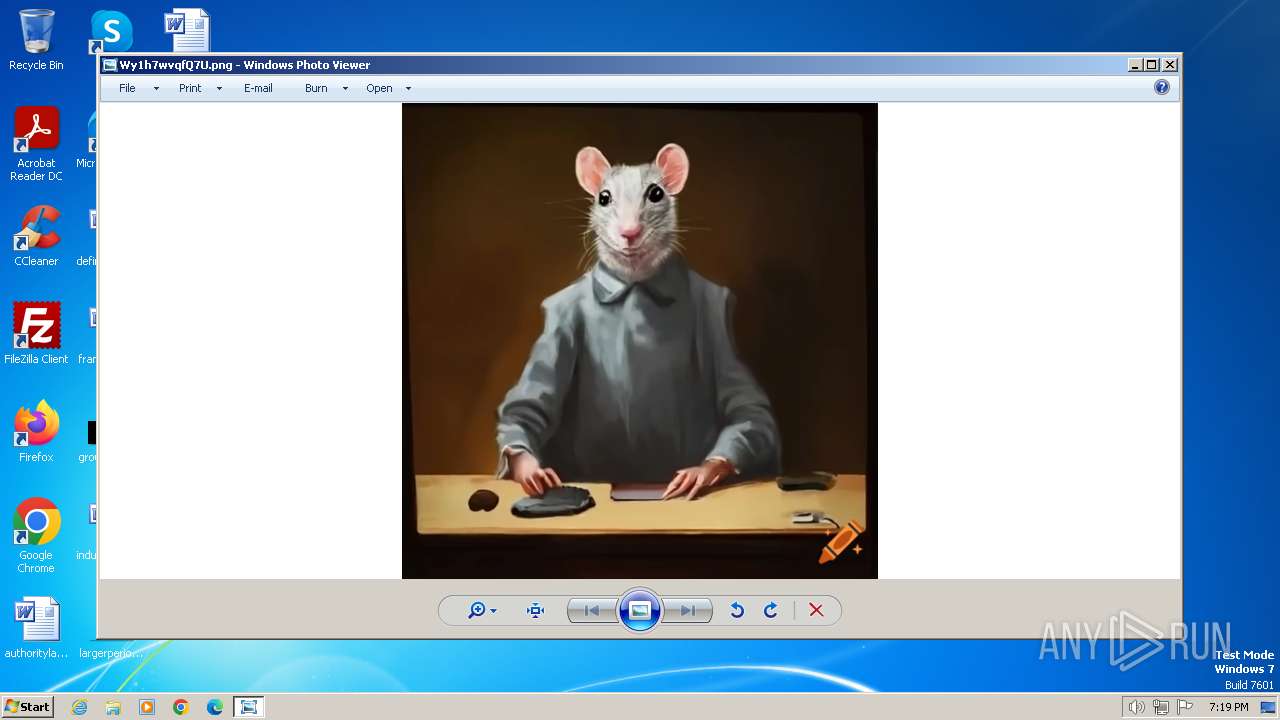
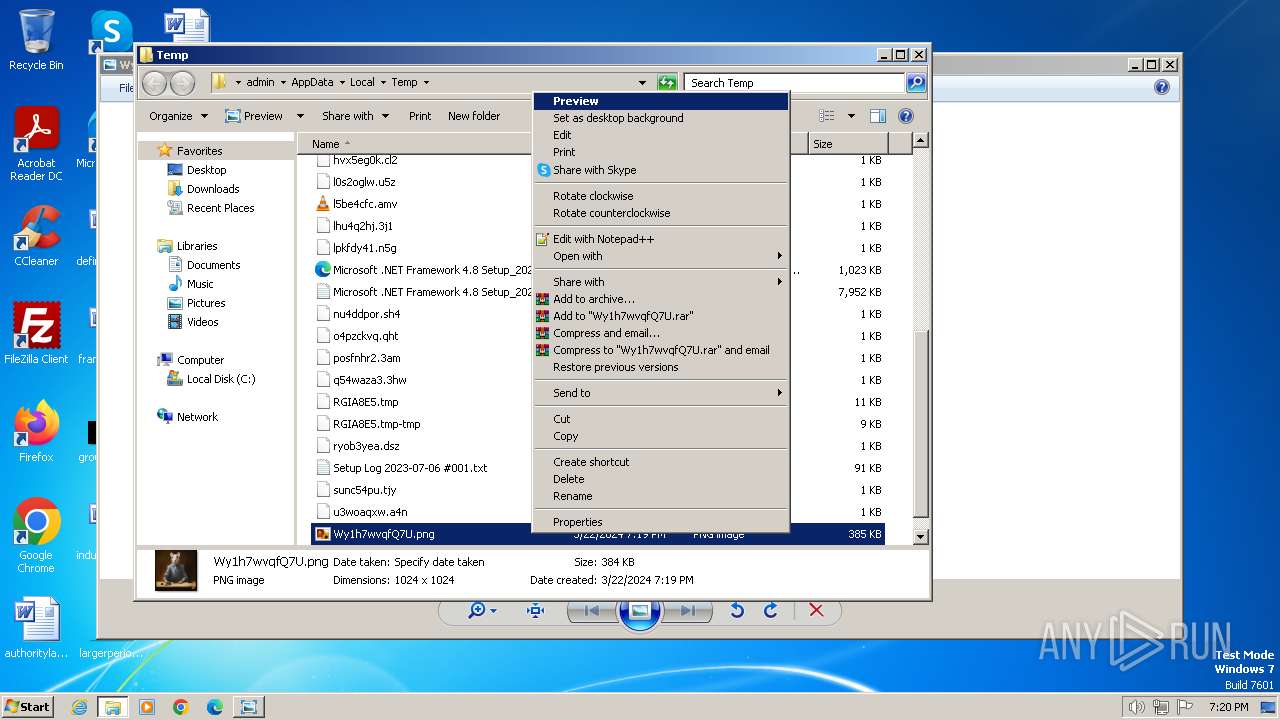
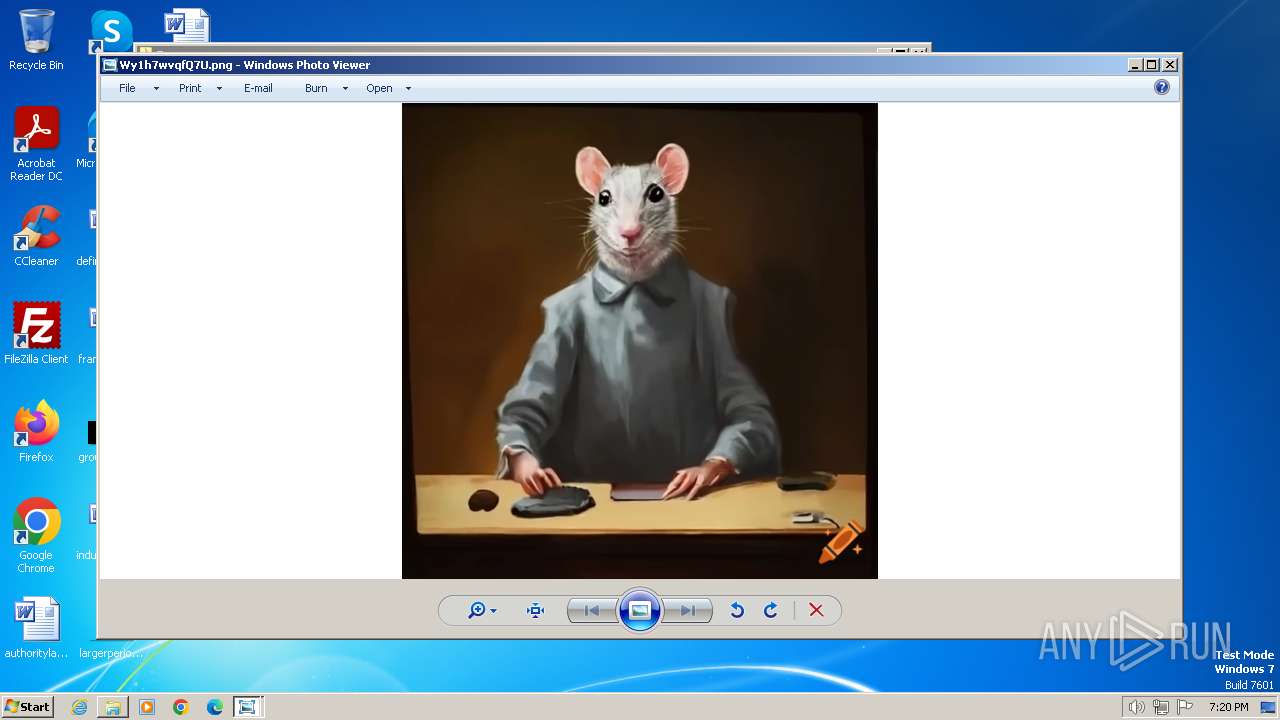
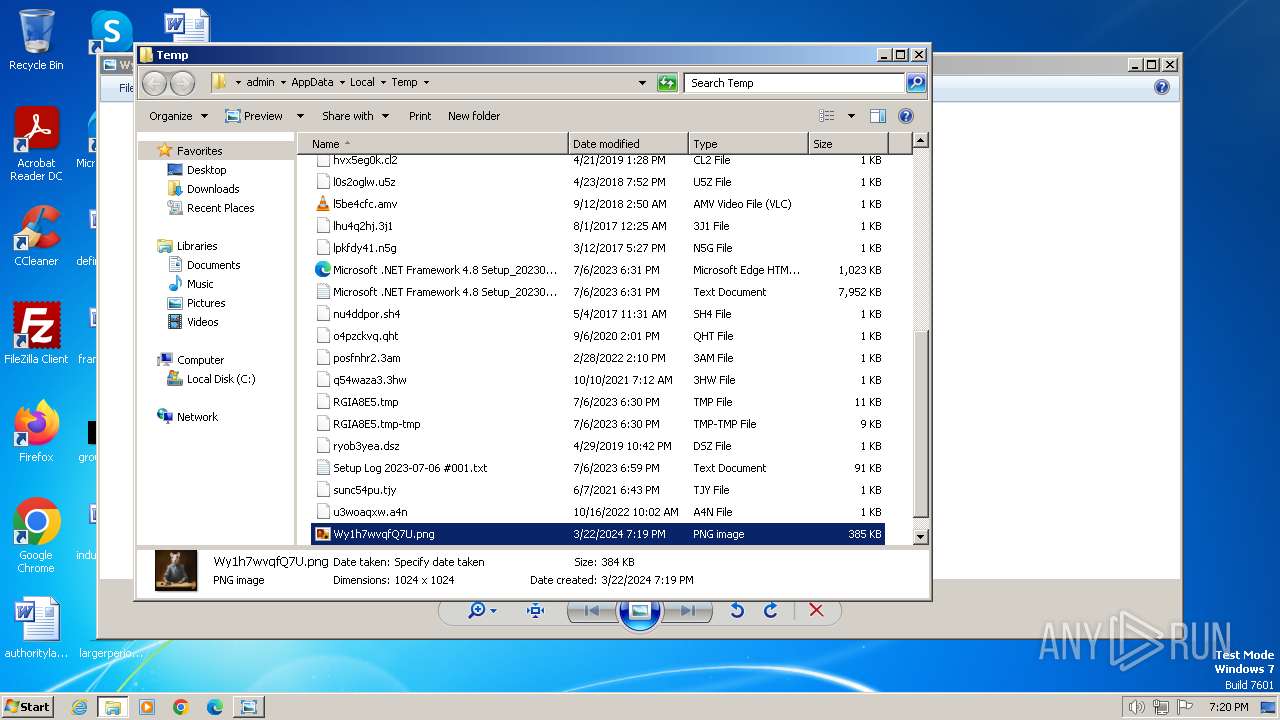
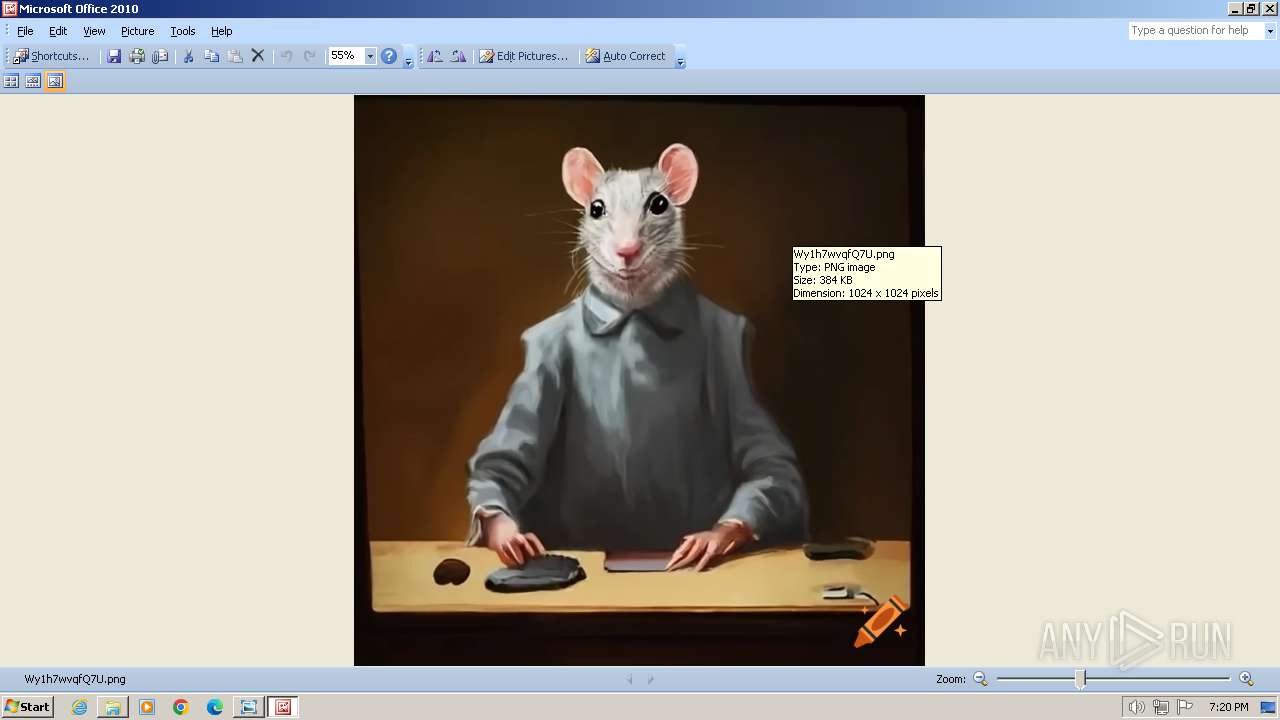
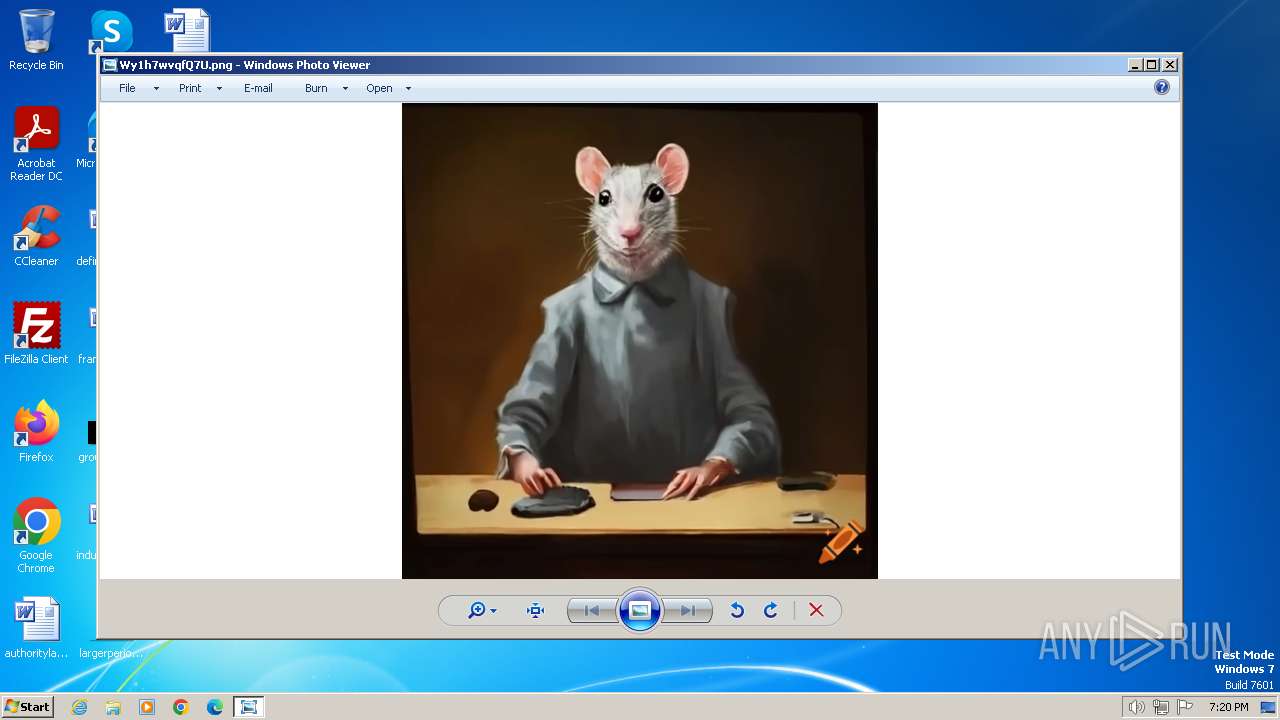
| File name: | Wy1h7wvqfQ7U.png |
| Full analysis: | https://app.any.run/tasks/9e98c453-0f7b-4d65-aff3-8ce257618a77 |
| Verdict: | Malicious activity |
| Analysis date: | March 22, 2024, 19:19:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | image/png |
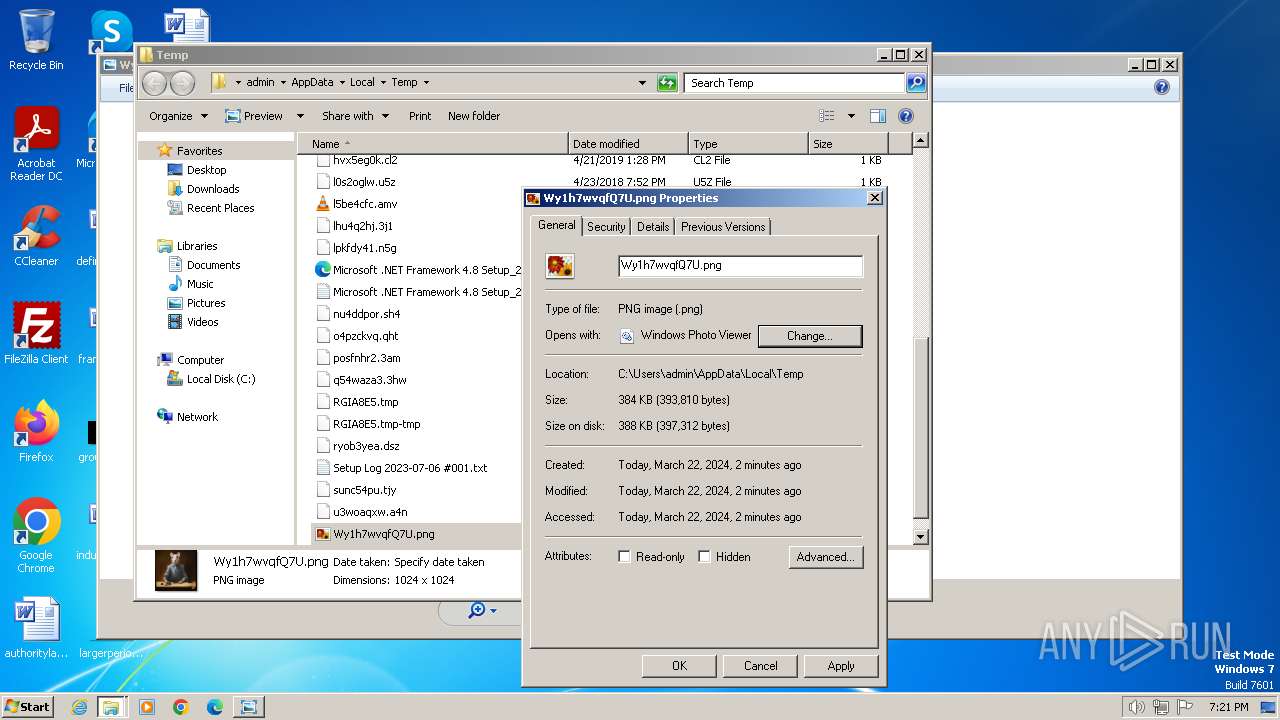
| File info: | PNG image data, 1024 x 1024, 8-bit/color RGB, non-interlaced |
| MD5: | 680291832013D2807AE81EAC160DC703 |
| SHA1: | 3D8AD872347DA2E23DC00E998882BD09253FA12C |
| SHA256: | 1E74D779A815B16EBBC9ED4C23CDE8B02AF715CF1ED8E562A00119CFFFFF0C15 |
| SSDEEP: | 12288:oEspfS8AV0IenMWlPHGoo+ReY61poS37fFCaAOlLrQmWhgscYqa:onK8AWIeMWJmo3Re71poYDFCaAyLrQmE |
MALICIOUS
The DLL Hijacking
- OIS.EXE (PID: 3308)
SUSPICIOUS
Non-standard symbols in registry
- OIS.EXE (PID: 3308)
Creates file in the systems drive root
- ntvdm.exe (PID: 2096)
INFO
Manual execution by a user
- notepad++.exe (PID: 2792)
- OIS.EXE (PID: 3308)
- ntvdm.exe (PID: 2096)
Reads the computer name
- OIS.EXE (PID: 3308)
Reads Microsoft Office registry keys
- OIS.EXE (PID: 3308)
Checks supported languages
- OIS.EXE (PID: 3308)
Creates files or folders in the user directory
- OIS.EXE (PID: 3308)
Reads the machine GUID from the registry
- OIS.EXE (PID: 3308)
Reads Environment values
- OIS.EXE (PID: 3308)
Process checks computer location settings
- OIS.EXE (PID: 3308)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .png | | | Portable Network Graphics (100) |
|---|
EXIF
PNG
| ImageWidth: | 1024 |
|---|---|
| ImageHeight: | 1024 |
| BitDepth: | 8 |
| ColorType: | RGB |
| Compression: | Deflate/Inflate |
| Filter: | Adaptive |
| Interlace: | Noninterlaced |
| WhitePointX: | 0.3127 |
| WhitePointY: | 0.329 |
| RedX: | 0.64 |
| RedY: | 0.33 |
| GreenX: | 0.3 |
| GreenY: | 0.6 |
| BlueX: | 0.15 |
| BlueY: | 0.06 |
| BackgroundColor: | 255 255 255 |
| Datecreate: | 2024-03-22T09:27:00+00:00 |
| Datemodify: | 2024-03-22T09:27:00+00:00 |
| Datetimestamp: | 2024-03-22T09:27:00+00:00 |
Composite
| ImageSize: | 1024x1024 |
|---|---|
| Megapixels: | 1 |
Total processes
44
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
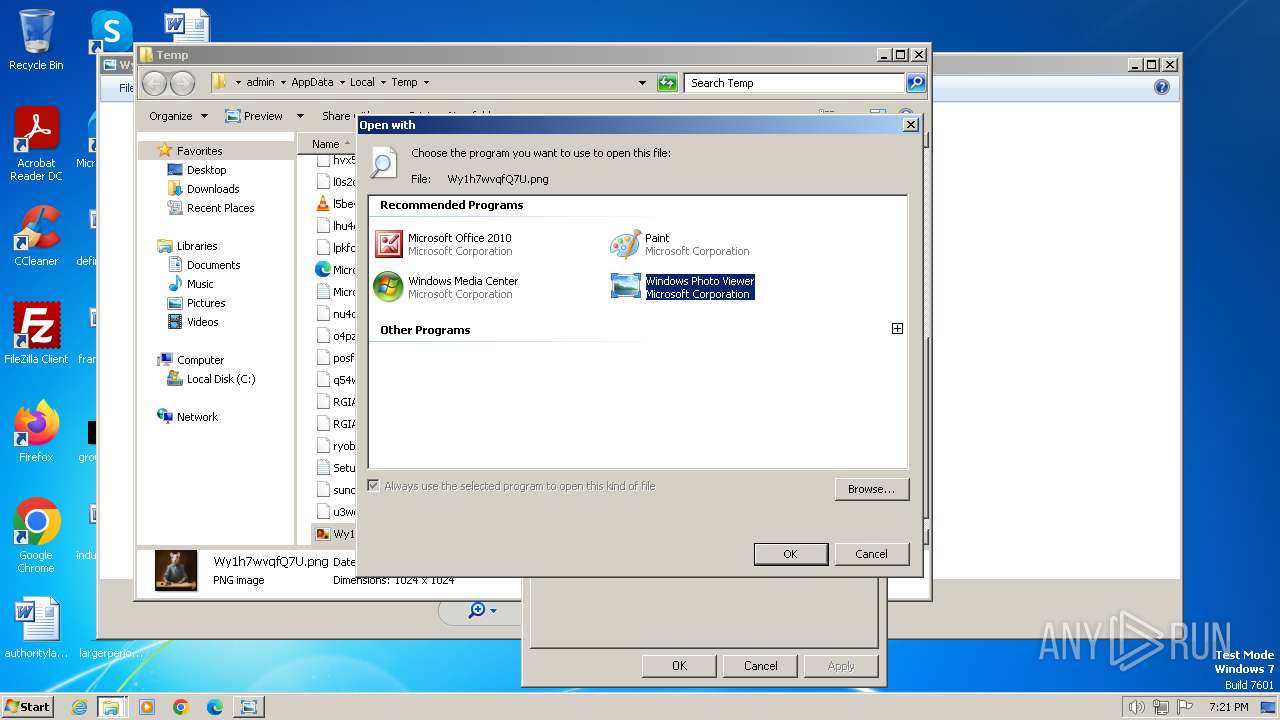
| 1836 | "C:\Windows\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\AppData\Local\Temp\Wy1h7wvqfQ7U.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2096 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\System32\ntvdm.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2364 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2792 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\AppData\Local\Temp\Wy1h7wvqfQ7U.png" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
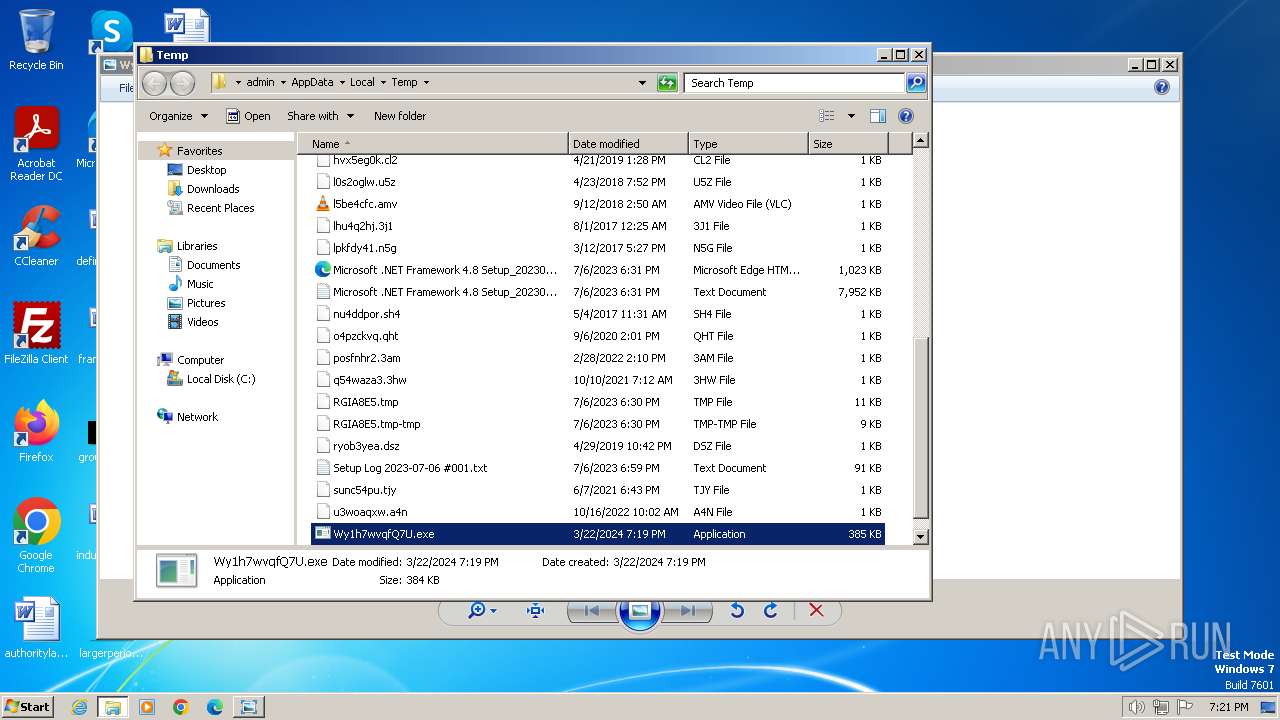
| 3308 | "C:\PROGRA~1\MICROS~1\Office14\OIS.EXE" /shellOpen "C:\Users\admin\AppData\Local\Temp\Wy1h7wvqfQ7U.png" | C:\Program Files\Microsoft Office\Office14\OIS.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office 2010 Exit code: 0 Version: 14.0.6015.1000 Modules
| |||||||||||||||
Total events
9 528
Read events
9 463
Write events
61
Delete events
4
Modification events
| (PID) Process: | (1836) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: rundll32.exe | |||
| (PID) Process: | (1836) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.png\OpenWithProgids |
| Operation: | write | Name: | pngfile |
Value: | |||
| (PID) Process: | (1836) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (1836) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (1836) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (1836) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (2792) notepad++.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2364) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: DllHost.exe | |||
| (PID) Process: | (2364) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.png\OpenWithProgids |
| Operation: | write | Name: | pngfile |
Value: | |||
| (PID) Process: | (2364) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Photo Viewer\Viewer |
| Operation: | write | Name: | MainWndPos |
Value: 6000000034000000A00400008002000000000000 | |||
Executable files
0
Suspicious files
0
Text files
5
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3308 | OIS.EXE | C:\Users\admin\AppData\Local\Temp\CVR49B1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2792 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:3EACC8FF7784160C55BA69630FFE32BB | SHA256:23CF33DD1669B4E32EBBA5E8A976FC8EB79F908AF6335C4DDEA14E501B18356E | |||
| 3308 | OIS.EXE | C:\Users\admin\AppData\Roaming\Microsoft\OIS\Toolbars.dat | binary | |
MD5:5208F2A5927850141DCE452DD8C0DDD1 | SHA256:784FFD6F8683F00CBEB11FEA5A17F2E34B367F739B55ADF6770BEB14B19C890C | |||
| 2792 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:EA9FE896B4305C2A9629FEB279084544 | SHA256:EF99FB4EFE424FABB1F3CD0076CC532EF5767D6CD1D09611C4F69F1BE03702B6 | |||
| 2096 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs580.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 2096 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs570.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 3308 | OIS.EXE | C:\Users\admin\AppData\Local\Microsoft\OIS\OIScatalog.cag | text | |
MD5:45853C6351B8FC9AFA51B30051D6C127 | SHA256:80F0A83A0E3BBB345694B0C0811221869099E8C15C1CE1D54CA1C437210DCDAB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|