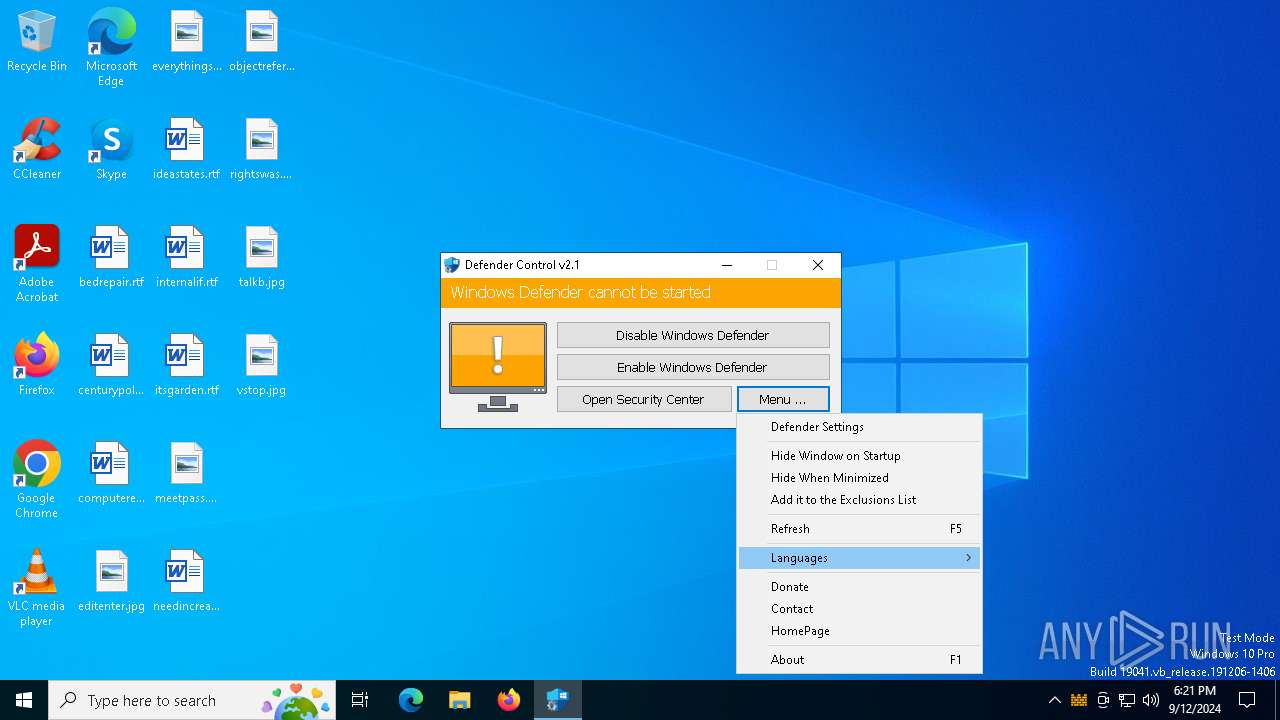
| File name: | dControl.exe |
| Full analysis: | https://app.any.run/tasks/b97e4fa9-10fa-4a15-9cfa-d43788404561 |
| Verdict: | Malicious activity |
| Analysis date: | September 12, 2024, 18:20:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 58008524A6473BDF86C1040A9A9E39C3 |
| SHA1: | CB704D2E8DF80FD3500A5B817966DC262D80DDB8 |
| SHA256: | 1EF6C1A4DFDC39B63BFE650CA81AB89510DE6C0D3D7C608AC5BE80033E559326 |
| SSDEEP: | 6144:Vzv+kSn74iCmfianQGDM3OXTWRDy9GYQDUmJFXIXHrsUBnBTF8JJCYrYNsQJzfgu:Vzcn7EanlQiWtYhmJFSwUBLcQZfgiD |
MALICIOUS
Antivirus name has been found in the command line (generic signature)
- MpCmdRun.exe (PID: 6396)
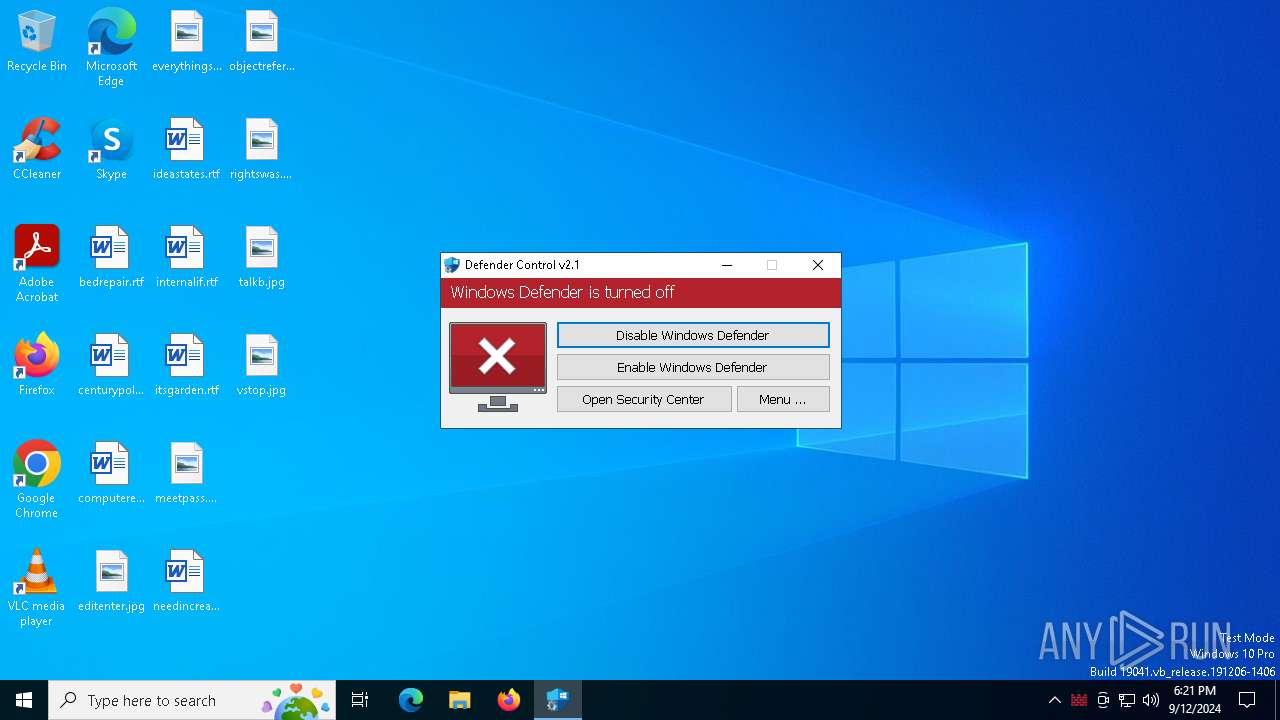
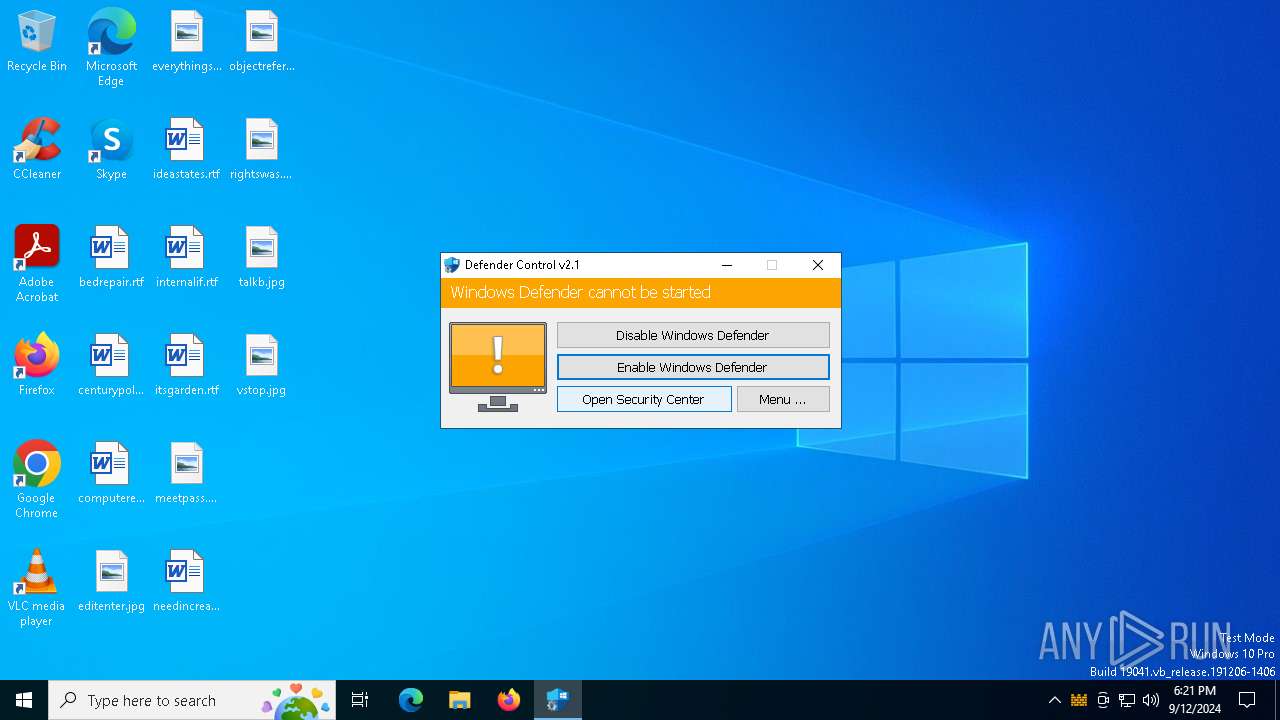
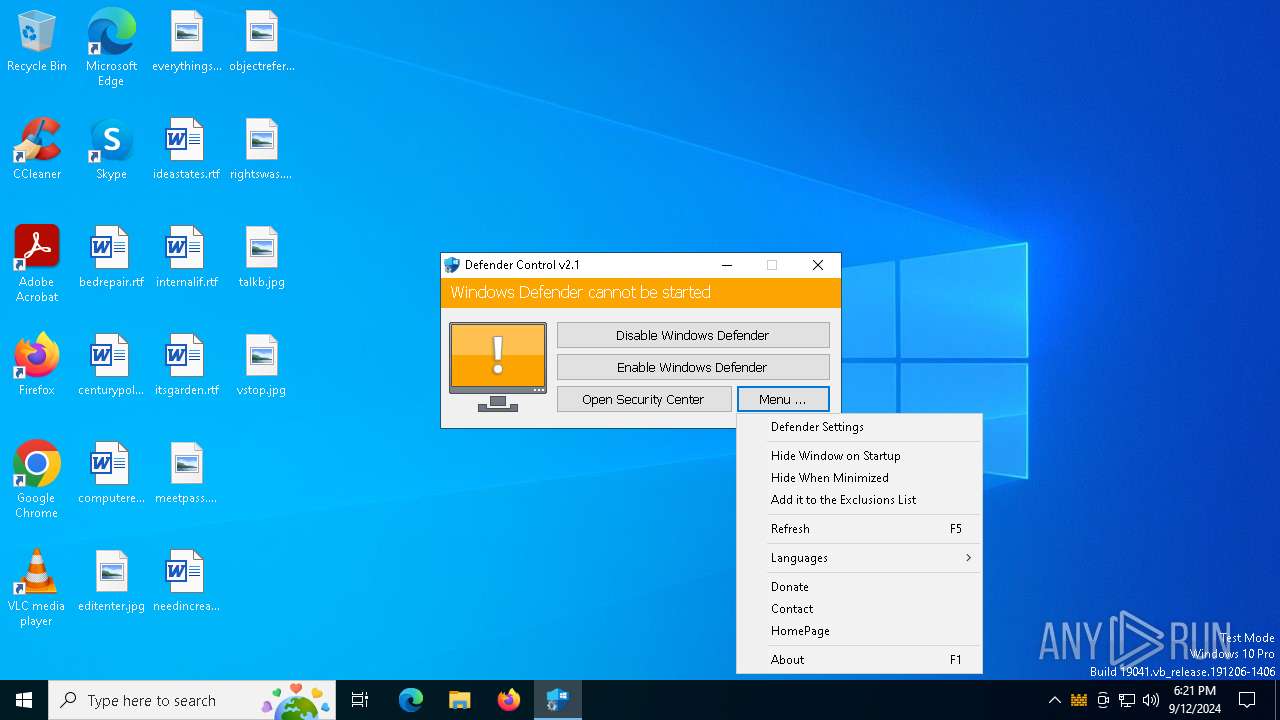
Disables Windows Defender
- dControl.exe (PID: 5532)
Changes image file execution options
- dControl.exe (PID: 5532)
Creates or modifies Windows services
- dControl.exe (PID: 5532)
SUSPICIOUS
Application launched itself
- dControl.exe (PID: 6808)
- dControl.exe (PID: 4444)
- dControl.exe (PID: 5532)
Creates or modifies Windows services
- dControl.exe (PID: 5532)
Explorer used for Indirect Command Execution
- explorer.exe (PID: 1712)
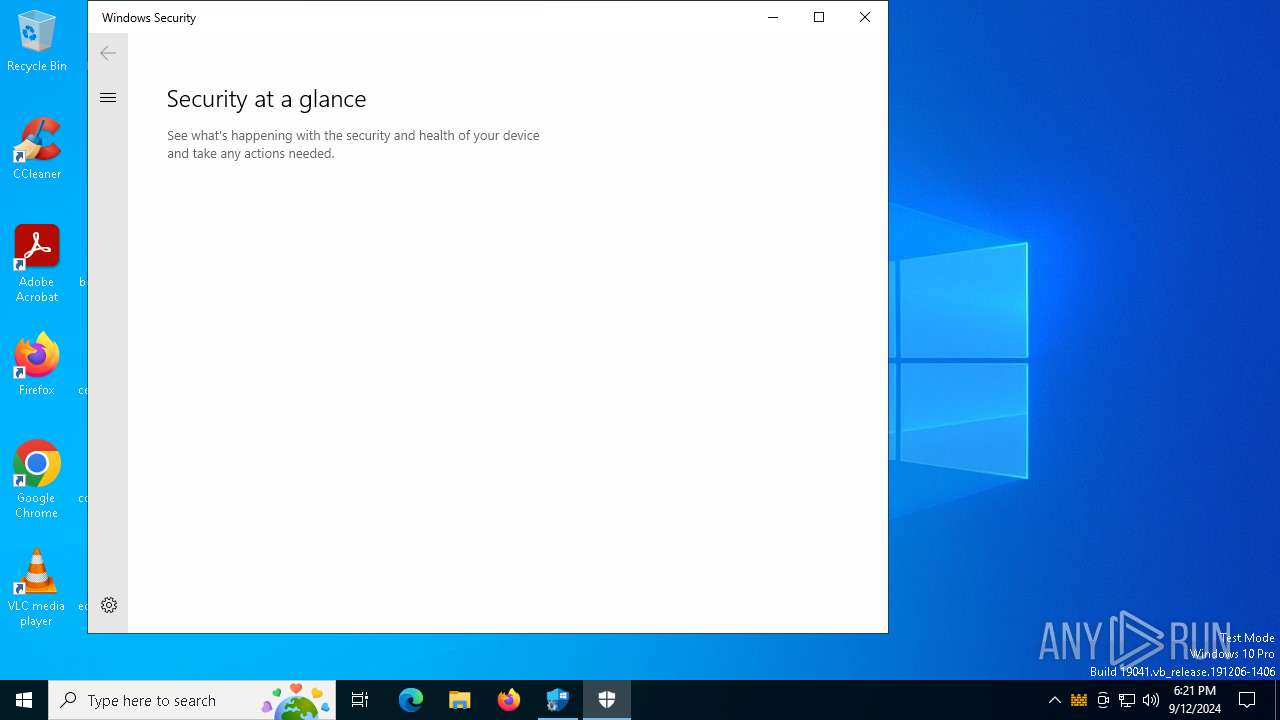
Reads security settings of Internet Explorer
- SecHealthUI.exe (PID: 6308)
INFO
Create files in a temporary directory
- dControl.exe (PID: 6808)
- dControl.exe (PID: 5532)
Reads mouse settings
- dControl.exe (PID: 6808)
- dControl.exe (PID: 4444)
- dControl.exe (PID: 5532)
- dControl.exe (PID: 3728)
- dControl.exe (PID: 5072)
Reads the computer name
- dControl.exe (PID: 6808)
- dControl.exe (PID: 4444)
- MpCmdRun.exe (PID: 6396)
- dControl.exe (PID: 3728)
- dControl.exe (PID: 5532)
- dControl.exe (PID: 5072)
- SecHealthUI.exe (PID: 6308)
Checks supported languages
- dControl.exe (PID: 6808)
- dControl.exe (PID: 4444)
- dControl.exe (PID: 5532)
- dControl.exe (PID: 3728)
- MpCmdRun.exe (PID: 6396)
- SecHealthUI.exe (PID: 6308)
- dControl.exe (PID: 5072)
Reads security settings of Internet Explorer
- explorer.exe (PID: 7024)
- explorer.exe (PID: 5544)
- explorer.exe (PID: 3104)
The process uses AutoIt
- dControl.exe (PID: 5532)
UPX packer has been detected
- dControl.exe (PID: 5532)
Sends debugging messages
- SecHealthUI.exe (PID: 6308)
The process uses the downloaded file
- explorer.exe (PID: 7024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (28.6) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (28) |
| .exe | | | Win32 EXE Yoda's Crypter (27.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (6.8) |
| .exe | | | Win32 Executable (generic) (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:12:23 10:59:31+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 270336 |
| InitializedDataSize: | 61440 |
| UninitializedDataSize: | 503808 |
| EntryPoint: | 0xbd650 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.1.0.0 |
| ProductVersionNumber: | 2.1.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| FileVersion: | 2.1.0.0 |
| Comments: | dControl v2.1 |
| FileDescription: | dControl v2.1 |
| LegalCopyright: | Copyright © 2015-2022 www.sordum.org All Rights Reserved. |
| CompanyName: | www.sordum.org |
| ProductVersion: | 2.1.0.0 |
| OriginalFileName: | dControl.exe |
| Coder: | By BlueLife |
Total processes
170
Monitored processes
20
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1712 | "C:\WINDOWS\Explorer.exe" C:\WINDOWS\System32\SecurityHealthSystray.exe | C:\Windows\explorer.exe | — | dControl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2456 | "C:\Users\admin\AppData\Local\Temp\dControl.exe" | C:\Users\admin\AppData\Local\Temp\dControl.exe | — | explorer.exe | |||||||||||
User: admin Company: www.sordum.org Integrity Level: MEDIUM Description: dControl v2.1 Exit code: 3221226540 Version: 2.1.0.0 Modules
| |||||||||||||||
| 3032 | C:\Windows\System32\SecurityHealthHost.exe {E041C90B-68BA-42C9-991E-477B73A75C90} -Embedding | C:\Windows\System32\SecurityHealthHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Security Health Host Exit code: 0 Version: 4.18.1907.16384 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3104 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3728 | "C:\Users\admin\AppData\Local\Temp\dControl.exe" /EXP |4552| | C:\Users\admin\AppData\Local\Temp\dControl.exe | — | dControl.exe | |||||||||||
User: SYSTEM Company: www.sordum.org Integrity Level: SYSTEM Description: dControl v2.1 Exit code: 0 Version: 2.1.0.0 Modules
| |||||||||||||||
| 4076 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4080 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4444 | C:\Users\admin\AppData\Local\Temp\dControl.exe | C:\Users\admin\AppData\Local\Temp\dControl.exe | dControl.exe | ||||||||||||
User: SYSTEM Company: www.sordum.org Integrity Level: SYSTEM Description: dControl v2.1 Exit code: 0 Version: 2.1.0.0 Modules
| |||||||||||||||
| 5072 | "C:\Users\admin\AppData\Local\Temp\dControl.exe" /EXP |4552| | C:\Users\admin\AppData\Local\Temp\dControl.exe | — | dControl.exe | |||||||||||
User: SYSTEM Company: www.sordum.org Integrity Level: SYSTEM Description: dControl v2.1 Exit code: 0 Version: 2.1.0.0 Modules
| |||||||||||||||
| 5172 | "C:\Windows\System32\SecurityHealthSystray.exe" | C:\Windows\System32\SecurityHealthSystray.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Security notification icon Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 274
Read events
3 208
Write events
52
Delete events
14
Modification events
| (PID) Process: | (5532) dControl.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Notifications\Settings\Windows.SystemToast.SecurityAndMaintenance |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (5532) dControl.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WdFilter |
| Operation: | write | Name: | Start |
Value: 4 | |||
| (PID) Process: | (5532) dControl.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WdNisSvc |
| Operation: | write | Name: | Start |
Value: 4 | |||
| (PID) Process: | (5532) dControl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
| (PID) Process: | (5532) dControl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiVirus |
Value: 1 | |||
| (PID) Process: | (5532) dControl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
| (PID) Process: | (5532) dControl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiVirus |
Value: 1 | |||
| (PID) Process: | (5532) dControl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection |
| Operation: | write | Name: | DisableRealtimeMonitoring |
Value: 1 | |||
| (PID) Process: | (5532) dControl.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WinDefend |
| Operation: | write | Name: | Start |
Value: 4 | |||
| (PID) Process: | (5532) dControl.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mpcmdrun.exe |
| Operation: | write | Name: | Debugger |
Value: C:\WINDOWS\System32\systray.exe | |||
Executable files
0
Suspicious files
16
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4444 | dControl.exe | C:\Windows\Temp\autB3C8.tmp | binary | |
MD5:EFE44D9F6E4426A05E39F99AD407D3E7 | SHA256:5EA3B26C6B1B71EDAEF17CE365D50BE963AE9F4CB79B39EC723FE6E9E4054366 | |||
| 4444 | dControl.exe | C:\Windows\Temp\autB3C9.tmp | binary | |
MD5:ECFFD3E81C5F2E3C62BCDC122442B5F2 | SHA256:9874AB363B07DCC7E9CD6022A380A64102C1814343642295239A9F120CB941C5 | |||
| 4444 | dControl.exe | C:\Windows\Temp\4j4u4m4y.tmp | text | |
MD5:E00DCC76E4DCD90994587375125DE04B | SHA256:C8709F5A8B971D136E2273D66E65449791CA8EBA1F47DD767733EA52EE635447 | |||
| 4444 | dControl.exe | C:\Windows\Temp\autB3B8.tmp | binary | |
MD5:9D5A0EF18CC4BB492930582064C5330F | SHA256:8F5BBCC572BC62FEB13A669F856D21886A61888FD6288AFD066272A27EA79BB3 | |||
| 5532 | dControl.exe | C:\Windows\Temp\autB464.tmp | binary | |
MD5:9D5A0EF18CC4BB492930582064C5330F | SHA256:8F5BBCC572BC62FEB13A669F856D21886A61888FD6288AFD066272A27EA79BB3 | |||
| 5532 | dControl.exe | C:\Windows\Temp\autB474.tmp | binary | |
MD5:EFE44D9F6E4426A05E39F99AD407D3E7 | SHA256:5EA3B26C6B1B71EDAEF17CE365D50BE963AE9F4CB79B39EC723FE6E9E4054366 | |||
| 6808 | dControl.exe | C:\Users\admin\AppData\Local\Temp\autB241.tmp | binary | |
MD5:9D5A0EF18CC4BB492930582064C5330F | SHA256:8F5BBCC572BC62FEB13A669F856D21886A61888FD6288AFD066272A27EA79BB3 | |||
| 5532 | dControl.exe | C:\Windows\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:A205A64883D657DE511B900BEC778255 | SHA256:02BD4DD91B5A9AA5EE58C09F66D1E79677AFCFED8756B483907B5AAC555CE06C | |||
| 5532 | dControl.exe | C:\Users\admin\AppData\Local\Temp\dControl.ini | text | |
MD5:6759DEC31B72635A3F21287213744EB9 | SHA256:D7CF817D38A43A75691EB81B4EE1C63209A958EACAAEDB890B566BC69FA4B723 | |||
| 5532 | dControl.exe | C:\Windows\Temp\autB485.tmp | binary | |
MD5:ECFFD3E81C5F2E3C62BCDC122442B5F2 | SHA256:9874AB363B07DCC7E9CD6022A380A64102C1814343642295239A9F120CB941C5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
31
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7004 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7004 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4760 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1764 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4760 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6276 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4760 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2256 | svchost.exe | 224.0.0.251:5353 | — | — | — | unknown |
2256 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1764 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1764 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |