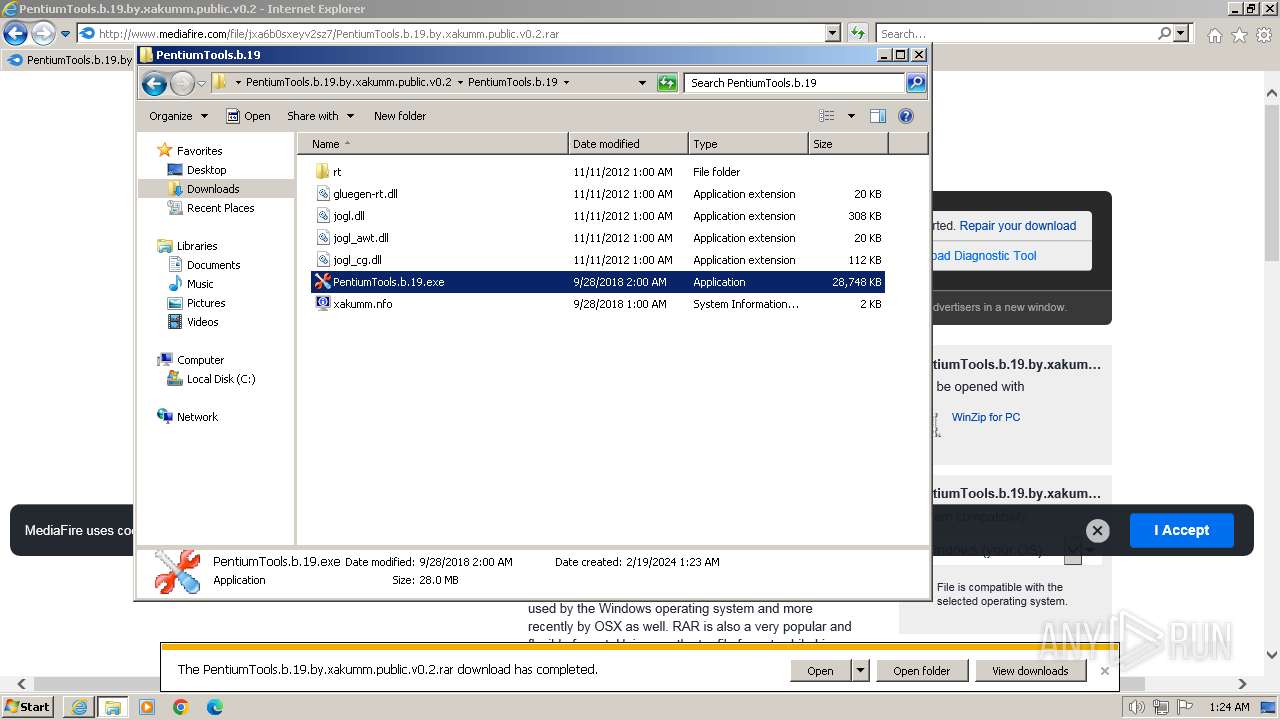
| URL: | http://download2272.mediafire.com/x4b7dozb8mmgrZ-JHsVU4k2Ml0FY0g-j3Qv8fk5L4DTJ_3k6AYLudonskVwcCCH9dPgHbGtkdmh5_CuVwGNoQgzfZkTjPiIMxnMocxWW2tVfudIpXk66Ht3Gendu5mN0yjdetc-849gcOnhflc9mipr65_JdqWtF4NNDVHYTgw0jhA/jxa6b0sxeyv2sz7/PentiumTools.b.19.by.xakumm.public.v0.2.rar |
| Full analysis: | https://app.any.run/tasks/5e5afc50-f285-40a6-8bfe-72b13dda702d |
| Verdict: | Malicious activity |
| Analysis date: | February 19, 2024, 01:21:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | D4958BBD7816334E9903244689F59A3E |
| SHA1: | AD2DF7D0FA07ADD3517E57B5DCE33CCB70014D3F |
| SHA256: | 1FA60790C8E212FF6AEFF3ADFF03B27337C7AC4506FB431238603996345D7A5E |
| SSDEEP: | 6:CalJeGO/CH4LEcwGgwHoKEDUsM5QI4Axrm7zPdsqGlCUIL8V+:NJev6HvjGpIKED+dDxq7zPd2d284 |
MALICIOUS
Drops the executable file immediately after the start
- PentiumTools.b.19.exe (PID: 268)
- PentiumTools.b.19.exe (PID: 3040)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 2376)
Executable content was dropped or overwritten
- PentiumTools.b.19.exe (PID: 268)
- PentiumTools.b.19.exe (PID: 3040)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2376)
- iexplore.exe (PID: 3864)
Application launched itself
- iexplore.exe (PID: 3864)
Manual execution by a user
- explorer.exe (PID: 3068)
- WinRAR.exe (PID: 2376)
- PentiumTools.b.19.exe (PID: 268)
- PentiumTools.b.19.exe (PID: 3040)
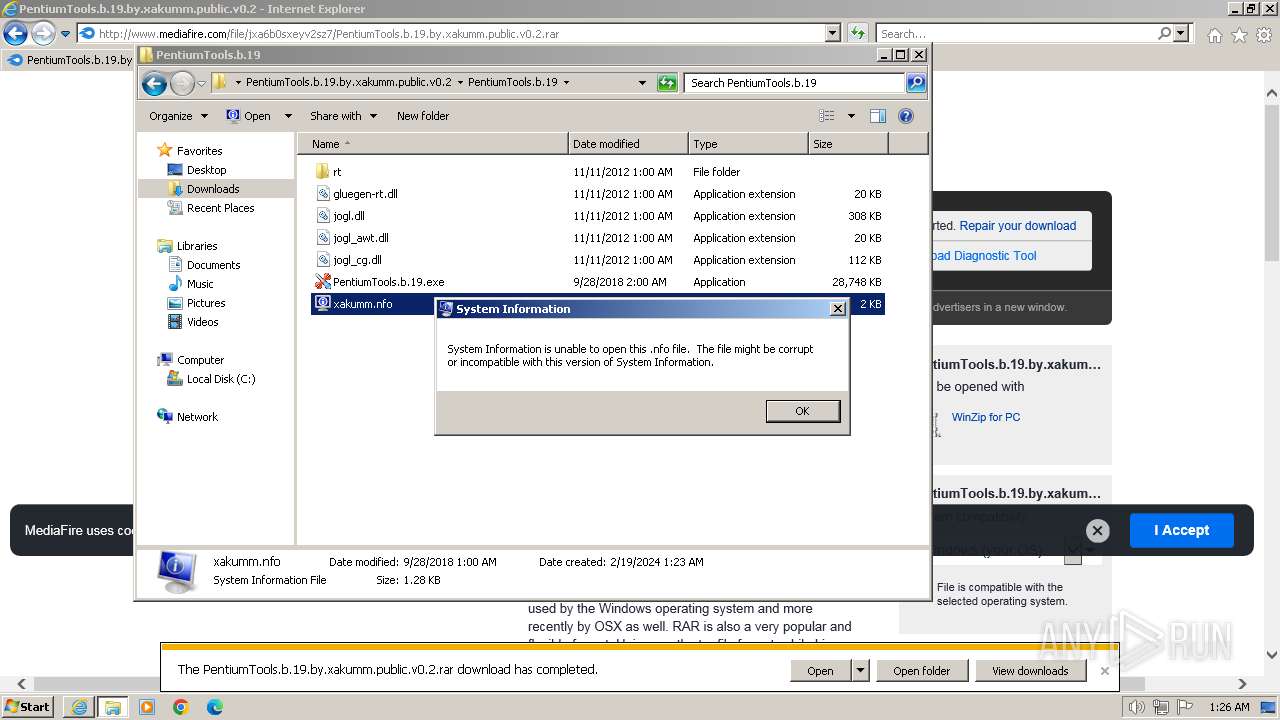
- msinfo32.exe (PID: 3080)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2376)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3864)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2376)
Checks supported languages
- PentiumTools.b.19.exe (PID: 268)
- PentiumTools.b.19.exe (PID: 3040)
Create files in a temporary directory
- PentiumTools.b.19.exe (PID: 268)
- PentiumTools.b.19.exe (PID: 3040)
Reads the time zone
- PentiumTools.b.19.exe (PID: 268)
- PentiumTools.b.19.exe (PID: 3040)
Reads the computer name
- PentiumTools.b.19.exe (PID: 268)
- PentiumTools.b.19.exe (PID: 3040)
Reads the machine GUID from the registry
- PentiumTools.b.19.exe (PID: 268)
- PentiumTools.b.19.exe (PID: 3040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
54
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Users\admin\Downloads\PentiumTools.b.19.by.xakumm.public.v0.2\PentiumTools.b.19\PentiumTools.b.19.exe" | C:\Users\admin\Downloads\PentiumTools.b.19.by.xakumm.public.v0.2\PentiumTools.b.19\PentiumTools.b.19.exe | explorer.exe | ||||||||||||
User: admin Company: Pentium Software Integrity Level: MEDIUM Description: PentiumTools Exit code: 0 Version: 2.0.0.19 Modules
| |||||||||||||||
| 2376 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\PentiumTools.b.19.by.xakumm.public.v0.2.rar" C:\Users\admin\Downloads\PentiumTools.b.19.by.xakumm.public.v0.2\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3040 | "C:\Users\admin\Downloads\PentiumTools.b.19.by.xakumm.public.v0.2\PentiumTools.b.19\PentiumTools.b.19.exe" | C:\Users\admin\Downloads\PentiumTools.b.19.by.xakumm.public.v0.2\PentiumTools.b.19\PentiumTools.b.19.exe | explorer.exe | ||||||||||||
User: admin Company: Pentium Software Integrity Level: MEDIUM Description: PentiumTools Exit code: 0 Version: 2.0.0.19 Modules
| |||||||||||||||
| 3068 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3080 | "C:\Windows\system32\msinfo32.exe" "C:\Users\admin\Downloads\PentiumTools.b.19.by.xakumm.public.v0.2\PentiumTools.b.19\xakumm.nfo" | C:\Windows\System32\msinfo32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: System Information Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3864 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://download2272.mediafire.com/x4b7dozb8mmgrZ-JHsVU4k2Ml0FY0g-j3Qv8fk5L4DTJ_3k6AYLudonskVwcCCH9dPgHbGtkdmh5_CuVwGNoQgzfZkTjPiIMxnMocxWW2tVfudIpXk66Ht3Gendu5mN0yjdetc-849gcOnhflc9mipr65_JdqWtF4NNDVHYTgw0jhA/jxa6b0sxeyv2sz7/PentiumTools.b.19.by.xakumm.public.v0.2.rar" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3952 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3864 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
47 131
Read events
46 952
Write events
141
Delete events
38
Modification events
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31089361 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 20022348 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31089362 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
81
Suspicious files
58
Text files
199
Unknown types
33
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\jquery.min[1].js | html | |
MD5:B8D64D0BC142B3F670CC0611B0AEBCAE | SHA256:47B68DCE8CB6805AD5B3EA4D27AF92A241F4E29A5C12A274C852E4346A0500B4 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\060EYAQY.txt | text | |
MD5:9EFC838C261DDF503F27683809199F96 | SHA256:C8F137D96227E90DEC41CD013F944ACAF3313A5B18E91D50FFA8983D4D3842C1 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\mfv3_121925[1].css | text | |
MD5:EBDF56BB5589A1188D10F05C7AF75AE7 | SHA256:A367DB2D796543D8667B4E244B058D31E3B97A3B97EBBD7D63BD0A67AAD9E522 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\master_121925[1].js | text | |
MD5:6B5CAF0BB6C58716C9CE2BA29E8B45EB | SHA256:02F0D99176865796E1F3C031048B3CF2084CC389E501FDE0F25EF75BD739BCAF | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\mf_logo_u1_full_color_reversed[1].svg | image | |
MD5:BCD95CFB6B9474DBA955AAB2CFE0432B | SHA256:1A0EC73A3CA7F354865D6B95401C50627FDF5A9B0DA763A6F75FA818FD775B55 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\NY0CYG1G.txt | text | |
MD5:1C4BC561724D60915AF4DC79D36BE87E | SHA256:88945D1932A26285119FBC98FB2C04D700F6D2B48AD37B7BD959BF67A558A83D | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\download_repair[1].htm | html | |
MD5:BC285EB4AF02DB3C48EC6C9E6E28C92A | SHA256:1B5E979B2553CEEF1FA61DA88807D80B6EDE269DB64940B7C45CFCEBFC517C07 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:5386C4748AF64CA2369F54B4A418DD59 | SHA256:CEBAE3280C7DF65DC0BA3E6D74F0DDA554E5343121D8CAAE5B60364651FC796F | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\default[1].png | image | |
MD5:853E3C671ADABBC17B0AD9929D507085 | SHA256:873B28A0419545D56F83B0E1CC449CE219F35C579BB7CE2CDF2D8FD6D374A2F1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
148
TCP/UDP connections
101
DNS requests
43
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3952 | iexplore.exe | GET | 302 | 199.91.155.13:80 | http://download2272.mediafire.com/x4b7dozb8mmgrZ-JHsVU4k2Ml0FY0g-j3Qv8fk5L4DTJ_3k6AYLudonskVwcCCH9dPgHbGtkdmh5_CuVwGNoQgzfZkTjPiIMxnMocxWW2tVfudIpXk66Ht3Gendu5mN0yjdetc-849gcOnhflc9mipr65_JdqWtF4NNDVHYTgw0jhA/jxa6b0sxeyv2sz7/PentiumTools.b.19.by.xakumm.public.v0.2.rar | unknown | — | — | unknown |
3952 | iexplore.exe | GET | 200 | 104.16.113.74:80 | http://www.mediafire.com/download_repair.php?flag=2&dkey=x4b7dozb8mmgrZ%2DJHsVU4k2Ml0FY0g%2Dj3Qv8fk5L4DTJ%5F3k6AYLudonskVwcCCH9dPgHbGtkdmh5%5FCuVwGNoQgzfZkTjPiIMxnMocxWW2tVfudIpXk66Ht3Gendu5mN0yjdetc%2D849gcOnhflc9mipr65%5FJdqWtF4NNDVHYTgw0jhA&qkey=jxa6b0sxeyv2sz7&ip=216%2E24%2E213%2E187 | unknown | html | 10.2 Kb | unknown |
3952 | iexplore.exe | GET | 200 | 104.16.113.74:80 | http://www.mediafire.com/images/icons/myfiles/default.png | unknown | image | 363 b | unknown |
3952 | iexplore.exe | GET | 200 | 104.16.113.74:80 | http://static.mediafire.com/css/mfv4_121925.php?ver=nonssl&date=2024-02-18 | unknown | text | 51.8 Kb | unknown |
3952 | iexplore.exe | GET | 200 | 104.16.113.74:80 | http://static.mediafire.com/images/backgrounds/header/mf_logo_u1_full_color.svg | unknown | image | 2.04 Kb | unknown |
3952 | iexplore.exe | GET | 200 | 104.16.113.74:80 | http://static.mediafire.com/css/mfv3_121925.php?ver=nonssl | unknown | text | 42.2 Kb | unknown |
3952 | iexplore.exe | GET | 200 | 104.16.113.74:80 | http://static.mediafire.com/images/backgrounds/header/mf_logo_u1_full_color_reversed.svg | unknown | image | 2.02 Kb | unknown |
3952 | iexplore.exe | GET | 200 | 104.16.113.74:80 | http://static.mediafire.com/js/master_121925.js | unknown | text | 148 Kb | unknown |
3952 | iexplore.exe | GET | 304 | 173.222.108.210:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?31edca662c8b6304 | unknown | — | — | unknown |
3952 | iexplore.exe | GET | 200 | 172.217.18.10:80 | http://ajax.googleapis.com/ajax/libs/jquery/1.7.2/jquery.min.js | unknown | html | 92.6 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3952 | iexplore.exe | 199.91.155.13:80 | download2272.mediafire.com | MEDIAFIRE | US | unknown |
3952 | iexplore.exe | 104.16.113.74:80 | www.mediafire.com | CLOUDFLARENET | — | unknown |
3952 | iexplore.exe | 216.58.212.170:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
3952 | iexplore.exe | 172.217.16.196:443 | www.google.com | GOOGLE | US | whitelisted |
3952 | iexplore.exe | 172.217.18.10:80 | ajax.googleapis.com | GOOGLE | US | whitelisted |
3952 | iexplore.exe | 142.250.185.136:443 | www.googletagmanager.com | GOOGLE | US | unknown |
3952 | iexplore.exe | 104.16.57.101:443 | static.cloudflareinsights.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download2272.mediafire.com |
| unknown |
www.mediafire.com |
| shared |
static.mediafire.com |
| shared |
fonts.googleapis.com |
| whitelisted |
www.google.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |