| URL: | https://fivemods.io/ |
| Full analysis: | https://app.any.run/tasks/3873c9ab-031c-4a43-bfe7-23d522e098ae |
| Verdict: | Malicious activity |
| Analysis date: | March 05, 2024, 10:54:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 621F269197213F63D765556556CA8AF7 |
| SHA1: | 25915D063A9E84FD73F0CD0A3B9A46D4ED82D2D3 |
| SHA256: | 1E321ABCAE5D66136F8A6C325AB3E09AEE159F702CE278DC00E7DF13559AA891 |
| SSDEEP: | 3:N8hTKK:2L |
MALICIOUS
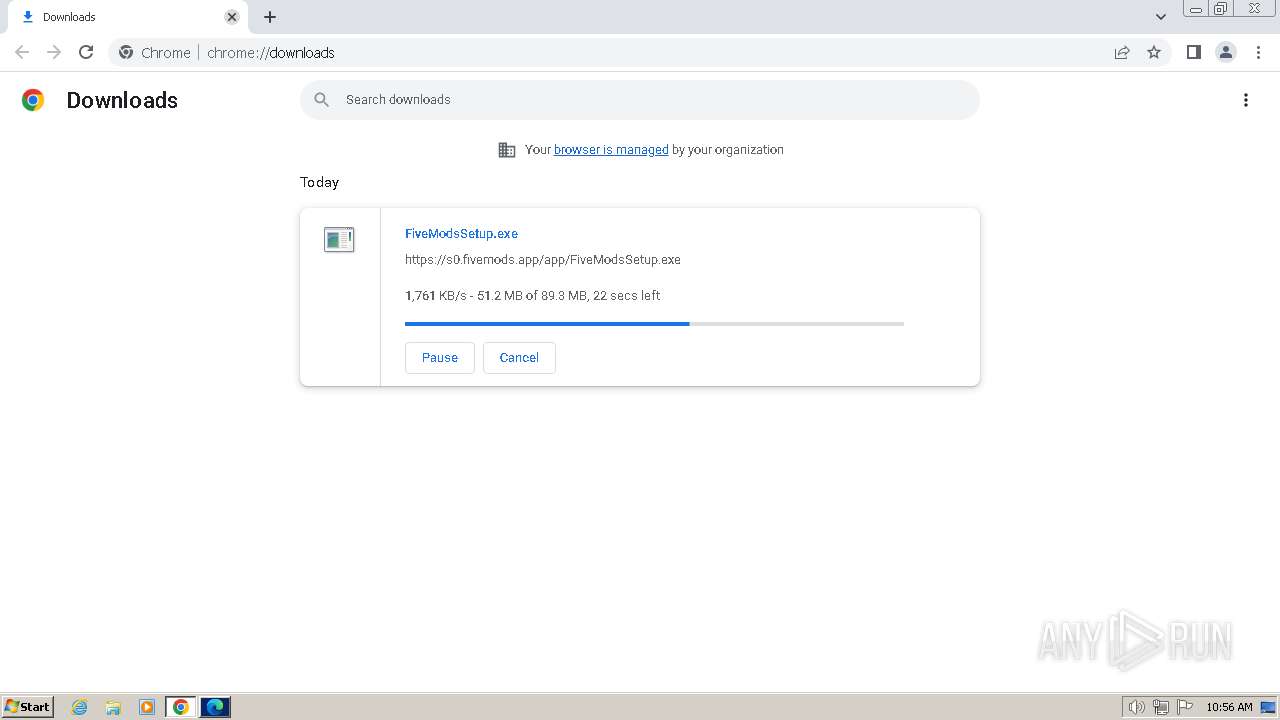
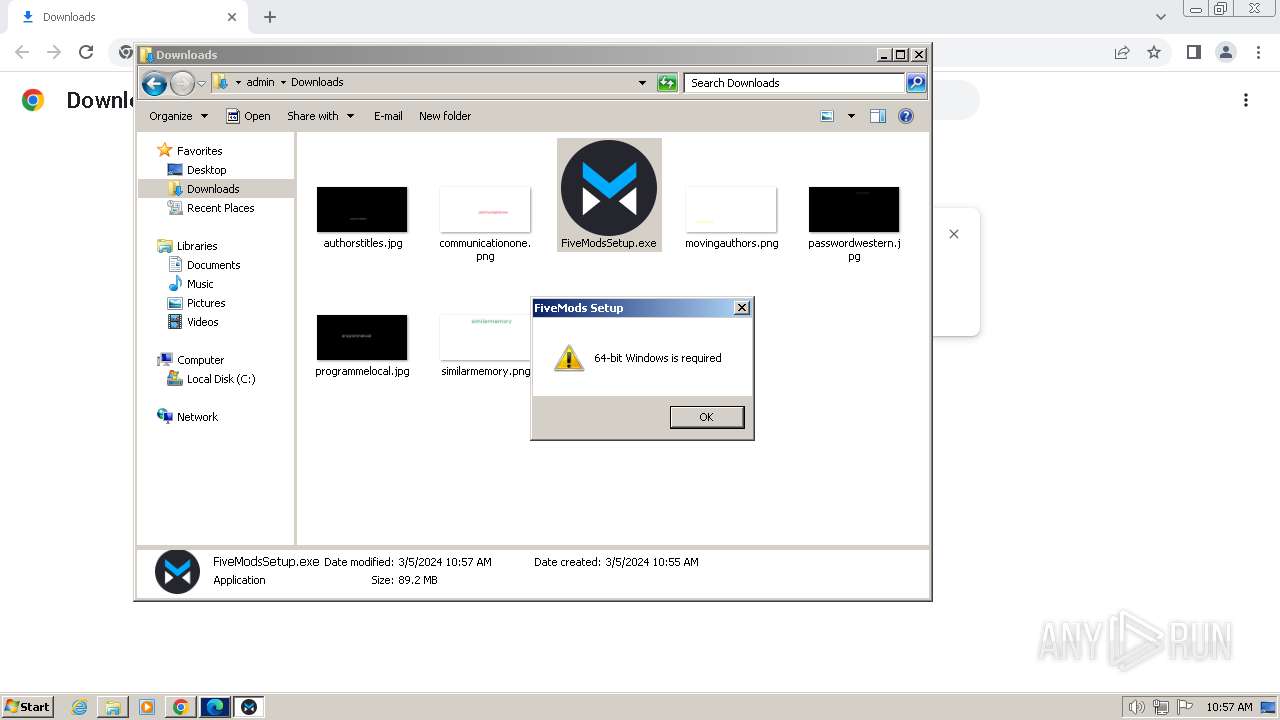
Drops the executable file immediately after the start
- FiveModsSetup.exe (PID: 696)
- FiveModsSetup.exe (PID: 3960)
SUSPICIOUS
The process creates files with name similar to system file names
- FiveModsSetup.exe (PID: 696)
- FiveModsSetup.exe (PID: 3960)
Executable content was dropped or overwritten
- FiveModsSetup.exe (PID: 696)
- FiveModsSetup.exe (PID: 3960)
Malware-specific behavior (creating "System.dll" in Temp)
- FiveModsSetup.exe (PID: 3960)
- FiveModsSetup.exe (PID: 696)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 3668)
- FiveModsSetup.exe (PID: 3960)
- FiveModsSetup.exe (PID: 696)
Checks supported languages
- wmpnscfg.exe (PID: 3668)
- FiveModsSetup.exe (PID: 3960)
- FiveModsSetup.exe (PID: 696)
Application launched itself
- iexplore.exe (PID: 1432)
- msedge.exe (PID: 2904)
- chrome.exe (PID: 1232)
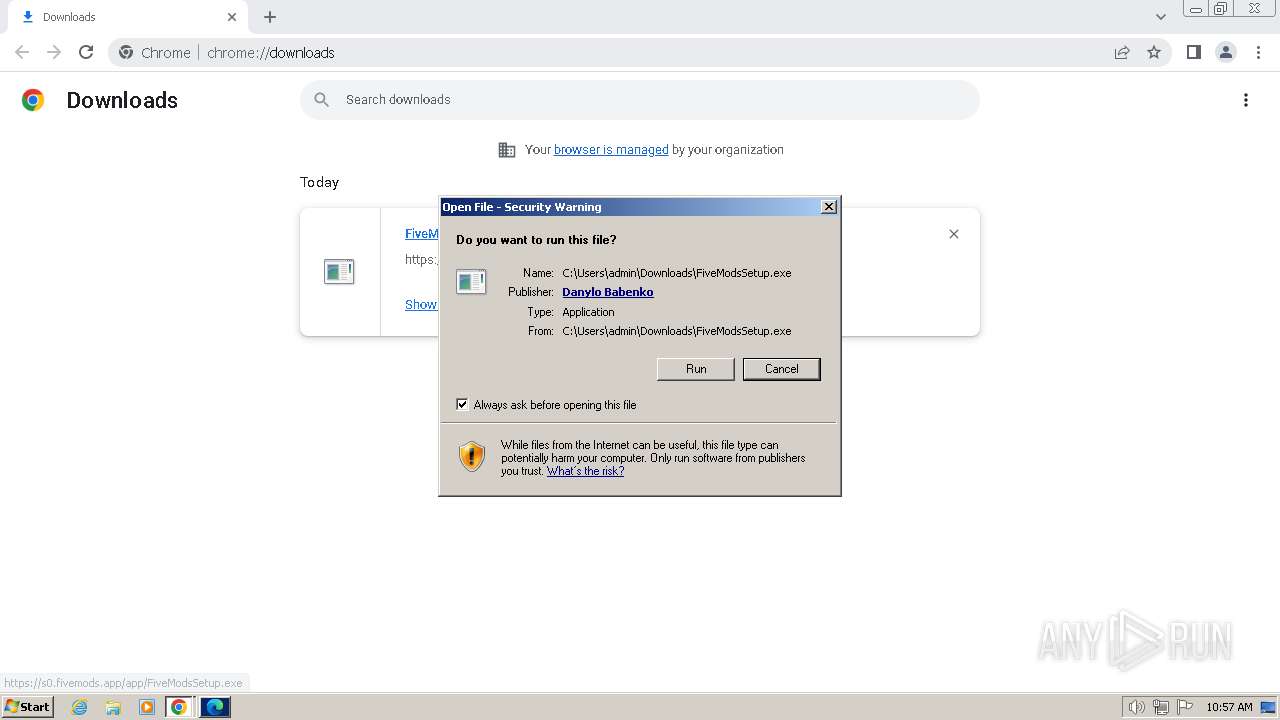
Manual execution by a user
- msedge.exe (PID: 2904)
- chrome.exe (PID: 1232)
- FiveModsSetup.exe (PID: 696)
- explorer.exe (PID: 1624)
The process uses the downloaded file
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 3396)
- chrome.exe (PID: 3876)
- chrome.exe (PID: 1232)
Executable content was dropped or overwritten
- chrome.exe (PID: 1232)
Drops the executable file immediately after the start
- chrome.exe (PID: 1232)
Create files in a temporary directory
- FiveModsSetup.exe (PID: 696)
- FiveModsSetup.exe (PID: 3960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
91
Monitored processes
48
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 492 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1464 --field-trial-handle=1300,i,8972673202082081404,9784428239521781611,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
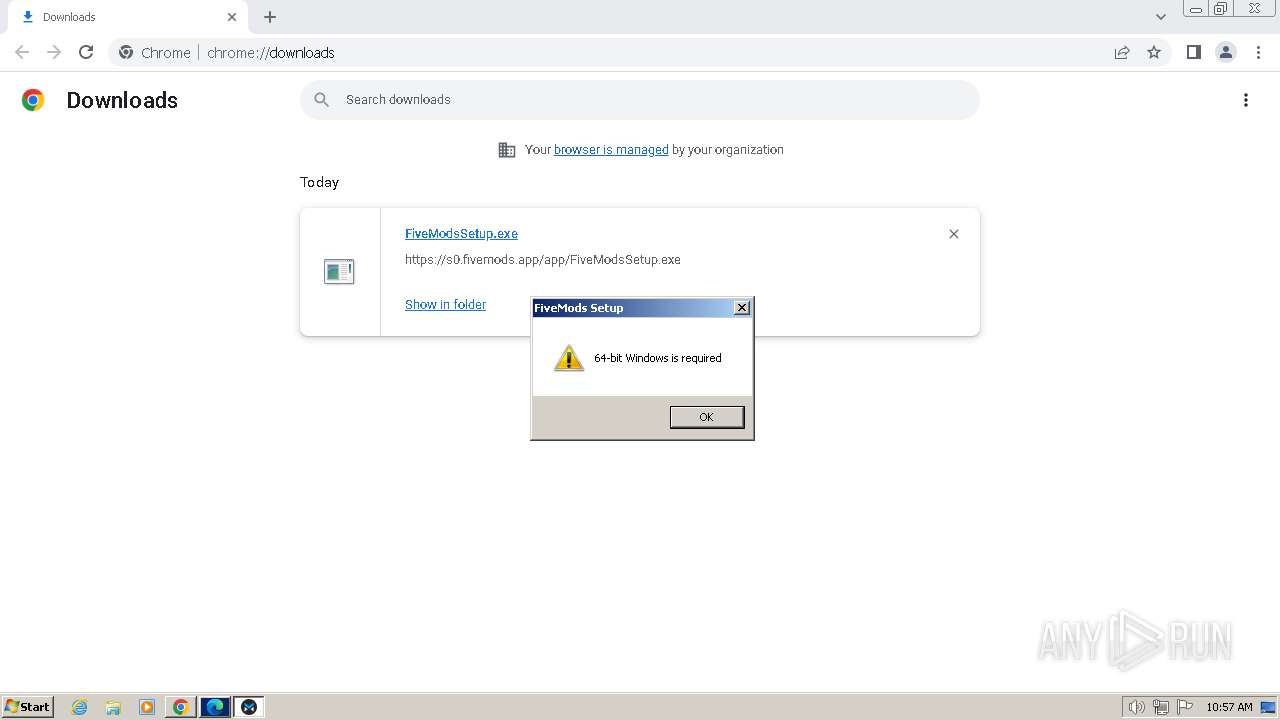
| 696 | "C:\Users\admin\Downloads\FiveModsSetup.exe" | C:\Users\admin\Downloads\FiveModsSetup.exe | explorer.exe | ||||||||||||
User: admin Company: FiveMods Integrity Level: MEDIUM Description: Install stunning mods for FiveM in a single click via FiveMods Exit code: 2 Version: 0.1.47 Modules
| |||||||||||||||
| 864 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=2084 --field-trial-handle=1132,i,17748900638695698909,14804379846856692644,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 884 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=1040 --field-trial-handle=1132,i,17748900638695698909,14804379846856692644,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1124 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3532 --field-trial-handle=1300,i,8972673202082081404,9784428239521781611,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1172 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=2208 --field-trial-handle=1132,i,17748900638695698909,14804379846856692644,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1404 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6a888b38,0x6a888b48,0x6a888b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1424 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=2324 --field-trial-handle=1132,i,17748900638695698909,14804379846856692644,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1432 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://fivemods.io/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
54 914
Read events
54 474
Write events
382
Delete events
58
Modification events
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31092459 | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31092459 | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
14
Suspicious files
287
Text files
216
Unknown types
250
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:A50C296B0773682B489E5137AFF315D7 | SHA256:5DCAA0FFFA0E3905164EEE327300475BFDDECF14AF8D4857E66CB2E6DED35900 | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\2-e4f172e9[1].webp | image | |
MD5:DBF4C3DC1A965670F26A3BAC477ABD88 | SHA256:9BF82ED6C5DB698D5E3ACA8547CA2671B96F798AB8AA58B0F78926EE7C26E8BF | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\app-ed45db4c[1].js | text | |
MD5:4C238886FA2FC60668D1B9EF12745794 | SHA256:0D6A0C41BB5EF35C667076F8C8E08070F25503242080178EC328D3DD02D9DC8C | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\email-decode.min[1].js | html | |
MD5:9E8F56E8E1806253BA01A95CFC3D392C | SHA256:2595496FE48DF6FCF9B1BC57C29A744C121EB4DD11566466BC13D2E52E6BBCC8 | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\1-b9a956f1[1].webp | image | |
MD5:AC062457ACB72AD80E9DDFD435D3D945 | SHA256:F97585758243301569B4DE78670AE15CB7E7E5F47A3C096445E0E5C6FB4E9C1D | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\SRZUCU66.txt | text | |
MD5:60AF036785371031E070BA163C67814A | SHA256:4678A52B18E5ACBE2341AD973400536D5DFCEADACE75E23AF68C56760E94C8C9 | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\M3H0U47Y.htm | html | |
MD5:3D8A40D26D382D9EA9C8645F5CB06F06 | SHA256:2079087B272A4183C65DA723DBB0C6885D8062144D3CF4F05C9FBA0BCA67FF51 | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:68272D24BE5B10F500D88CE263AAEF14 | SHA256:877549E958DFF178F68DDD836210C6D9385237279ABFBBAE411736621C74E4BE | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\p1-8ed93740[1].webp | image | |
MD5:8F191400EC7C221338D2C2D68A06449F | SHA256:0A37E251F5ED2D1B164D8D7684A32DF3F64A1AEE931E836BE140D46E1762FB69 | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\p2-a2816da8[1].webp | image | |
MD5:922018579FAAA4CC17C81B6DCB6E24F7 | SHA256:CA6A071A5849905C709B5F0F2A05DC026AAB933B6E69B16C476922416866EF7C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
164
DNS requests
151
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3892 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?927e0d673a39dd41 | unknown | — | — | unknown |
3892 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d362edf7b65e9a48 | unknown | — | — | unknown |
3892 | iexplore.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3892 | iexplore.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
3892 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
3892 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
3892 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
3892 | iexplore.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3892 | iexplore.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDDidhelLJLaQnsKqlsZYpa | unknown | binary | 472 b | unknown |
3892 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3892 | iexplore.exe | 188.114.97.3:443 | fivemods.io | CLOUDFLARENET | NL | unknown |
3892 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3892 | iexplore.exe | 142.250.185.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3892 | iexplore.exe | 104.16.125.175:443 | unpkg.com | CLOUDFLARENET | — | shared |
3892 | iexplore.exe | 151.101.2.137:443 | code.jquery.com | FASTLY | US | unknown |
3892 | iexplore.exe | 104.16.87.20:443 | cdn.jsdelivr.net | CLOUDFLARENET | — | shared |
3892 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fivemods.io |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
unpkg.com |
| whitelisted |
code.jquery.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3892 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
3892 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
3892 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
3892 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
3128 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
3128 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
3128 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
3128 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |