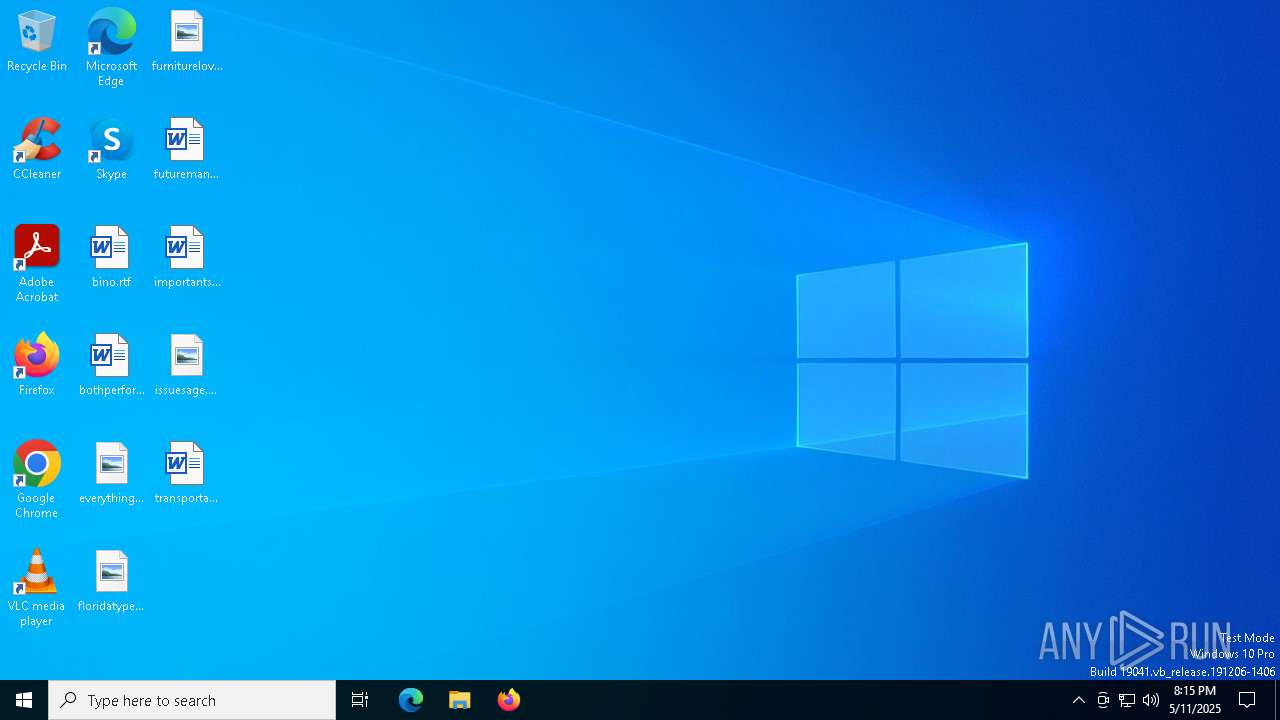
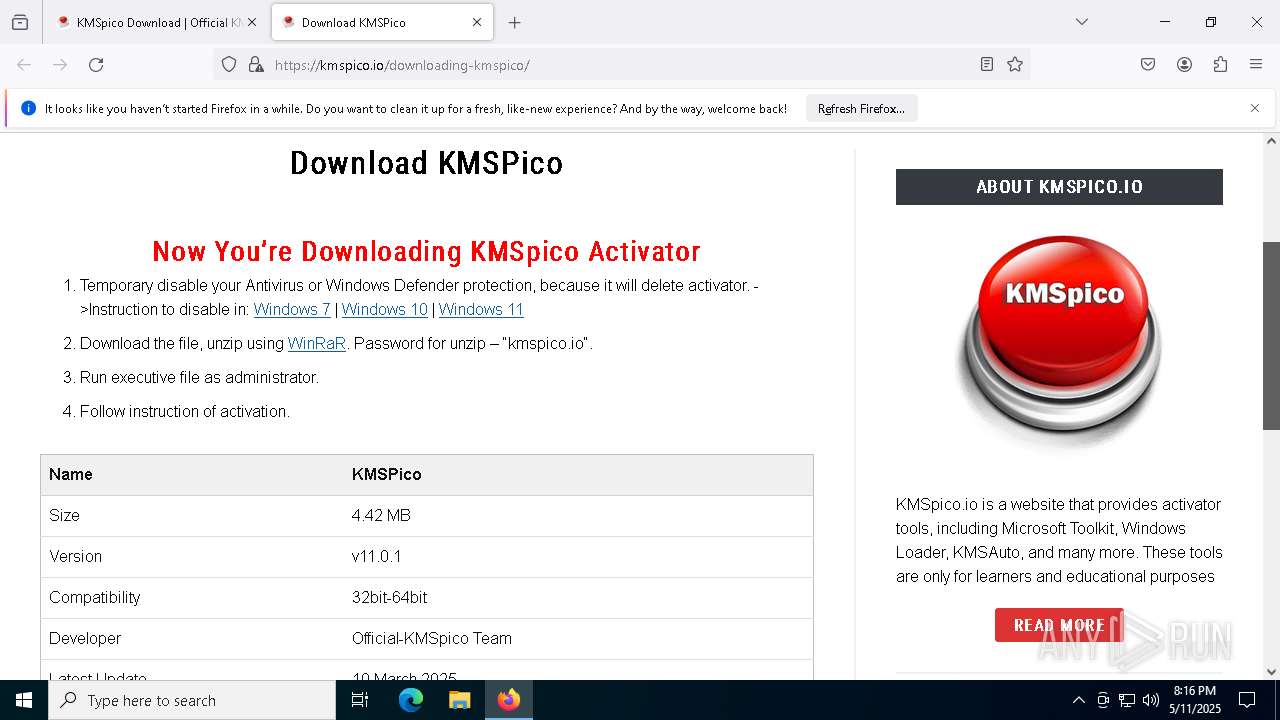
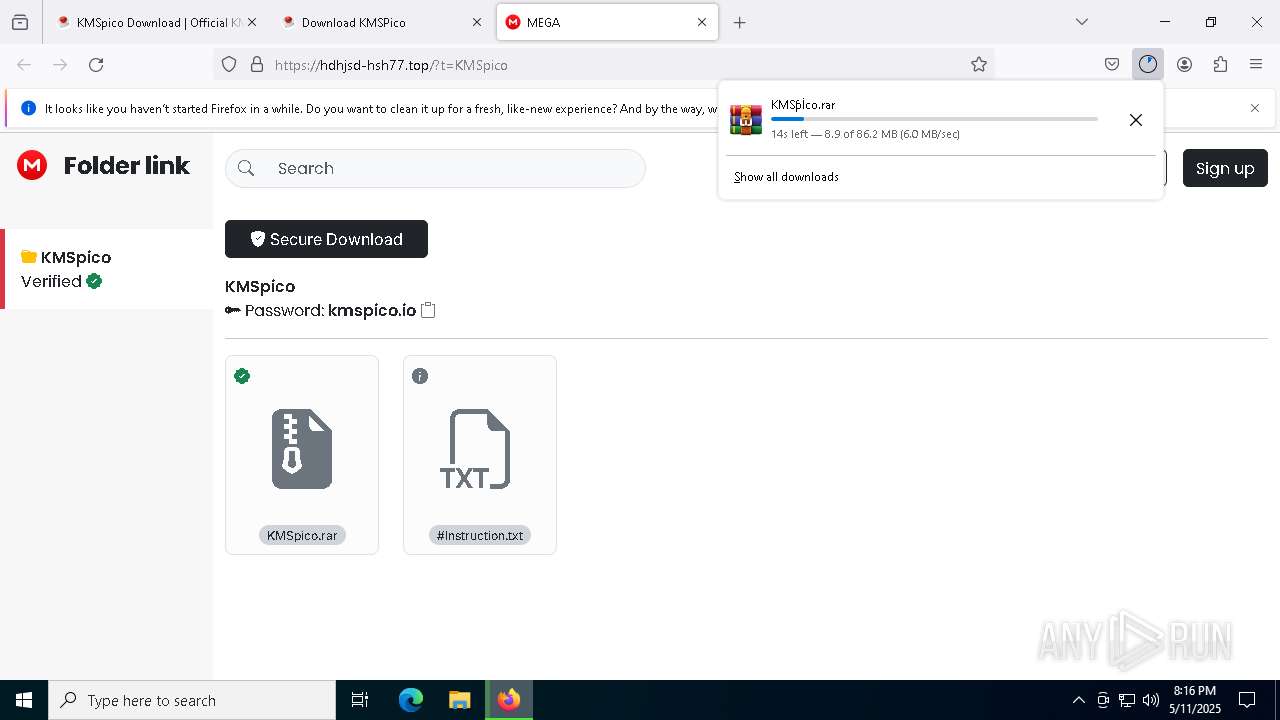
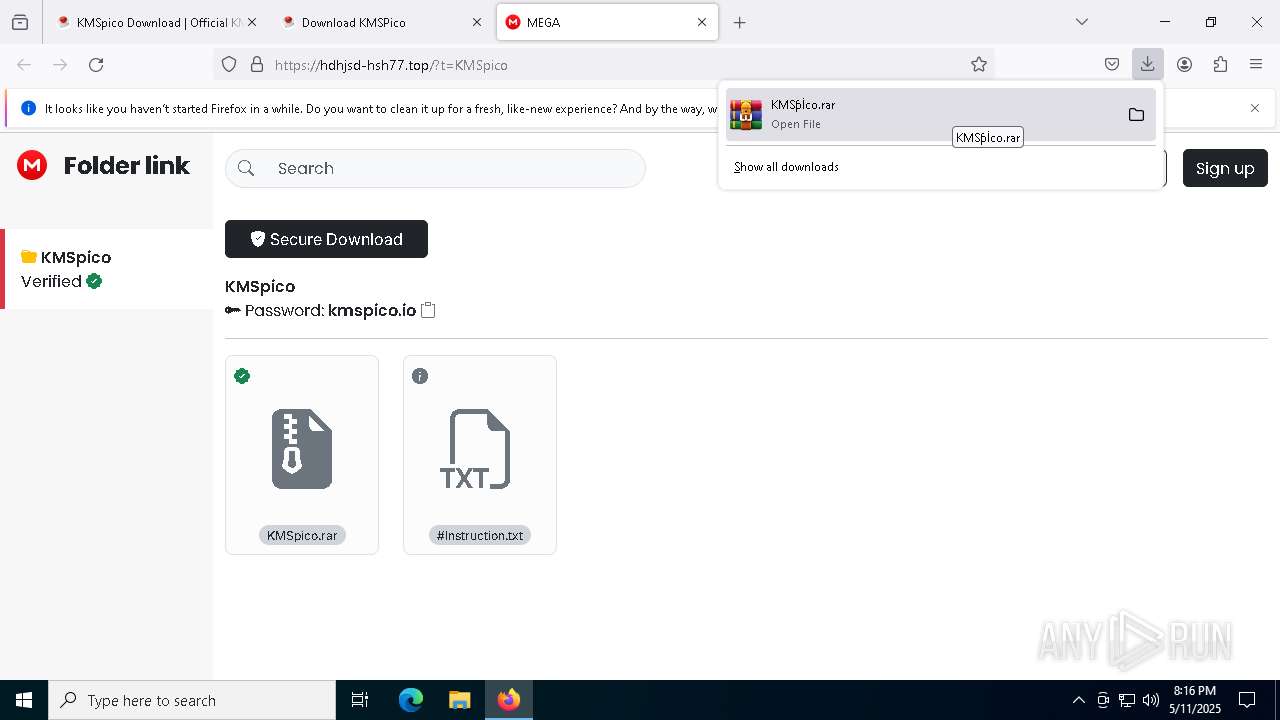
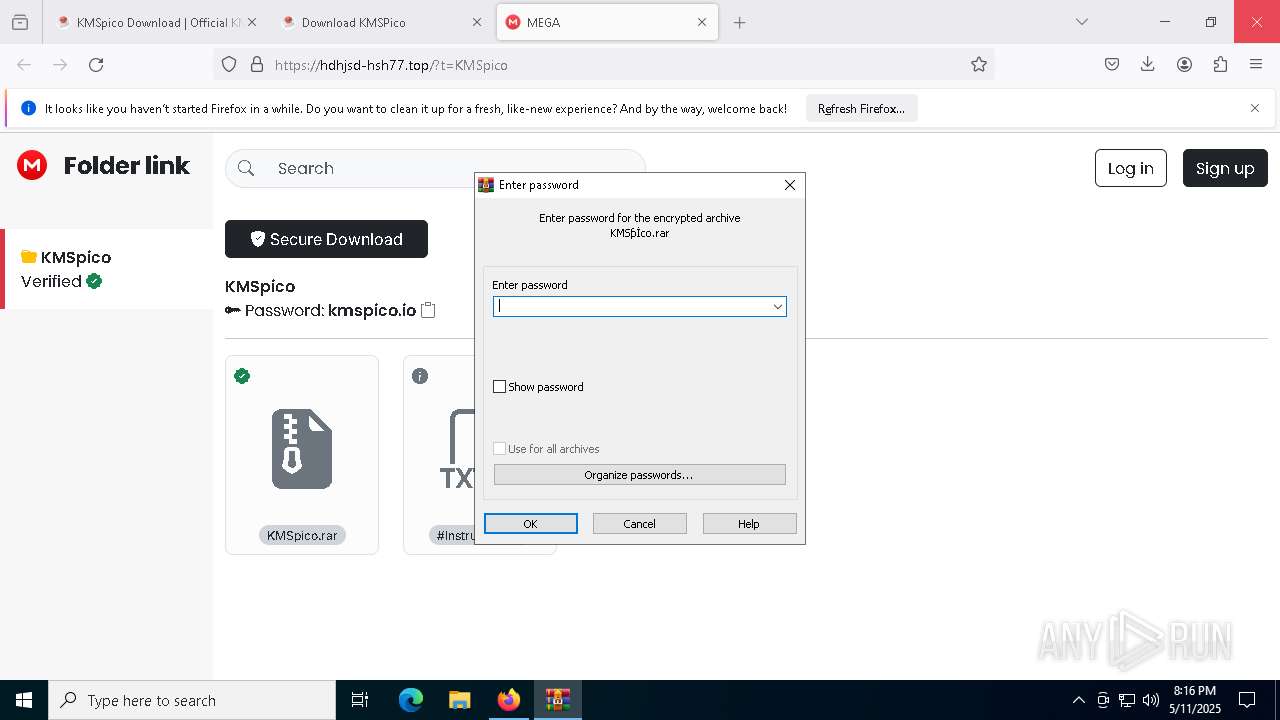
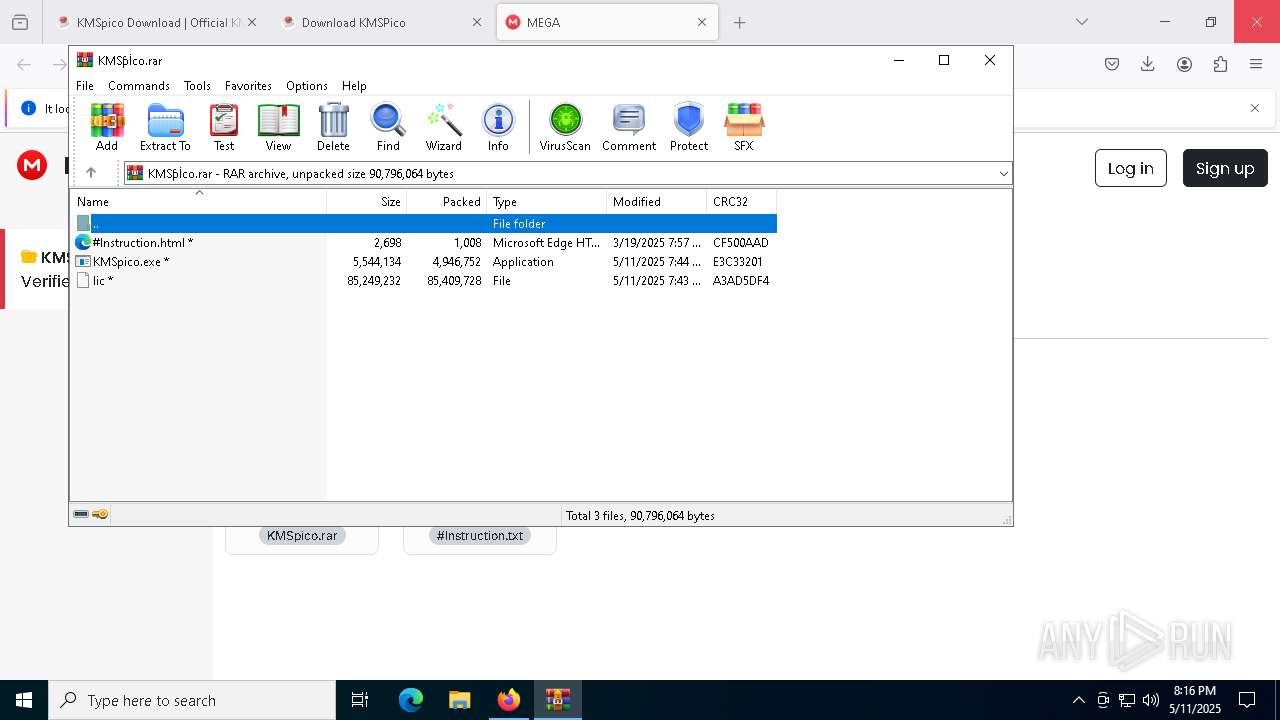
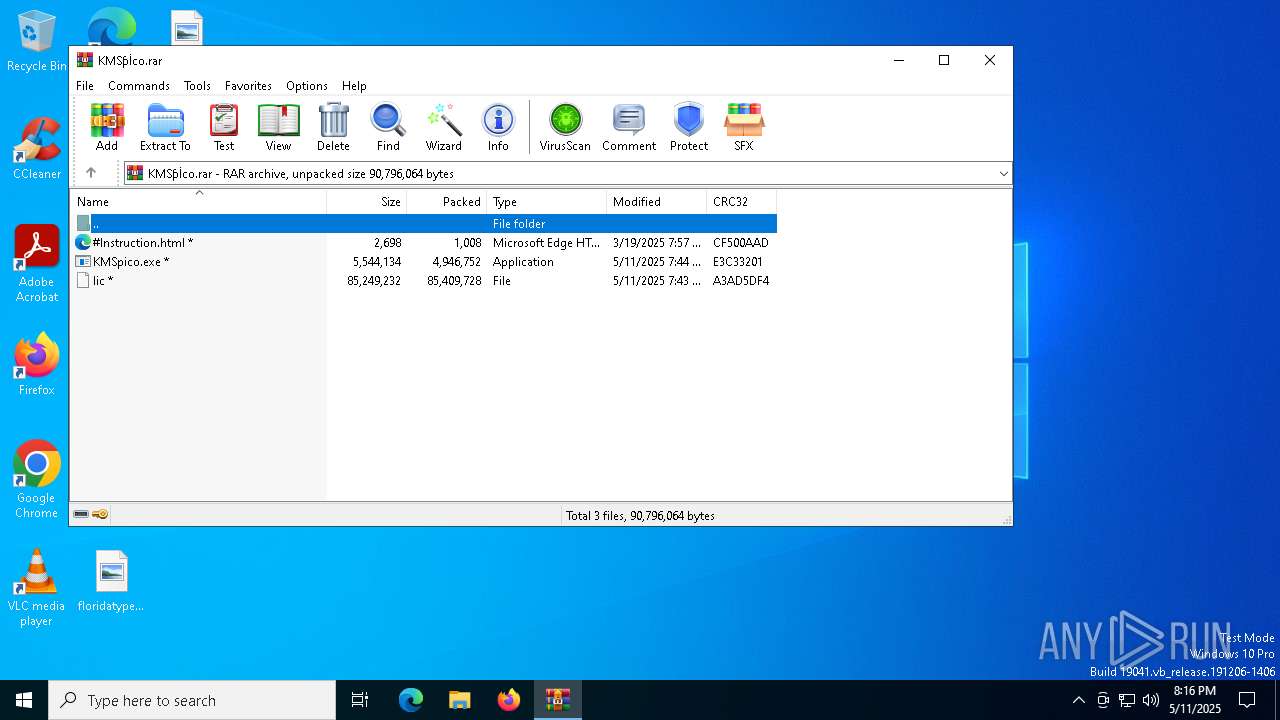
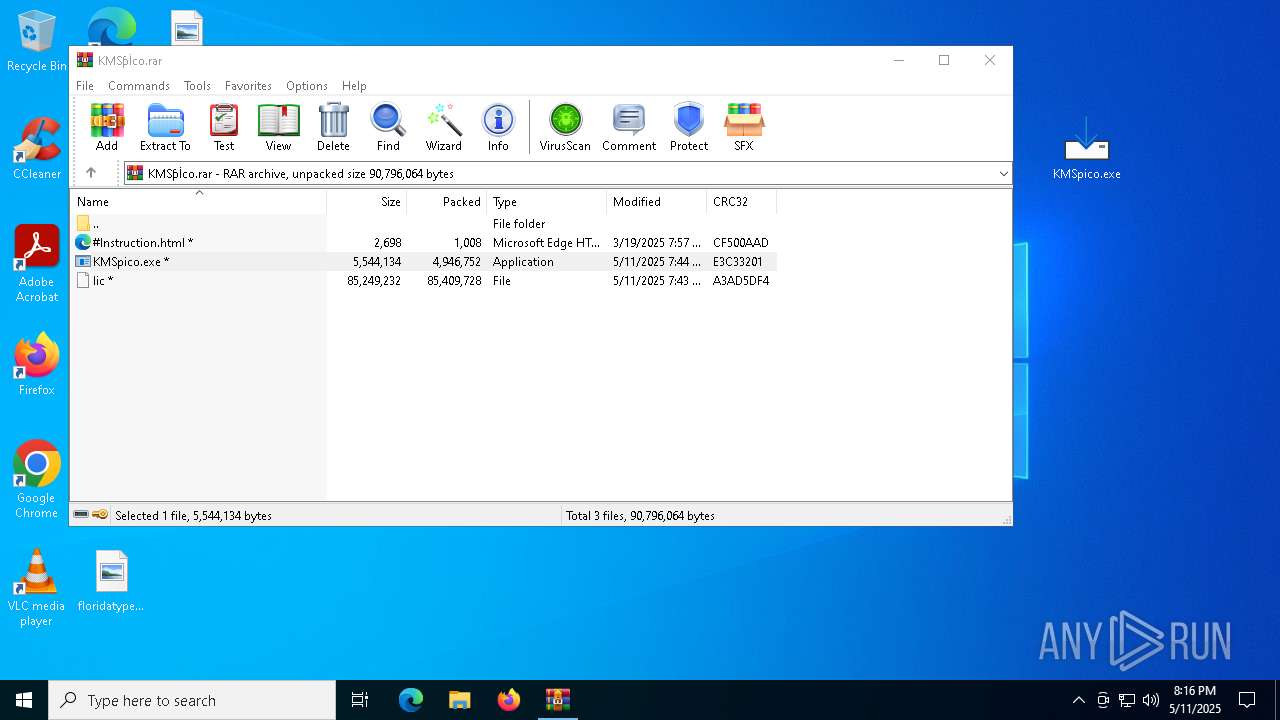
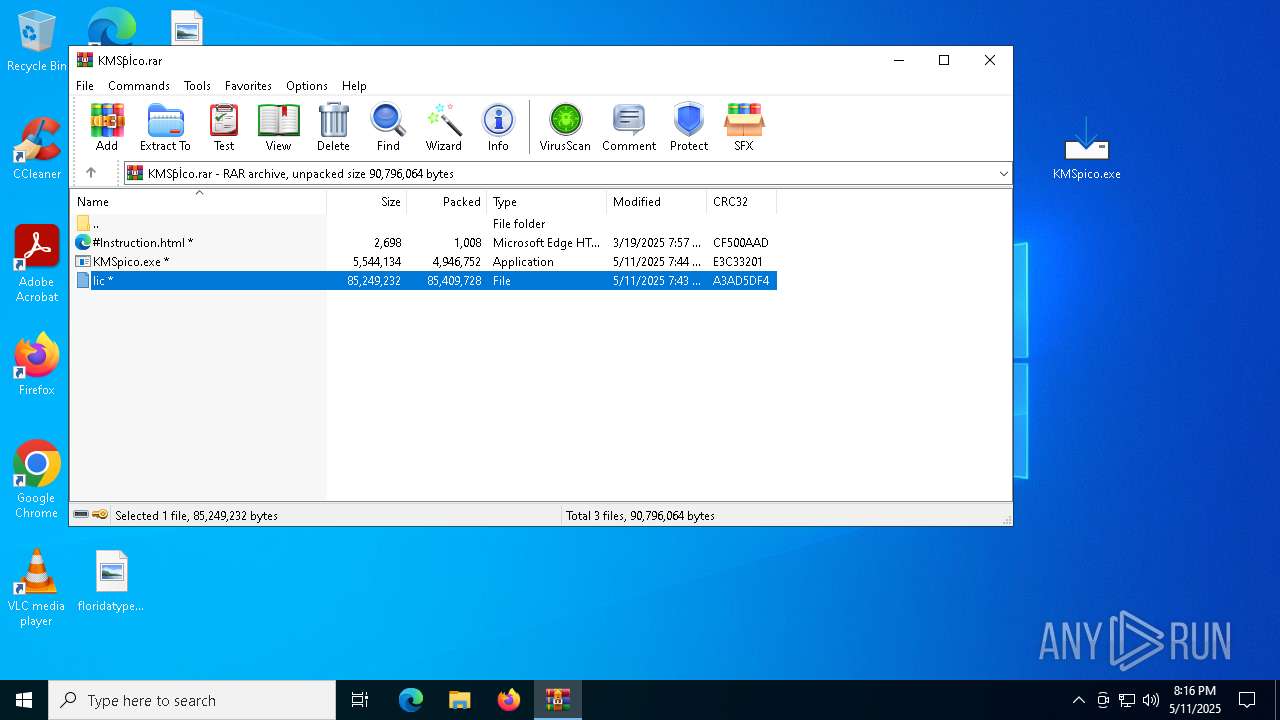
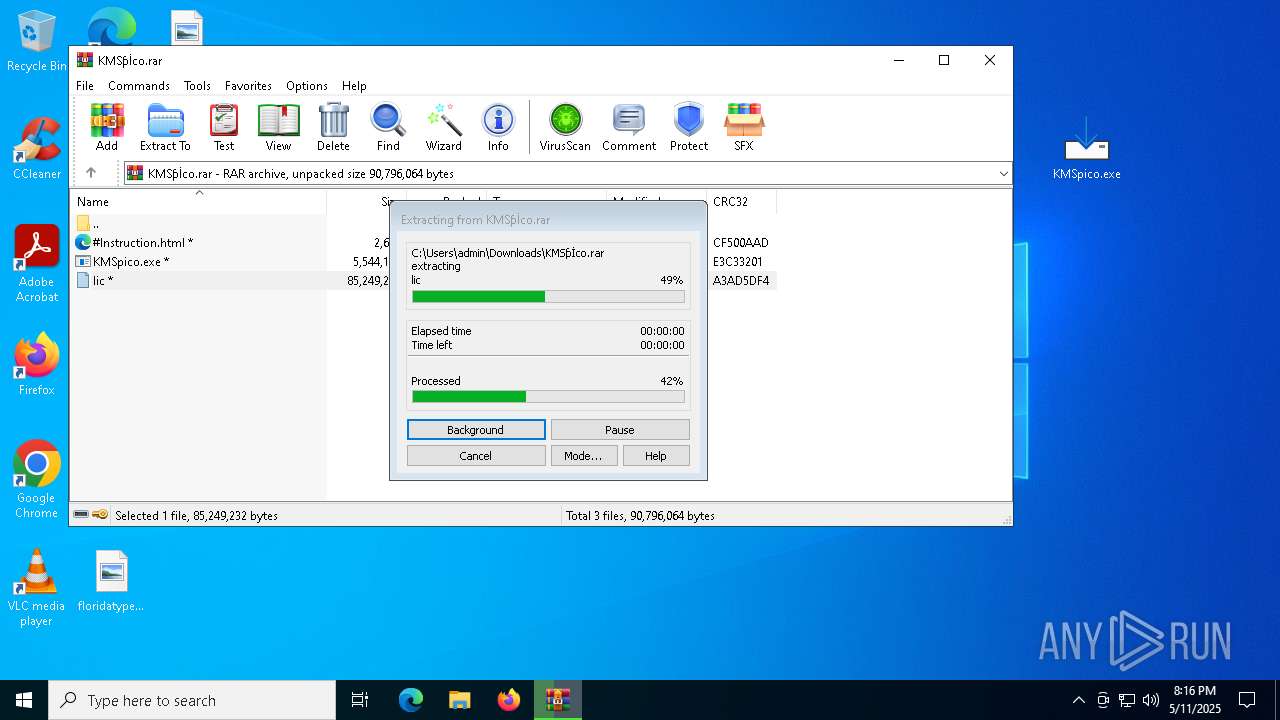
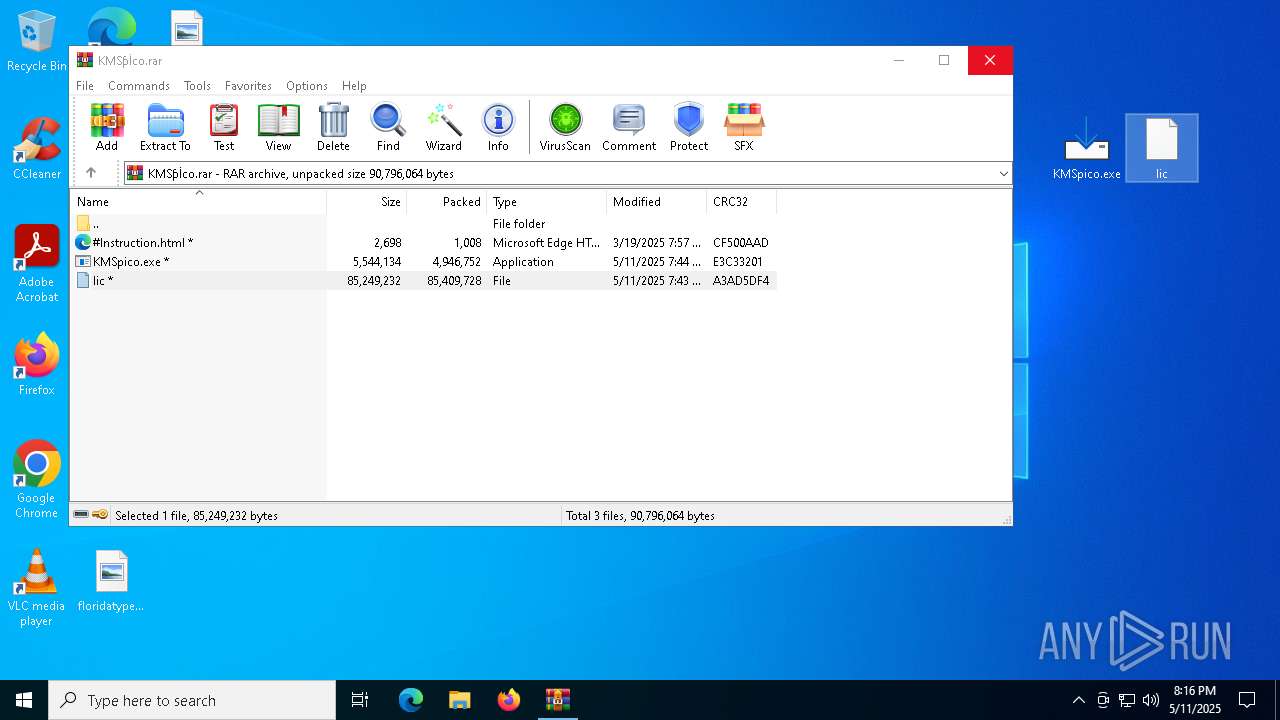
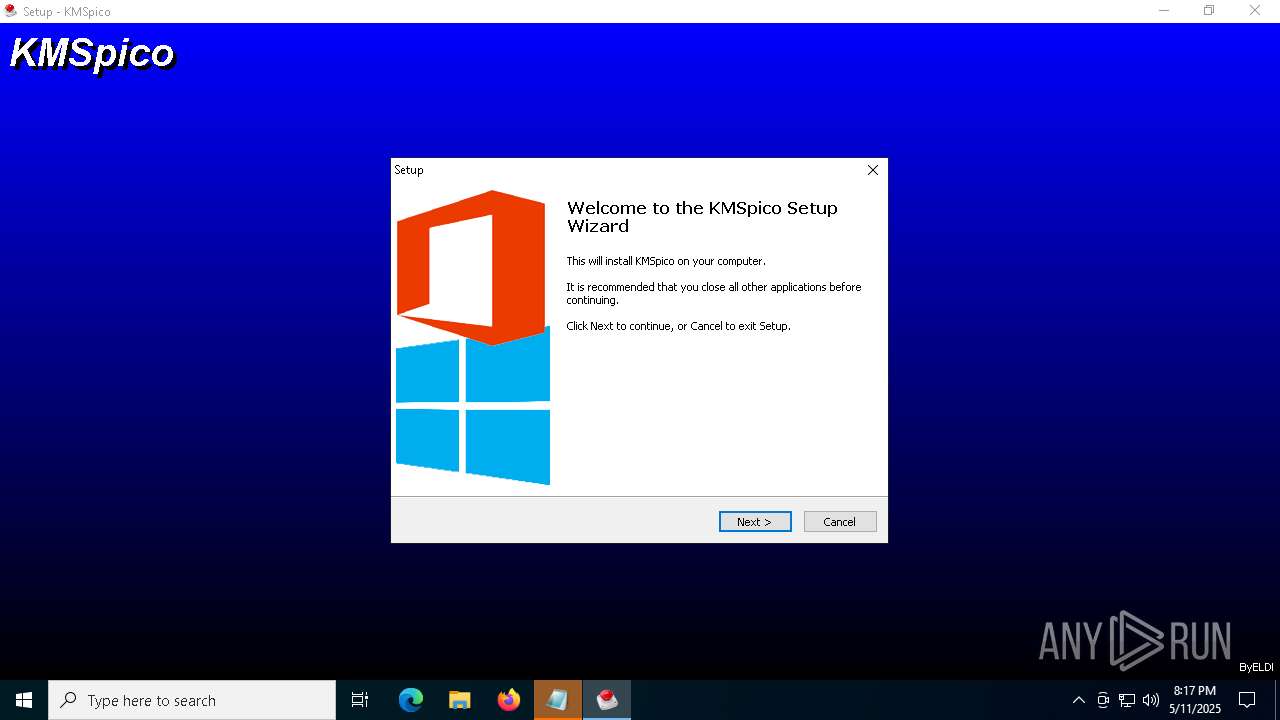
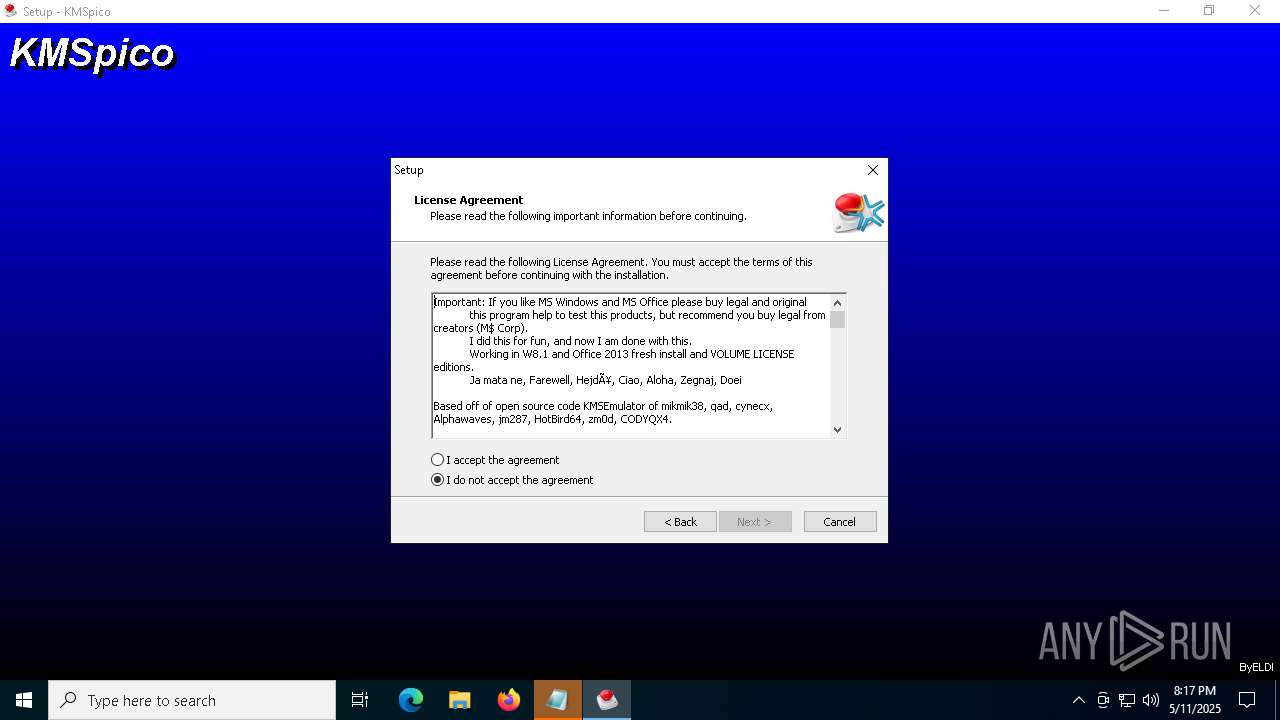
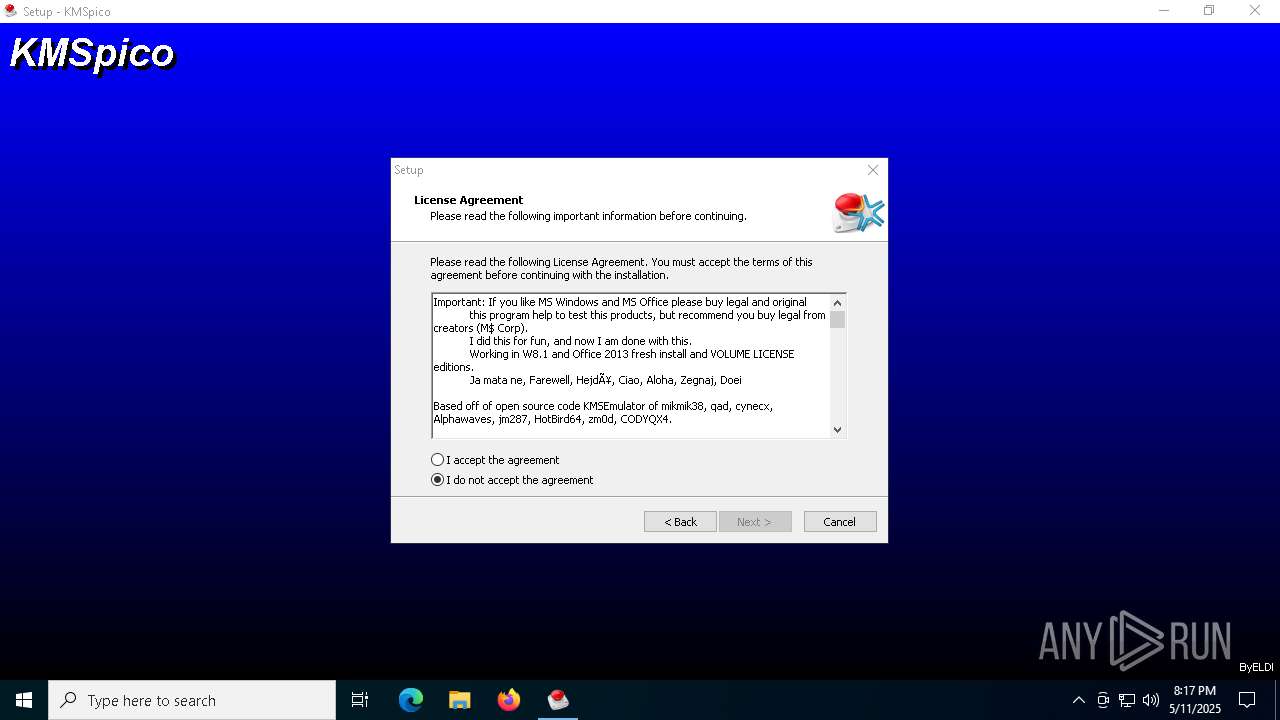
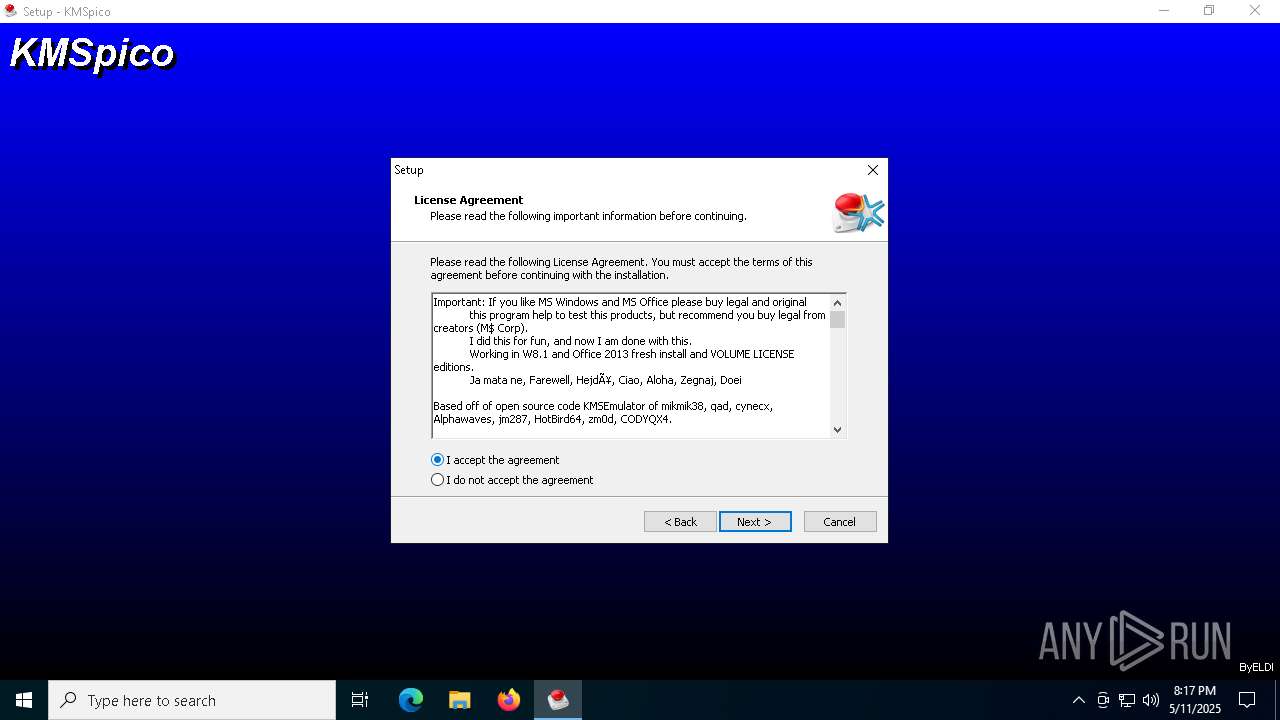
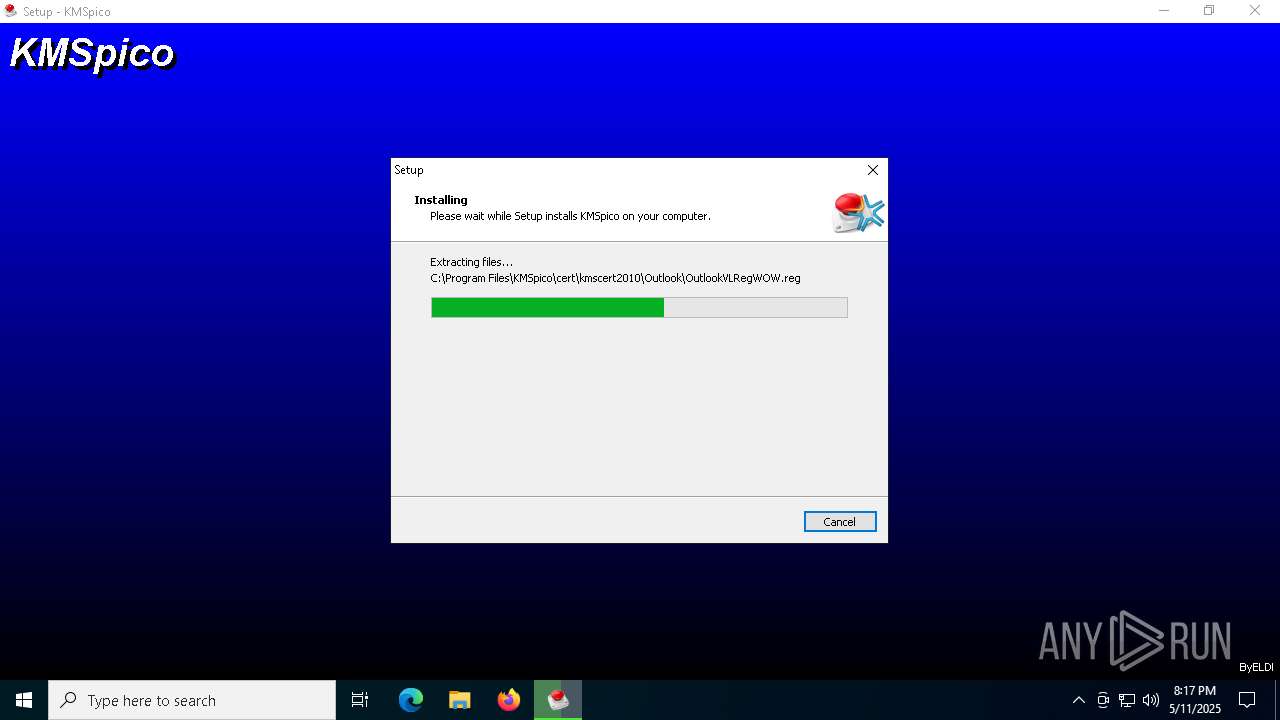
| URL: | https://kmspico.io/ |
| Full analysis: | https://app.any.run/tasks/26216955-25b7-4c85-84c0-8f9ceb6b5d36 |
| Verdict: | Malicious activity |
| Analysis date: | May 11, 2025, 20:15:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
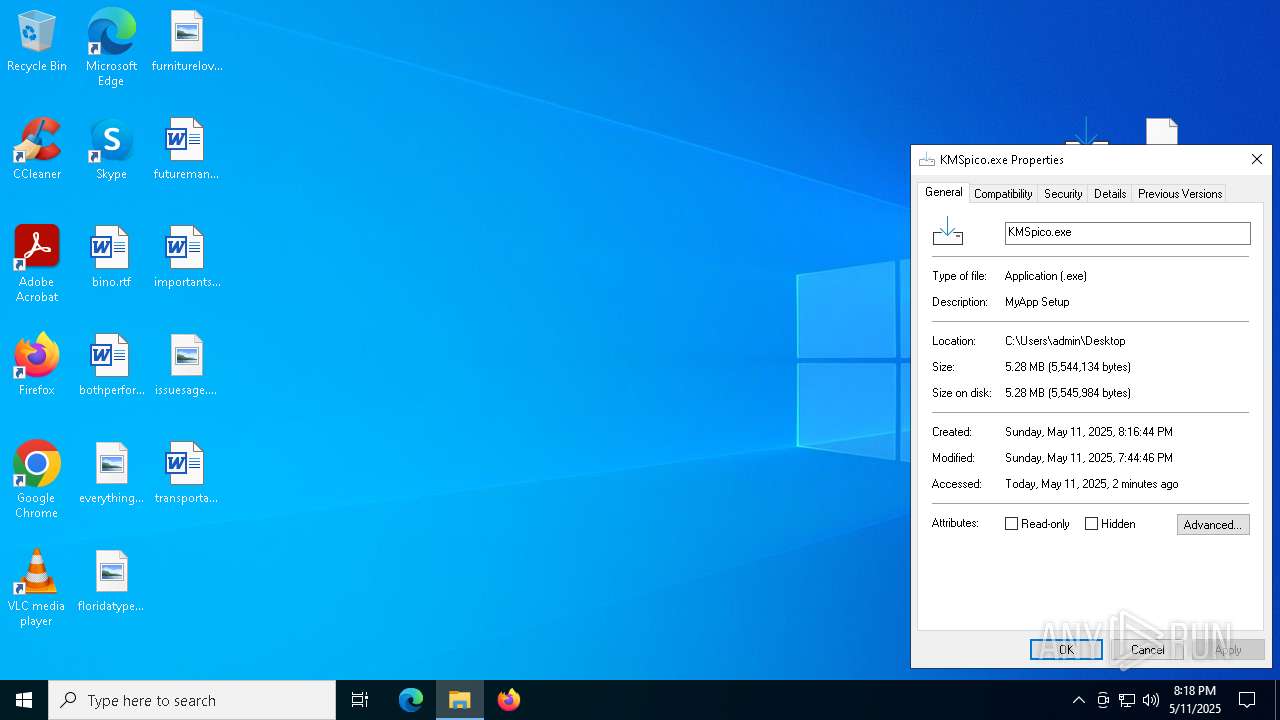
| MD5: | EFF322499A6DC1C2A439874DC93541A6 |
| SHA1: | C53ABAFB84B7A2FC0CD9EBC363346F9EF06BEADB |
| SHA256: | 1E2A39CD89239D282E8C4600F88A0C88E89487619655E62341DE25B81A44DB32 |
| SSDEEP: | 3:N8N/JKn:2dEn |
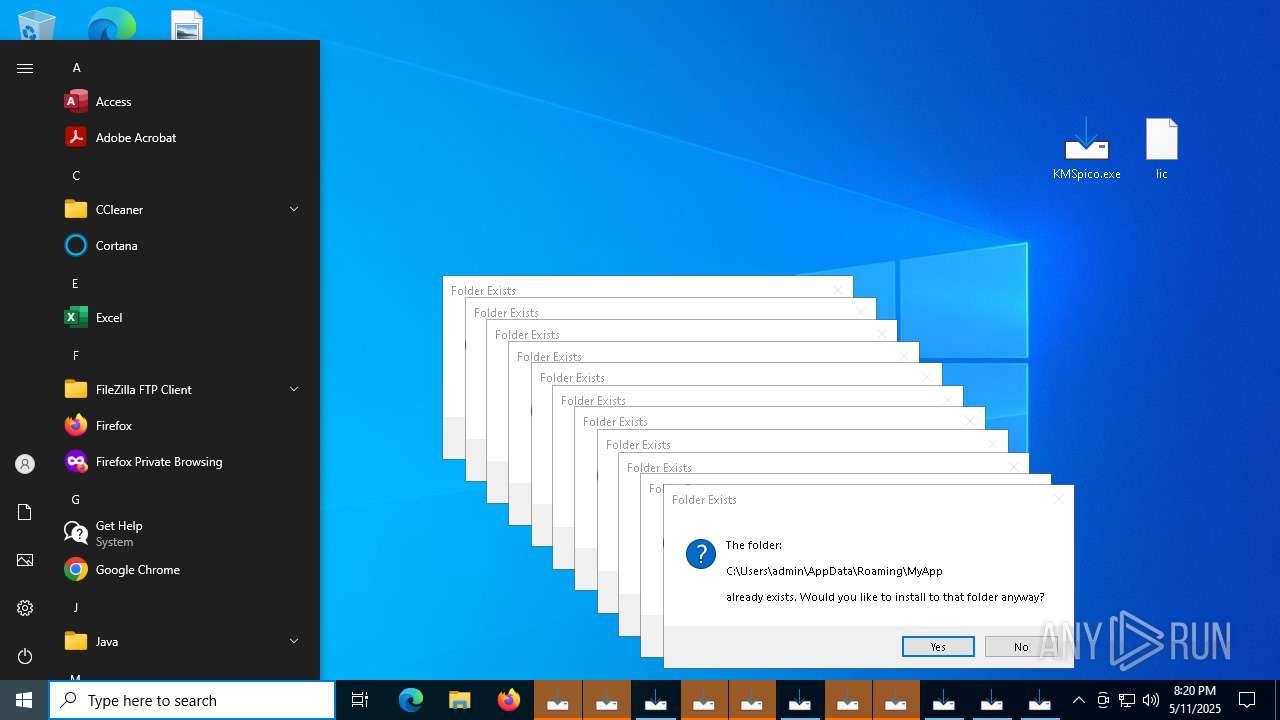
MALICIOUS
Connects to the CnC server
- firefox.exe (PID: 4880)
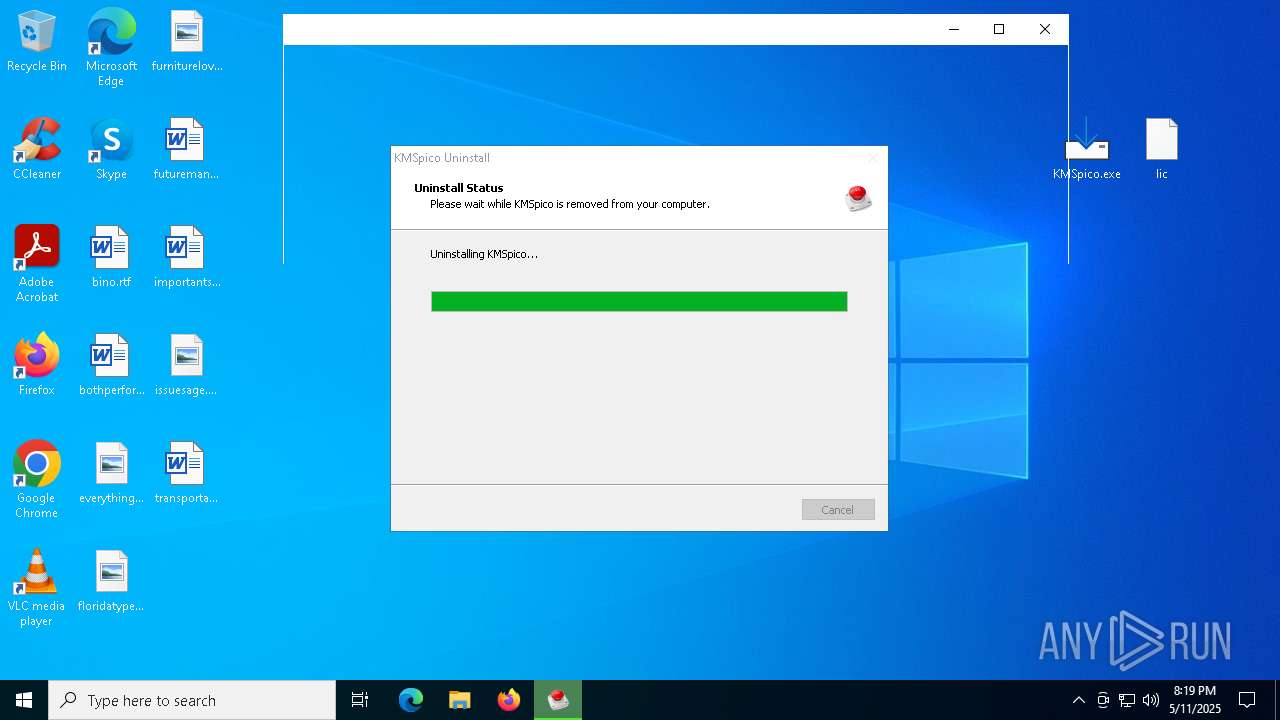
GENERIC has been found (auto)
- KMSpico.tmp (PID: 5212)
- KMSpico.tmp (PID: 6264)
- KMSpico.tmp (PID: 7104)
Executing a file with an untrusted certificate
- KMSpico.exe (PID: 8004)
- core.exe (PID: 6268)
- KMSpico.exe (PID: 5588)
- KMSELDI.exe (PID: 7372)
- AutoPico.exe (PID: 5084)
- KMSpico.exe (PID: 2840)
- KMSpico.exe (PID: 6476)
- core.exe (PID: 5936)
- KMSpico.exe (PID: 924)
- core.exe (PID: 7904)
- KMSpico.exe (PID: 1240)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7716)
SUSPICIOUS
Executable content was dropped or overwritten
- KMSpico.exe (PID: 208)
- KMSpico.tmp (PID: 5212)
- KMSpico.exe (PID: 8004)
- KMSpico.exe (PID: 5588)
- KMSpico.tmp (PID: 5452)
- KMSELDI.exe (PID: 7372)
- unins000.exe (PID: 7716)
- KMSpico.exe (PID: 4408)
- _iu14D2N.tmp (PID: 8008)
- KMSpico.tmp (PID: 7608)
- KMSpico.exe (PID: 960)
- KMSpico.tmp (PID: 7372)
- KMSpico.exe (PID: 7672)
- KMSpico.exe (PID: 5136)
- KMSpico.tmp (PID: 5744)
- KMSpico.exe (PID: 8044)
- KMSpico.tmp (PID: 5172)
- KMSpico.exe (PID: 5556)
- KMSpico.tmp (PID: 1196)
- KMSpico.tmp (PID: 5364)
- KMSpico.exe (PID: 4284)
- KMSpico.exe (PID: 1764)
- KMSpico.tmp (PID: 8080)
- KMSpico.exe (PID: 2084)
- KMSpico.exe (PID: 4000)
- KMSpico.tmp (PID: 7668)
- KMSpico.tmp (PID: 7104)
- KMSpico.tmp (PID: 6264)
- KMSpico.exe (PID: 6944)
- KMSpico.exe (PID: 924)
- KMSpico.exe (PID: 6476)
- KMSpico.exe (PID: 1240)
- KMSpico.tmp (PID: 4188)
- KMSpico.exe (PID: 2840)
- KMSpico.tmp (PID: 6676)
- KMSpico.tmp (PID: 6852)
Reads the Windows owner or organization settings
- KMSpico.tmp (PID: 5212)
Reads security settings of Internet Explorer
- KMSpico.tmp (PID: 5212)
- KMSpico.tmp (PID: 1748)
Starts CMD.EXE for commands execution
- KMSpico.tmp (PID: 5452)
- _iu14D2N.tmp (PID: 8008)
Executing commands from ".cmd" file
- KMSpico.tmp (PID: 5452)
- _iu14D2N.tmp (PID: 8008)
Creates a new Windows service
- sc.exe (PID: 7456)
Starts SC.EXE for service management
- cmd.exe (PID: 7708)
- cmd.exe (PID: 680)
Connects to unusual port
- KMSELDI.exe (PID: 7372)
Process drops legitimate windows executable
- KMSpico.tmp (PID: 5452)
- _iu14D2N.tmp (PID: 8008)
- KMSpico.tmp (PID: 6264)
- KMSpico.tmp (PID: 7104)
- KMSpico.tmp (PID: 4188)
- KMSpico.tmp (PID: 6676)
Stops a currently running service
- sc.exe (PID: 7308)
- sc.exe (PID: 7524)
Windows service management via SC.EXE
- sc.exe (PID: 7348)
- sc.exe (PID: 2088)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 7584)
- schtasks.exe (PID: 6800)
Starts application with an unusual extension
- unins000.exe (PID: 7716)
Starts itself from another location
- unins000.exe (PID: 7716)
INFO
Application launched itself
- firefox.exe (PID: 4880)
- firefox.exe (PID: 4300)
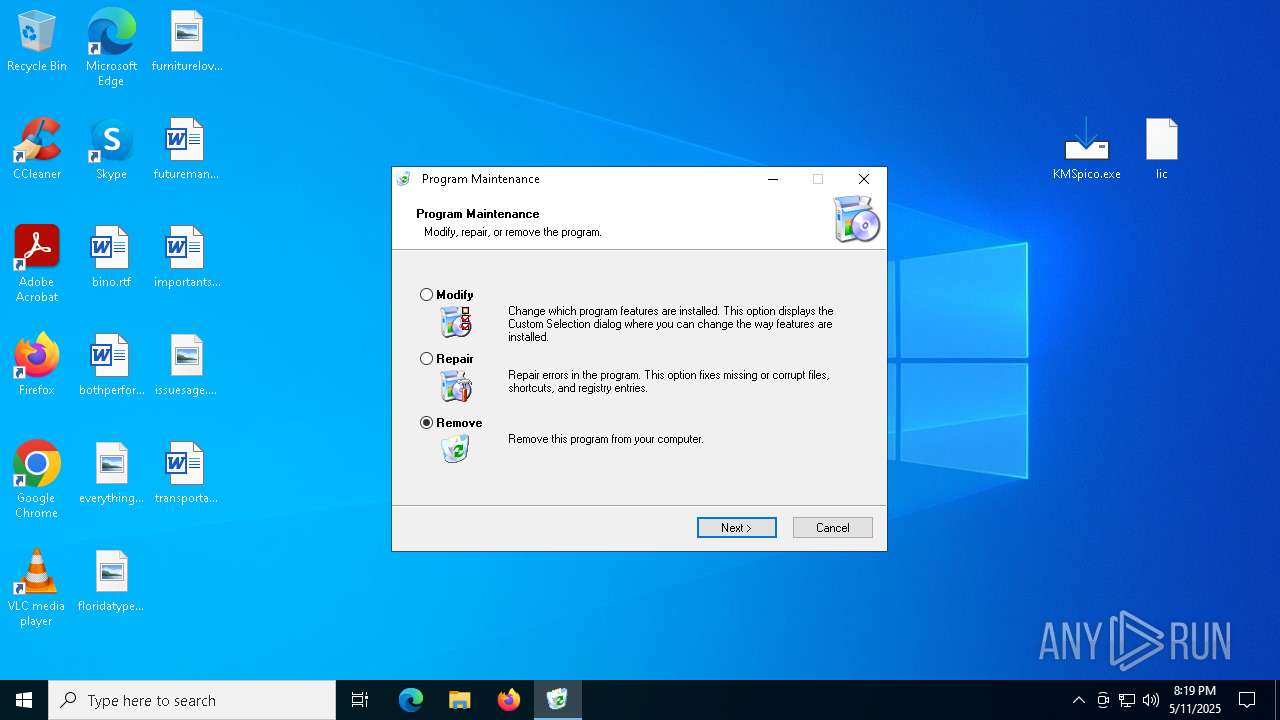
Manual execution by a user
- WinRAR.exe (PID: 5164)
- KMSpico.exe (PID: 208)
- UninsHs.exe (PID: 7424)
- UninsHs.exe (PID: 2596)
- KMSpico.exe (PID: 4408)
- KMSpico.exe (PID: 960)
- KMSpico.exe (PID: 7672)
- KMSpico.exe (PID: 5136)
- KMSpico.exe (PID: 8044)
- KMSpico.exe (PID: 4000)
- KMSpico.exe (PID: 5556)
- KMSpico.exe (PID: 2084)
- KMSpico.exe (PID: 1764)
- KMSpico.exe (PID: 4284)
- KMSpico.exe (PID: 6944)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1388)
- OpenWith.exe (PID: 5436)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5164)
Reads the software policy settings
- slui.exe (PID: 8184)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5436)
Checks supported languages
- KMSpico.exe (PID: 208)
- KMSpico.tmp (PID: 5212)
- KMSpico.exe (PID: 8004)
- core.exe (PID: 6268)
- KMSpico.tmp (PID: 1748)
- KMSpico.exe (PID: 5588)
Create files in a temporary directory
- KMSpico.exe (PID: 208)
- KMSpico.tmp (PID: 5212)
- KMSpico.exe (PID: 8004)
- KMSpico.exe (PID: 5588)
Reads the computer name
- KMSpico.tmp (PID: 5212)
- KMSpico.tmp (PID: 1748)
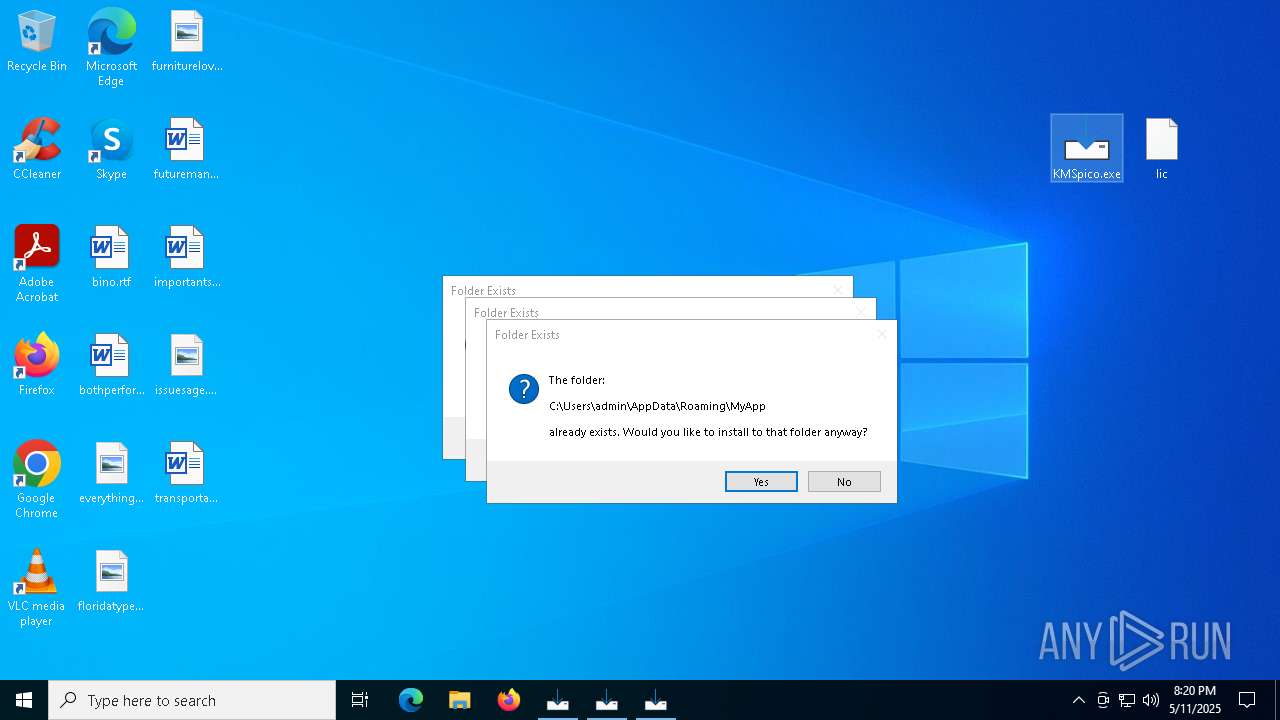
Creates files or folders in the user directory
- KMSpico.tmp (PID: 5212)
Creates a software uninstall entry
- KMSpico.tmp (PID: 5212)
Process checks computer location settings
- KMSpico.tmp (PID: 5212)
- KMSpico.tmp (PID: 1748)
Compiled with Borland Delphi (YARA)
- KMSpico.tmp (PID: 1748)
- KMSpico.tmp (PID: 5452)
Detects InnoSetup installer (YARA)
