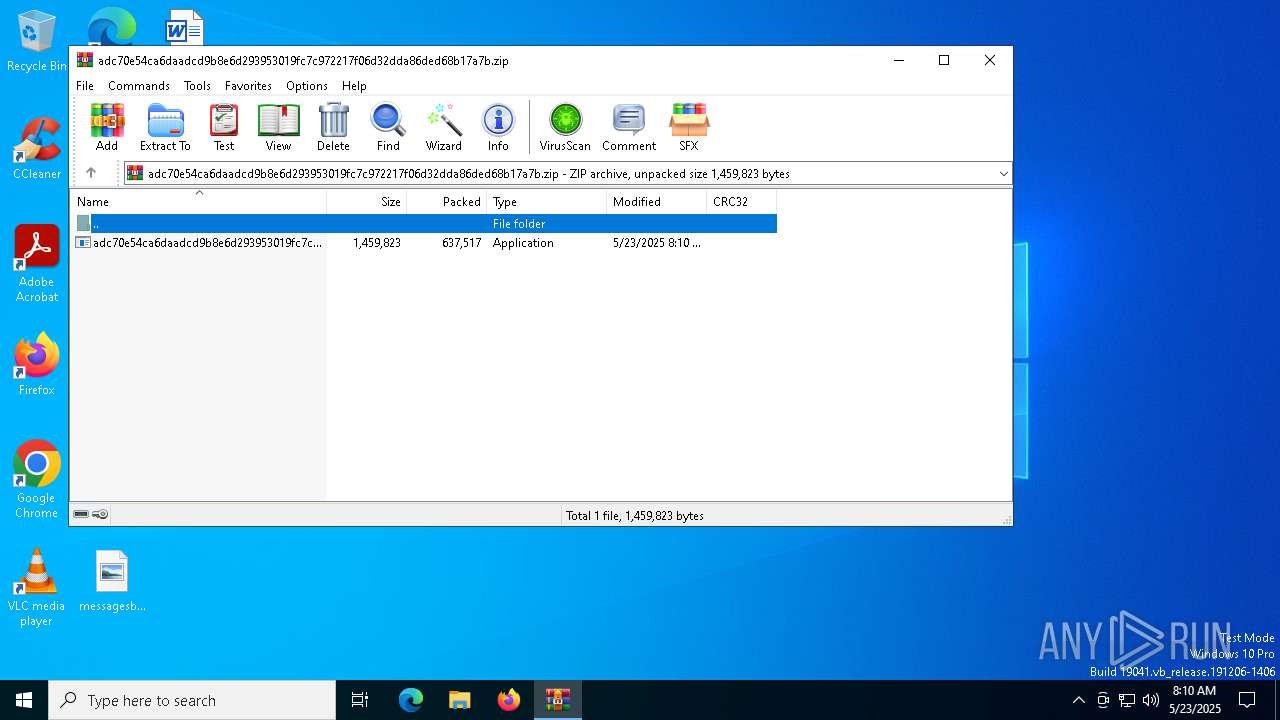
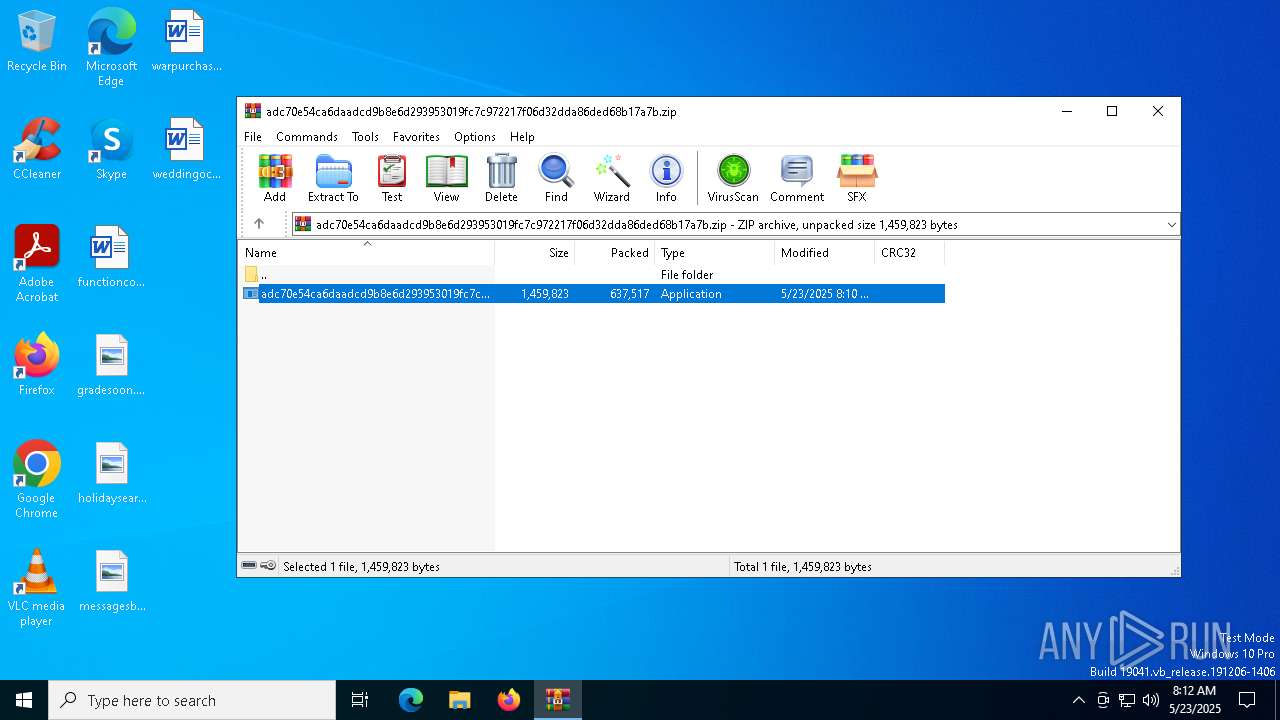
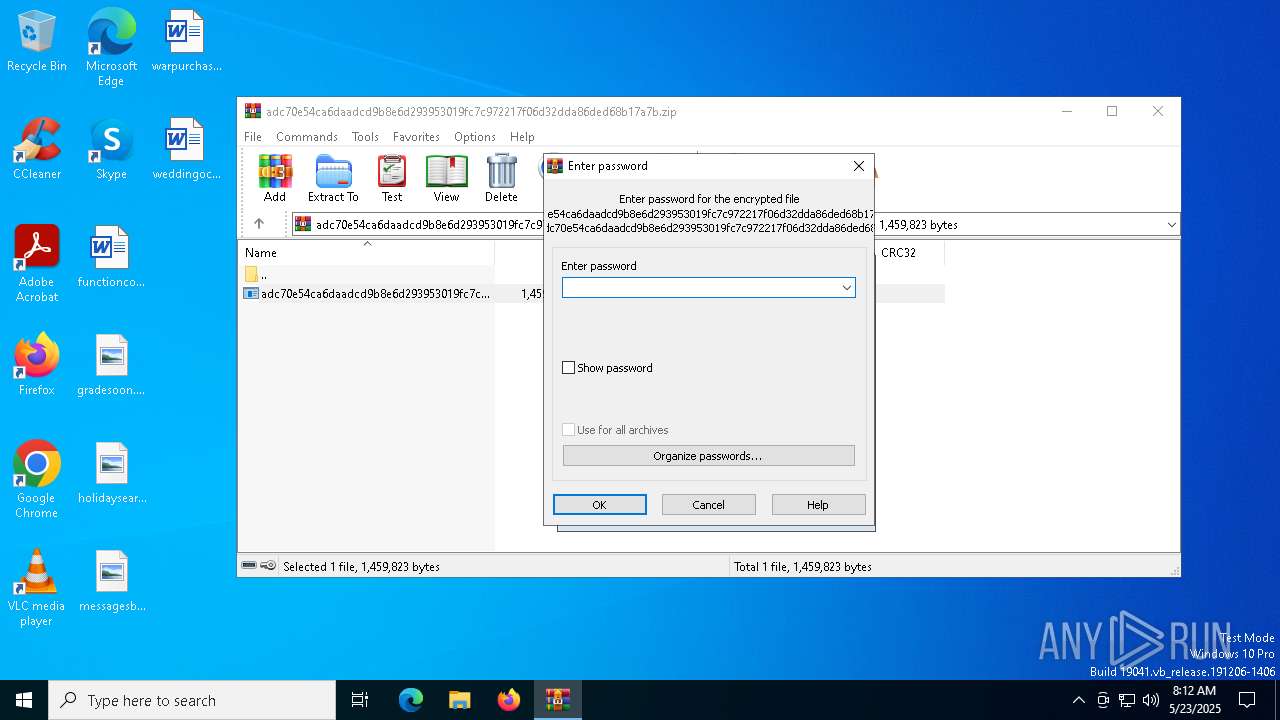
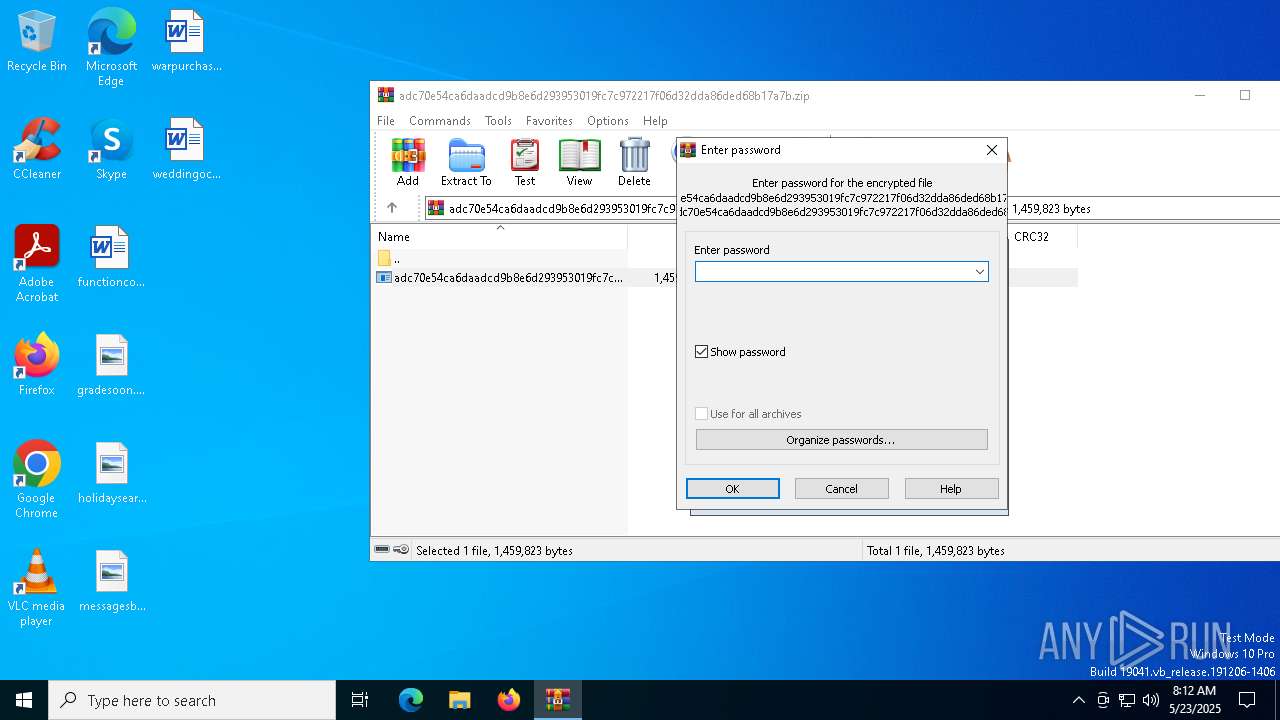
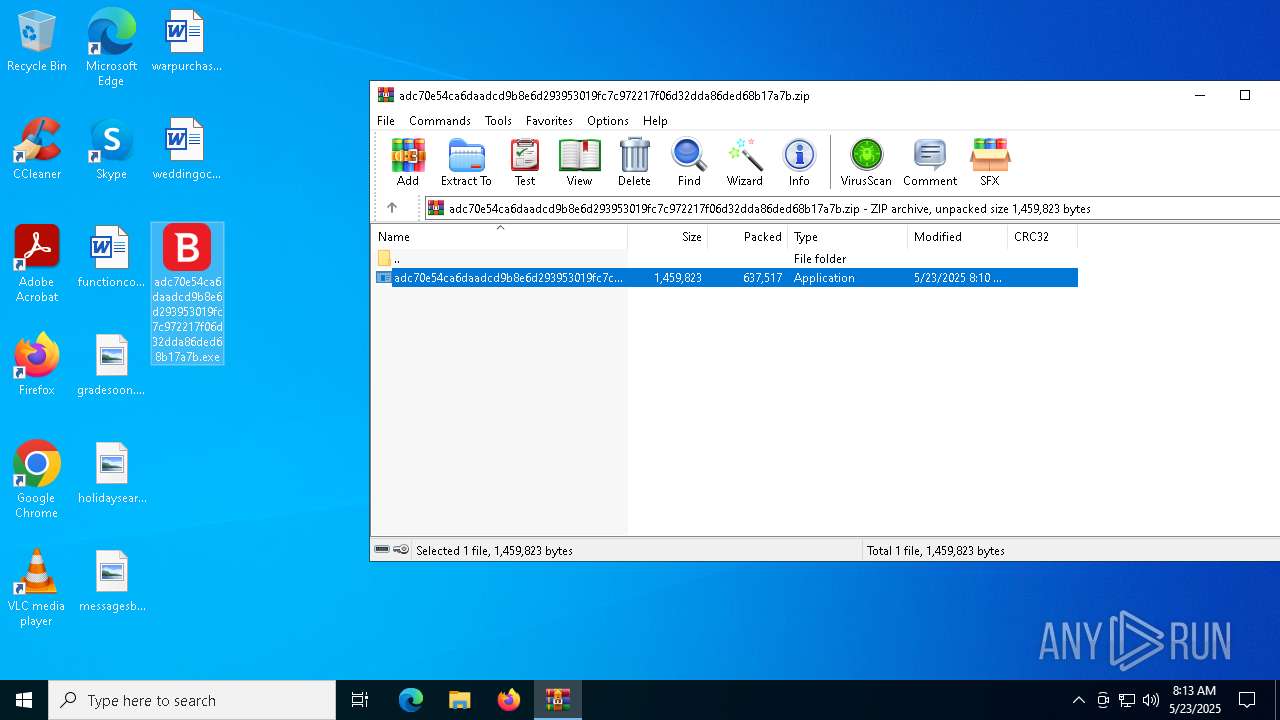
| File name: | adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.zip |
| Full analysis: | https://app.any.run/tasks/eb4b6e21-dfdc-416c-9aed-369a59b12994 |
| Verdict: | Malicious activity |
| Analysis date: | May 23, 2025, 08:10:41 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
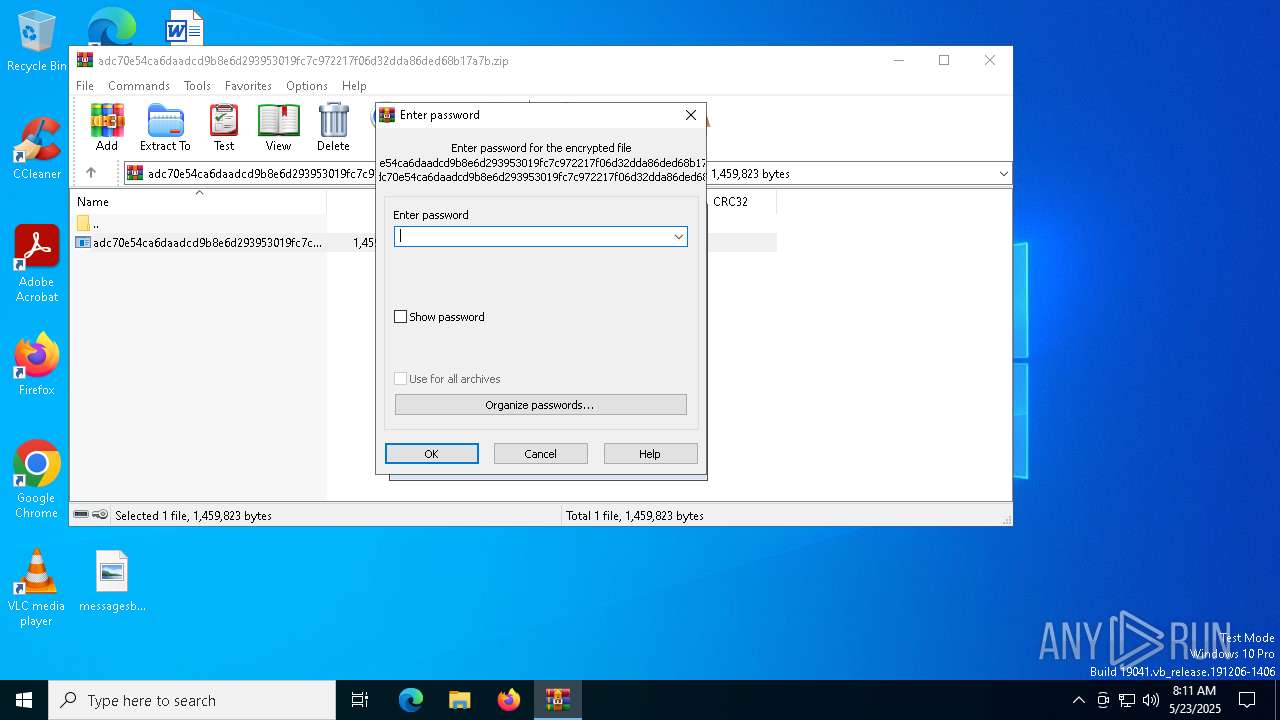
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 142104694661F311E56EB25F850D3480 |
| SHA1: | 3E82F29AB3355491F03376BA6C0D16CD114A61DF |
| SHA256: | 1ED2583FB933EEFE14100049987767E2B32D7FBDE74E25EECA20117163A985BD |
| SSDEEP: | 24576:dwkRrHhGgyAW+G6A++0Cl2R7ZC4vpms9g0RDRnCjXBnBML4bBVKJs3G:mkRrHhGgyAW+G6A++0Cl2R7ZC4vpms9F |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6940)
Executing a file with an untrusted certificate
- adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe (PID: 208)
- adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe (PID: 5892)
- adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe (PID: 3008)
Signed with known abused certificate
- WinRAR.exe (PID: 6940)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6940)
Found 4leaf Holding certificate that may have been compromised
- adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe (PID: 208)
- adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe (PID: 5892)
- adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe (PID: 3008)
Executes application which crashes
- adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe (PID: 208)
- adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe (PID: 5892)
- adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe (PID: 3008)
Connects to unusual port
- ctfmon.exe (PID: 3996)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6940)
Checks supported languages
- adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe (PID: 208)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6940)
Manual execution by a user
- adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe (PID: 3008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:23 08:10:02 |
| ZipCRC: | 0xa8d3cae9 |
| ZipCompressedSize: | 637517 |
| ZipUncompressedSize: | 1459823 |
| ZipFileName: | adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe |
Total processes
149
Monitored processes
14
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb6940.17913\adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb6940.17913\adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe | WinRAR.exe | ||||||||||||
User: admin Company: Bitdefender Integrity Level: MEDIUM Description: bduserhost Exit code: 3221225477 Version: 27.0.25.114 Modules
| |||||||||||||||
| 856 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2660 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 3008 -s 560 | C:\Windows\SysWOW64\WerFault.exe | — | adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3008 | "C:\Users\admin\Desktop\adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe" | C:\Users\admin\Desktop\adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe | explorer.exe | ||||||||||||
User: admin Company: Bitdefender Integrity Level: MEDIUM Description: bduserhost Exit code: 3221225477 Version: 27.0.25.114 Modules
| |||||||||||||||
| 3032 | "C:\Windows\SysWOW64\ctfmon.exe -p 1234" | C:\Windows\SysWOW64\ctfmon.exe | — | adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3996 | "C:\Windows\SysWOW64\ctfmon.exe -p 1234" | C:\Windows\SysWOW64\ctfmon.exe | adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4428 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5304 | "C:\Windows\SysWOW64\ctfmon.exe -p 1234" | C:\Windows\SysWOW64\ctfmon.exe | — | adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5624 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5892 -s 536 | C:\Windows\SysWOW64\WerFault.exe | — | adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 113
Read events
8 102
Write events
11
Delete events
0
Modification events
| (PID) Process: | (6940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.zip | |||
| (PID) Process: | (6940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
Executable files
3
Suspicious files
6
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6436 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_adc70e54ca6daadc_3aa4d231fe71c2f692d4f0fdec9b7adff4b69c_d467fce9_b071251b-14b0-421f-9726-ddd2d3a7d8d5\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5624 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_adc70e54ca6daadc_3aa4d231fe71c2f692d4f0fdec9b7adff4b69c_d467fce9_e4e3ffe2-ce31-4aea-b7ea-0ab64852d253\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2660 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_adc70e54ca6daadc_3aa4d231fe71c2f692d4f0fdec9b7adff4b69c_d467fce9_ffe90200-6201-45bb-b8ed-9bc0c651b968\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6436 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6BD7.tmp.WERInternalMetadata.xml | xml | |
MD5:F5F9DC184CA063C97CEFA294741640B5 | SHA256:A1D47B83410B5BE1FEE37DC3373E4E8E15E3AA7AF1FF410D07C835F51E4EFC43 | |||
| 6436 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6C07.tmp.xml | xml | |
MD5:856E4D0DD272799E4232A1DA154F825F | SHA256:35D5819C76BEC1FB72EEA034AB3D49DFB8954382F4355AB7BCDC08E67BEF7CD1 | |||
| 6436 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6B59.tmp.dmp | binary | |
MD5:A3D29274C9FB3AADD540D09DB7C272F9 | SHA256:2DC7CF7C03F057763D16199CBCC120C66353CC80A33480BC8EF3D3FCA43BF785 | |||
| 6436 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe.208.dmp | binary | |
MD5:1303FCF4DFC91E2F892BC232C128C543 | SHA256:EA8D345890B63007929469E85FEAAF1425E15653563EFAFD2E6A34830DDB01A5 | |||
| 6940 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6940.28637\adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe | executable | |
MD5:F01747EBD0C60747E8BFA92EAB4AD488 | SHA256:ADC70E54CA6DAADCD9B8E6D293953019FC7C972217F06D32DDA86DED68B17A7B | |||
| 2660 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\adc70e54ca6daadcd9b8e6d293953019fc7c972217f06d32dda86ded68b17a7b.exe.3008.dmp | binary | |
MD5:0962EA19BDC26BE57EA7E91EAB2DBBA4 | SHA256:CF012319B49100AE478A42F1B6384F9F13AD325A8B37CC1687CCC1E3F02D3F37 | |||
| 2660 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER1179.tmp.WERInternalMetadata.xml | xml | |
MD5:5E63DBDACB2B73947021AA5FCBD6F42E | SHA256:E8E8593DEA7833901AC0700C44AB2C2886D4E5C741DE92F32033BFC953F4A2F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
47
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5796 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6644 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6644 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3284 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3284 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5796 | svchost.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5796 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |