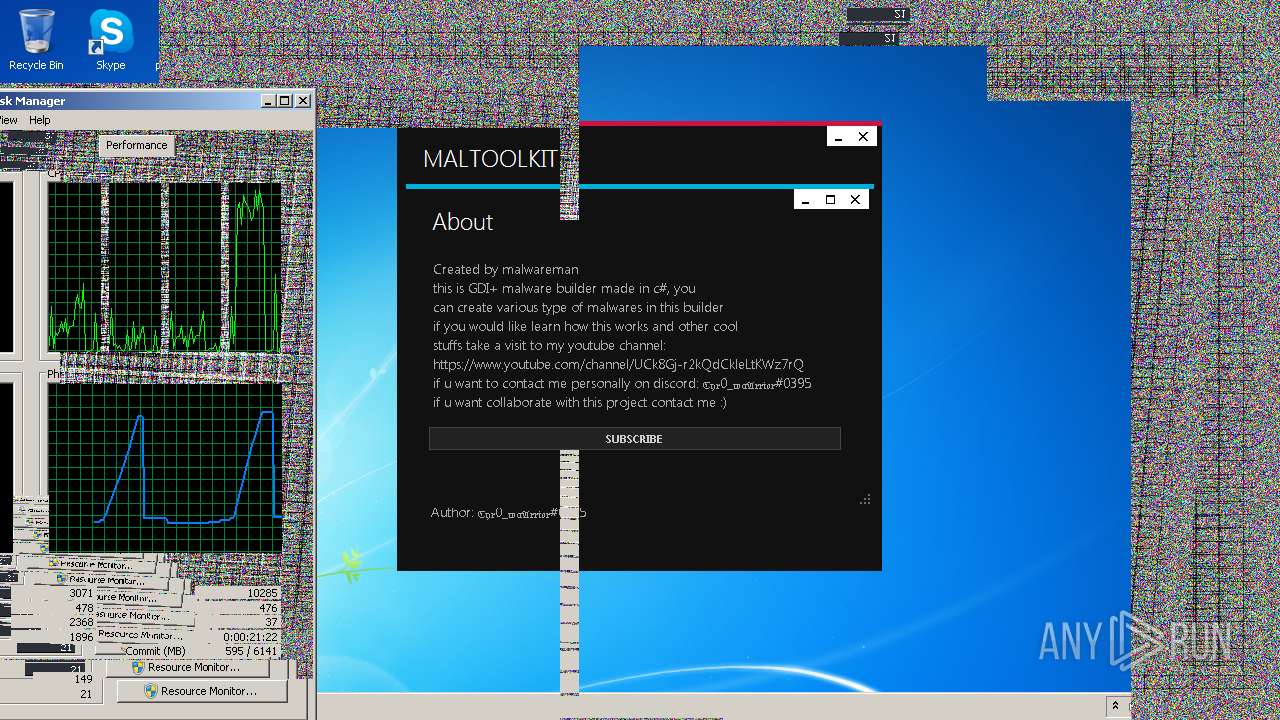
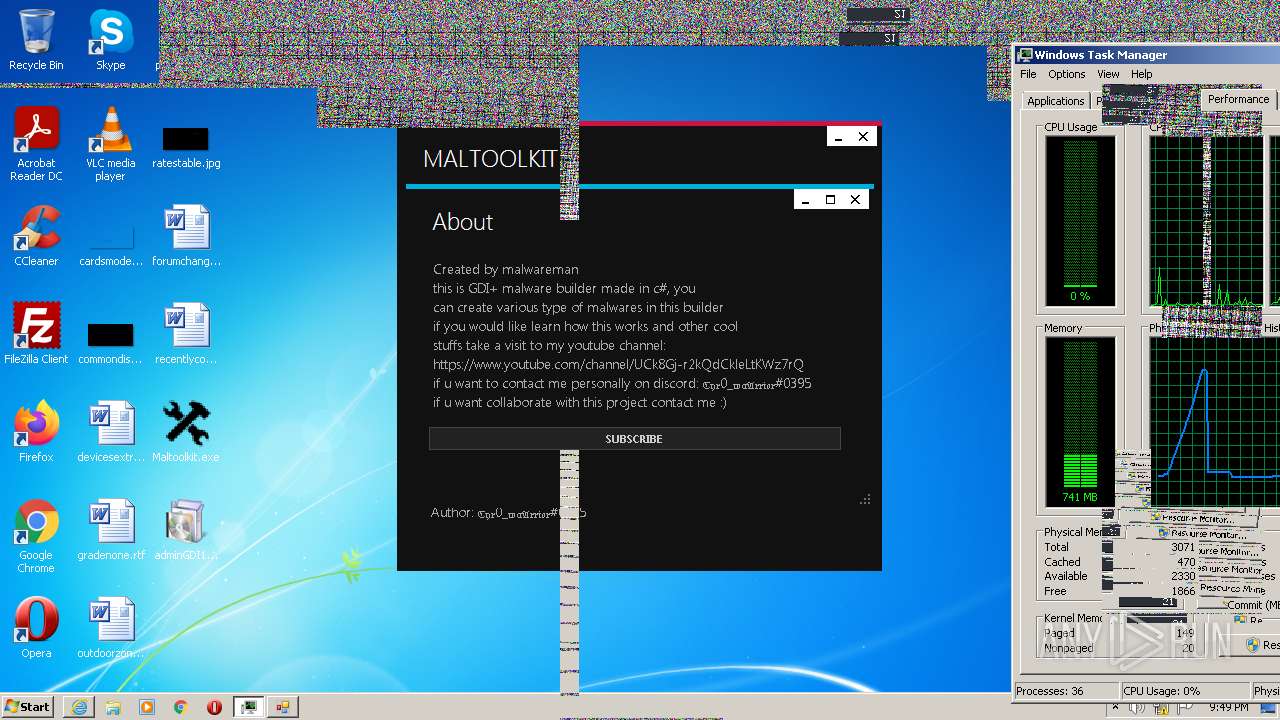
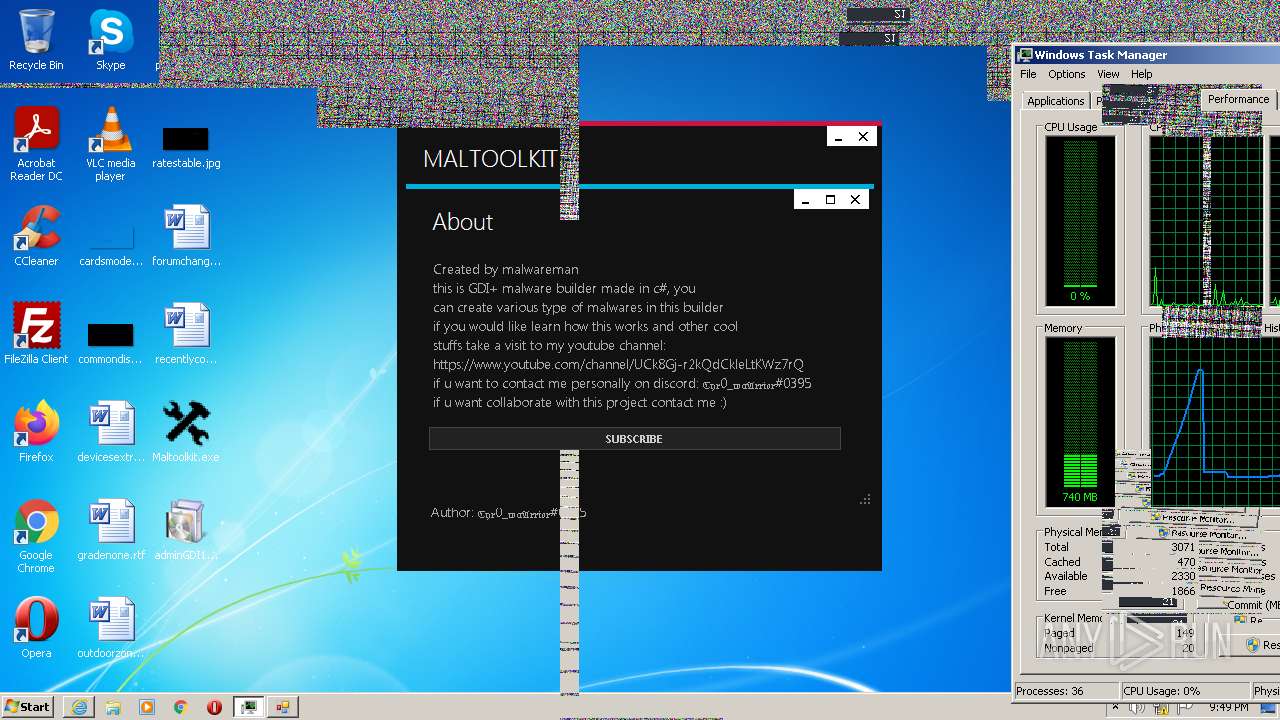
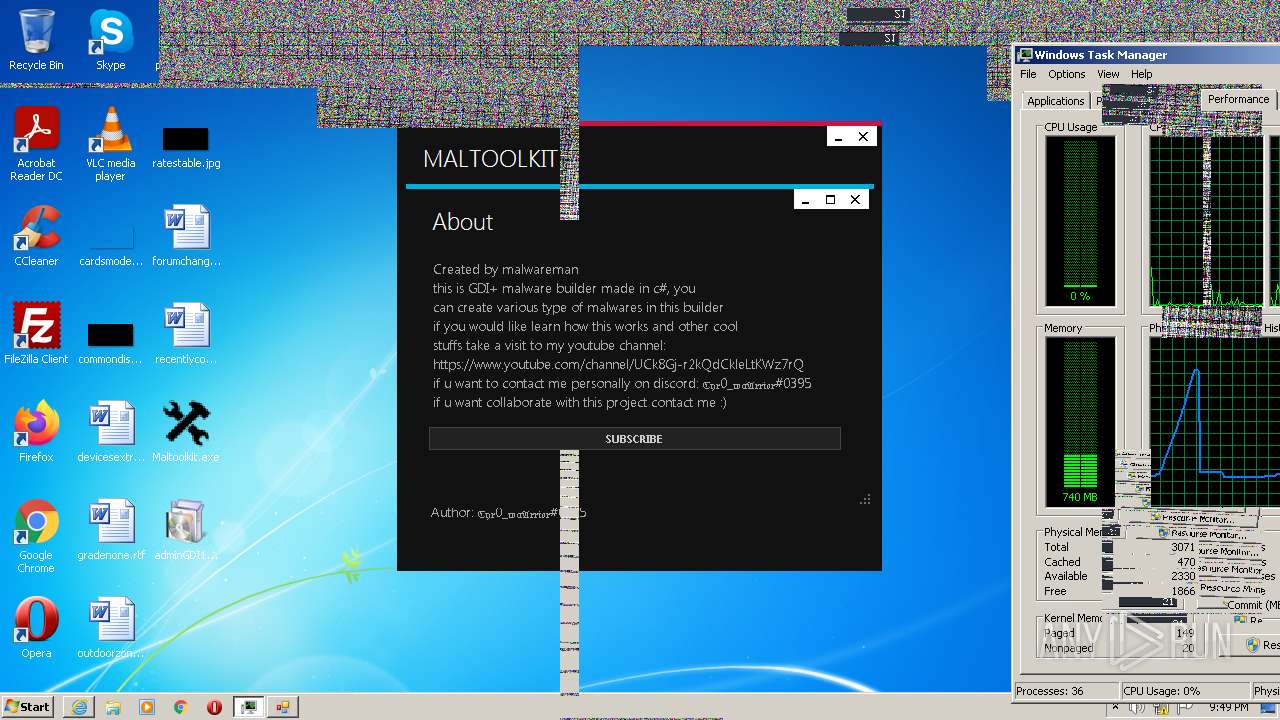
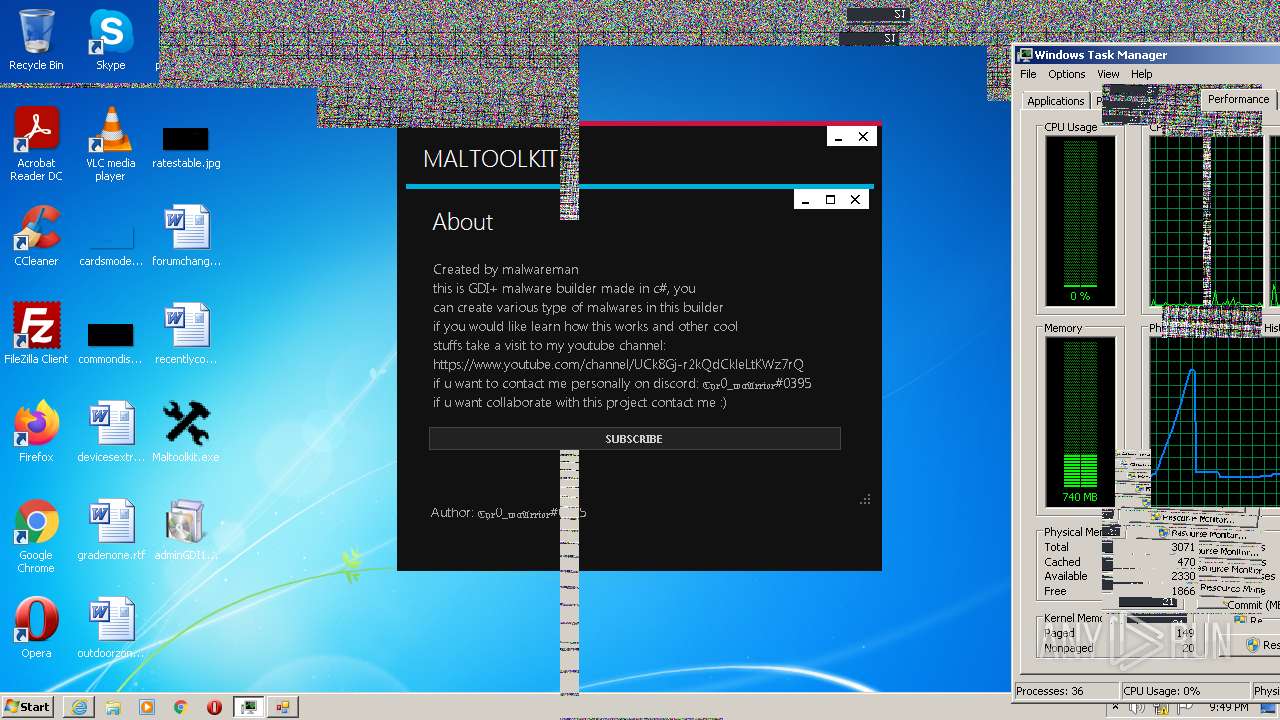
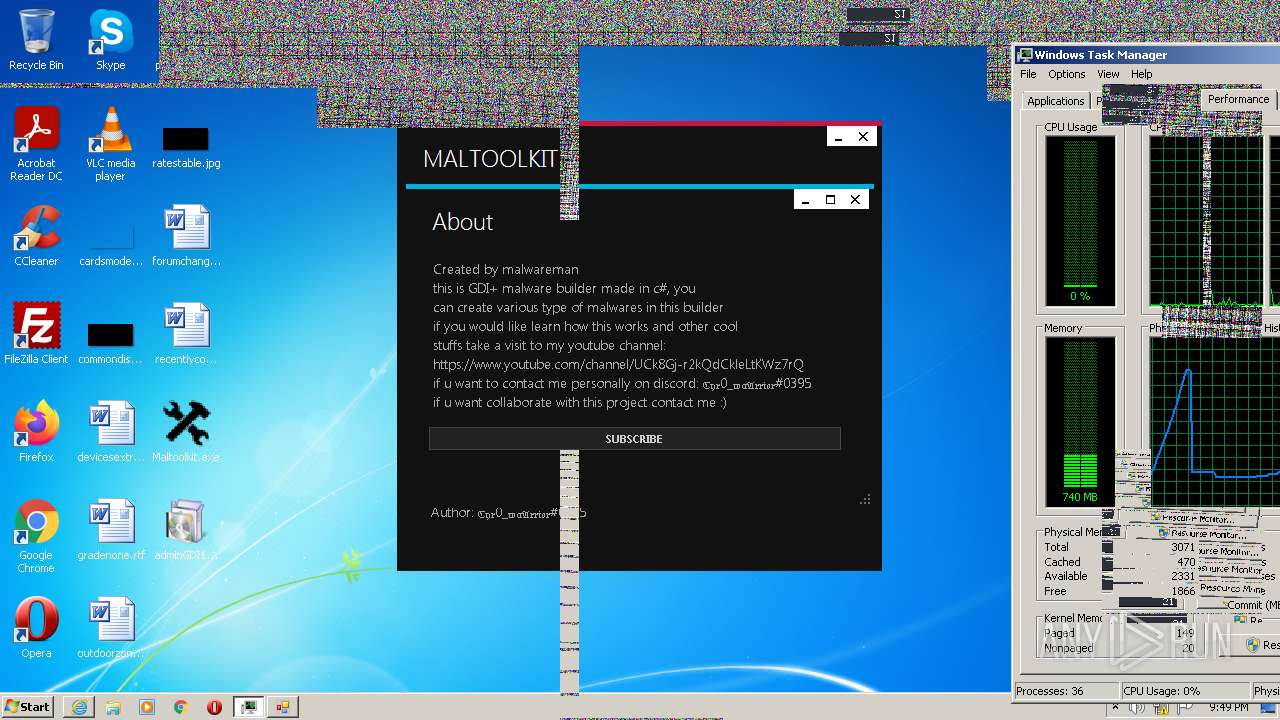
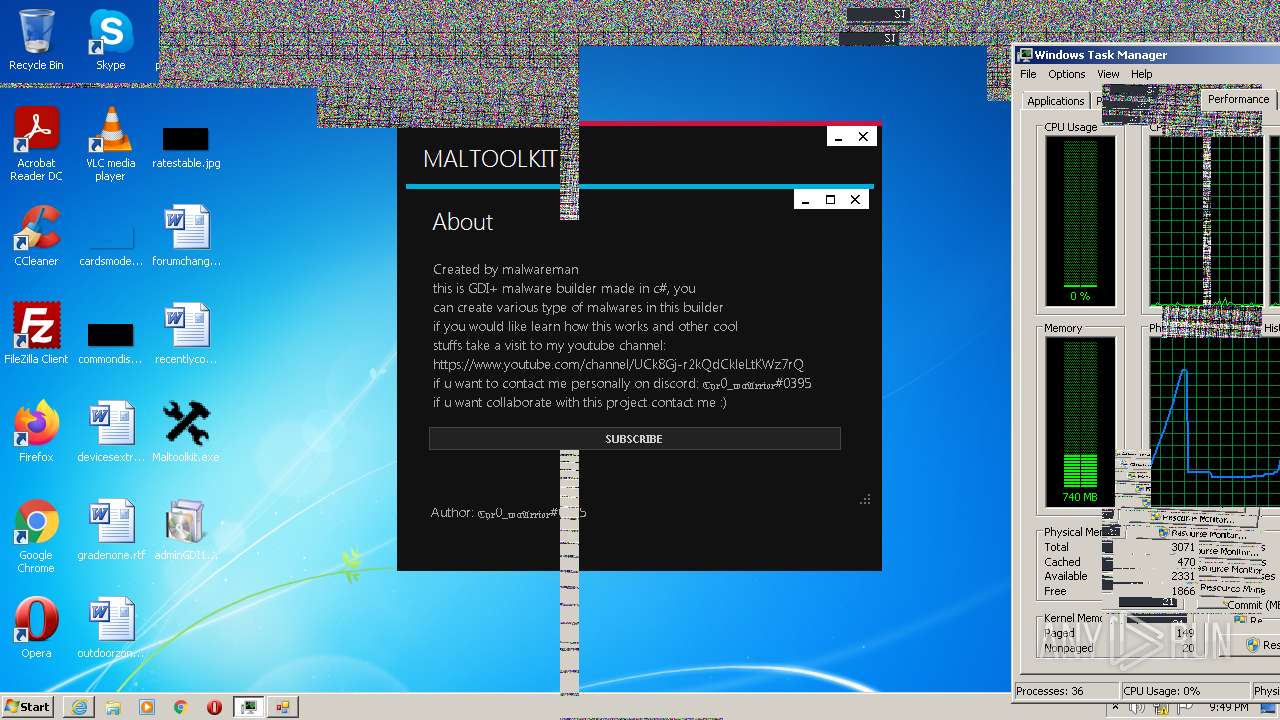
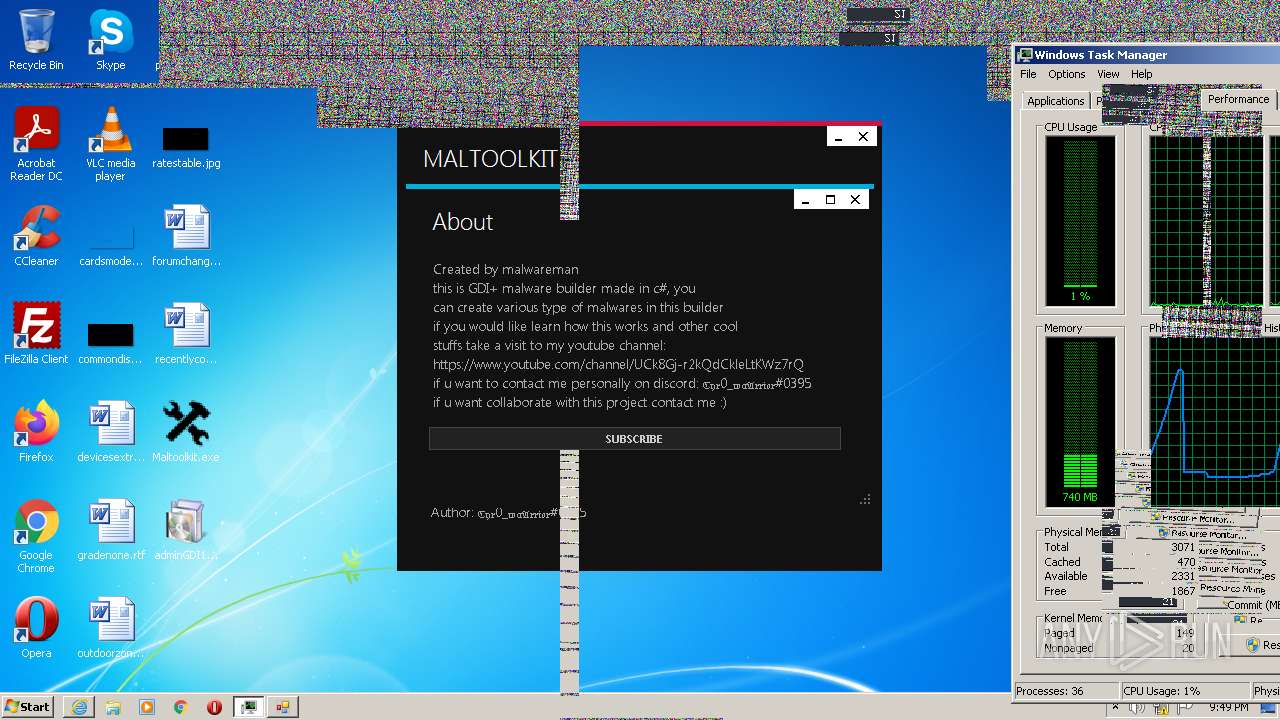
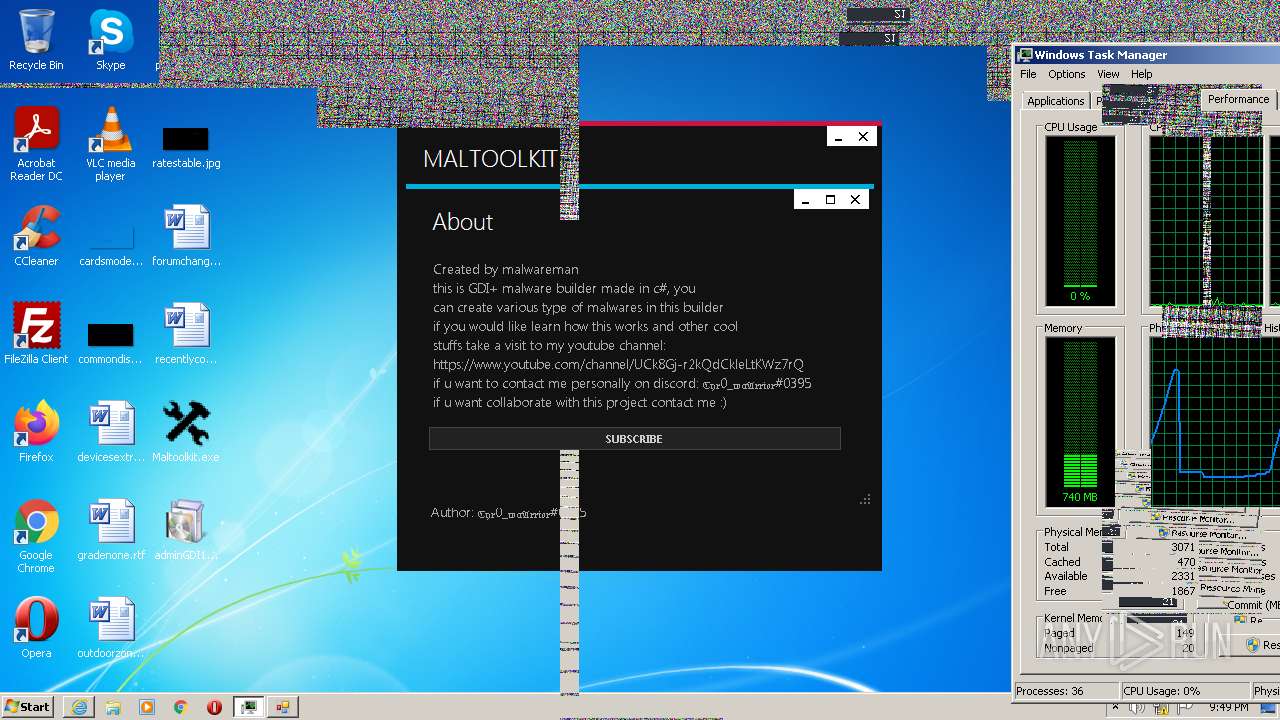
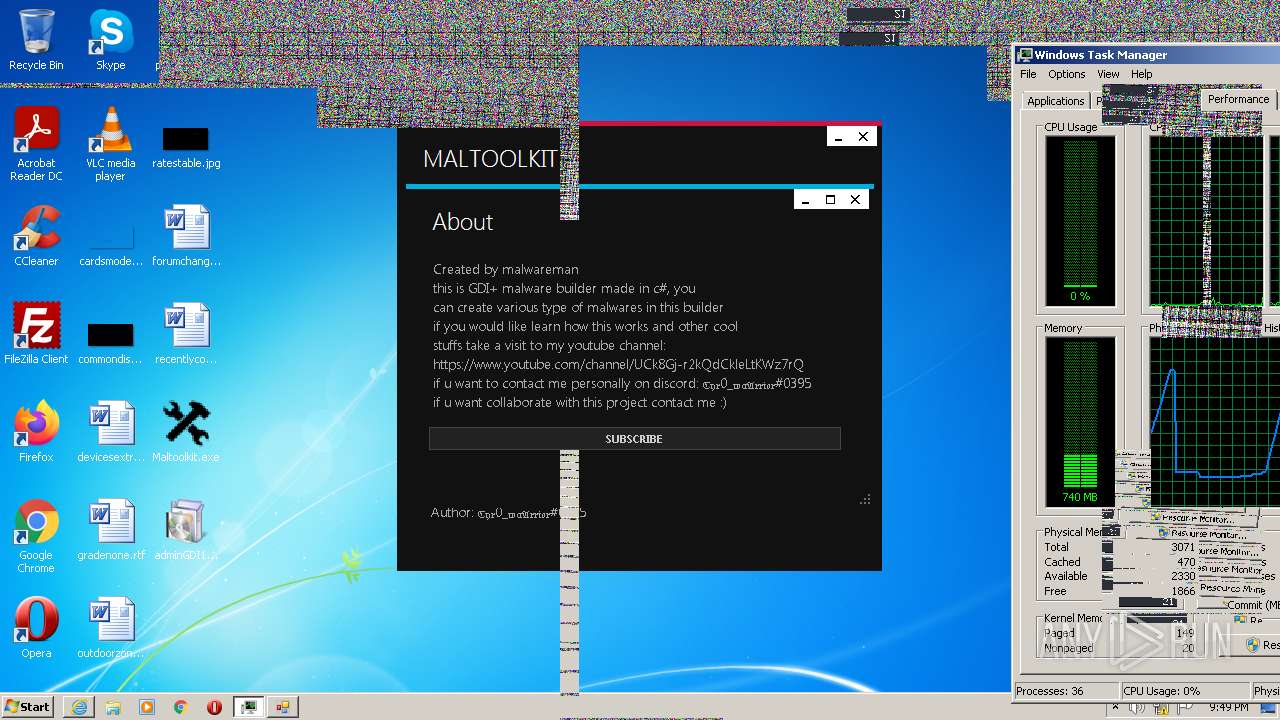
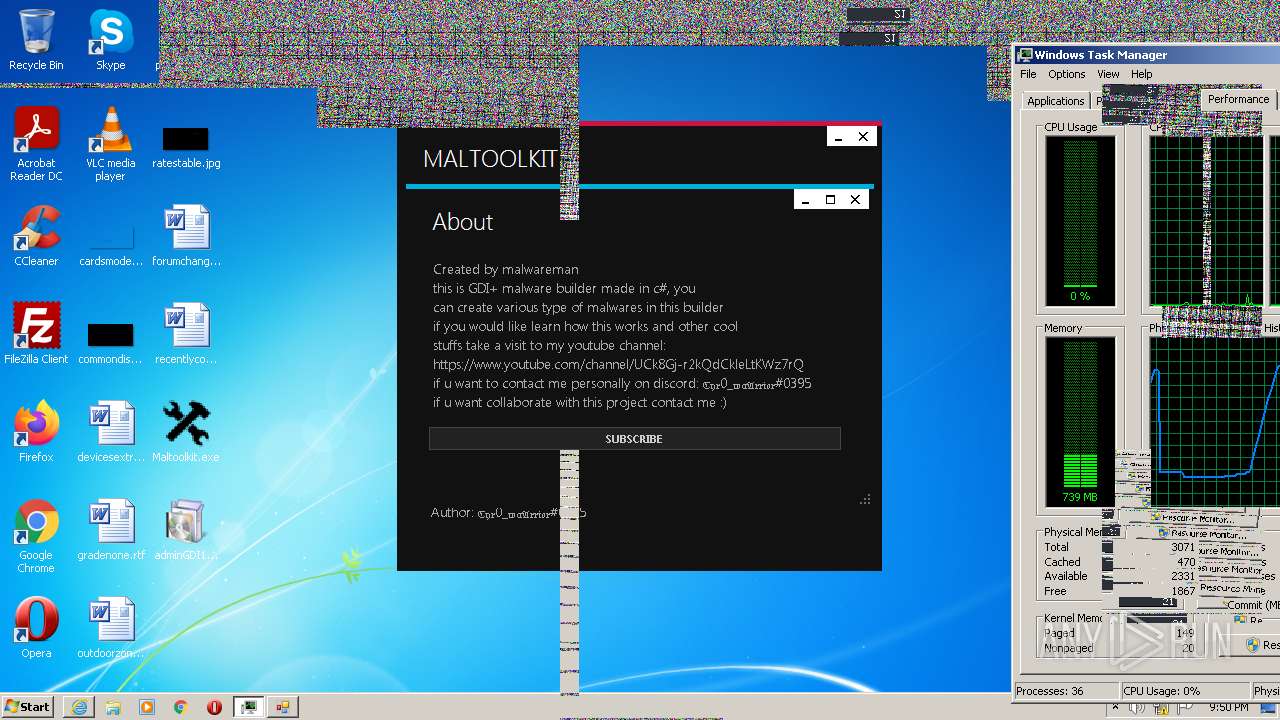
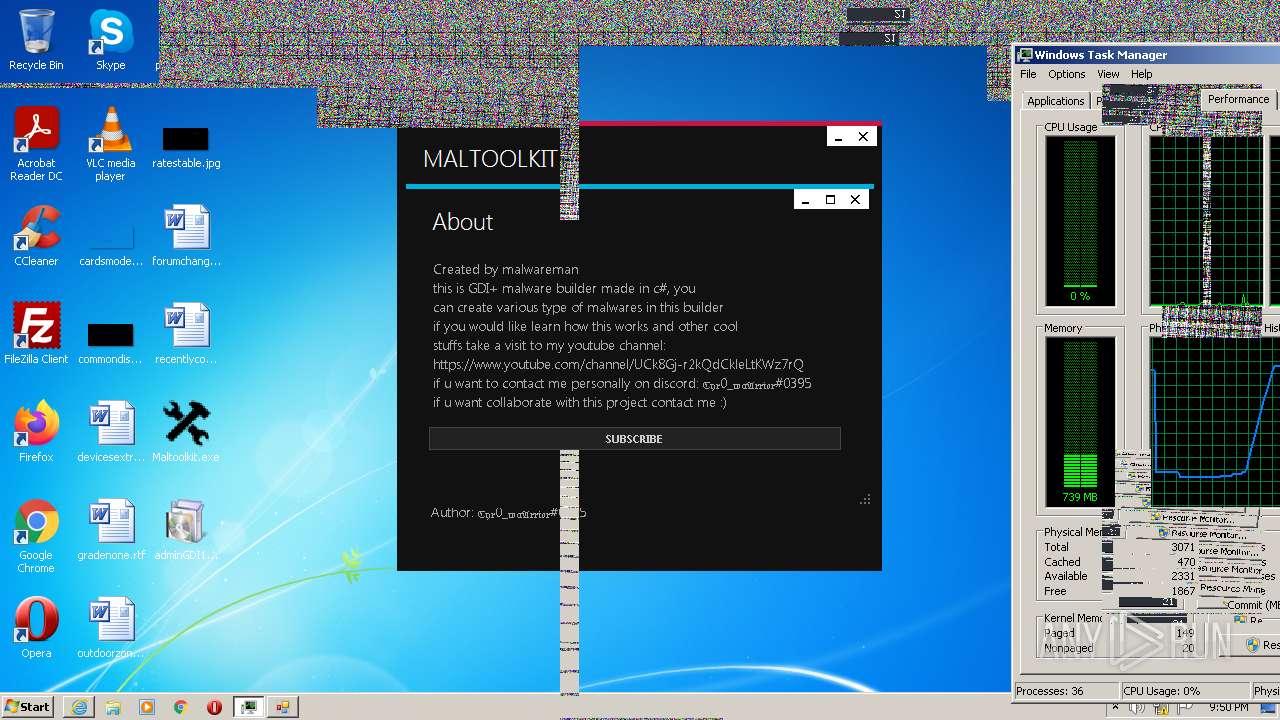
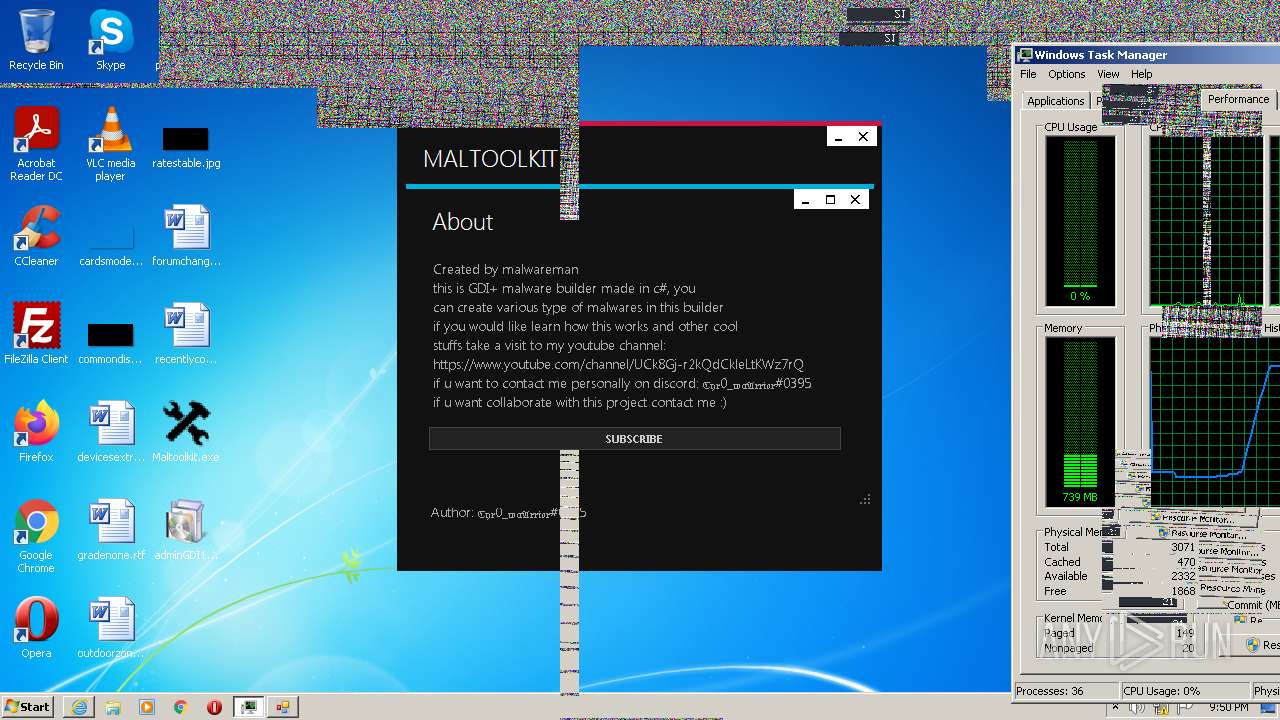
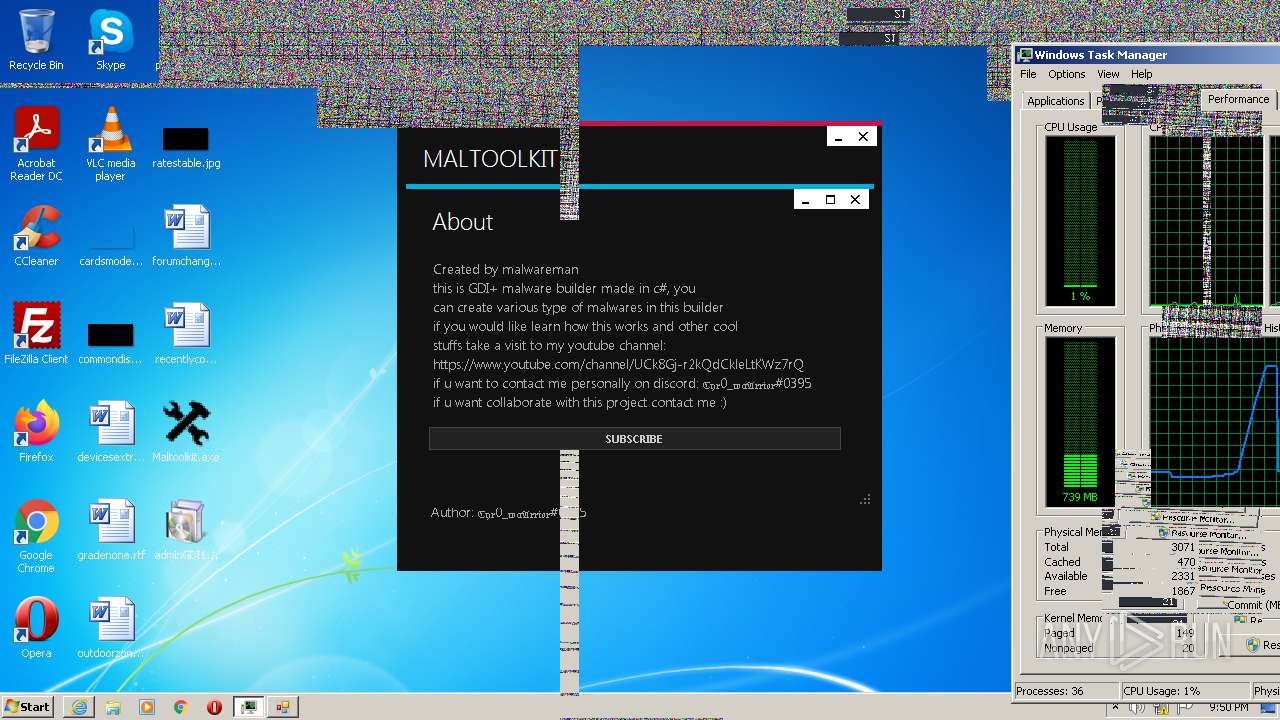
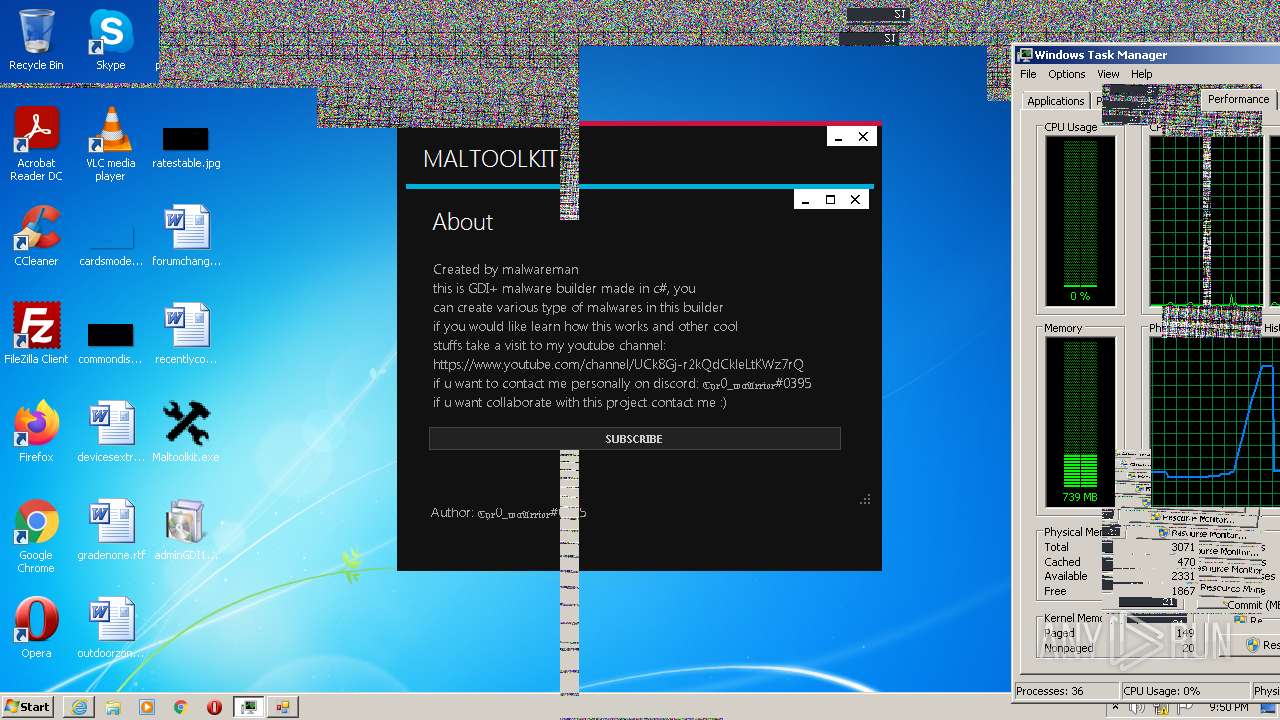
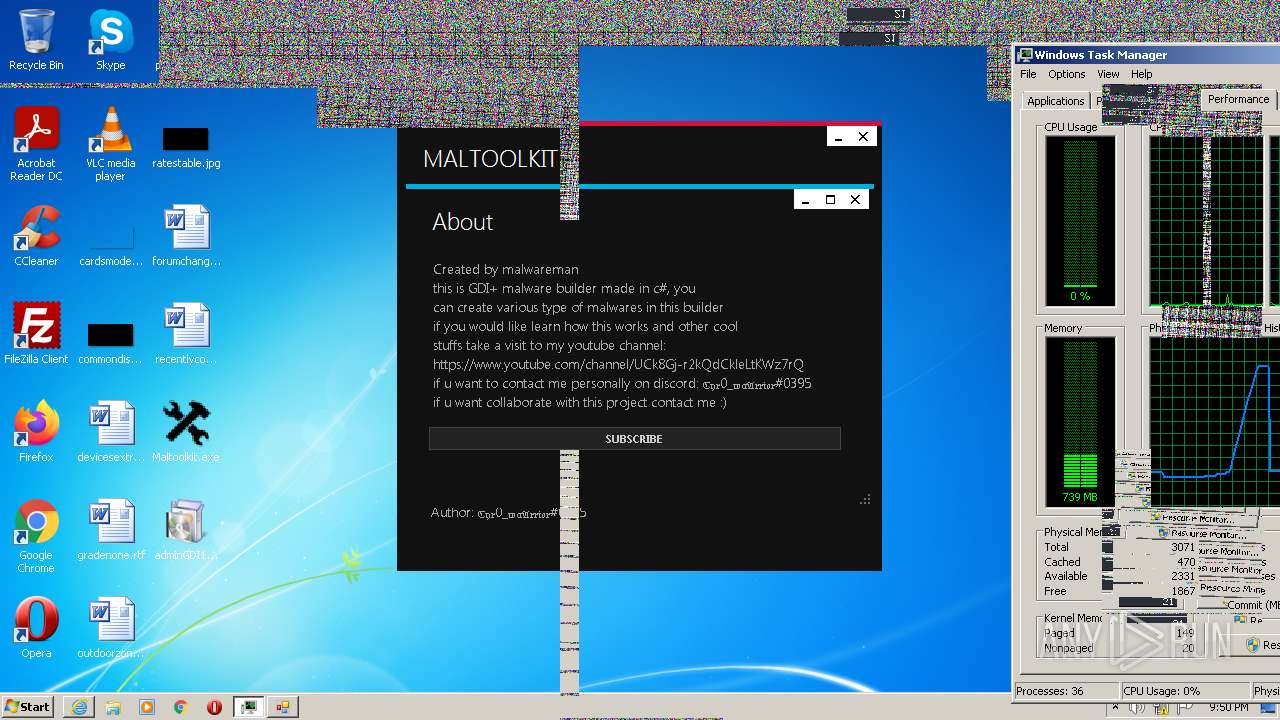
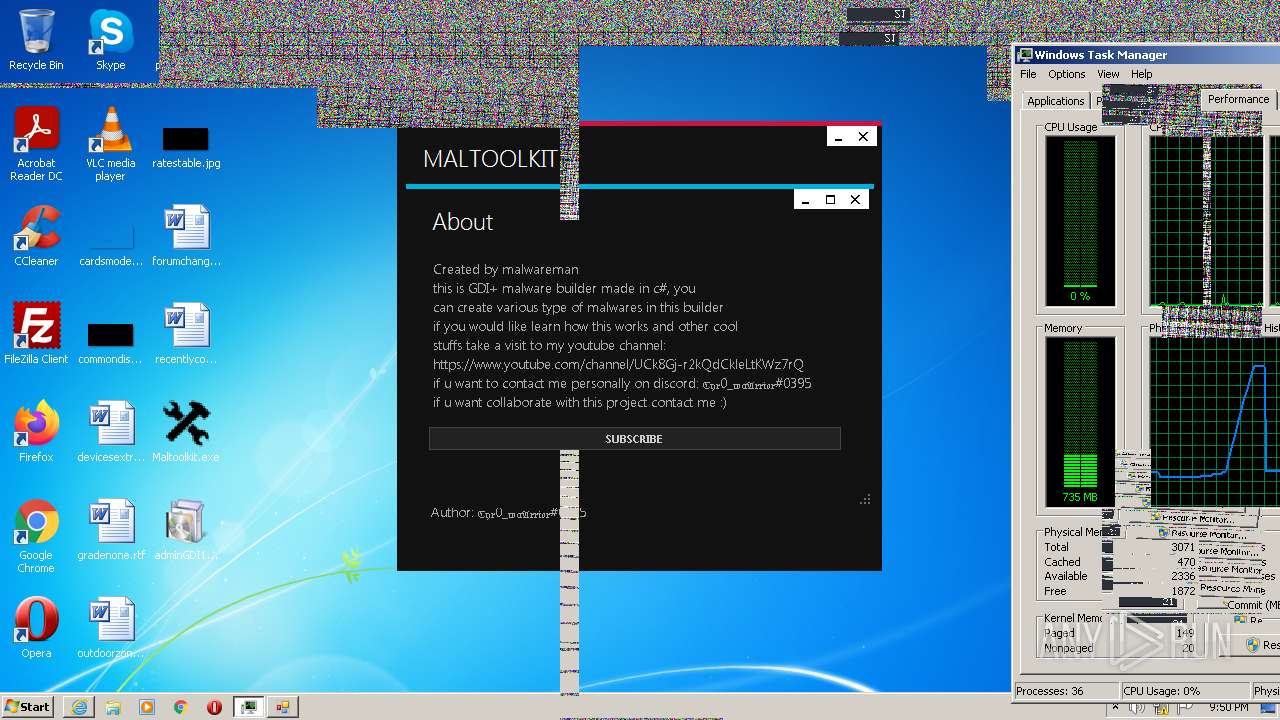
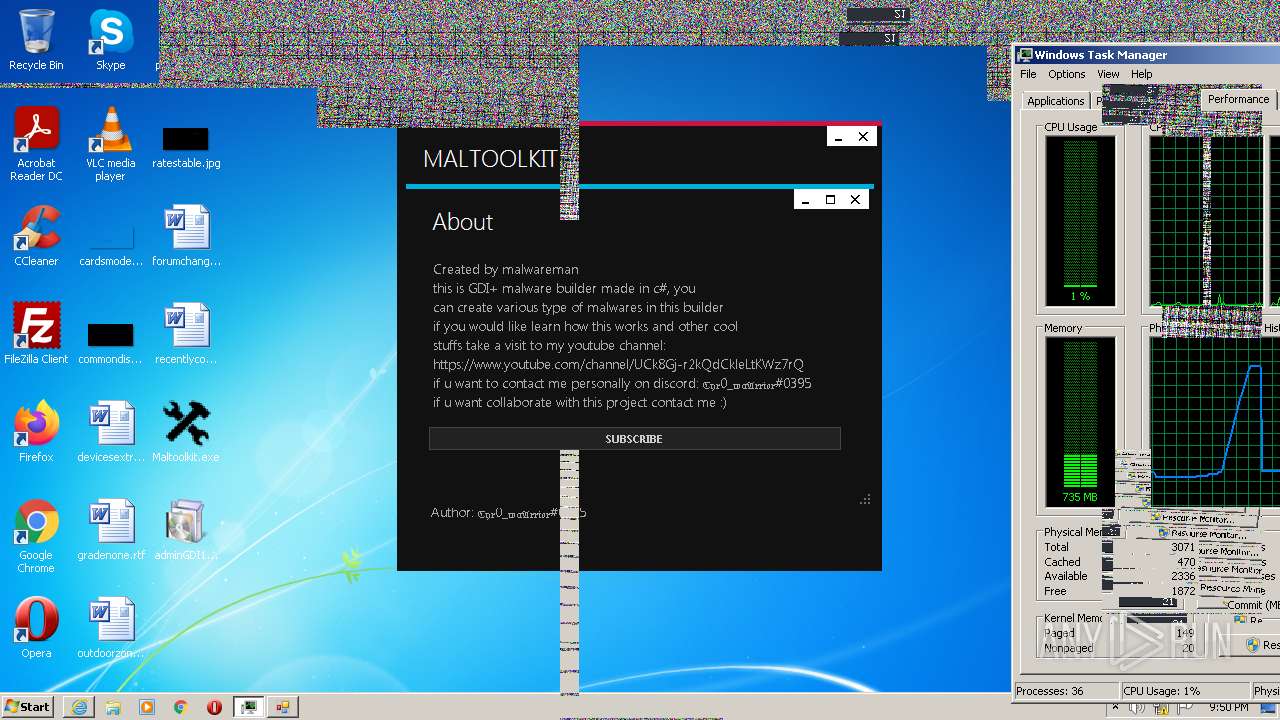
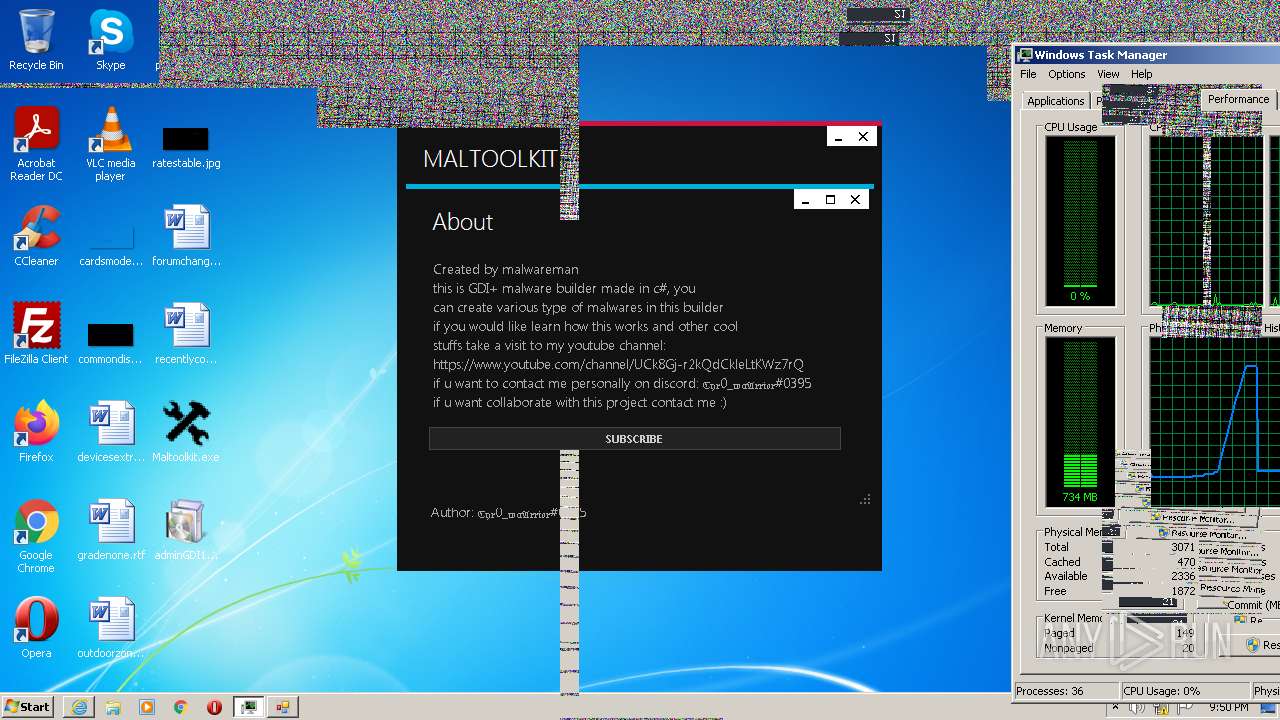
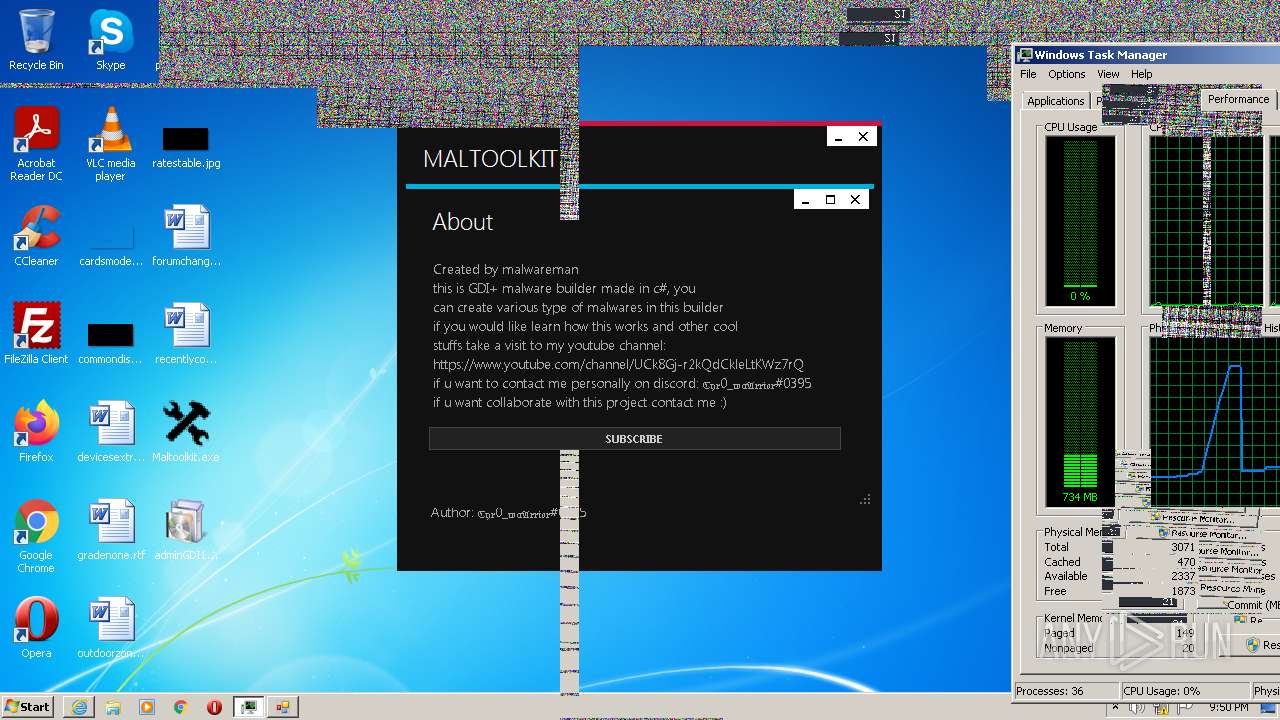
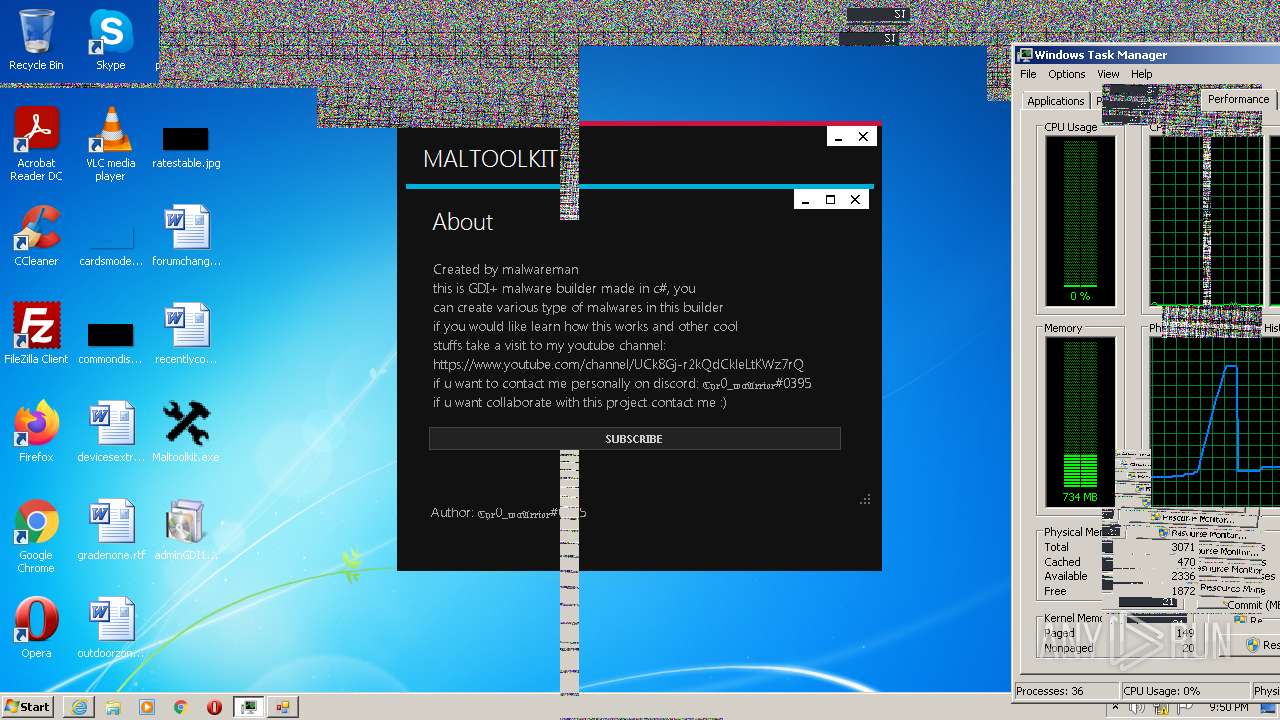
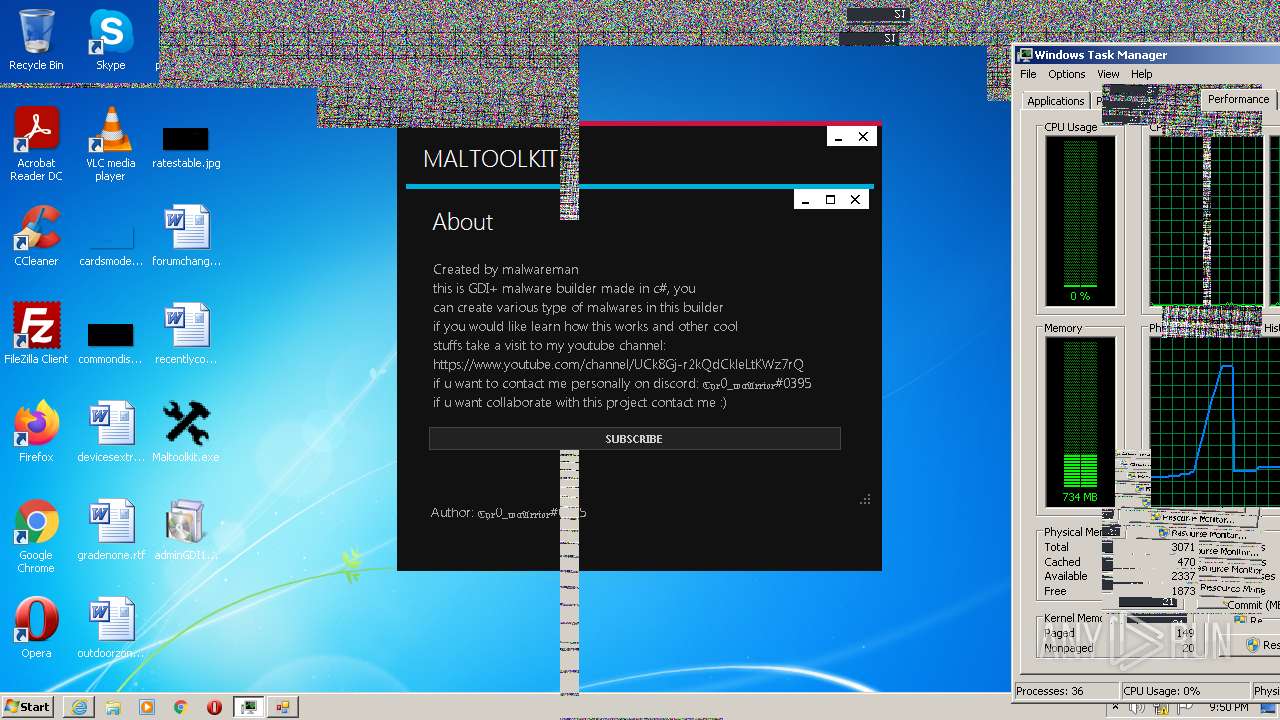
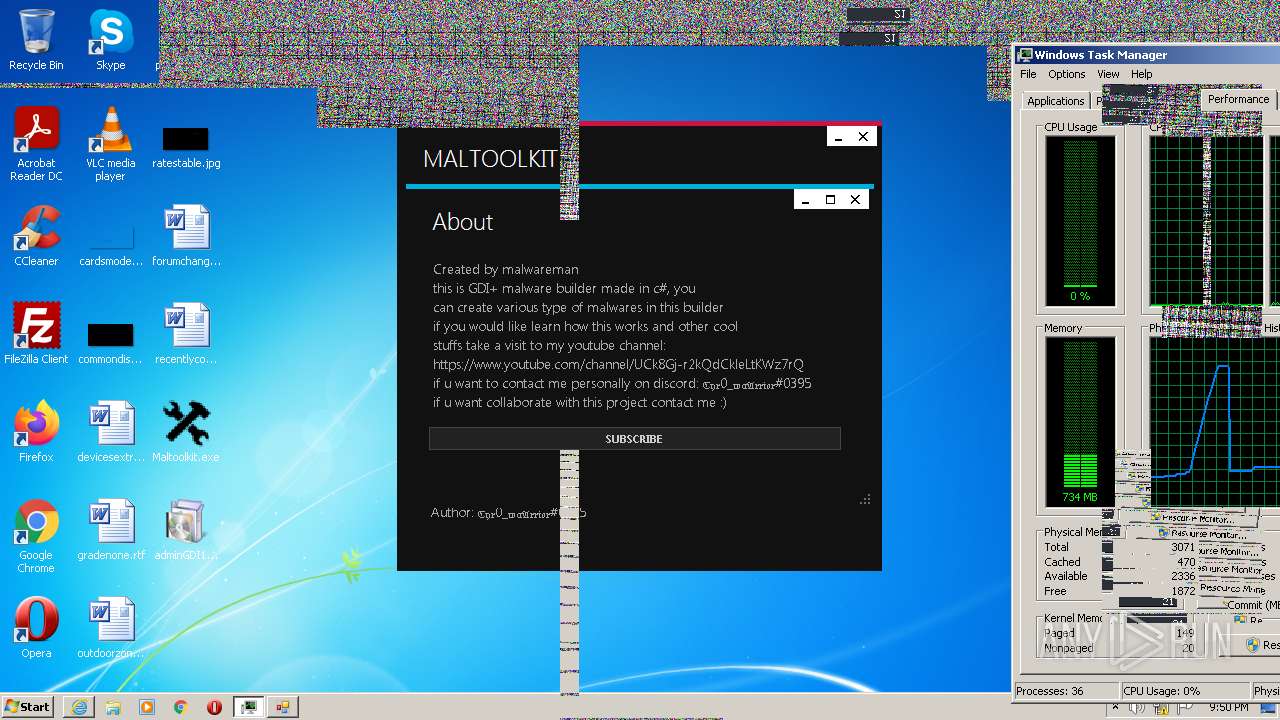
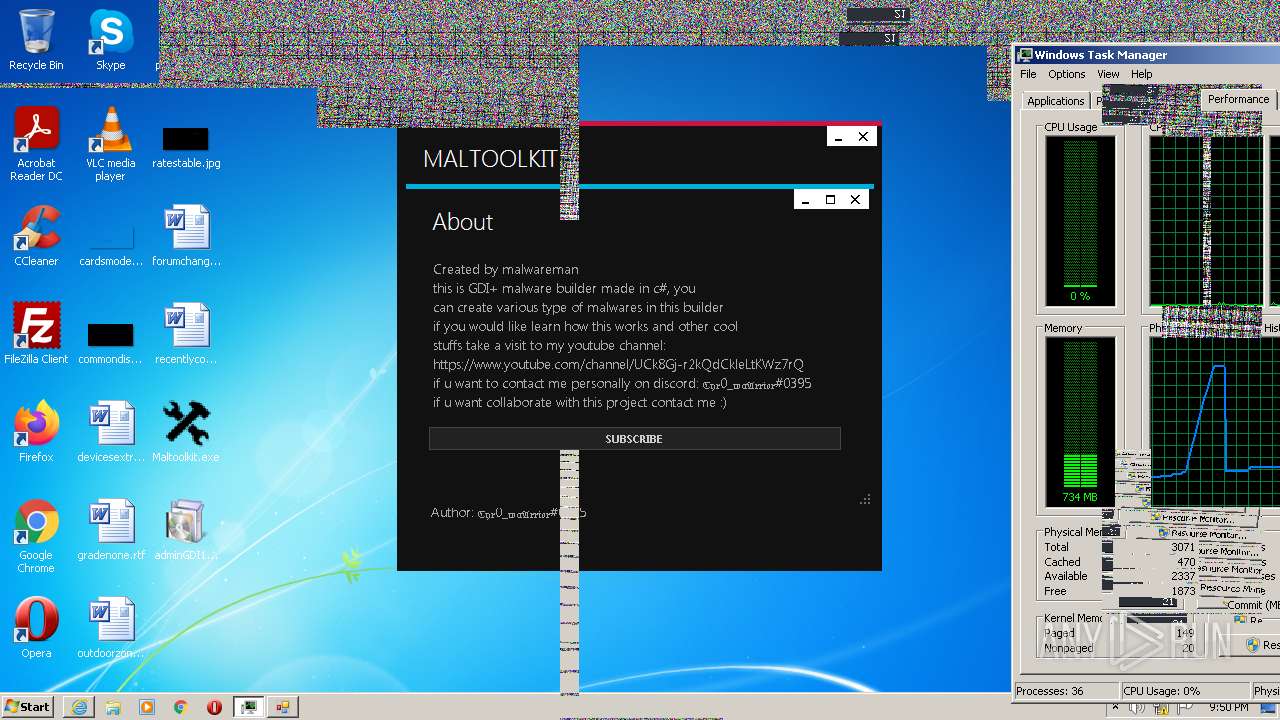
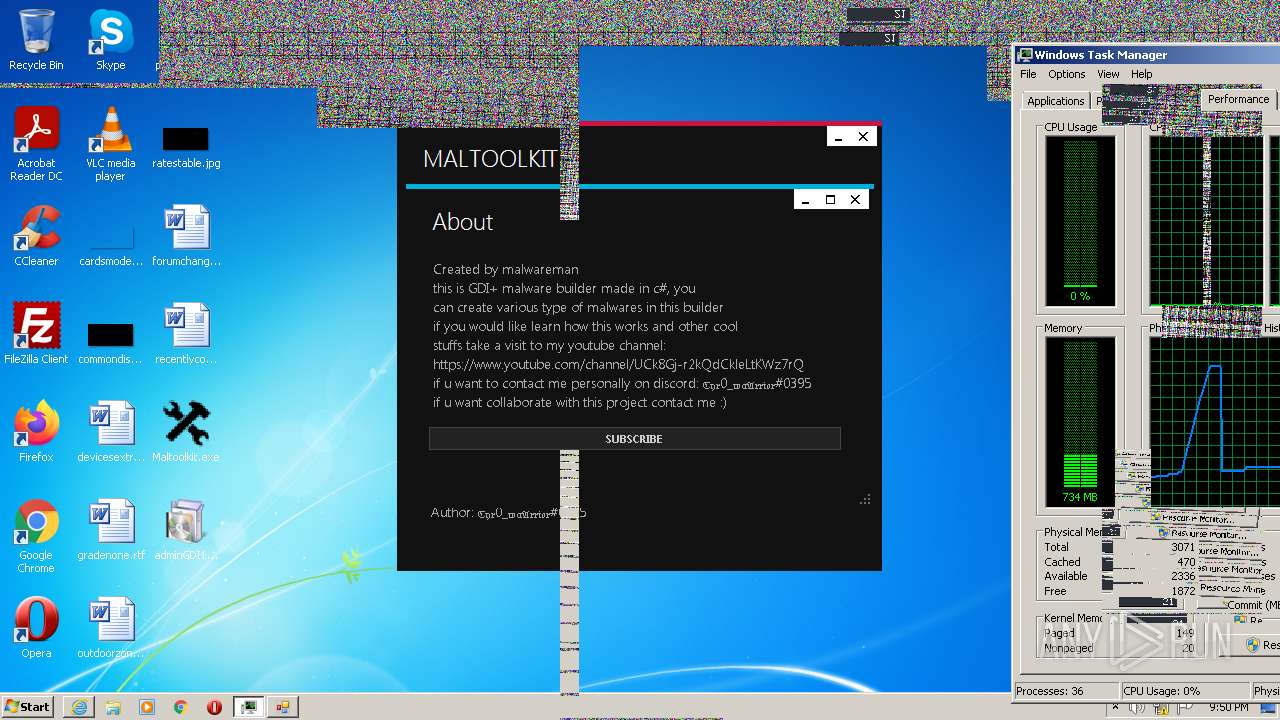
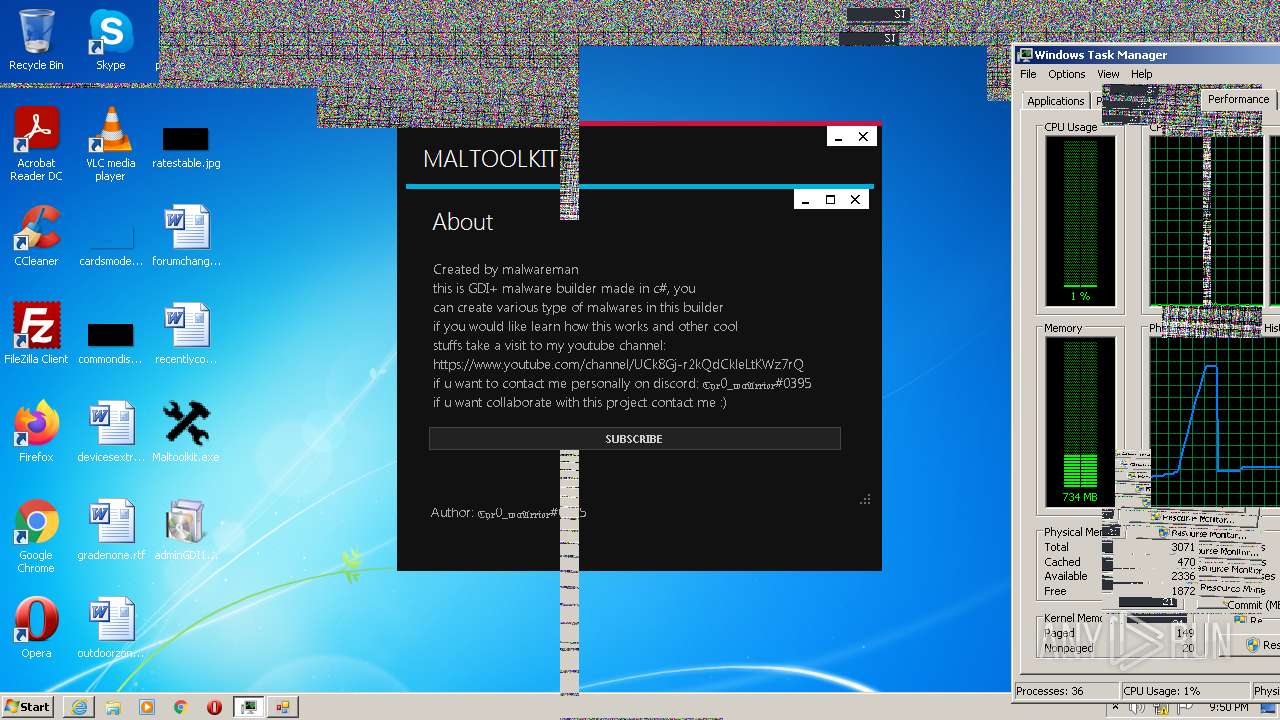
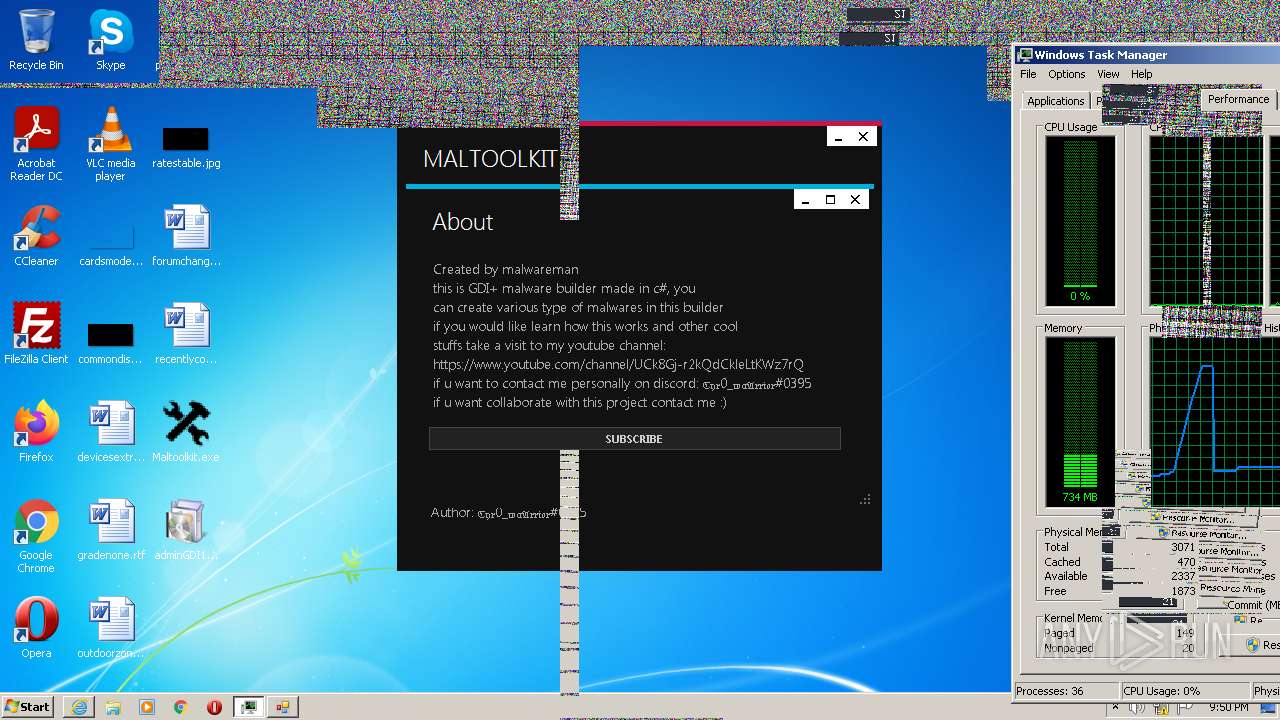
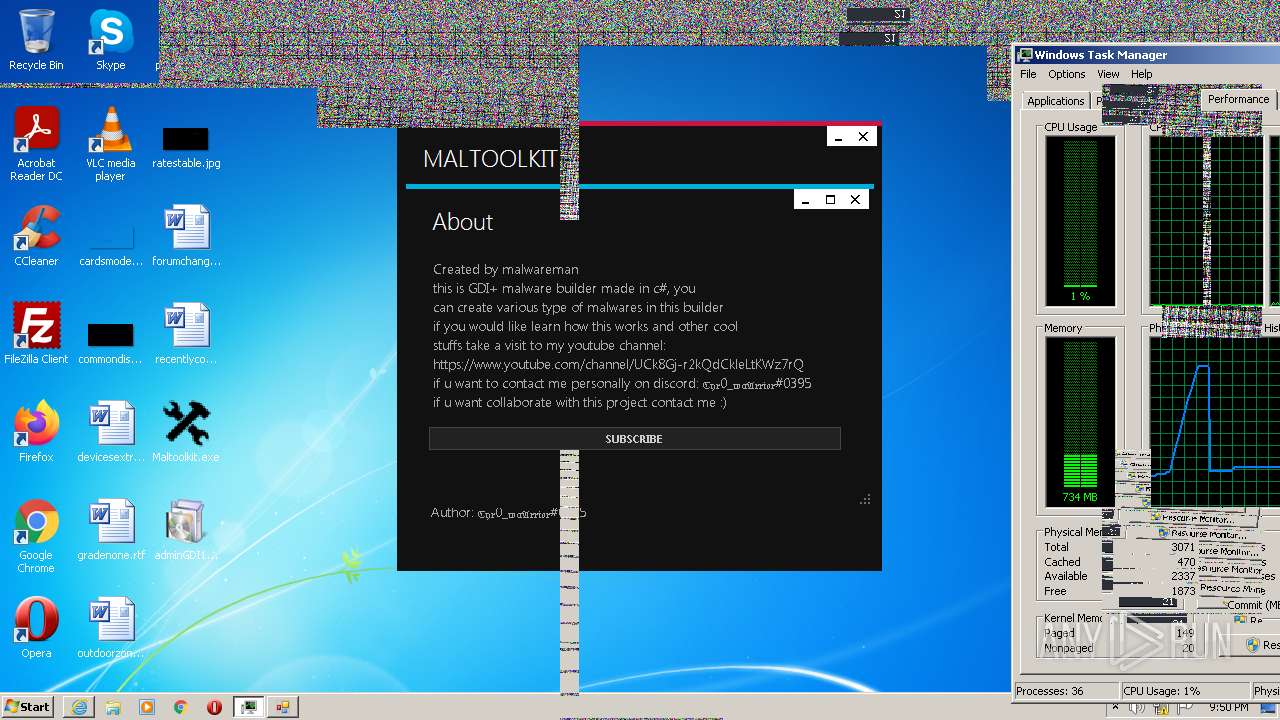
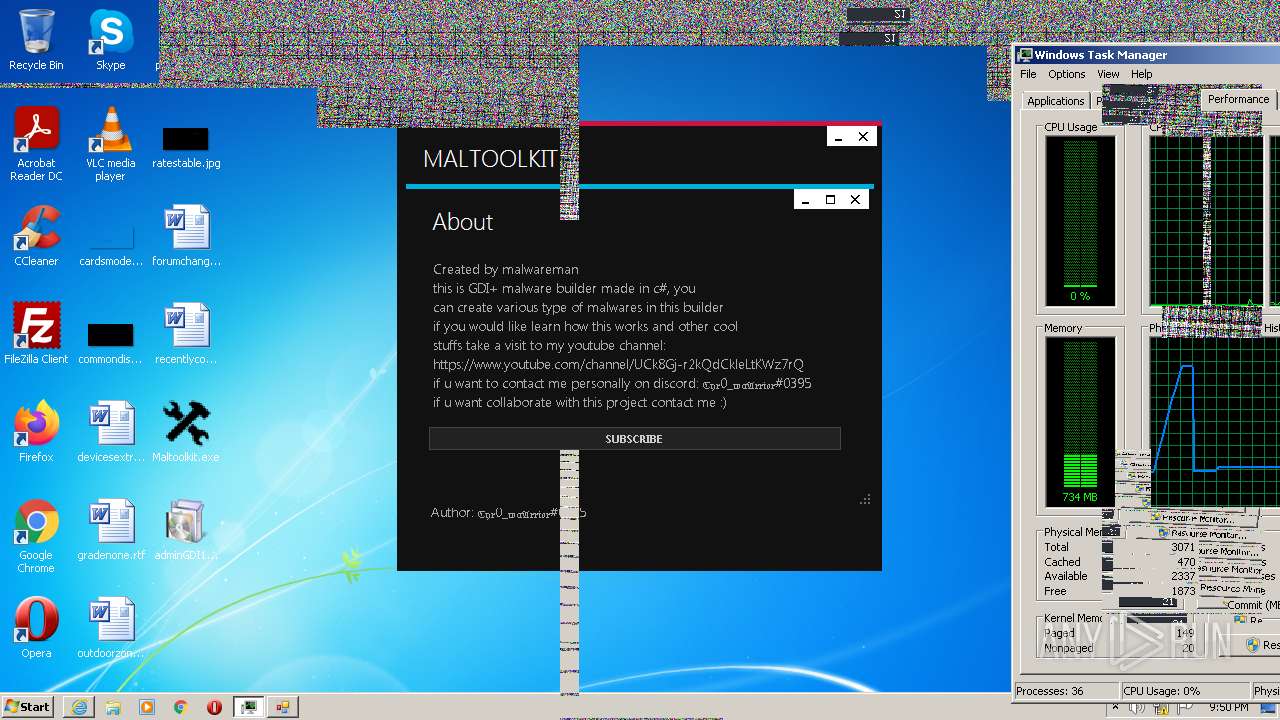
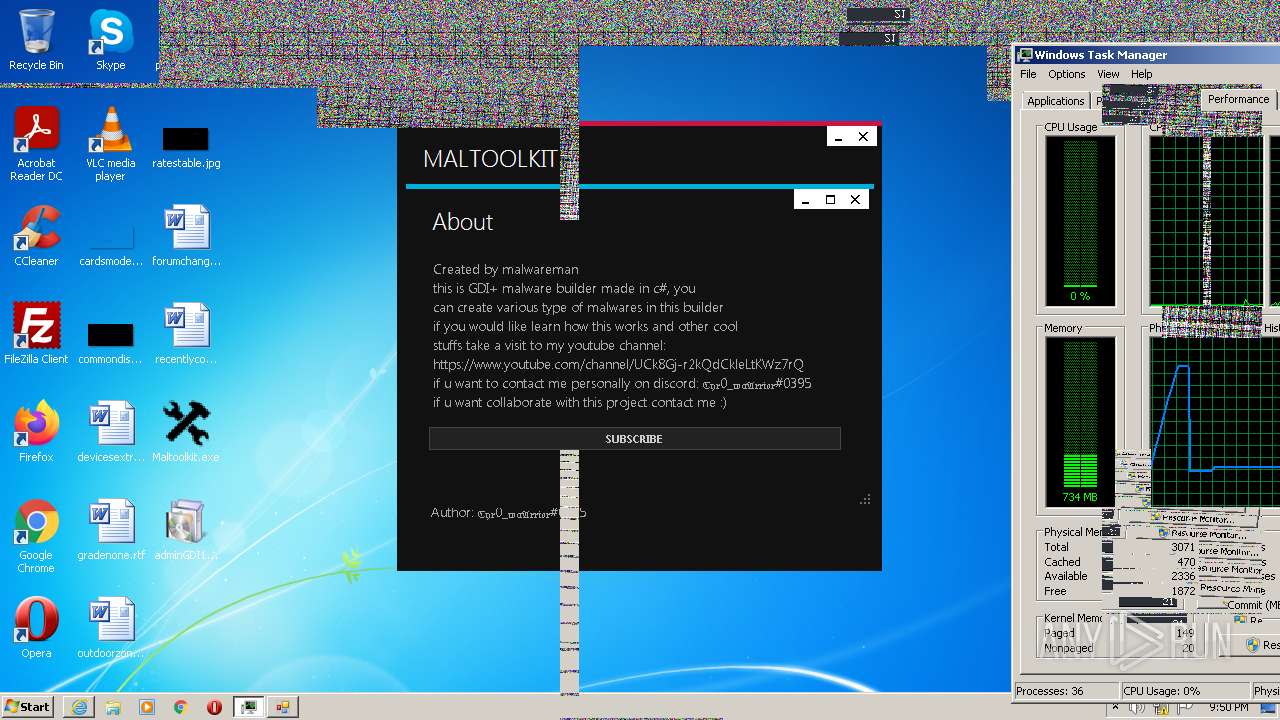
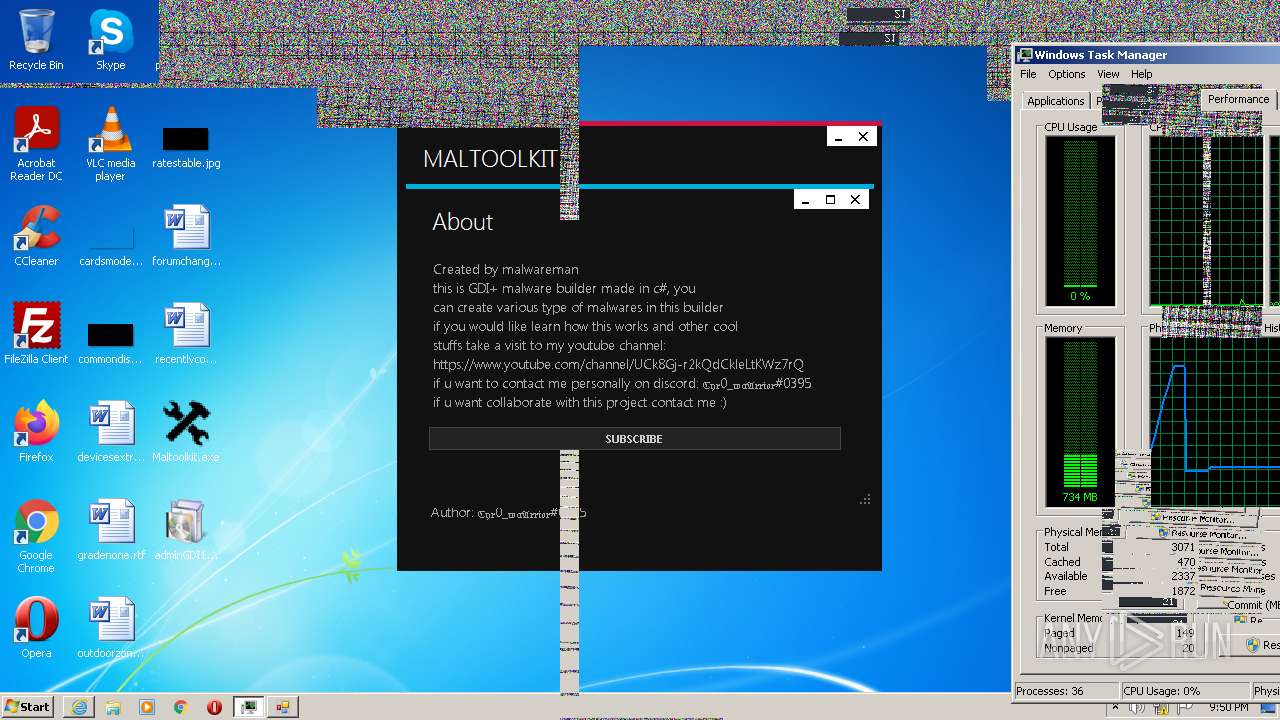
| File name: | Maltoolkit.exe |
| Full analysis: | https://app.any.run/tasks/4253e374-0bda-4f99-9a06-28a69c99135e |
| Verdict: | Malicious activity |
| Analysis date: | June 17, 2023, 20:46:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | D4163D85BA71A09B181DEA459744698C |
| SHA1: | 002EFBDAF3B87A486CD1B577B219A36995A66489 |
| SHA256: | 1FD51D6DD83F903B81C2FE5EE5811A32F4EEDDAE97B02C89659E6F0E7DA16B1E |
| SSDEEP: | 12288:FkJiiL9fPbGXY3ZuTmlOIq76xb35zdtKTKKpKKM:Fk0iL97ngEMWx35 |
MALICIOUS
Application was dropped or rewritten from another process
- adminGDI169.exe.exe (PID: 2532)
- adminGDI169.exe.exe (PID: 2384)
SUSPICIOUS
Starts CMD.EXE for commands execution
- Maltoolkit.exe (PID: 2732)
- adminGDI169.exe.exe (PID: 2532)
- adminGDI169.exe.exe (PID: 2384)
Executable content was dropped or overwritten
- iexpress.exe (PID: 3416)
- adminGDI169.exe.exe (PID: 2532)
- adminGDI169.exe.exe (PID: 2384)
Reads the Internet Settings
- Maltoolkit.exe (PID: 3824)
INFO
Checks supported languages
- Maltoolkit.exe (PID: 2732)
- adminGDI169.exe.exe (PID: 2532)
- Maltoolkit.exe (PID: 2804)
- Maltoolkit.exe (PID: 3824)
- adminGDI169.exe.exe (PID: 2384)
- Maltoolkit.exe (PID: 2448)
Reads the computer name
- Maltoolkit.exe (PID: 2732)
- Maltoolkit.exe (PID: 2804)
- Maltoolkit.exe (PID: 3824)
- Maltoolkit.exe (PID: 2448)
Reads the machine GUID from the registry
- Maltoolkit.exe (PID: 2732)
- Maltoolkit.exe (PID: 2804)
- Maltoolkit.exe (PID: 3824)
- Maltoolkit.exe (PID: 2448)
Create files in a temporary directory
- Maltoolkit.exe (PID: 2732)
- adminGDI169.exe.exe (PID: 2532)
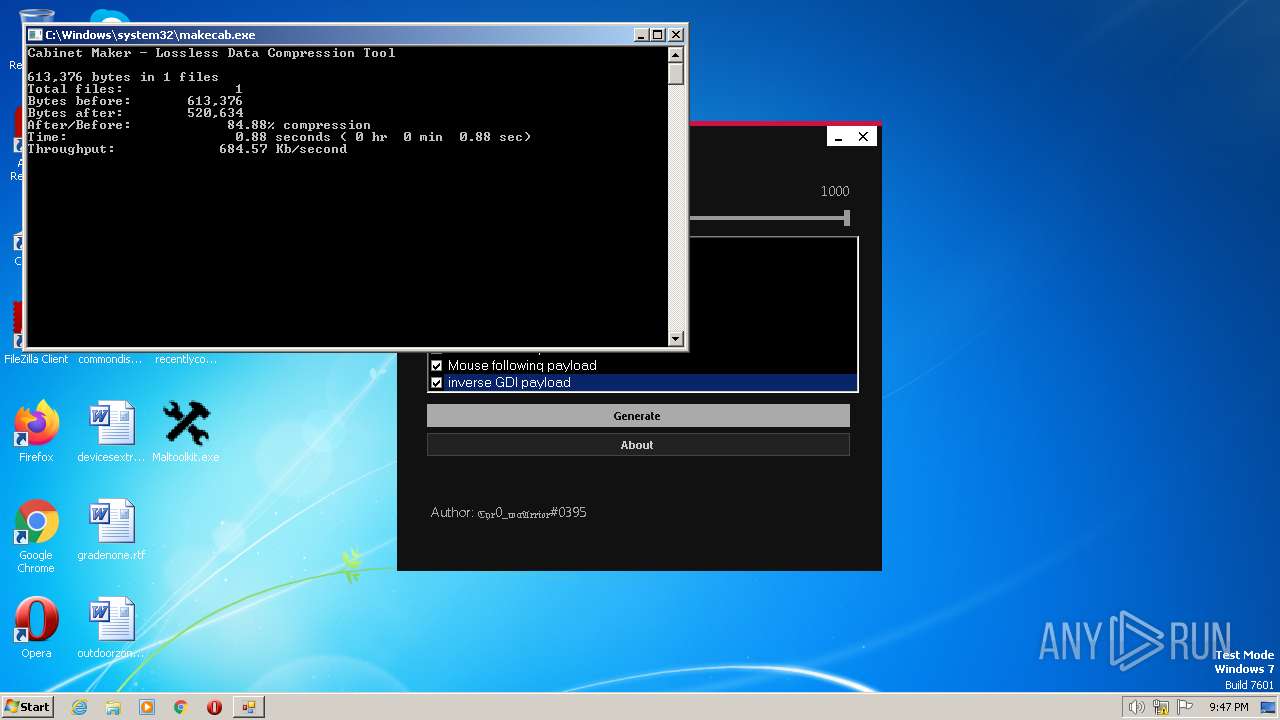
- makecab.exe (PID: 3572)
- adminGDI169.exe.exe (PID: 2384)
Manual execution by a user
- taskmgr.exe (PID: 1432)
- adminGDI169.exe.exe (PID: 2532)
- adminGDI169.exe.exe (PID: 2384)
- Maltoolkit.exe (PID: 3824)
The process checks LSA protection
- Maltoolkit.exe (PID: 2732)
- Maltoolkit.exe (PID: 2804)
- Maltoolkit.exe (PID: 3824)
- Maltoolkit.exe (PID: 2448)
The executable file from the user directory is run by the CMD process
- Maltoolkit.exe (PID: 2804)
- Maltoolkit.exe (PID: 2448)
Application launched itself
- iexplore.exe (PID: 292)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| AssemblyVersion: | 1.0.0.0 |
|---|---|
| ProductVersion: | 1.0.0.0 |
| ProductName: | Maltoolkit |
| OriginalFileName: | Maltoolkit.exe |
| LegalTrademarks: | - |
| LegalCopyright: | Copyright © MALWAREMAN |
| InternalName: | Maltoolkit.exe |
| FileVersion: | 1.0.0.0 |
| FileDescription: | Maltoolkit |
| CompanyName: | MALWAREMAN |
| Comments: | Made by malwareman https://www.youtube.com/channel/UCk8Gj-r2kQdCkleLtKWz7rQ |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.0.0.0 |
| FileVersionNumber: | 1.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x95f1e |
| UninitializedDataSize: | - |
| InitializedDataSize: | 6656 |
| CodeSize: | 606208 |
| LinkerVersion: | 48 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| TimeStamp: | 2046:11:16 21:21:40+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 16-Nov-2046 21:21:40 |
| Debug artifacts: |
|
| Comments: | Made by malwareman https://www.youtube.com/channel/UCk8Gj-r2kQdCkleLtKWz7rQ |
| CompanyName: | MALWAREMAN |
| FileDescription: | Maltoolkit |
| FileVersion: | 1.0.0.0 |
| InternalName: | Maltoolkit.exe |
| LegalCopyright: | Copyright © MALWAREMAN |
| LegalTrademarks: | - |
| OriginalFilename: | Maltoolkit.exe |
| ProductName: | Maltoolkit |
| ProductVersion: | 1.0.0.0 |
| Assembly Version: | 1.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 16-Nov-2046 21:21:40 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00093F24 | 0x00094000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.97834 |
.rsrc | 0x00096000 | 0x0000173C | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.15768 |
.reloc | 0x00098000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
32512 | 1.91924 | 20 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
59
Monitored processes
14
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
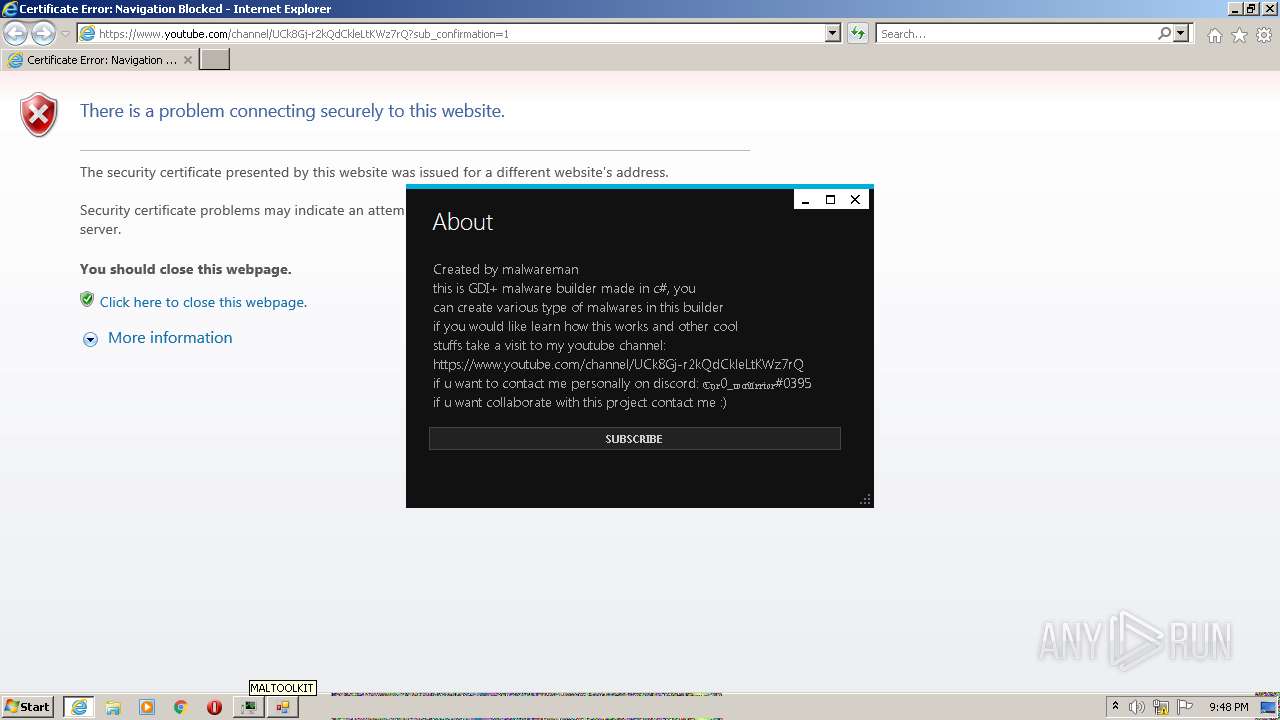
| 292 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.youtube.com/channel/UCk8Gj-r2kQdCkleLtKWz7rQ?sub_confirmation=1 | C:\Program Files\Internet Explorer\iexplore.exe | Maltoolkit.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
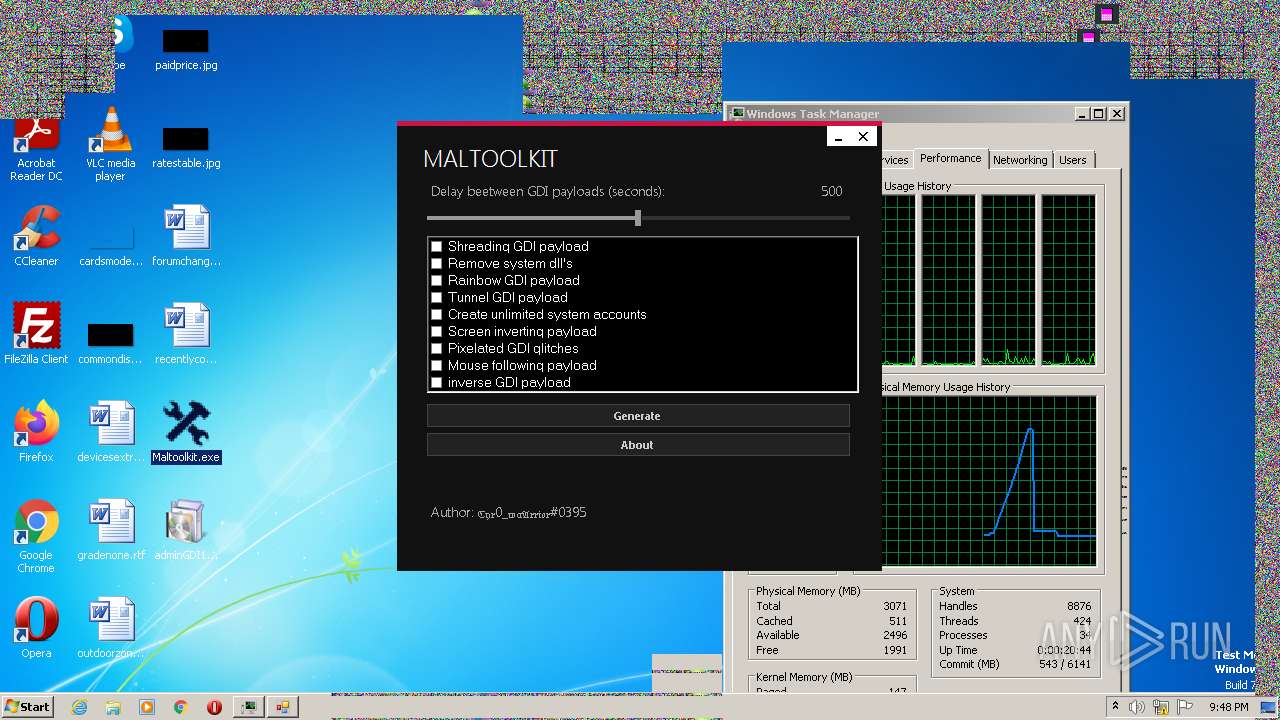
| 596 | cmd /c Maltoolkit.exe --shreadinggdipayloadremovesystemdll'stunnelgdipayloadcreateunlimitedsystemaccountsscreeninvertingpayloadpixelatedgdiglitchesmousefollowingpayloadinversegdipayload1000 | C:\Windows\System32\cmd.exe | — | adminGDI169.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3762504530 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1432 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2384 | "C:\Users\admin\Desktop\adminGDI169.exe.exe" | C:\Users\admin\Desktop\adminGDI169.exe.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2448 | Maltoolkit.exe --shreadinggdipayloadremovesystemdll'stunnelgdipayloadcreateunlimitedsystemaccountsscreeninvertingpayloadpixelatedgdiglitchesmousefollowingpayloadinversegdipayload1000 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\Maltoolkit.exe | cmd.exe | ||||||||||||
User: admin Company: MALWAREMAN Integrity Level: MEDIUM Description: Maltoolkit Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2532 | "C:\Users\admin\Desktop\adminGDI169.exe.exe" | C:\Users\admin\Desktop\adminGDI169.exe.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2732 | "C:\Users\admin\Desktop\Maltoolkit.exe" | C:\Users\admin\Desktop\Maltoolkit.exe | — | explorer.exe | |||||||||||
User: admin Company: MALWAREMAN Integrity Level: MEDIUM Description: Maltoolkit Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2804 | Maltoolkit.exe --shreadinggdipayloadremovesystemdll'stunnelgdipayloadcreateunlimitedsystemaccountsscreeninvertingpayloadpixelatedgdiglitchesmousefollowingpayloadinversegdipayload1000 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\Maltoolkit.exe | cmd.exe | ||||||||||||
User: admin Company: MALWAREMAN Integrity Level: MEDIUM Description: Maltoolkit Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2908 | cmd /c Maltoolkit.exe --shreadinggdipayloadremovesystemdll'stunnelgdipayloadcreateunlimitedsystemaccountsscreeninvertingpayloadpixelatedgdiglitchesmousefollowingpayloadinversegdipayload1000 | C:\Windows\System32\cmd.exe | — | adminGDI169.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3762504530 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2996 | "cmd.exe" | C:\Windows\System32\cmd.exe | — | Maltoolkit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
15 411
Read events
15 344
Write events
67
Delete events
0
Modification events
| (PID) Process: | (292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
5
Suspicious files
9
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2732 | Maltoolkit.exe | C:\Users\admin\AppData\Local\Temp\optionfile.SED | binary | |
MD5:24DCE8A55BA8CB3D98860EB155F0E3A8 | SHA256:89DDDBADF2A3C8FD39B65C18F37ED32469BC4BC1D9D65A9818059BE2F011DE03 | |||
| 3572 | makecab.exe | C:\Users\admin\AppData\Local\Temp\cab_3572_6 | binary | |
MD5:DDA1C310C86AC5428D44130A96E53BCA | SHA256:FB0E2BC7F199515BA130C707693D8C2570554076C3F0D844AFA6C66539836D03 | |||
| 3416 | iexpress.exe | C:\Users\admin\Desktop\~adminGDI169.exe.DDF | binary | |
MD5:E47F3A2CC48ECA297B04DB3474F3BC0C | SHA256:C3E817B746CF0BDD516945A96C8BBB8B4C993F125FF30A74B1BECB18AFB1B4EA | |||
| 3572 | makecab.exe | C:\Users\admin\AppData\Local\Temp\inf_3572_2 | text | |
MD5:CB492B7DF9B5C170D7C87527940EFF3B | SHA256:DBA5166AD9DB9BA648C1032EBBD34DCD0D085B50023B839EF5C68CA1DB93A563 | |||
| 2732 | Maltoolkit.exe | C:\Windows\Temp\data.tmp | text | |
MD5:B871481EB1A9B7C41FC2BFB0D7AE527B | SHA256:25B1AD3FAA6CAE40F52B10CA23039C1F5CFC59268F859DAC518061047DFD00BE | |||
| 3572 | makecab.exe | C:\Users\admin\AppData\Local\Temp\cab_3572_8 | binary | |
MD5:DDA1C310C86AC5428D44130A96E53BCA | SHA256:FB0E2BC7F199515BA130C707693D8C2570554076C3F0D844AFA6C66539836D03 | |||
| 3572 | makecab.exe | C:\Users\admin\AppData\Local\Temp\inf_3572_4 | text | |
MD5:5D9466FC3F6A64D5CA6528EF13C9130F | SHA256:1FA0AF78417461F9E70E28694584A0ADBED143084CC5E08634E521CB2B878C21 | |||
| 3572 | makecab.exe | C:\Users\admin\Desktop\~adminGDI169.exe.CAB | compressed | |
MD5:5571C9EADA20AF46F55358CDBE5879E3 | SHA256:F5326A8A8A6ED85A71C5ADE82B75AD41D033DD07F8AA1BD1053359530CBD00BE | |||
| 3572 | makecab.exe | C:\Users\admin\AppData\Local\Temp\inf_3572_3 | text | |
MD5:3CC7909DDDA0CAD2B92E51C82A913AE4 | SHA256:44D7C1AAB0F4DC094D3F501E545372DA3107A4017DDA20CB359056E0A3D77C3D | |||
| 3416 | iexpress.exe | C:\Users\admin\Desktop\RCXFA99.tmp | executable | |
MD5:FFE7CA92A4D4CD9E7B6E63415DDD95F7 | SHA256:A879E1865353F20691D320C6A31639800E057A6A4CEAB79363BC18E8410F8C25 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
23
DNS requests
14
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
292 | iexplore.exe | GET | 404 | 67.27.235.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0bd78179f2c13cfd | US | xml | 341 b | whitelisted |
292 | iexplore.exe | GET | 404 | 67.27.235.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4fc6619cbf5d2bbd | US | xml | 341 b | whitelisted |
292 | iexplore.exe | GET | 404 | 67.27.235.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3cb40fb57f2ef7ff | US | xml | 341 b | whitelisted |
1076 | svchost.exe | GET | 404 | 8.253.95.120:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6937215a1f99fe7a | US | xml | 341 b | whitelisted |
292 | iexplore.exe | GET | 404 | 67.27.235.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4206c1c789c60d12 | US | xml | 341 b | whitelisted |
292 | iexplore.exe | GET | 404 | 67.27.235.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?adab7207e8c873ff | US | xml | 341 b | whitelisted |
3032 | iexplore.exe | GET | 404 | 67.27.235.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?12350f424d98b979 | US | xml | 341 b | whitelisted |
3032 | iexplore.exe | GET | 404 | 67.27.235.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?69473f7d56e03b6c | US | xml | 341 b | whitelisted |
1076 | svchost.exe | GET | 404 | 67.27.235.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a74158113368dad0 | US | xml | 341 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3032 | iexplore.exe | 216.58.212.142:443 | www.youtube.com | GOOGLE | US | whitelisted |
568 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3032 | iexplore.exe | 67.27.235.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
292 | iexplore.exe | 184.86.251.27:443 | www.bing.com | Akamai International B.V. | DE | suspicious |
292 | iexplore.exe | 67.27.235.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
3032 | iexplore.exe | 67.27.235.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
292 | iexplore.exe | 204.79.197.200:443 | ieonline.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.youtube.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
11 ETPRO signatures available at the full report