- KMSpico.exe (PID: 5588)
- KMSpico.tmp (PID: 5452)
- KMSpico.exe (PID: 8004)
- KMSpico.tmp (PID: 1748)
The sample compiled with english language support
- KMSpico.tmp (PID: 5452)
- _iu14D2N.tmp (PID: 8008)
- KMSpico.tmp (PID: 6264)
- KMSpico.tmp (PID: 7104)
- KMSpico.tmp (PID: 4188)
- KMSpico.tmp (PID: 6676)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
240
Monitored processes
93
Malicious processes
15
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
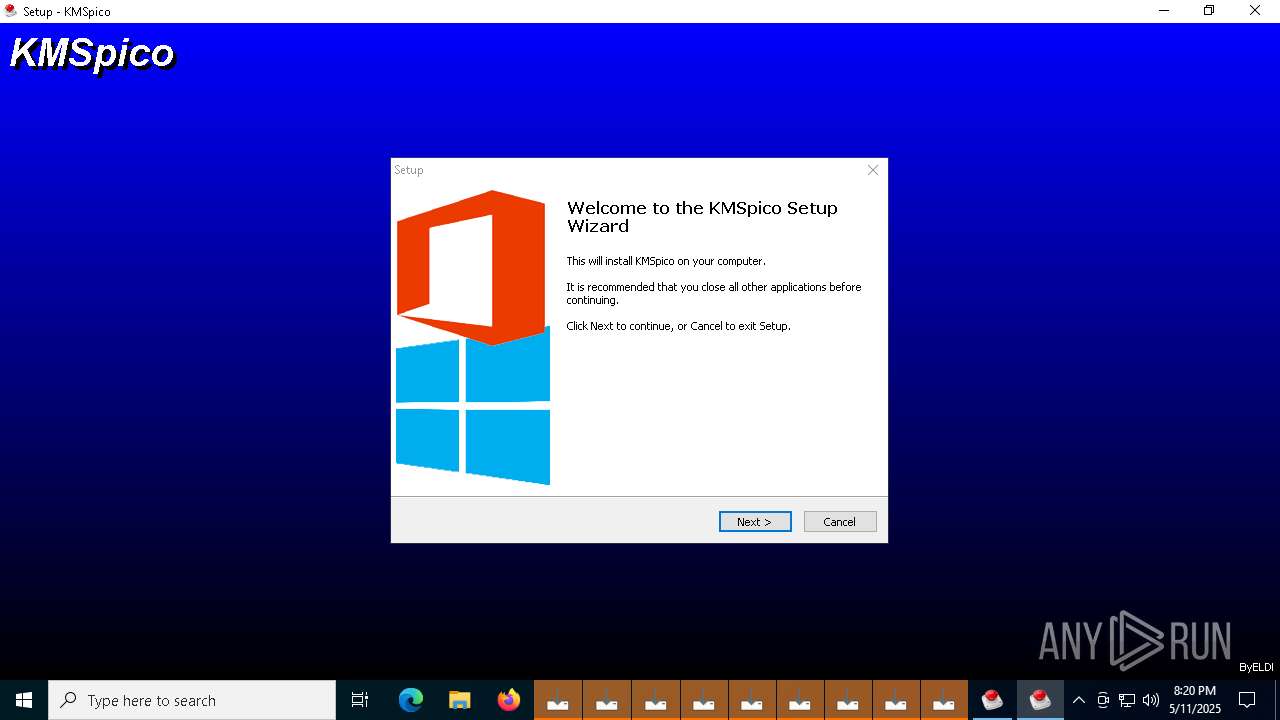
| 208 | "C:\Users\admin\Desktop\KMSpico.exe" | C:\Users\admin\Desktop\KMSpico.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: MyApp Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 680 | "C:\WINDOWS\system32\cmd.exe" /C ""C:\Program Files\KMSpico\scripts\UnInstall_Service.cmd"" | C:\Windows\System32\cmd.exe | — | _iu14D2N.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | "C:\Users\admin\AppData\Roaming\MyApp\data\KMSpico.exe" | C:\Users\admin\AppData\Roaming\MyApp\data\KMSpico.exe | KMSpico.tmp | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: KMSpico Setup Version: 10.2.0 Modules
| |||||||||||||||
| 960 | "C:\Users\admin\Desktop\KMSpico.exe" | C:\Users\admin\Desktop\KMSpico.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: MyApp Setup Version: Modules
| |||||||||||||||
| 1128 | "C:\Users\admin\AppData\Local\Temp\is-68O3T.tmp\KMSpico.tmp" /SL5="$20670,2952592,69120,C:\Users\admin\AppData\Roaming\MyApp\data\KMSpico.exe" | C:\Users\admin\AppData\Local\Temp\is-68O3T.tmp\KMSpico.tmp | — | KMSpico.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Version: 51.52.0.0 Modules
| |||||||||||||||
| 1196 | "C:\Users\admin\AppData\Local\Temp\is-8RMKN.tmp\KMSpico.tmp" /SL5="$B02D8,4576627,844800,C:\Users\admin\Desktop\KMSpico.exe" | C:\Users\admin\AppData\Local\Temp\is-8RMKN.tmp\KMSpico.tmp | KMSpico.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1240 | "C:\Users\admin\AppData\Roaming\MyApp\data\KMSpico.exe" /SPAWNWND=$2063C /NOTIFYWND=$20670 | C:\Users\admin\AppData\Roaming\MyApp\data\KMSpico.exe | KMSpico.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: KMSpico Setup Version: 10.2.0 Modules
| |||||||||||||||
| 1348 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
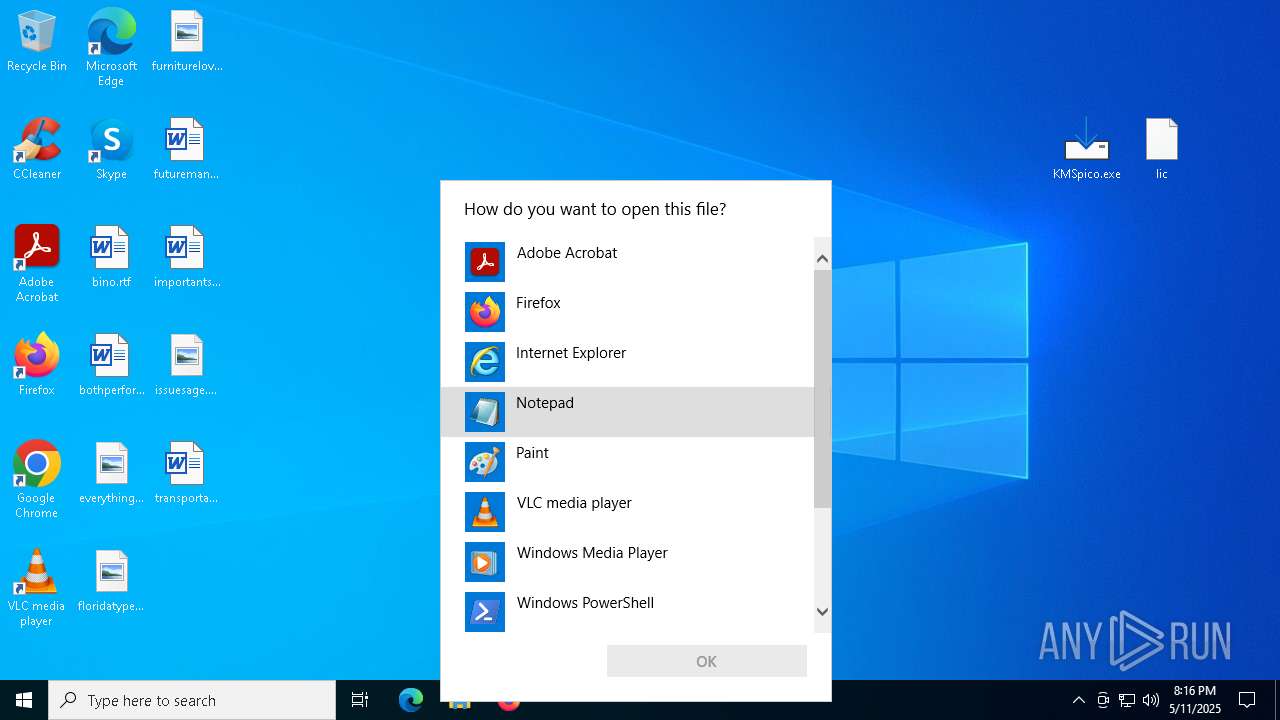
| 1388 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\lic | C:\Windows\System32\notepad.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1748 | "C:\Users\admin\AppData\Local\Temp\is-R2K5A.tmp\KMSpico.tmp" /SL5="$802C6,2952592,69120,C:\Users\admin\AppData\Roaming\MyApp\data\KMSpico.exe" | C:\Users\admin\AppData\Local\Temp\is-R2K5A.tmp\KMSpico.tmp | — | KMSpico.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
Total events
28 977
