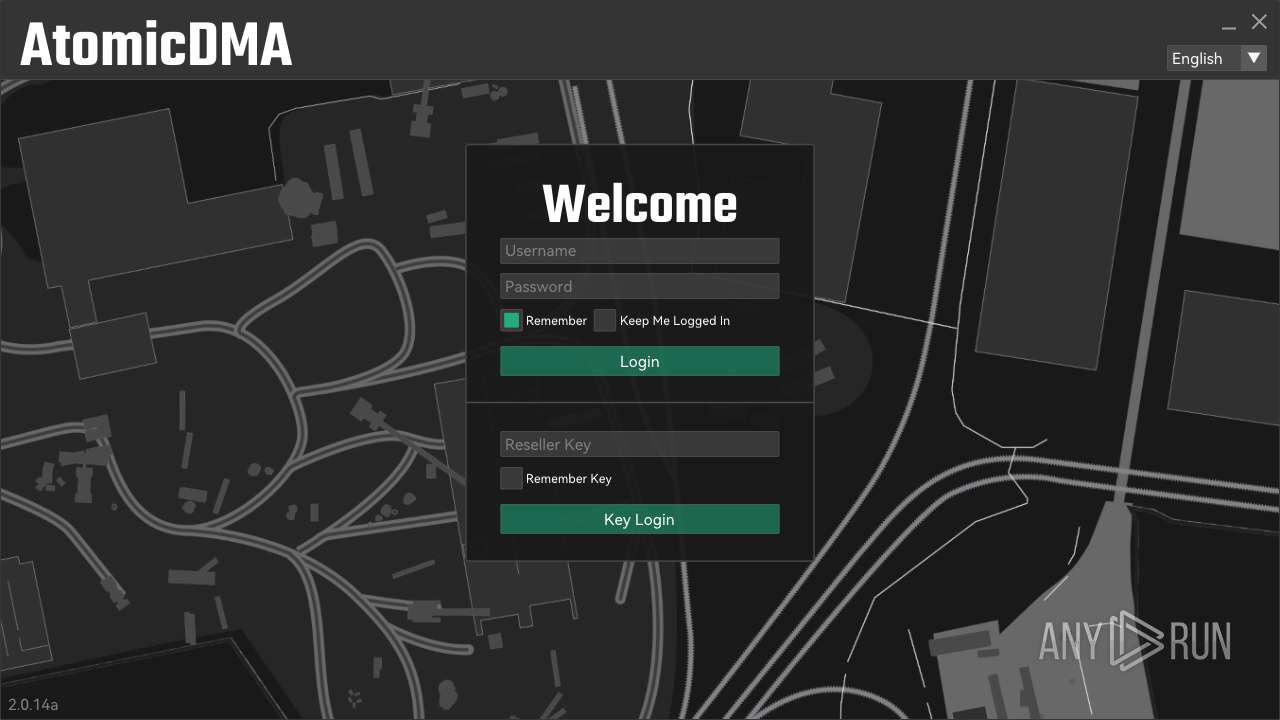
| File name: | AtomicDMA-Launcher.exe |
| Full analysis: | https://app.any.run/tasks/959e87fc-8337-453c-845d-a30e4e492af8 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2024, 12:46:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | DF2087336B35AB61C81AD047983EF44A |
| SHA1: | 6312D326226A8B184ED4C70AF4AC4914FF24F066 |
| SHA256: | 1E161B2DC46F258345910A972542817E5BF00C8755439B165D0CFF4A9A19AA3D |
| SSDEEP: | 98304:Grtss5S2qNRzXYzm0kiyF3XhdyqshOzTfgaS5BKEQA3FSsHfZ/kDgF6NBEhQNKjb:x3gXT+Q86 |
MALICIOUS
Drops the executable file immediately after the start
- AtomicDMA-Launcher.exe (PID: 2448)
SUSPICIOUS
Reads the BIOS version
- AtomicDMA-Launcher.exe (PID: 2448)
Connects to unusual port
- AtomicDMA-Launcher.exe (PID: 2448)
INFO
Checks supported languages
- AtomicDMA-Launcher.exe (PID: 2448)
Reads the computer name
- AtomicDMA-Launcher.exe (PID: 2448)
Reads the software policy settings
- AtomicDMA-Launcher.exe (PID: 2448)
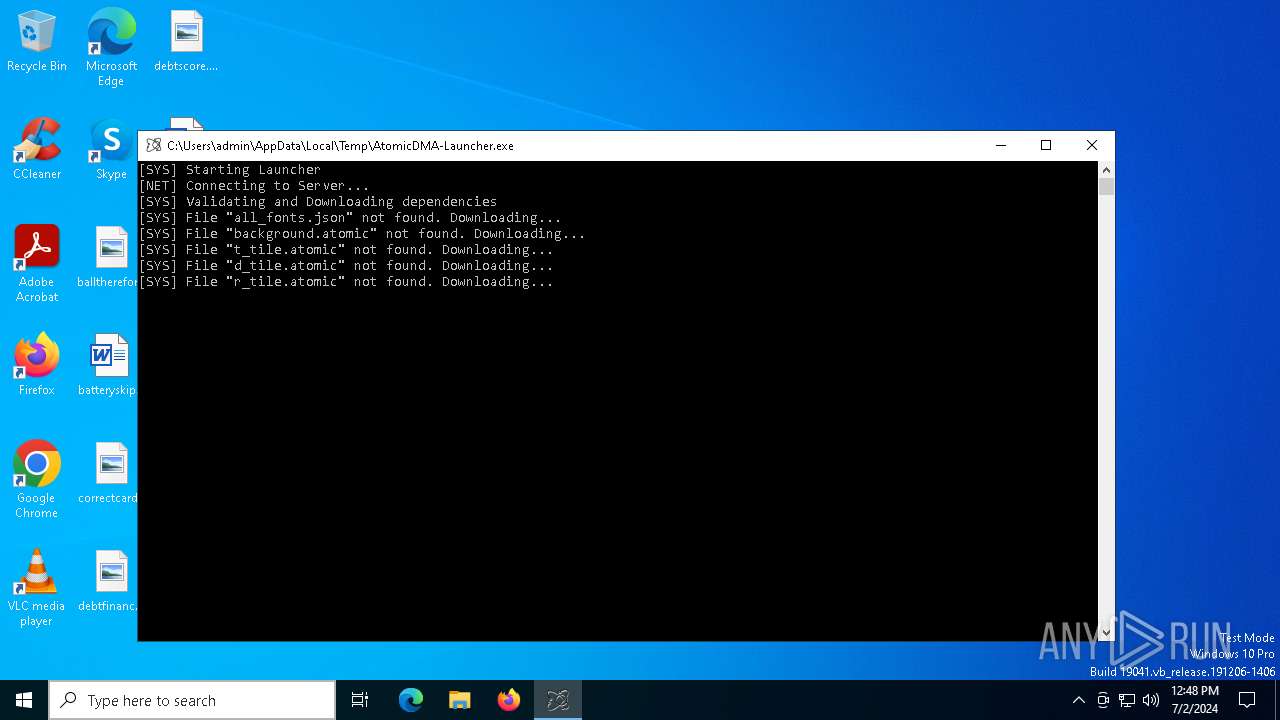
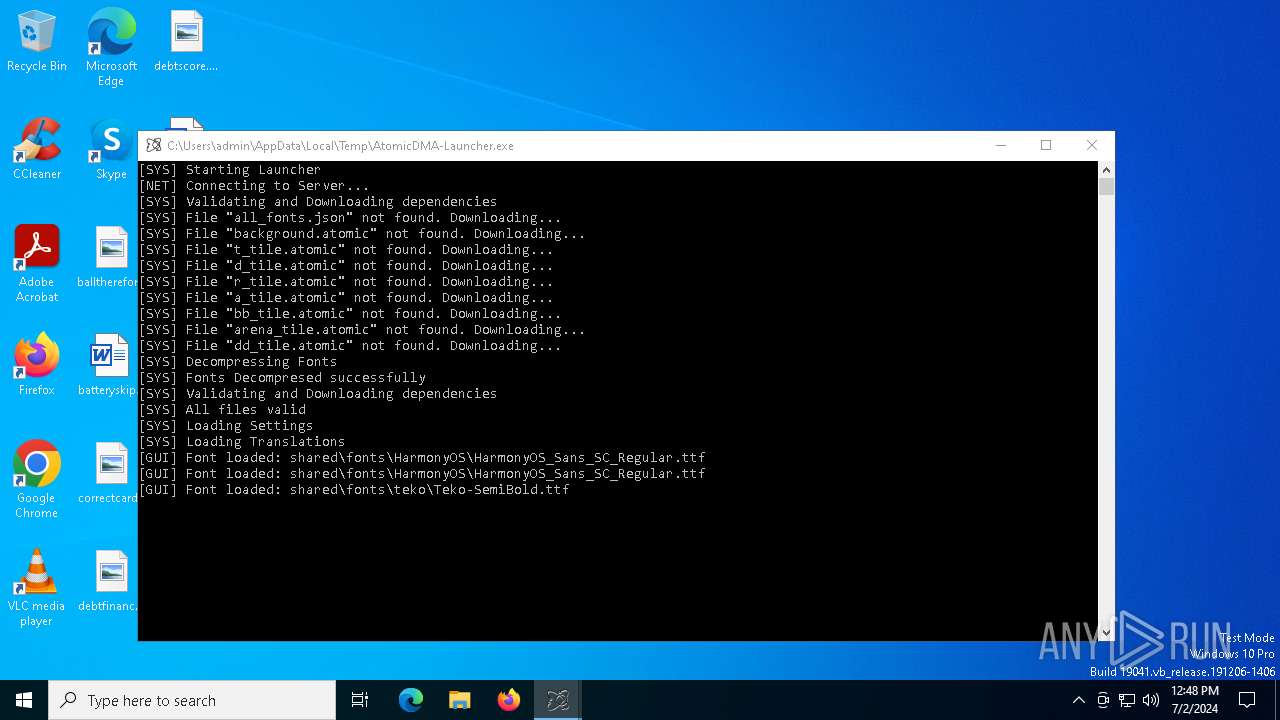
Creates files or folders in the user directory
- AtomicDMA-Launcher.exe (PID: 2448)
Themida protector has been detected
- AtomicDMA-Launcher.exe (PID: 2448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:06:02 01:12:38+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14 |
| CodeSize: | 770560 |
| InitializedDataSize: | 311808 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9d2058 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
133
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2268 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AtomicDMA-Launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2448 | "C:\Users\admin\AppData\Local\Temp\AtomicDMA-Launcher.exe" | C:\Users\admin\AppData\Local\Temp\AtomicDMA-Launcher.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
608
Read events
608
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
4
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2448 | AtomicDMA-Launcher.exe | C:\Users\admin\AppData\Roaming\AtomicDMA\shared\all_fonts.json | — | |
MD5:— | SHA256:— | |||
| 2448 | AtomicDMA-Launcher.exe | C:\Users\admin\AppData\Roaming\AtomicDMA\shared\fonts\MiSans\MiSans-Demibold.ttf | — | |
MD5:— | SHA256:— | |||
| 2448 | AtomicDMA-Launcher.exe | C:\Users\admin\AppData\Roaming\AtomicDMA\shared\fonts\HarmonyOS\HarmonyOS_Sans_SC_Medium.ttf | — | |
MD5:— | SHA256:— | |||
| 2448 | AtomicDMA-Launcher.exe | C:\Users\admin\AppData\Roaming\AtomicDMA\shared\fonts\HarmonyOS\HarmonyOS_Sans_SC_Regular.ttf | — | |
MD5:— | SHA256:— | |||
| 2448 | AtomicDMA-Launcher.exe | C:\Users\admin\AppData\Roaming\AtomicDMA\shared\fonts\HarmonyOS\HarmonyOS_Sans_SC_Bold.ttf | — | |
MD5:— | SHA256:— | |||
| 2448 | AtomicDMA-Launcher.exe | C:\Users\admin\AppData\Roaming\AtomicDMA\launcher\images\background.atomic | text | |
MD5:69788D9300DEDAEDEE781AE45E4C7451 | SHA256:30E7F6398AD90563C9888EF3D07F4926E057332A8B3C9E6EA134437CD90BE28D | |||
| 2448 | AtomicDMA-Launcher.exe | C:\Users\admin\AppData\Roaming\AtomicDMA\launcher\images\dd_tile.atomic | text | |
MD5:9AA70BF1EF152850695AEA9444A098EC | SHA256:41C9B97929E609598B4B70C7E004D6D2E47E1355C7EB12C0C6A48955F55FC9C8 | |||
| 2448 | AtomicDMA-Launcher.exe | C:\Users\admin\AppData\Roaming\AtomicDMA\launcher\images\r_tile.atomic | text | |
MD5:1AC77CD0410A961D1D31355434526DA7 | SHA256:ABA8CA8D1F4B25AACD8DA8822E537E535B5A2B45187F69747165D83507EA3E2E | |||
| 2448 | AtomicDMA-Launcher.exe | C:\Users\admin\AppData\Roaming\AtomicDMA\launcher\images\t_tile.atomic | text | |
MD5:044B679B2D3B319FC064036E01780296 | SHA256:1C55BBB66FF23160A8168DA19FDF0C4BBE070AAA8A32EAEA2F252FB91FCD88B4 | |||
| 2448 | AtomicDMA-Launcher.exe | C:\Users\admin\AppData\Roaming\AtomicDMA\shared\fonts\HarmonyOS\HarmonyOS_Sans_Medium.ttf | ttf | |
MD5:1EC44B30A3B03D9267628D6F8969EA53 | SHA256:F6B009D07D8D894D55EADEB7080B4916C3A2C83FF3EE60BBE851E6698D73BAFD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
69
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2468 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
256 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
256 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
2468 | svchost.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4120 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
4684 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2336 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2448 | AtomicDMA-Launcher.exe | 188.114.96.3:2096 | atomicdma.com | CLOUDFLARENET | NL | unknown |
2468 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4632 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2468 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2468 | svchost.exe | 88.221.125.143:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 20.189.173.5:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3040 | OfficeClickToRun.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
atomicdma.com |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |