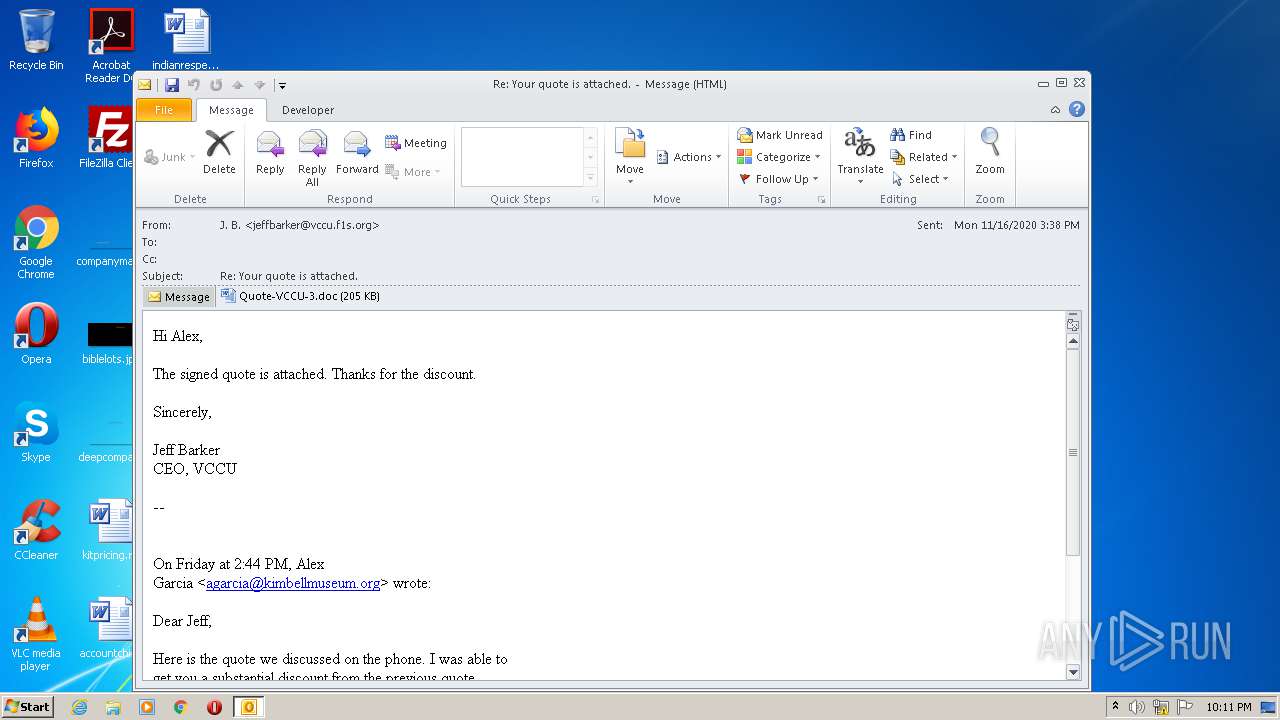
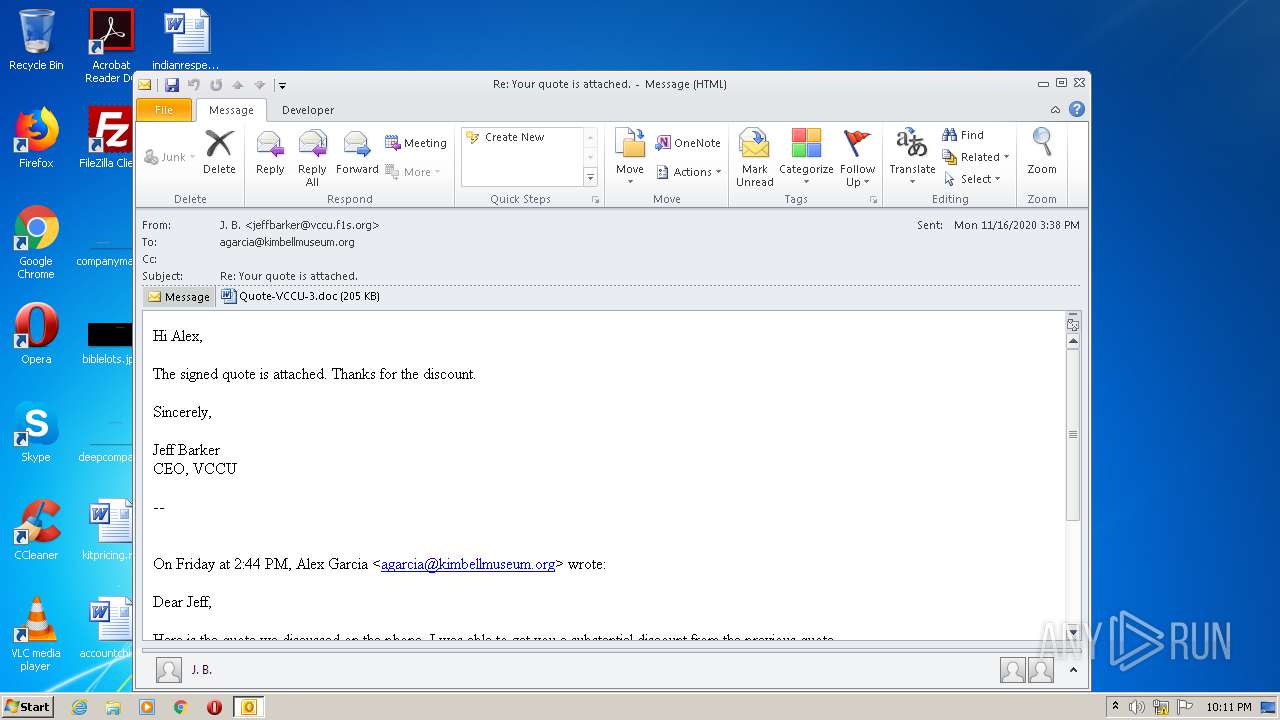
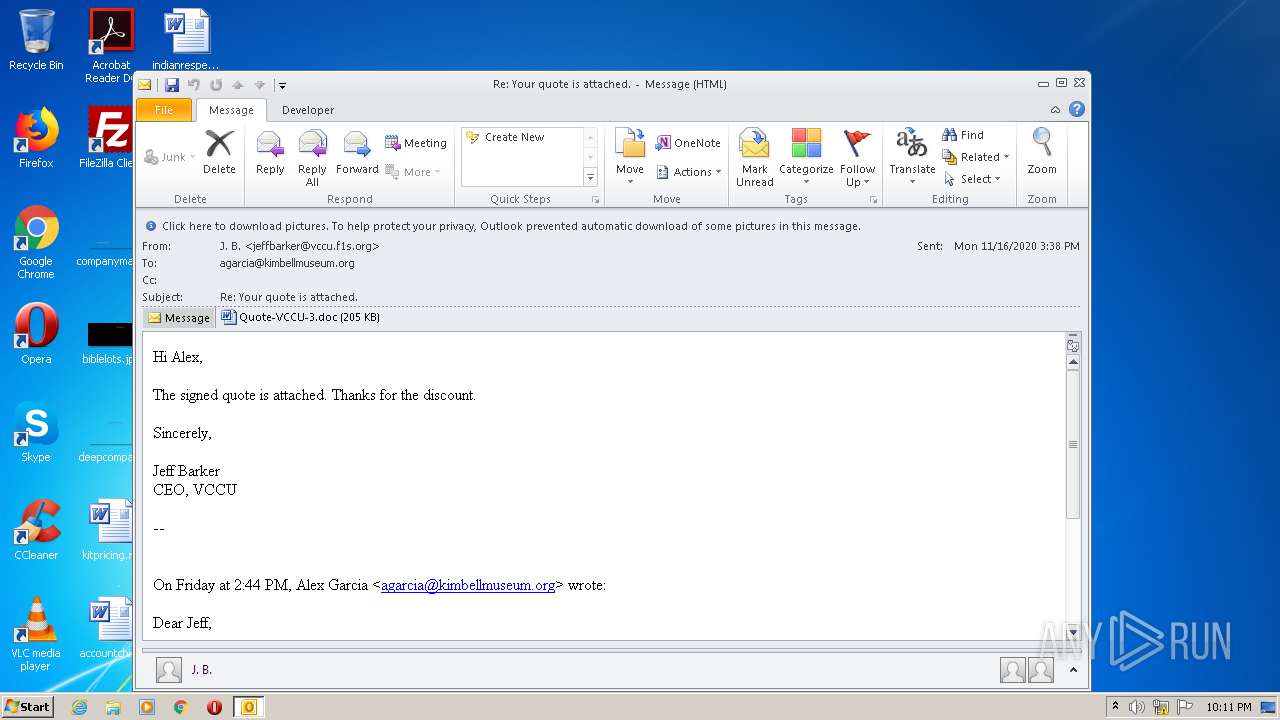
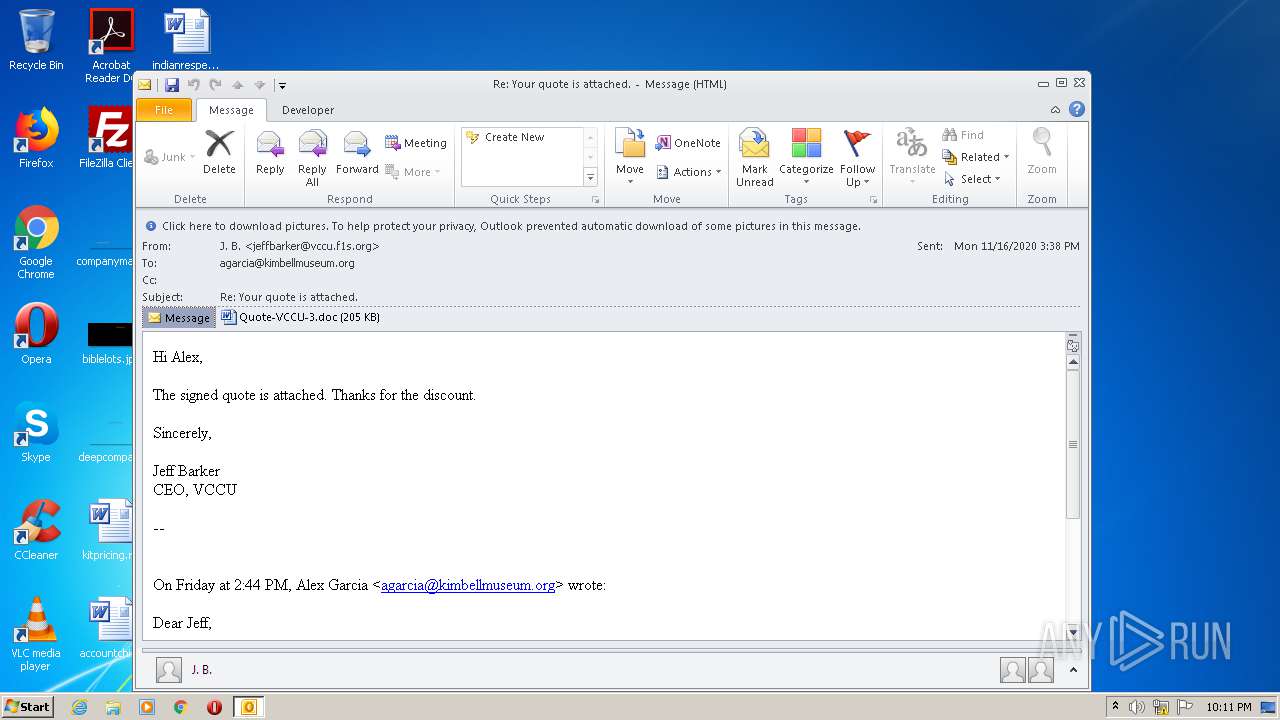
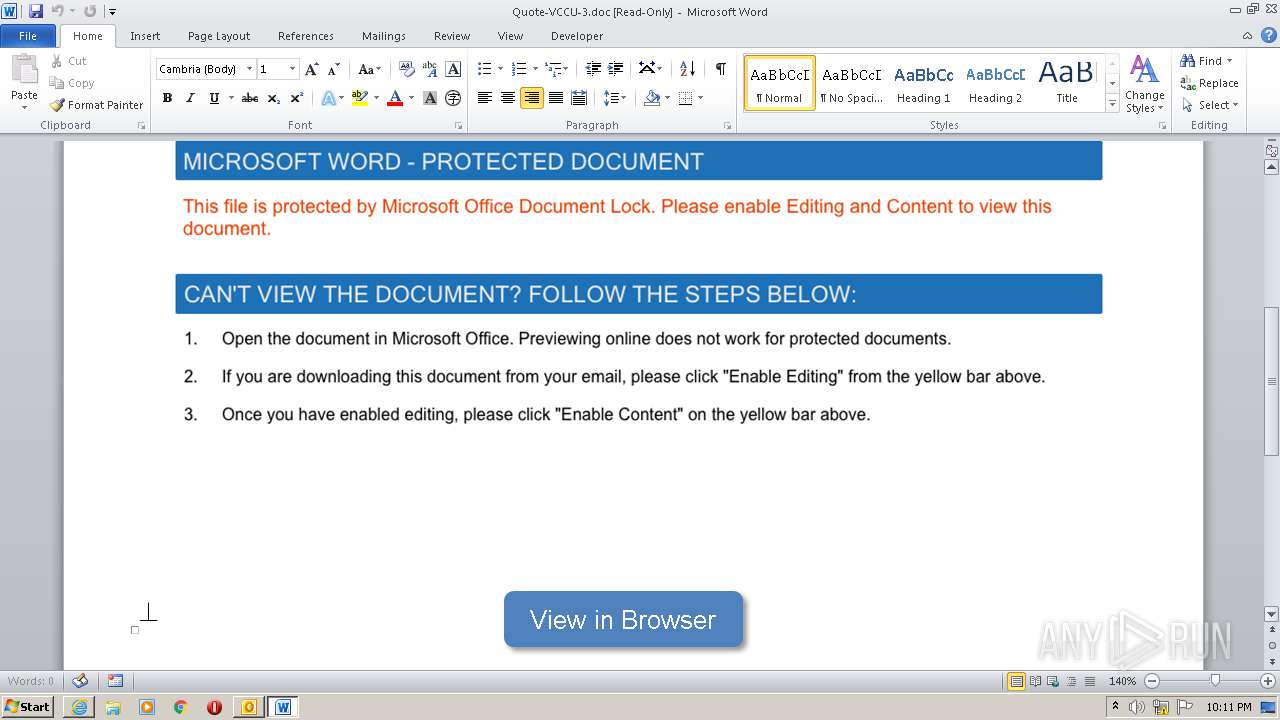
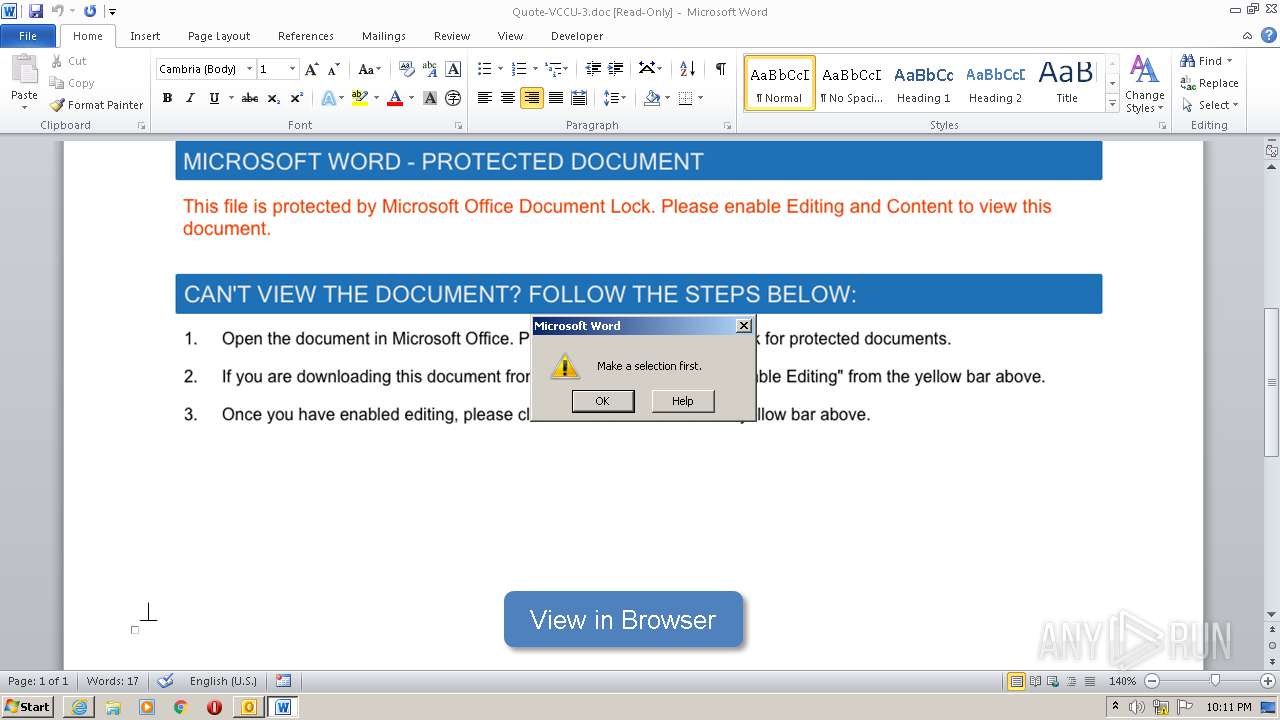
| File name: | Re_ Your quote is attached.eml |
| Full analysis: | https://app.any.run/tasks/f22328cc-85c7-4ae9-aa25-dd916ccb460e |
| Verdict: | Malicious activity |
| Analysis date: | November 16, 2020, 22:11:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 11EC04EA8929617CA7D30EA774909C65 |
| SHA1: | ADBF8B9C87D7FD8ADD3F2D013C5C39513F107FBC |
| SHA256: | 1F8E29CAC7F40697459C3DEA74A5D90372D94245651BC09FE2F39372086EEF30 |
| SSDEEP: | 6144:Jj/Um+4OCPzMmjgmvOLuYxJQyw1AfPcowjflBOjDwW:hUx+zzjgmvYDG1icoUXUwW |
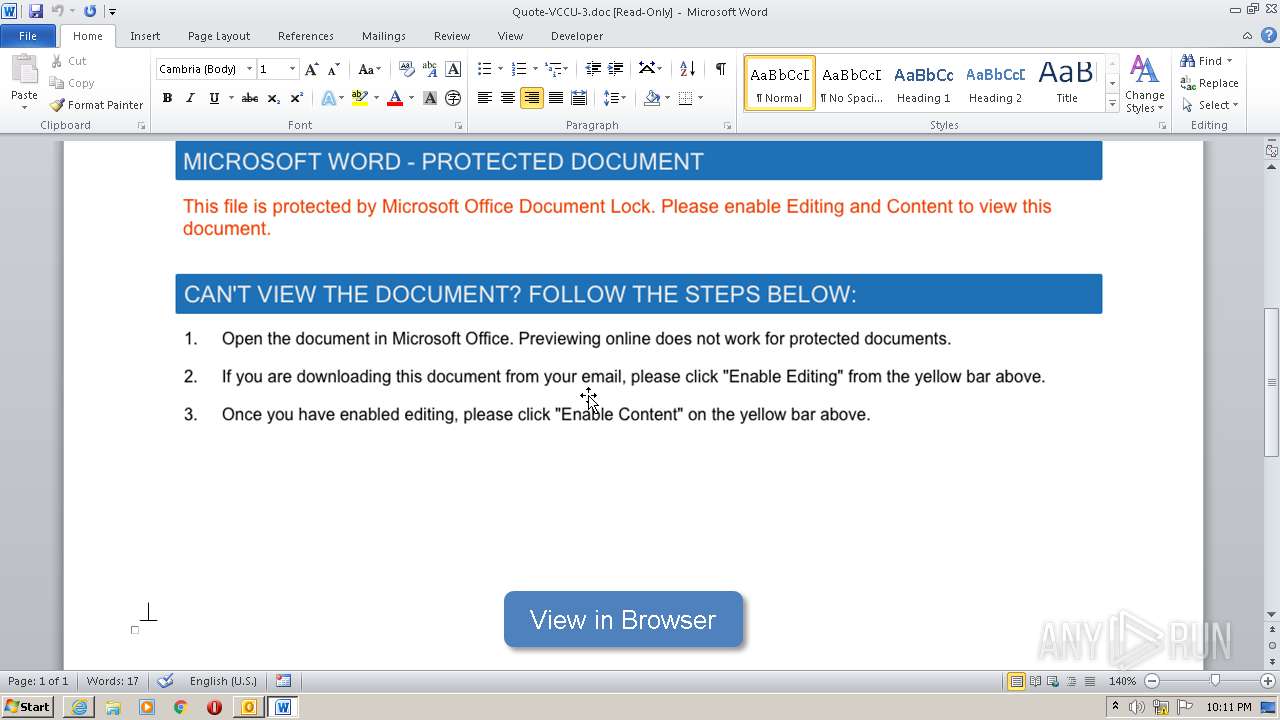
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2900)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 900)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 900)
Application launched itself
- WINWORD.EXE (PID: 2900)
Starts Internet Explorer
- WINWORD.EXE (PID: 2900)
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 900)
- WINWORD.EXE (PID: 2900)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2900)
- OUTLOOK.EXE (PID: 900)
- WINWORD.EXE (PID: 2400)
Reads internet explorer settings
- iexplore.exe (PID: 2116)
Reads settings of System Certificates
- iexplore.exe (PID: 3508)
- WINWORD.EXE (PID: 2900)
Changes settings of System certificates
- iexplore.exe (PID: 3508)
Creates files in the user directory
- WINWORD.EXE (PID: 2900)
- iexplore.exe (PID: 3508)
Application launched itself
- iexplore.exe (PID: 3508)
Reads Internet Cache Settings
- iexplore.exe (PID: 2116)
- WINWORD.EXE (PID: 2900)
- iexplore.exe (PID: 3508)
Changes internet zones settings
- iexplore.exe (PID: 3508)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 900 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Re_ Your quote is attached.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2116 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3508 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2400 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
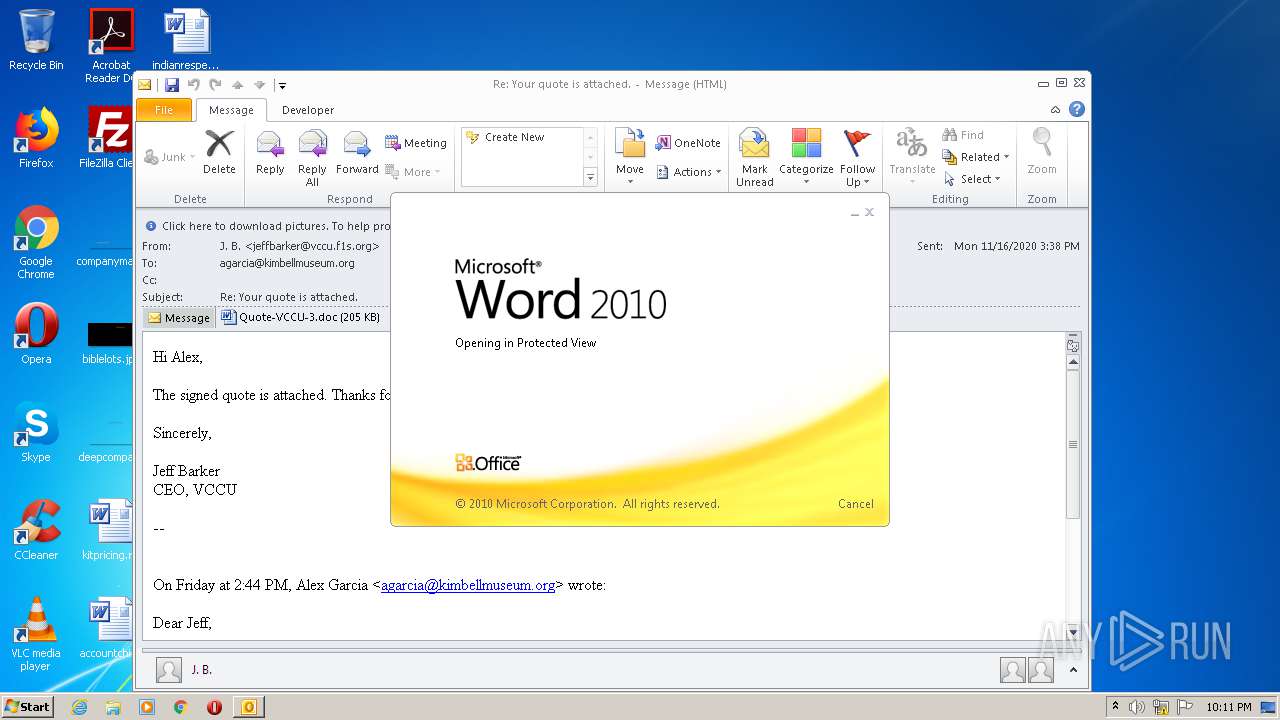
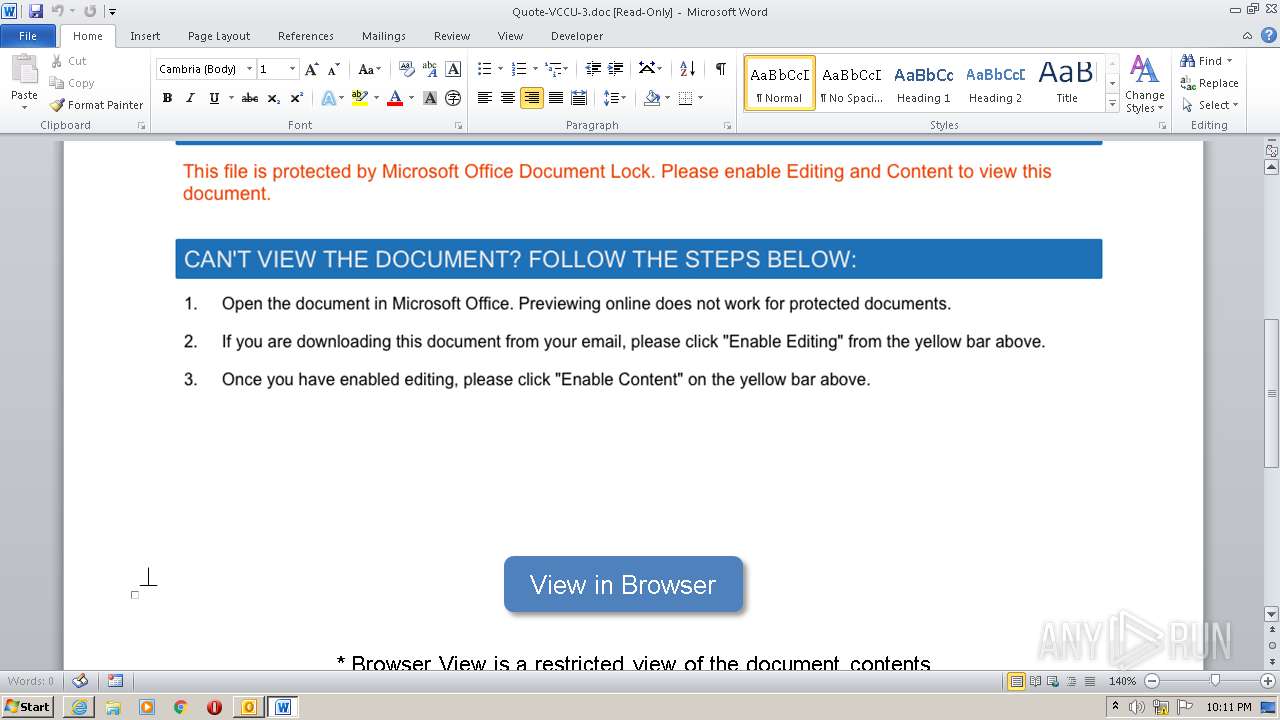
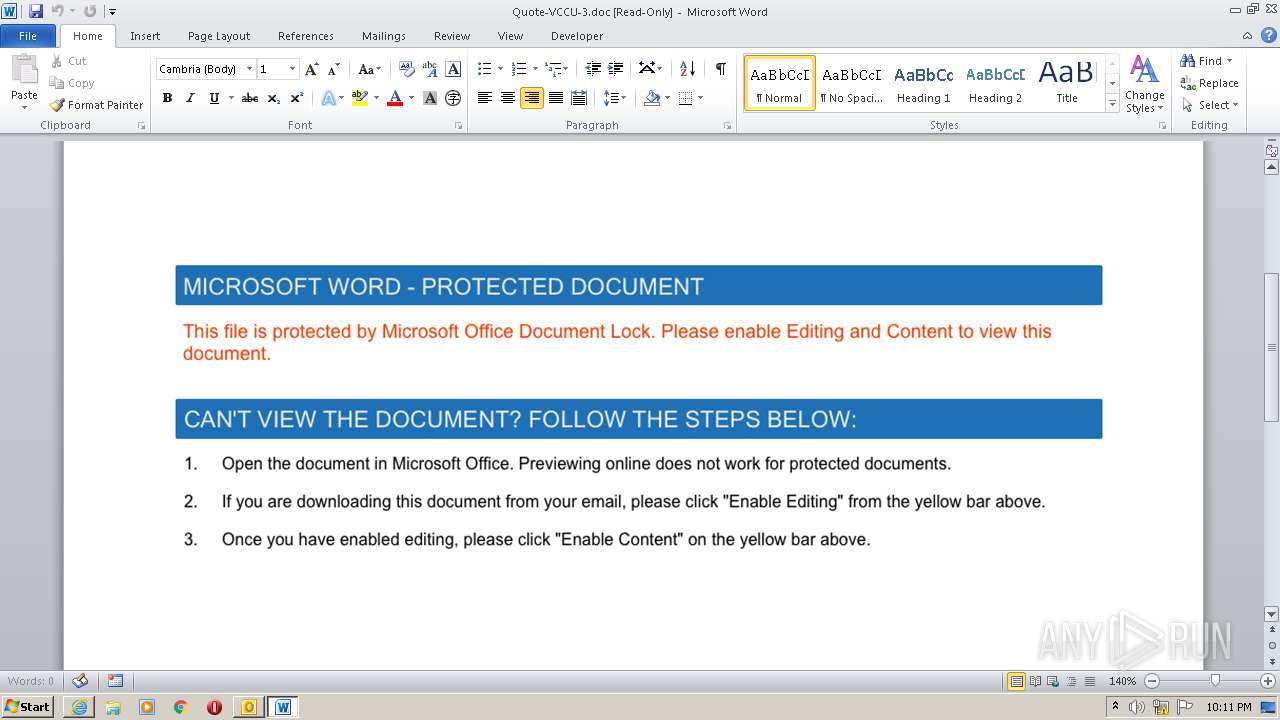
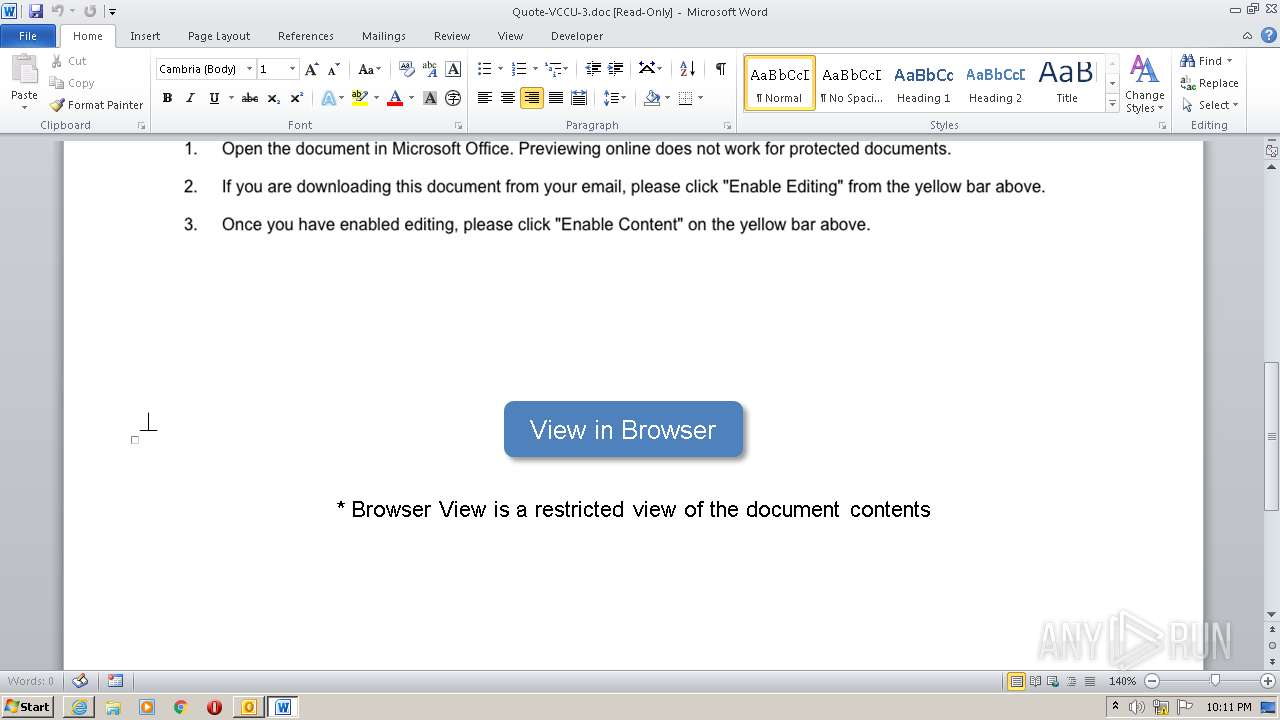
| 2900 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\72S6OKQR\Quote-VCCU-3.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
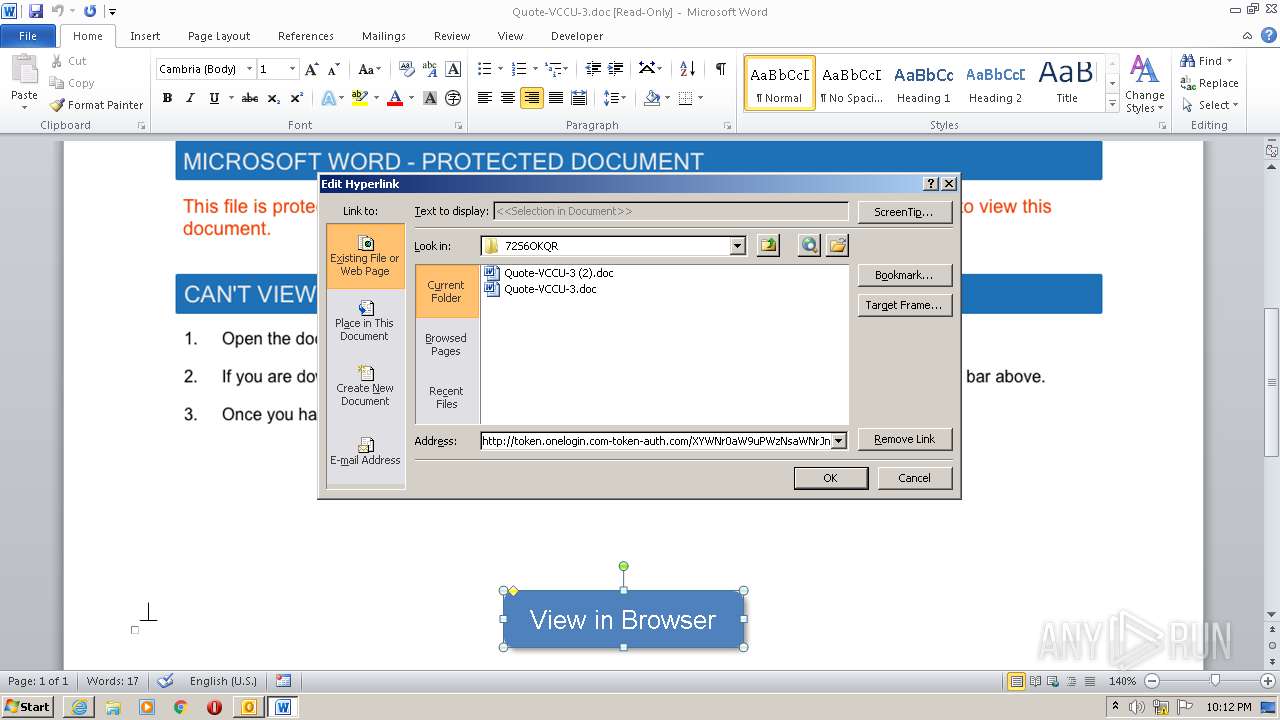
| 3508 | "C:\Program Files\Internet Explorer\iexplore.exe" http://token.onelogin.com-token-auth.com/XYWNy0aW9uPWi1hY3JvJneVybD1osqdHRwpczovL3NlaY3nVyZWQtbG9naW4ubmV0tL3BhZ2VzL2M4MTdkNjlmNjY0NSZyZWNpcGllbnRfaWQ9NzI5ODE1NDcyJmNhbXBhaWduX3J1bl9pZD0zODg5NDY3 | C:\Program Files\Internet Explorer\iexplore.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
4 647
Read events
3 308
Write events
1 233
Delete events
106
Modification events
| (PID) Process: | (900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
34
Text files
44
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 900 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRA91A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 900 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmpAB2F.tmp | — | |
MD5:— | SHA256:— | |||
| 900 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\72S6OKQR\Quote-VCCU-3 (2).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2900 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRCA4E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2900 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_46707A81-7364-4B37-9FF5-F8FAE2E2AD71.0\C0B32F76.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2400 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_46707A81-7364-4B37-9FF5-F8FAE2E2AD71.0\msoDB0E.tmp | — | |
MD5:— | SHA256:— | |||
| 2400 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_46707A81-7364-4B37-9FF5-F8FAE2E2AD71.0\2F15DFB1.jpeg | — | |
MD5:— | SHA256:— | |||
| 2900 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\msoE7C9.tmp | — | |
MD5:— | SHA256:— | |||
| 2900 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\D0886CFF.jpeg | — | |
MD5:— | SHA256:— | |||
| 2400 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_46707A81-7364-4B37-9FF5-F8FAE2E2AD71.0\F385E1FE.jpeg | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
36
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
900 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
2116 | iexplore.exe | GET | 301 | 52.86.68.115:80 | http://token.onelogin.com-token-auth.com/XYWNy0aW9uPWi1hY3JvJneVybD1osqdHRwpczovL3NlaY3nVyZWQtbG9naW4ubmV0tL3BhZ2VzL2M4MTdkNjlmNjY0NSZyZWNpcGllbnRfaWQ9NzI5ODE1NDcyJmNhbXBhaWduX3J1bl9pZD0zODg5NDY3 | US | — | — | suspicious |
2900 | WINWORD.EXE | GET | 301 | 52.86.68.115:80 | http://token.onelogin.com-token-auth.com/XYWNc0aW9uPWnF0dGFjaGo1lbnQmhlcmVjuaXBpZW50jX2jlkPTcyOTgxNTQ3MiZjfYW1wYWlnbl9ydW5faWQ9Mzg4OTQ2Nw== | US | — | — | suspicious |
2900 | WINWORD.EXE | GET | 200 | 13.32.56.83:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
3508 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2116 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAPp1injTY%2Fh1Wan30S3y%2FE%3D | US | der | 279 b | whitelisted |
3508 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3508 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2116 | iexplore.exe | GET | 200 | 13.224.195.13:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEAHbZX6QrpkhkTQ8ngFcWLE%3D | US | der | 471 b | whitelisted |
2116 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
900 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2900 | WINWORD.EXE | 52.86.68.115:80 | token.onelogin.com-token-auth.com | Amazon.com, Inc. | US | unknown |
2900 | WINWORD.EXE | 52.86.68.115:443 | token.onelogin.com-token-auth.com | Amazon.com, Inc. | US | unknown |
2116 | iexplore.exe | 52.86.68.115:443 | token.onelogin.com-token-auth.com | Amazon.com, Inc. | US | unknown |
2900 | WINWORD.EXE | 13.32.56.83:80 | o.ss2.us | — | US | unknown |
2900 | WINWORD.EXE | 143.204.101.74:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
2900 | WINWORD.EXE | 143.204.101.124:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
2116 | iexplore.exe | 18.207.67.81:443 | token.onelogin.com-token-auth.com | — | US | malicious |
3508 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2116 | iexplore.exe | 13.224.195.167:80 | ocsp.sca1b.amazontrust.com | — | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
token.onelogin.com-token-auth.com |
| suspicious |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.sca1b.amazontrust.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
secured-login.net |
| whitelisted |
cdn2.hubspot.net |
| whitelisted |