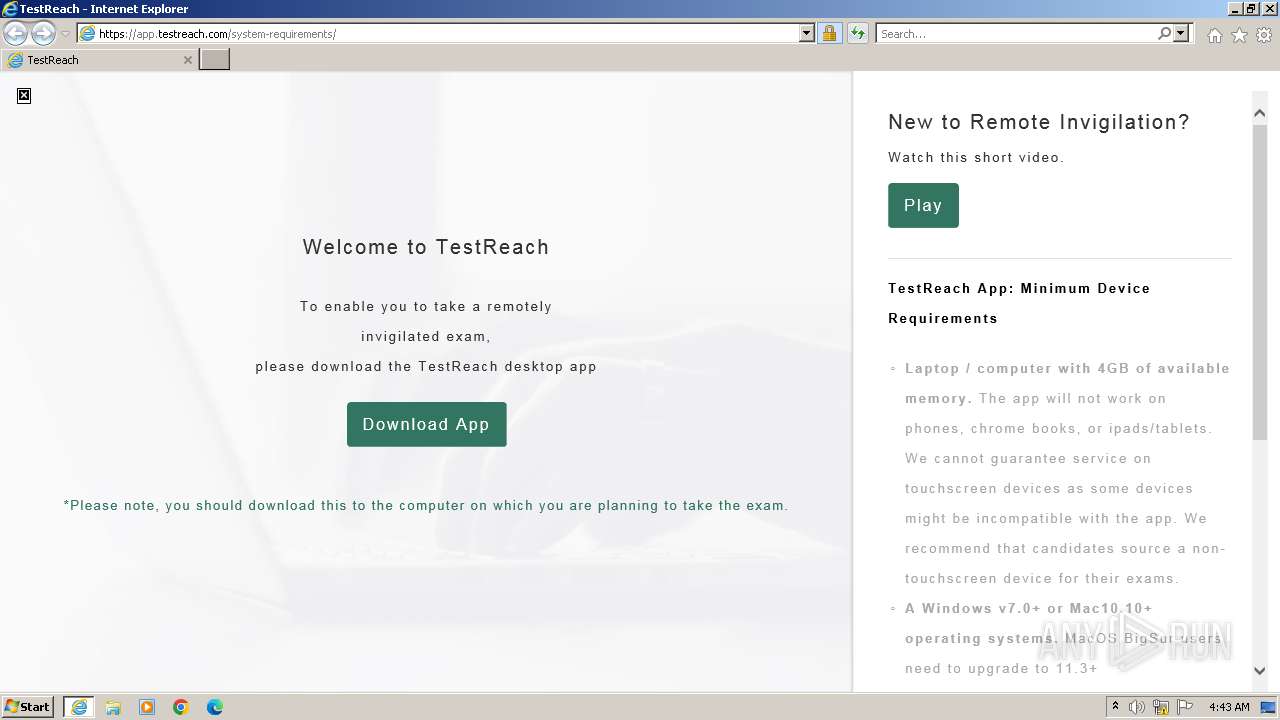
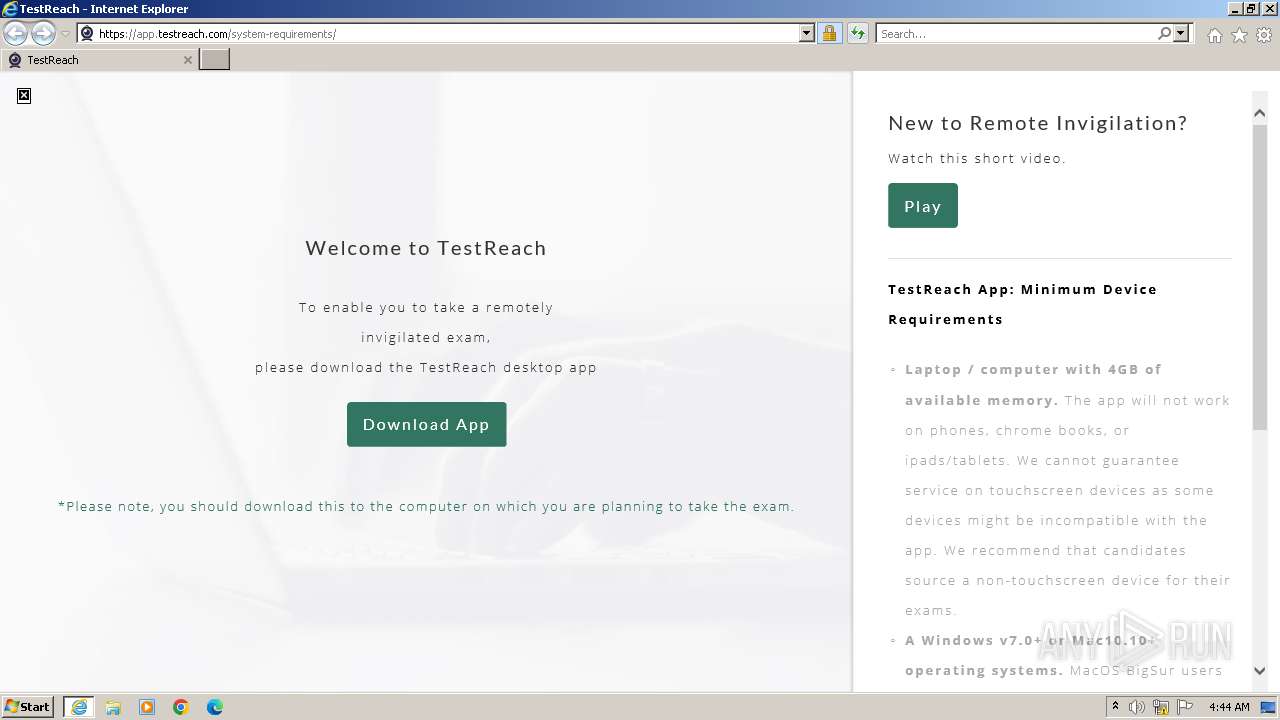
| URL: | https://app.testreach.com/system-requirements/ |
| Full analysis: | https://app.any.run/tasks/98a3026d-ba5e-40d1-bf4e-8c977fc6e151 |
| Verdict: | Malicious activity |
| Analysis date: | June 06, 2024, 03:43:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 58EFD02C8540080D488FA9E266D2068E |
| SHA1: | 7411740402FFD0CEFFE0E1808036E7F89FEEFFCF |
| SHA256: | 1F7E0BFCFC992DC5584DF61D0BC89EF76D79D1C9CFAD45A20E72867C01C50655 |
| SSDEEP: | 3:N8aaWxYVWRAIFMI/:2abpAAJ/ |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 1212)
- TestReach.exe (PID: 2676)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 2512)
Process drops legitimate windows executable
- msiexec.exe (PID: 1212)
Checks Windows Trust Settings
- msiexec.exe (PID: 1212)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 1212)
Reads the Internet Settings
- TestReach.exe (PID: 2676)
- WMIC.exe (PID: 3440)
- WMIC.exe (PID: 3452)
- WMIC.exe (PID: 3932)
- WMIC.exe (PID: 3456)
- WMIC.exe (PID: 3776)
- WMIC.exe (PID: 1604)
- WMIC.exe (PID: 1852)
- WMIC.exe (PID: 2072)
- WMIC.exe (PID: 3632)
- WMIC.exe (PID: 3624)
- WMIC.exe (PID: 2024)
- WMIC.exe (PID: 676)
- WMIC.exe (PID: 3812)
- WMIC.exe (PID: 992)
- WMIC.exe (PID: 2704)
- WMIC.exe (PID: 3364)
- WMIC.exe (PID: 736)
- WMIC.exe (PID: 2404)
- WMIC.exe (PID: 3268)
- WMIC.exe (PID: 3280)
- WMIC.exe (PID: 3284)
- WMIC.exe (PID: 2736)
- WMIC.exe (PID: 3788)
- WMIC.exe (PID: 3808)
- WMIC.exe (PID: 1080)
- WMIC.exe (PID: 616)
- WMIC.exe (PID: 1764)
Application launched itself
- TestReach.exe (PID: 2676)
Executable content was dropped or overwritten
- TestReach.exe (PID: 2676)
Reads settings of System Certificates
- TestReach.exe (PID: 2668)
Starts CMD.EXE for commands execution
- TestReach.exe (PID: 2776)
Uses WMIC.EXE to obtain system information
- cmd.exe (PID: 3144)
- cmd.exe (PID: 1596)
- cmd.exe (PID: 3072)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 3104)
- cmd.exe (PID: 3092)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 580)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 3016)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 3104)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 2800)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- cmd.exe (PID: 3092)
- cmd.exe (PID: 580)
- cmd.exe (PID: 3016)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 3092)
- cmd.exe (PID: 580)
- cmd.exe (PID: 3016)
Uses WMIC.EXE to obtain data on processes
- cmd.exe (PID: 3104)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 2800)
Accesses computer name via WMI (SCRIPT)
- WMIC.exe (PID: 3456)
- WMIC.exe (PID: 3624)
Uses WMIC.EXE to obtain information about the network interface controller
- cmd.exe (PID: 3104)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 2800)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 2244)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 3104)
INFO
Application launched itself
- iexplore.exe (PID: 3988)
Reads the computer name
- wmpnscfg.exe (PID: 768)
- msiexec.exe (PID: 1212)
- TestReach.exe (PID: 2676)
- TestReach.exe (PID: 2732)
- TestReach.exe (PID: 2668)
- TestReach.exe (PID: 3000)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3988)
Checks supported languages
- wmpnscfg.exe (PID: 768)
- msiexec.exe (PID: 1212)
- TestReach.exe (PID: 2676)
- TestReach.exe (PID: 2732)
- TestReach.exe (PID: 2668)
- TestReach.exe (PID: 2776)
- TestReach.exe (PID: 3000)
- TestReach.exe (PID: 3044)
- TestReach.exe (PID: 3520)
- TestReach.exe (PID: 3028)
Manual execution by a user
- wmpnscfg.exe (PID: 768)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 736)
Reads the machine GUID from the registry
- msiexec.exe (PID: 1212)
- TestReach.exe (PID: 2668)
Reads the software policy settings
- msiexec.exe (PID: 1212)
- msiexec.exe (PID: 736)
- TestReach.exe (PID: 2668)
The process uses the downloaded file
- iexplore.exe (PID: 3988)
Create files in a temporary directory
- msiexec.exe (PID: 1212)
- TestReach.exe (PID: 2676)
Creates files or folders in the user directory
- msiexec.exe (PID: 1212)
- TestReach.exe (PID: 2676)
- TestReach.exe (PID: 2668)
- TestReach.exe (PID: 2776)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1212)
Creates a software uninstall entry
- msiexec.exe (PID: 1212)
Process checks computer location settings
- TestReach.exe (PID: 2776)
- TestReach.exe (PID: 2676)
- TestReach.exe (PID: 3028)
- TestReach.exe (PID: 3044)
- TestReach.exe (PID: 3520)
Reads product name
- TestReach.exe (PID: 2776)
Reads Environment values
- TestReach.exe (PID: 2776)
Reads CPU info
- TestReach.exe (PID: 2776)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
102
Monitored processes
54
Malicious processes
4
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 580 | C:\Windows\system32\cmd.exe /d /s /c "wmic baseboard get Manufacturer,product,version,serialnumber & wmic computersystem get Manufacturer,OEMStringArray,Model & wmic csproduct get Name,Vendor" | C:\Windows\System32\cmd.exe | — | TestReach.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 616 | wmic csproduct get Name,Vendor | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 676 | wmic computersystem get /format:"C:\Windows\System32\wbem\en-us\csv" | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 736 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\TestReach-6.2.0.msi" | C:\Windows\System32\msiexec.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 736 | wmic nicconfig get /format:"C:\Windows\System32\wbem\en-us\csv" | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 768 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 992 | wmic computersystem get Manufacturer,OEMStringArray,Model | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1080 | wmic nicconfig get /format:"C:\Windows\System32\wbem\en-us\csv" | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1212 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | C:\Windows\system32\cmd.exe /d /s /c "wmic sysdriver get Description,name" | C:\Windows\System32\cmd.exe | — | TestReach.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
53 864
Read events
53 370
Write events
446
Delete events
48
Modification events
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31111107 | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31111107 | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
10
Suspicious files
177
Text files
44
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4052 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | der | |
MD5:A2F0F14049C896AC78BC01195966B87C | SHA256:BDC578858CC44239CCB689D977FC721BA1C299E866F2430B92BEDA4B6E206E05 | |||
| 4052 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:40B8194CCBFA1CD11B1D65584E0935BE | SHA256:5207CA8B1CF0DC56B93AF597B64DB41B1610F998A78F2701B9F966E8D6D57A72 | |||
| 4052 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | der | |
MD5:7582CA2C0E85A42D45975D00971CB390 | SHA256:280AC29CAF1CBF7770CF6A2794223A45C54E0B4169DD8883705777AC0DE7F2DF | |||
| 4052 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | der | |
MD5:5C146814452981224E30A1A099AFBF72 | SHA256:7C9E91F0F0A60107666794211526C50C78DA17E8B9915F0FF682A6F3ACCDF984 | |||
| 4052 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:547D30481C92725C51EEB4DC991E6611 | SHA256:8D21D42BAF9099FC6656919A695C13C4CB5319EAEBD7DF60A2FF74EA5E82FC8E | |||
| 4052 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:7C24FAEFA834F8965C35CD1F408E50B7 | SHA256:F6297516219EDD831ADCED07D28F9FEBC6594AD63CA193984221A6F5D39259A7 | |||
| 4052 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:8D1040B12A663CA4EC7277CFC1CE44F0 | SHA256:3086094D4198A5BBD12938B0D2D5F696C4DFC77E1EAE820ADDED346A59AA8727 | |||
| 4052 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\system-requirements[1].htm | html | |
MD5:78EBB8BF8B895FACEA17A2B84013BBB6 | SHA256:64665421E7B7F4777B6AE93BE027F136D9A4B09D7BC0EBB28D0C71C0EAEC43C1 | |||
| 4052 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:5DC910F0A599AC42BED1FCC1CB8D1889 | SHA256:7FA87AB18AC0637C349E0DA0FA2D02D50184172B157385A5F2F4942207FDE456 | |||
| 4052 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:69EF96D8A86D93527332D8B721A6923D | SHA256:0BC3F7CBE079CA59D131EBE677901F6C4AEA62D7FA299A65218C112EFB3D05C5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
68
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4052 | iexplore.exe | GET | 304 | 217.20.57.34:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?50242446d4326aec | unknown | — | — | unknown |
4052 | iexplore.exe | GET | 304 | 217.20.57.34:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6f8f941c1bb5cb08 | unknown | — | — | unknown |
4052 | iexplore.exe | GET | 200 | 108.138.2.173:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | — | — | unknown |
4052 | iexplore.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | — | — | unknown |
4052 | iexplore.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | unknown |
— | — | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
4052 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | unknown |
4052 | iexplore.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | — | — | unknown |
4052 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | unknown |
4052 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACECQyBTPXUvQOCpXwaId8vI4%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4052 | iexplore.exe | 18.245.86.126:443 | app.testreach.com | — | US | unknown |
4052 | iexplore.exe | 217.20.57.34:80 | ctldl.windowsupdate.com | — | US | unknown |
4052 | iexplore.exe | 108.138.2.173:80 | o.ss2.us | AMAZON-02 | US | unknown |
4052 | iexplore.exe | 18.66.142.79:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | unknown |
4052 | iexplore.exe | 142.250.185.138:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
4052 | iexplore.exe | 13.225.84.112:443 | d1rnvcroqs1811.cloudfront.net | AMAZON-02 | US | unknown |
4052 | iexplore.exe | 13.33.218.24:443 | www.datadoghq-browser-agent.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
app.testreach.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
www.datadoghq-browser-agent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
d1rnvcroqs1811.cloudfront.net |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
c.pki.goog |
| unknown |