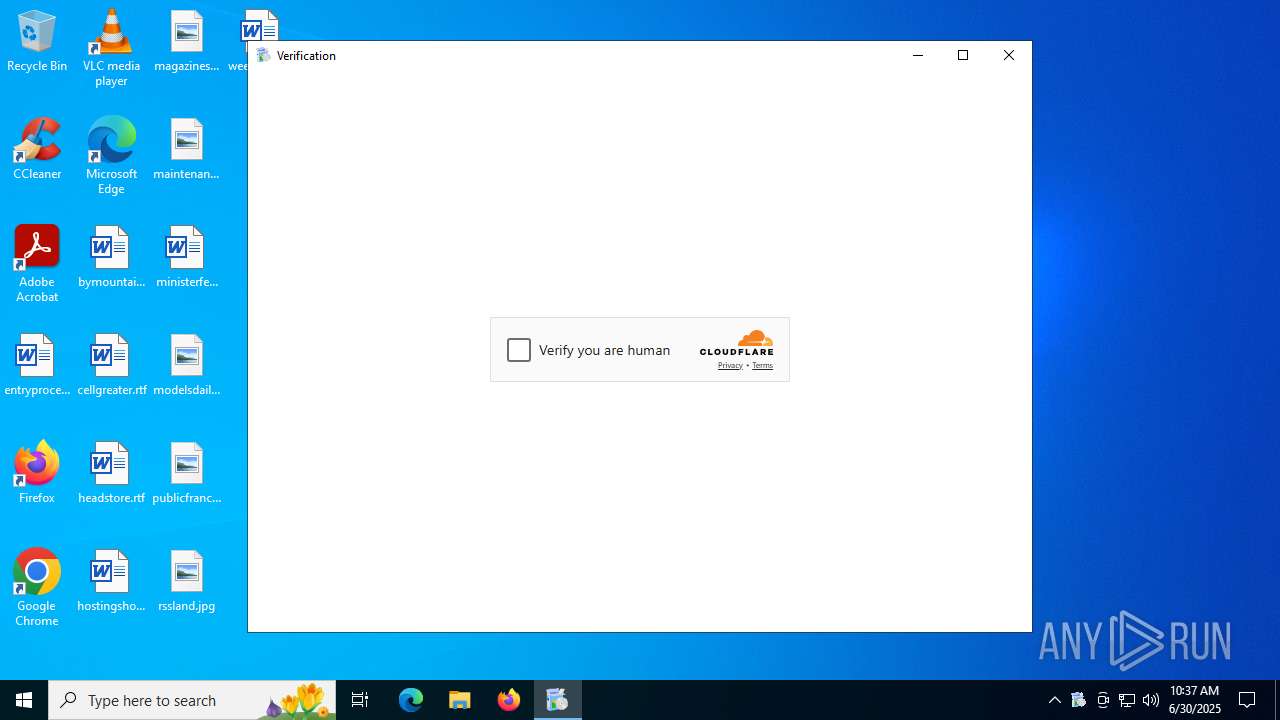
| File name: | TribeWars Setup 10.2.27.exe |
| Full analysis: | https://app.any.run/tasks/dddb5af9-3fa9-4bee-b8b9-ad5018fc1900 |
| Verdict: | Malicious activity |
| Analysis date: | June 30, 2025, 10:37:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 338D2F80BDC1DDB0F7B99C47CCBF12A4 |
| SHA1: | 9E0B823DDAD5363DDB47D5F35AE47DF2EDB4DF3C |
| SHA256: | 1F5823734E47720858F9D49060CDE39C3A7313D99198C65DCA70D67B2B1EFF0C |
| SSDEEP: | 1572864:/BYKVzcooUSYOSd8gHgGgWaUp/T9R5Qhb:/2KVzhP7HgGgWaU3R5Ib |
MALICIOUS
Executing a file with an untrusted certificate
- TribeWars Setup 10.2.27.exe (PID: 6876)
- TribeWars Setup 10.2.27.exe (PID: 5712)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- TribeWars Setup 10.2.27.exe (PID: 6876)
The process creates files with name similar to system file names
- TribeWars Setup 10.2.27.exe (PID: 6876)
Reads security settings of Internet Explorer
- TribeWars Setup 10.2.27.exe (PID: 6876)
- TribeWars.exe (PID: 1336)
Drops 7-zip archiver for unpacking
- TribeWars Setup 10.2.27.exe (PID: 6876)
Process drops legitimate windows executable
- TribeWars Setup 10.2.27.exe (PID: 6876)
- TribeWars.exe (PID: 1336)
Creates a software uninstall entry
- TribeWars Setup 10.2.27.exe (PID: 6876)
Executable content was dropped or overwritten
- TribeWars Setup 10.2.27.exe (PID: 6876)
- TribeWars.exe (PID: 1336)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5992)
- cmd.exe (PID: 7072)
- cmd.exe (PID: 5424)
- cmd.exe (PID: 7544)
- cmd.exe (PID: 7836)
- cmd.exe (PID: 8160)
- cmd.exe (PID: 7340)
- cmd.exe (PID: 7352)
- cmd.exe (PID: 2160)
- cmd.exe (PID: 7648)
- cmd.exe (PID: 7408)
Starts CMD.EXE for commands execution
- TribeWars.exe (PID: 1336)
- TribeWars.exe (PID: 5400)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 6264)
- cmd.exe (PID: 6520)
- cmd.exe (PID: 7696)
- cmd.exe (PID: 7284)
- cmd.exe (PID: 2808)
Application launched itself
- TribeWars.exe (PID: 1336)
- TribeWars.exe (PID: 5400)
Process drops python dynamic module
- TribeWars.exe (PID: 1336)
Reads the date of Windows installation
- TribeWars.exe (PID: 1336)
The process drops C-runtime libraries
- TribeWars.exe (PID: 1336)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 1300)
- WMIC.exe (PID: 1216)
- WMIC.exe (PID: 7748)
- WMIC.exe (PID: 7480)
- WMIC.exe (PID: 6128)
INFO
The sample compiled with english language support
- TribeWars Setup 10.2.27.exe (PID: 6876)
- TribeWars.exe (PID: 1336)
Checks supported languages
- TribeWars Setup 10.2.27.exe (PID: 6876)
- TribeWars.exe (PID: 4044)
- TribeWars.exe (PID: 1336)
- TribeWars.exe (PID: 4816)
- TribeWars.exe (PID: 3944)
- TribeWars.exe (PID: 4960)
- TribeWars.exe (PID: 5400)
- TribeWars.exe (PID: 2216)
- TribeWars.exe (PID: 2804)
- TribeWars.exe (PID: 6836)
- TribeWars.exe (PID: 5564)
Create files in a temporary directory
- TribeWars Setup 10.2.27.exe (PID: 6876)
- TribeWars.exe (PID: 1336)
- TribeWars.exe (PID: 5400)
Reads the computer name
- TribeWars Setup 10.2.27.exe (PID: 6876)
- TribeWars.exe (PID: 1336)
- TribeWars.exe (PID: 4044)
- TribeWars.exe (PID: 2216)
- TribeWars.exe (PID: 5400)
- TribeWars.exe (PID: 2804)
- TribeWars.exe (PID: 6836)
Creates files in the program directory
- TribeWars Setup 10.2.27.exe (PID: 6876)
Manual execution by a user
- TribeWars.exe (PID: 3800)
- TribeWars.exe (PID: 1336)
- cmd.exe (PID: 8072)
- notepad.exe (PID: 5244)
- OpenWith.exe (PID: 8084)
Creates files or folders in the user directory
- TribeWars Setup 10.2.27.exe (PID: 6876)
- TribeWars.exe (PID: 1336)
- TribeWars.exe (PID: 2216)
- TribeWars.exe (PID: 5400)
- TribeWars.exe (PID: 6836)
Reads product name
- TribeWars.exe (PID: 1336)
- TribeWars.exe (PID: 5400)
Reads Environment values
- TribeWars.exe (PID: 1336)
- TribeWars.exe (PID: 5400)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1300)
- WMIC.exe (PID: 1216)
- WMIC.exe (PID: 7748)
- notepad.exe (PID: 5244)
- WMIC.exe (PID: 6128)
- WMIC.exe (PID: 7480)
Process checks computer location settings
- TribeWars.exe (PID: 1336)
- TribeWars.exe (PID: 4816)
- TribeWars.exe (PID: 4960)
- TribeWars.exe (PID: 3944)
- TribeWars.exe (PID: 5400)
- TribeWars.exe (PID: 5564)
Reads CPU info
- TribeWars.exe (PID: 1336)
- TribeWars.exe (PID: 5400)
Reads the machine GUID from the registry
- TribeWars.exe (PID: 1336)
- TribeWars.exe (PID: 5400)
Checks proxy server information
- TribeWars.exe (PID: 1336)
- TribeWars.exe (PID: 5400)
- slui.exe (PID: 7980)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3608)
- powershell.exe (PID: 4168)
Reads Windows Product ID
- powershell.exe (PID: 7596)
- powershell.exe (PID: 3100)
- powershell.exe (PID: 7692)
Node.js compiler has been detected
- TribeWars.exe (PID: 1336)
Reads the software policy settings
- slui.exe (PID: 7980)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 8084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 22:26:14+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 473088 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x338f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.2.27.0 |
| ProductVersionNumber: | 10.2.27.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | TribeWars designed with cutting-edge cybersecurity measures, this application prioritizes user safety. |
| FileVersion: | 10.2.27 |
| LegalCopyright: | Copyright © 2025 TribeWars |
| ProductName: | TribeWars |
| ProductVersion: | 10.2.27 |
Total processes
202
Monitored processes
68
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 592 | powershell.exe -Command "(Get-CimInstance Win32_ComputerSystemProduct).UUID" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1212 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | wmic path win32_VideoController get name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | wmic path win32_VideoController get name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1336 | "C:\Program Files\TribeWars\TribeWars.exe" | C:\Program Files\TribeWars\TribeWars.exe | explorer.exe | ||||||||||||
User: admin Company: GitHub, Inc. Integrity Level: HIGH Description: TribeWars designed with cutting-edge cybersecurity measures, this application prioritizes user safety. Version: 10.2.27 Modules
| |||||||||||||||
| 2160 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell.exe -Command "(Get-CimInstance Win32_ComputerSystemProduct).UUID"" | C:\Windows\System32\cmd.exe | — | TribeWars.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2216 | "C:\Program Files\TribeWars\TribeWars.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --user-data-dir="C:\Users\admin\AppData\Roaming\TribeWars" --field-trial-handle=1916,i,3839292653697606189,8764772325148775987,262144 --enable-features=PdfUseShowSaveFilePicker --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit --variations-seed-version --mojo-platform-channel-handle=2172 /prefetch:3 | C:\Program Files\TribeWars\TribeWars.exe | TribeWars.exe | ||||||||||||
User: admin Company: GitHub, Inc. Integrity Level: HIGH Description: TribeWars designed with cutting-edge cybersecurity measures, this application prioritizes user safety. Version: 10.2.27 Modules
| |||||||||||||||
| 2596 | "C:\Program Files\TribeWars\TribeWars.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\TribeWars" --app-path="C:\Program Files\TribeWars\resources\app.asar" --no-sandbox --no-zygote --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=1916,i,3839292653697606189,8764772325148775987,262144 --enable-features=PdfUseShowSaveFilePicker --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit --variations-seed-version --mojo-platform-channel-handle=3508 /prefetch:1 | C:\Program Files\TribeWars\TribeWars.exe | — | TribeWars.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: HIGH Description: TribeWars designed with cutting-edge cybersecurity measures, this application prioritizes user safety. Exit code: 0 Version: 10.2.27 Modules
| |||||||||||||||
| 2804 | "C:\Program Files\TribeWars\TribeWars.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\TribeWars" --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=1868,i,1049388130966278802,4643420627023583204,262144 --enable-features=PdfUseShowSaveFilePicker --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit --variations-seed-version --mojo-platform-channel-handle=1848 /prefetch:2 | C:\Program Files\TribeWars\TribeWars.exe | — | TribeWars.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: LOW Description: TribeWars designed with cutting-edge cybersecurity measures, this application prioritizes user safety. Exit code: 0 Version: 10.2.27 Modules
| |||||||||||||||
Total events
55 089
Read events
55 017
Write events
18
Delete events
54
Modification events
| (PID) Process: | (6876) TribeWars Setup 10.2.27.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\5f153963-6af3-5c10-aafa-05db07f67181 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\TribeWars | |||
| (PID) Process: | (6876) TribeWars Setup 10.2.27.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\5f153963-6af3-5c10-aafa-05db07f67181 |
| Operation: | write | Name: | KeepShortcuts |
Value: true | |||
| (PID) Process: | (6876) TribeWars Setup 10.2.27.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\5f153963-6af3-5c10-aafa-05db07f67181 |
| Operation: | write | Name: | ShortcutName |
Value: TribeWars | |||
| (PID) Process: | (6876) TribeWars Setup 10.2.27.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\5f153963-6af3-5c10-aafa-05db07f67181 |
| Operation: | write | Name: | DisplayName |
Value: TribeWars 10.2.27 | |||
| (PID) Process: | (6876) TribeWars Setup 10.2.27.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\5f153963-6af3-5c10-aafa-05db07f67181 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\TribeWars\Uninstall TribeWars.exe" /allusers | |||
| (PID) Process: | (6876) TribeWars Setup 10.2.27.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\5f153963-6af3-5c10-aafa-05db07f67181 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Program Files\TribeWars\Uninstall TribeWars.exe" /allusers /S | |||
| (PID) Process: | (6876) TribeWars Setup 10.2.27.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\5f153963-6af3-5c10-aafa-05db07f67181 |
| Operation: | write | Name: | DisplayVersion |
Value: 10.2.27 | |||
| (PID) Process: | (6876) TribeWars Setup 10.2.27.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\5f153963-6af3-5c10-aafa-05db07f67181 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\TribeWars\TribeWars.exe,0 | |||
| (PID) Process: | (6876) TribeWars Setup 10.2.27.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\5f153963-6af3-5c10-aafa-05db07f67181 |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (6876) TribeWars Setup 10.2.27.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\5f153963-6af3-5c10-aafa-05db07f67181 |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
Executable files
49
Suspicious files
206
Text files
139
Unknown types
139
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6876 | TribeWars Setup 10.2.27.exe | C:\Users\admin\AppData\Local\Temp\nsb77A2.tmp\app-64.7z | — | |
MD5:— | SHA256:— | |||
| 6876 | TribeWars Setup 10.2.27.exe | C:\Users\admin\AppData\Local\Temp\nsb77A2.tmp\7z-out\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 6876 | TribeWars Setup 10.2.27.exe | C:\Users\admin\AppData\Local\Temp\nsb77A2.tmp\7z-out\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 6876 | TribeWars Setup 10.2.27.exe | C:\Users\admin\AppData\Local\Temp\nsb77A2.tmp\nsProcess.dll | executable | |
MD5:F0438A894F3A7E01A4AAE8D1B5DD0289 | SHA256:30C6C3DD3CC7FCEA6E6081CE821ADC7B2888542DAE30BF00E881C0A105EB4D11 | |||
| 6876 | TribeWars Setup 10.2.27.exe | C:\Users\admin\AppData\Local\Temp\nsb77A2.tmp\StdUtils.dll | executable | |
MD5:C6A6E03F77C313B267498515488C5740 | SHA256:B72E9013A6204E9F01076DC38DABBF30870D44DFC66962ADBF73619D4331601E | |||
| 6876 | TribeWars Setup 10.2.27.exe | C:\Users\admin\AppData\Local\Temp\nsb77A2.tmp\7z-out\LICENSE.electron.txt | text | |
MD5:4D42118D35941E0F664DDDBD83F633C5 | SHA256:5154E165BD6C2CC0CFBCD8916498C7ABAB0497923BAFCD5CB07673FE8480087D | |||
| 6876 | TribeWars Setup 10.2.27.exe | C:\Users\admin\AppData\Local\Temp\nsb77A2.tmp\System.dll | executable | |
MD5:0D7AD4F45DC6F5AA87F606D0331C6901 | SHA256:3EB38AE99653A7DBC724132EE240F6E5C4AF4BFE7C01D31D23FAF373F9F2EACA | |||
| 6876 | TribeWars Setup 10.2.27.exe | C:\Users\admin\AppData\Local\Temp\nsb77A2.tmp\7z-out\locales\am.pak | pgc | |
MD5:AC46141BE8E9F9784CDCB942B7FCA1E0 | SHA256:EC212255CCF8D31D00F179D37A361E7D28DC29C2EBEC52F2D354D9359E115B9F | |||
| 6876 | TribeWars Setup 10.2.27.exe | C:\Users\admin\AppData\Local\Temp\nsb77A2.tmp\nsis7z.dll | executable | |
MD5:80E44CE4895304C6A3A831310FBF8CD0 | SHA256:B393F05E8FF919EF071181050E1873C9A776E1A0AE8329AEFFF7007D0CADF592 | |||
| 6876 | TribeWars Setup 10.2.27.exe | C:\Users\admin\AppData\Local\Temp\nsb77A2.tmp\7z-out\chrome_200_percent.pak | pgc | |
MD5:3C2498DA8019596DFD760412E71E019C | SHA256:0EC6C7CB89256736AE3BACB06C6B6E2B2EEE92F79D395BD76B372197FB4D07F4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
30
DNS requests
22
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5060 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6344 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5060 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
592 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6344 | svchost.exe | 20.190.160.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6344 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
macattic.com |
| unknown |
challenges.cloudflare.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2216 | TribeWars.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2216 | TribeWars.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2216 | TribeWars.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2216 | TribeWars.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2216 | TribeWars.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2216 | TribeWars.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |