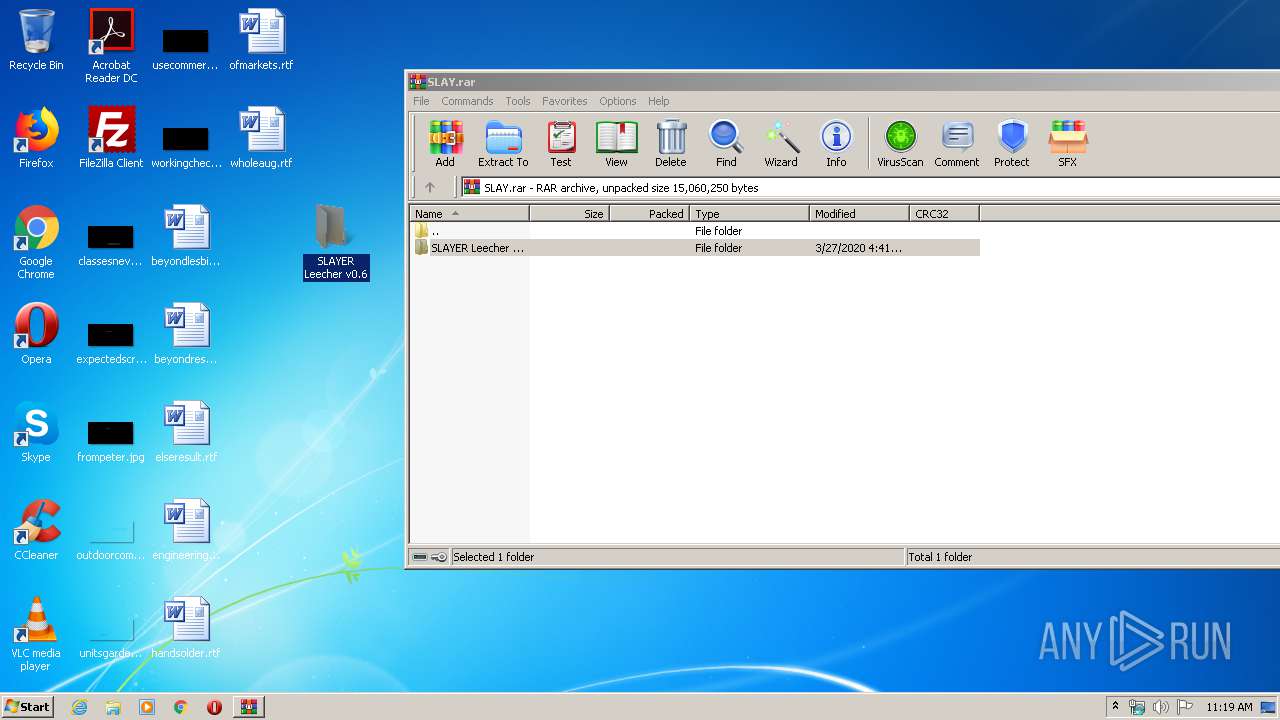
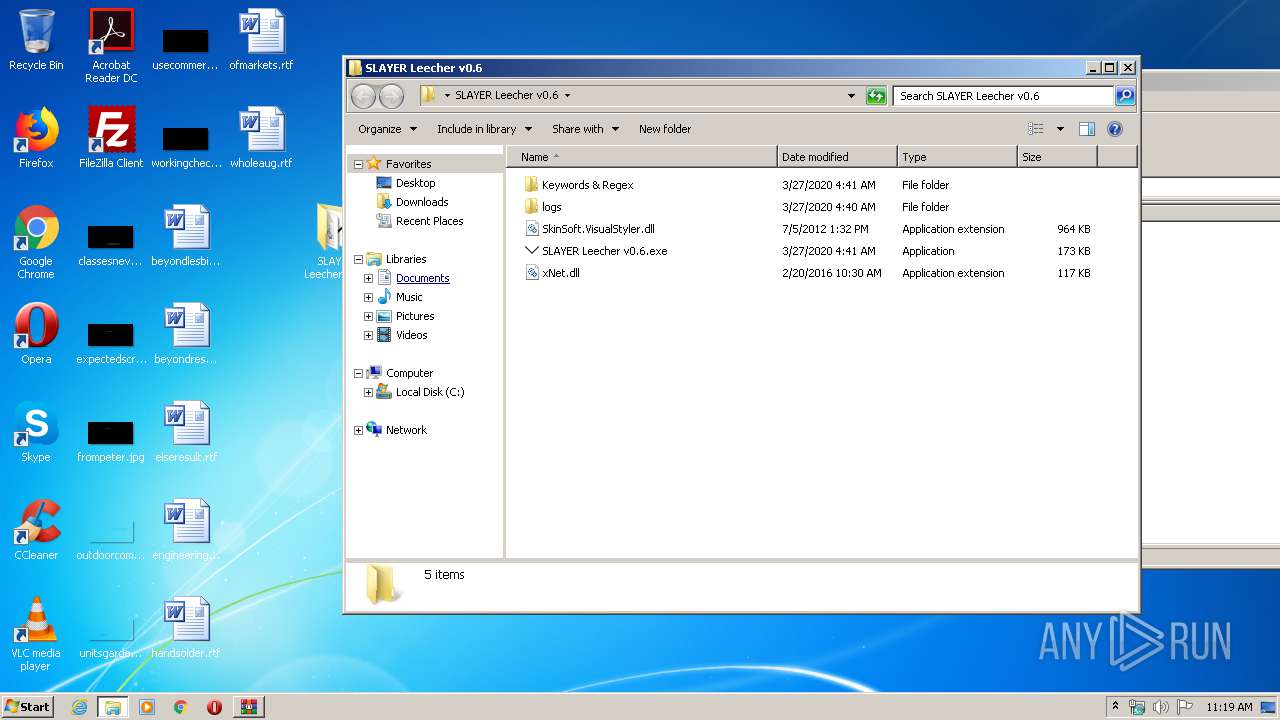
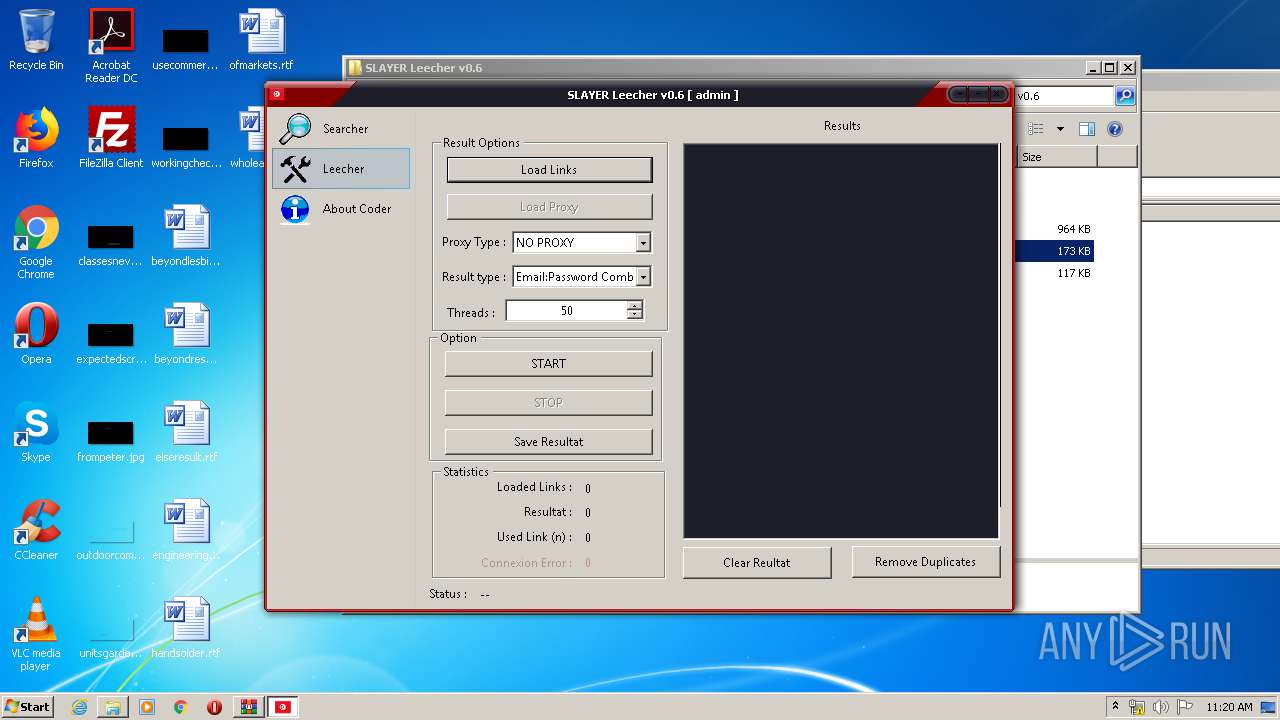
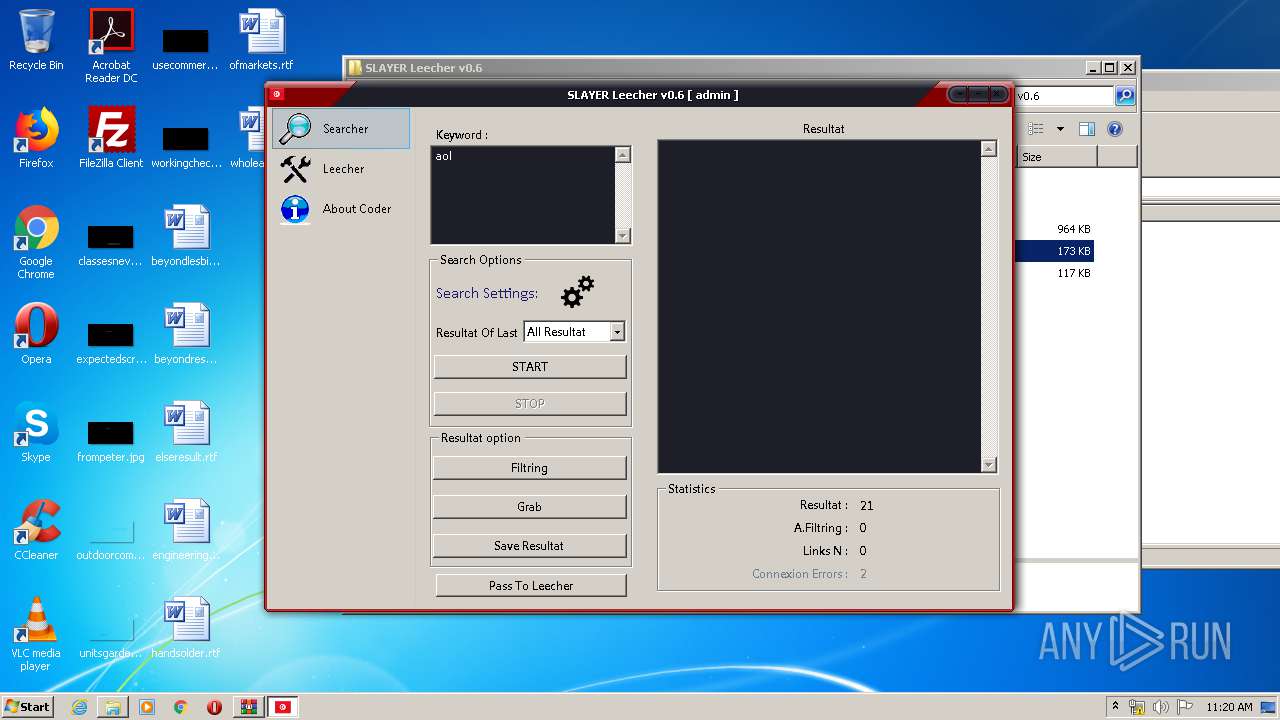
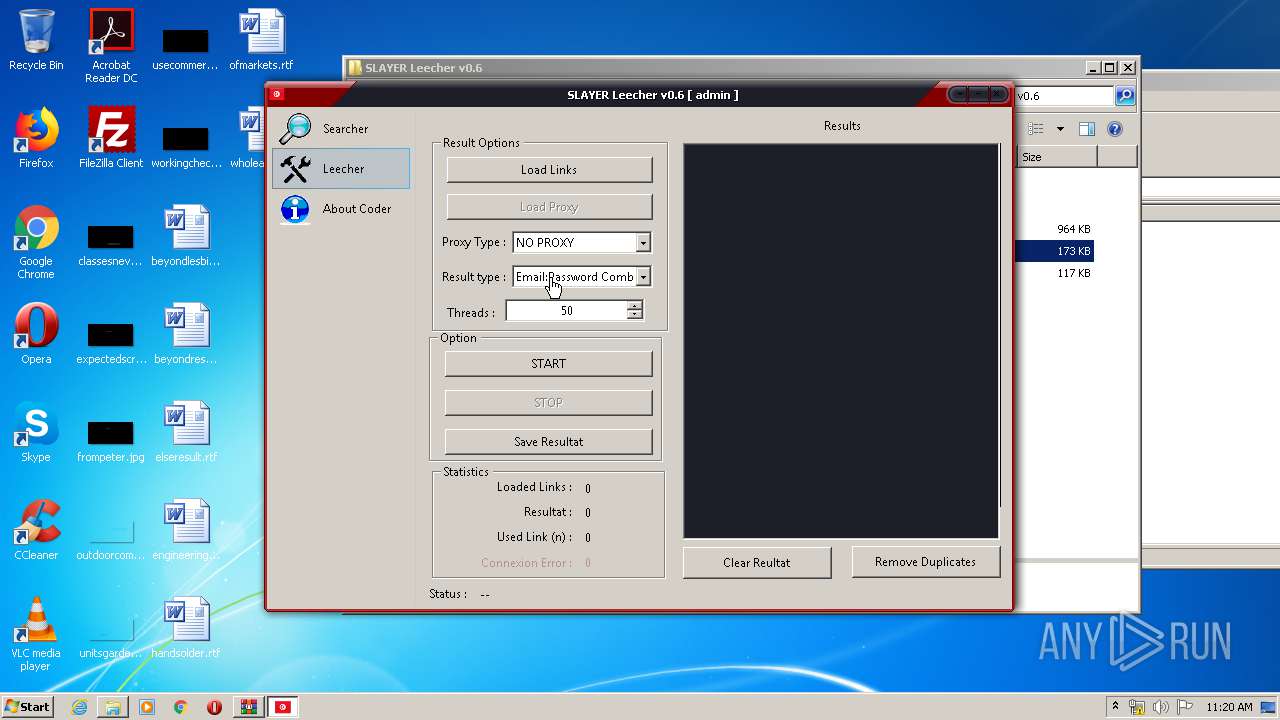
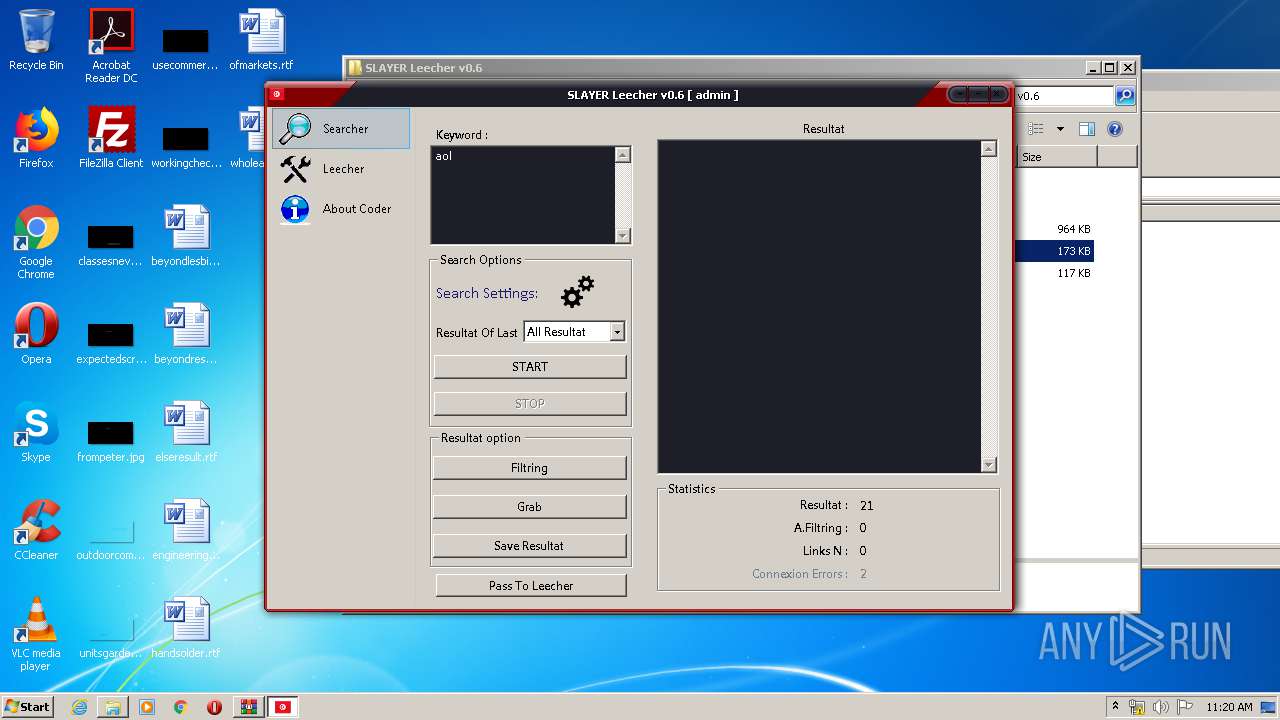
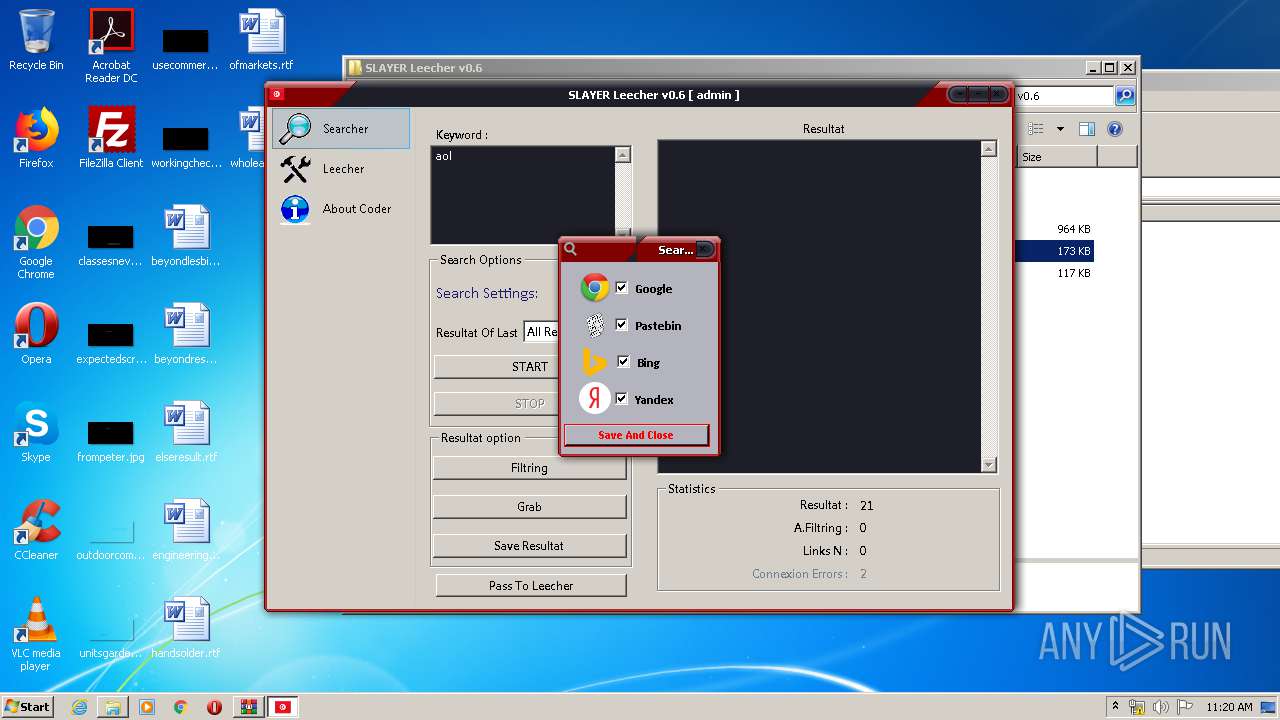
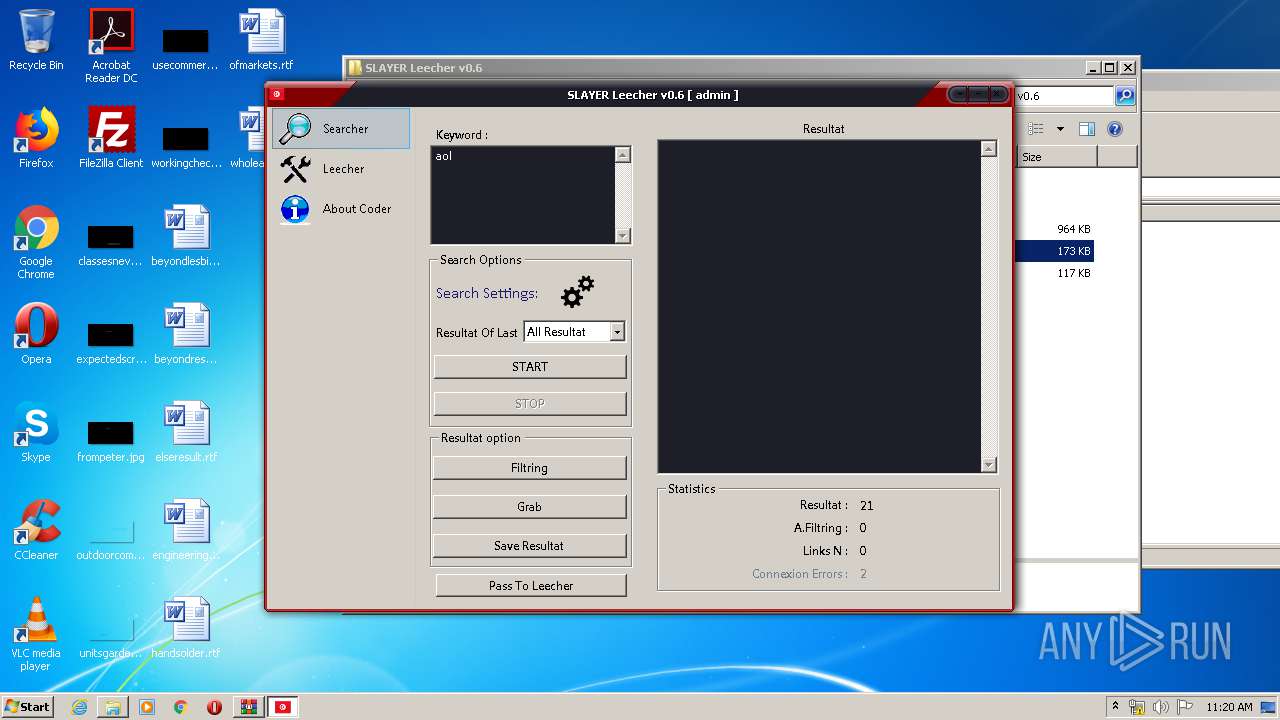
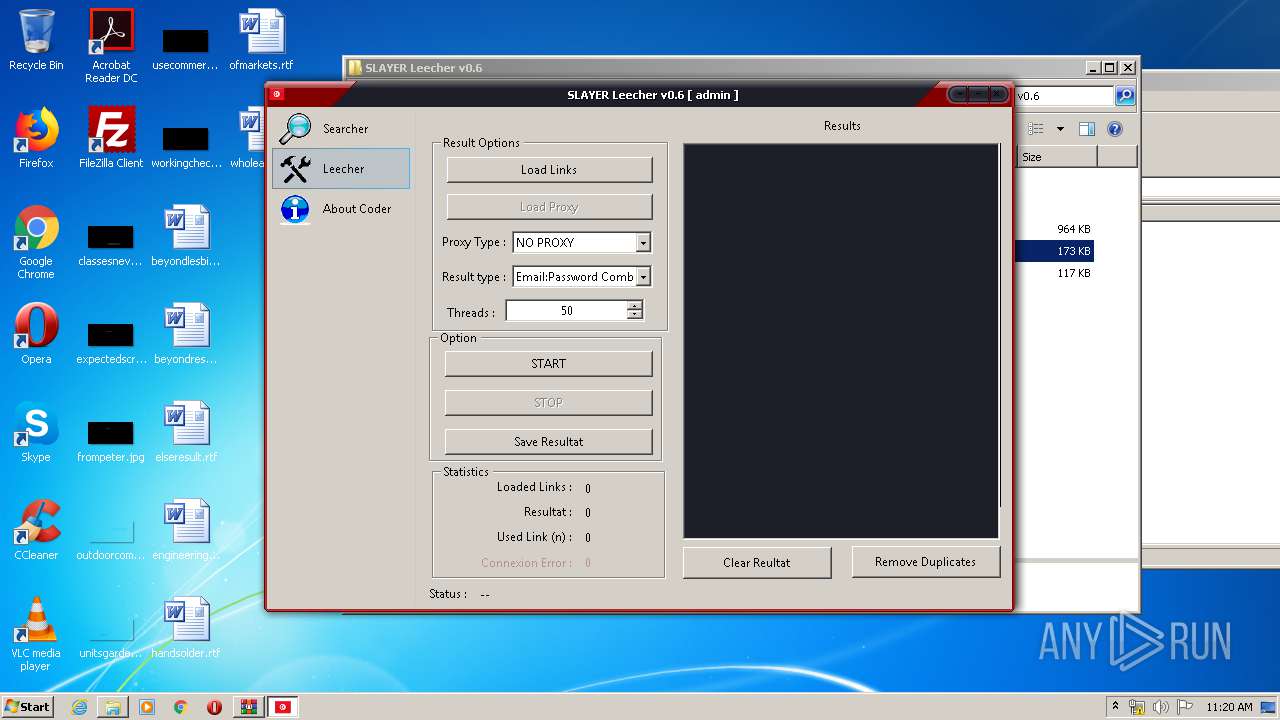
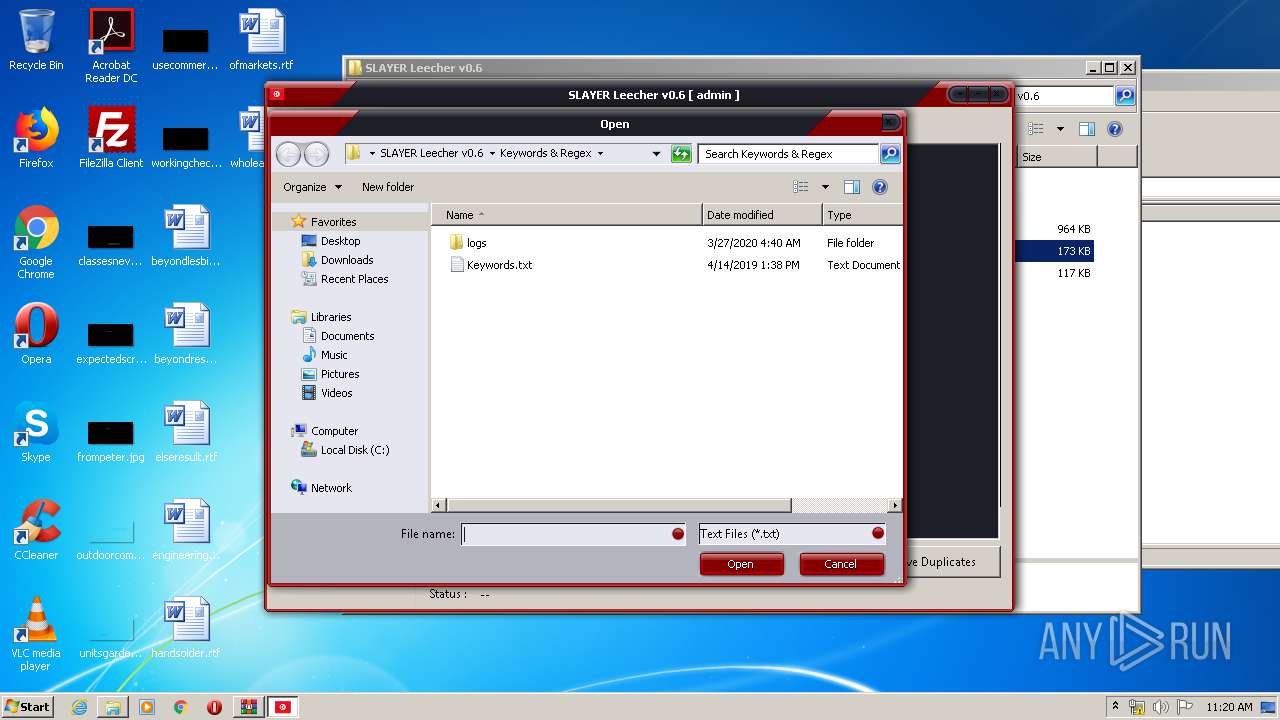
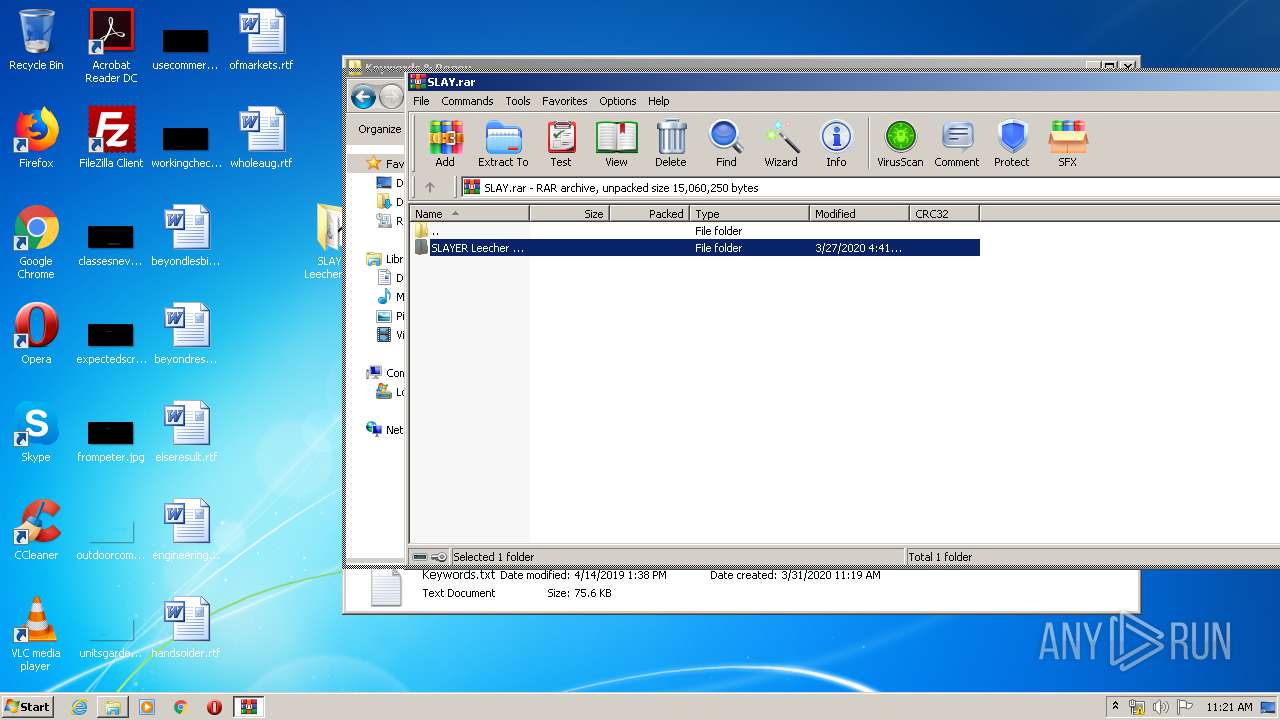
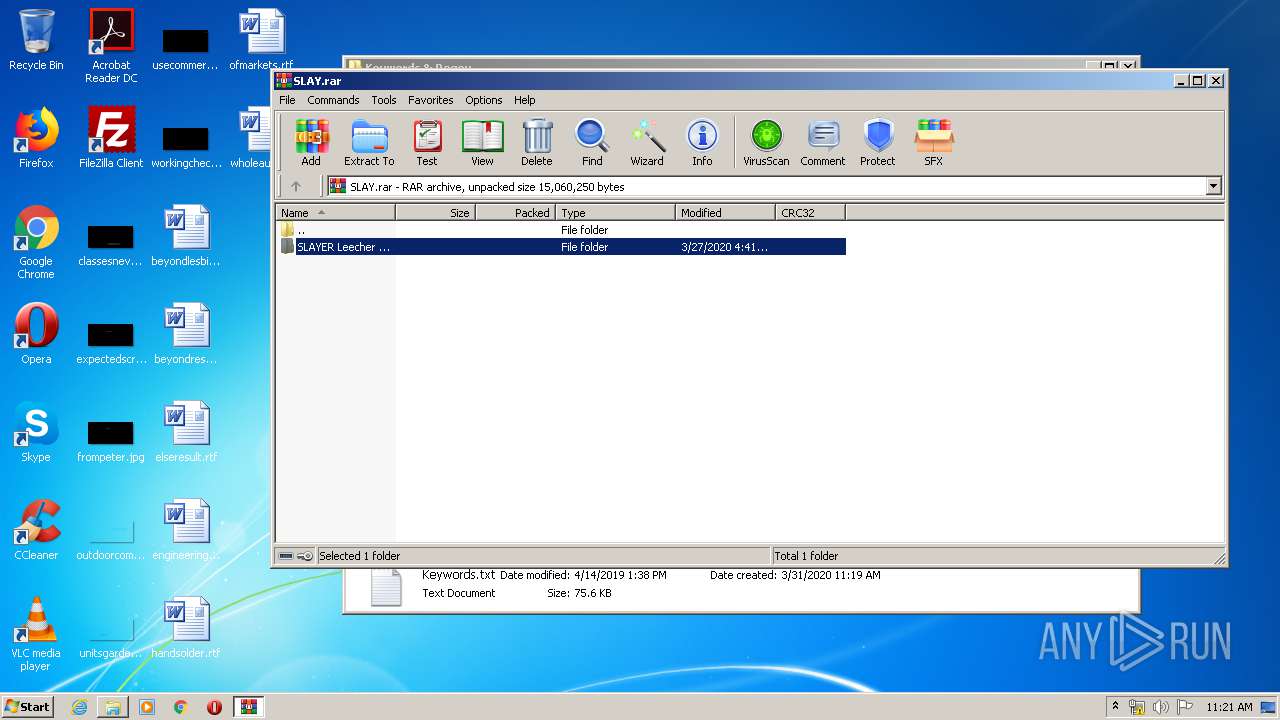
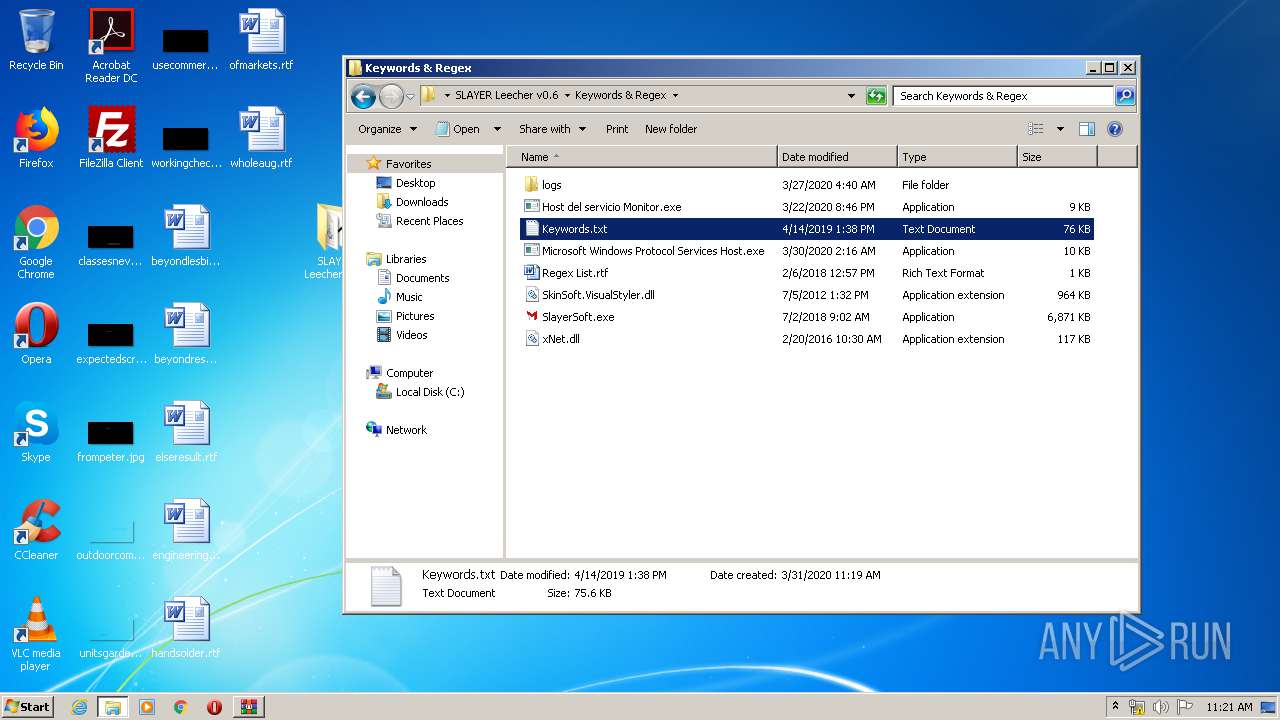
| File name: | SLAY.rar |
| Full analysis: | https://app.any.run/tasks/1d4b9ec7-196e-46a1-a7bd-80b860e5ab8a |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2020, 10:18:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F6B312C7108D5B83F383573039D3A27D |
| SHA1: | ECBBE62E77883830AEEC133A15FD0D52358D8795 |
| SHA256: | 1E1E79A9FCE8278DDBF01C65A162FEEB8EFEAB7DCCF8F648ED7A310C3B637590 |
| SSDEEP: | 98304:Ze+ZJrlHWdXI7x/9gdwUd21GGkfRPM1z6PDu1ckQG6bc3wzMgw4JC5JZE3DUMe+P:ZM1IV/9gdI1GGmPMo7cNQGtgzMp4JSJW |
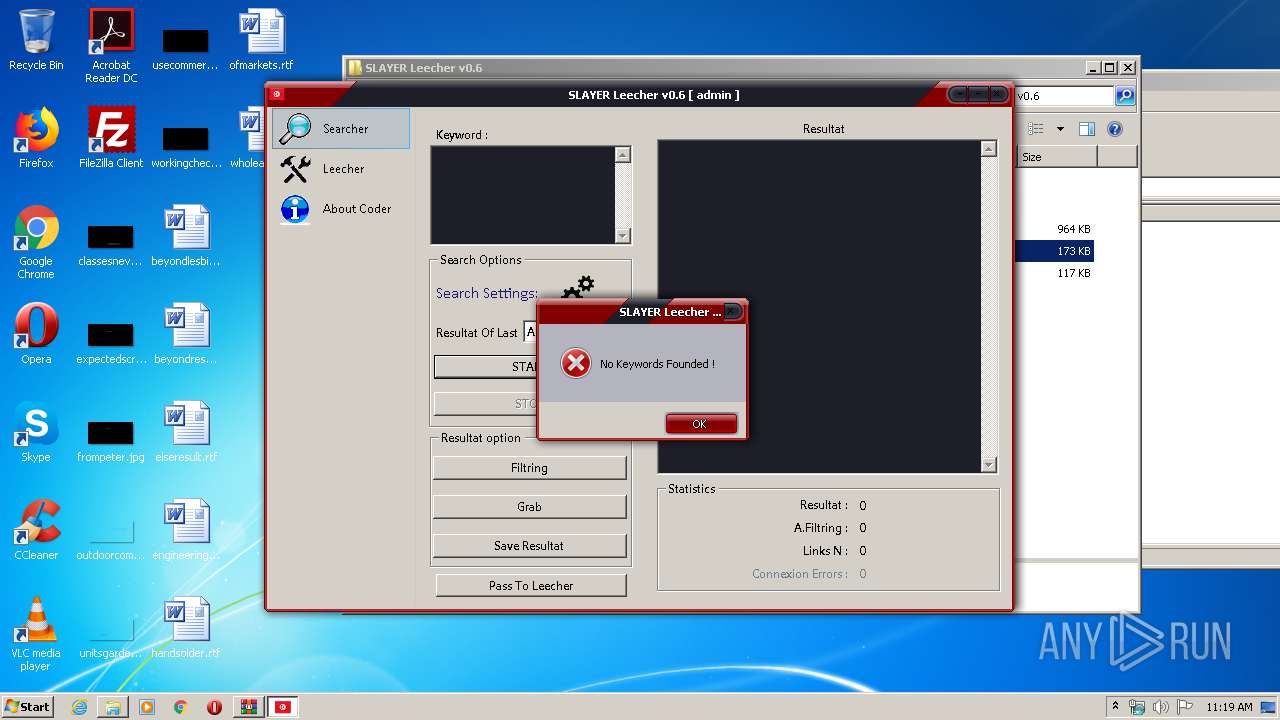
MALICIOUS
Writes to a start menu file
- SLAYER Leecher v0.6.exe (PID: 3200)
- SLAYER Leecher v0.6.exe (PID: 1944)
Application was dropped or rewritten from another process
- Host del servicio Monitor.exe (PID: 1904)
- Microsoft Windows Protocol Services Host.exe (PID: 1696)
- Microsoft Windows Protocol Services Host.exe (PID: 3144)
- Host del servicio Monitor.exe (PID: 884)
Loads dropped or rewritten executable
- SlayerSoft.exe (PID: 2576)
- SlayerSoft.exe (PID: 2944)
Changes settings of System certificates
- SlayerSoft.exe (PID: 2576)
SUSPICIOUS
Creates files in the Windows directory
- SLAYER Leecher v0.6.exe (PID: 3200)
Executable content was dropped or overwritten
- SLAYER Leecher v0.6.exe (PID: 3200)
- WinRAR.exe (PID: 1832)
- SlayerSoft.exe (PID: 2576)
Creates files in the program directory
- SLAYER Leecher v0.6.exe (PID: 3200)
Creates files in the user directory
- SLAYER Leecher v0.6.exe (PID: 3200)
Reads Environment values
- SlayerSoft.exe (PID: 2576)
- SlayerSoft.exe (PID: 2944)
Adds / modifies Windows certificates
- SlayerSoft.exe (PID: 2576)
INFO
Manual execution by user
- SLAYER Leecher v0.6.exe (PID: 3200)
- SLAYER Leecher v0.6.exe (PID: 1944)
- NOTEPAD.EXE (PID: 1916)
Reads settings of System Certificates
- SlayerSoft.exe (PID: 2576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
51
Monitored processes
10
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 884 | "C:\Windows\Program Files (x86)\Microsoft Host Interface\Keywords & Regex\Host del servicio Monitor.exe" | C:\Windows\Program Files (x86)\Microsoft Host Interface\Keywords & Regex\Host del servicio Monitor.exe | — | Microsoft Windows Protocol Services Host.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Microsoft Windows Protocol Monitor Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1696 | "C:\Windows\Program Files (x86)\Microsoft Host Interface\Keywords & Regex\Microsoft Windows Protocol Services Host.exe" {Arguments If Needed} | C:\Windows\Program Files (x86)\Microsoft Host Interface\Keywords & Regex\Microsoft Windows Protocol Services Host.exe | — | SLAYER Leecher v0.6.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Microsoft Windows Protocol Services Host Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1832 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SLAY.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1904 | "C:\Windows\Program Files (x86)\Microsoft Host Interface\Keywords & Regex\Host del servicio Monitor.exe" | C:\Windows\Program Files (x86)\Microsoft Host Interface\Keywords & Regex\Host del servicio Monitor.exe | — | Microsoft Windows Protocol Services Host.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Microsoft Windows Protocol Monitor Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
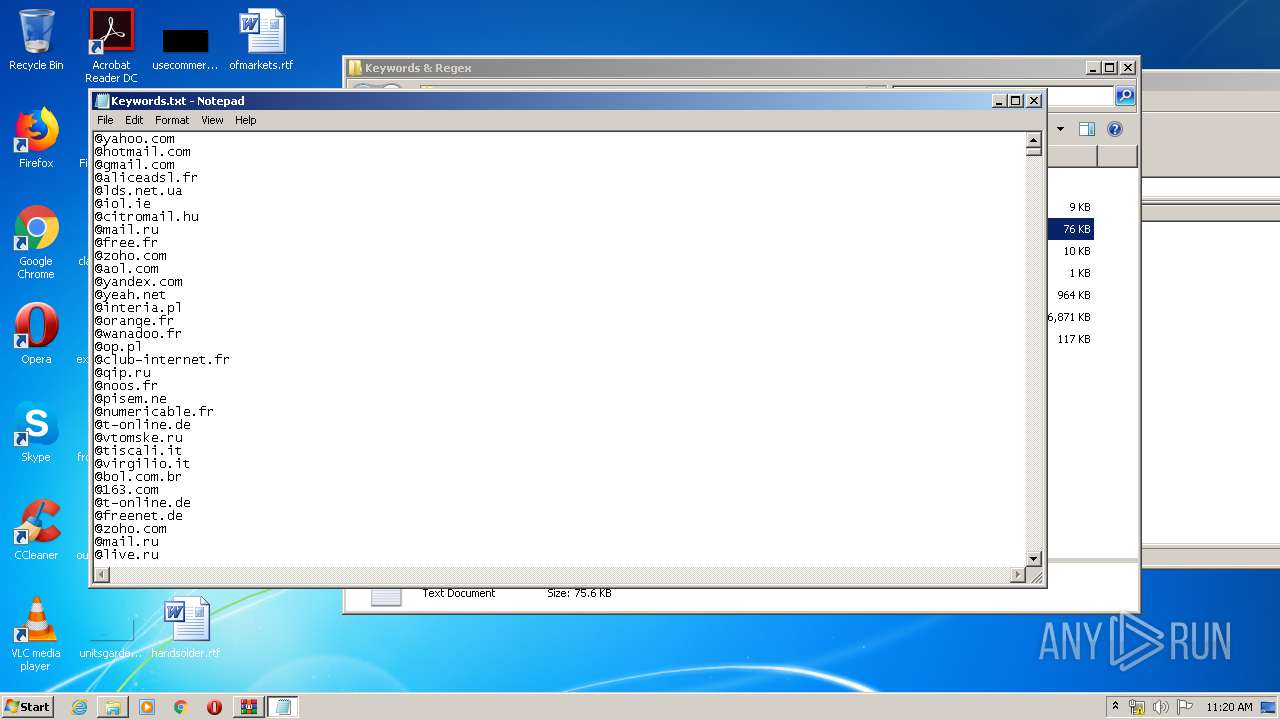
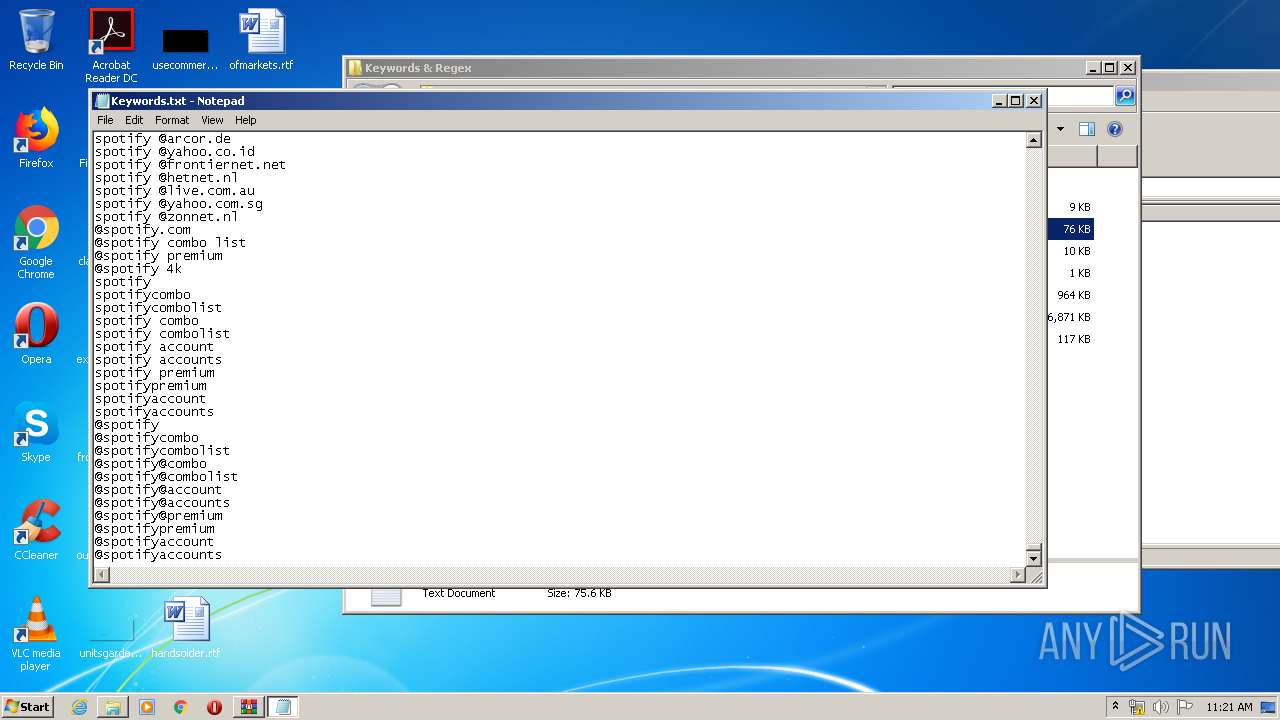
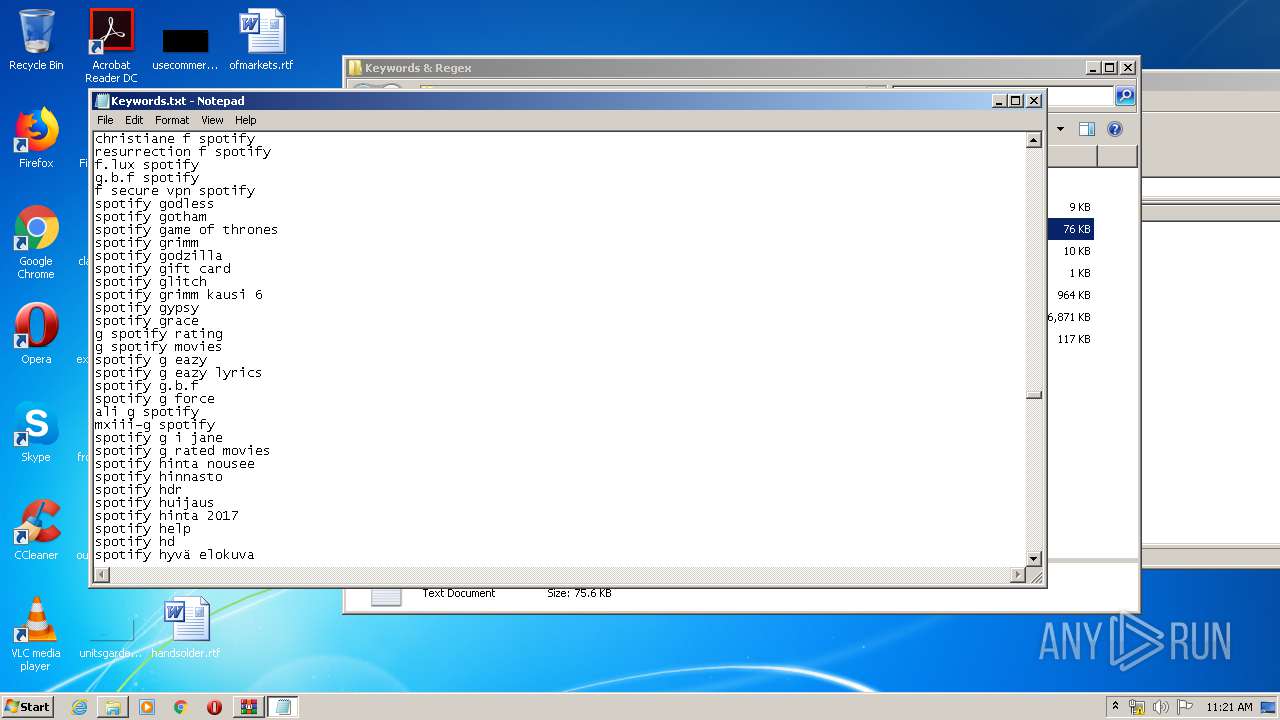
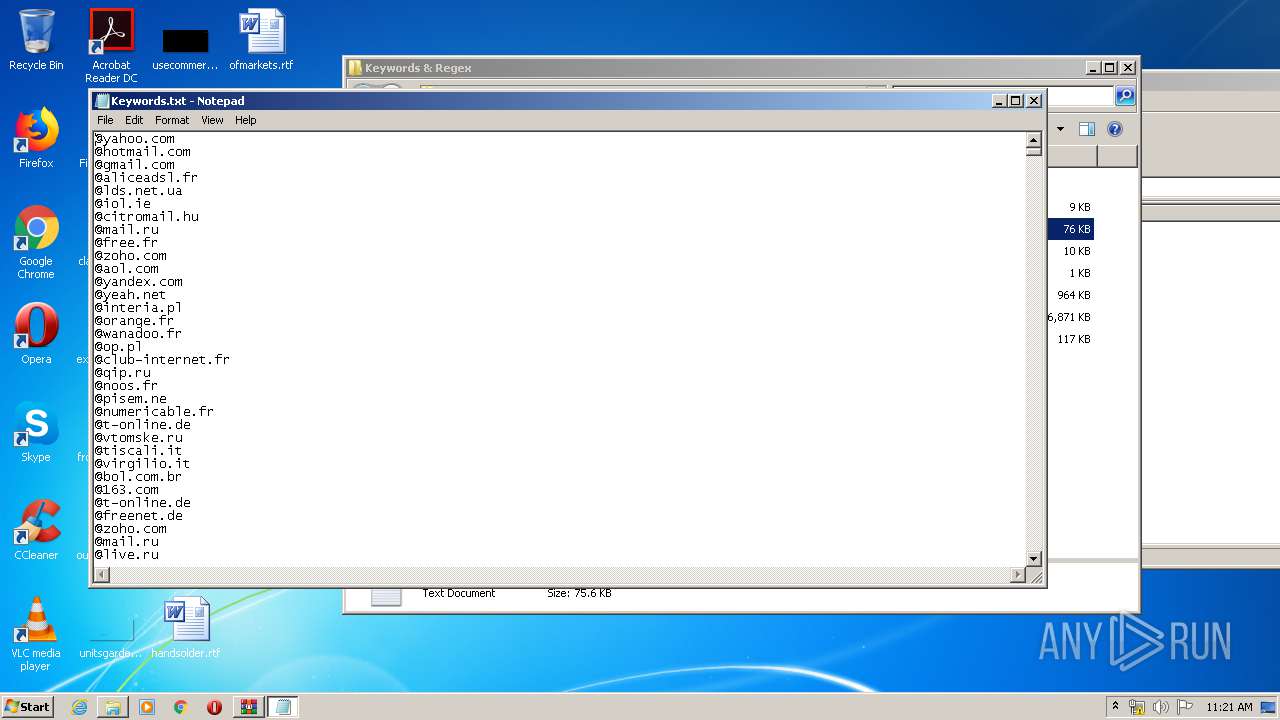
| 1916 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\SLAYER Leecher v0.6\Keywords & Regex\Keywords.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
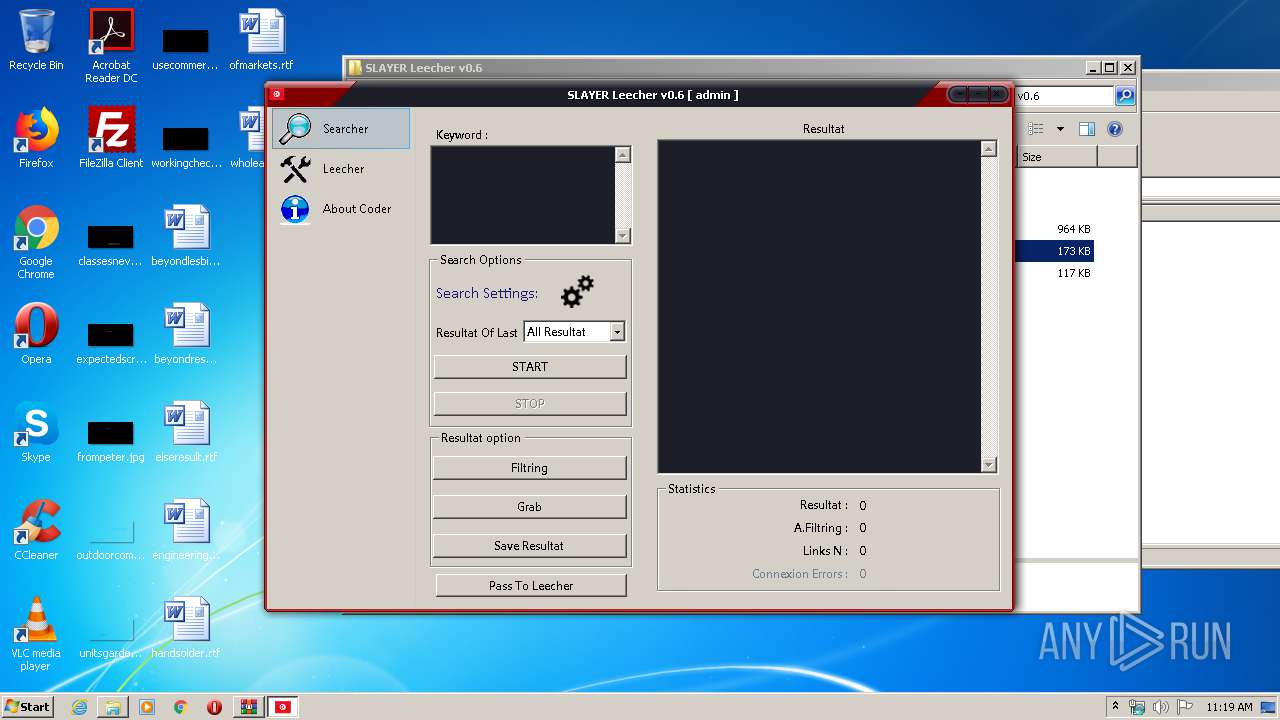
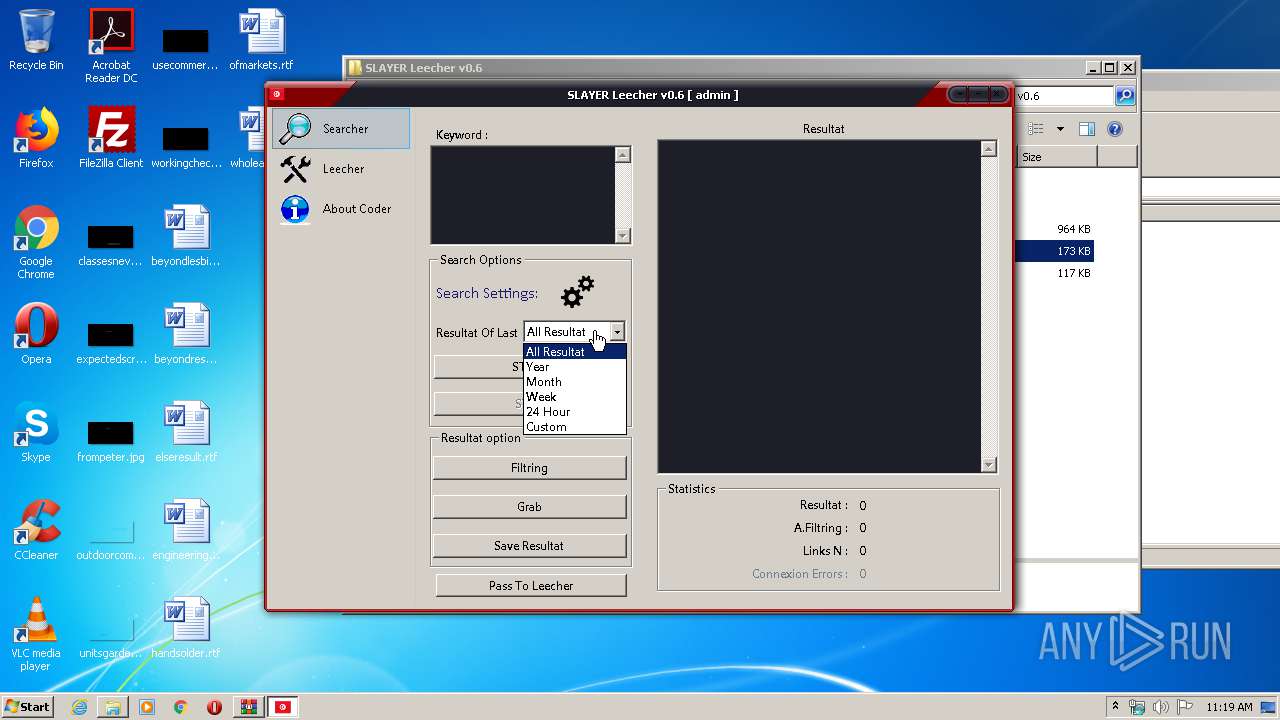
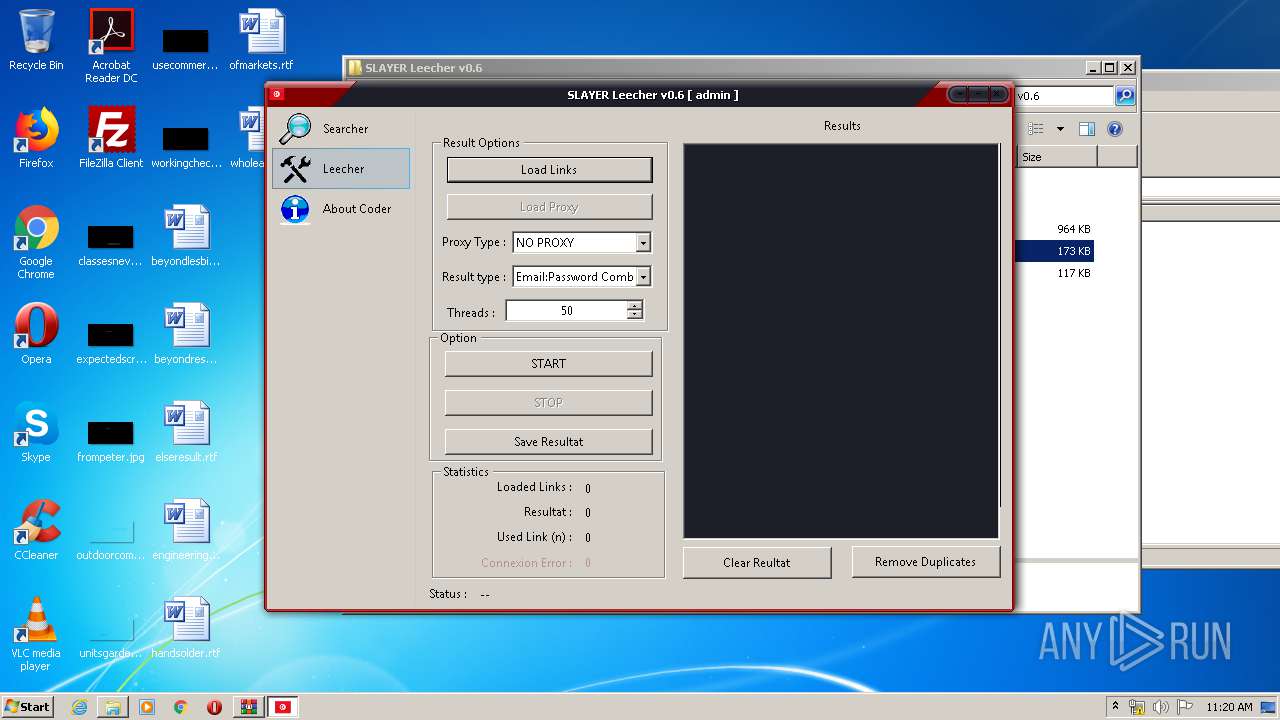
| 1944 | "C:\Users\admin\Desktop\SLAYER Leecher v0.6\SLAYER Leecher v0.6.exe" | C:\Users\admin\Desktop\SLAYER Leecher v0.6\SLAYER Leecher v0.6.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: interface Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
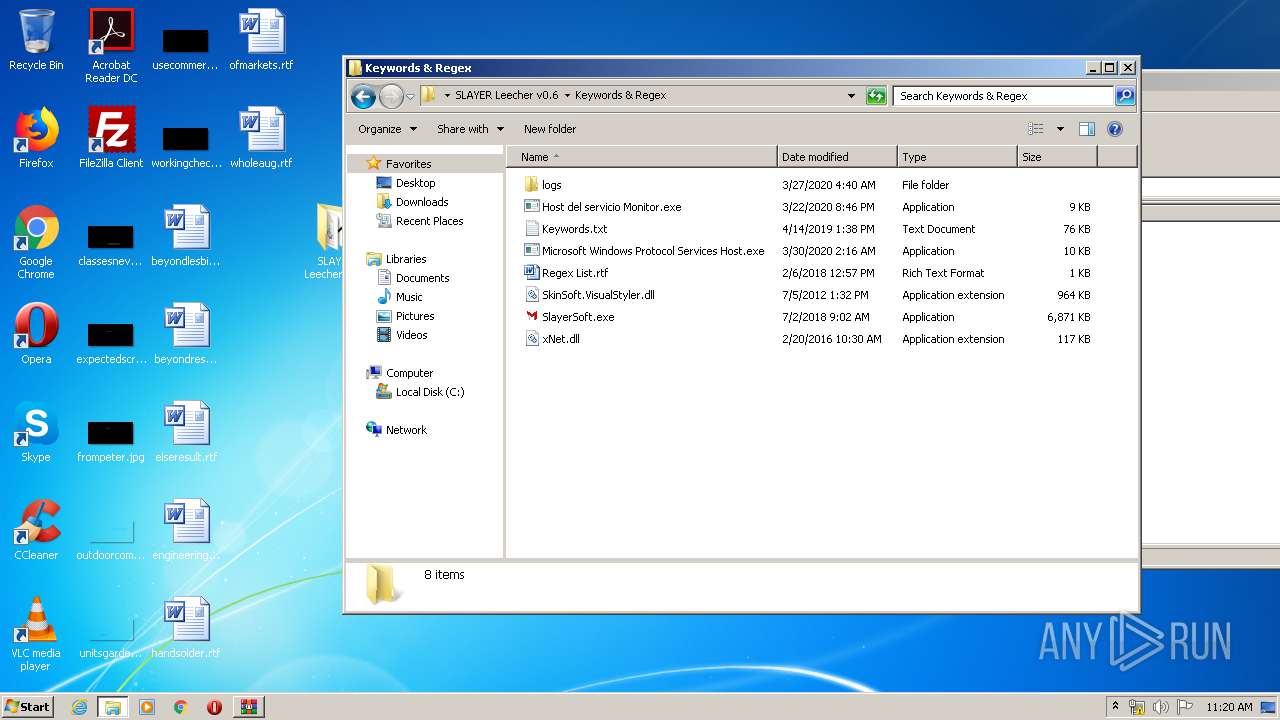
| 2576 | "C:\Users\admin\Desktop\SLAYER Leecher v0.6\Keywords & Regex\SlayerSoft.exe" {Arguments If Needed} | C:\Users\admin\Desktop\SLAYER Leecher v0.6\Keywords & Regex\SlayerSoft.exe | SLAYER Leecher v0.6.exe | ||||||||||||
User: admin Company: Iheb Briki Integrity Level: HIGH Description: SLAYER Leecher Exit code: 0 Version: 0.4.1 Modules
| |||||||||||||||
| 2944 | "C:\Users\admin\Desktop\SLAYER Leecher v0.6\Keywords & Regex\SlayerSoft.exe" {Arguments If Needed} | C:\Users\admin\Desktop\SLAYER Leecher v0.6\Keywords & Regex\SlayerSoft.exe | SLAYER Leecher v0.6.exe | ||||||||||||
User: admin Company: Iheb Briki Integrity Level: MEDIUM Description: SLAYER Leecher Exit code: 0 Version: 0.4.1 Modules
| |||||||||||||||
| 3144 | "C:\Windows\Program Files (x86)\Microsoft Host Interface\Keywords & Regex\Microsoft Windows Protocol Services Host.exe" {Arguments If Needed} | C:\Windows\Program Files (x86)\Microsoft Host Interface\Keywords & Regex\Microsoft Windows Protocol Services Host.exe | — | SLAYER Leecher v0.6.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Microsoft Windows Protocol Services Host Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
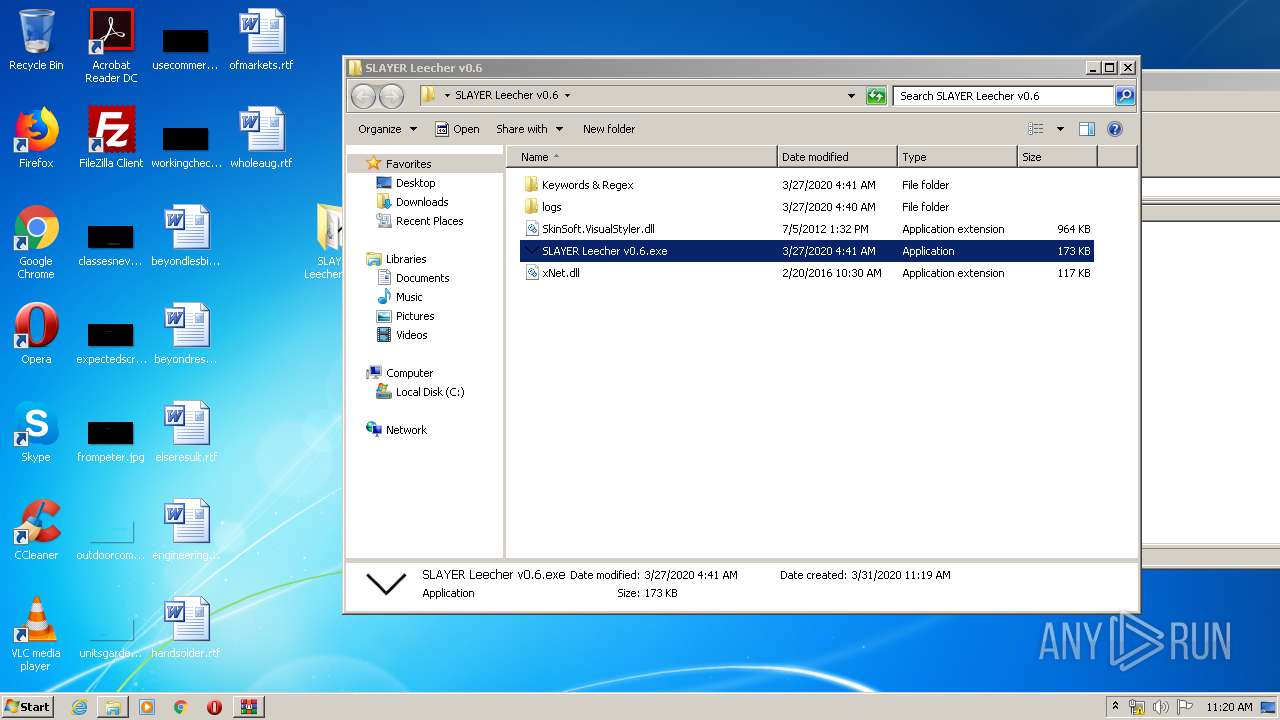
| 3200 | "C:\Users\admin\Desktop\SLAYER Leecher v0.6\SLAYER Leecher v0.6.exe" | C:\Users\admin\Desktop\SLAYER Leecher v0.6\SLAYER Leecher v0.6.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: interface Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
2 700
Read events
1 385
Write events
1 312
Delete events
3
Modification events
| (PID) Process: | (1832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1832) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SLAY.rar | |||
| (PID) Process: | (1832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3200) SLAYER Leecher v0.6.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3200) SLAYER Leecher v0.6.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
5
Suspicious files
0
Text files
3
Unknown types
3
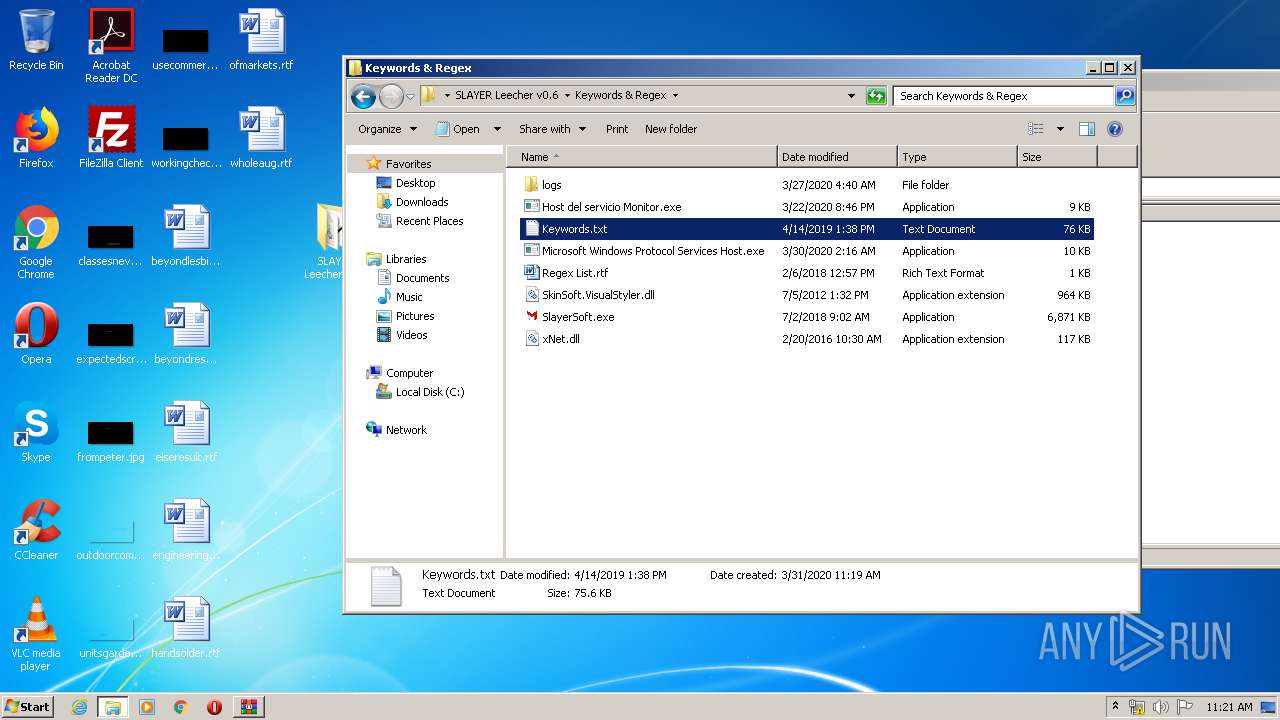
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1832.28232\SLAYER Leecher v0.6\Keywords & Regex\SkinSoft.VisualStyler.dll | — | |
MD5:— | SHA256:— | |||
| 1832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1832.28232\SLAYER Leecher v0.6\Keywords & Regex\SlayerSoft.exe | — | |
MD5:— | SHA256:— | |||
| 1832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1832.28232\SLAYER Leecher v0.6\Keywords & Regex\xNet.dll | — | |
MD5:— | SHA256:— | |||
| 1832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1832.28232\SLAYER Leecher v0.6\logs\SceSetupLog.etl | — | |
MD5:— | SHA256:— | |||
| 1832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1832.28232\SLAYER Leecher v0.6\SkinSoft.VisualStyler.dll | — | |
MD5:— | SHA256:— | |||
| 1832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1832.28232\SLAYER Leecher v0.6\SLAYER Leecher v0.6.exe | — | |
MD5:— | SHA256:— | |||
| 1832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1832.28232\SLAYER Leecher v0.6\xNet.dll | — | |
MD5:— | SHA256:— | |||
| 2576 | SlayerSoft.exe | C:\Users\admin\AppData\Local\Iheb_Briki\SlayerSoft.exe_Url_bg01wsso431xqnzbyvhv5qxpm45rjygp\0.4.1.0\awjzcslo.newcfg | — | |
MD5:— | SHA256:— | |||
| 2576 | SlayerSoft.exe | C:\Users\admin\AppData\Local\Iheb_Briki\SlayerSoft.exe_Url_bg01wsso431xqnzbyvhv5qxpm45rjygp\0.4.1.0\fwdsktvl.newcfg | — | |
MD5:— | SHA256:— | |||
| 1832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1832.28232\SLAYER Leecher v0.6\Keywords & Regex\logs\SceSetupLog.etl | etl | |
MD5:D72E3AB3CE47EAF5C3C2932D3D53C38A | SHA256:FD3FC12F31FA74F92E49E4177947870087CFF6D3034CD3E6755686E60C3C53D1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
9
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
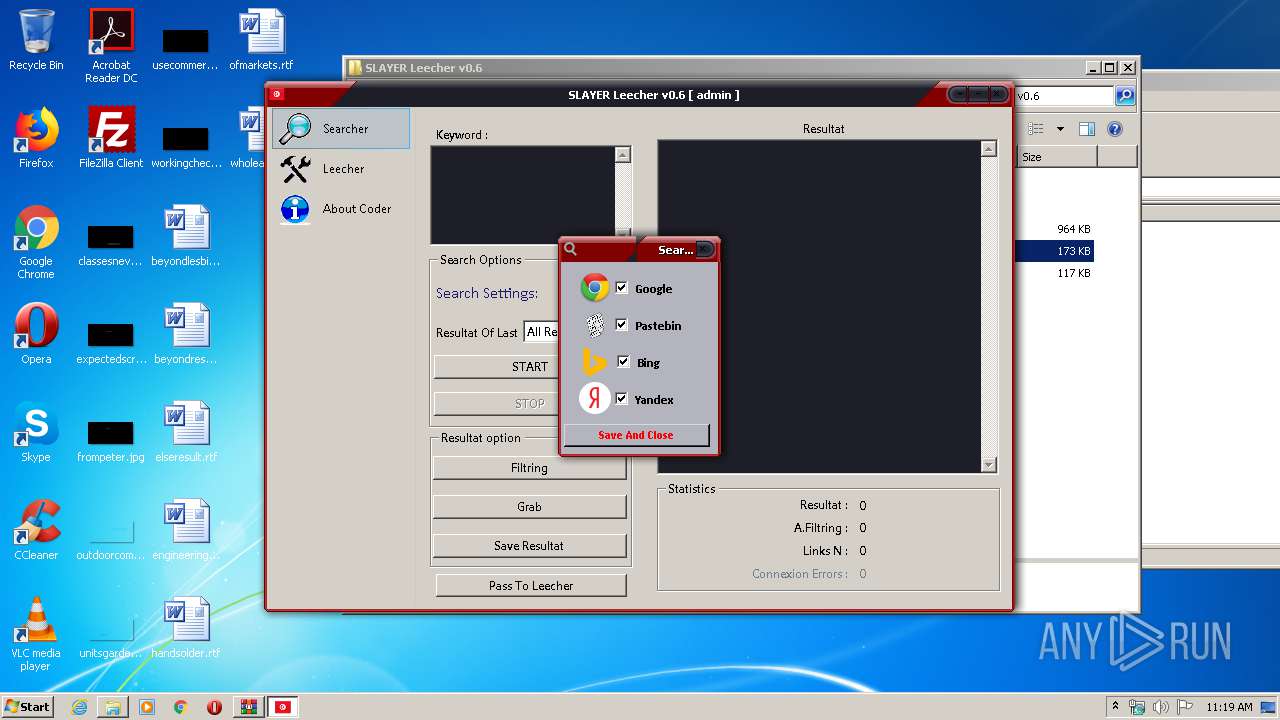
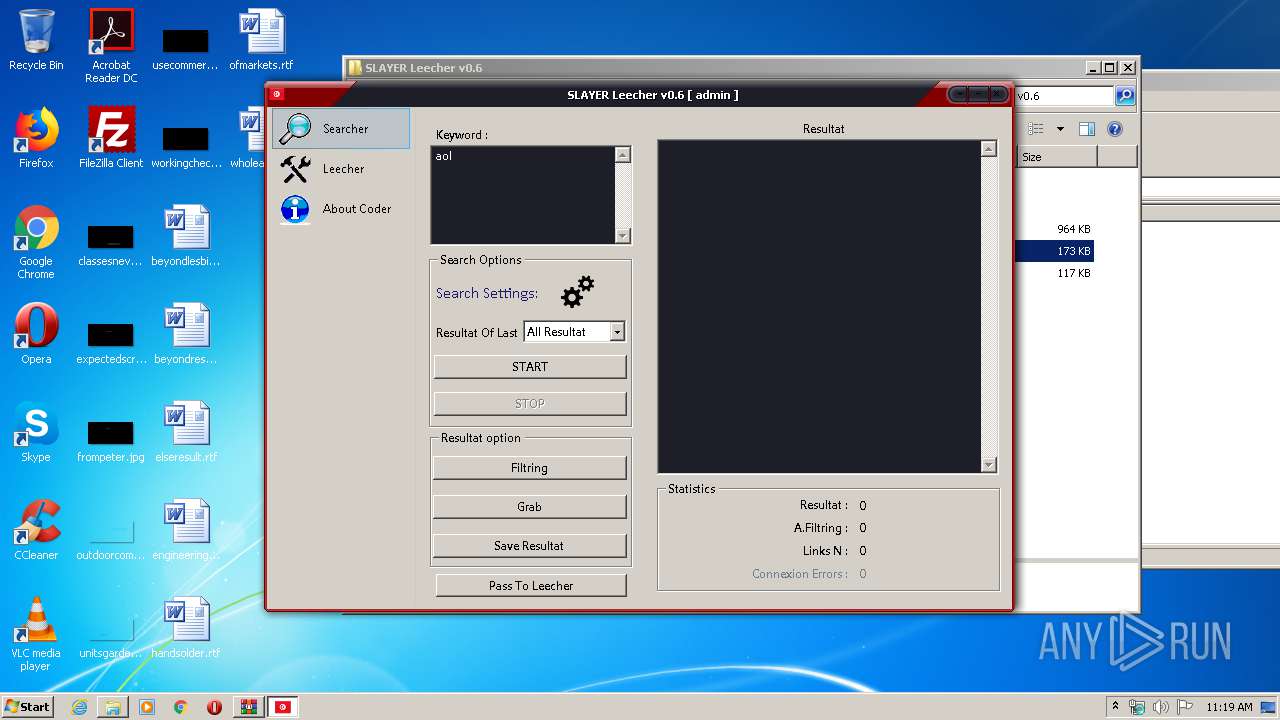
2576 | SlayerSoft.exe | GET | 429 | 216.58.208.36:80 | http://www.google.com/sorry/index?continue=http://www.google.com/search%3Fq%3Daol%26num%3D100%26tbs%3Dqdr:all%26ei%3D-d2PUqnoIOyp7AbP2IGoBQ%26start%3D50%26sa%3DN%26biw%3D1366%26bih%3D604&q=EgS5t2vsGMqyjPQFIhkA8aeDS3kSlCu6M-VXwRNaNYWYe_LC0VerMgFy | US | html | 3.08 Kb | malicious |
2576 | SlayerSoft.exe | GET | 302 | 216.58.208.36:80 | http://www.google.com/search?q=aol&num=100&tbs=qdr:all&ei=-d2PUqnoIOyp7AbP2IGoBQ&start=50&sa=N&biw=1366&bih=604 | US | html | 446 b | malicious |
2576 | SlayerSoft.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/search?q=aol&start=55 | US | html | 55.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2576 | SlayerSoft.exe | 79.125.108.59:443 | duckduckgo.com | Amazon.com, Inc. | IE | unknown |
2944 | SlayerSoft.exe | 104.23.98.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
2576 | SlayerSoft.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2576 | SlayerSoft.exe | 216.58.208.36:80 | www.google.com | Google Inc. | US | whitelisted |
2576 | SlayerSoft.exe | 104.23.98.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
2576 | SlayerSoft.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2576 | SlayerSoft.exe | 216.58.208.36:443 | www.google.com | Google Inc. | US | whitelisted |
2576 | SlayerSoft.exe | 77.88.55.77:443 | yandex.ru | YANDEX LLC | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
www.google.com |
| malicious |
yandex.ru |
| whitelisted |
www.bing.com |
| whitelisted |
duckduckgo.com |
| whitelisted |