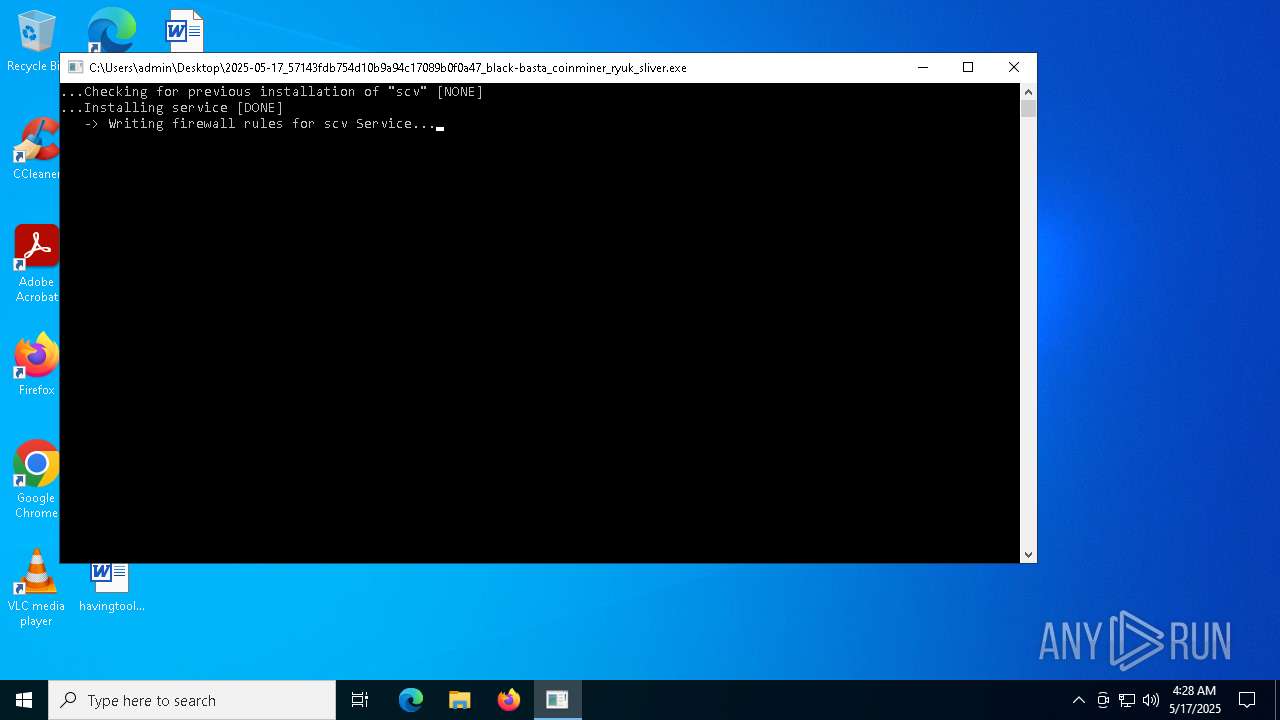
| File name: | 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver |
| Full analysis: | https://app.any.run/tasks/d21c976e-7574-425f-b724-3c6a9347b7fd |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 04:28:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | 57143FDB754D10B9A94C17089B0F0A47 |
| SHA1: | D58405A88203DFB4E7FD8AF4622551B705B5C9AF |
| SHA256: | 1E70F3C8E828403D6D924073E10838C7A289F0842444030C62DB8813BE44806B |
| SSDEEP: | 49152:CFW8kiN6MhRRcR+x1ztwpjl5+wXmub27NlALcQiLw8nRSe8QBtehAURhSOaXczi+:TSRntkm/7NlY8Rtpt0vSPXBjXq |
MALICIOUS
Executing a file with an untrusted certificate
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 4488)
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 3268)
- scvhos.exe (PID: 2136)
SUSPICIOUS
Uses WMIC.EXE to obtain operating system information
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 4488)
Reads security settings of Internet Explorer
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 4488)
Reads the date of Windows installation
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 4488)
Application launched itself
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 4488)
Executable content was dropped or overwritten
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 3268)
Creates a software uninstall entry
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 3268)
Creates or modifies Windows services
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 3268)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 5392)
- cmd.exe (PID: 1228)
- cmd.exe (PID: 6512)
- cmd.exe (PID: 2552)
Starts CMD.EXE for commands execution
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 3268)
Executes as Windows Service
- scvhos.exe (PID: 2136)
Starts POWERSHELL.EXE for commands execution
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 3268)
INFO
The sample compiled with english language support
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 4488)
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 3268)
Checks supported languages
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 4488)
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 3268)
- scvhos.exe (PID: 2136)
Reads the computer name
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 4488)
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 3268)
- scvhos.exe (PID: 2136)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1660)
- powershell.exe (PID: 2108)
Process checks computer location settings
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 4488)
Reads product name
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 3268)
- scvhos.exe (PID: 2136)
Reads Environment values
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 3268)
- scvhos.exe (PID: 2136)
Creates files in the program directory
- 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe (PID: 3268)
- scvhos.exe (PID: 2136)
Reads the software policy settings
- powershell.exe (PID: 2108)
- slui.exe (PID: 4400)
Create files in a temporary directory
- powershell.exe (PID: 2108)
Checks proxy server information
- slui.exe (PID: 4400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2021:03:26 00:18:40+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14 |
| CodeSize: | 2033152 |
| InitializedDataSize: | 955904 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1c420c |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.2.1.3 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Windows Services |
| FileVersion: | 0.2.1.3 |
| InternalName: | Win32 |
| LegalCopyright: | Apache 2.0 License |
| OriginalFileName: | Win32.exe |
| ProductName: | Windows Services |
| ProductVersion: | 0, 0, 0, 0 |
| Comments: | Modified by an unpaid evaluation copy of Resource Tuner 2. http://www.heaventools.com |
Total processes
150
Monitored processes
22
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | /C "netsh advfirewall firewall add rule name="scv Management Traffic (TCP-2) {9b6cb212-2131-4788-57ae-9c26d77ee7e2}" action=allow description="Mesh Central Agent Management Traffic" dir=in program="C:\Program Files\Windowtemp\scv\scvhos.exe" protocol=TCP profile="public,private,domain" interfacetype=any edge=yes localport=16991" | C:\Windows\System32\cmd.exe | — | 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1276 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | netsh advfirewall firewall add rule name="scv Peer-to-Peer Traffic (UDP-1) {eeac12e9-ebe5-4287-7996-084c87040809}" action=allow description="Mesh Central Agent Peer-to-Peer Traffic" dir=in program="C:\Program Files\Windowtemp\scv\scvhos.exe" protocol=UDP profile="public,private,domain" interfacetype=any edge=yes localport=16990 | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | wmic os get oslanguage /FORMAT:LIST | C:\Windows\System32\wbem\WMIC.exe | — | 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2108 | /C "Get-Module -ListAvailable -Name netsecurity" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1067 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Windowtemp\scv\scvhos.exe" --meshServiceName="scv" --installedByUser="S-1-5-21-1693682860-607145093-2874071422-1001" | C:\Program Files\Windowtemp\scv\scvhos.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: Windows Services Version: 0.2.1.3 Modules
| |||||||||||||||
| 2552 | /C "netsh advfirewall firewall add rule name="scv Peer-to-Peer Traffic (UDP-2) {24917704-759d-4586-ed95-1e2ec3f90d5f}" action=allow description="Mesh Central Agent Peer-to-Peer Traffic" dir=in program="C:\Program Files\Windowtemp\scv\scvhos.exe" protocol=UDP profile="public,private,domain" interfacetype=any edge=yes localport=16991" | C:\Windows\System32\cmd.exe | — | 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2800 | netsh advfirewall firewall add rule name="scv Management Traffic (TCP-2) {9b6cb212-2131-4788-57ae-9c26d77ee7e2}" action=allow description="Mesh Central Agent Management Traffic" dir=in program="C:\Program Files\Windowtemp\scv\scvhos.exe" protocol=TCP profile="public,private,domain" interfacetype=any edge=yes localport=16991 | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 203
Read events
11 186
Write events
17
Delete events
0
Modification events
| (PID) Process: | (3268) 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\scv |
| Operation: | write | Name: | ImagePath |
Value: "C:\Program Files\Windowtemp\scv\scvhos.exe" --meshServiceName="scv" --installedByUser="S-1-5-21-1693682860-607145093-2874071422-1001" | |||
| (PID) Process: | (3268) 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\scv |
| Operation: | write | Name: | _InstalledBy |
Value: S-1-5-21-1693682860-607145093-2874071422-1001 | |||
| (PID) Process: | (3268) 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\scv |
| Operation: | write | Name: | DisplayName |
Value: Adobe | |||
| (PID) Process: | (3268) 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\scv |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Windowtemp\scv\scvhos.exe | |||
| (PID) Process: | (3268) 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\scv |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Windowtemp\scv\ | |||
| (PID) Process: | (3268) 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\scv |
| Operation: | write | Name: | EstimatedSize |
Value: 2949 | |||
| (PID) Process: | (3268) 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\scv |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (3268) 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\scv |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
| (PID) Process: | (3268) 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\scv |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files\Windowtemp\scv\scvhos.exe -funinstall --meshServiceName="scv" | |||
| (PID) Process: | (2136) scvhos.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Open Source\MeshAgent2 |
| Operation: | write | Name: | KeyStore |
Value: Microsoft Software Key Storage Provider | |||
Executable files
1
Suspicious files
4
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2108 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_c2fqhugf.mpv.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3268 | 2025-05-17_57143fdb754d10b9a94c17089b0f0a47_black-basta_coinminer_ryuk_sliver.exe | C:\Program Files\Windowtemp\scv\scvhos.exe | executable | |
MD5:57143FDB754D10B9A94C17089B0F0A47 | SHA256:1E70F3C8E828403D6D924073E10838C7A289F0842444030C62DB8813BE44806B | |||
| 2136 | scvhos.exe | C:\Program Files\Windowtemp\scv\scvhos.log | text | |
MD5:E9A2A90C737236AC789C1AE4CB18BB04 | SHA256:0169AD380DD656245BEC066FAA52D30214A1E4245625C74343FA4F85728A5888 | |||
| 2136 | scvhos.exe | C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\SystemCertificates\My\Keys\864790D3EBA5DD9D1B64E8697819B8D5A1D4C59E | binary | |
MD5:808B0F4C70AF7698105DE062E417A5BE | SHA256:5B0C75038C78AE48E278BC660880F88A726777C312EB839B21D4C4744B66D7A5 | |||
| 2136 | scvhos.exe | C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\SystemCertificates\My\Certificates\2D0136577B6778A5641867E2EE2F448859359DFF | binary | |
MD5:D8EFB665FEEB92DD8C135D0988358292 | SHA256:3F8BB9E66746FFA51E1FC629E773BC56A21E132986B3483B9489CFC2D993A062 | |||
| 2108 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jgclmy4m.5cv.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2108 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_et5ck4ik.reo.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2108 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ywo0t4nd.thc.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2136 | scvhos.exe | C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\SystemCertificates\My\Certificates\F482690308BA13EC16D30854DB64F43248AE89AC | binary | |
MD5:1C484AE7E4CF7A72306EE4D08EA9C0BE | SHA256:83DF215C1125049C6F011A8C1B28E35221C4FA3BDDF2D0304593D4CD57E11289 | |||
| 2136 | scvhos.exe | C:\Program Files\Windowtemp\scv\scvhos.msh | text | |
MD5:C6C6612E9B36A463442D654EED826FEE | SHA256:F9752297061EA93FD633C191E7D394A57648F99DA5AE79D40268555395773C12 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
51
DNS requests
21
Threats
12
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2136 | scvhos.exe | 192.46.210.125:443 | — | Linode, LLC | IN | unknown |
5964 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5964 | SIHClient.exe | 13.95.31.18:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |