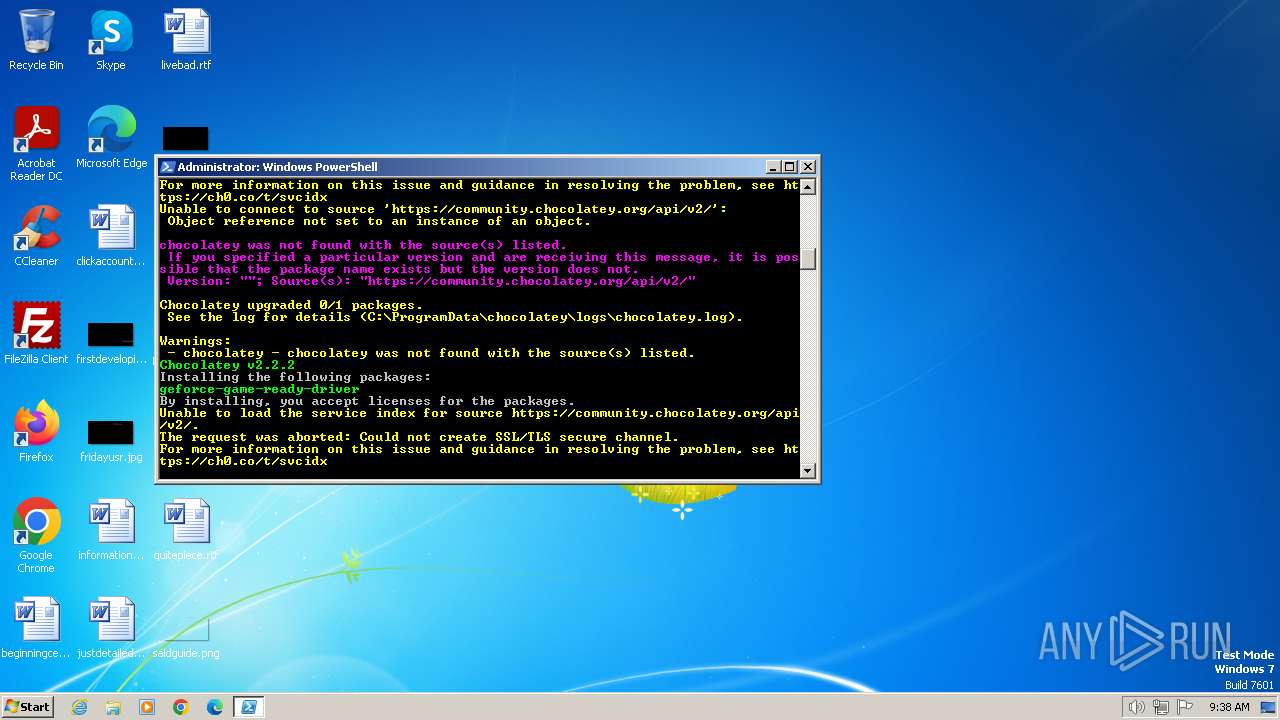
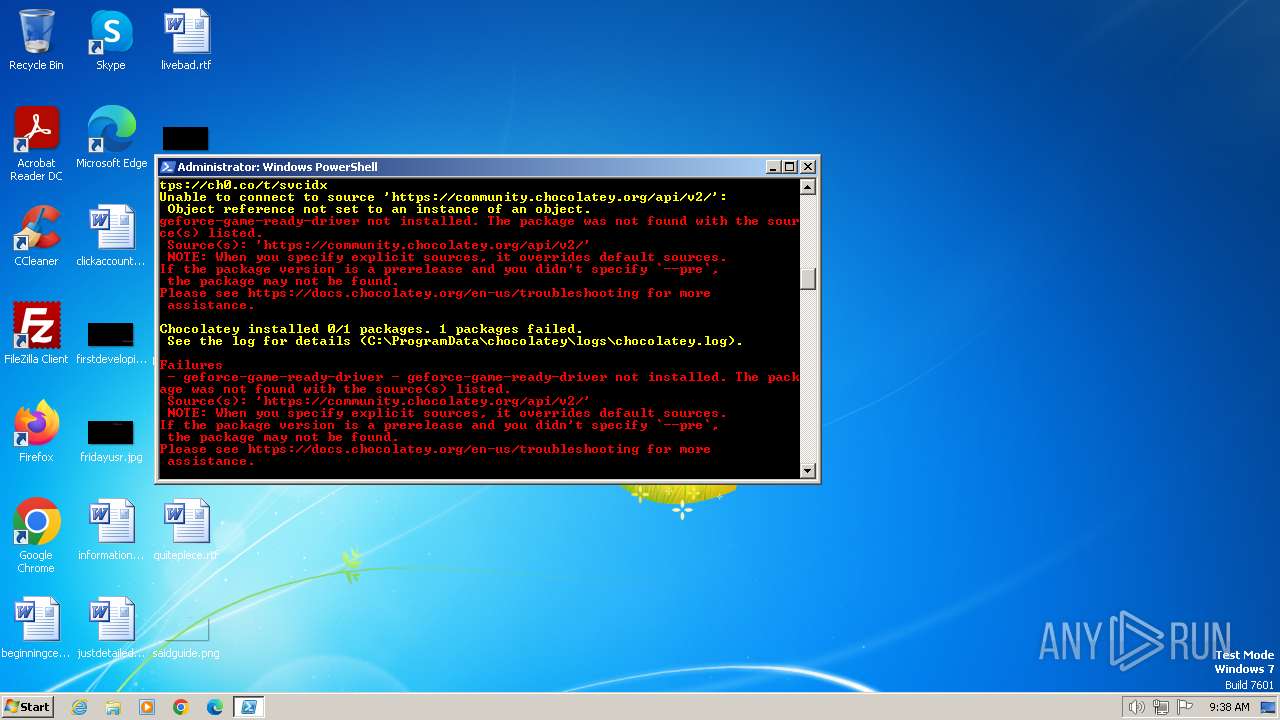
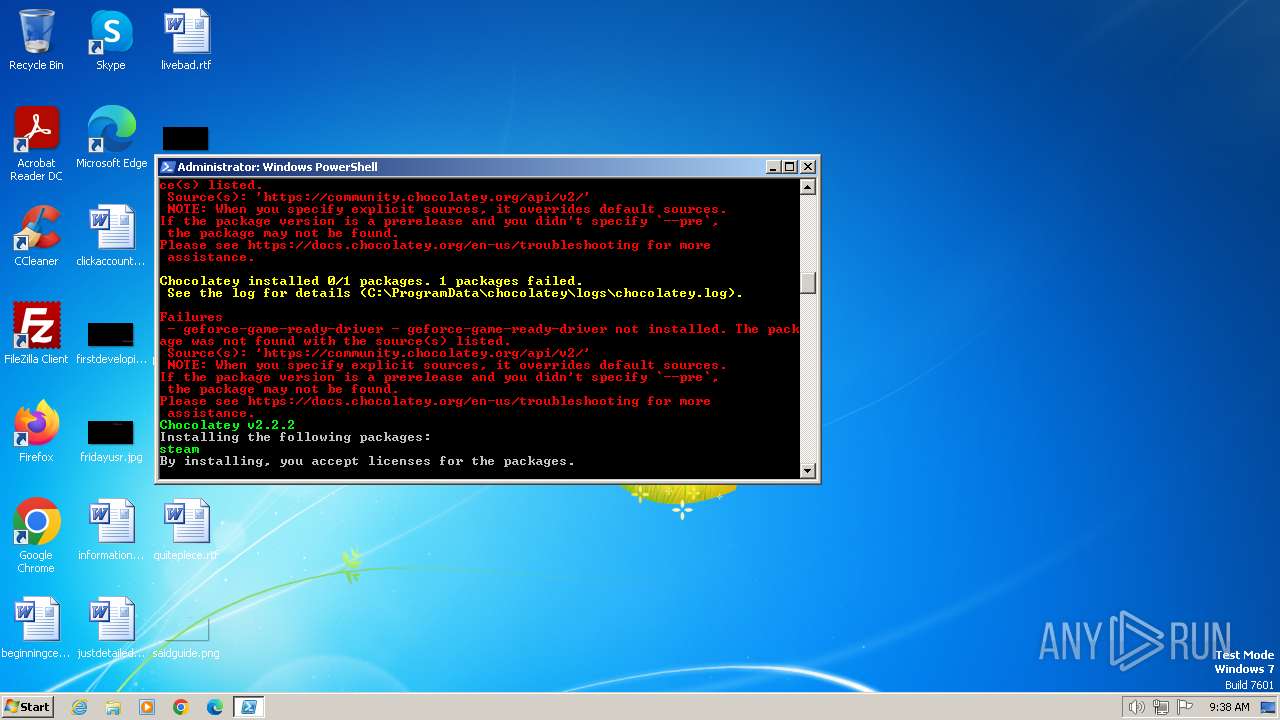
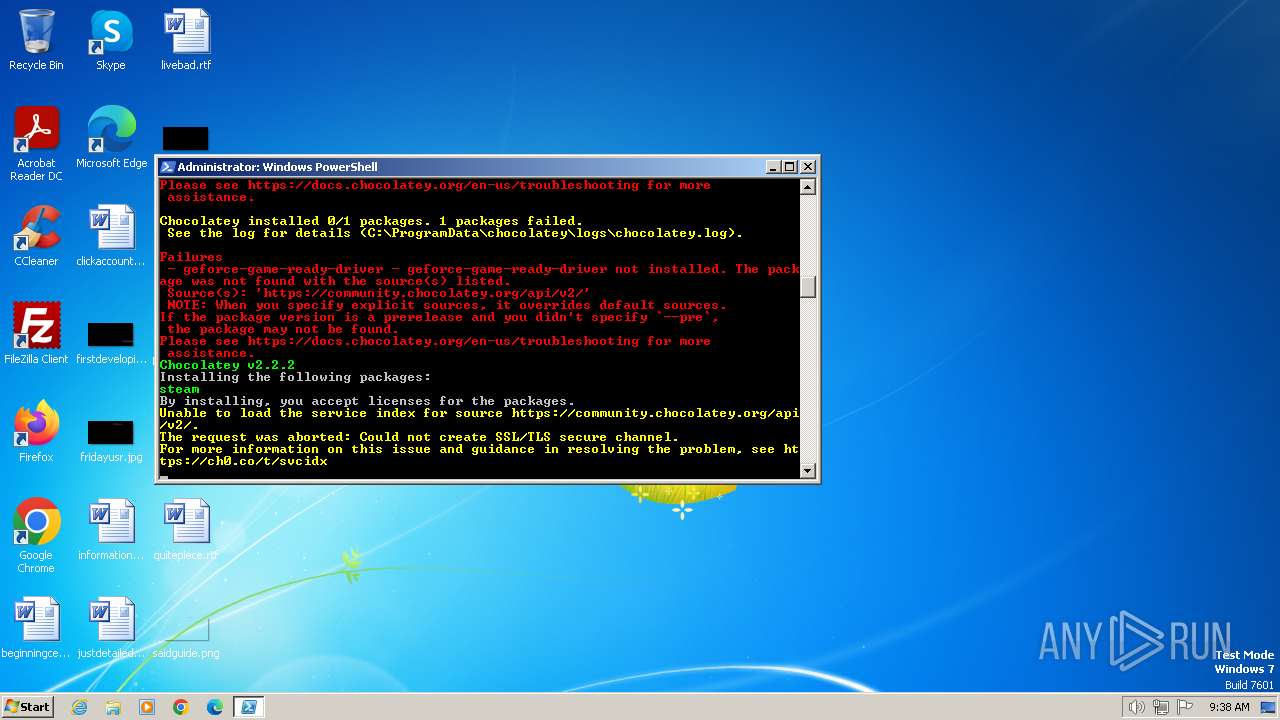
| File name: | script.ps1 |
| Full analysis: | https://app.any.run/tasks/2c7562e0-2a88-4f87-96ee-673f50415632 |
| Verdict: | Malicious activity |
| Analysis date: | January 22, 2024, 09:37:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | UTF-8 Unicode text, with CRLF line terminators |
| MD5: | A0296FF750A6E390576467EDE3C61EF3 |
| SHA1: | 25712311B1D24E2CCD0415909D58815DFD82A3B5 |
| SHA256: | 1E3C4E8BE1DD218A9F4A9B2983849532C34CFE8C2522C2A054E2DDC2E4CACD38 |
| SSDEEP: | 24:VLmIULR6L9hAlu2OxvthLgMqp92hFzFXzY3FgNdliQ8/CFqfFgNP:ZmFRO9fDxVhop92Fs3FgfliQ8KFqfFgB |
MALICIOUS
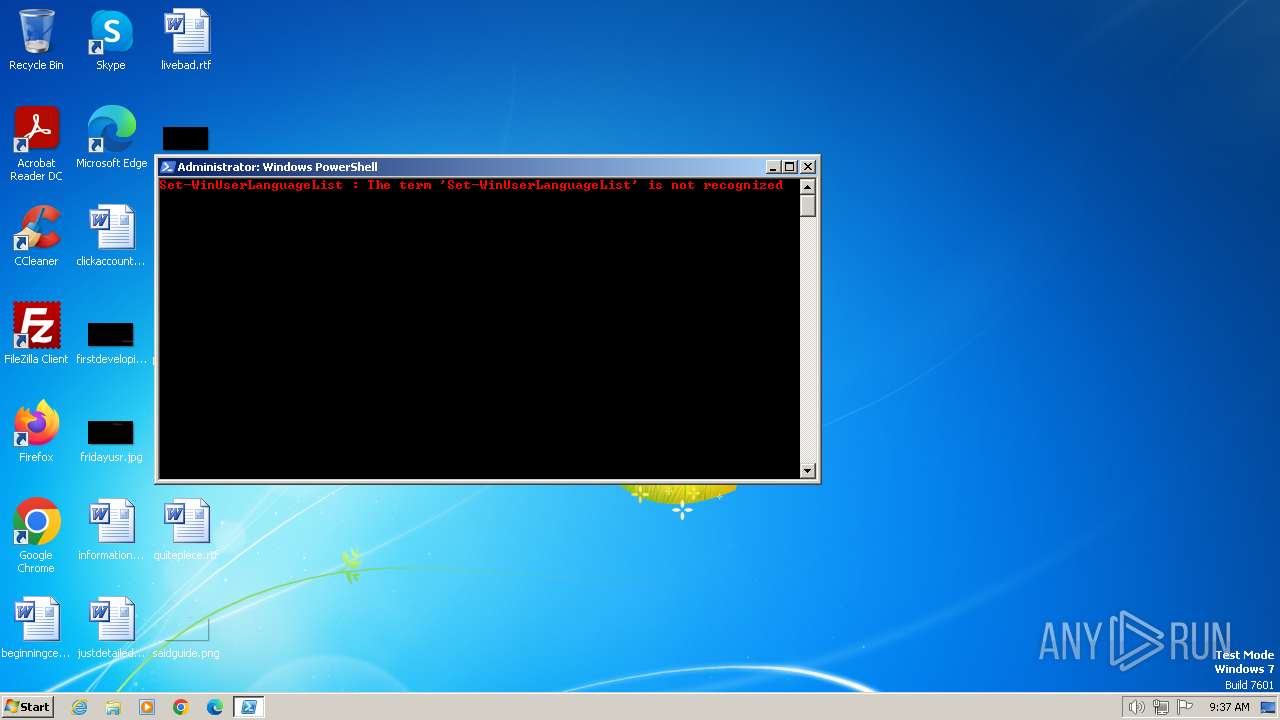
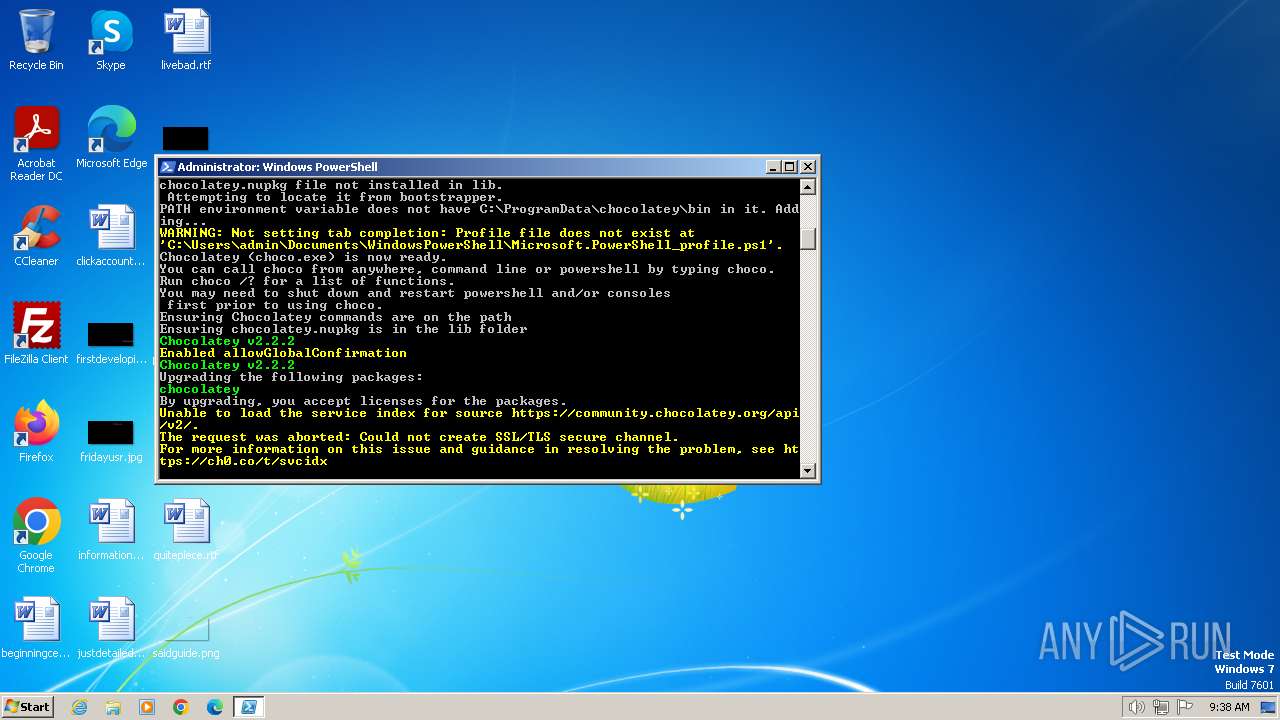
Bypass execution policy to execute commands
- powershell.exe (PID: 1652)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 2040)
Drops the executable file immediately after the start
- powershell.exe (PID: 1652)
- csc.exe (PID: 2340)
Starts Visual C# compiler
- powershell.exe (PID: 1652)
SUSPICIOUS
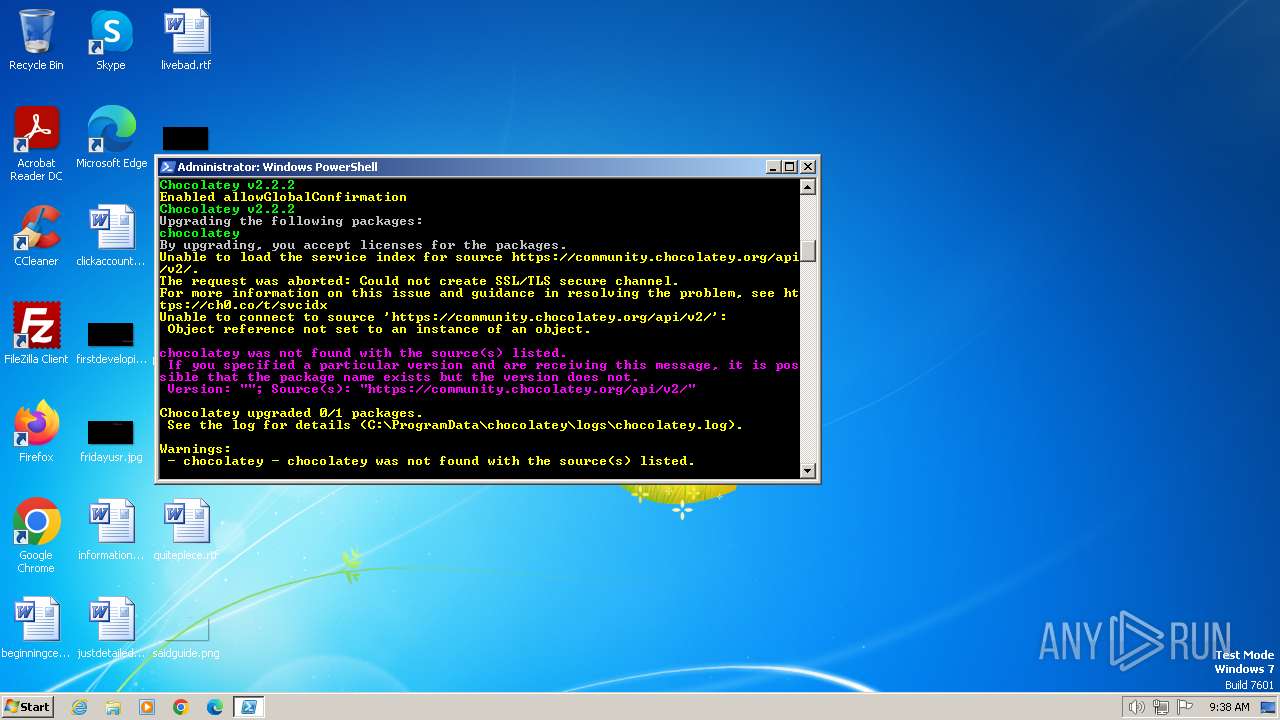
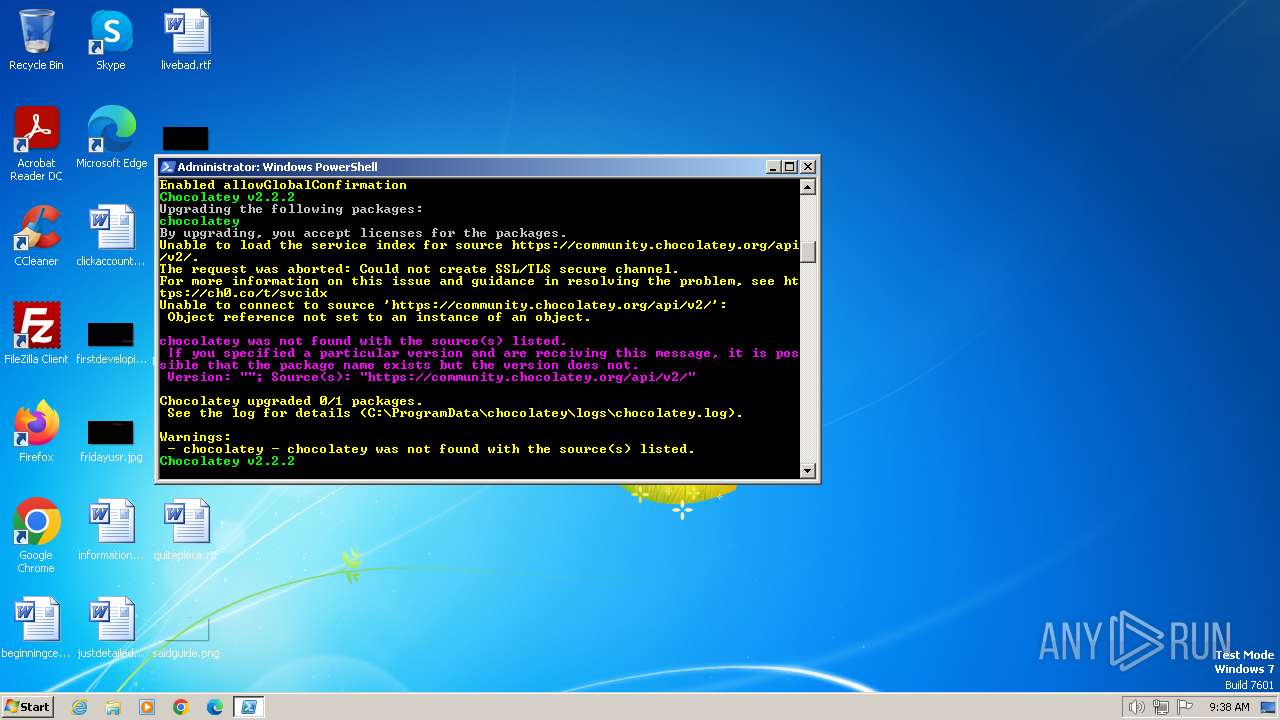
Reads the Internet Settings
- powershell.exe (PID: 2040)
- powershell.exe (PID: 696)
- powershell.exe (PID: 1652)
- choco.exe (PID: 2572)
- choco.exe (PID: 1424)
- choco.exe (PID: 240)
- choco.exe (PID: 908)
Application launched itself
- powershell.exe (PID: 2040)
- powershell.exe (PID: 1652)
The process executes Powershell scripts
- powershell.exe (PID: 2040)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 2040)
- powershell.exe (PID: 1652)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 2040)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 696)
- powershell.exe (PID: 1652)
Unusual connection from system programs
- powershell.exe (PID: 1652)
The Powershell connects to the Internet
- powershell.exe (PID: 1652)
Executable content was dropped or overwritten
- powershell.exe (PID: 1652)
- csc.exe (PID: 2340)
Uses .NET C# to load dll
- powershell.exe (PID: 1652)
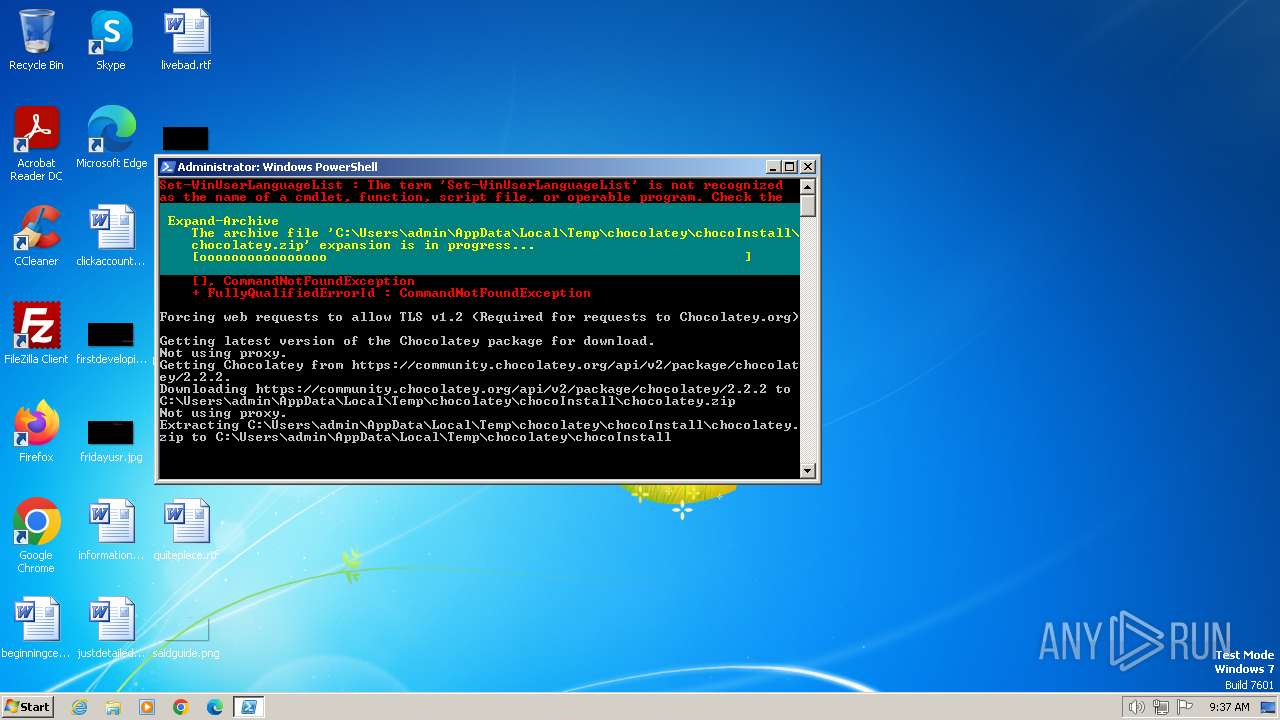
Drops 7-zip archiver for unpacking
- powershell.exe (PID: 1652)
INFO
Checks supported languages
- csc.exe (PID: 2340)
- cvtres.exe (PID: 2448)
- choco.exe (PID: 1892)
- choco.exe (PID: 2440)
- choco.exe (PID: 2644)
- choco.exe (PID: 1924)
- choco.exe (PID: 2572)
- choco.exe (PID: 2760)
- choco.exe (PID: 240)
- choco.exe (PID: 1424)
- choco.exe (PID: 2792)
- choco.exe (PID: 2524)
- choco.exe (PID: 908)
- choco.exe (PID: 948)
- choco.exe (PID: 3068)
Reads the machine GUID from the registry
- cvtres.exe (PID: 2448)
- choco.exe (PID: 2644)
- csc.exe (PID: 2340)
- choco.exe (PID: 1892)
- choco.exe (PID: 1424)
- choco.exe (PID: 2572)
- choco.exe (PID: 908)
- choco.exe (PID: 948)
- choco.exe (PID: 240)
Create files in a temporary directory
- csc.exe (PID: 2340)
- cvtres.exe (PID: 2448)
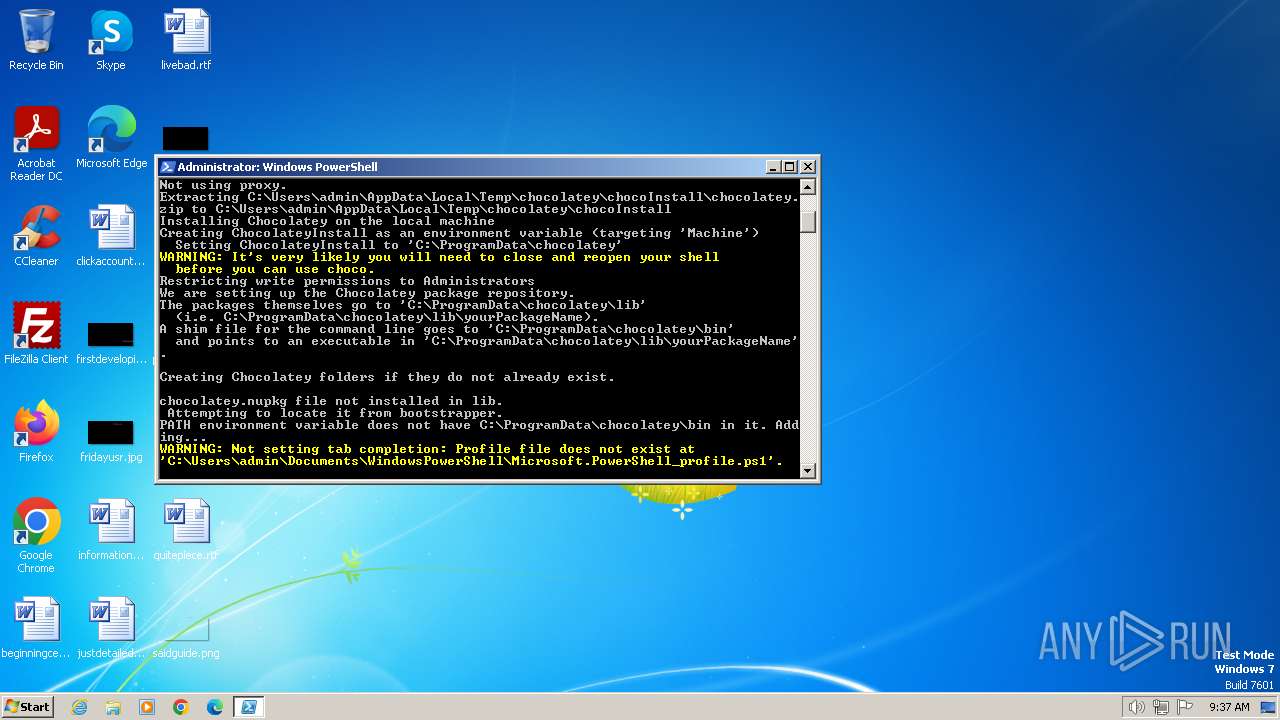
Creates files in the program directory
- powershell.exe (PID: 1652)
- choco.exe (PID: 1892)
- choco.exe (PID: 2644)
Reads the computer name
- choco.exe (PID: 1892)
- choco.exe (PID: 2440)
- choco.exe (PID: 2644)
- choco.exe (PID: 1924)
- choco.exe (PID: 2572)
- choco.exe (PID: 2760)
- choco.exe (PID: 1424)
- choco.exe (PID: 2792)
- choco.exe (PID: 2524)
- choco.exe (PID: 908)
- choco.exe (PID: 3068)
- choco.exe (PID: 948)
- choco.exe (PID: 240)
Reads Environment values
- choco.exe (PID: 2644)
- choco.exe (PID: 2572)
- choco.exe (PID: 1424)
- choco.exe (PID: 240)
- choco.exe (PID: 908)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
57
Monitored processes
20
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
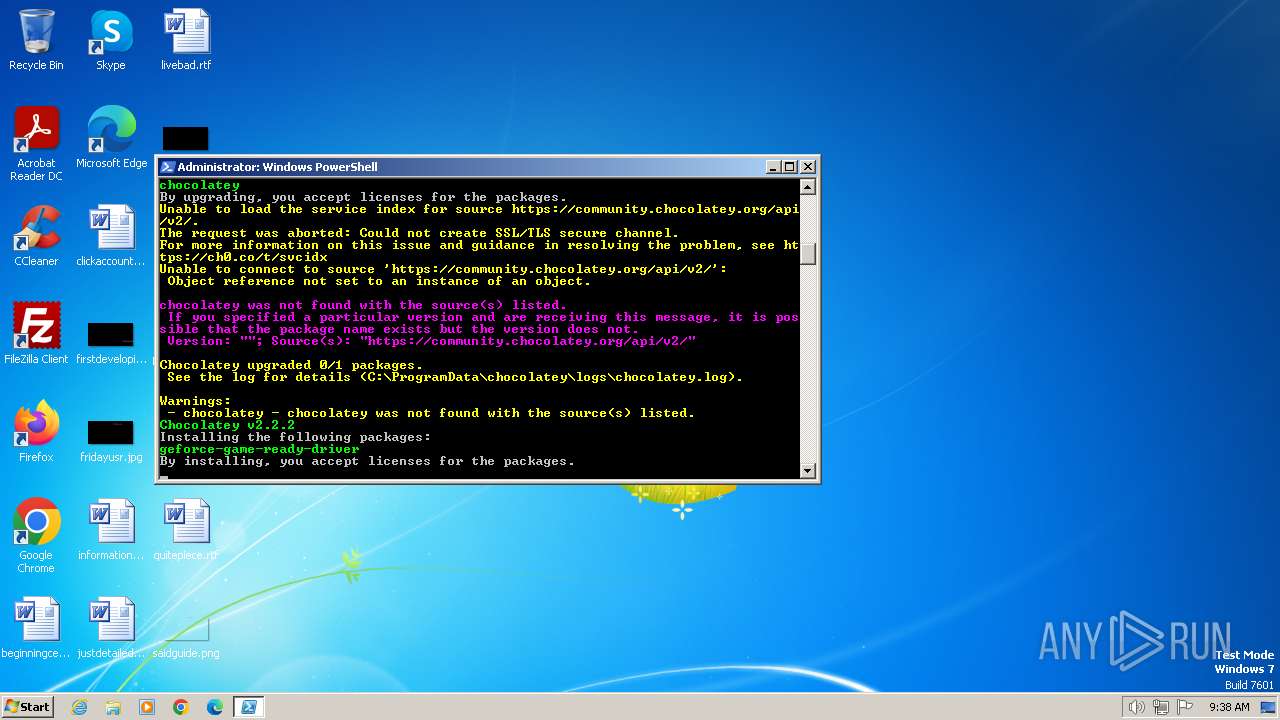
| 240 | "C:\ProgramData\chocolatey\choco.exe" install steam | C:\ProgramData\chocolatey\choco.exe | choco.exe | ||||||||||||
User: admin Company: Chocolatey Software, Inc. Integrity Level: HIGH Description: Exit code: 1 Version: 2.2.2.0 Modules
| |||||||||||||||
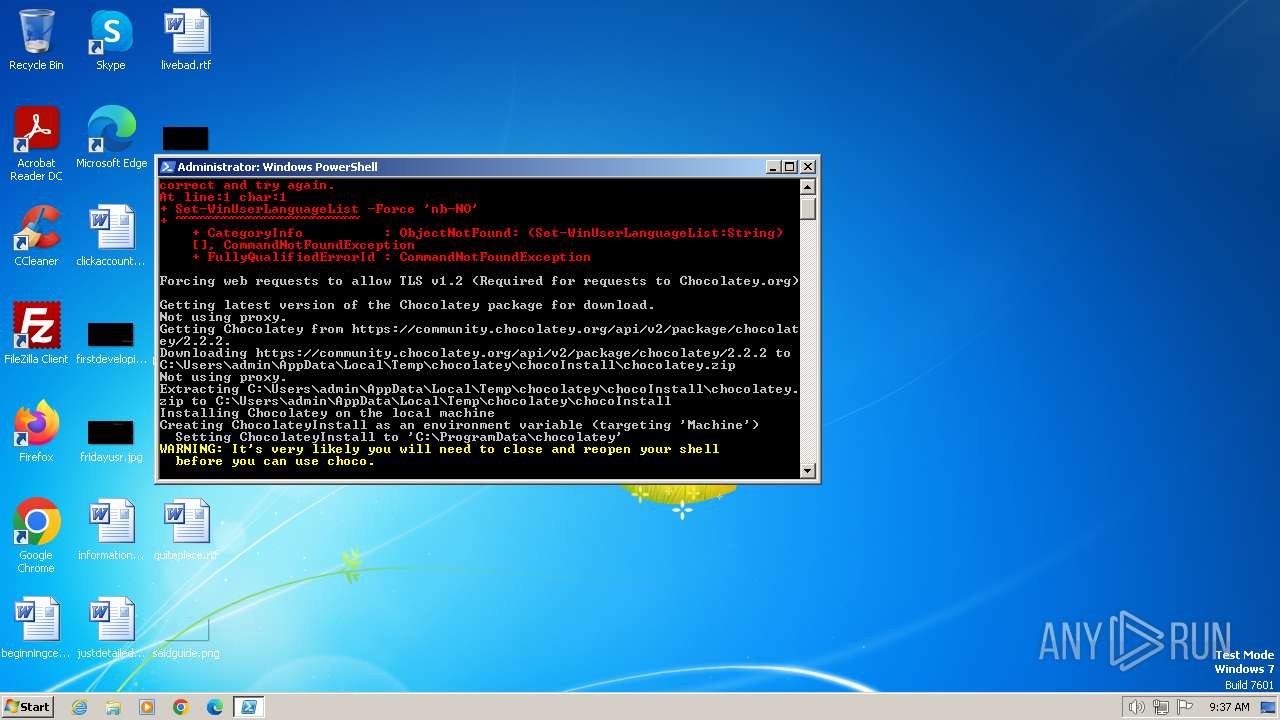
| 696 | "C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe" -command "Set-WinUserLanguageList -Force 'nb-NO'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 908 | "C:\ProgramData\chocolatey\choco.exe" install epicgameslauncher | C:\ProgramData\chocolatey\choco.exe | choco.exe | ||||||||||||
User: admin Company: Chocolatey Software, Inc. Integrity Level: HIGH Description: Exit code: 1 Version: 2.2.2.0 Modules
| |||||||||||||||
| 948 | "C:\ProgramData\chocolatey\choco.exe" install firefox | C:\ProgramData\chocolatey\choco.exe | — | choco.exe | |||||||||||
User: admin Company: Chocolatey Software, Inc. Integrity Level: HIGH Description: Exit code: 0 Version: 2.2.2.0 Modules
| |||||||||||||||
| 1424 | "C:\ProgramData\chocolatey\choco.exe" install geforce-game-ready-driver | C:\ProgramData\chocolatey\choco.exe | choco.exe | ||||||||||||
User: admin Company: Chocolatey Software, Inc. Integrity Level: HIGH Description: Exit code: 1 Version: 2.2.2.0 Modules
| |||||||||||||||
| 1652 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\script.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1892 | "C:\ProgramData\chocolatey\choco.exe" -v | C:\ProgramData\chocolatey\choco.exe | — | powershell.exe | |||||||||||
User: admin Company: Chocolatey Software, Inc. Integrity Level: HIGH Description: Exit code: 0 Version: 2.2.2.0 Modules
| |||||||||||||||
| 1924 | "C:\ProgramData\chocolatey\bin\choco.exe" upgrade chocolatey | C:\ProgramData\chocolatey\bin\choco.exe | — | powershell.exe | |||||||||||
User: admin Company: Chocolatey Software, Inc. Integrity Level: HIGH Description: chocolatey - Chocolatey Shim Exit code: 0 Version: 0.12.1.0 Modules
| |||||||||||||||
| 2040 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\AppData\Local\Temp\script.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2096 | "C:\Windows\System32\setx.exe" ChocolateyLastPathUpdate "133503898779627500" | C:\Windows\System32\setx.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setx - Sets environment variables Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
11 686
Read events
11 538
Write events
148
Delete events
0
Modification events
| (PID) Process: | (2040) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2040) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2040) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2040) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2040) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1652) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (696) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (696) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (696) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (696) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
14
Suspicious files
18
Text files
134
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 696 | powershell.exe | C:\Users\admin\AppData\Local\Temp\gj5abpas.viy.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2040 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\IU9VISJH8TGNXMKNR9OX.temp | binary | |
MD5:F500255BDC0DD45A0934243E38529D10 | SHA256:AD4304402753CEF71770C63692428001309617BDA00D87E229D197721D29496E | |||
| 1652 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\SYY6YFSM6YLRYUD5FP3K.temp | binary | |
MD5:F500255BDC0DD45A0934243E38529D10 | SHA256:AD4304402753CEF71770C63692428001309617BDA00D87E229D197721D29496E | |||
| 2040 | powershell.exe | C:\Users\admin\AppData\Local\Temp\uxyrwygv.wui.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2040 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 2040 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:F500255BDC0DD45A0934243E38529D10 | SHA256:AD4304402753CEF71770C63692428001309617BDA00D87E229D197721D29496E | |||
| 2040 | powershell.exe | C:\Users\admin\AppData\Local\Temp\vxik4p22.g2h.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1652 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateysetup.psm1 | text | |
MD5:410F754FE754319C97795531165435CA | SHA256:082A446EFFA970A29AD3C6D2CB8EB12F6BB20B9988C410E0C61D203860D76C7E | |||
| 1652 | powershell.exe | C:\Users\admin\AppData\Local\Temp\oqz130y5.lf0.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1652 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RFdfca0.TMP | binary | |
MD5:F500255BDC0DD45A0934243E38529D10 | SHA256:AD4304402753CEF71770C63692428001309617BDA00D87E229D197721D29496E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
23
DNS requests
2
Threats
25
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1652 | powershell.exe | 104.20.74.28:443 | community.chocolatey.org | CLOUDFLARENET | — | shared |
2572 | choco.exe | 104.20.74.28:443 | community.chocolatey.org | CLOUDFLARENET | — | shared |
1424 | choco.exe | 104.20.74.28:443 | community.chocolatey.org | CLOUDFLARENET | — | shared |
240 | choco.exe | 104.20.74.28:443 | community.chocolatey.org | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
community.chocolatey.org |
| malicious |
packages.chocolatey.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1652 | powershell.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
2572 | choco.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
2572 | choco.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
2572 | choco.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
2572 | choco.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
2572 | choco.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
2572 | choco.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
1424 | choco.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
1424 | choco.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
1424 | choco.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |