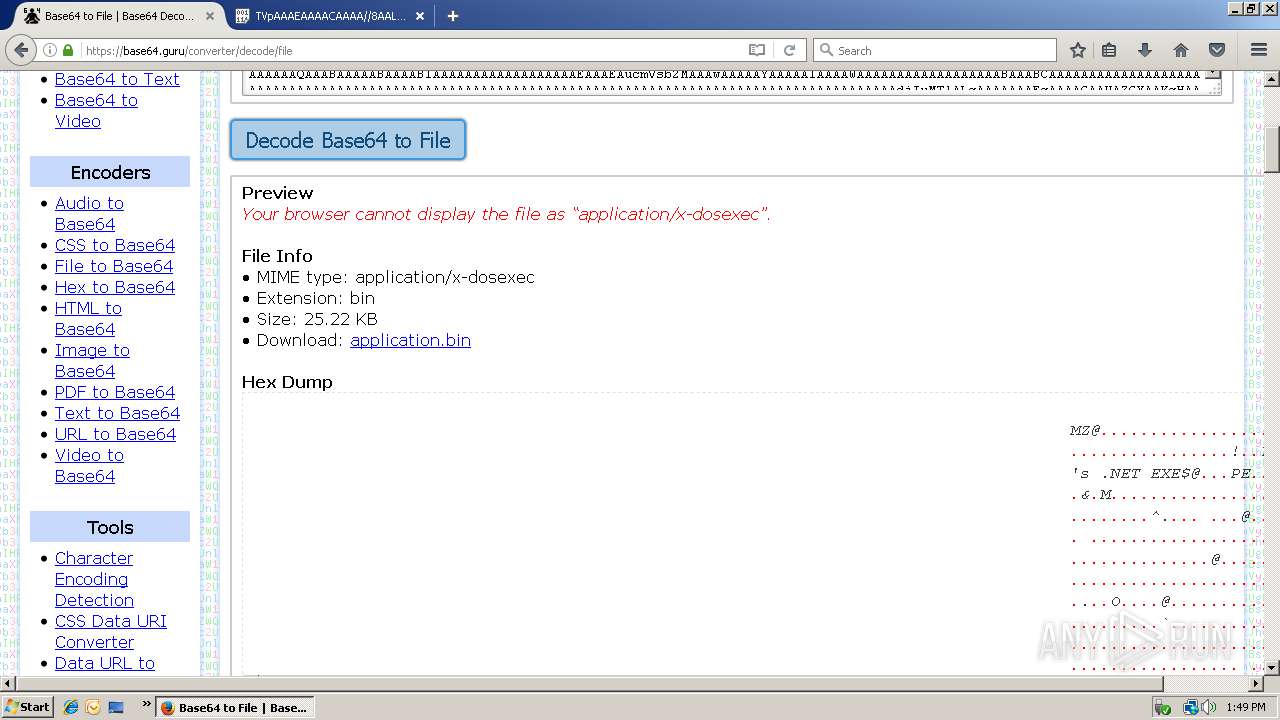
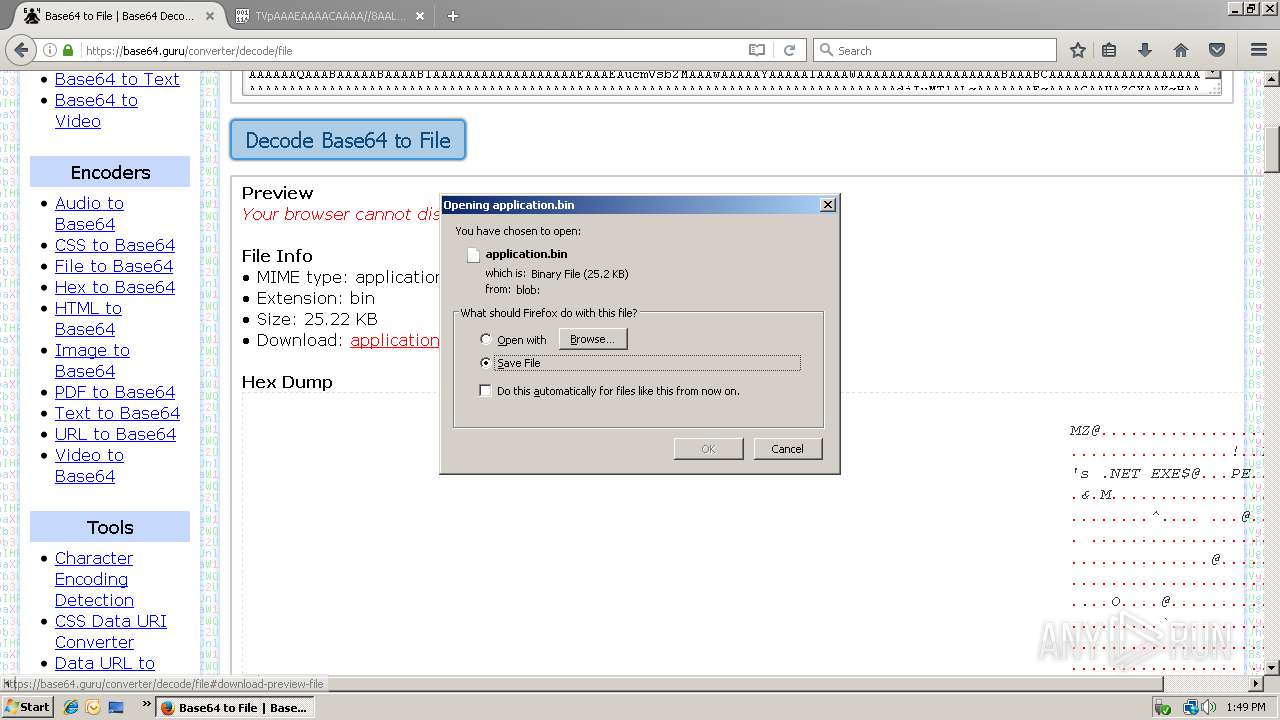
| URL: | https://base64.guru/converter/decode/file |
| Full analysis: | https://app.any.run/tasks/6698d5eb-d81f-411f-b21b-2e0a983f1891 |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2020, 13:47:18 |
| OS: | Windows Vista Business Service Pack 2 (build: 6002, 32 bit) |
| Indicators: | |
| MD5: | BEAE4DD9059DE2544CC61218E113C092 |
| SHA1: | A43A0AB999266128CF8E36DE24BE98540FAC6FBB |
| SHA256: | 1EE4E6664B6A404CF62FA6433E878D9C3098E8CB749EE9BEBEAEEA6A9C794170 |
| SSDEEP: | 3:N8ldGAk2Kxn:2TX6 |
MALICIOUS
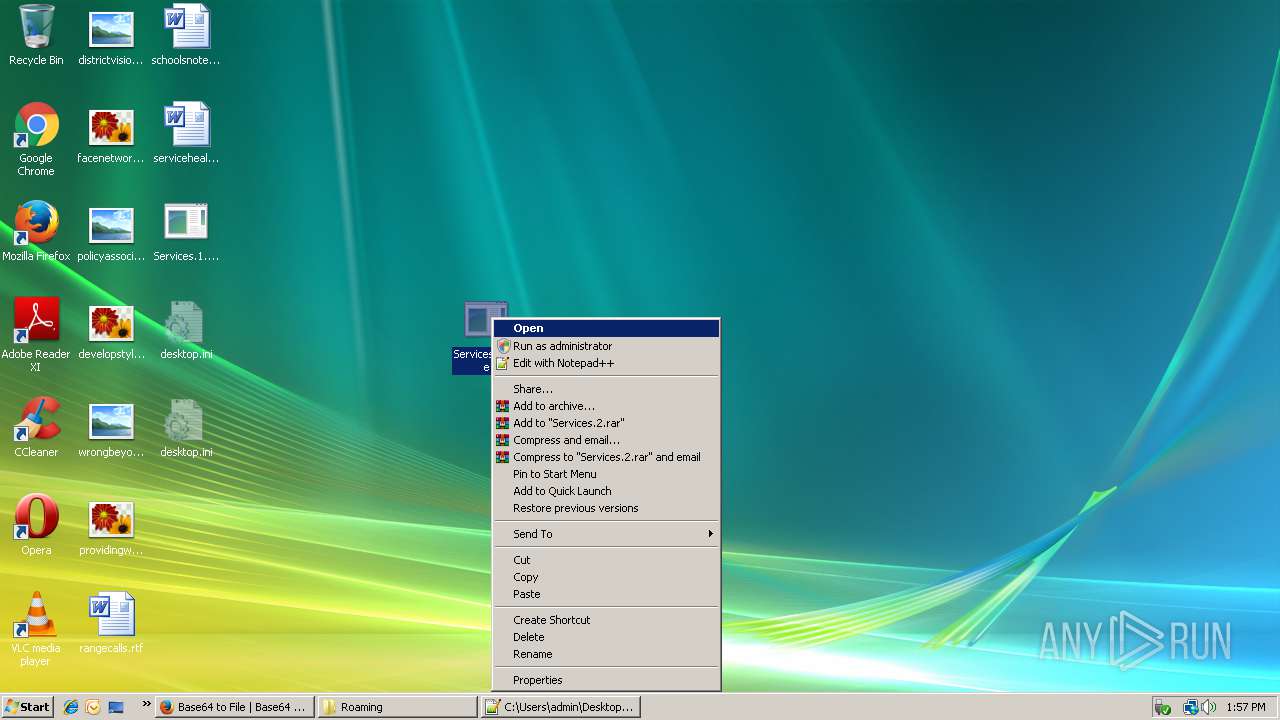
Application was dropped or rewritten from another process
- application.com (PID: 788)
- application.exe (PID: 2812)
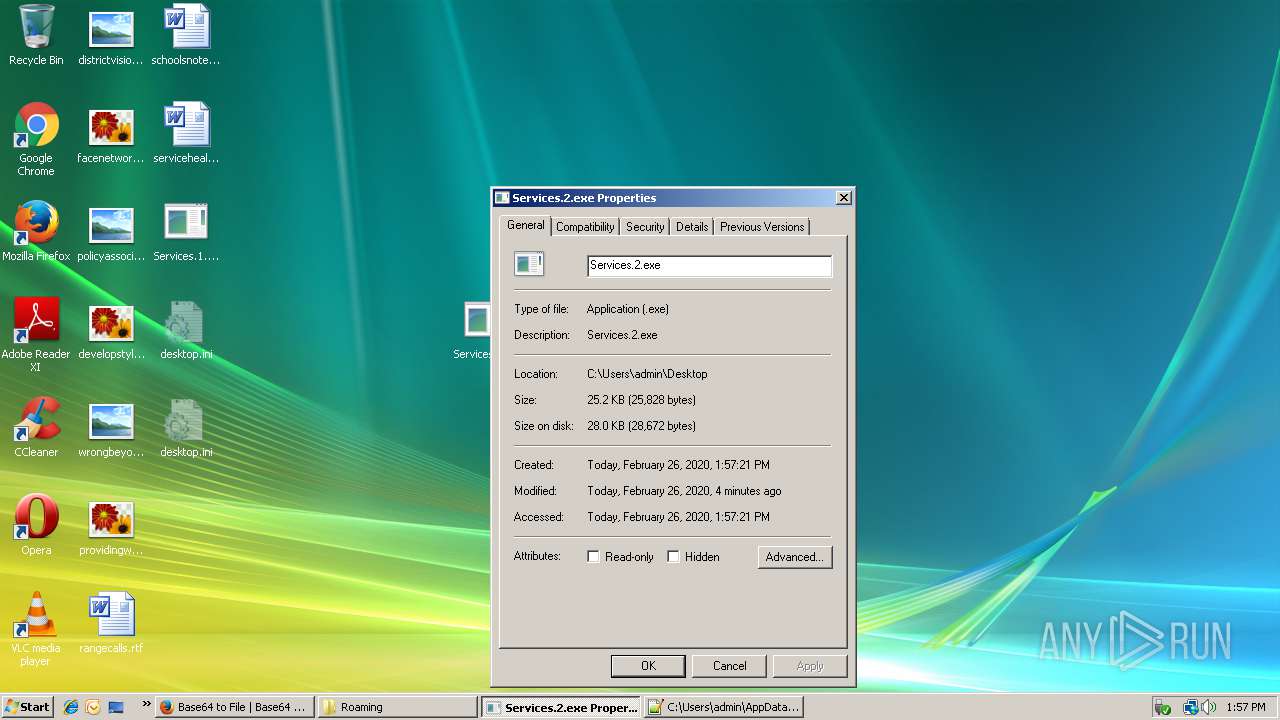
- Services.2.exe (PID: 2940)
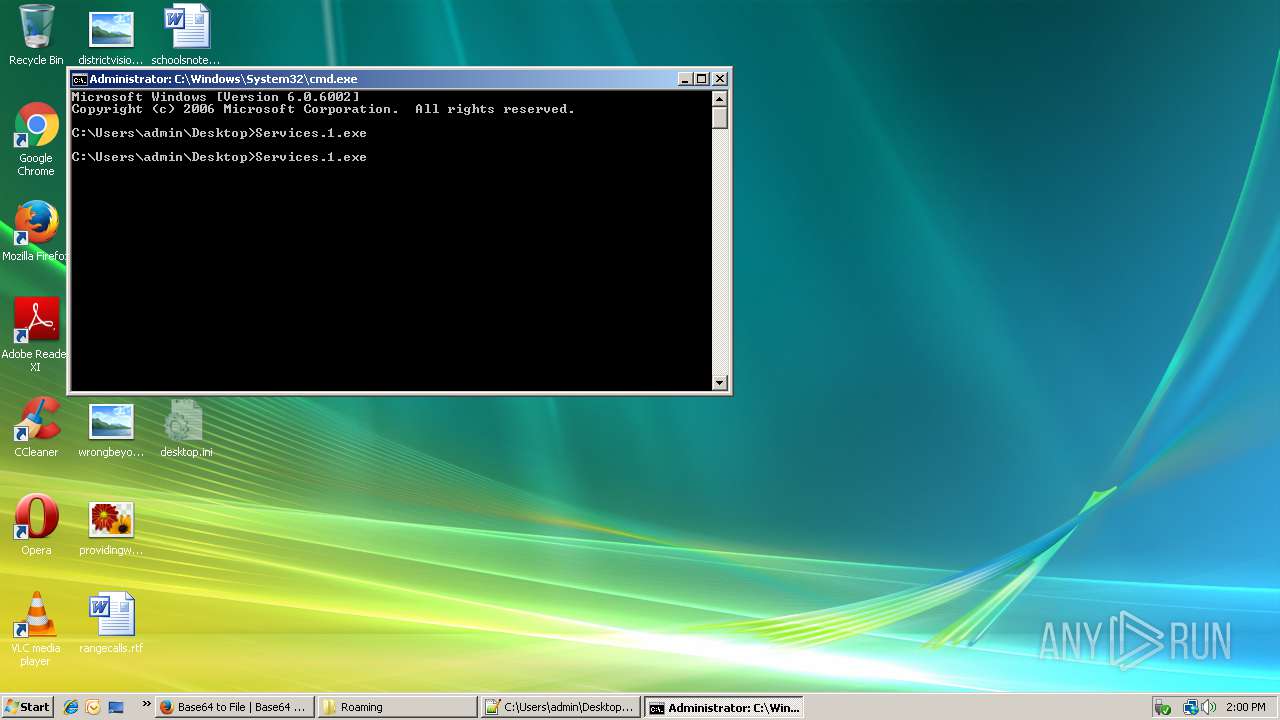
- Services.1.exe (PID: 3656)
SUSPICIOUS
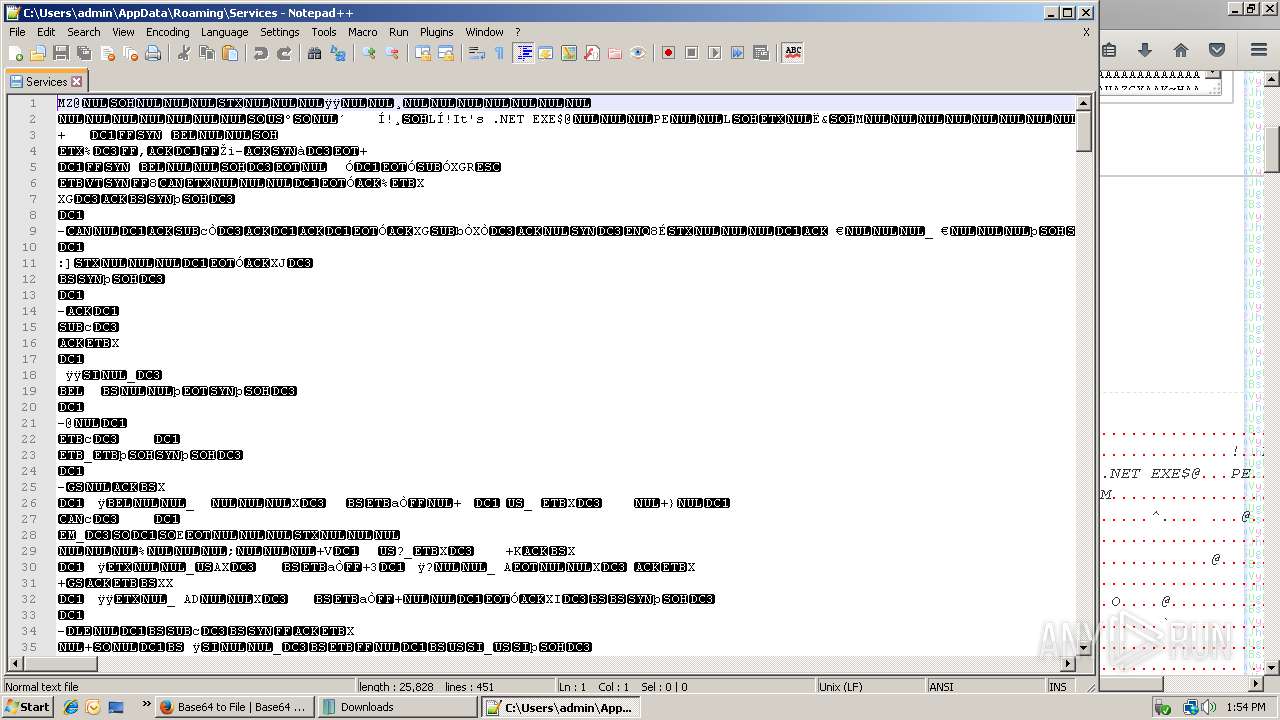
Executable content was dropped or overwritten
- firefox.exe (PID: 3432)
- application.com (PID: 788)
- notepad++.exe (PID: 712)
- Services.2.exe (PID: 2940)
- Services.1.exe (PID: 3656)
- application.exe (PID: 2812)
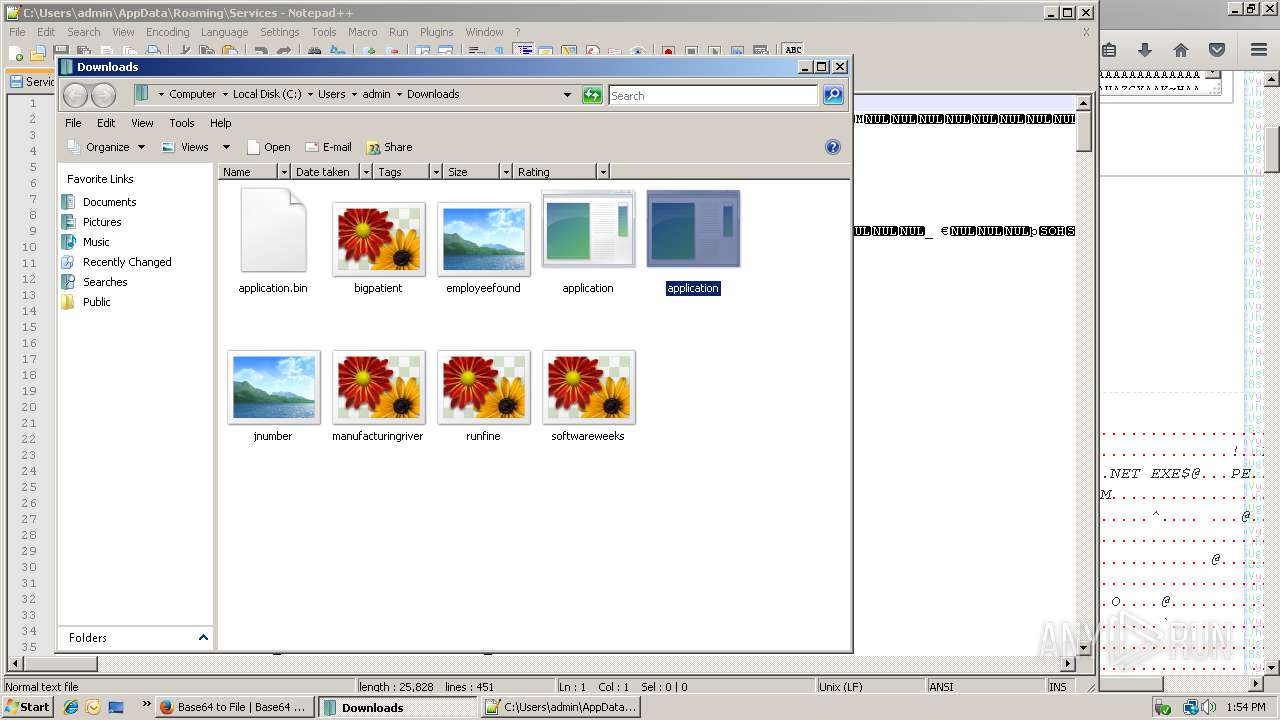
Creates files in the user directory
- application.exe (PID: 2812)
- application.com (PID: 788)
- notepad++.exe (PID: 712)
- Services.2.exe (PID: 2940)
- Services.1.exe (PID: 3656)
Uses RUNDLL32.EXE to load library
- application.com (PID: 788)
- application.exe (PID: 2812)
- explorer.exe (PID: 3696)
- Services.2.exe (PID: 2940)
- Services.1.exe (PID: 3656)
Application launched itself
- notepad++.exe (PID: 712)
Starts CMD.EXE for commands execution
- rundll32.exe (PID: 2696)
INFO
Reads CPU info
- firefox.exe (PID: 3432)
- firefox.exe (PID: 3264)
Application launched itself
- firefox.exe (PID: 3432)
Manual execution by user
- verclsid.exe (PID: 2152)
- verclsid.exe (PID: 3268)
- verclsid.exe (PID: 2724)
- verclsid.exe (PID: 3724)
- verclsid.exe (PID: 2708)
- verclsid.exe (PID: 2956)
- verclsid.exe (PID: 2480)
- application.com (PID: 788)
- verclsid.exe (PID: 3656)
- application.exe (PID: 2812)
- notepad++.exe (PID: 2692)
- verclsid.exe (PID: 2552)
- Services.2.exe (PID: 2940)
- notepad++.exe (PID: 2088)
Creates files in the user directory
- firefox.exe (PID: 3432)
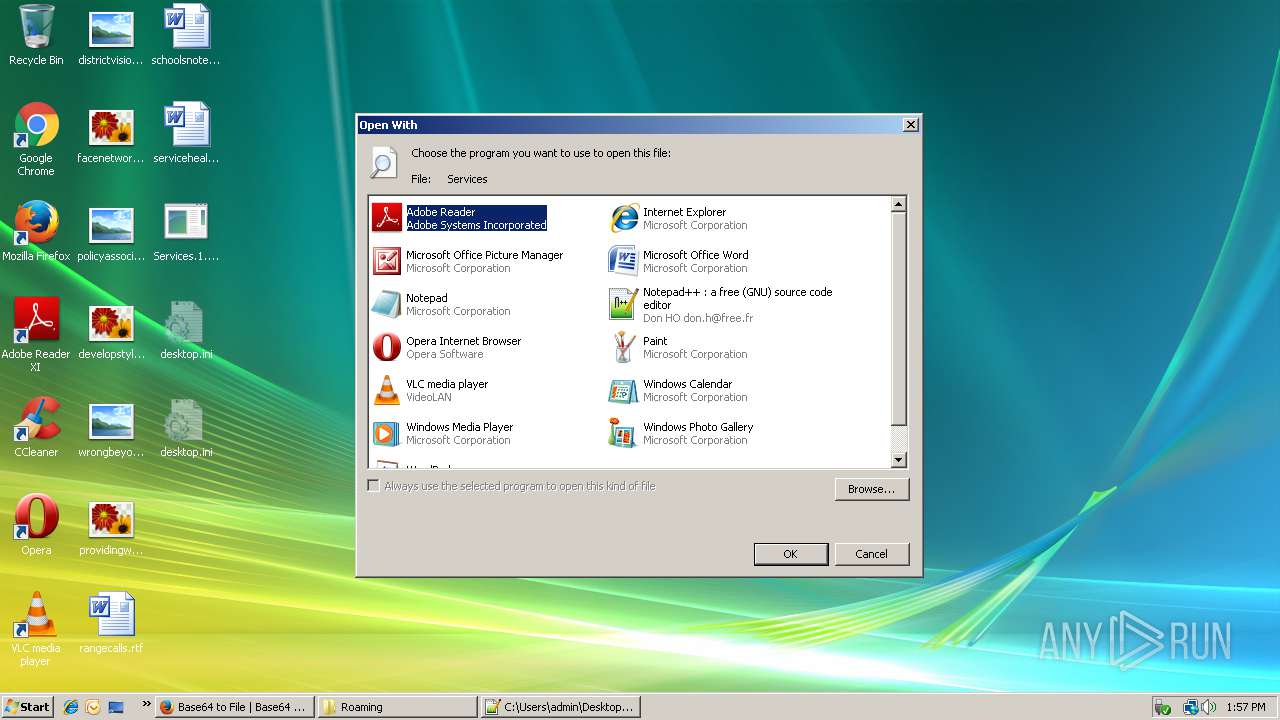
Modifies the open verb of a shell class
- rundll32.exe (PID: 2352)
- rundll32.exe (PID: 4088)
- rundll32.exe (PID: 2696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
71
Monitored processes
28
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 348 | C:\Windows\system32\conime.exe | C:\Windows\system32\conime.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console IME Exit code: 0 Version: 6.0.6002.18005 (lh_sp2rtm.090410-1830) Modules
| |||||||||||||||
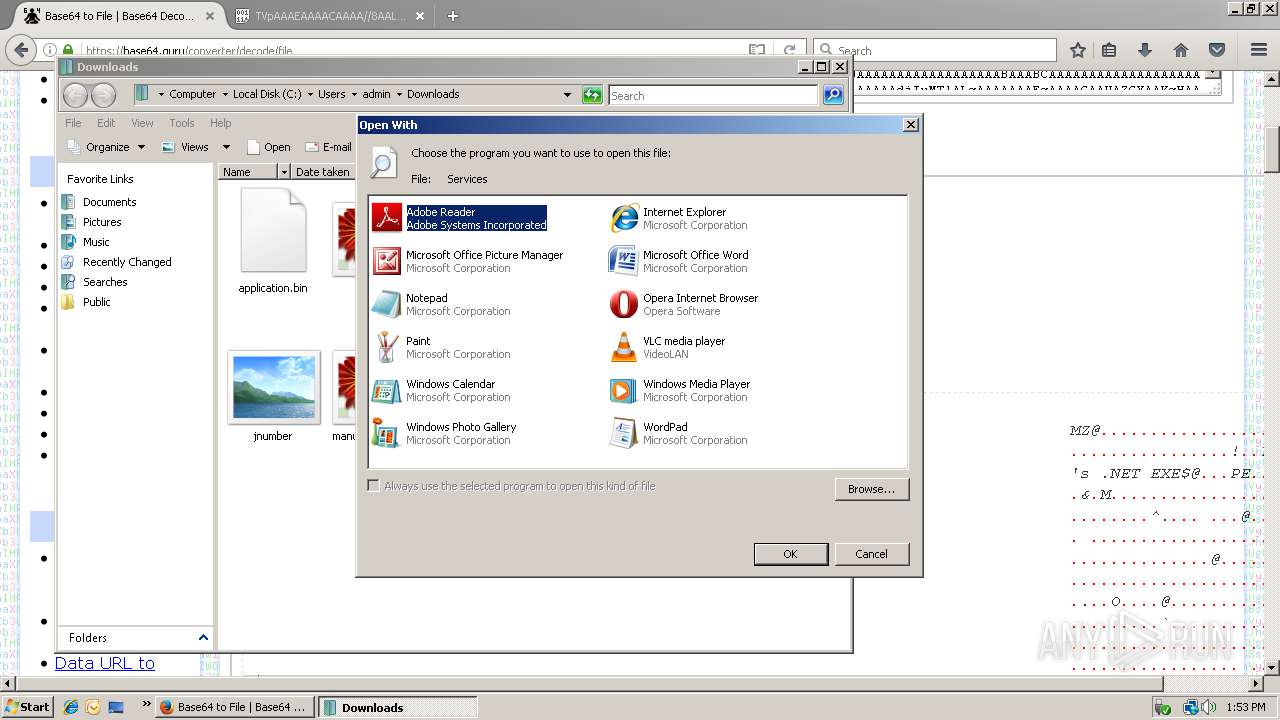
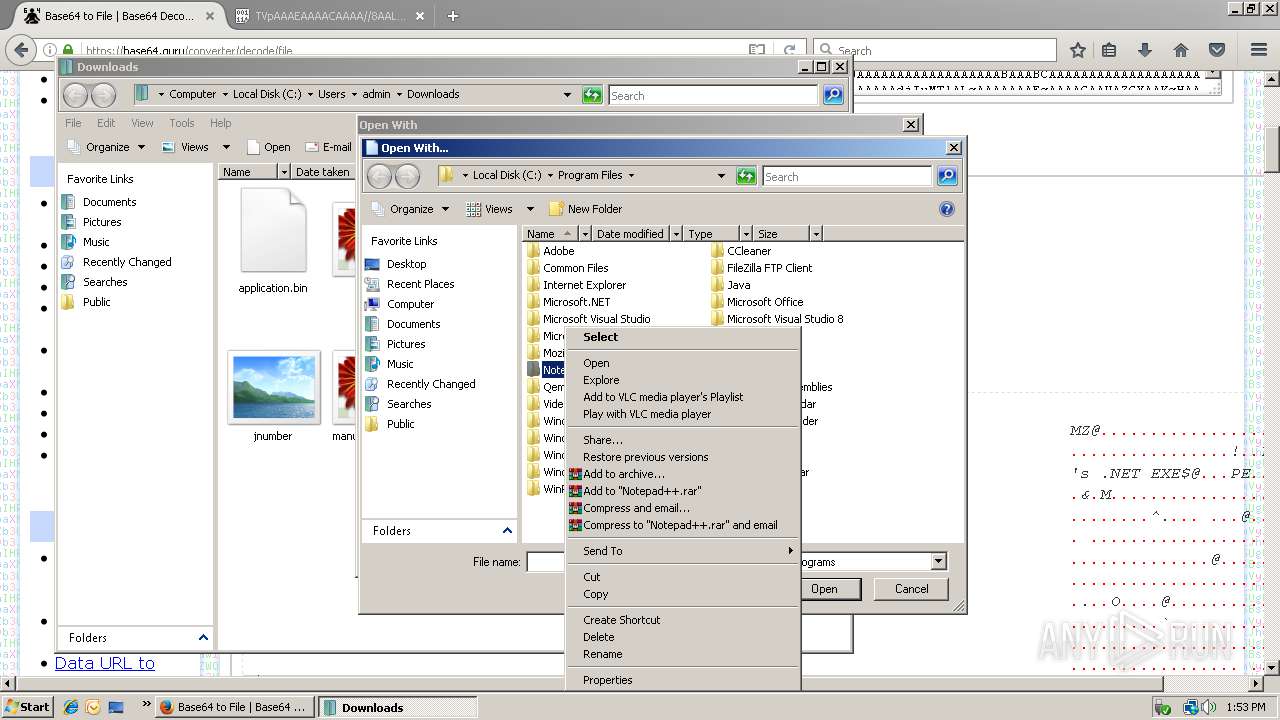
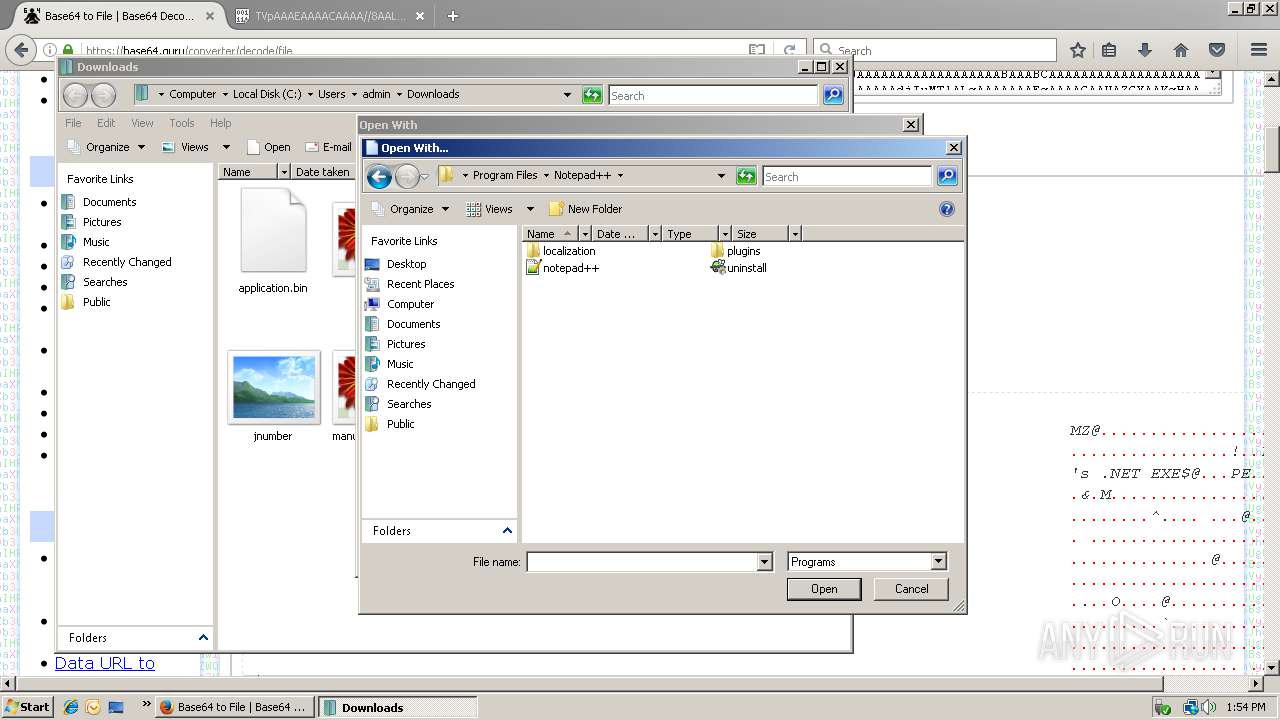
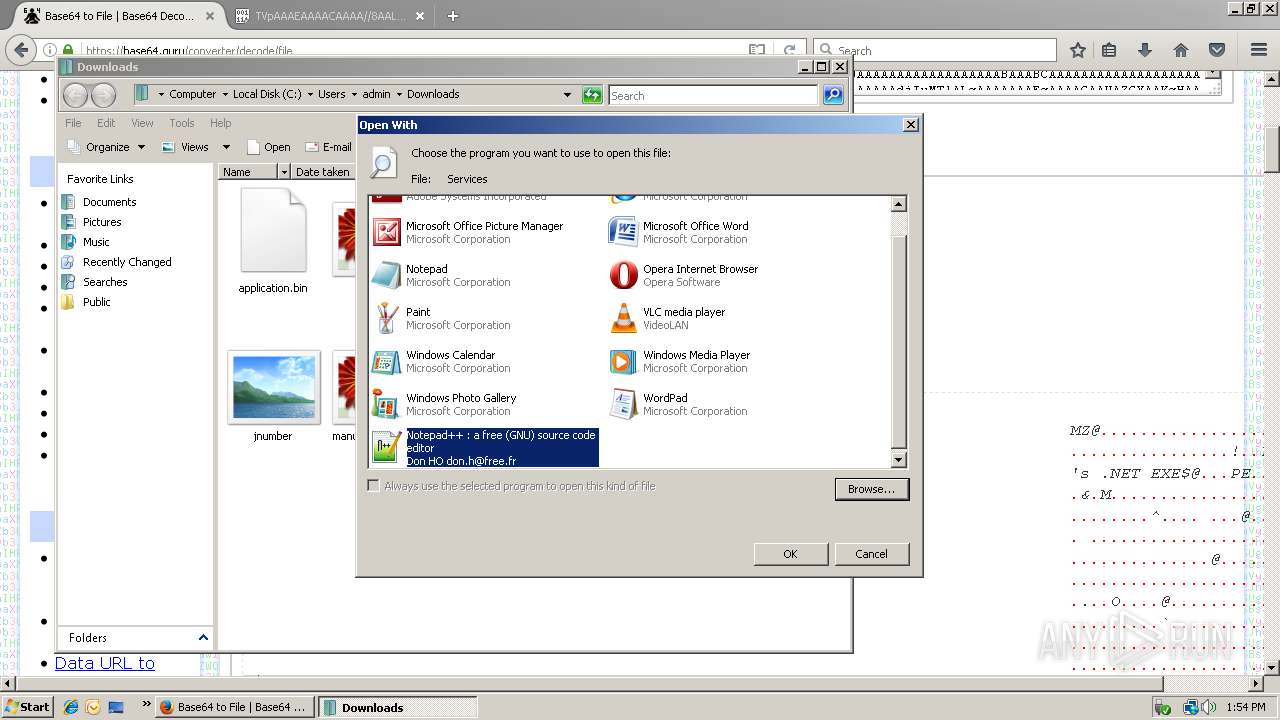
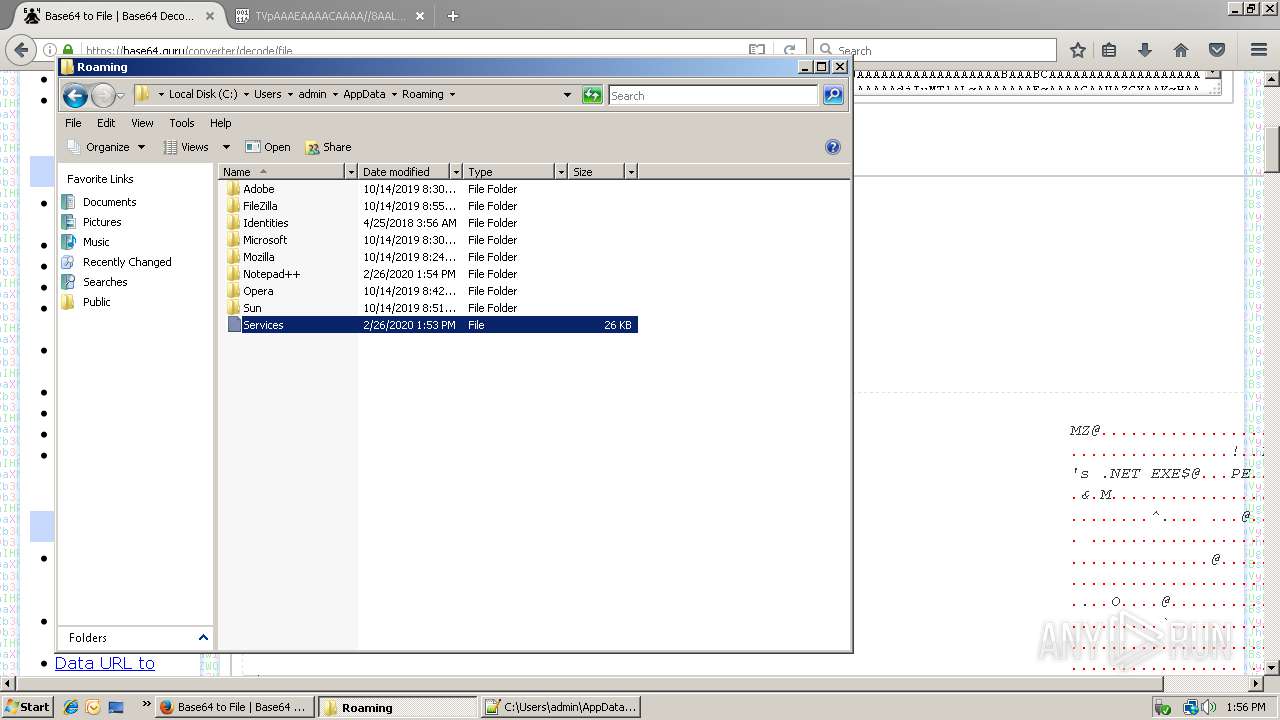
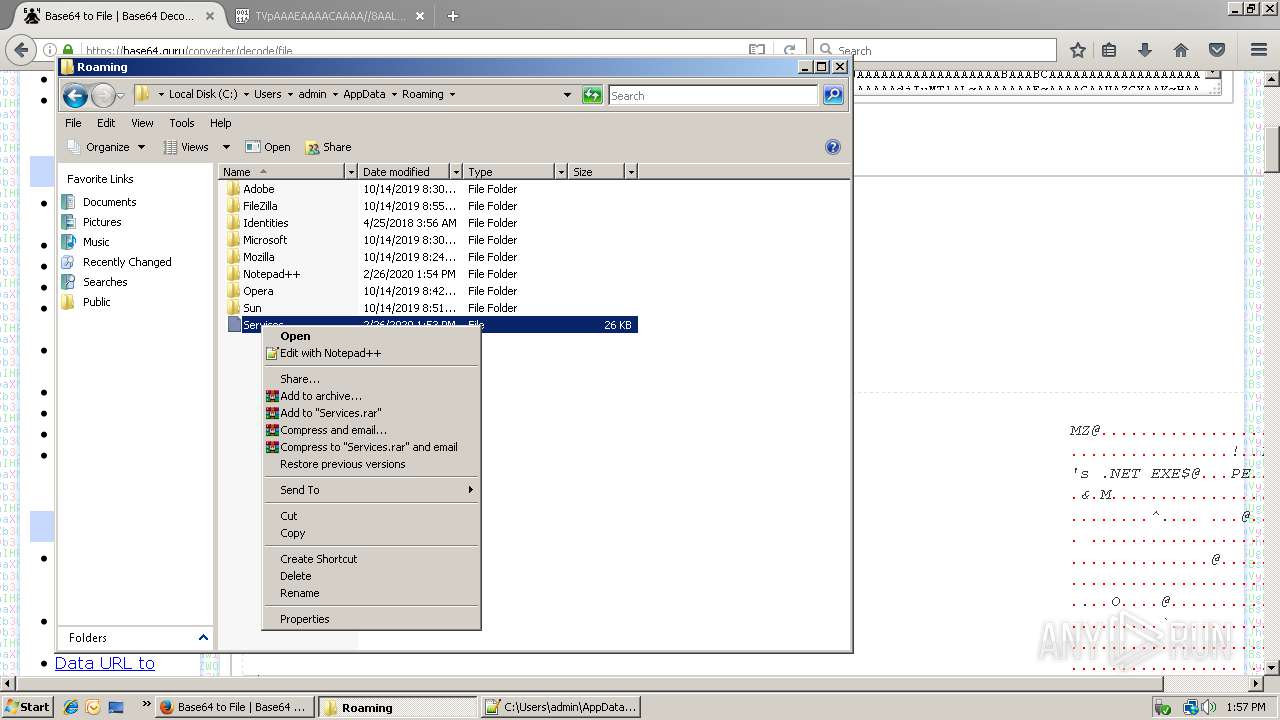
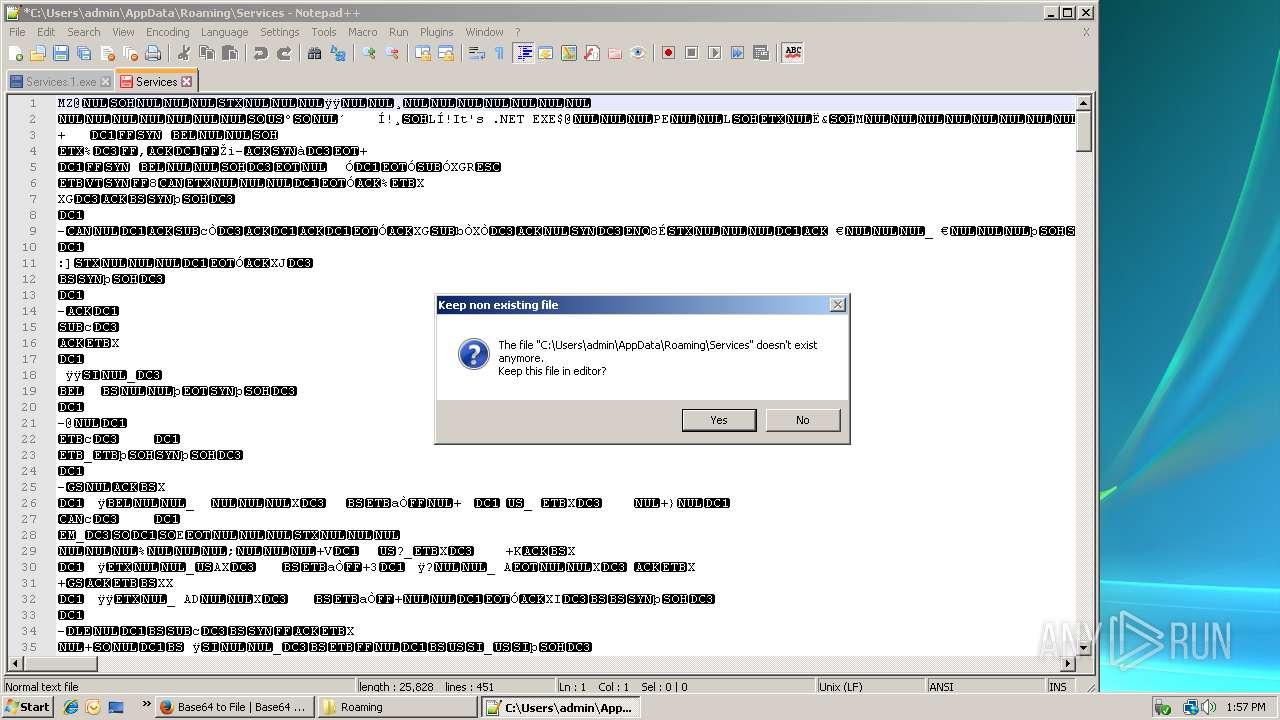
| 712 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\AppData\Roaming\Services" | C:\Program Files\Notepad++\notepad++.exe | rundll32.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.54 Modules
| |||||||||||||||
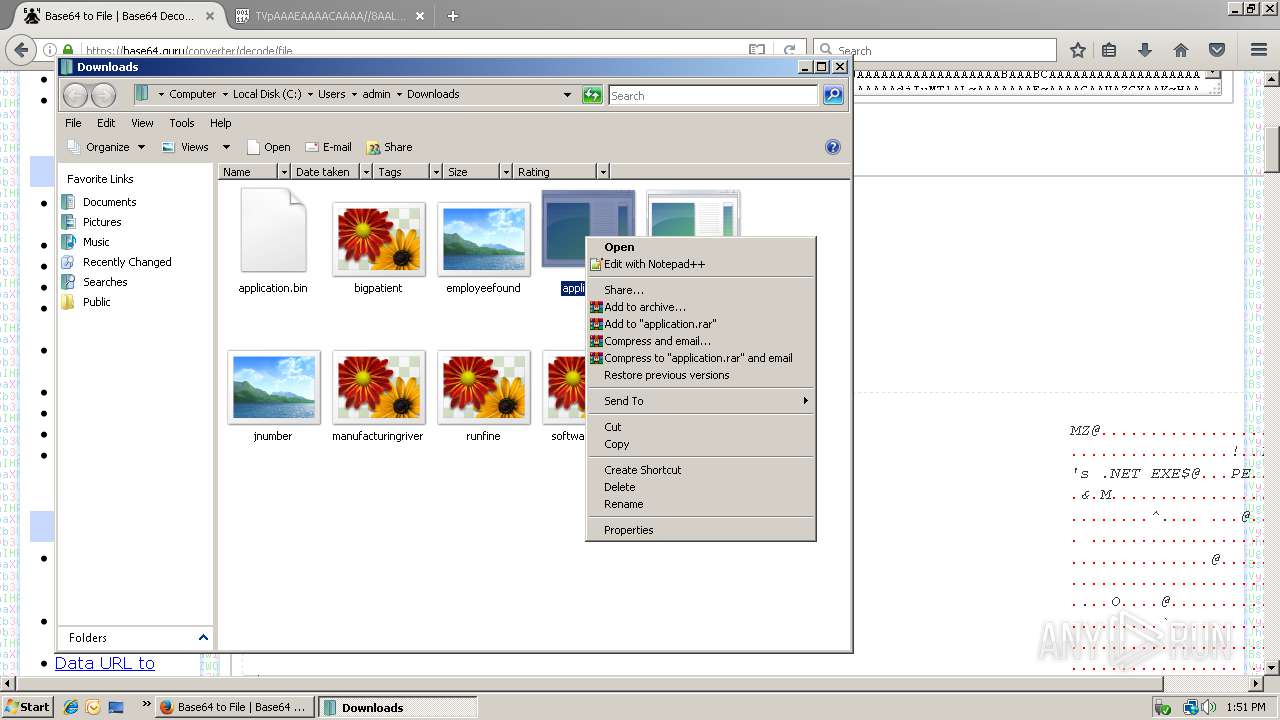
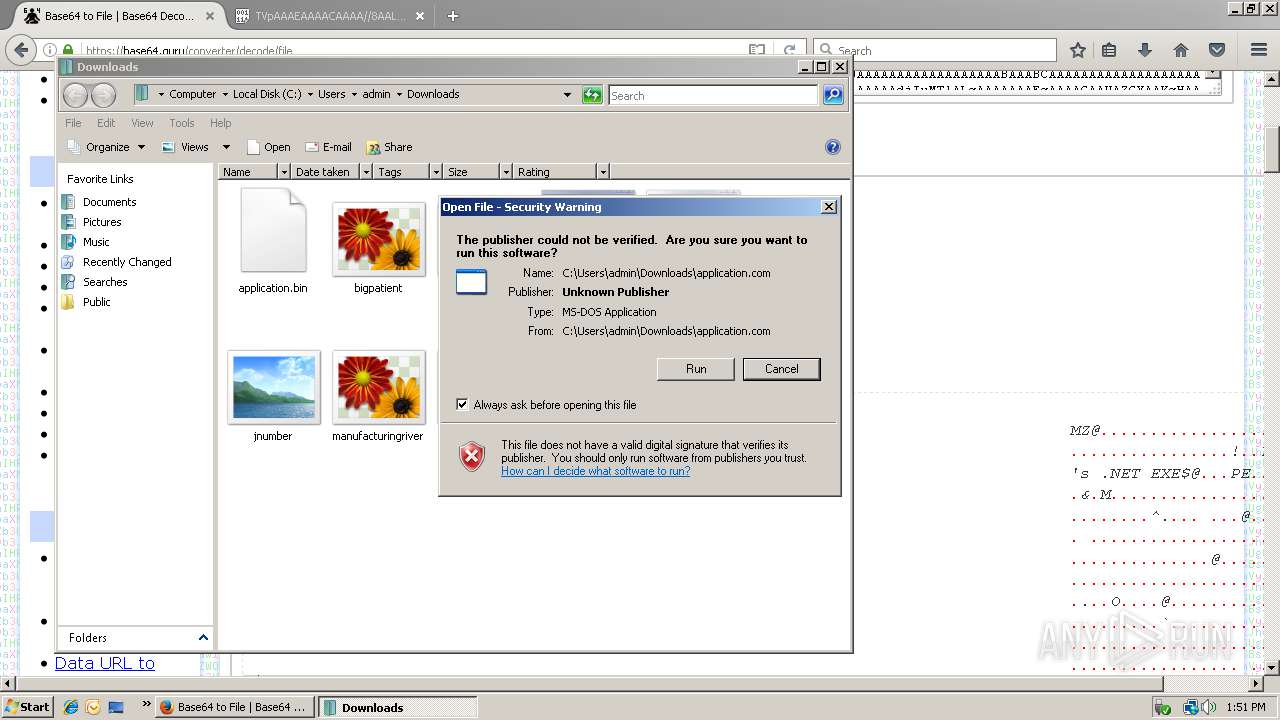
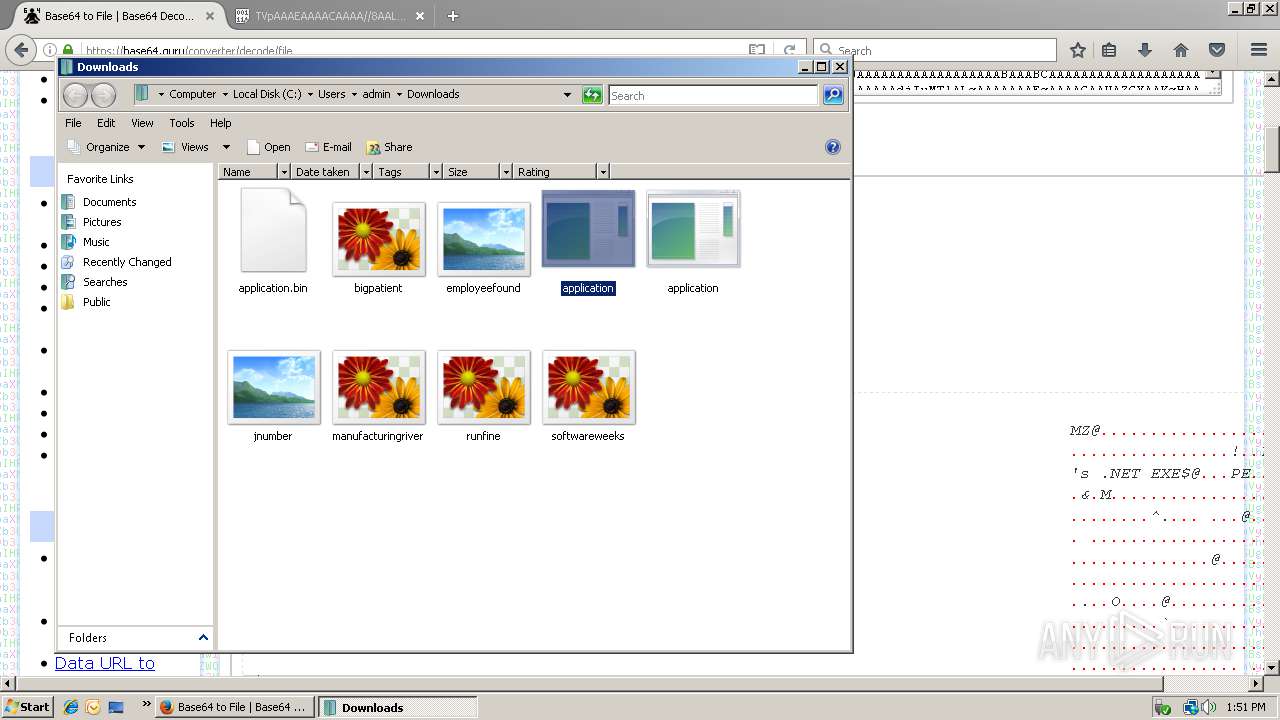
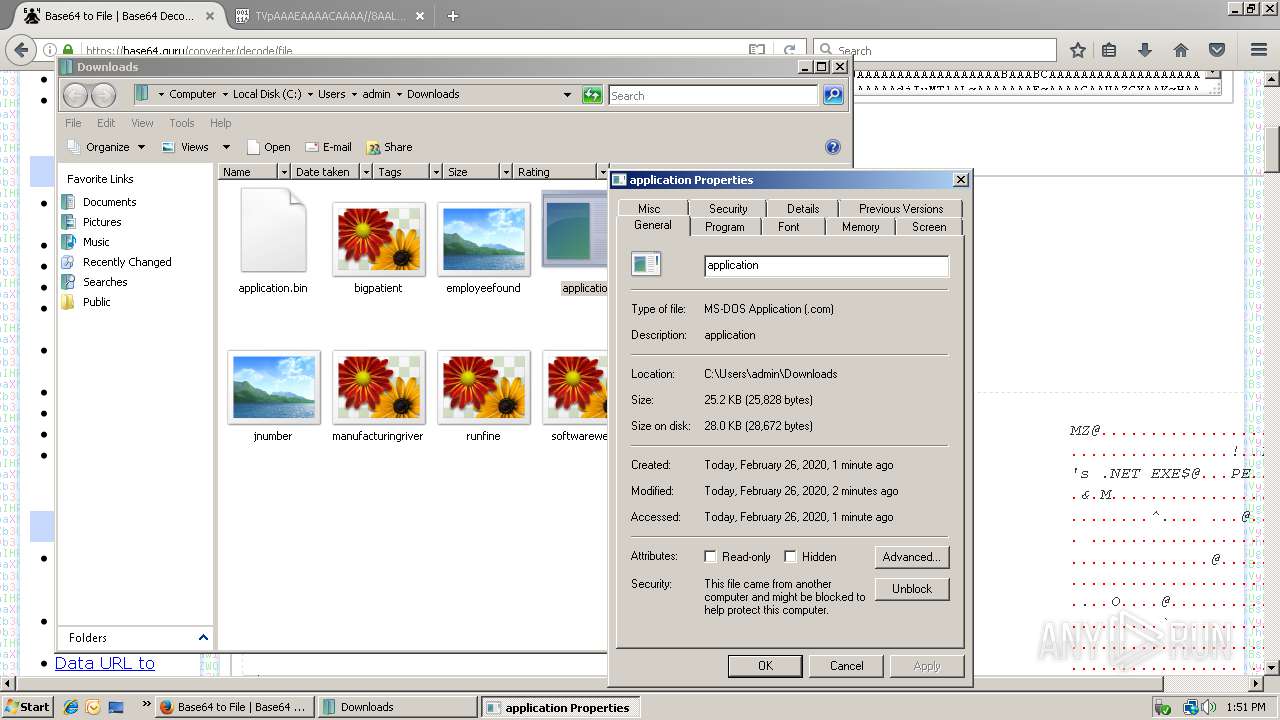
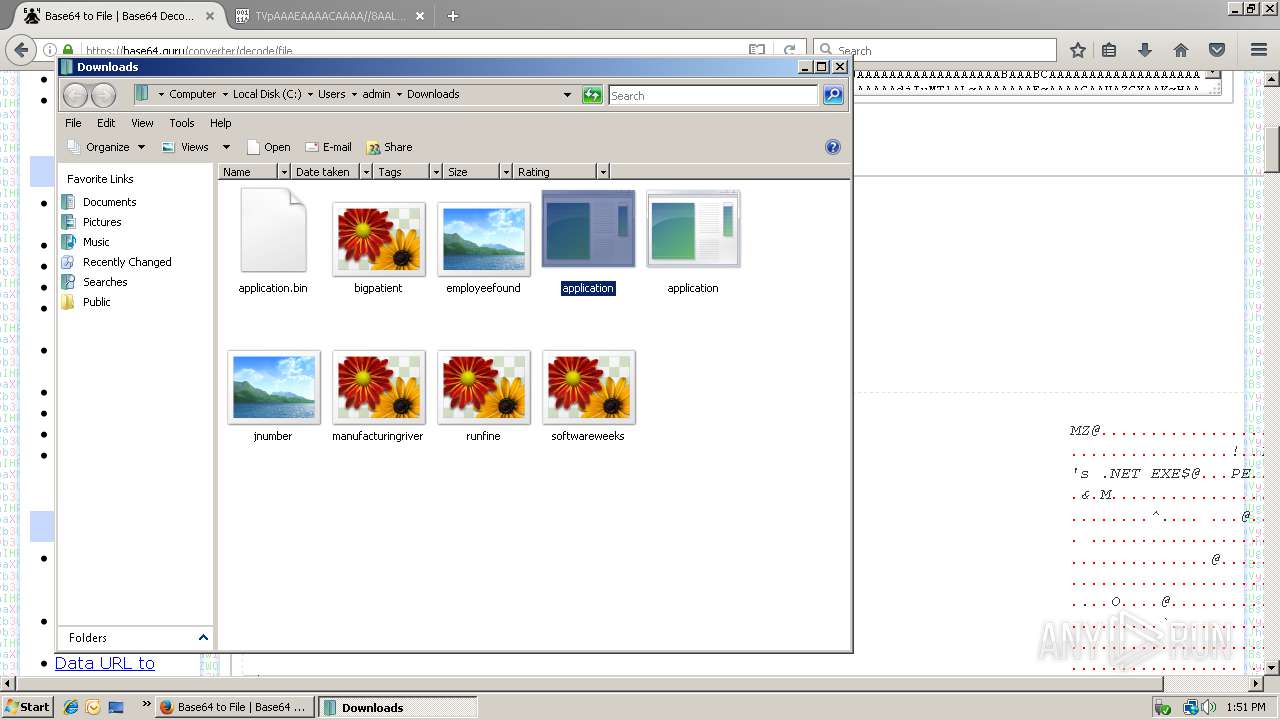
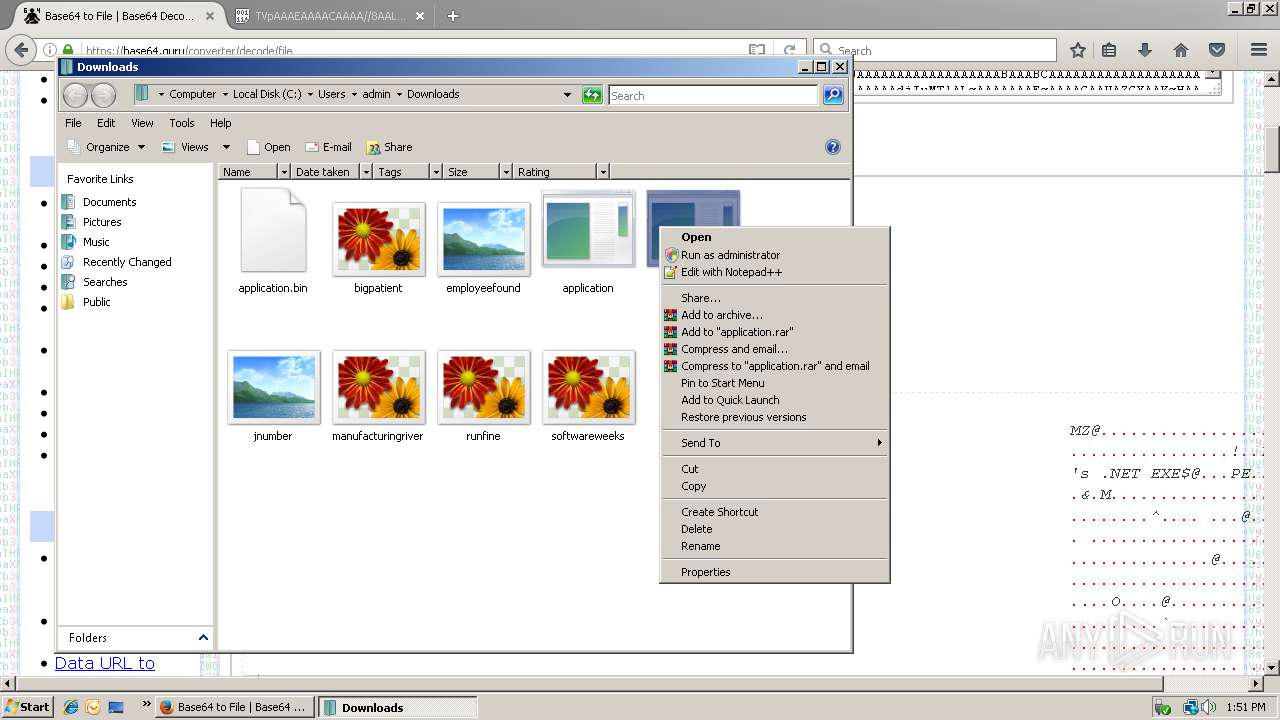
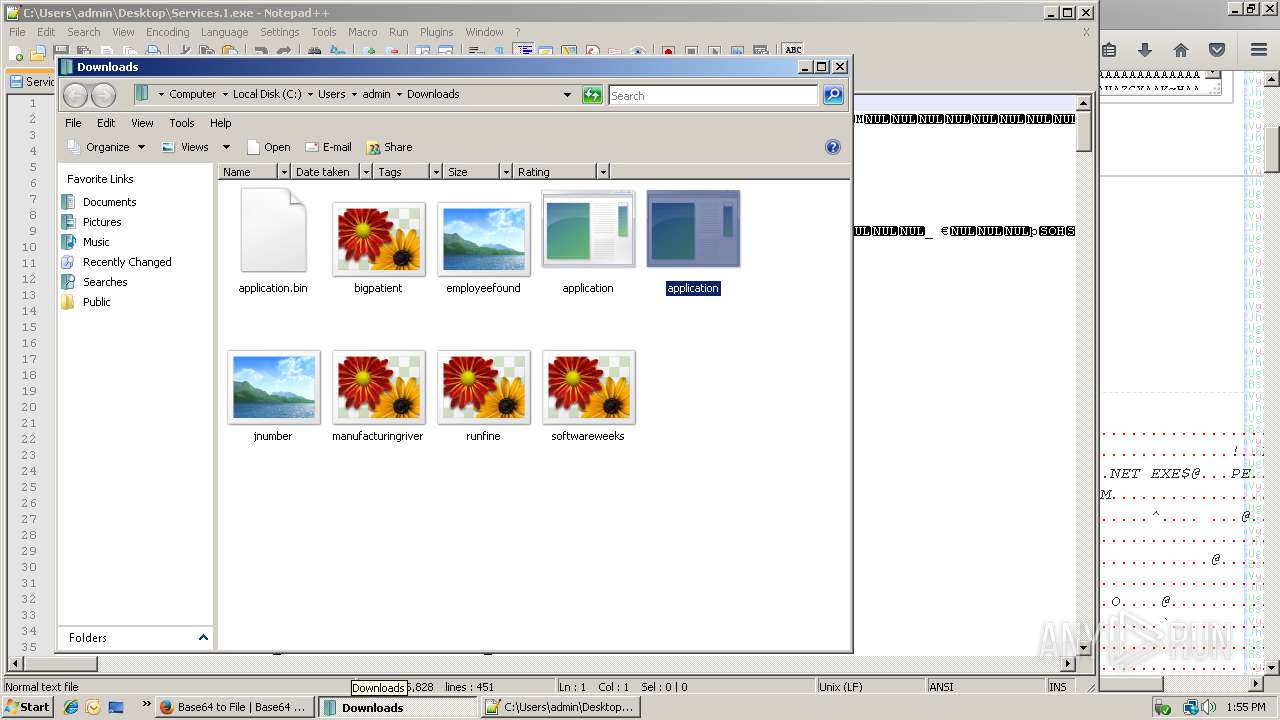
| 788 | "C:\Users\admin\Downloads\application.com" | C:\Users\admin\Downloads\application.com | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2088 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Downloads\application.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.54 Modules
| |||||||||||||||
| 2152 | "C:\Windows\system32\verclsid.exe" /S /C {596AB062-B4D2-4215-9F74-E9109B0A8153} /I {000214E9-0000-0000-C000-000000000046} /X 0x401 | C:\Windows\system32\verclsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extension CLSID Verification Host Exit code: 0 Version: 6.0.6000.16386 (vista_rtm.061101-2205) Modules
| |||||||||||||||
| 2348 | "C:\Windows\System32\cmd.exe" "C:\Users\admin\AppData\Roaming\Services" | C:\Windows\System32\cmd.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.0.6000.16386 (vista_rtm.061101-2205) Modules
| |||||||||||||||
| 2352 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Roaming\Services | C:\Windows\system32\rundll32.exe | — | Services.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.0.6000.16386 (vista_rtm.061101-2205) Modules
| |||||||||||||||
| 2360 | "C:\Program Files\Windows NT\Accessories\WORDPAD.EXE" "C:\Users\admin\AppData\Roaming\Services" | C:\Program Files\Windows NT\Accessories\WORDPAD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Wordpad Application Exit code: 0 Version: 6.0.6000.16386 (vista_rtm.061101-2205) Modules
| |||||||||||||||
| 2480 | "C:\Windows\system32\verclsid.exe" /S /C {513D916F-2A8E-4F51-AEAB-0CBC76FB1AF8} /I {000214E9-0000-0000-C000-000000000046} /X 0x401 | C:\Windows\system32\verclsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extension CLSID Verification Host Exit code: 0 Version: 6.0.6000.16386 (vista_rtm.061101-2205) Modules
| |||||||||||||||
| 2552 | "C:\Windows\system32\verclsid.exe" /S /C {7EFA68C6-086B-43E1-A2D2-55A113531240} /I {000214E9-0000-0000-C000-000000000046} /X 0x401 | C:\Windows\system32\verclsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extension CLSID Verification Host Exit code: 3 Version: 6.0.6000.16386 (vista_rtm.061101-2205) Modules
| |||||||||||||||
Total events
3 907
Read events
3 254
Write events
642
Delete events
11
Modification events
| (PID) Process: | (3432) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{9da96397-48b9-11e8-bb1b-806e6f6e6963} |
| Operation: | write | Name: | BaseClass |
Value: Drive | |||
| (PID) Process: | (3432) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | MigrateProxy |
Value: 1 | |||
| (PID) Process: | (3432) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3432) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000002F000000010000000000000000000000000000000000000000000000A064E98E49DCD301000000000000000000000000030000001700000000000000FE800000000000008C79D8E2DC06194A0800000070C7E77580C7E775B0F1E875F8C7E775010000005044393800000000000000000000000000000000000000000000000000000000000000000800000000000000E8DB1900E0A65C0400080000020000000000006000000020F00A000040595D04020000001700000000000000FE8000000000000000005EFEC0A801F80900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002C00000020000000C8000000000000000000000000000000000000000000000000000000070000000000000000000000000000000000000002000000C0A801F8000000000000000000000000000000000000000000000000181002C00000000000000000000000000000000001000000485F4C040000000000000000000000000100000000000000FFFFFFFFFFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000001C00000000 | |||
| (PID) Process: | (3432) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3432) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (788) application.com | Key: | HKEY_CURRENT_USER |
| Operation: | write | Name: | di |
Value: ! | |||
| (PID) Process: | (3776) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{9da96397-48b9-11e8-bb1b-806e6f6e6963} |
| Operation: | write | Name: | BaseClass |
Value: Drive | |||
| (PID) Process: | (3776) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (3776) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office12\OIS.EXE |
Value: Microsoft Office Picture Manager | |||
Executable files
7
Suspicious files
343
Text files
153
Unknown types
57
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3432 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\xdgwq2fe.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 3432 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\xdgwq2fe.default\pluginreg.dat.tmp | — | |
MD5:— | SHA256:— | |||
| 3432 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\xdgwq2fe.default\cache2\entries\0C9EDA557001CC75CF75B75B38FB3D432636836C | compressed | |
MD5:— | SHA256:— | |||
| 3432 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\xdgwq2fe.default\cache2\entries\0F93D7B5588BE55B8ADBC70692BDCA9BC70BCD2D | image | |
MD5:— | SHA256:— | |||
| 3432 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\xdgwq2fe.default\cache2\entries\EB6716021FF919BE6F3EB4368005756C26416B60 | binary | |
MD5:— | SHA256:— | |||
| 3432 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\xdgwq2fe.default\safebrowsing-backup | — | |
MD5:— | SHA256:— | |||
| 3432 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\xdgwq2fe.default\cache2\entries\9ECE75DCFB73B863A3B5B42C3C57851DDA8B477C | image | |
MD5:— | SHA256:— | |||
| 3432 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\xdgwq2fe.default\cache2\entries\780095100CBA241B48DA1F80004E1F0ACAF675CB | compressed | |
MD5:— | SHA256:— | |||
| 3432 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\xdgwq2fe.default\pluginreg.dat | text | |
MD5:— | SHA256:— | |||
| 3432 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\xdgwq2fe.default\cache2\entries\DDC6770BCF19C5611D819DBDC678F583C57A388B | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
464
TCP/UDP connections
322
DNS requests
435
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
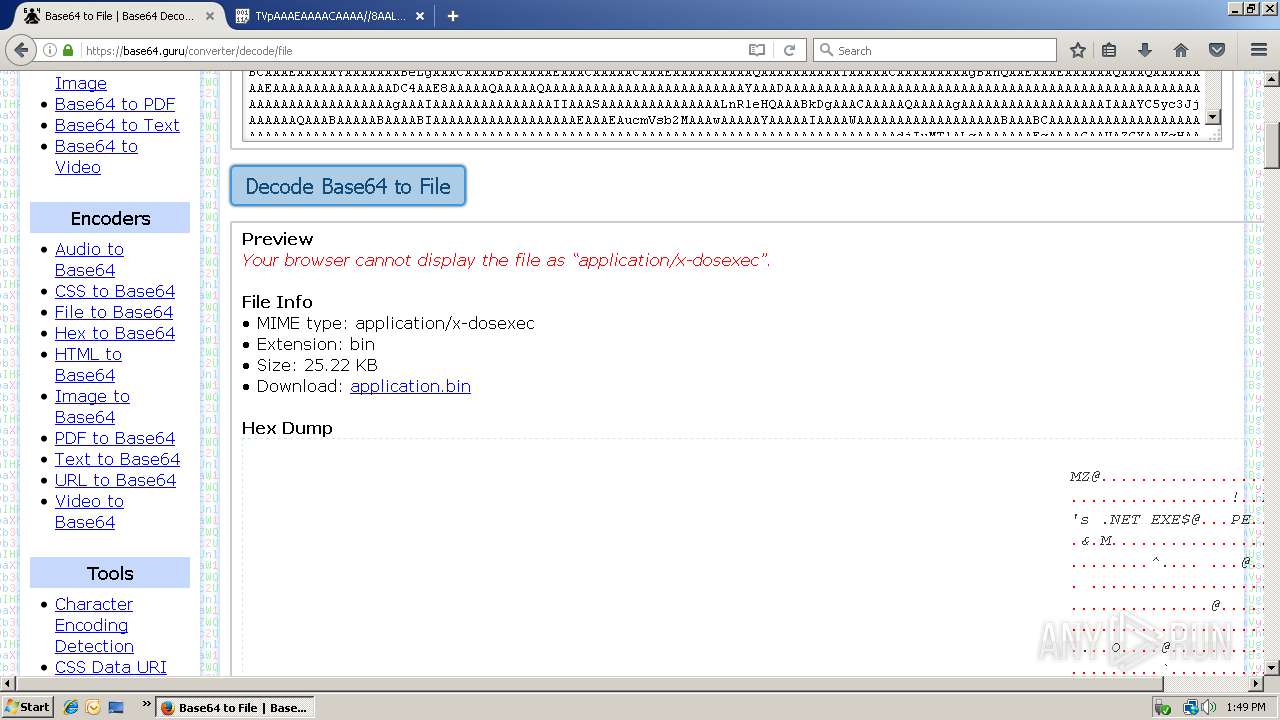
3432 | firefox.exe | GET | 200 | 104.27.142.51:443 | https://base64.guru/converter/decode/file | US | html | 48.1 Kb | malicious |
3432 | firefox.exe | GET | 200 | 52.11.143.45:443 | https://search.services.mozilla.com/1/firefox/50.0.2/esr/en-US/DE/default/default | US | text | 152 b | whitelisted |
3432 | firefox.exe | GET | 200 | 104.27.142.51:443 | https://static.base64.guru/css/style.min.css?1.0.60 | US | text | 11.1 Kb | whitelisted |
3432 | firefox.exe | GET | 200 | 104.27.142.51:443 | https://static.base64.guru/js/comments.min.js?1.0.37 | US | text | 2.79 Kb | whitelisted |
3432 | firefox.exe | GET | 200 | 172.217.16.136:443 | https://www.googletagmanager.com/gtag/js?id=UA-134607367-1 | US | text | 74.4 Kb | whitelisted |
3432 | firefox.exe | GET | 200 | 104.27.142.51:443 | https://static.base64.guru/js/form_base64.min.js?1.0.37 | US | text | 4.35 Kb | whitelisted |
3432 | firefox.exe | GET | 200 | 172.217.16.194:443 | https://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js | US | text | 105 Kb | whitelisted |
3432 | firefox.exe | GET | 200 | 172.217.18.162:443 | https://googleads.g.doubleclick.net/pagead/html/r20200224/r20190131/zrt_lookup.html | US | html | 9.77 Kb | whitelisted |
3432 | firefox.exe | GET | 200 | 172.217.22.66:443 | https://adservice.google.fr/adsid/integrator.js?domain=base64.guru | US | text | 109 b | whitelisted |
3432 | firefox.exe | GET | 200 | 216.58.207.46:443 | https://www.google-analytics.com/analytics.js | US | text | 44.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3432 | firefox.exe | 52.11.143.45:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3432 | firefox.exe | 104.27.142.51:443 | base64.guru | Cloudflare Inc | US | unknown |
3432 | firefox.exe | 172.217.16.194:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
3432 | firefox.exe | 172.217.22.66:443 | adservice.google.fr | Google Inc. | US | whitelisted |
3432 | firefox.exe | 216.58.210.2:443 | adservice.google.com | Google Inc. | US | whitelisted |
3432 | firefox.exe | 172.217.18.162:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
3432 | firefox.exe | 216.58.205.226:443 | adservice.google.com | Google Inc. | US | whitelisted |
3432 | firefox.exe | 216.58.207.46:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3432 | firefox.exe | 64.233.167.156:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
3432 | firefox.exe | 172.217.23.142:443 | safebrowsing.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
base64.guru |
| malicious |
static.base64.guru |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
pagead46.l.doubleclick.net |
| whitelisted |
www-googletagmanager.l.google.com |
| whitelisted |
adservice.google.fr |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1240 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1240 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|