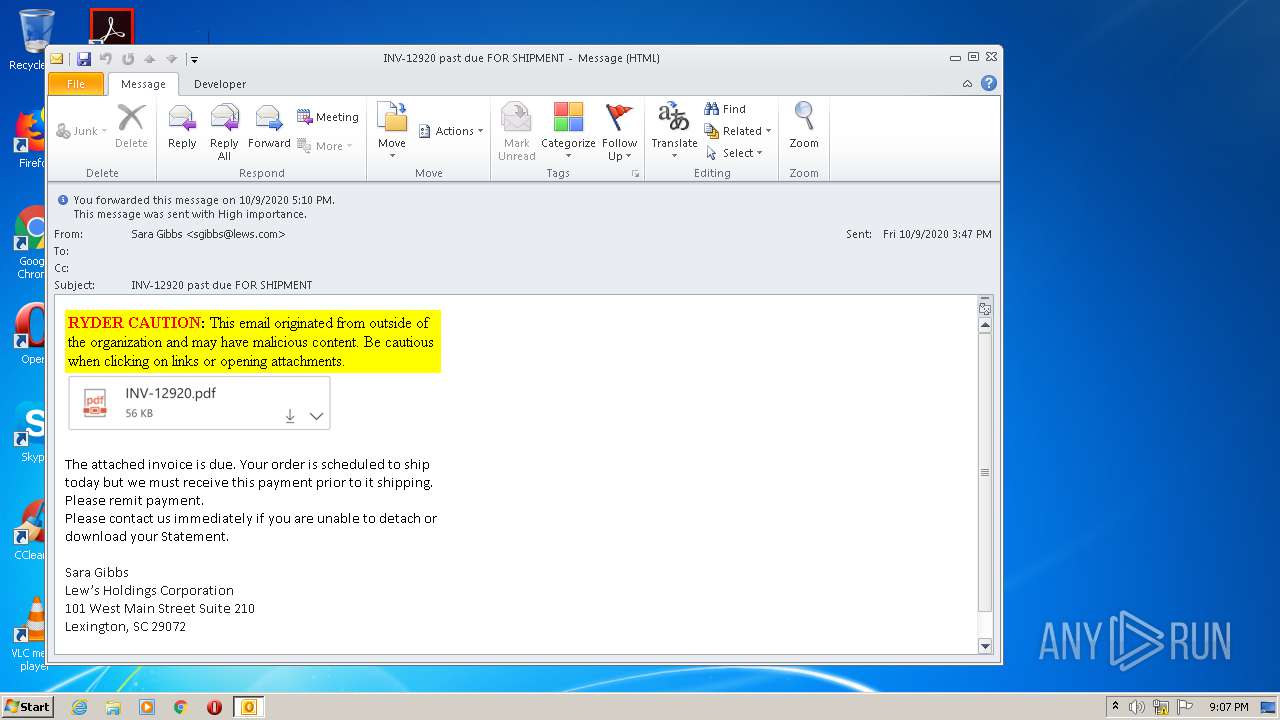
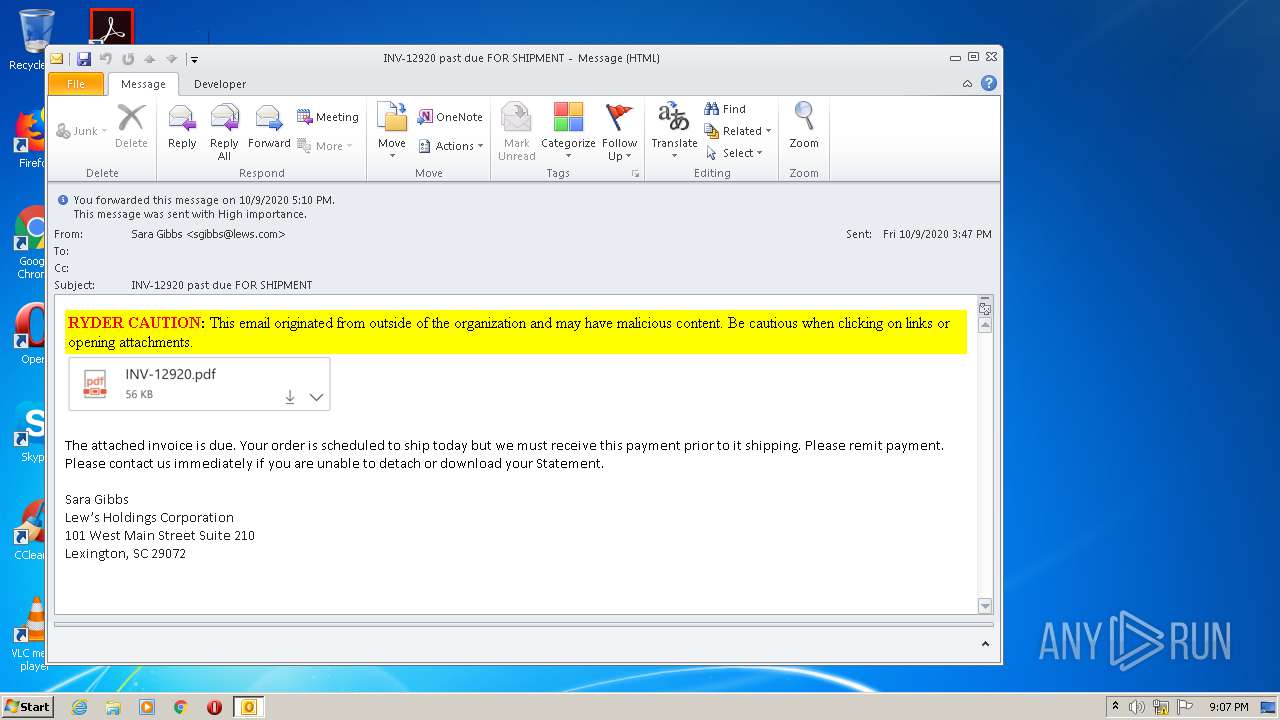
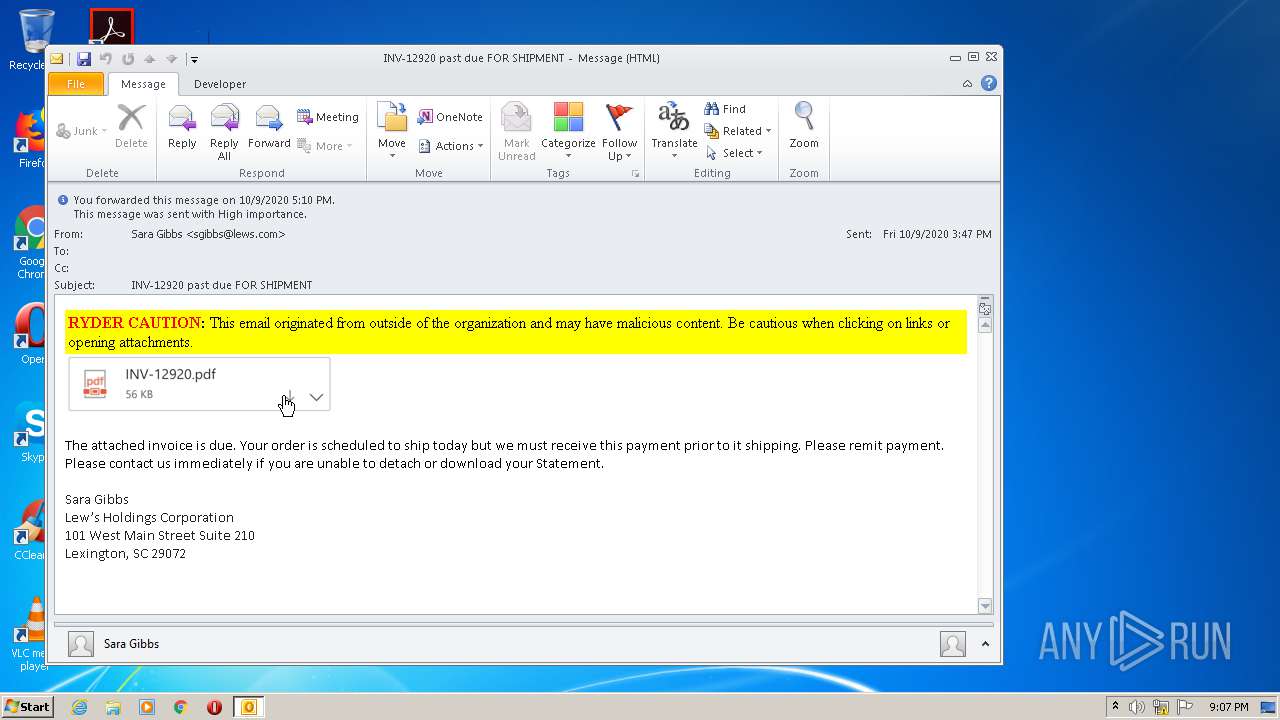
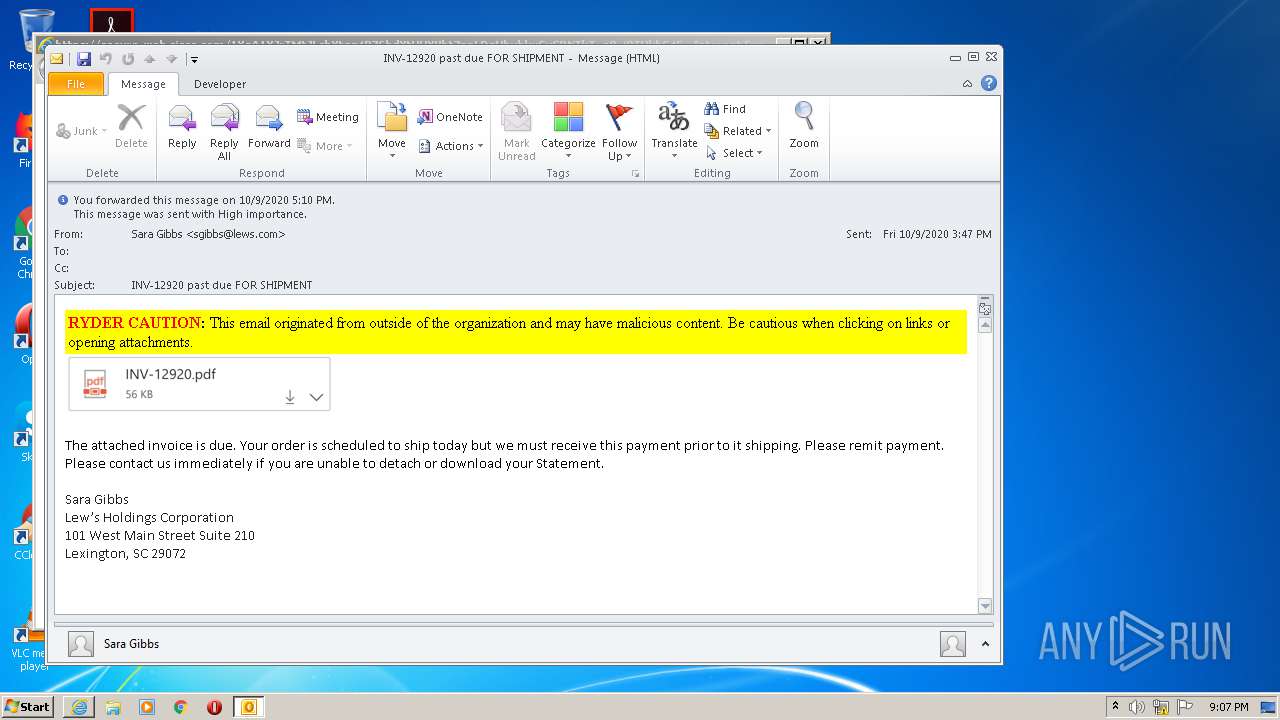
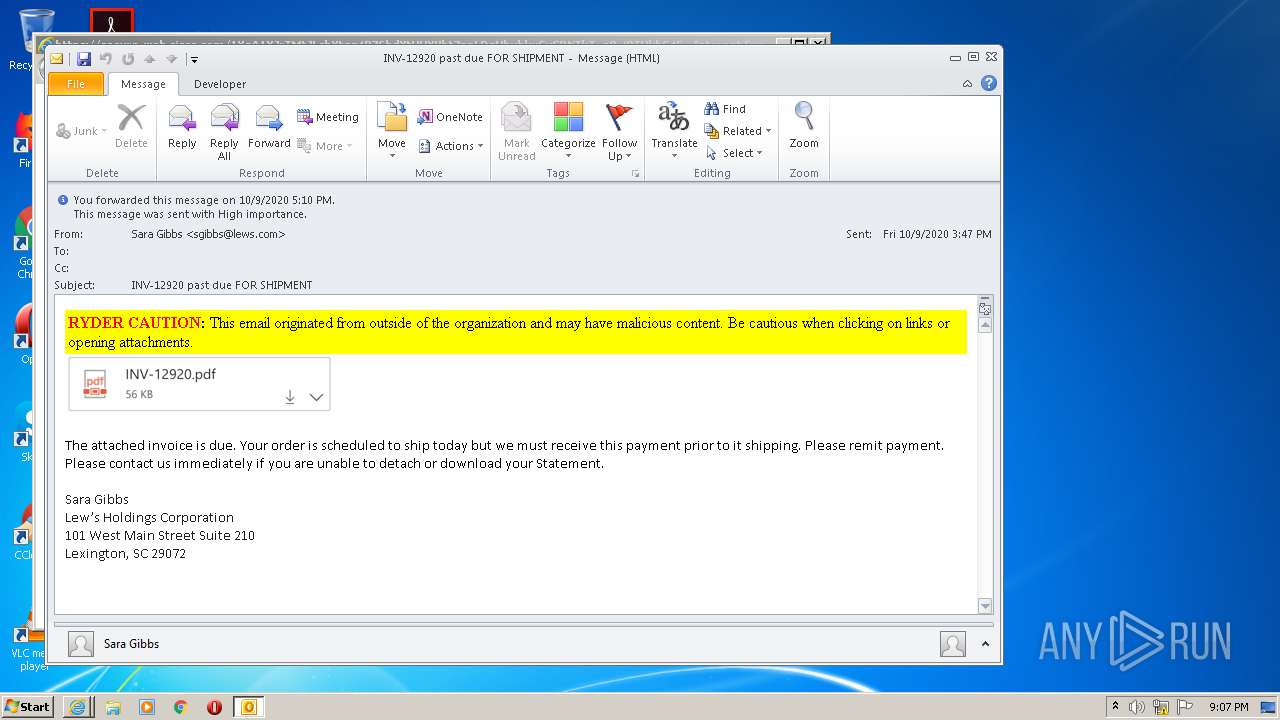
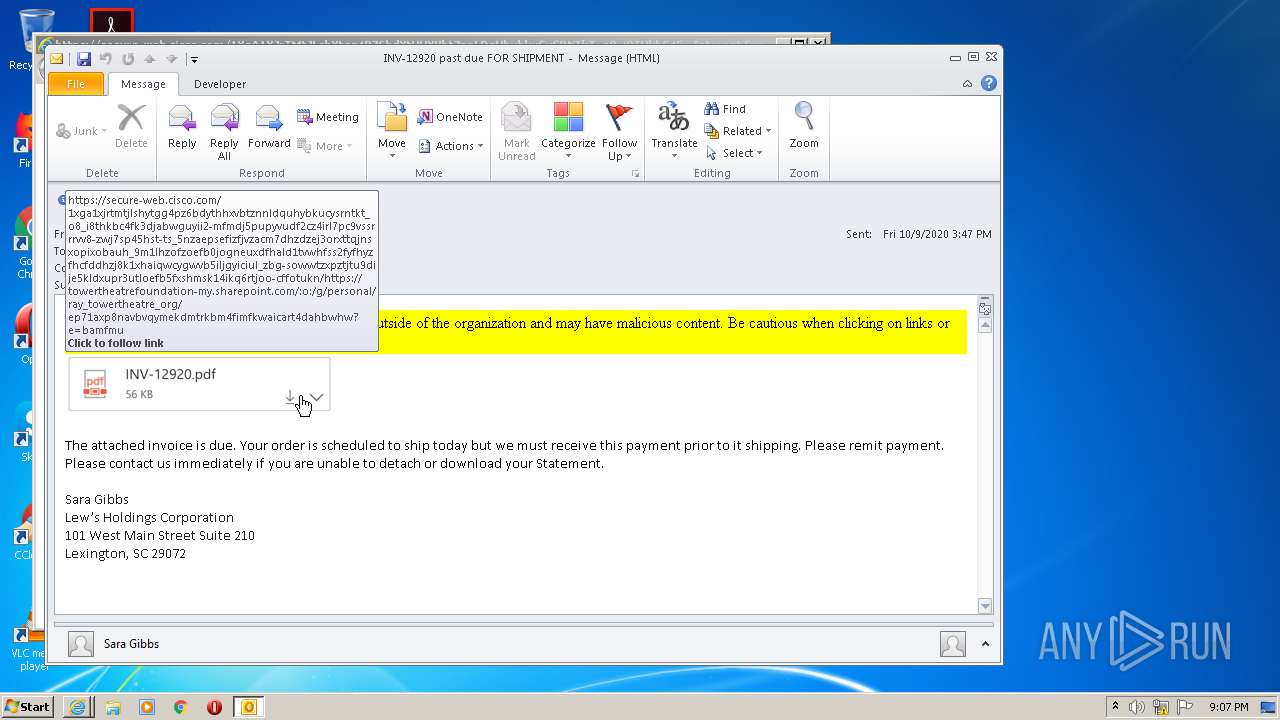
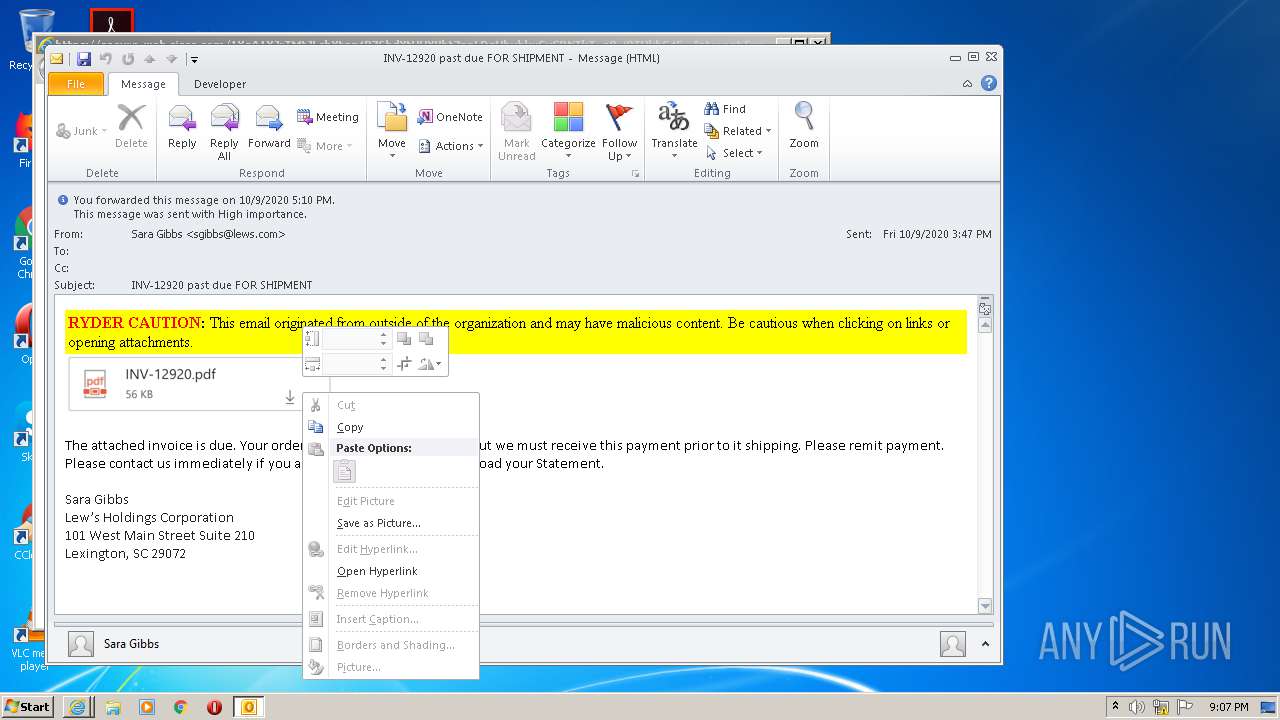
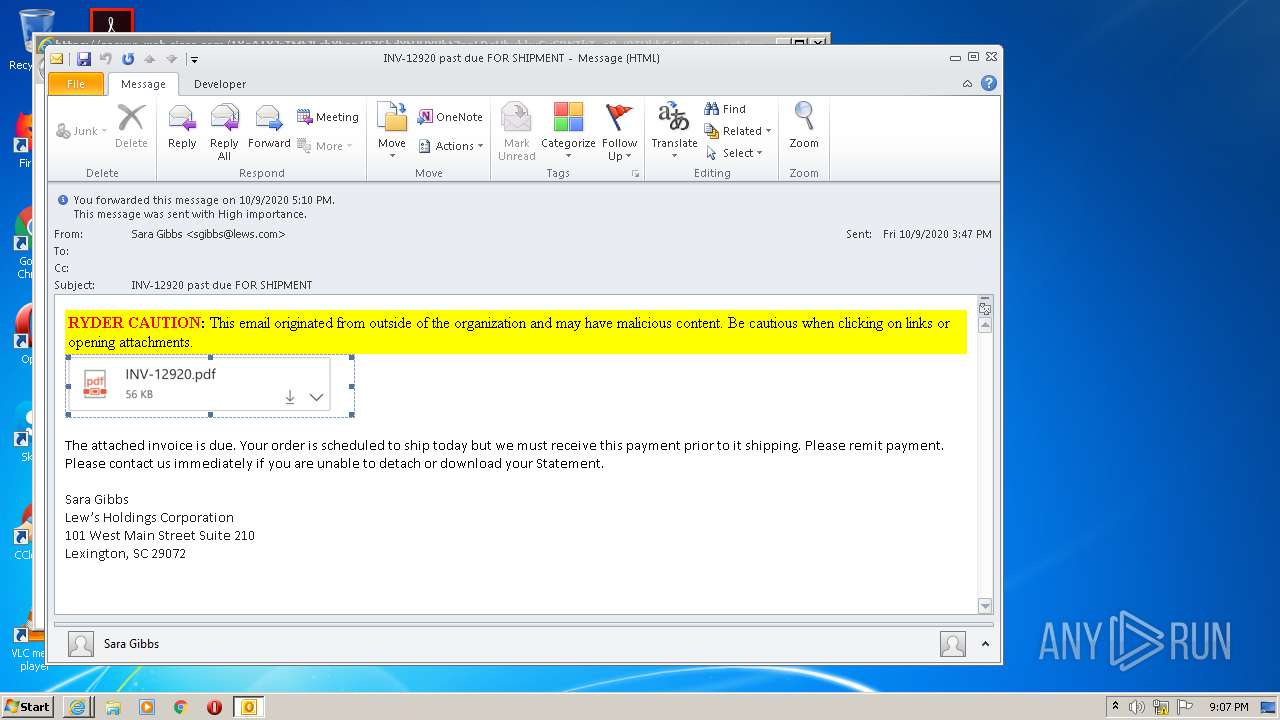
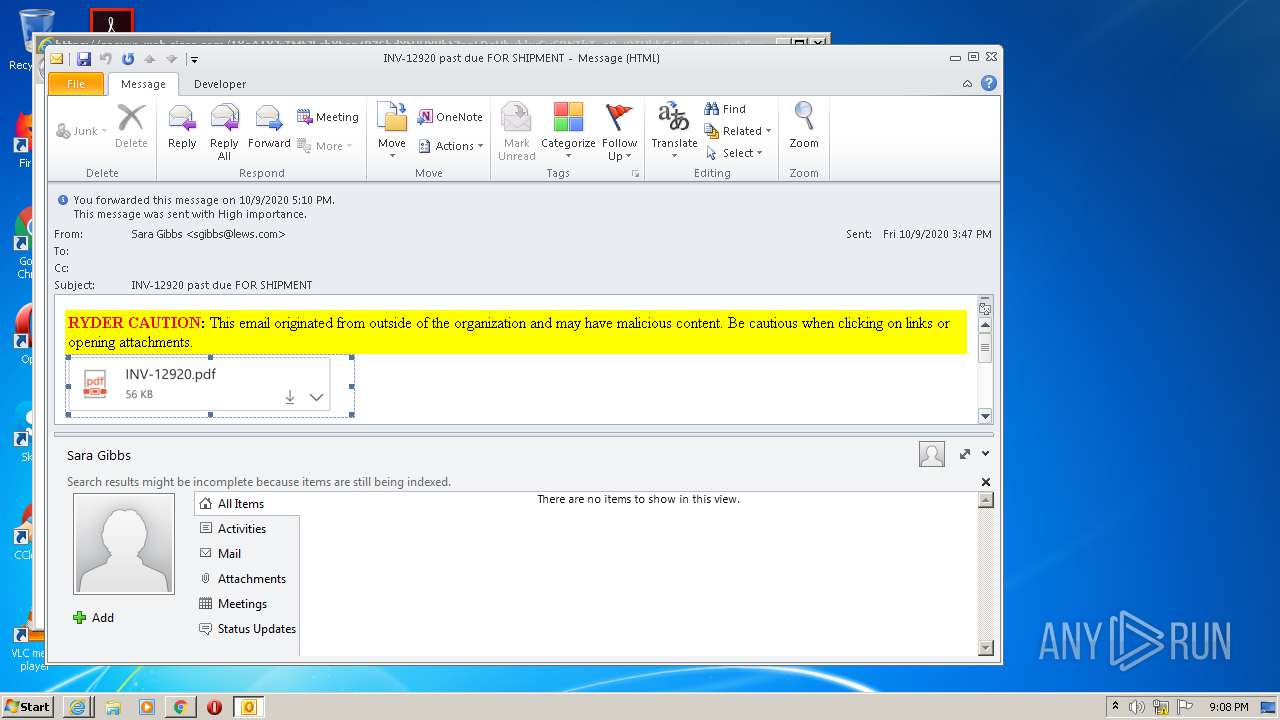
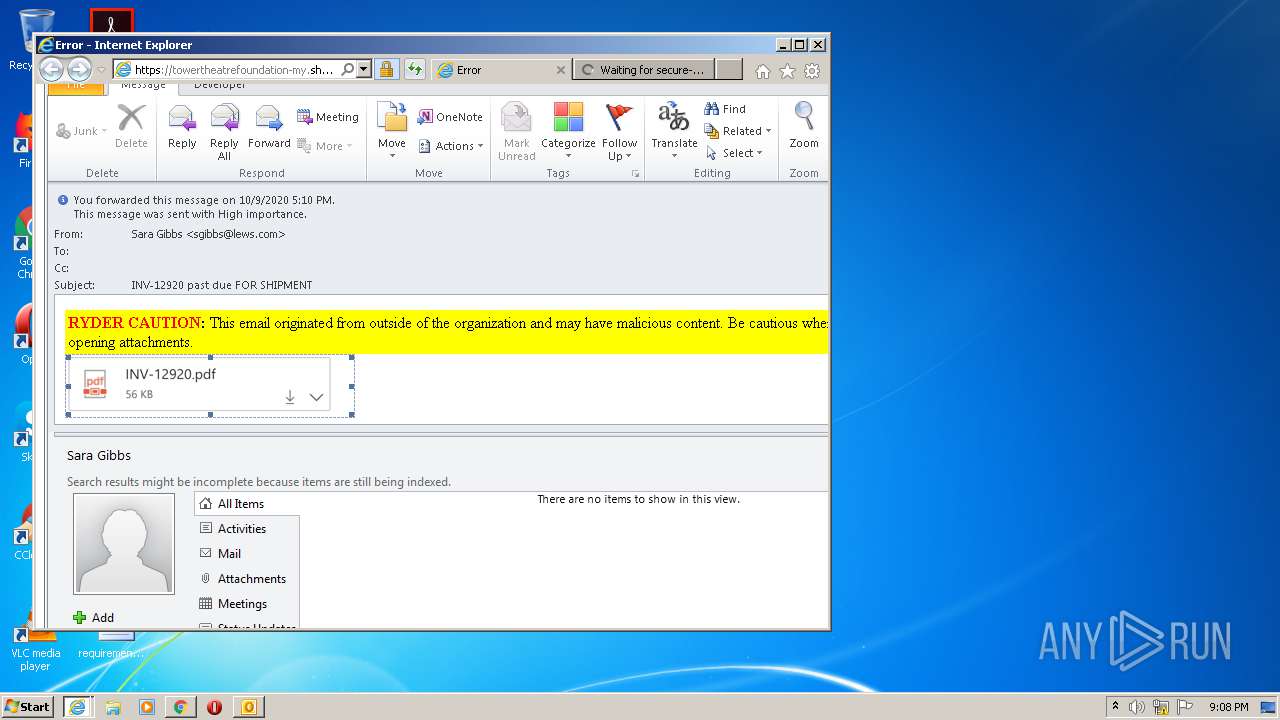
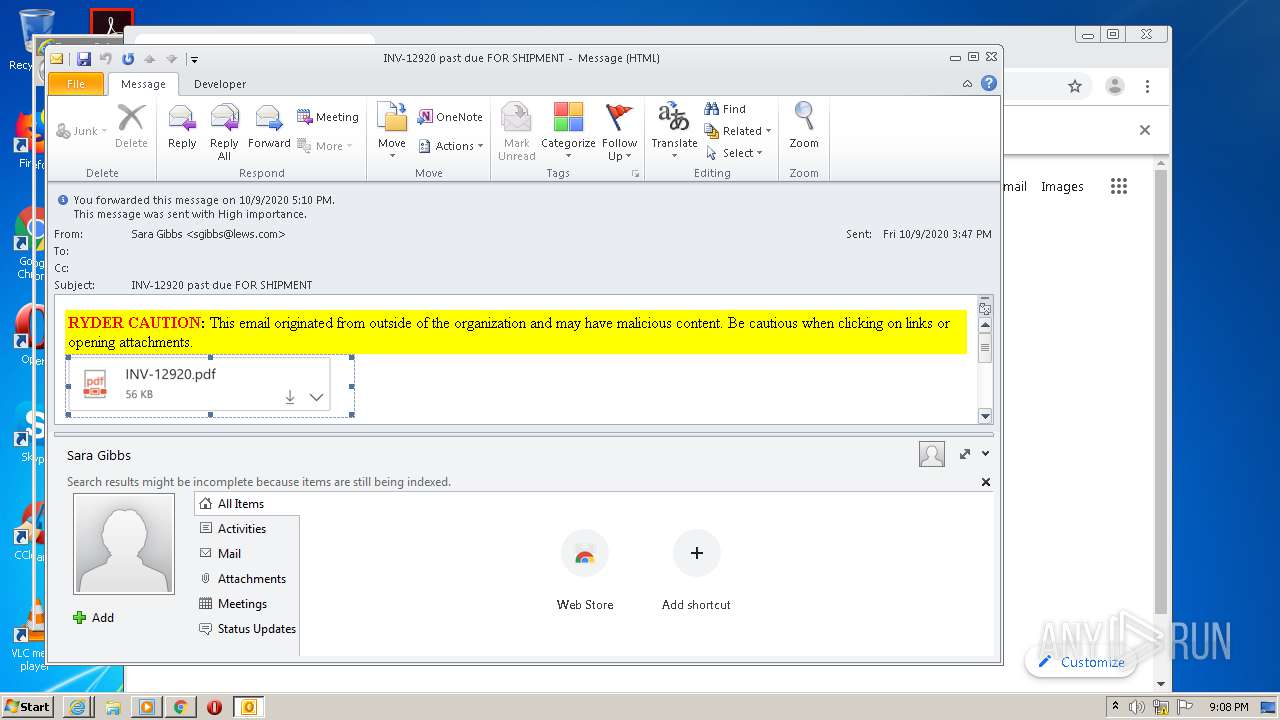
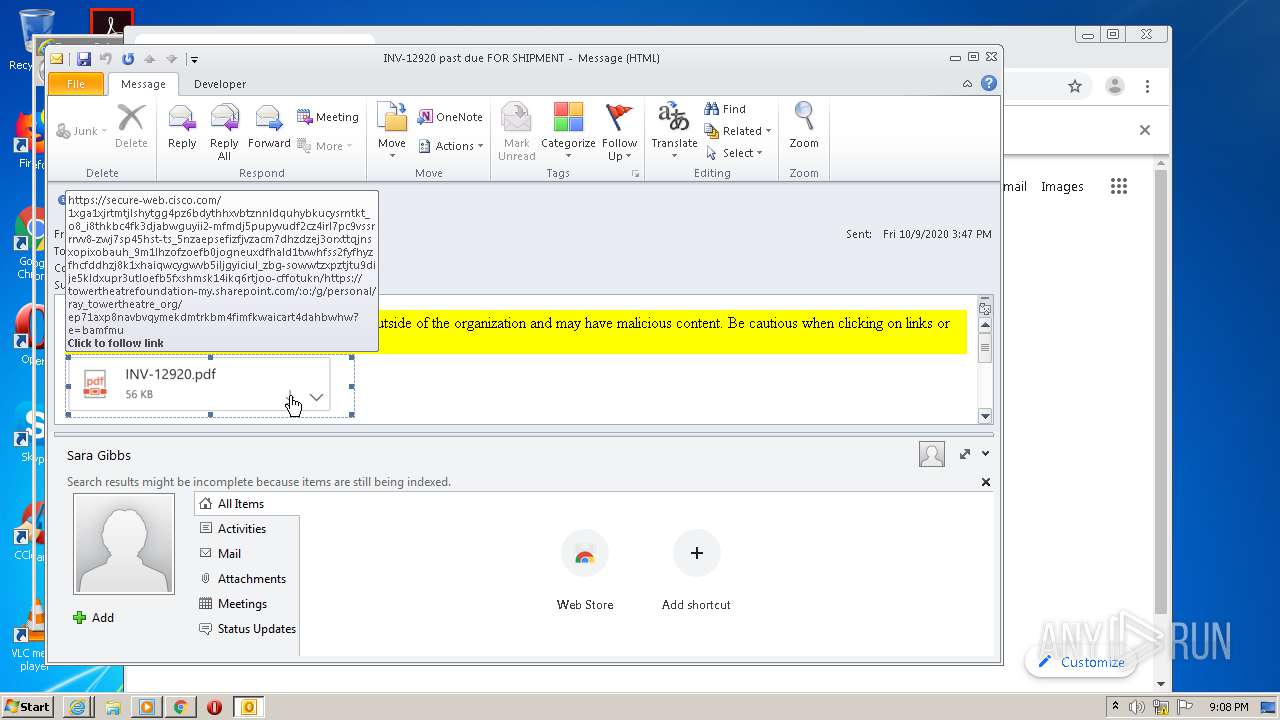
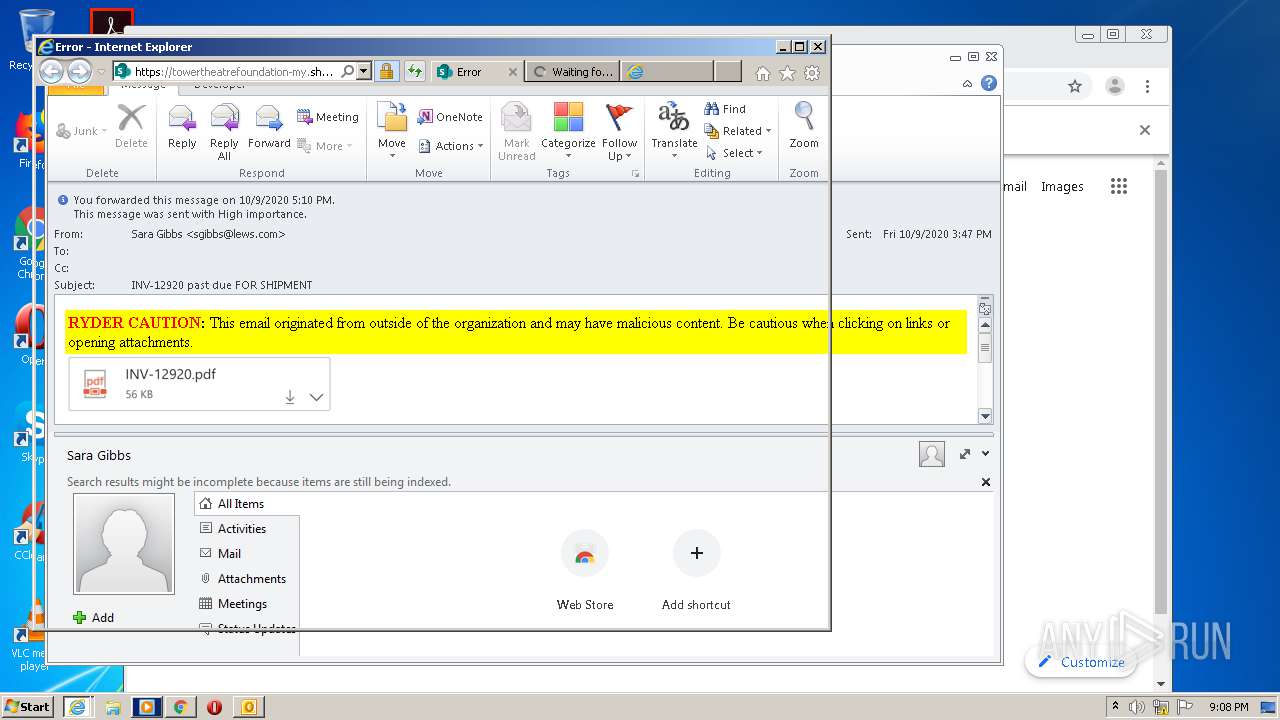
| File name: | INV-12920 past due FOR SHIPMENT.msg |
| Full analysis: | https://app.any.run/tasks/b7edad44-9bb6-4d64-bc2e-98b1cb080586 |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2020, 20:07:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | D647724104948AD49DA85922C086937D |
| SHA1: | B4B45AF26CE39BEF0DAAE9EB1D395C452116FF2E |
| SHA256: | 1F281B38379407D47E1DAC239A79001C597574C92CF5CBBCD84B0605D2FFB335 |
| SSDEEP: | 3072:Mf1YcxvriqhLk2rYIejImytYocLkxxR3UiOxAunGsOs8Wi8zgnP5OyckBYvv:oxv59cIC+zmqPOxJnNHJ8nBcs |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2728)
SUSPICIOUS
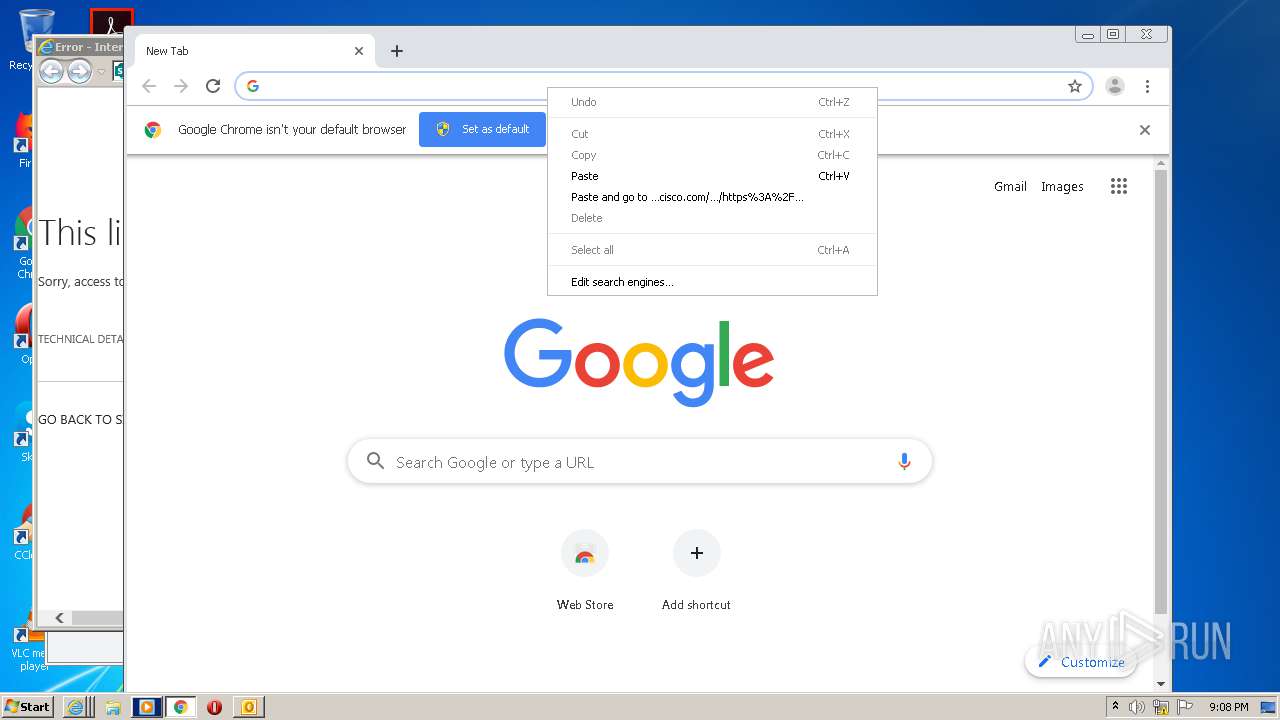
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2728)
INFO
Creates files in the user directory
- OUTLOOK.EXE (PID: 2728)
- iexplore.exe (PID: 1204)
Reads Internet Cache Settings
- iexplore.exe (PID: 4076)
- iexplore.exe (PID: 1204)
- iexplore.exe (PID: 2268)
- iexplore.exe (PID: 1748)
Changes internet zones settings
- iexplore.exe (PID: 1204)
Reads settings of System Certificates
- iexplore.exe (PID: 4076)
- chrome.exe (PID: 3876)
- iexplore.exe (PID: 1204)
- iexplore.exe (PID: 2268)
- iexplore.exe (PID: 1748)
Reads internet explorer settings
- OUTLOOK.EXE (PID: 2728)
- iexplore.exe (PID: 4076)
- iexplore.exe (PID: 1748)
- iexplore.exe (PID: 2268)
Application launched itself
- iexplore.exe (PID: 1204)
- chrome.exe (PID: 1516)
Manual execution by user
- chrome.exe (PID: 1516)
- wmplayer.exe (PID: 2836)
Reads the hosts file
- chrome.exe (PID: 1516)
- chrome.exe (PID: 3876)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1204)
Changes settings of System certificates
- iexplore.exe (PID: 1204)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
65
Monitored processes
25
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 908 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,10180684765480355529,7699959464398542706,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13100187140992337929 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2456 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 932 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,10180684765480355529,7699959464398542706,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=17206357458615752710 --mojo-platform-channel-handle=3636 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
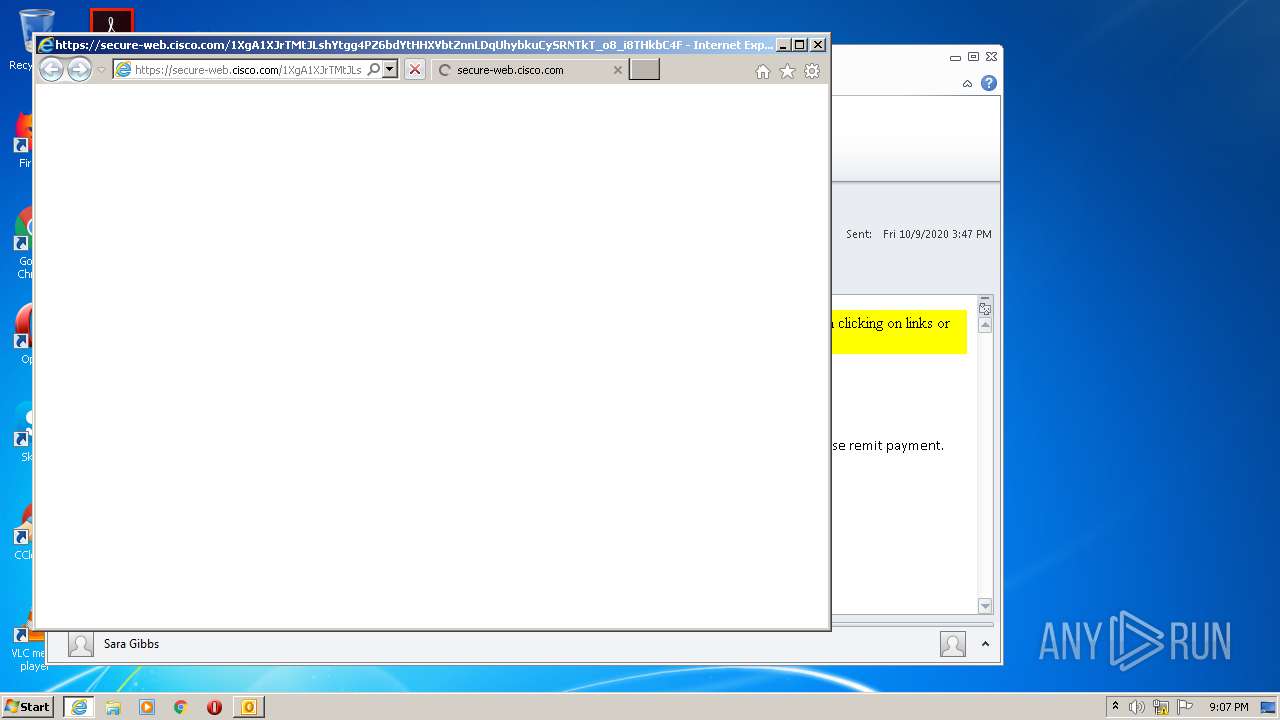
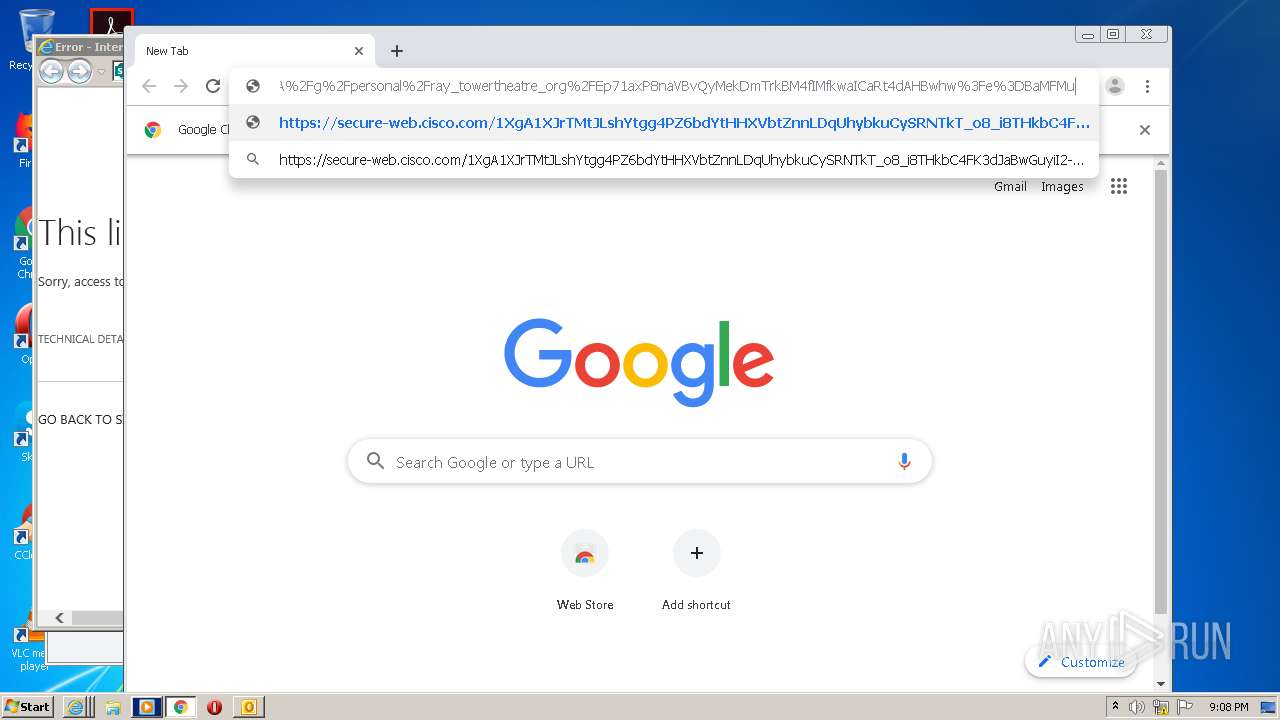
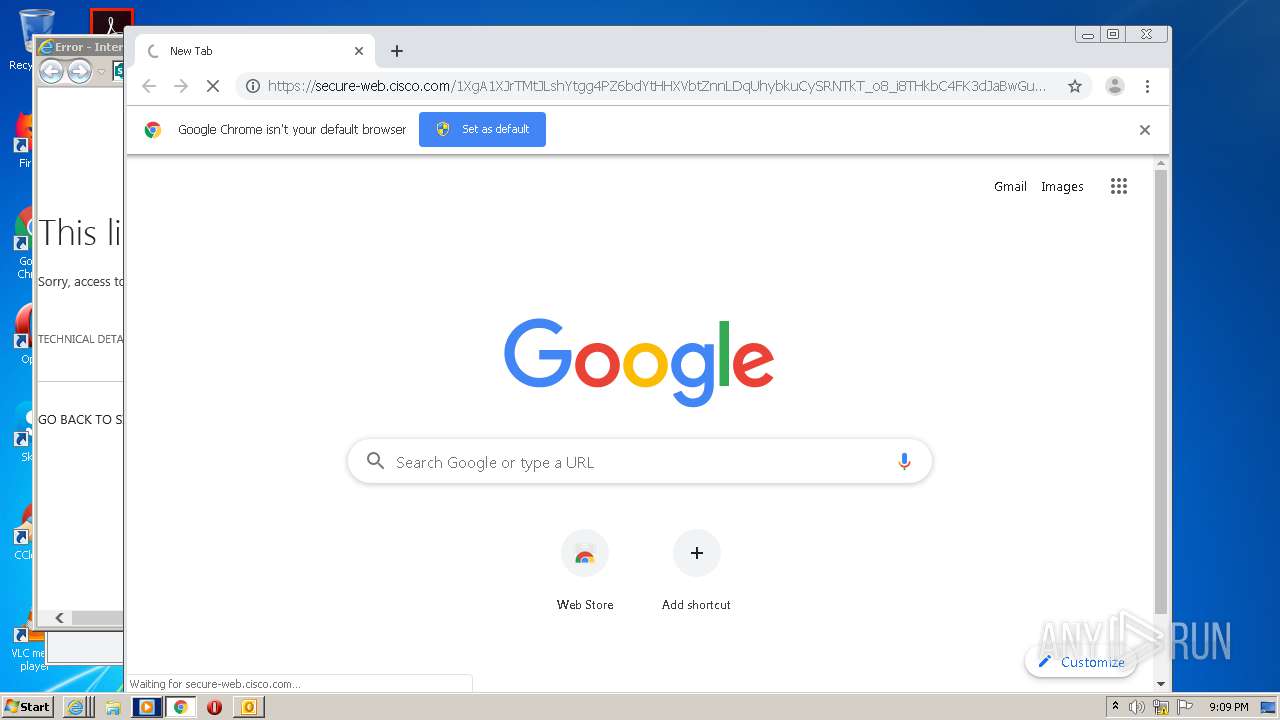
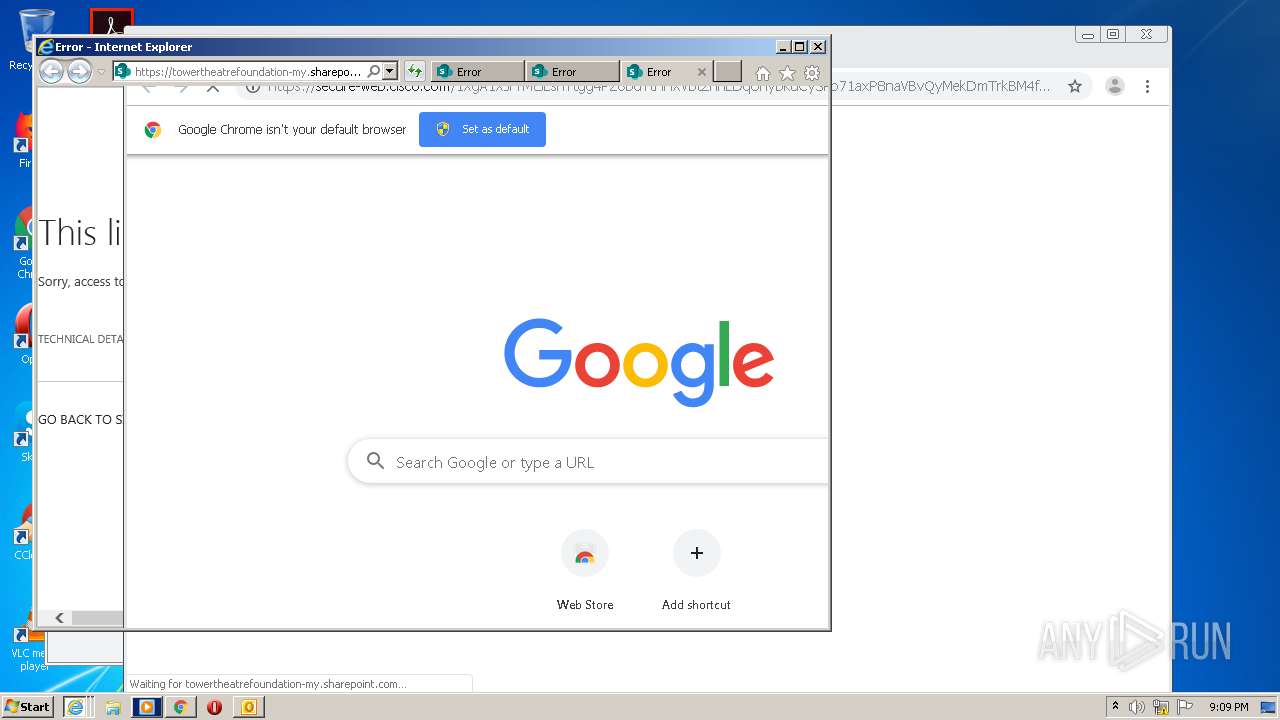
| 1204 | "C:\Program Files\Internet Explorer\iexplore.exe" https://secure-web.cisco.com/1XgA1XJrTMtJLshYtgg4PZ6bdYtHHXVbtZnnLDqUhybkuCySRNTkT_o8_i8THkbC4FK3dJaBwGuyiI2-MfMdj5PuPYvudf2Cz4iRl7pc9vSSRrrvV8-ZWj7SP45hST-TS_5nZAepSeFIZFjvZacM7DhzdzEJ3ORxtTQJnsxopiXObaUH_9M1LHZoFzoEfB0joGNeuxDFHALd1TvwHFss2FYfhYzFhCfDDhZJ8k1XhaIQWcYgwvb5ILJgYiCIUl_Zbg-SOwWtzXpZtjtu9diJe5kLdxUpR3uTloeFB5fXShmSK14IKq6rtJOO-cFFotukn/https%3A%2F%2Ftowertheatrefoundation-my.sharepoint.com%2F%3Ao%3A%2Fg%2Fpersonal%2Fray_towertheatre_org%2FEp71axP8naVBvQyMekDmTrkBM4fIMfkwaICaRt4dAHBwhw%3Fe%3DBaMFMu | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1516 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1748 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1204 CREDAT:3085599 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1764 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,10180684765480355529,7699959464398542706,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=348274159359712775 --mojo-platform-channel-handle=3584 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1964 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,10180684765480355529,7699959464398542706,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1053994552630558704 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2232 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1968 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=996,10180684765480355529,7699959464398542706,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=8942338265935283261 --mojo-platform-channel-handle=1012 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,10180684765480355529,7699959464398542706,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14633169707793498564 --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=904 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,10180684765480355529,7699959464398542706,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2367195997117259562 --mojo-platform-channel-handle=3380 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
3 739
Read events
2 943
Write events
770
Delete events
26
Modification events
| (PID) Process: | (2728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
63
Text files
118
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2728 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR421E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 4076 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab767D.tmp | — | |
MD5:— | SHA256:— | |||
| 4076 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar767E.tmp | — | |
MD5:— | SHA256:— | |||
| 2728 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2728 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 4076 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2F23D0F5E4D72862517E1CB26A329742_F6FACC49395CFA949BCE851E73323C49 | der | |
MD5:— | SHA256:— | |||
| 4076 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2F23D0F5E4D72862517E1CB26A329742_F6FACC49395CFA949BCE851E73323C49 | binary | |
MD5:— | SHA256:— | |||
| 2728 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\AB948400.dat | image | |
MD5:— | SHA256:— | |||
| 4076 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B0F2D31D2C32B49DCC8F7CC5C73F3C5D_2C8AAFA9D67255B0364928E0BF09B2FE | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
64
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4076 | iexplore.exe | GET | 200 | 52.210.26.218:80 | http://ocsp.quovadisglobal.com/MFUwUzBRME8wTTAJBgUrDgMCGgUABBTyhcKR1A4XhQLFZRt5u%2BT8TDsYdQQUGoRivEhMMyUE1O7Q9gPEGUbRlGsCFHUXFneD0EN%2BtVbDV5RuRWO469Os | IE | der | 1.78 Kb | whitelisted |
1204 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
4076 | iexplore.exe | GET | 200 | 35.158.10.169:80 | http://ocsp.quovadisglobal.com/MFUwUzBRME8wTTAJBgUrDgMCGgUABBTyhcKR1A4XhQLFZRt5u%2BT8TDsYdQQUGoRivEhMMyUE1O7Q9gPEGUbRlGsCFHUXFneD0EN%2BtVbDV5RuRWO469Os | DE | der | 1.78 Kb | whitelisted |
4076 | iexplore.exe | GET | 200 | 35.158.10.169:80 | http://ocsp.quovadisglobal.com/MFUwUzBRME8wTTAJBgUrDgMCGgUABBRPT4HWWg2N6N2sdizmyiRTaupwfgQUmGq2LS6%2Fp6qf9vfWCa%2FVi1f5ircCFAJ6LdwhHmBeL%2BjGokwlqon6ciFk | DE | der | 1.81 Kb | whitelisted |
4076 | iexplore.exe | GET | 200 | 35.158.10.169:80 | http://ocsp.quovadisglobal.com/MFUwUzBRME8wTTAJBgUrDgMCGgUABBRPT4HWWg2N6N2sdizmyiRTaupwfgQUmGq2LS6%2Fp6qf9vfWCa%2FVi1f5ircCFAJ6LdwhHmBeL%2BjGokwlqon6ciFk | DE | der | 1.81 Kb | whitelisted |
1052 | svchost.exe | GET | 200 | 67.27.157.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.5 Kb | whitelisted |
1052 | svchost.exe | GET | 200 | 2.16.186.120:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | der | 781 b | whitelisted |
4076 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAGewca9P1l7sgwzOOVR2Hc%3D | US | der | 471 b | whitelisted |
4076 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertGlobalRootCA.crl | US | der | 631 b | whitelisted |
4076 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2728 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
4076 | iexplore.exe | 52.210.26.218:80 | ocsp.quovadisglobal.com | Amazon.com, Inc. | IE | unknown |
1204 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
4076 | iexplore.exe | 35.158.10.169:80 | ocsp.quovadisglobal.com | Amazon.com, Inc. | DE | whitelisted |
4076 | iexplore.exe | 13.107.136.9:443 | towertheatrefoundation-my.sharepoint.com | Microsoft Corporation | US | whitelisted |
4076 | iexplore.exe | 208.90.58.178:443 | secure-web.cisco.com | Cisco Systems Ironport Division | US | suspicious |
3876 | chrome.exe | 216.58.212.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
1204 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 13.107.136.9:443 | towertheatrefoundation-my.sharepoint.com | Microsoft Corporation | US | whitelisted |
3876 | chrome.exe | 172.217.23.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
secure-web.cisco.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.quovadisglobal.com |
| whitelisted |
towertheatrefoundation-my.sharepoint.com |
| suspicious |
ocsp.digicert.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |