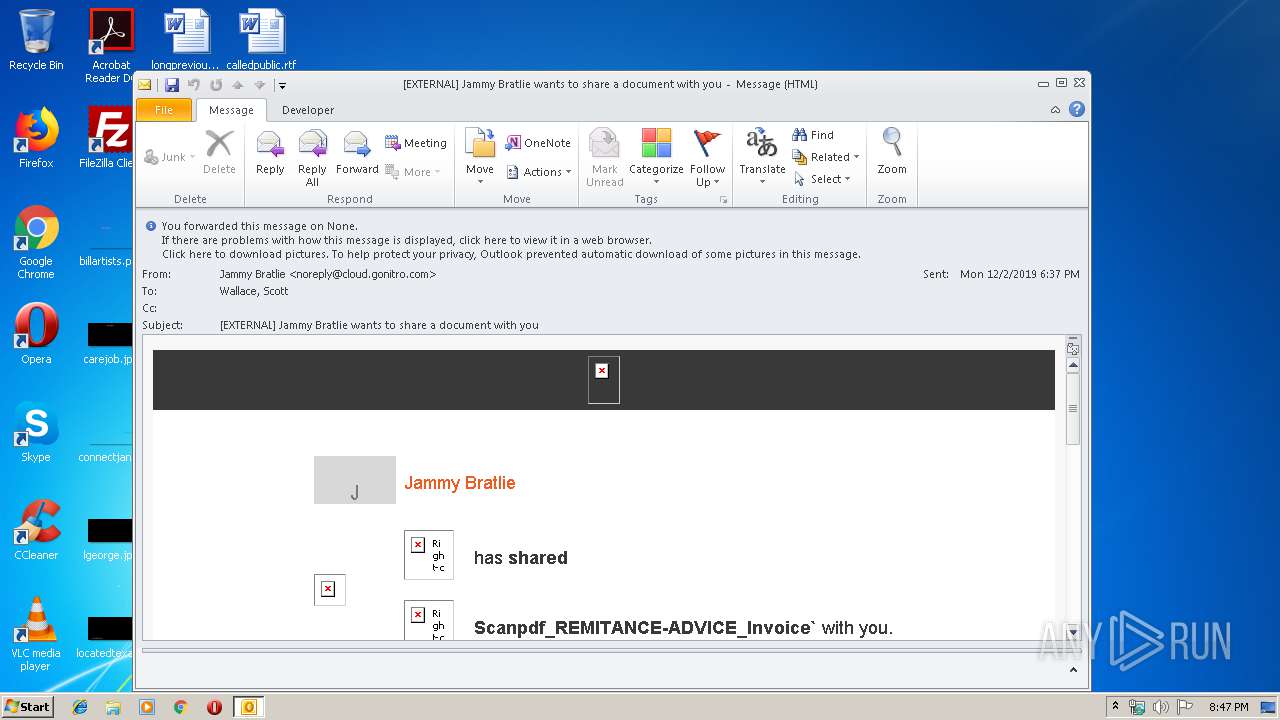
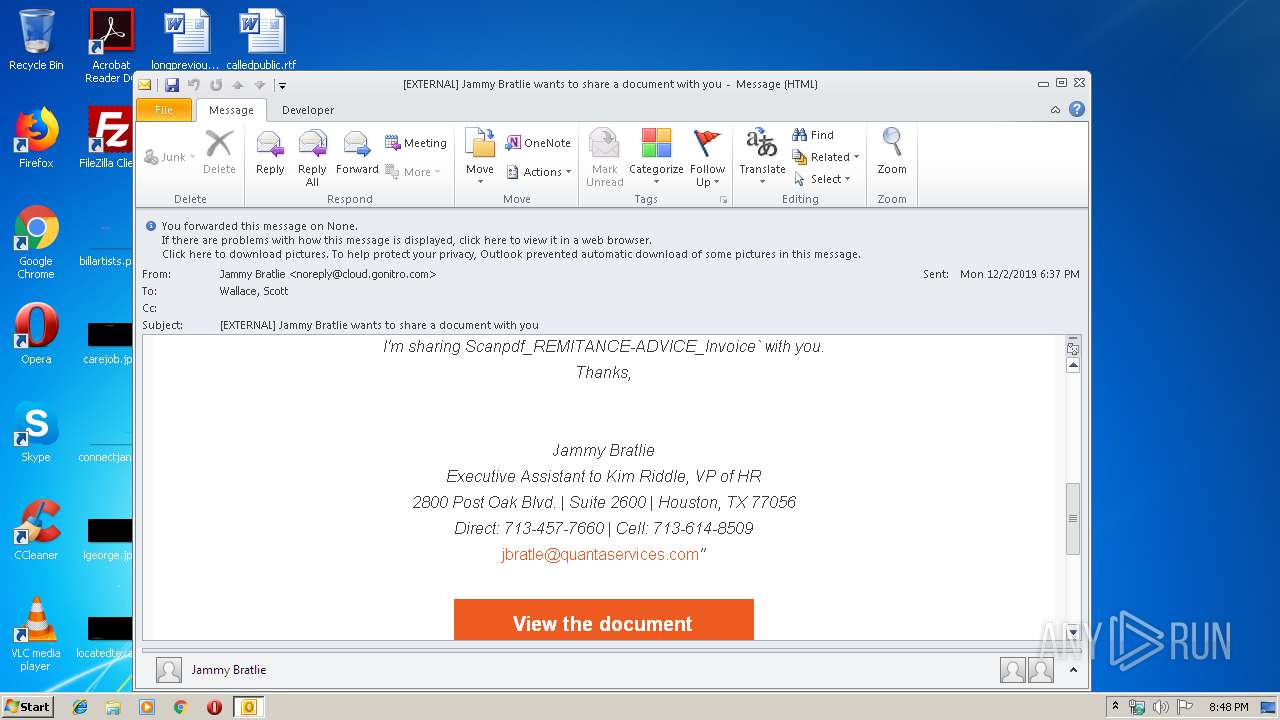
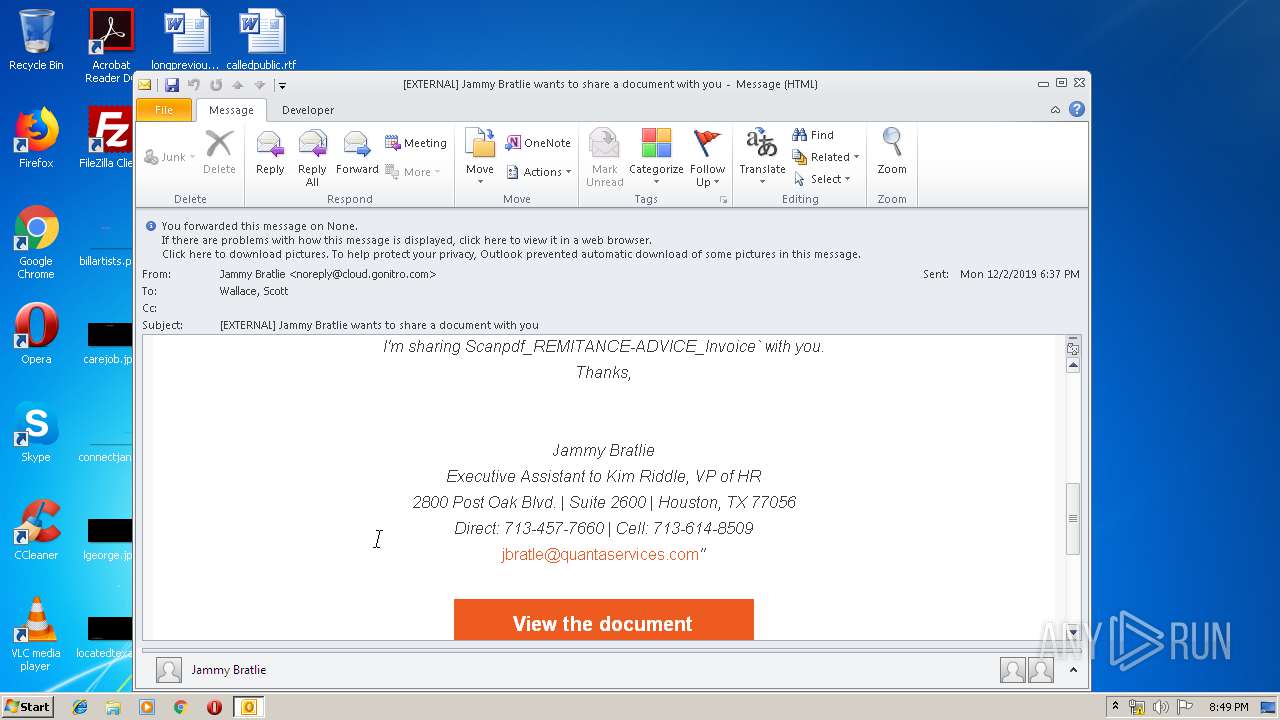
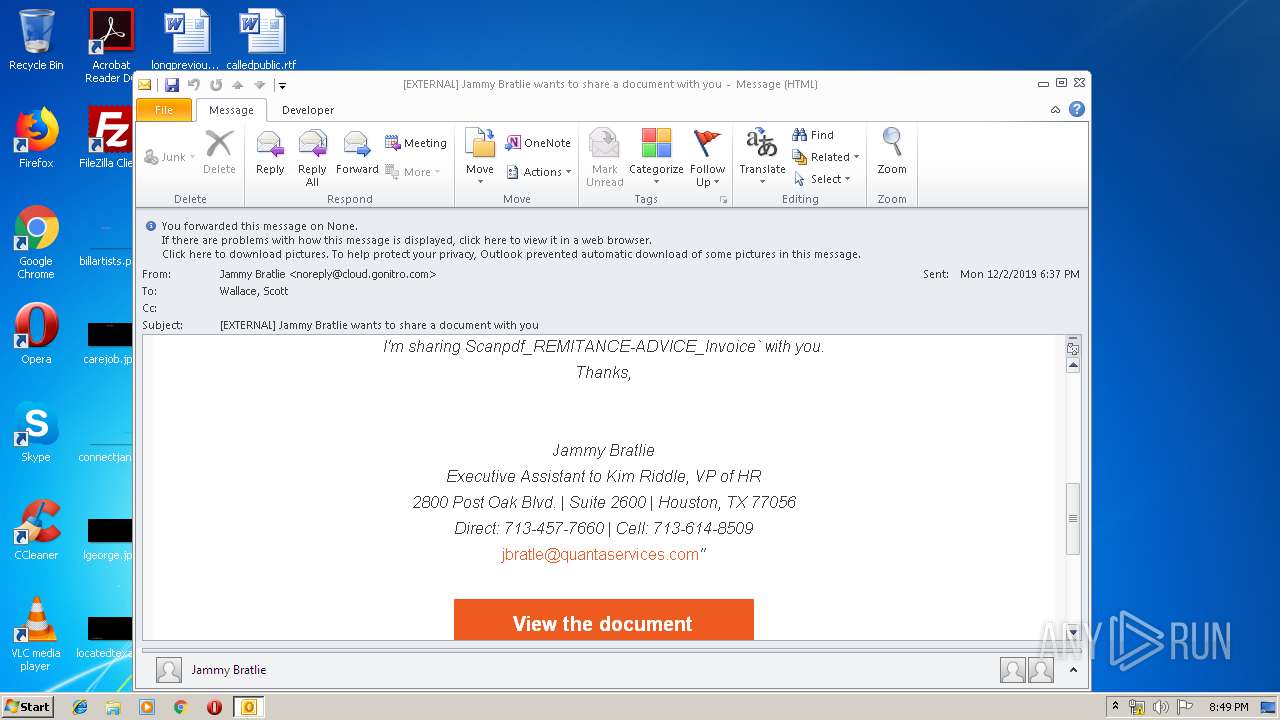
| File name: | EXTERNAL Jammy Bratlie wants to share a document with you.msg |
| Full analysis: | https://app.any.run/tasks/7627c039-f037-4507-b70c-9c9f50b2d9de |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2019, 20:47:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 9BFD91F8AF6F83CC57133D88DD2CA6BD |
| SHA1: | 4B4A0D5676022219775AAD1DAAE4504E171D6E60 |
| SHA256: | 1FAE3B4B94889E5FA9B1824E71DE12D1BB97908C9EDDC793E71B8F0F16DEF7D3 |
| SSDEEP: | 768:VjWphuazBaM8pvW6GlgMHfV+XqB/S5U7WsK0WsKWxWsK0WLzK32VDNhQQYpQG5+B:MzBjSagMHfJB/b7W8W6W8WnKOMWz |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2416)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 2416)
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2604)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2416)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2416)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3000)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3236)
Creates files in the user directory
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2604)
- iexplore.exe (PID: 2040)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3236)
Application launched itself
- chrome.exe (PID: 3000)
- iexplore.exe (PID: 3236)
Changes settings of System certificates
- iexplore.exe (PID: 3236)
Reads Internet Cache Settings
- iexplore.exe (PID: 2040)
- iexplore.exe (PID: 3236)
Reads the hosts file
- chrome.exe (PID: 2128)
- chrome.exe (PID: 3000)
Manual execution by user
- chrome.exe (PID: 3000)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2416)
Reads internet explorer settings
- iexplore.exe (PID: 2040)
Reads settings of System Certificates
- chrome.exe (PID: 2128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
75
Monitored processes
36
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,4017384340031775275,5134087149239693296,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9142881467038207020 --mojo-platform-channel-handle=3432 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6feda9d0,0x6feda9e0,0x6feda9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,4017384340031775275,5134087149239693296,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1660571191684204376 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2404 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 532 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,4017384340031775275,5134087149239693296,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17998104620746591809 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2236 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1072 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2776 --on-initialized-event-handle=312 --parent-handle=316 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1244 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,4017384340031775275,5134087149239693296,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12684454143068076472 --mojo-platform-channel-handle=3296 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,4017384340031775275,5134087149239693296,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=622259733394781351 --mojo-platform-channel-handle=3876 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1756 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,4017384340031775275,5134087149239693296,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10958646115171345931 --renderer-client-id=29 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2248 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,4017384340031775275,5134087149239693296,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12479882179987511960 --mojo-platform-channel-handle=3356 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3236 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 647
Read events
1 899
Write events
719
Delete events
29
Modification events
| (PID) Process: | (2416) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2416) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2416) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2416) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2416) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2416) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2416) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2416) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2416) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1333919924 | |||
| (PID) Process: | (2416) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources |
| Operation: | write | Name: | UISnapshot |
Value: 1033;1046;1036;1031;1040;1041;1049;3082;1042;1055 | |||
Executable files
0
Suspicious files
44
Text files
317
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2416 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRA39D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3236 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2416 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2040 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab2502.tmp | — | |
MD5:— | SHA256:— | |||
| 2040 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar2503.tmp | — | |
MD5:— | SHA256:— | |||
| 2040 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab2514.tmp | — | |
MD5:— | SHA256:— | |||
| 2040 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar2515.tmp | — | |
MD5:— | SHA256:— | |||
| 2416 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
60
DNS requests
43
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2416 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
2128 | chrome.exe | GET | 302 | 172.217.18.110:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 510 b | whitelisted |
2128 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRJ9L2KGL92BpjF3kAtaDtxauTmhgQUPdNQpdagre7zSmAKZdMh1Pj41g8CEAggB5NQF2%2FrfdtiHHSJddU%3D | US | der | 471 b | whitelisted |
2128 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAx5qUSwjBGVIJJhX%2BJrHYM%3D | US | der | 471 b | whitelisted |
2128 | chrome.exe | GET | 302 | 172.217.18.110:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 515 b | whitelisted |
2040 | iexplore.exe | GET | 200 | 172.217.16.170:80 | http://fonts.googleapis.com/css?family=Open+Sans:400,600|Cedarville+Cursive | US | text | 235 b | whitelisted |
2040 | iexplore.exe | GET | 200 | 13.224.197.208:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
2128 | chrome.exe | GET | 200 | 74.125.153.27:80 | http://r5---sn-hpa7zned.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mip=185.128.27.151&mm=28&mn=sn-hpa7zned&ms=nvh&mt=1575319704&mv=m&mvi=4&pl=24&shardbypass=yes | US | crx | 293 Kb | whitelisted |
3236 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
2040 | iexplore.exe | GET | 200 | 67.27.157.126:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.4 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2416 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2040 | iexplore.exe | 104.47.41.28:443 | nam03.safelinks.protection.outlook.com | Microsoft Corporation | US | whitelisted |
3236 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2040 | iexplore.exe | 99.80.104.131:443 | r6ws0xrm.r.eu-west-1.awstrack.me | AT&T Services, Inc. | US | unknown |
2040 | iexplore.exe | 151.101.2.110:443 | js-agent.newrelic.com | Fastly | US | suspicious |
2040 | iexplore.exe | 172.217.18.104:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
2040 | iexplore.exe | 52.222.168.217:443 | d1txdfm4y4p5qh.cloudfront.net | Amazon.com, Inc. | US | suspicious |
2040 | iexplore.exe | 162.247.242.18:443 | bam.nr-data.net | New Relic | US | whitelisted |
2040 | iexplore.exe | 216.58.205.238:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3236 | iexplore.exe | 52.222.168.217:443 | d1txdfm4y4p5qh.cloudfront.net | Amazon.com, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
nam03.safelinks.protection.outlook.com |
| whitelisted |
www.bing.com |
| whitelisted |
r6ws0xrm.r.eu-west-1.awstrack.me |
| unknown |
x.ss2.us |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
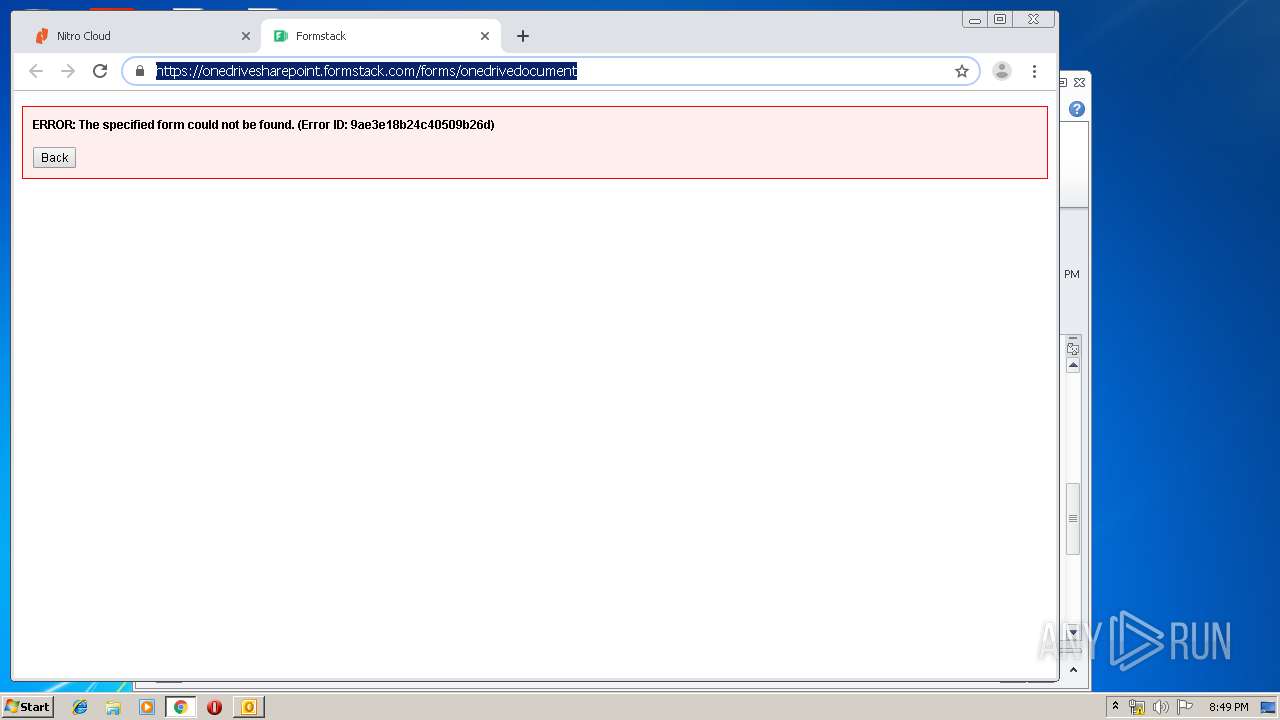
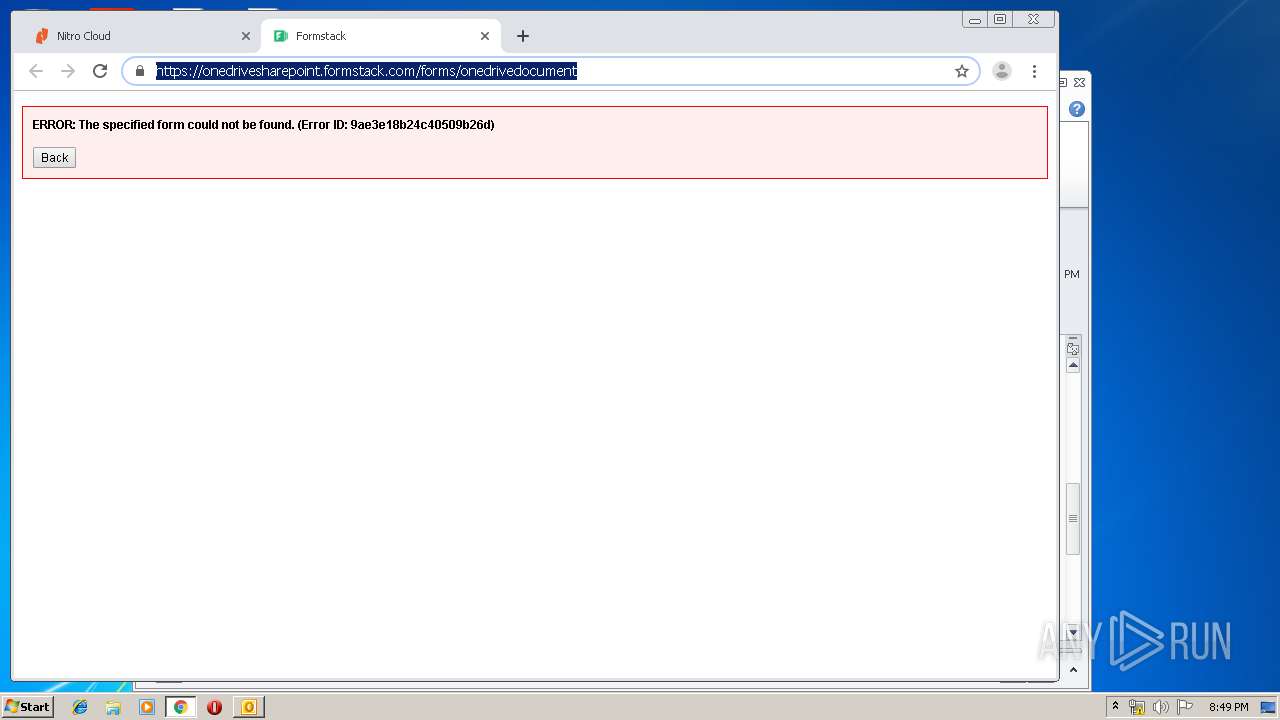
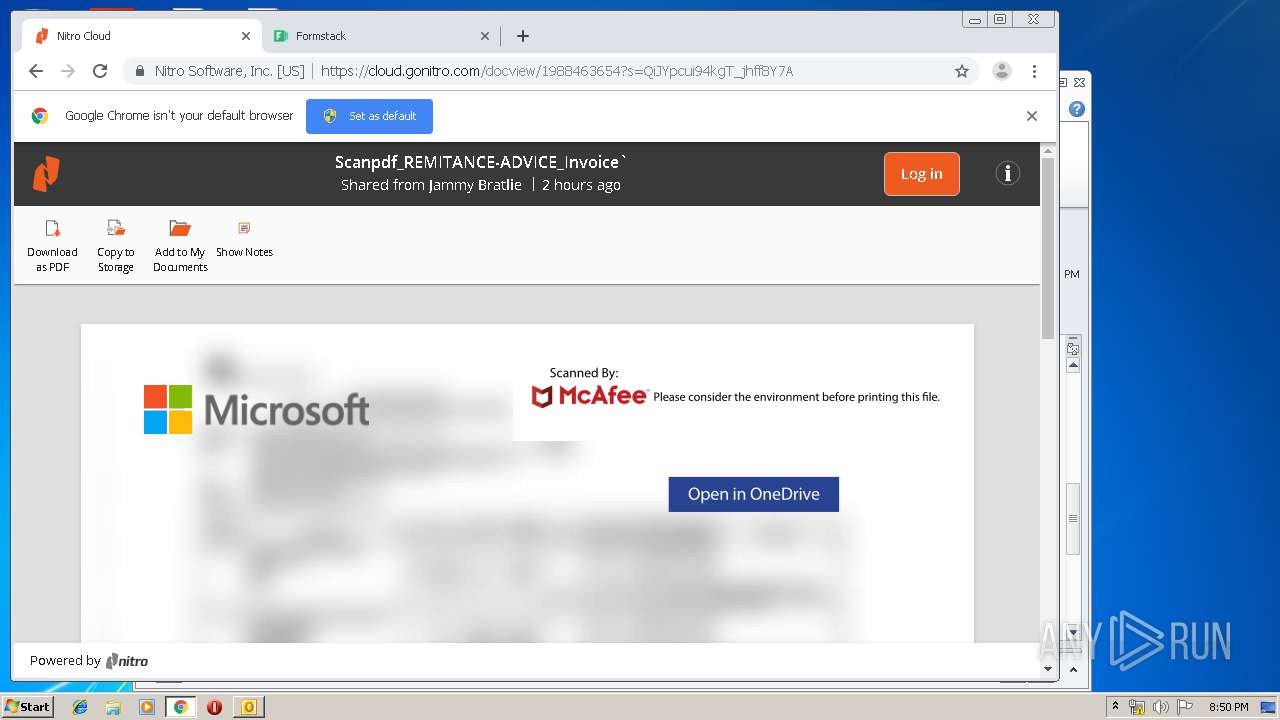
cloud.gonitro.com |
| unknown |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |