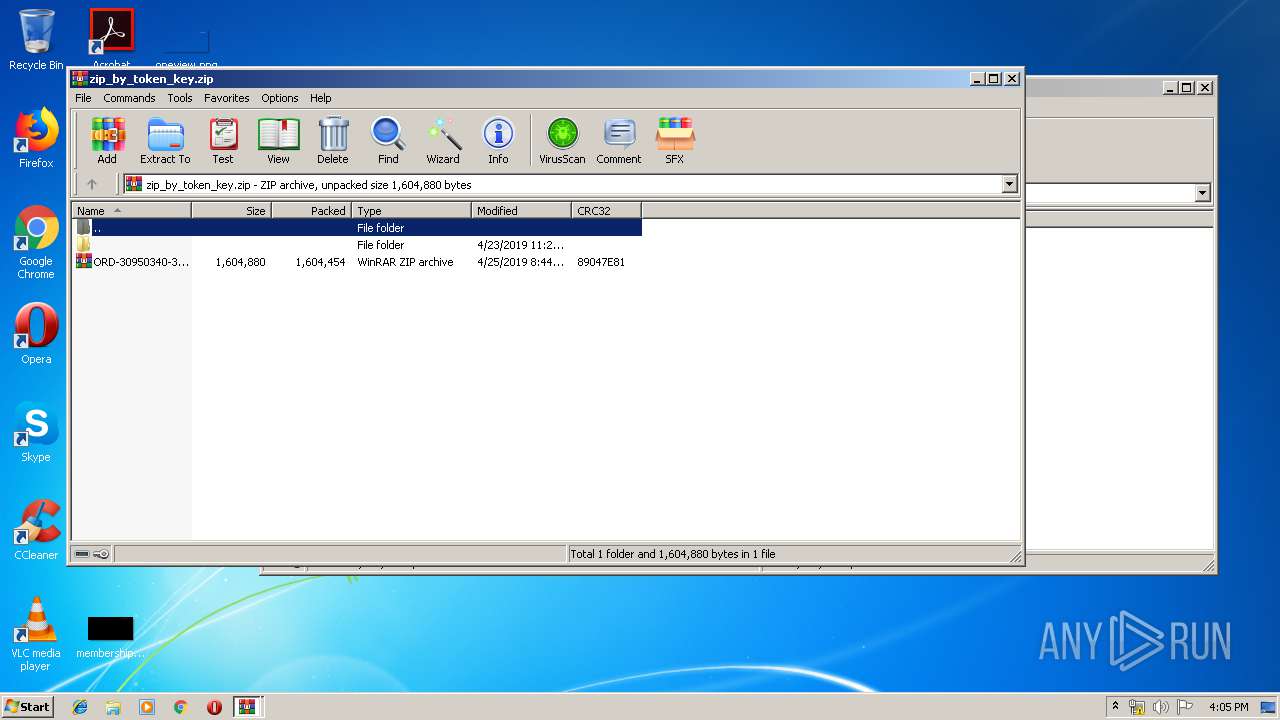
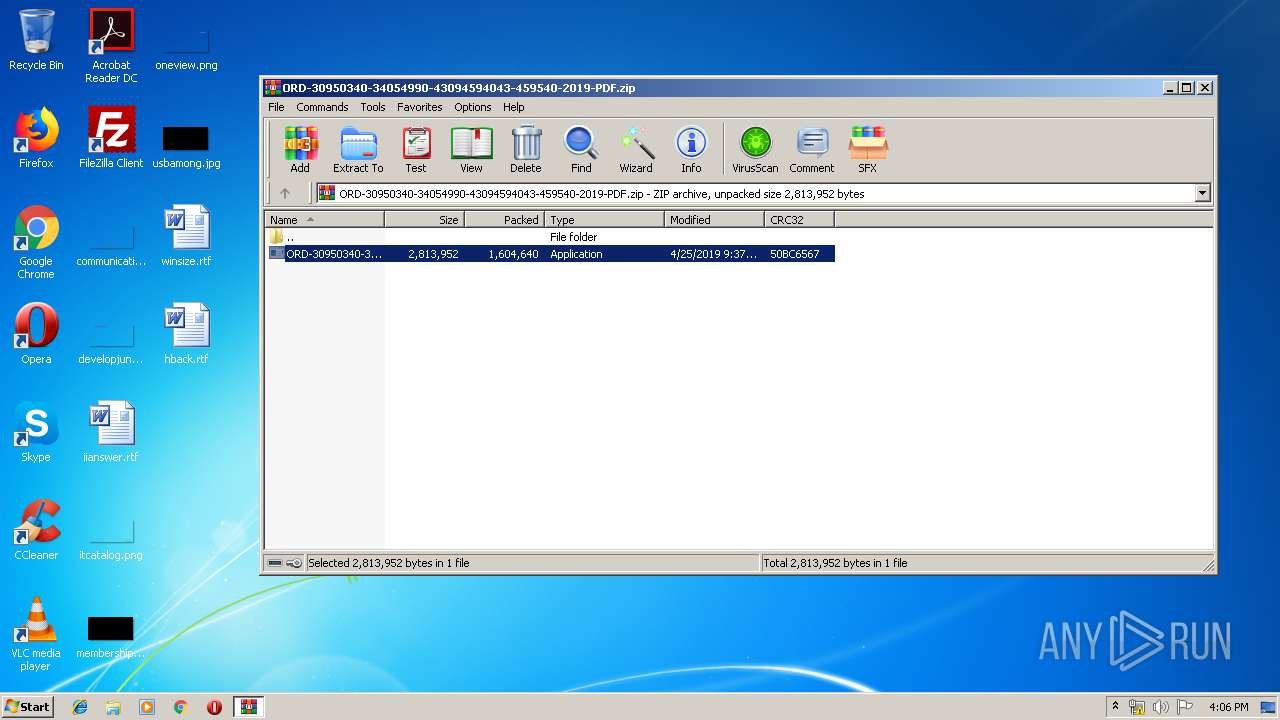
| download: | zip_by_token_key |
| Full analysis: | https://app.any.run/tasks/57eea2af-a43f-457b-92e9-4f3150d21562 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2019, 15:05:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 3DE8C0E50EC029B5853274EC645CCBBE |
| SHA1: | 6E70FF7E308ED0296ECD171B539406BAD9718174 |
| SHA256: | 1EF2B809B6753374C709EF9F6E8DB273A43841EB2A640E0CAD22690D75BD4DF7 |
| SSDEEP: | 49152:RhRHp6jITkn5M0/II4etSN03BIosuhDUwR2P7pIEQrdM:RhZp6Hn5M0/II4sSkOo5h4u29IED |
MALICIOUS
Application was dropped or rewritten from another process
- ORD-30950340-34054990-43094594043-459540-2019-PDF.exe (PID: 2776)
Writes to a start menu file
- ORD-30950340-34054990-43094594043-459540-2019-PDF.exe (PID: 2776)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 2524)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1796)
- ORD-30950340-34054990-43094594043-459540-2019-PDF.exe (PID: 2776)
Creates files in the user directory
- ORD-30950340-34054990-43094594043-459540-2019-PDF.exe (PID: 2776)
- rundll32.exe (PID: 3156)
- RegAsm.exe (PID: 1640)
Uses RUNDLL32.EXE to load library
- RegAsm.exe (PID: 1640)
Reads Internet Cache Settings
- rundll32.exe (PID: 3156)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:04:23 11:20:25 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | / |
Total processes
36
Monitored processes
5
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1640 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | ORD-30950340-34054990-43094594043-459540-2019-PDF.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 1796 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa2524.24202\ORD-30950340-34054990-43094594043-459540-2019-PDF.zip | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2524 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\zip_by_token_key.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2776 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1796.24812\ORD-30950340-34054990-43094594043-459540-2019-PDF.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1796.24812\ORD-30950340-34054990-43094594043-459540-2019-PDF.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3156 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | RegAsm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 015
Read events
939
Write events
76
Delete events
0
Modification events
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\zip_by_token_key.zip | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
2
Suspicious files
1
Text files
10
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1796.24812\ORD-30950340-34054990-43094594043-459540-2019-PDF.exe | executable | |
MD5:— | SHA256:— | |||
| 2776 | ORD-30950340-34054990-43094594043-459540-2019-PDF.exe | C:\Users\admin\SystemPropertiesAdvanced\BarcodeProvisioningPlugin.exe | executable | |
MD5:— | SHA256:— | |||
| 2776 | ORD-30950340-34054990-43094594043-459540-2019-PDF.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ie4ushowIE.url | text | |
MD5:— | SHA256:— | |||
| 3156 | rundll32.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2776 | ORD-30950340-34054990-43094594043-459540-2019-PDF.exe | C:\Users\admin\SystemPropertiesAdvanced\ie4ushowIE.vbs | text | |
MD5:— | SHA256:— | |||
| 2524 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2524.24202\ORD-30950340-34054990-43094594043-459540-2019-PDF.zip | compressed | |
MD5:— | SHA256:— | |||
| 3156 | rundll32.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\index.dat | dat | |
MD5:D7A950FEFD60DBAA01DF2D85FEFB3862 | SHA256:75D0B1743F61B76A35B1FEDD32378837805DE58D79FA950CB6E8164BFA72073A | |||
| 3156 | rundll32.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BIAQDWEN\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 3156 | rundll32.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PI4HXAW7\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 3156 | rundll32.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\KWIVIFL8\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
4
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1640 | RegAsm.exe | 104.25.209.99:443 | ipapi.co | Cloudflare Inc | US | shared |
1640 | RegAsm.exe | 192.253.242.196:6000 | monopak.dns-cloud.net | SoftLayer Technologies Inc. | AU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ipapi.co |
| shared |
monopak.dns-cloud.net |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup Domain (ipapi .co in DNS lookup) |