Read events
28 773
Write events
184
Delete events
20
Modification events
| (PID) Process: | (4880) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (5164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\KMSƥİco.rar | |||
| (PID) Process: | (5164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
79
Suspicious files
215
Text files
737
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4880 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 4880 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 4880 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 4880 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4880 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4880 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 4880 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4880 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 4880 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 4880 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.tmp | binary | |
MD5:F759EB25271E6A6F0A3500520813E5FE | SHA256:015E515D432DD64FDC9502ABE9C723EEF544E7AF11C36BDFE8B38412597CA1EC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
158
DNS requests
169
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.191:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4880 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
4880 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
4880 | firefox.exe | POST | 200 | 142.250.186.67:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
4880 | firefox.exe | POST | 200 | 184.24.77.83:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
4880 | firefox.exe | POST | 200 | 184.24.77.56:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
4880 | firefox.exe | POST | 200 | 184.24.77.83:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
4880 | firefox.exe | POST | 200 | 184.24.77.56:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
4880 | firefox.exe | POST | 200 | 142.250.186.67:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.191:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4880 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | — | — | whitelisted |
4880 | firefox.exe | 142.250.184.202:443 | safebrowsing.googleapis.com | — | — | whitelisted |
4880 | firefox.exe | 45.12.1.24:443 | kmspico.io | Virtual Systems LLC | UA | malicious |
4880 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
kmspico.io |
| malicious |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4880 | firefox.exe | Misc Attack | ET Threatview.io High Confidence Cobalt Strike C2 IP group 13 |
4880 | firefox.exe | Misc Attack | ET Threatview.io High Confidence Cobalt Strike C2 IP group 12 |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |