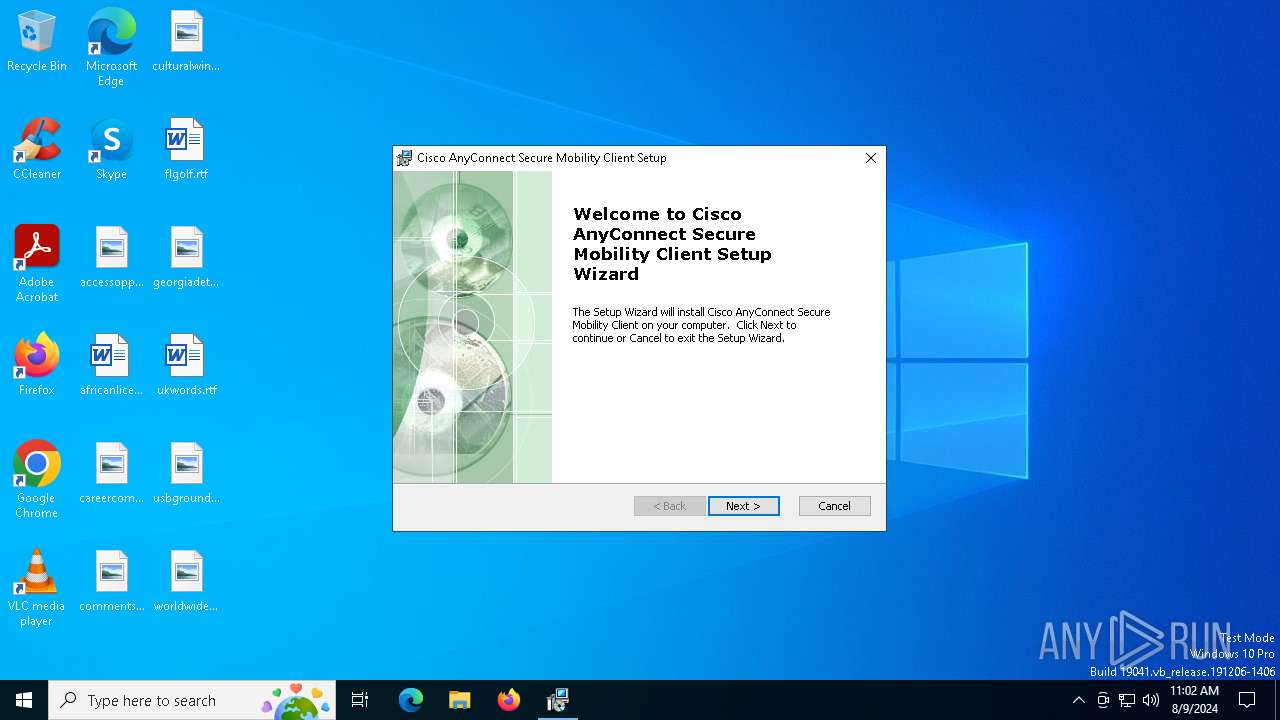
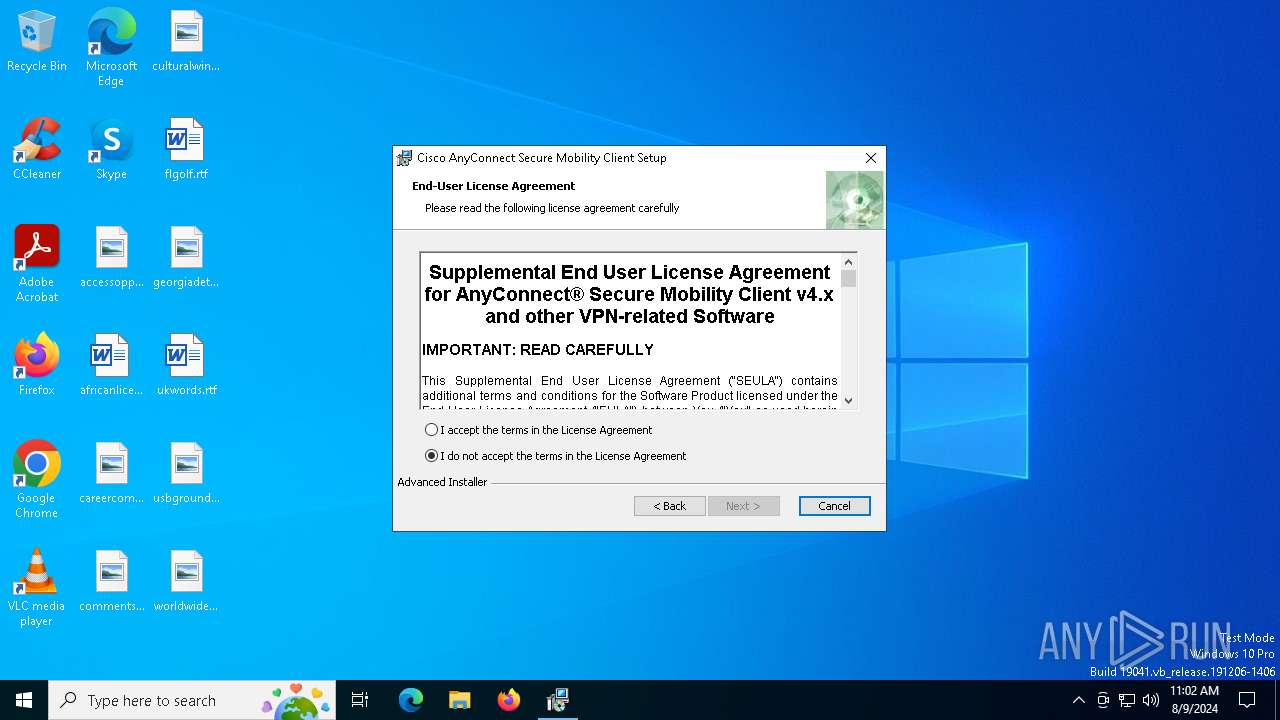
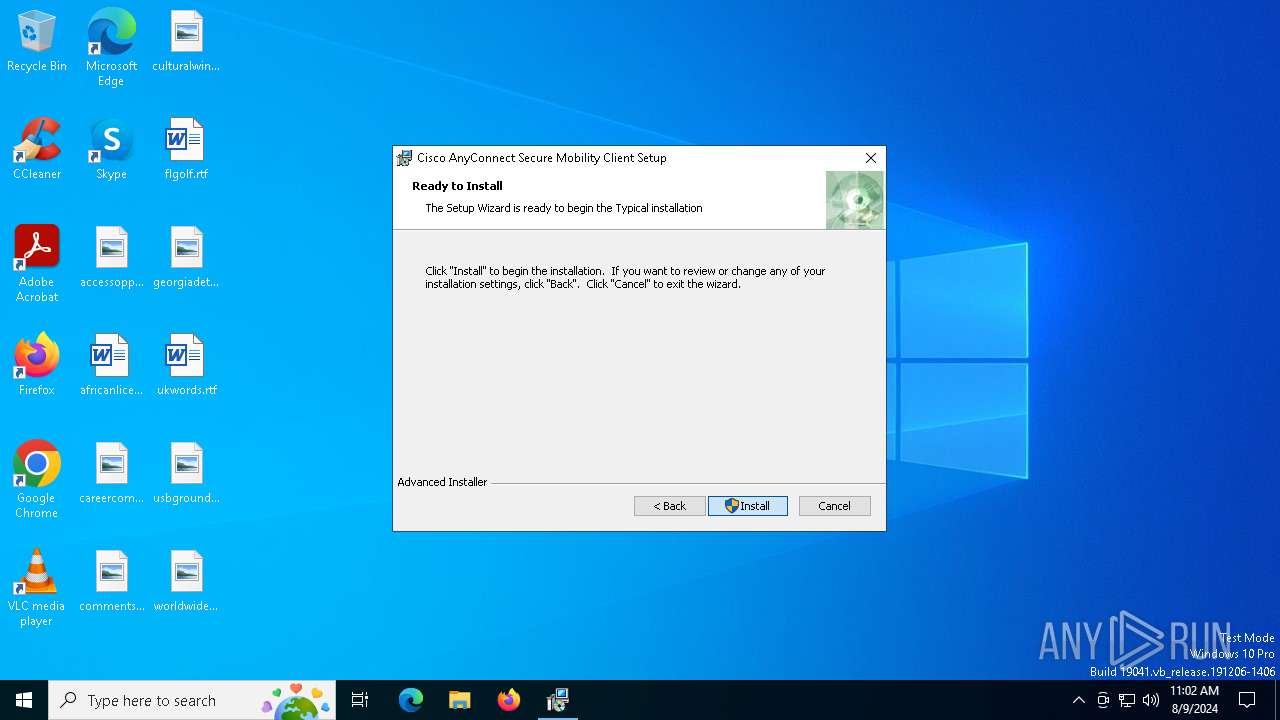
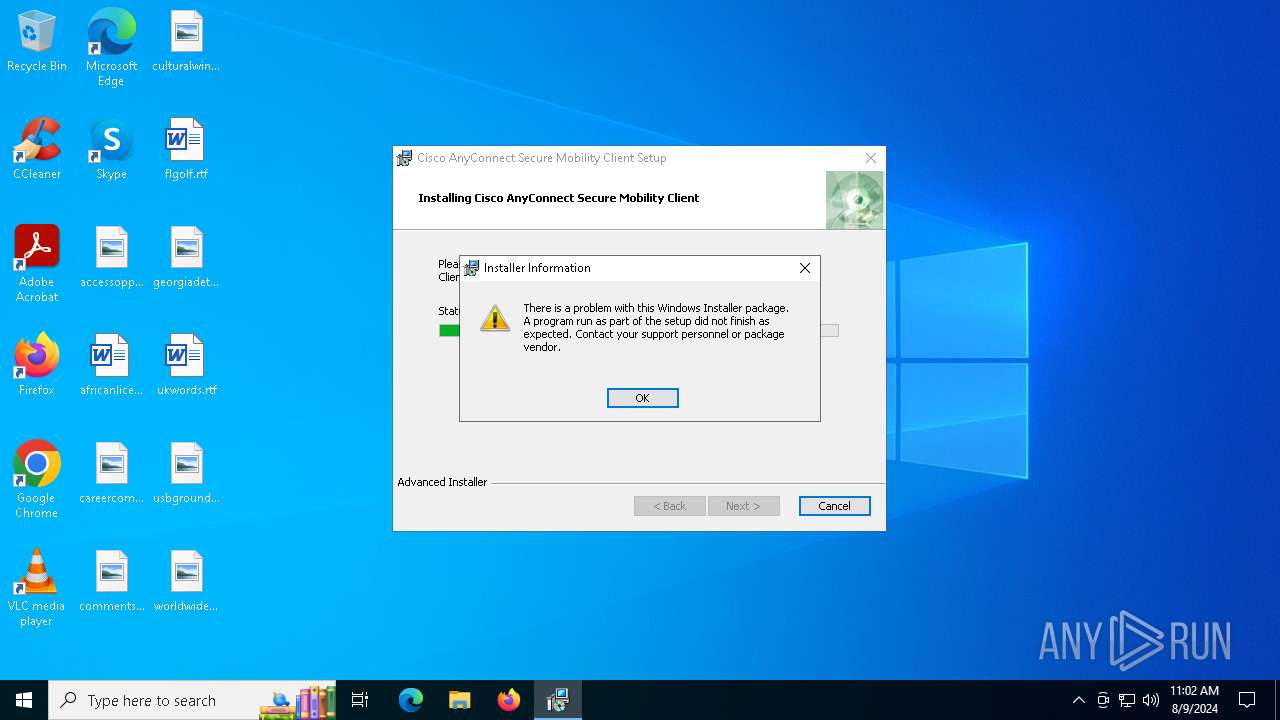
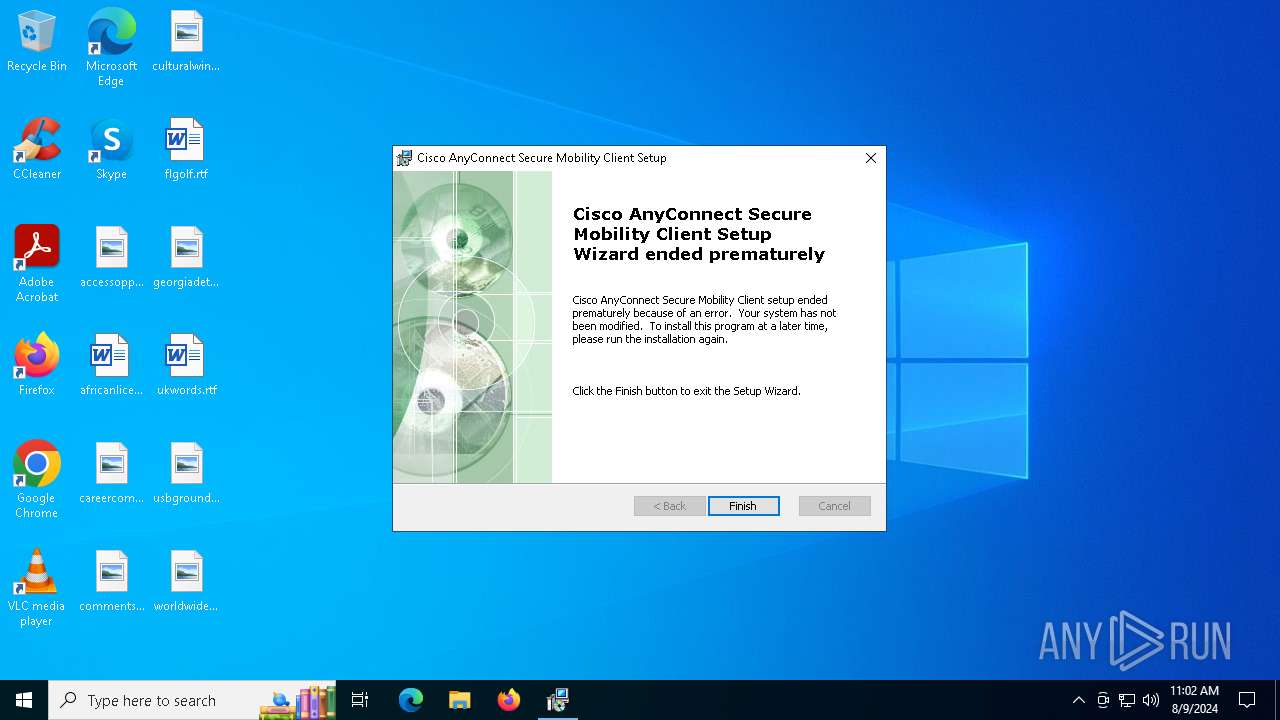
| File name: | anyconnect-win-4.9.05042-core-vpn-predeploy-k9.msi |
| Full analysis: | https://app.any.run/tasks/baaf57f9-c292-4841-ac4c-20b7a32bf510 |
| Verdict: | Malicious activity |
| Analysis date: | August 09, 2024, 11:02:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Dec 11 11:47:44 2009, Security: 0, Code page: 1252, Revision Number: {F9B5A0DA-D96E-417A-9007-9FFBE6581C48}, Number of Words: 2, Subject: Cisco AnyConnect Secure Mobility Client, Author: Cisco Systems, Inc., Name of Creating Application: Advanced Installer 17.4 build a9d5b2ae, Template: ;1033, Comments: A SmartNET contract is required for support - Cisco AnyConnect Secure Mobility Client., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | 7493E451BBE0A54B544772D91CDCB934 |
| SHA1: | 222622F2FDD8546E7C79A4D5AA2F0CE679555AFD |
| SHA256: | 1FC163EB3A5156E4DA19AAE8FC9381F438B514A4DB2C5E6B04E50FE217BE50D4 |
| SSDEEP: | 98304:kYoRJC7qYBv+bfSQp+hop7KokIcGU32Ddu3k6IMPXLJ6U04y+OW908wGxkziSIzy:L+cYNfq6B2mhSxLSZhr/rlErFwXp |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 6944)
Drops the executable file immediately after the start
- msiexec.exe (PID: 6672)
- msiexec.exe (PID: 2204)
- drvinst.exe (PID: 3044)
Process drops legitimate windows executable
- msiexec.exe (PID: 6672)
Checks Windows Trust Settings
- msiexec.exe (PID: 6672)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 6672)
- msiexec.exe (PID: 2204)
- drvinst.exe (PID: 3044)
The process drops C-runtime libraries
- msiexec.exe (PID: 6672)
Executable content was dropped or overwritten
- drvinst.exe (PID: 3044)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6512)
Reads Environment values
- msiexec.exe (PID: 6728)
Reads the computer name
- msiexec.exe (PID: 6728)
- msiexec.exe (PID: 6672)
An automatically generated document
- msiexec.exe (PID: 6512)
Creates files or folders in the user directory
- msiexec.exe (PID: 6512)
Checks supported languages
- msiexec.exe (PID: 6728)
- msiexec.exe (PID: 6672)
Checks proxy server information
- msiexec.exe (PID: 6512)
Reads the software policy settings
- msiexec.exe (PID: 6512)
- msiexec.exe (PID: 6672)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6512)
- msiexec.exe (PID: 6672)
- msiexec.exe (PID: 2204)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6672)
Application launched itself
- msiexec.exe (PID: 6672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2009:12:11 11:47:44 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {F9B5A0DA-D96E-417A-9007-9FFBE6581C48} |
| Words: | 2 |
| Subject: | Cisco AnyConnect Secure Mobility Client |
| Author: | Cisco Systems, Inc. |
| LastModifiedBy: | - |
| Software: | Advanced Installer 17.4 build a9d5b2ae |
| Template: | ;1033 |
| Comments: | A SmartNET contract is required for support - Cisco AnyConnect Secure Mobility Client. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
159
Monitored processes
26
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | "C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\InstallHelper.exe" -copyFiles "C:\Users\admin\AppData\Local\Temp\Profiles\\" "C:\ProgramData\Cisco\Cisco AnyConnect Secure Mobility Client\\" "AnyConnectLocalPolicy.xml" | C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\InstallHelper.exe | — | msiexec.exe | |||||||||||
User: admin Company: Cisco Systems, Inc. Integrity Level: MEDIUM Description: AnyConnect Secure Mobility Client Install Helper Exit code: 1 Version: 4, 9, 05042 | |||||||||||||||
| 2204 | C:\Windows\System32\MsiExec.exe -Embedding 4DDCBF37ADEDECC92A73FCCEC3144BB5 E Global\MSI0000 | C:\Windows\System32\msiexec.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2476 | "C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\InstallHelper.exe" -registerdll "C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\vpnapi.dll" | C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\InstallHelper.exe | — | msiexec.exe | |||||||||||
User: admin Company: Cisco Systems, Inc. Integrity Level: MEDIUM Description: AnyConnect Secure Mobility Client Install Helper Exit code: 0 Version: 4, 9, 05042 | |||||||||||||||
| 2572 | "C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\InstallHelper.exe" -moveFiles "C:\ProgramData\\Cisco\Cisco AnyConnect VPN Client\l10n\\" "C:\ProgramData\Cisco\Cisco AnyConnect Secure Mobility Client\\l10n\\" "*.*" | C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\InstallHelper.exe | — | msiexec.exe | |||||||||||
User: admin Company: Cisco Systems, Inc. Integrity Level: MEDIUM Description: AnyConnect Secure Mobility Client Install Helper Exit code: 1 Version: 4, 9, 05042 | |||||||||||||||
| 3044 | DrvInst.exe "4" "1" "c:\program files (x86)\cisco\cisco anyconnect secure mobility client\vpnva-6.inf" "9" "458dd218b" "00000000000001D0" "WinSta0\Default" "00000000000001E8" "208" "c:\program files (x86)\cisco\cisco anyconnect secure mobility client" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 3758096967 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 4576 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 5140 | "C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\InstallHelper.exe" -moveIfExist "C:\Users\admin\AppData\Local\\Cisco\Cisco AnyConnect VPN Client\preferences.xml" "C:\Users\admin\AppData\Local\Cisco\Cisco AnyConnect Secure Mobility Client\\preferences.xml" | C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\InstallHelper.exe | — | msiexec.exe | |||||||||||
User: admin Company: Cisco Systems, Inc. Integrity Level: MEDIUM Description: AnyConnect Secure Mobility Client Install Helper Exit code: 0 Version: 4, 9, 05042 | |||||||||||||||
| 5476 | DrvInst.exe "3" "1" "ROOT\NET\0000" "" "" "458dd218b" "00000000000001D0" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 6400 | "C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\InstallHelper.exe" -moveIfExist "C:\ProgramData\\Cisco\Cisco AnyConnect VPN Client\preferences_global.xml" "C:\ProgramData\Cisco\Cisco AnyConnect Secure Mobility Client\\preferences_global.xml" | C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\InstallHelper.exe | — | msiexec.exe | |||||||||||
User: admin Company: Cisco Systems, Inc. Integrity Level: MEDIUM Description: AnyConnect Secure Mobility Client Install Helper Exit code: 0 Version: 4, 9, 05042 | |||||||||||||||
| 6512 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\anyconnect-win-4.9.05042-core-vpn-predeploy-k9.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1603 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 008
Read events
9 844
Write events
154
Delete events
10
Modification events
| (PID) Process: | (6672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000005AC0FB9D4BEADA01101A0000101B0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000009C22FE9D4BEADA01101A0000101B0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000BF243C9E4BEADA01101A0000101B0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000BF243C9E4BEADA01101A0000101B0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000009D883E9E4BEADA01101A0000101B0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000793D439E4BEADA01101A0000101B0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (6672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 48000000000000005A7CBA9E4BEADA01101A0000101B0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000B700BD9E4BEADA01101A0000A01B0000E80300000100000000000000000000007E74712F352EDC4BA067318780E08C6300000000000000000000000000000000 | |||
| (PID) Process: | (6944) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000BC6BC69E4BEADA01201B0000581B0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
63
Suspicious files
31
Text files
51
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6672 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6672 | msiexec.exe | C:\Windows\Installer\eac87.msi | — | |
MD5:— | SHA256:— | |||
| 6512 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CDE89F9DCB25D8AC547E3CEFDA4FB6C2_C90A4A142FC951BB5BA5ADB1D629C0D7 | binary | |
MD5:27744FDF9D9C54B0CA7DBD8649E0F4ED | SHA256:60E93B21A1A2B3A6332C263C4F5AD3E2FBF66BA5F2D0FBEFBAE2BE1742D954E0 | |||
| 6512 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI57A1.tmp | executable | |
MD5:7DF0342209022320E9608D101480BDE2 | SHA256:D10B0B32B86307341A2F507E0E98FAD33AD7B3350899D9A7C27919B1E7D81CBD | |||
| 6512 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI5B8C.tmp | executable | |
MD5:7DF0342209022320E9608D101480BDE2 | SHA256:D10B0B32B86307341A2F507E0E98FAD33AD7B3350899D9A7C27919B1E7D81CBD | |||
| 6512 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\472BC96E644745821BD57EA65406C816 | binary | |
MD5:780321AD557DDC64C262EE49AC672C7B | SHA256:0E4584A6A1175EAFFBB09B850BF25102692159B6B9CCC9254D310705B8D5B354 | |||
| 6512 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI589C.tmp | executable | |
MD5:7DF0342209022320E9608D101480BDE2 | SHA256:D10B0B32B86307341A2F507E0E98FAD33AD7B3350899D9A7C27919B1E7D81CBD | |||
| 6672 | msiexec.exe | C:\Windows\Installer\MSIB012.tmp | executable | |
MD5:7DF0342209022320E9608D101480BDE2 | SHA256:D10B0B32B86307341A2F507E0E98FAD33AD7B3350899D9A7C27919B1E7D81CBD | |||
| 6512 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\1B1401C7EC8E96BC79CBFD92F9DF762D_5398732881722BDE3E78D6CA6BB2B78B | binary | |
MD5:97997C7C26E38C54D8DF318E60125415 | SHA256:4F5361DCBC2B8DAC3EC98E010320DEE4D3ACC654C801E9FD00C781673DCEA20F | |||
| 6512 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI5CB6.tmp | executable | |
MD5:7DF0342209022320E9608D101480BDE2 | SHA256:D10B0B32B86307341A2F507E0E98FAD33AD7B3350899D9A7C27919B1E7D81CBD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
48
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6512 | msiexec.exe | GET | 200 | 152.199.19.74:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FYHKj6JjF6UBieQioTYpFsuEriQQUtnf6aUhHn1MS1cLqBzJ2B9GXBxkCEHwbNTVK59t050FfEWnKa6g%3D | unknown | — | — | whitelisted |
6512 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://s.symcb.com/universal-root.crl | unknown | — | — | whitelisted |
6512 | msiexec.exe | GET | 200 | 152.199.19.74:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FYHKj6JjF6UBieQioTYpFsuEriQQUtnf6aUhHn1MS1cLqBzJ2B9GXBxkCEHwbNTVK59t050FfEWnKa6g%3D | unknown | — | — | whitelisted |
2212 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4276 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6512 | msiexec.exe | GET | 200 | 152.199.19.74:80 | http://rb.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTDRSYViRCZTxmZjLENmnwVjLly9QQU1MAGIknrOUvdk%2BJcobhHdglyA1gCEDSwesDam3xemKiAzep%2Fvu4%3D | unknown | — | — | whitelisted |
1140 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4084 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
532 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6512 | msiexec.exe | 152.199.19.74:80 | s.symcd.com | EDGECAST | US | unknown |
6512 | msiexec.exe | 192.229.221.95:80 | s.symcb.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4084 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
s.symcd.com |
| shared |
s.symcb.com |
| whitelisted |
rb.symcd.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |