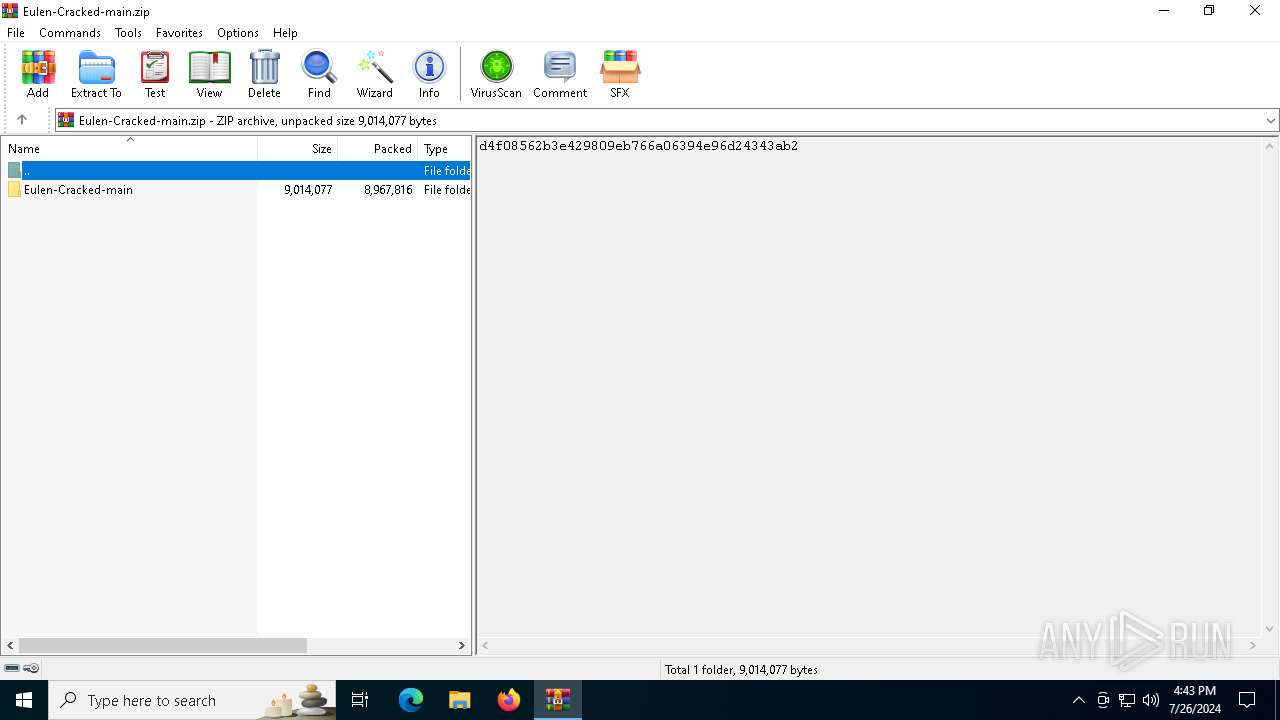
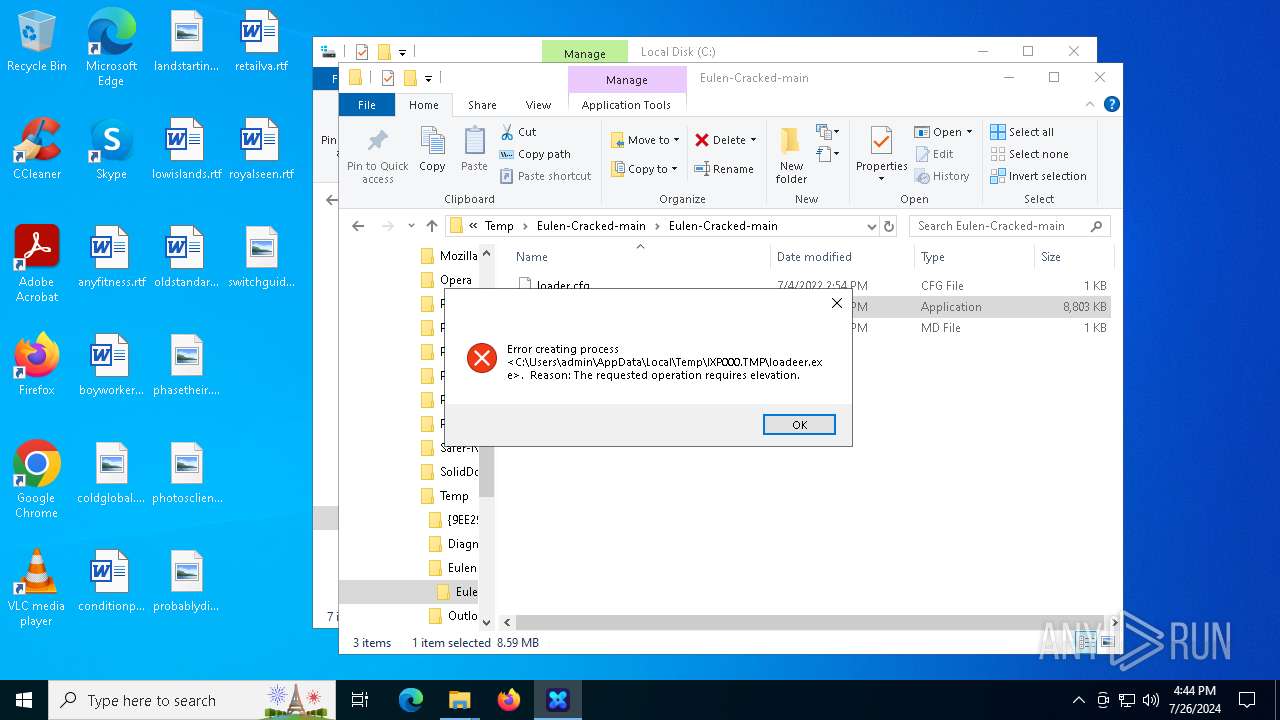
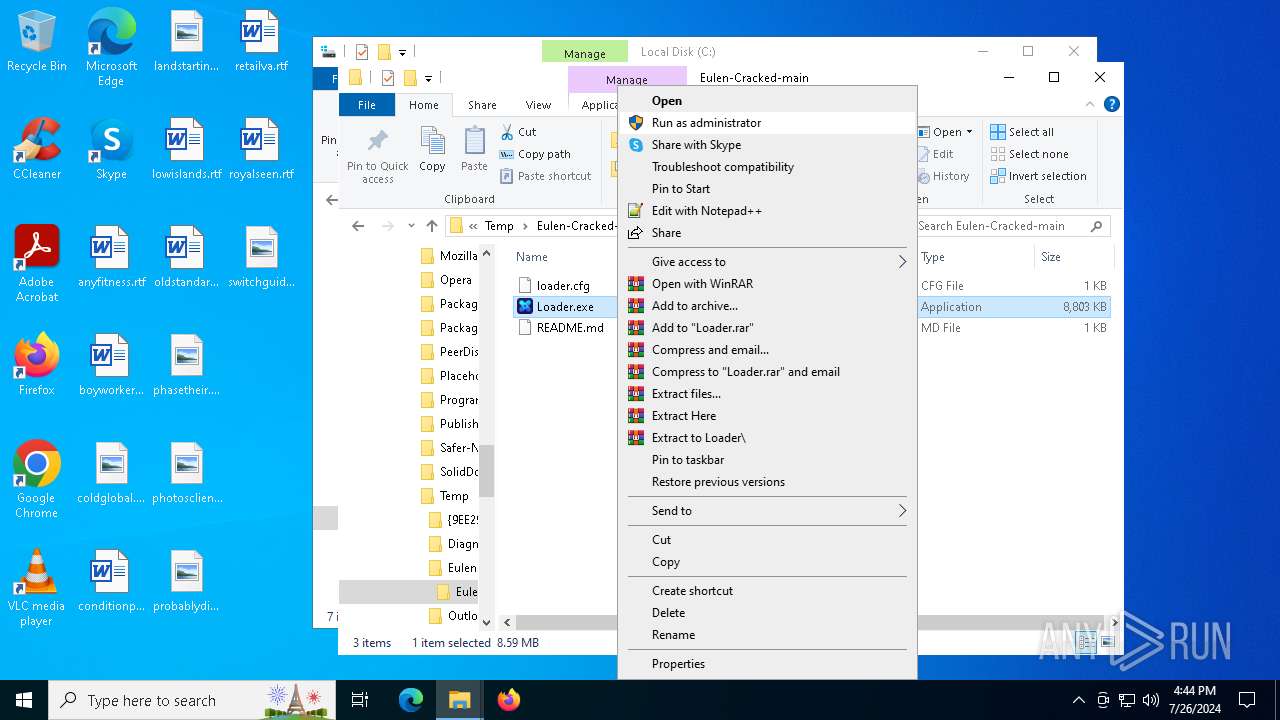
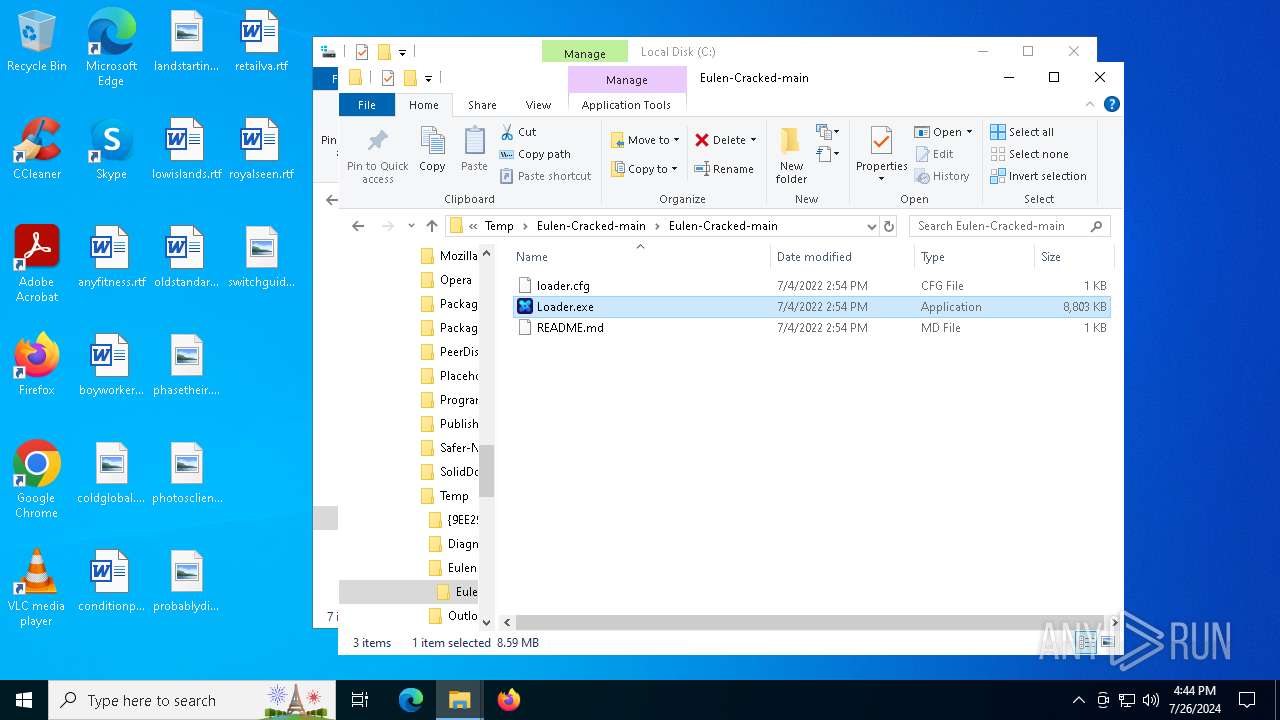
| File name: | Eulen-Cracked-main.zip |
| Full analysis: | https://app.any.run/tasks/e517d178-53df-4d21-99b8-2baa3a07bddf |
| Verdict: | Malicious activity |
| Analysis date: | July 26, 2024, 16:43:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | E8D145FB456531151F67E3AC02B8E1EF |
| SHA1: | 636351CE422CAA31BB2A380AC55CEAEEAB534031 |
| SHA256: | 1F3E0CB4529E623E771D5426395ADAB37FE0CE11E987EDABFF7025B4EE7E716A |
| SSDEEP: | 98304:9sYg+ZS4bJNP9SIzwAAX6xnkO/63fuxzhj3OYdpi9mNdpo9lQkDi9qZXOvD1SvdB:wvD4E5SdsL5 |
MALICIOUS
Changes the autorun value in the registry
- Loader.exe (PID: 1176)
Drops the executable file immediately after the start
- Loader.exe (PID: 3980)
- Loader.exe (PID: 1176)
- WinRAR.exe (PID: 6176)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6176)
Starts a Microsoft application from unusual location
- Loader.exe (PID: 3980)
- Loader.exe (PID: 1176)
Executable content was dropped or overwritten
- Loader.exe (PID: 3980)
- Loader.exe (PID: 1176)
Connects to unusual port
- loadeer.exe (PID: 2432)
INFO
Checks proxy server information
- slui.exe (PID: 4816)
Reads the software policy settings
- slui.exe (PID: 4816)
Checks supported languages
- Loader.exe (PID: 3980)
- Loader.exe (PID: 1176)
- loadeer.exe (PID: 2432)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6176)
Create files in a temporary directory
- Loader.exe (PID: 3980)
- Loader.exe (PID: 1176)
Manual execution by a user
- Loader.exe (PID: 3980)
- Loader.exe (PID: 1176)
Reads the computer name
- Loader.exe (PID: 3980)
- loadeer.exe (PID: 2432)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:07:04 07:54:20 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Eulen-Cracked-main/ |
Total processes
146
Monitored processes
6
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1176 | "C:\Users\admin\AppData\Local\Temp\Eulen-Cracked-main\Eulen-Cracked-main\Loader.exe" | C:\Users\admin\AppData\Local\Temp\Eulen-Cracked-main\Eulen-Cracked-main\Loader.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2432 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\loadeer.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\loadeer.exe | Loader.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 3980 | "C:\Users\admin\AppData\Local\Temp\Eulen-Cracked-main\Eulen-Cracked-main\Loader.exe" | C:\Users\admin\AppData\Local\Temp\Eulen-Cracked-main\Eulen-Cracked-main\Loader.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 2147943140 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4816 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6176 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Eulen-Cracked-main.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7048 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\loadeer.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\loadeer.exe | — | Loader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
5 846
Read events
5 824
Write events
22
Delete events
0
Modification events
| (PID) Process: | (6176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Eulen-Cracked-main.zip | |||
| (PID) Process: | (6176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
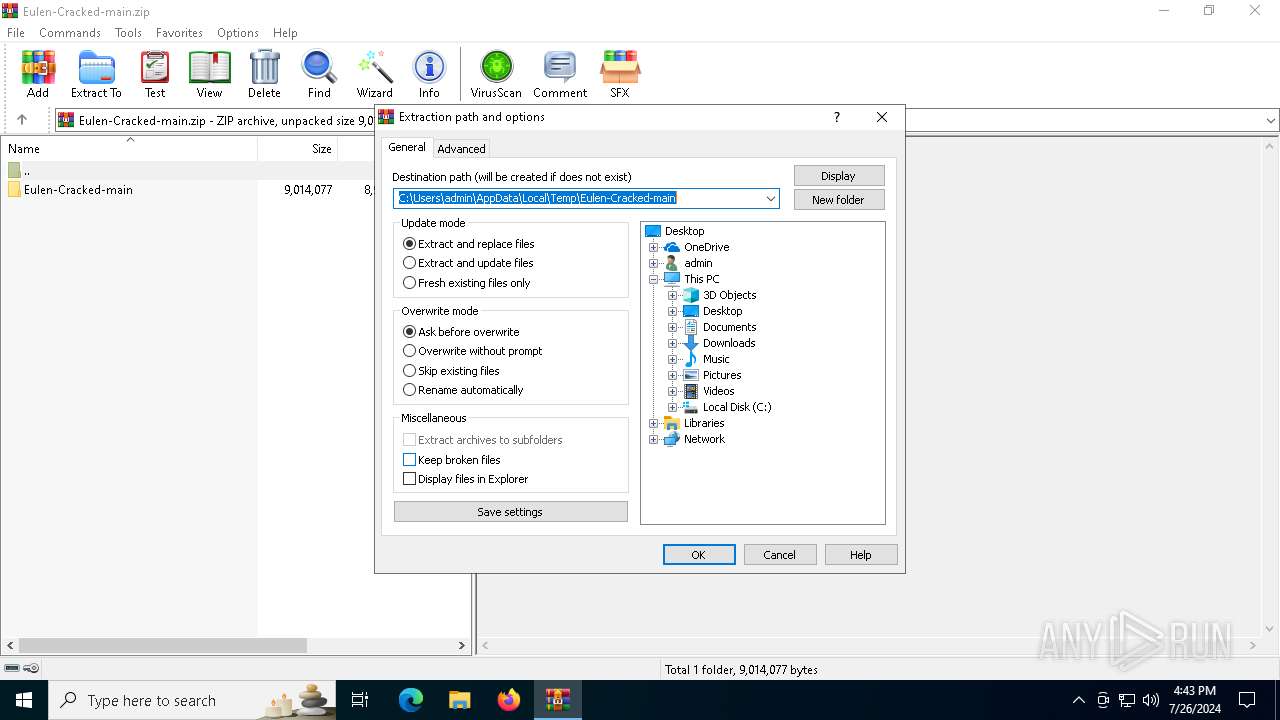
| (PID) Process: | (6176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Eulen-Cracked-main | |||
| (PID) Process: | (6176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
5
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Eulen-Cracked-main\Eulen-Cracked-main\loader.cfg | binary | |
MD5:14A5118095BD99B3ABEF308CDA92F9E7 | SHA256:946F3A29863B0BAA0C68C0594ADB02DDDDC52EF8EDDD1408EB50963A7BF87A1F | |||
| 1176 | Loader.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\loadeer.exe | executable | |
MD5:B6C5E0BA55C8DCCE8DB6989086329D7A | SHA256:B68178CD77A440CDF799BB7722368A6533E1FCA98B90BFFD559BE883A873699B | |||
| 6176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Eulen-Cracked-main\Eulen-Cracked-main\README.md | text | |
MD5:A26EE933676AA2825BB3E2E7CF6308CE | SHA256:377FD78E49817A95056934CA0403260B1EF106D7A64E81F67A237DFA27F6548B | |||
| 1176 | Loader.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\Loader.exe | executable | |
MD5:D707F494103F17E0CF2CC256D1A75290 | SHA256:63CC4CD86A4B3EF683FDB8C17A7245628AE51532F0CE594818F9CBA6A47F05AE | |||
| 3980 | Loader.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\Loader.exe | executable | |
MD5:D707F494103F17E0CF2CC256D1A75290 | SHA256:63CC4CD86A4B3EF683FDB8C17A7245628AE51532F0CE594818F9CBA6A47F05AE | |||
| 3980 | Loader.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\loadeer.exe | executable | |
MD5:B6C5E0BA55C8DCCE8DB6989086329D7A | SHA256:B68178CD77A440CDF799BB7722368A6533E1FCA98B90BFFD559BE883A873699B | |||
| 6176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Eulen-Cracked-main\Eulen-Cracked-main\Loader.exe | executable | |
MD5:5EB4067175A3B7AA668AAC004BA86F54 | SHA256:0B931CD2362516003F597243CD107C78F276B110E7ED6202C451ED0E1595E9DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
54
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2188 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
132 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | unknown |
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1292 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6564 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |