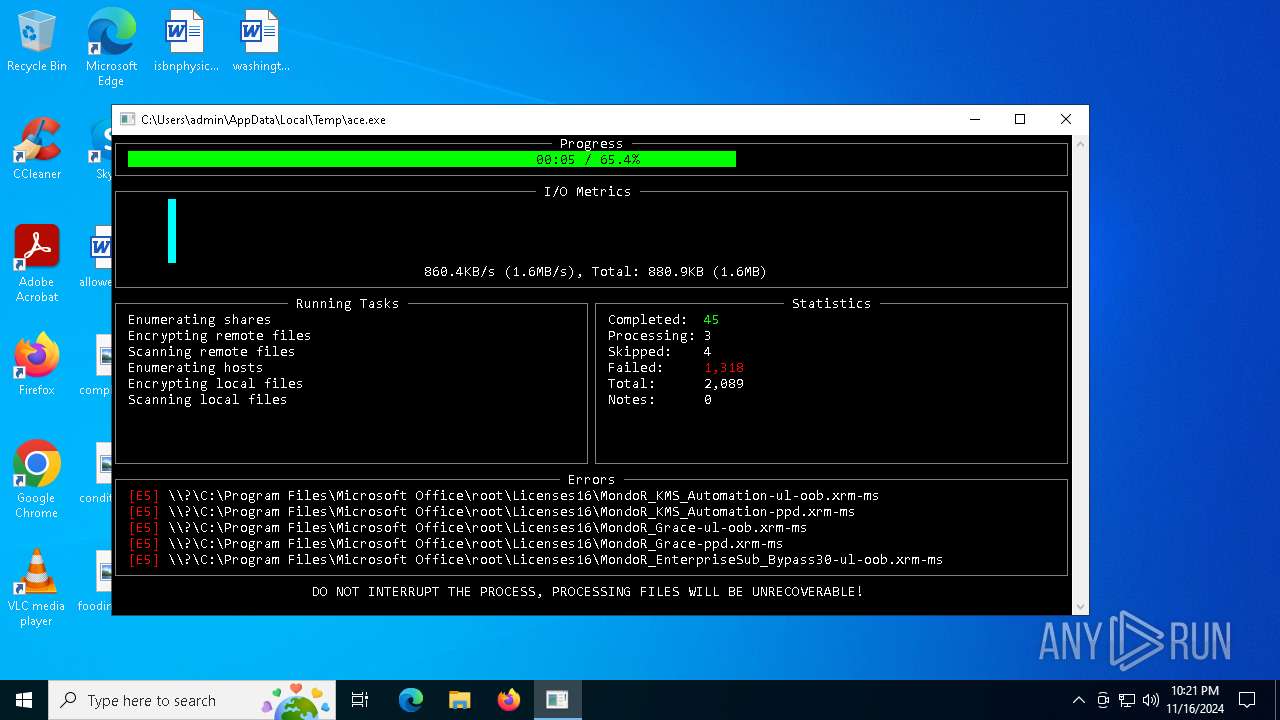
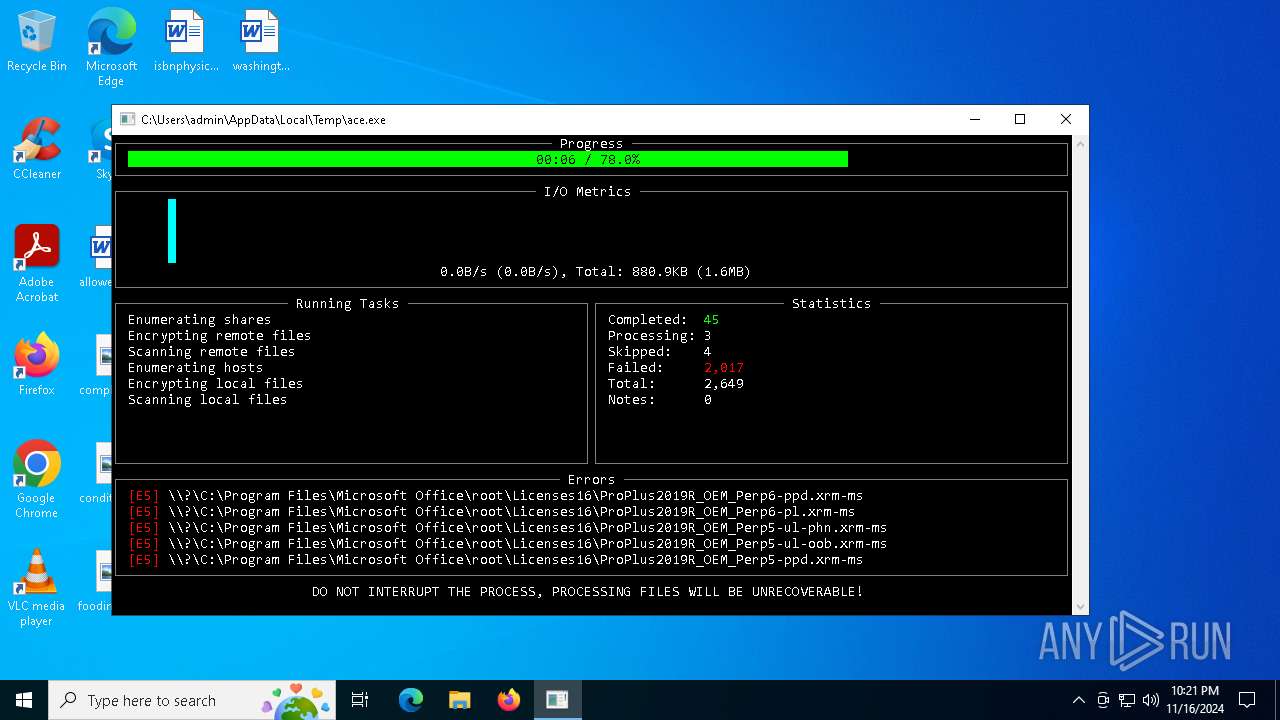
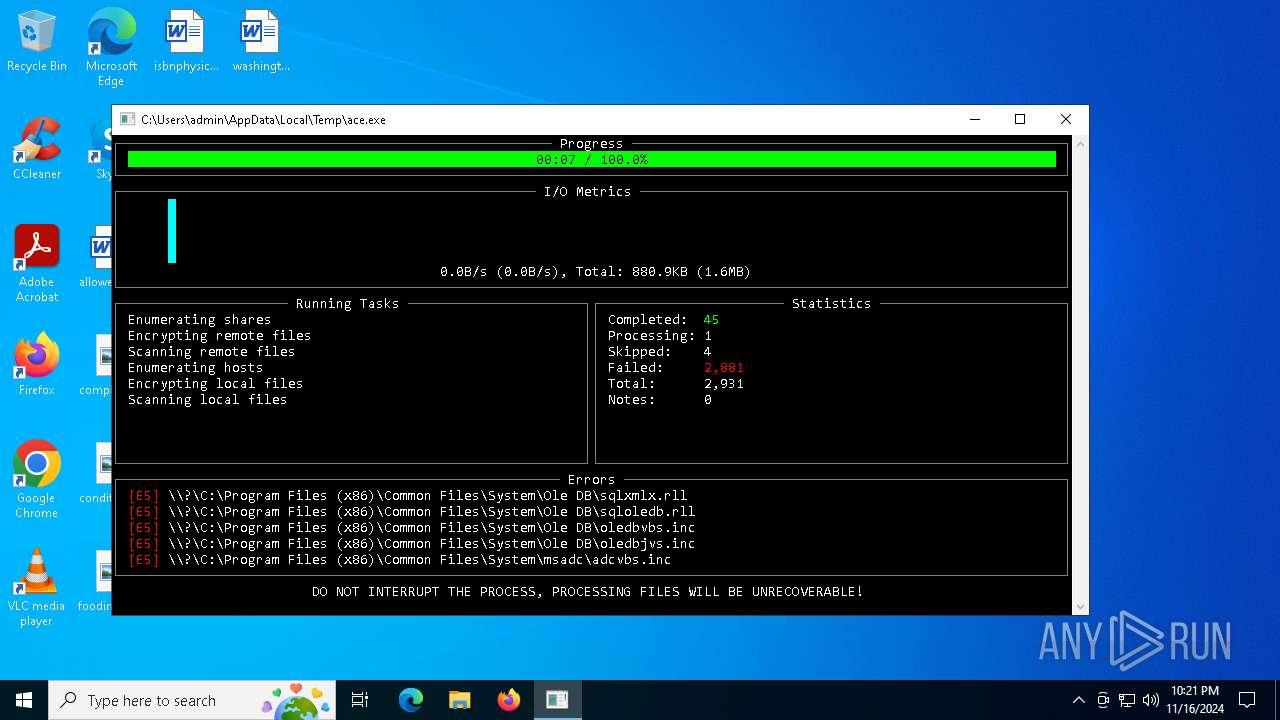
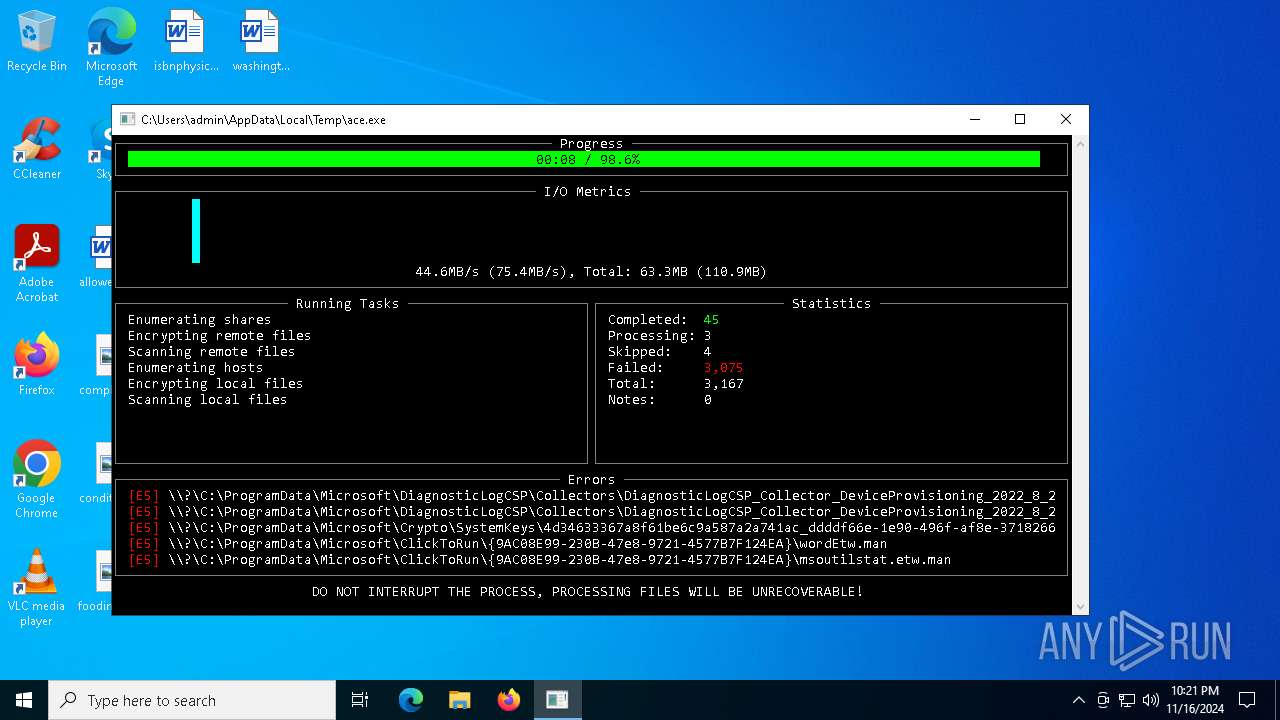
| File name: | ace.exe |
| Full analysis: | https://app.any.run/tasks/efcf68ca-23fd-44fc-aa78-9d57f4da6b53 |
| Verdict: | Malicious activity |
| Analysis date: | November 16, 2024, 22:21:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 9 sections |
| MD5: | C70AF1FBC30ACEE3A7A1E9A46E462909 |
| SHA1: | 962BB9A1FDA8D81607376BEDA61E4106BFEFD7FD |
| SHA256: | 1E60345F4285DB314F741F0A1796835C451F5746BB7F15851B86FDECB71A188D |
| SSDEEP: | 12288:UCactKZcSpItWdL90+dbhE3q/4maEdKPvBtF7uq9Ms5BUlqDDhjG5:UCMQf9Ms5/G |
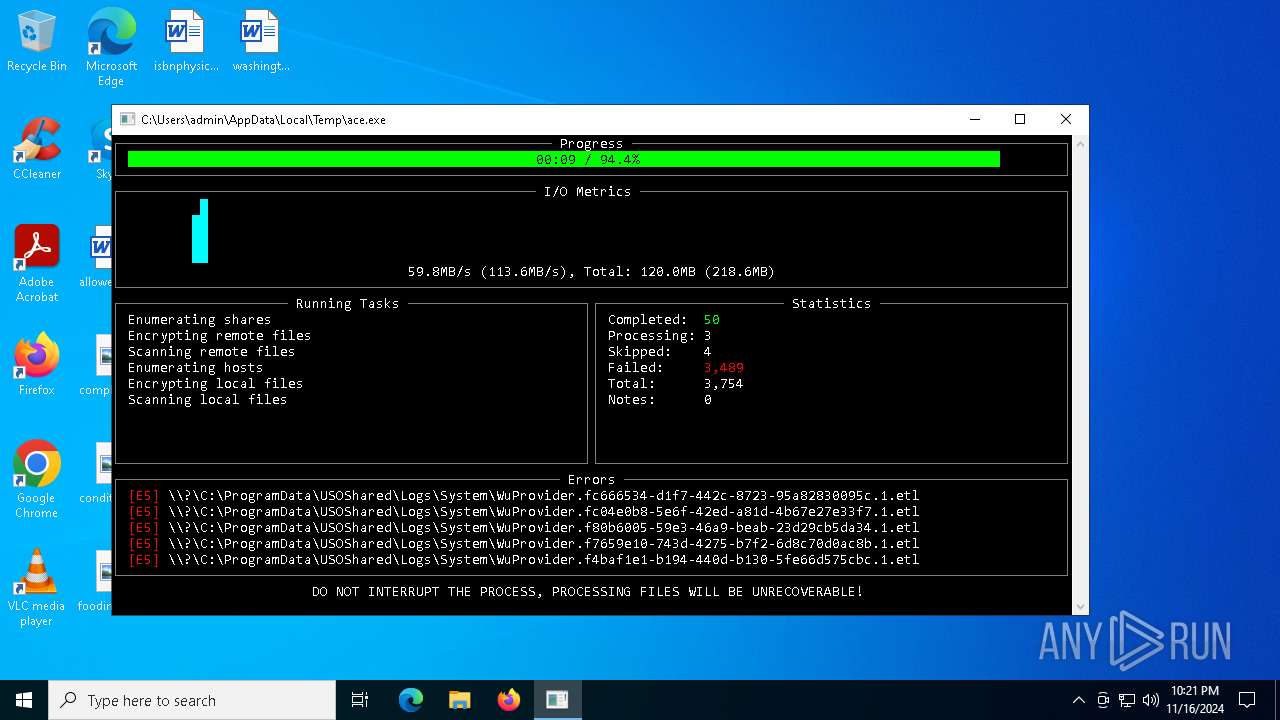
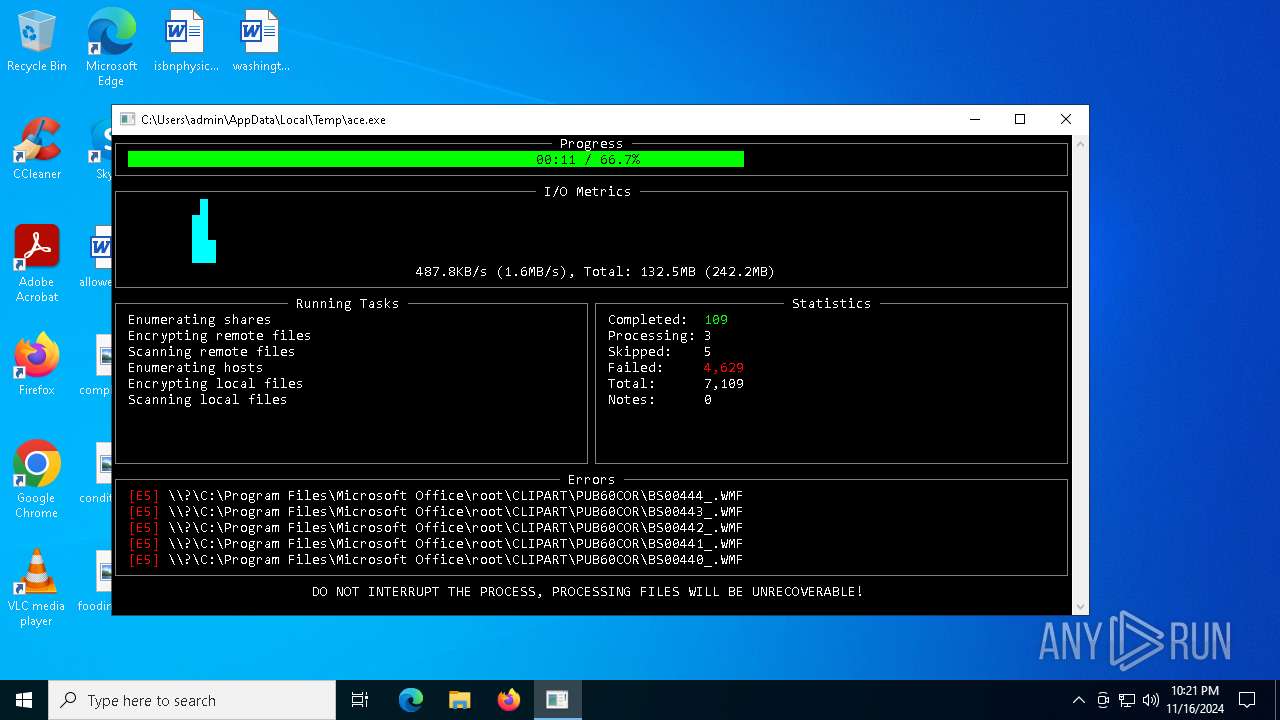
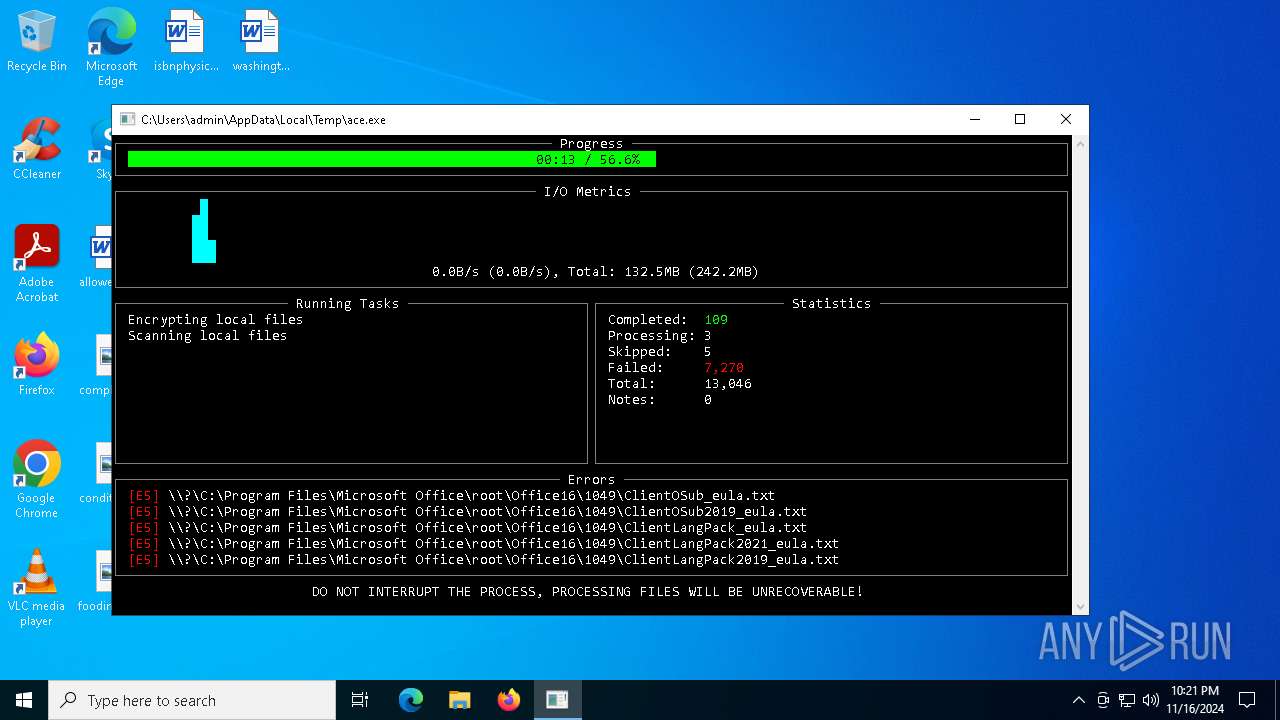
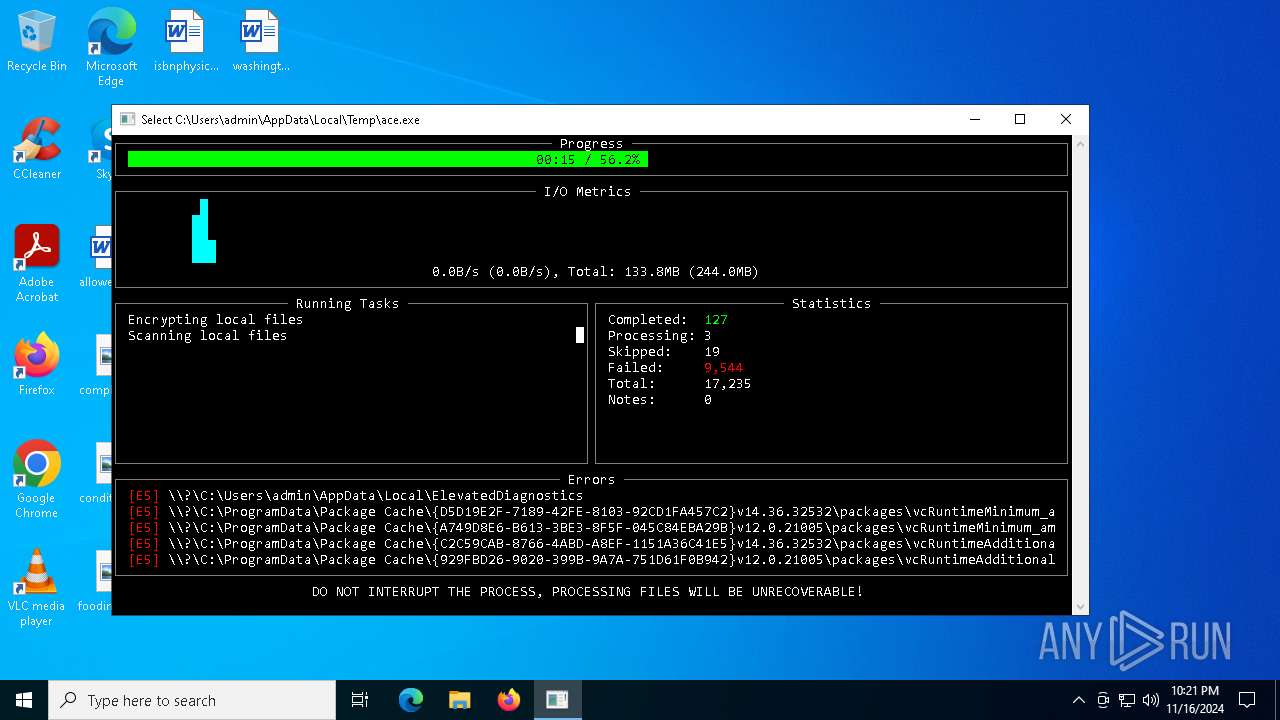
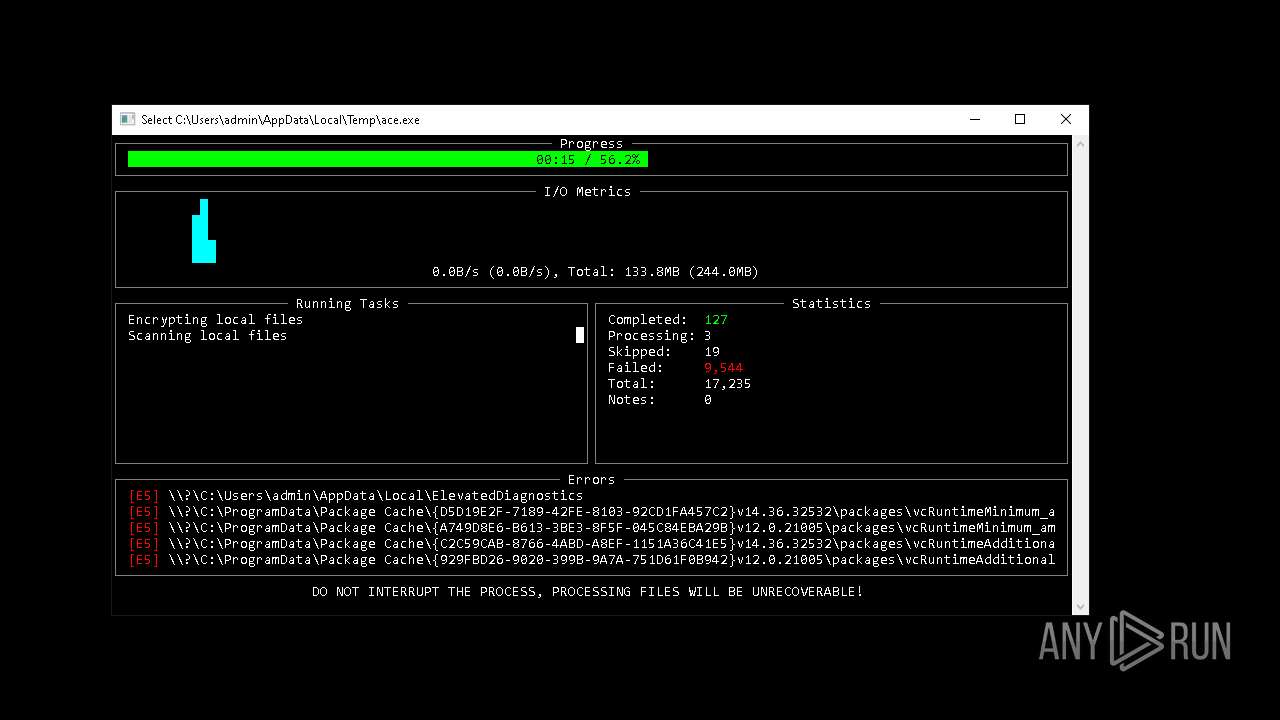
MALICIOUS
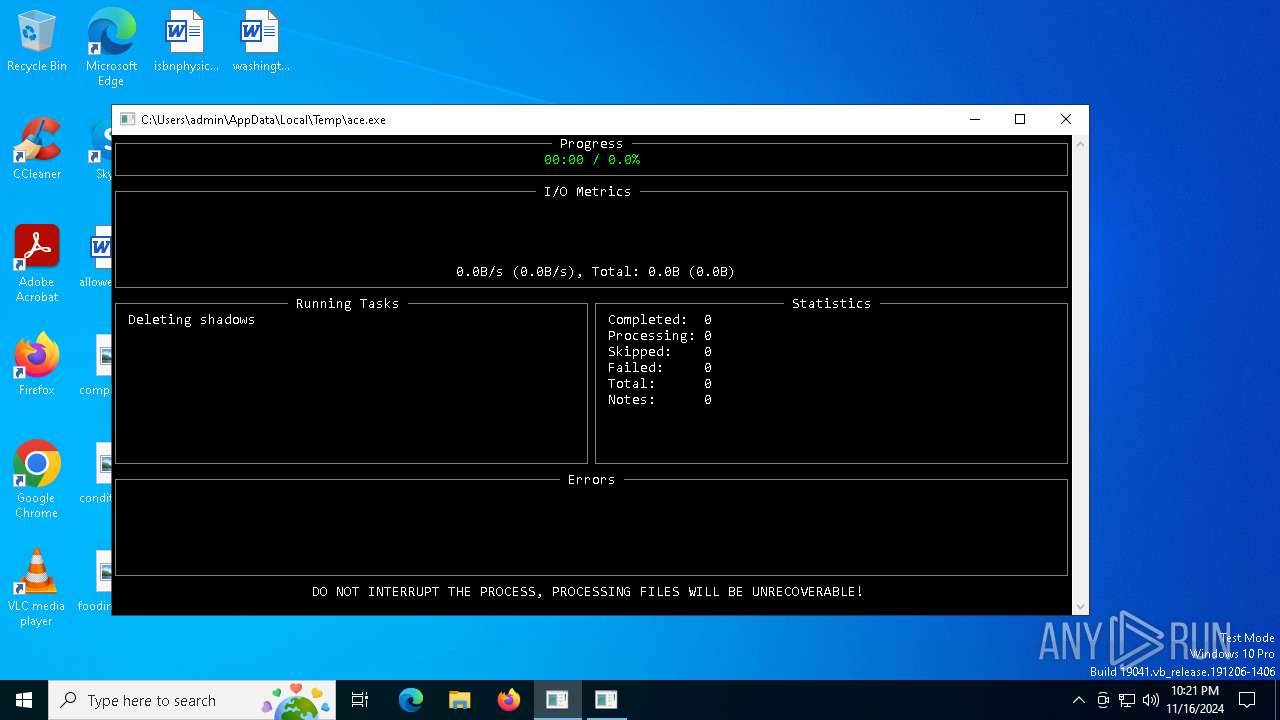
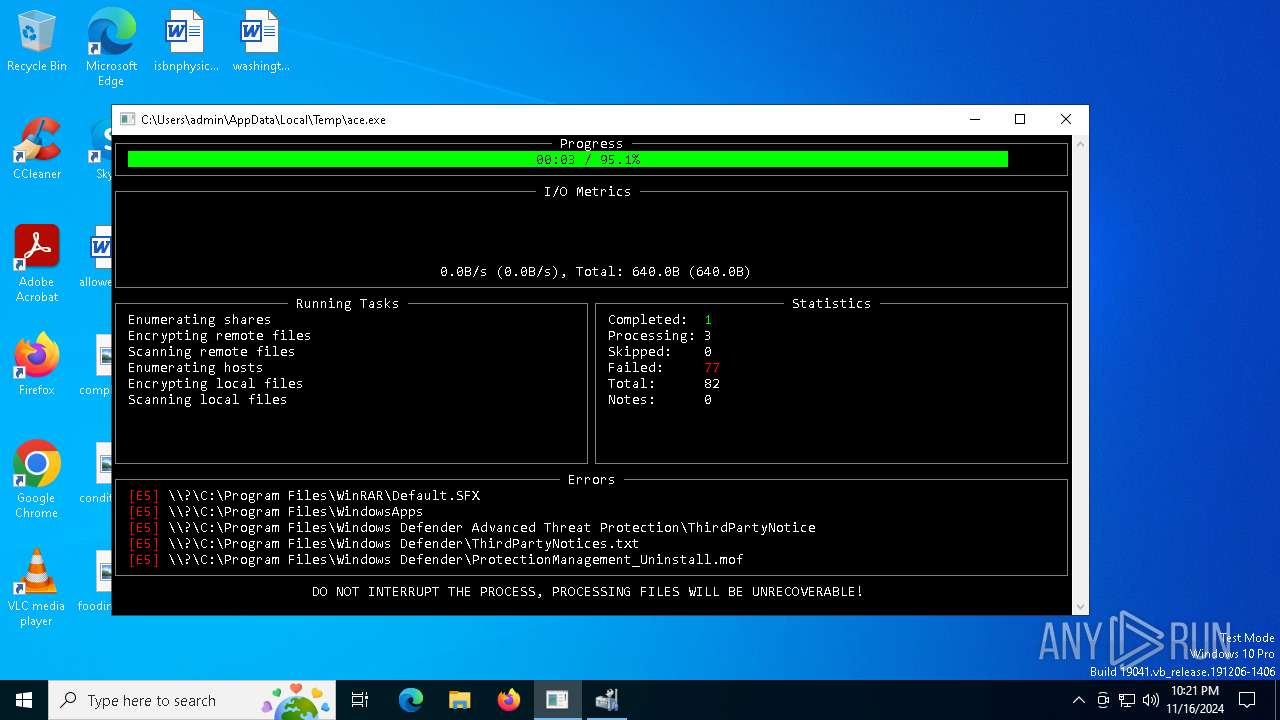
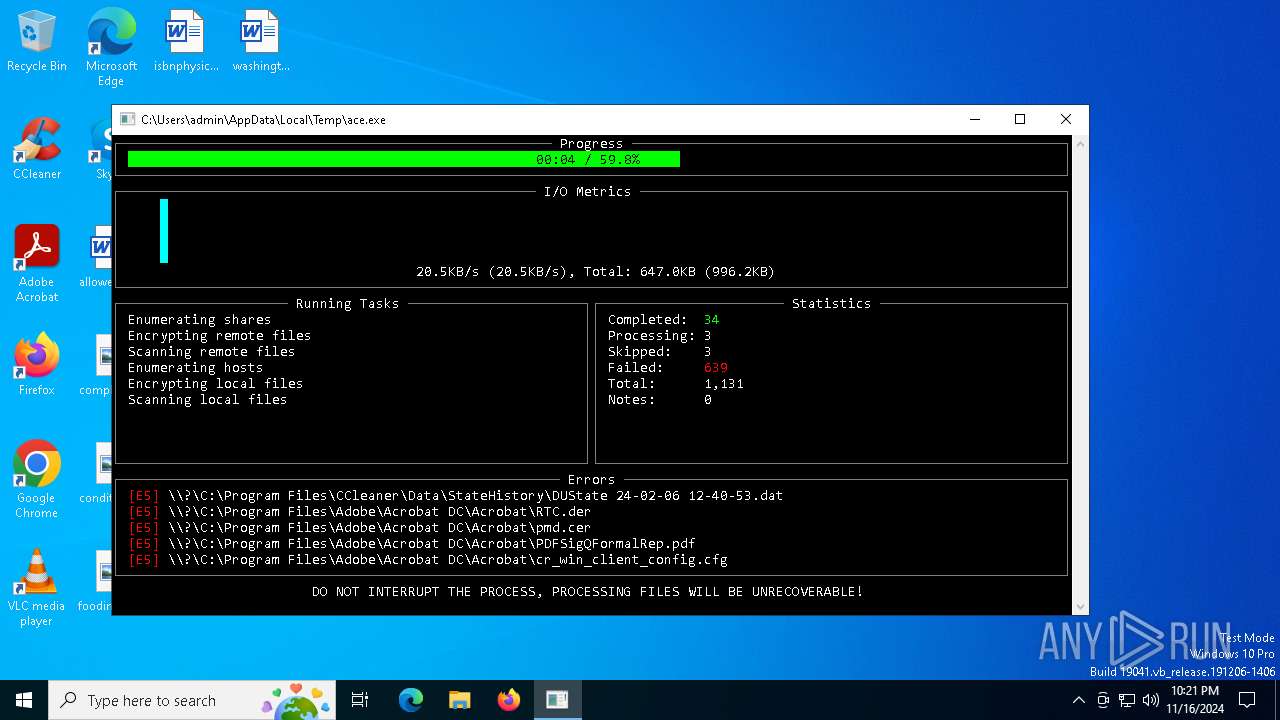
Deletes shadow copies
- ace.exe (PID: 6436)
Using BCDEDIT.EXE to modify recovery options
- ace.exe (PID: 6436)
SUSPICIOUS
Reads security settings of Internet Explorer
- ace.exe (PID: 6436)
Creates file in the systems drive root
- ace.exe (PID: 6436)
Reads the date of Windows installation
- ace.exe (PID: 6436)
Executable content was dropped or overwritten
- ace.exe (PID: 6436)
INFO
The process uses the downloaded file
- ace.exe (PID: 6436)
Process checks computer location settings
- ace.exe (PID: 6436)
Checks supported languages
- ace.exe (PID: 6436)
Reads the computer name
- ace.exe (PID: 6436)
Sends debugging messages
- wbadmin.exe (PID: 6800)
- wbadmin.exe (PID: 6296)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:10:25 16:36:47+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14 |
| CodeSize: | 486400 |
| InitializedDataSize: | 173056 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x642f0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
149
Monitored processes
19
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | "C:\Windows\System32\wbem\WMIC.exe" shadowcopy delete | C:\Windows\System32\wbem\WMIC.exe | — | ace.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1376 | "C:\Windows\System32\bcdedit.exe" /set {default} recoveryenabled No | C:\Windows\System32\bcdedit.exe | — | ace.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Boot Configuration Data Editor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1396 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | wbadmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1428 | "C:\Windows\System32\bcdedit.exe" /set {default} bootstatuspolicy ignoreallfailures | C:\Windows\System32\bcdedit.exe | — | ace.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Boot Configuration Data Editor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ace.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3396 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | bcdedit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3844 | "C:\Windows\System32\wbadmin.exe" delete catalog-quiet | C:\Windows\System32\wbadmin.exe | — | ace.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Command Line Interface for Microsoft® BLB Backup Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3972 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4188 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4556 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | bcdedit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 294
Read events
2 240
Write events
30
Delete events
24
Modification events
| (PID) Process: | (4936) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (4936) SearchApp.exe | Key: | \REGISTRY\A\{96200786-8ea1-d57b-2177-28c9e0c39da0}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_USEREMAIL |
Value: 0000D71468E27538DB01 | |||
| (PID) Process: | (4936) SearchApp.exe | Key: | \REGISTRY\A\{96200786-8ea1-d57b-2177-28c9e0c39da0}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPETEXT |
Value: 0000D71468E27538DB01 | |||
| (PID) Process: | (4936) SearchApp.exe | Key: | \REGISTRY\A\{96200786-8ea1-d57b-2177-28c9e0c39da0}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPE |
Value: 0000D71468E27538DB01 | |||
| (PID) Process: | (4936) SearchApp.exe | Key: | \REGISTRY\A\{96200786-8ea1-d57b-2177-28c9e0c39da0}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPE |
Value: 4E006F006E0065000000D71468E27538DB01 | |||
| (PID) Process: | (6436) ace.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Owner |
Value: 24190000057AF7D37538DB01 | |||
| (PID) Process: | (6436) ace.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | SessionHash |
Value: FF37E8F46F97E3AAE08E5E9CDD33C9B25CEC1B71852F64F6A4ADF73A051D1BE6 | |||
| (PID) Process: | (6436) ace.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6436) ace.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | RegFiles0000 |
Value: \\?\C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\Settings\settings.dat.LOG1 | |||
| (PID) Process: | (6436) ace.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | RegFilesHash |
Value: 875DB7CE177087539658F65A825BB7475389658970E3D209398FB8A09155C2FA | |||
Executable files
187
Suspicious files
2 016
Text files
627
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6436 | ace.exe | C:\Users\admin\Desktop\completedthank.png | image | |
MD5:4E94B0B184FC7518492E2303E91E4A09 | SHA256:7752979A2027A306A71454AB362DDCA13E1B7387E53978427AE81C3B0F2FD405 | |||
| 6436 | ace.exe | C:\bootTel.dat | binary | |
MD5:3934E97878056B9E1BF5B9AD86F64E9D | SHA256:80A64A698823F03D0686610E57881E3A46607242152E542D000C8D69DF4342CB | |||
| 6436 | ace.exe | C:\Users\admin\Documents\createprevious.rtf | text | |
MD5:8E552D4F0A6A07C1DD3AB5B53E0B32F1 | SHA256:319E83C25BD3006875C8E7148E7D9D4E5B2D6657E9A14122BDE9FB6908C8FDBC | |||
| 6436 | ace.exe | C:\Users\admin\Desktop\usingpassword.rtf | text | |
MD5:ADDA323375819494048EA9043A6F8E91 | SHA256:46AD0C5D21E368DD0297301ED5C3F6437994B0BA3388BB7A0DF47F75FD73BAFB | |||
| 6436 | ace.exe | C:\Users\admin\Desktop\conditionsand.jpg | image | |
MD5:93F8626D4C8DE6708BC6CDEA114538D6 | SHA256:8E509CEB6B5467C4D9B0FF17A1C657F0F04B19ED2C26F290457AECEB0006BFD1 | |||
| 6436 | ace.exe | C:\Users\admin\Desktop\foodimpact.jpg | image | |
MD5:D6DD47FDFE55336293C9186032B6441D | SHA256:DF0F23BC4B7C8D59429D1A34CC49988B6ED94D72474EBF55C608B5A93F992808 | |||
| 6436 | ace.exe | C:\Users\admin\Desktop\isbnphysical.rtf | text | |
MD5:5286261E5EB1D1AC6ACC8DDC738292D1 | SHA256:DC6CAC5A8A0E7AA560B56995A486B3485A336F61A66BD64E65E222DA0B9212F7 | |||
| 6436 | ace.exe | C:\Users\admin\Desktop\manageranyone.rtf | text | |
MD5:465651FF4E49B21EC4584E506197CA8B | SHA256:7044757834F79BE6AEE8ADA4ADAB17F2167CE83733188A7CE71EE1657850B828 | |||
| 6436 | ace.exe | C:\ProgramData\Mozilla-1de4eec8-1241-4177-a864-e594e8d1fb38\profile_count_308046B0AF4A39CB.json | binary | |
MD5:E680733B28404BA2CF4DC36B48DA6638 | SHA256:2D686ED27DADBADD377205D4D57823FCB044875575270FCFEB093542B246BC9F | |||
| 6436 | ace.exe | C:\ProgramData\Microsoft\MF\Pending.GRL | binary | |
MD5:F2495A670713630A432E8CD0380DF263 | SHA256:F57771C63820C877EE3EDFDE0DAD252A43477E60852320E6ECE682596BD4159D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
40
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
624 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3960 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5312 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5312 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4836 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
624 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
624 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
780 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
Process | Message |
|---|---|
wbadmin.exe | Invalid parameter passed to C runtime function.
|
wbadmin.exe | Invalid parameter passed to C runtime function.
|