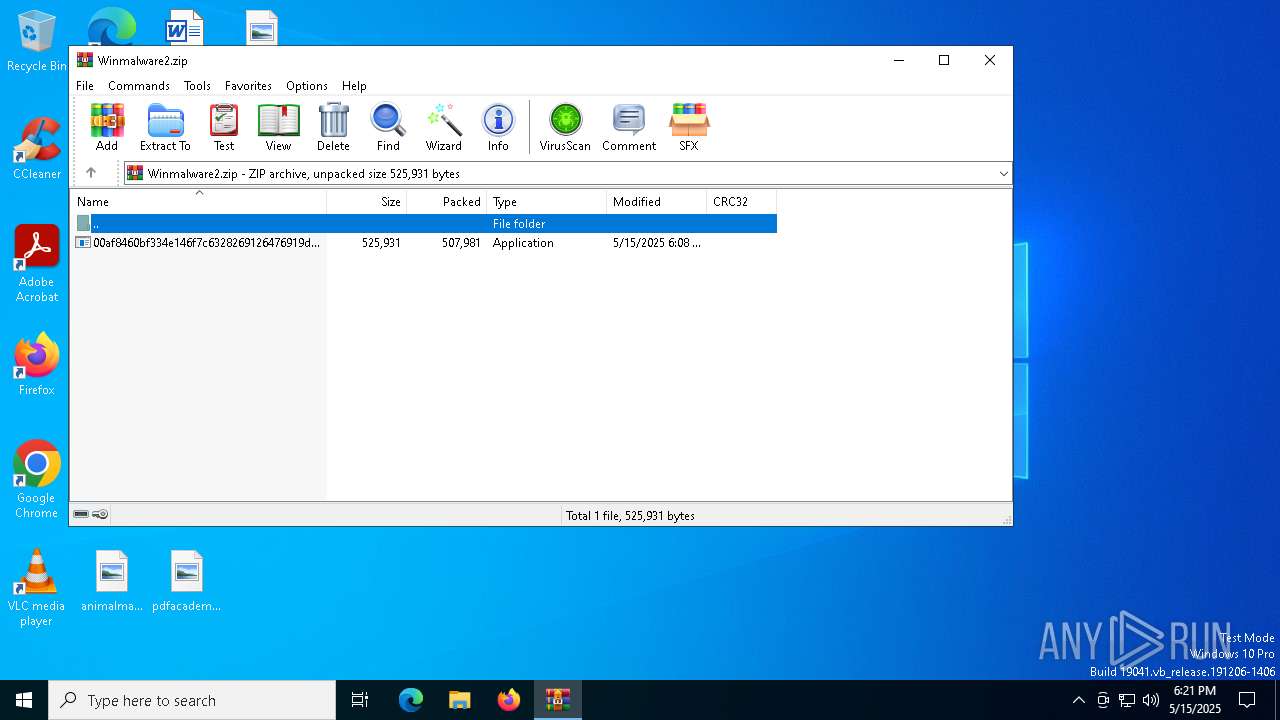
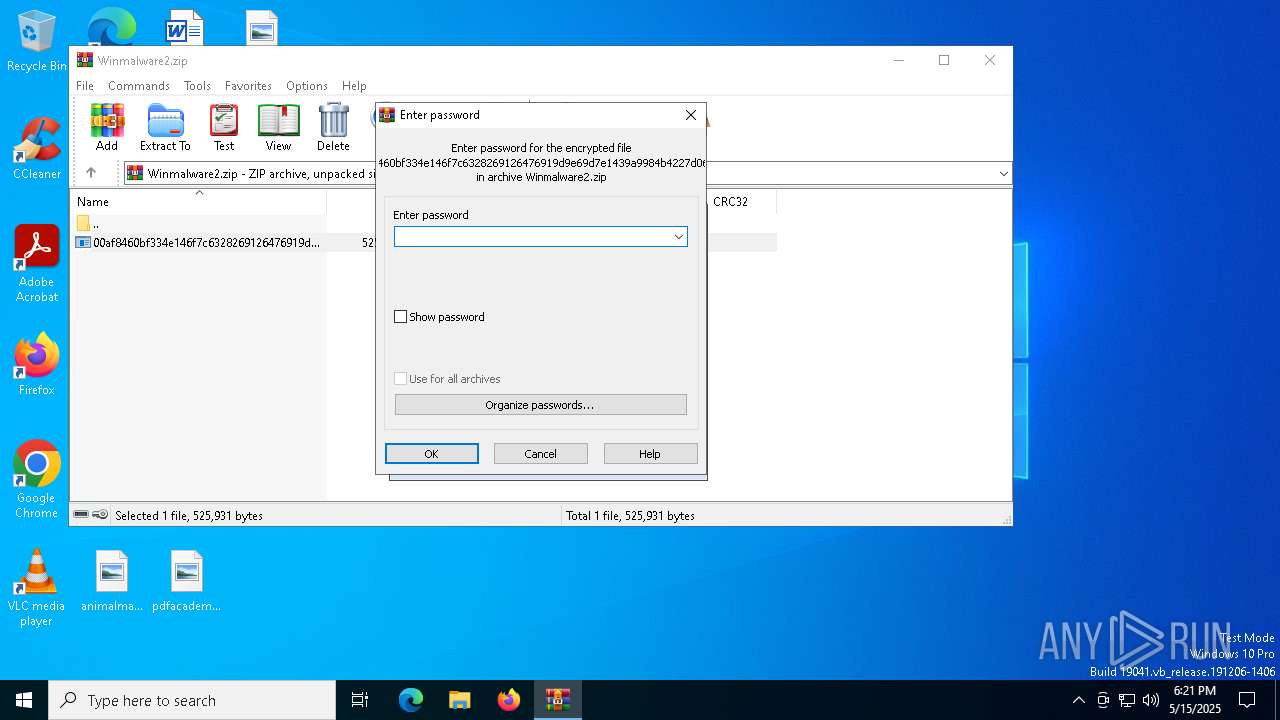
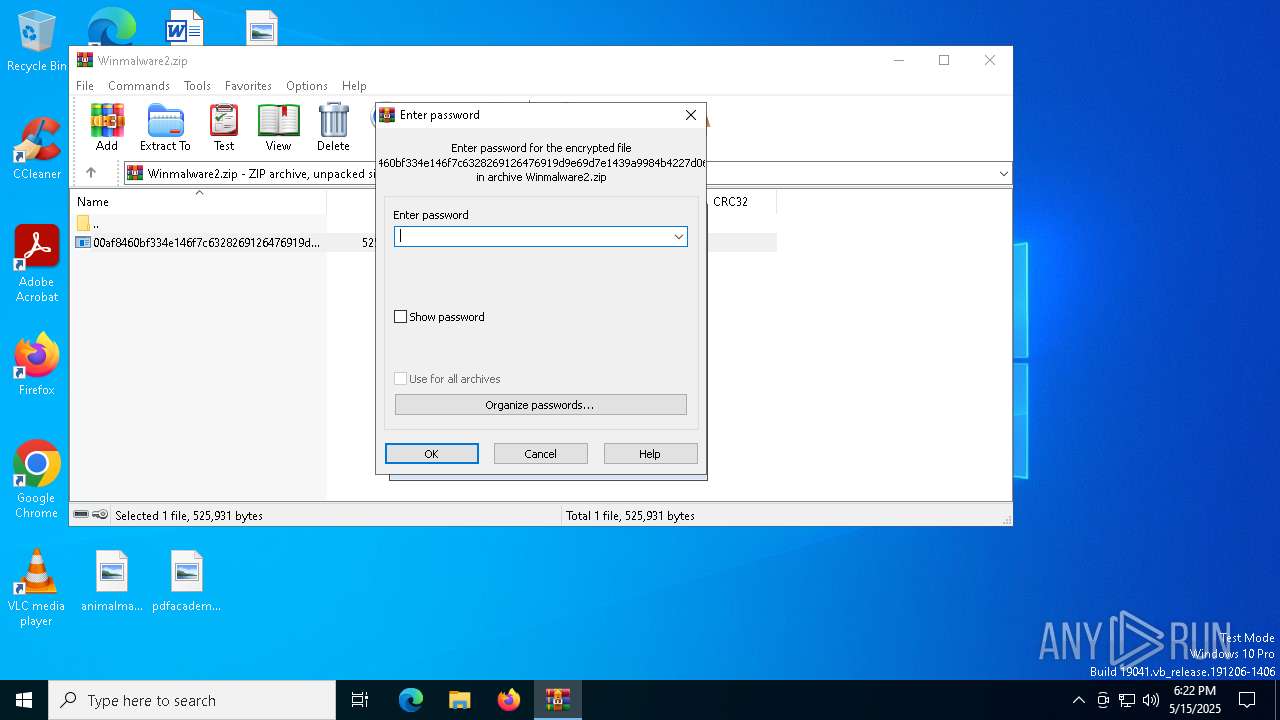
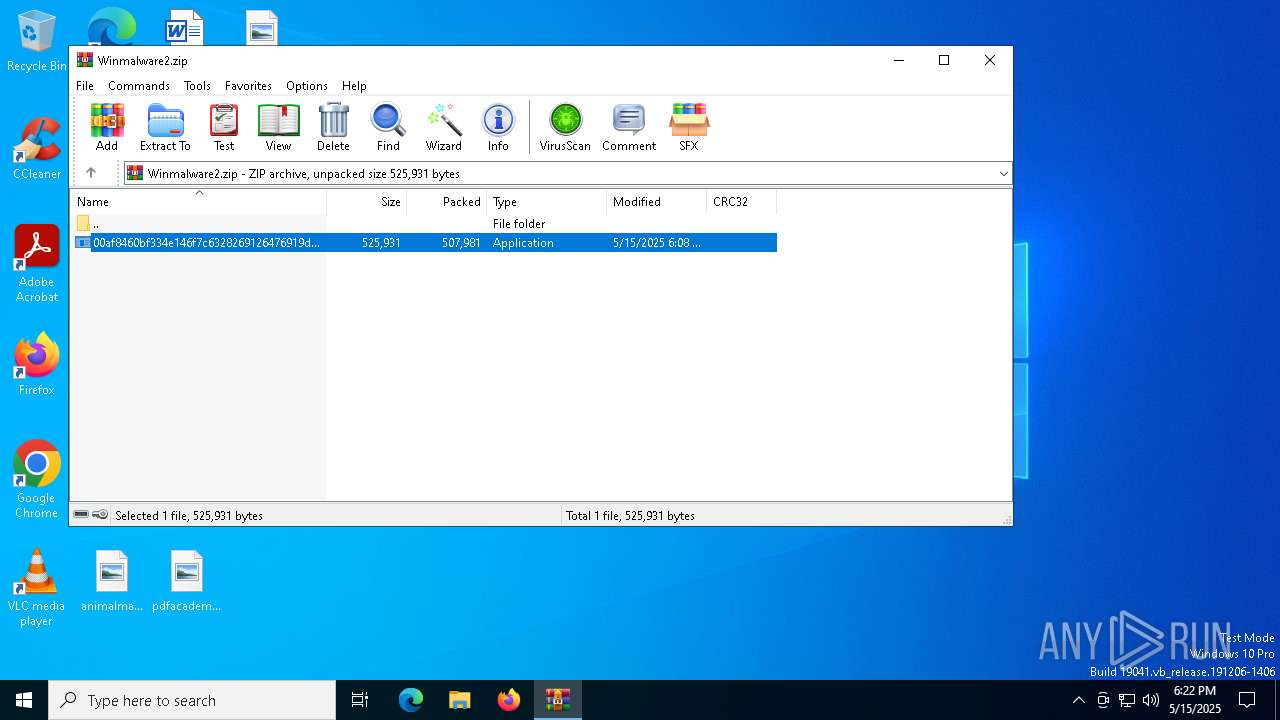
| File name: | Winmalware2.zip |
| Full analysis: | https://app.any.run/tasks/3f51eea6-c2d5-45c9-8b3d-54540e6bba9b |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 18:21:37 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 5FE7FB36BE8F6AEDC48A5703CEDAFDDC |
| SHA1: | 6FCADEFD469964272A8E5DCA15BF91876728F95B |
| SHA256: | 1F8A3D5F8C03BE105A824FFAA4D6D3C3E9518281DF0FDC599FCA0F9ED7E59BF3 |
| SSDEEP: | 24576:tBtRbsqfD3mAtsj/OXkgAvKqWIrb5pH8sAcr7F6//r3MnZ8CLC64Gt:tBtRbsqf6Atsj/OXkgAvKqWIr1pH8sAY |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2320)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2320)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 660)
Executable content was dropped or overwritten
- powershell.exe (PID: 660)
Connects to the server without a host name
- msiexec.exe (PID: 1568)
Starts POWERSHELL.EXE for commands execution
- 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe (PID: 4428)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 660)
INFO
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 660)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 660)
Gets data length (POWERSHELL)
- powershell.exe (PID: 660)
The sample compiled with english language support
- powershell.exe (PID: 660)
- WinRAR.exe (PID: 2320)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1568)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 660)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 660)
Checks proxy server information
- msiexec.exe (PID: 1568)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2320)
Checks supported languages
- 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe (PID: 4428)
Create files in a temporary directory
- 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe (PID: 4428)
Reads the computer name
- 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe (PID: 4428)
Creates files or folders in the user directory
- 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe (PID: 4428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:15 18:08:44 |
| ZipCRC: | 0xe3196897 |
| ZipCompressedSize: | 507981 |
| ZipUncompressedSize: | 525931 |
| ZipFileName: | 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe |
Total processes
135
Monitored processes
7
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "powershell.exe" -windowstyle minimized "$Limites=gc -Raw 'C:\Users\admin\AppData\Roaming\arbejdskrfters\ymeres\certifikatpligten\Balija.Pen';$Pedometrically=$Limites.SubString(40041,3);.$Pedometrically($Limites)" "$Limites=gc -Raw 'C:\Users\admin\AppData\Roaming\arbejdskrfters\ymeres\certifikatpligten\Balija.Pen';$Pedometrically=$Limites.SubString(40041,3);.$Pedometrically($Limites)" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | "C:\WINDOWS\SysWOW64\msiexec.exe" | C:\Windows\SysWOW64\msiexec.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Winmalware2.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4428 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2320.11939\00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2320.11939\00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe | — | WinRAR.exe | |||||||||||
User: admin Company: skovgrnsernes Integrity Level: MEDIUM Description: tilsjofledes signy teknikumet Exit code: 4294967295 Modules
| |||||||||||||||
| 5048 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5408 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6872 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 170
Read events
10 159
Write events
11
Delete events
0
Modification events
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Winmalware2.zip | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4428) 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe | Key: | HKEY_CURRENT_USER\prydens\styrian\oleoresins |
| Operation: | write | Name: | professionals |
Value: 1FB272 | |||
Executable files
2
Suspicious files
8
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4428 | 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe | C:\Users\admin\AppData\Roaming\arbejdskrfters\ymeres\certifikatpligten\Balija.Pen | text | |
MD5:AB67BDFB35AE2DE3E05BE0911750123D | SHA256:DD17C10E7B01056C2AFAD81F8E9EBDB367754D8861A96DA484BD1D679DC1F874 | |||
| 2320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2320.11939\00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe | executable | |
MD5:F68C9EE5BAF1F69A879EF27A8FD4E3D9 | SHA256:00AF8460BF334E146F7C6328269126476919D9E69D7E1439A9984B4227D06591 | |||
| 4428 | 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe | C:\Users\admin\AppData\Roaming\arbejdskrfters\ymeres\certifikatpligten\Afskridtedes\Netstatus.jpg | image | |
MD5:22F316F3F0218F9C3CC1F5C79DFB5752 | SHA256:FF5CB1A7C5EF1F5CC6E44EB93ACB8C2802CE1C1F4CF9907E6ADB1B22E1F8E11D | |||
| 4428 | 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe | C:\Users\admin\AppData\Roaming\arbejdskrfters\ymeres\certifikatpligten\Tilsendte.Tol | binary | |
MD5:D1E0CD01D06FC916628FE85D74BB271B | SHA256:4B8C984DA63E376267C3B2C23B3D79F8D59711EC124FE6C01199FCD67FD60954 | |||
| 4428 | 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe | C:\Users\admin\AppData\Roaming\arbejdskrfters\ymeres\certifikatpligten\Afskridtedes\Markrpositions.ini | text | |
MD5:A2CCF5E023D7773E8C73DC7EB6F81F05 | SHA256:FCD5AD634909535143BD0D8798625A377C8D217417BAB4B00768349A7CAA452A | |||
| 4428 | 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe | C:\Users\admin\AppData\Roaming\arbejdskrfters\ymeres\certifikatpligten\Afskridtedes\munkeordnerne.pol | binary | |
MD5:C15F434E740C7A3BD904A8292A226F6F | SHA256:8D0D6DB5C400E0FE3241C749A6BA272A5F567F03D308BDDDFD679828243B82C3 | |||
| 4428 | 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe | C:\Users\admin\AppData\Roaming\arbejdskrfters\ymeres\certifikatpligten\Afskridtedes\ouverturen.ini | binary | |
MD5:9525B25E33119C9FD95EAB4A79F9F244 | SHA256:E711AEC1CD2BAE505CF1387BBFB6DEEA7C9DDF338948A2B44C22E86C9F151154 | |||
| 4428 | 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe | C:\Users\admin\AppData\Roaming\arbejdskrfters\ymeres\certifikatpligten\Afskridtedes\Heredes.ini | text | |
MD5:5B1E73C4F05F69D079AC262B0E46ED41 | SHA256:22287491EFFA705126FC3268494EDEFF9474677DE1969322E9C23091AAAD0B5F | |||
| 4428 | 00af8460bf334e146f7c6328269126476919d9e69d7e1439a9984b4227d06591.exe | C:\Users\admin\AppData\Roaming\arbejdskrfters\ymeres\certifikatpligten\Afskridtedes\ingenirsekvensernes.pre | binary | |
MD5:7A60EC14504DEA7D547407850100DDF7 | SHA256:1A50D79C41680CDDEF3F3F50F6990FC2D86E885A8E64C7095EF23F4EB2FEDD48 | |||
| 660 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_y1kiir1t.zxi.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
20
DNS requests
13
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 88.221.110.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2772 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1568 | msiexec.exe | GET | — | 185.29.9.64:80 | http://185.29.9.64/gKihuwGhxt122.bin | unknown | — | — | unknown |
2772 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 88.221.110.114:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1568 | msiexec.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |