| File name: | Week6.exe |
| Full analysis: | https://app.any.run/tasks/8afa9642-6970-4566-99b5-c6d2de9abbde |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2024, 17:11:46 |
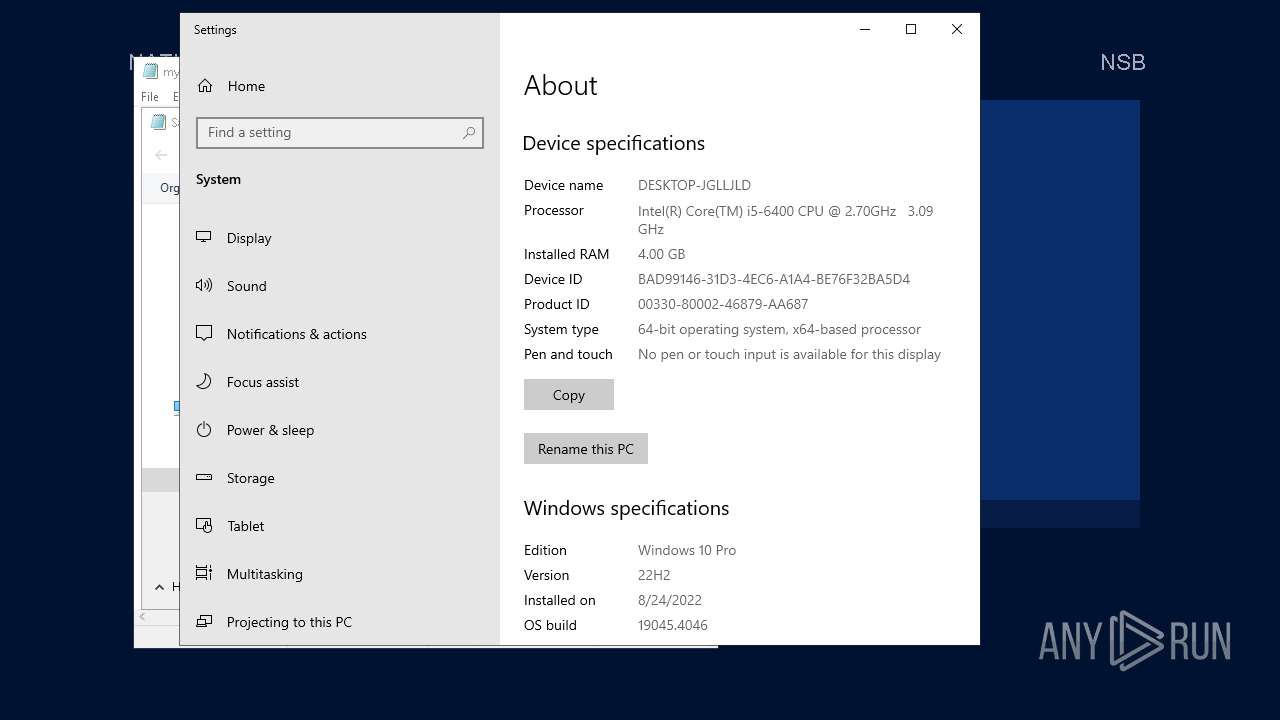
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | CEDF3C46EDEBD97EA1692AE590857CED |
| SHA1: | 27E2C1BFEC1C93997E9EB2125D76296D183A83CC |
| SHA256: | 1E143634419D85E54433FC35A1B6497F69D18C07A6A9015B06CAFB6B31C33B54 |
| SSDEEP: | 3072:z89zOrwVcyWdHvE7JH9NWHJH/S4ORkSOyBkGMj:aOr0ACVWpfS4xSO0kFj |
MALICIOUS
Application was injected by another process
- SystemPropertiesComputerName.exe (PID: 4344)
Changes the autorun value in the registry
- XWAQAQUE.exe (PID: 1940)
SUSPICIOUS
Connects to unusual port
- XWAQAQUE.exe (PID: 1940)
- Week6.exe (PID: 5600)
Executable content was dropped or overwritten
- Week6.exe (PID: 5600)
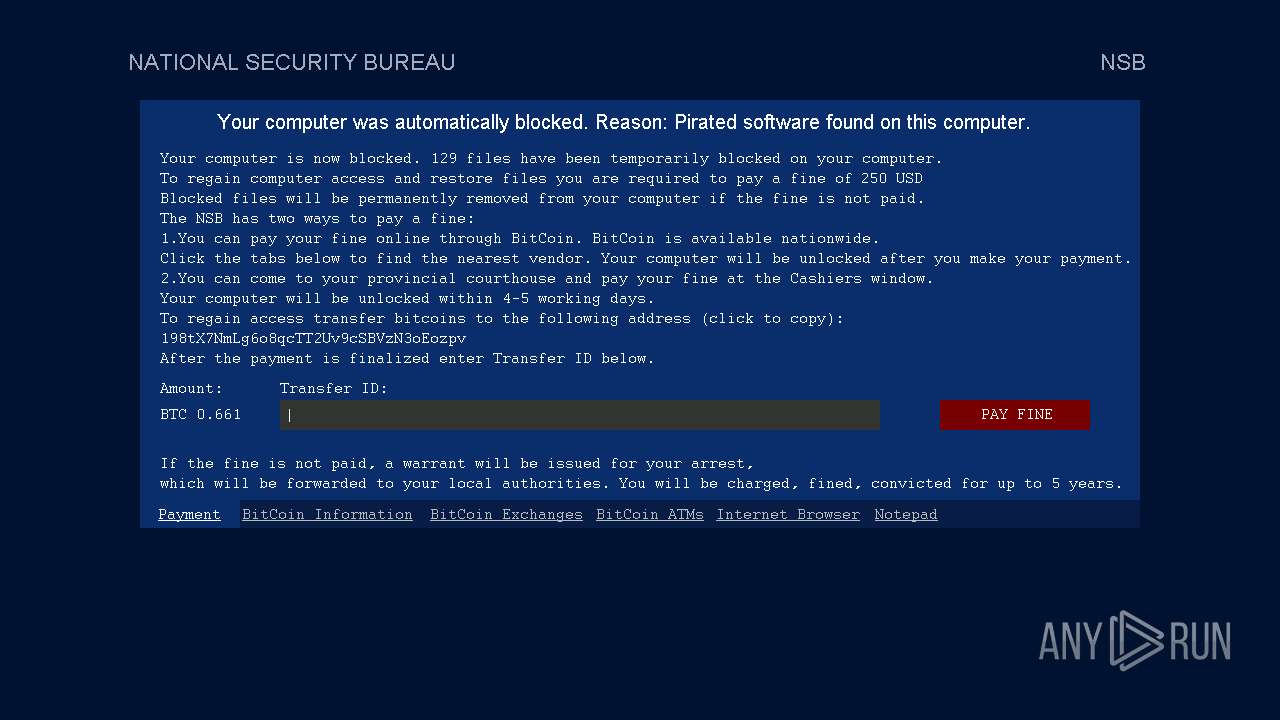
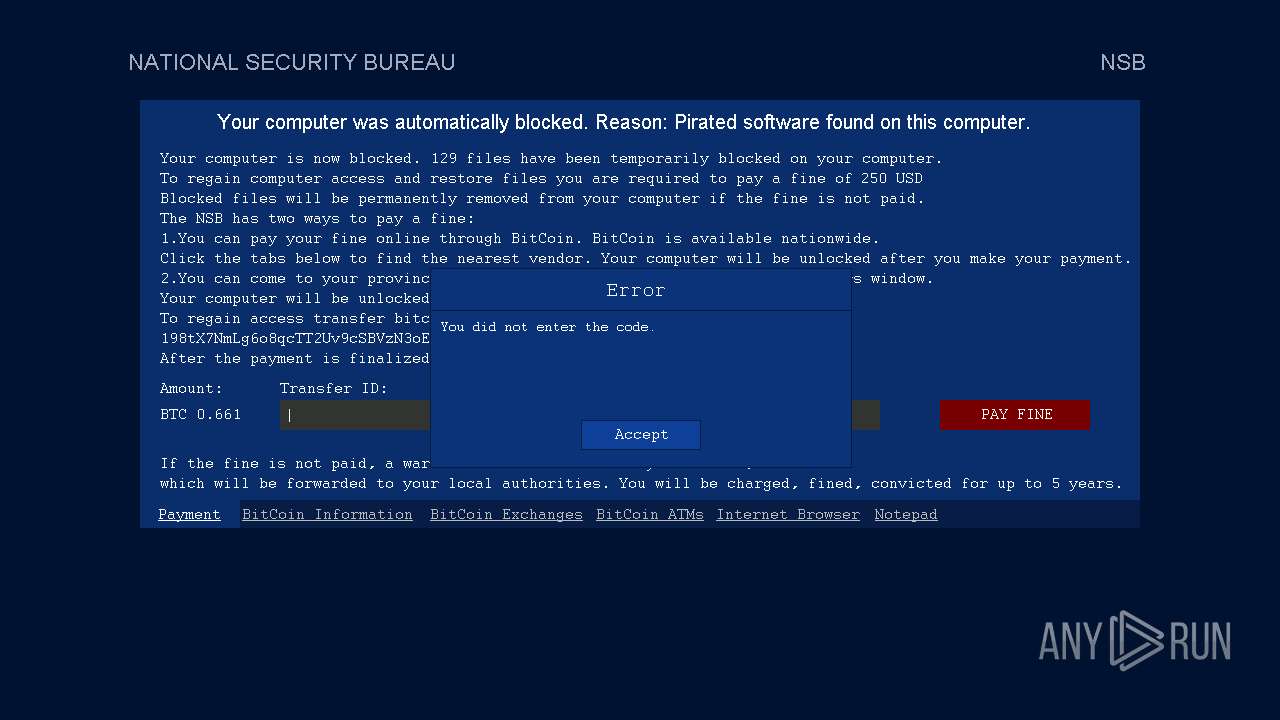
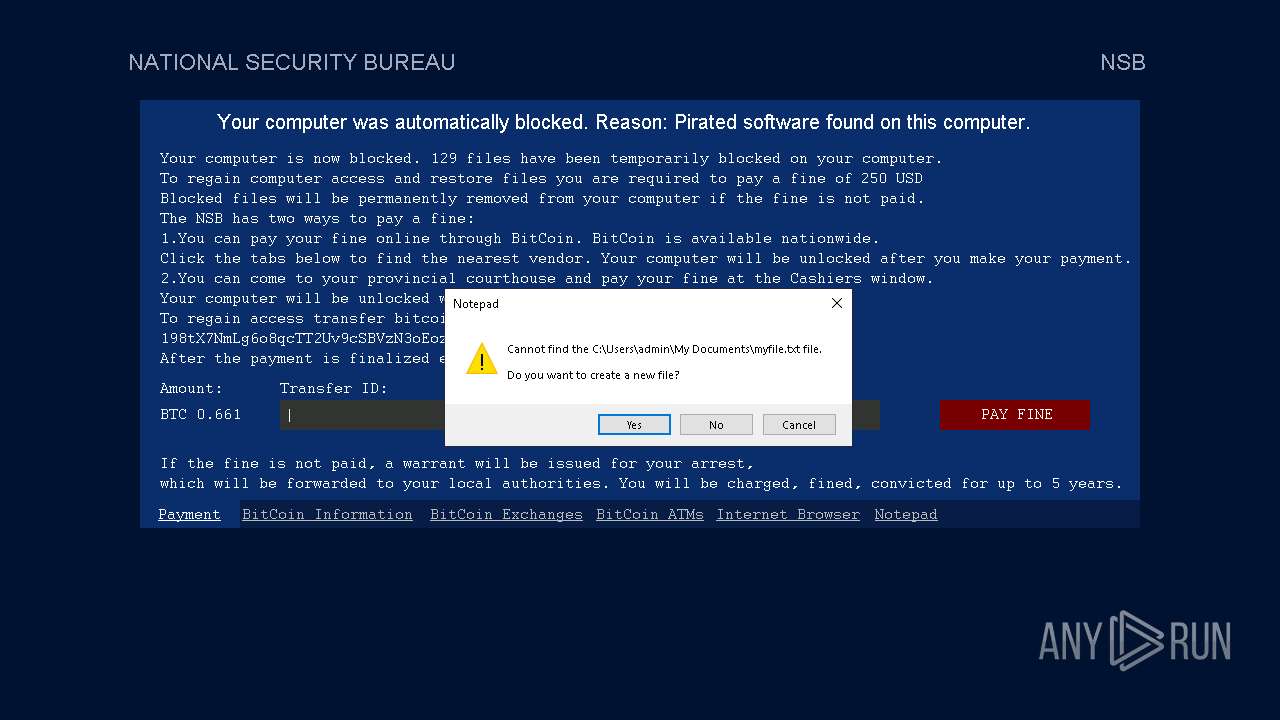
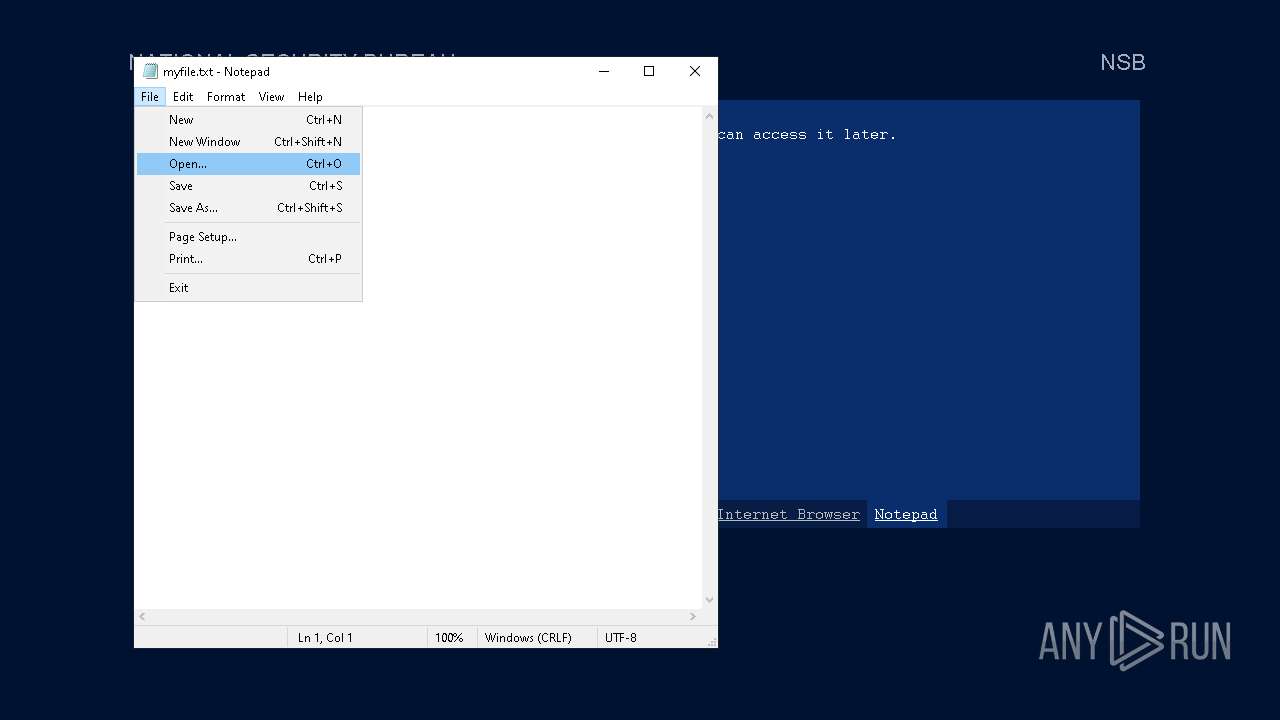
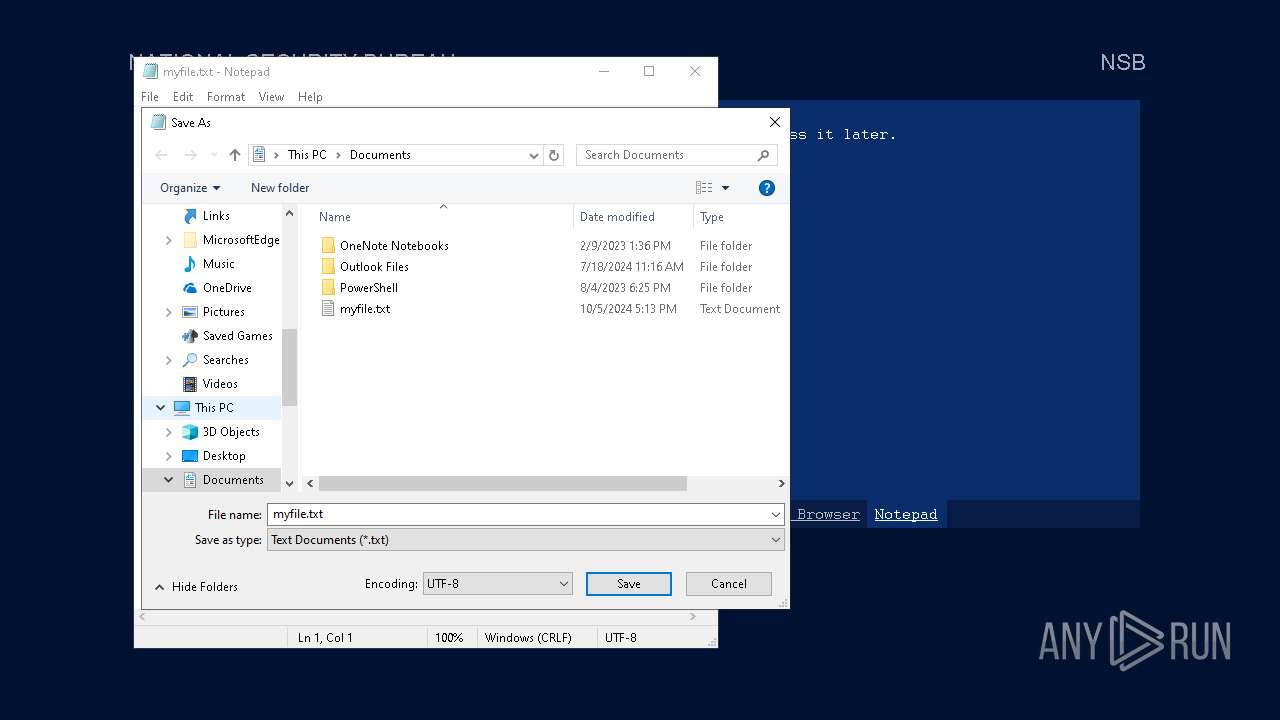
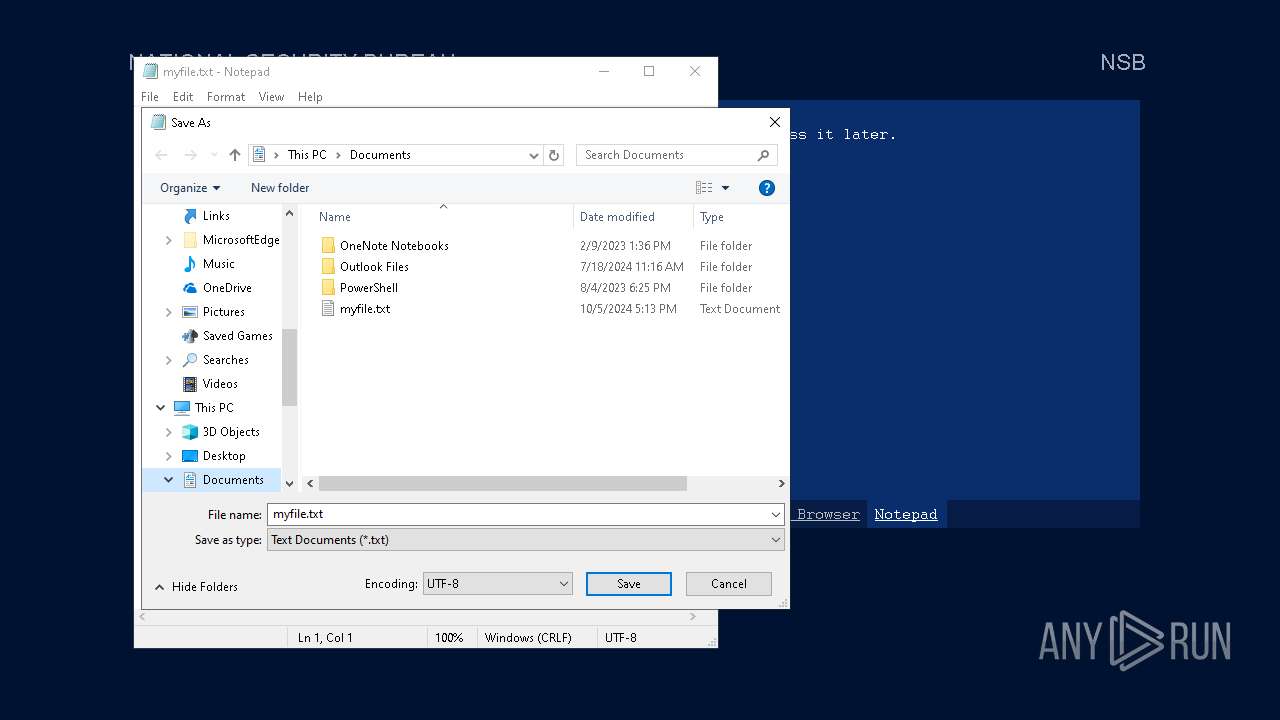
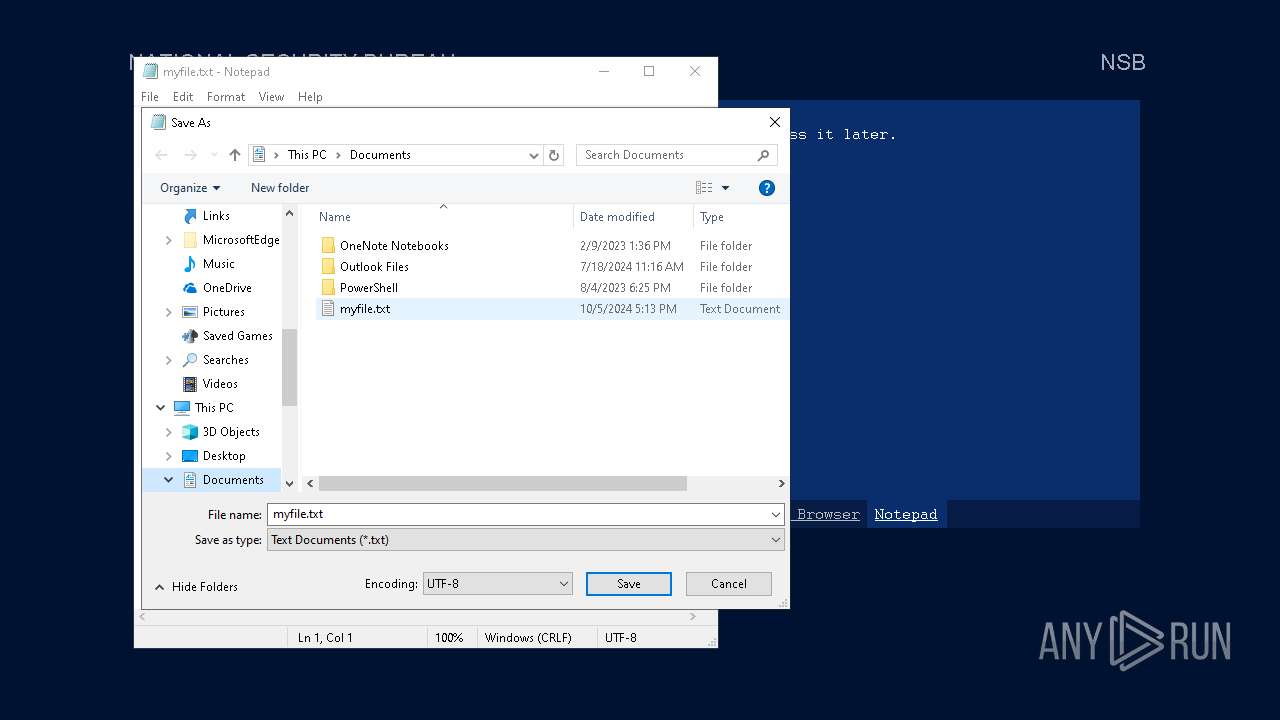
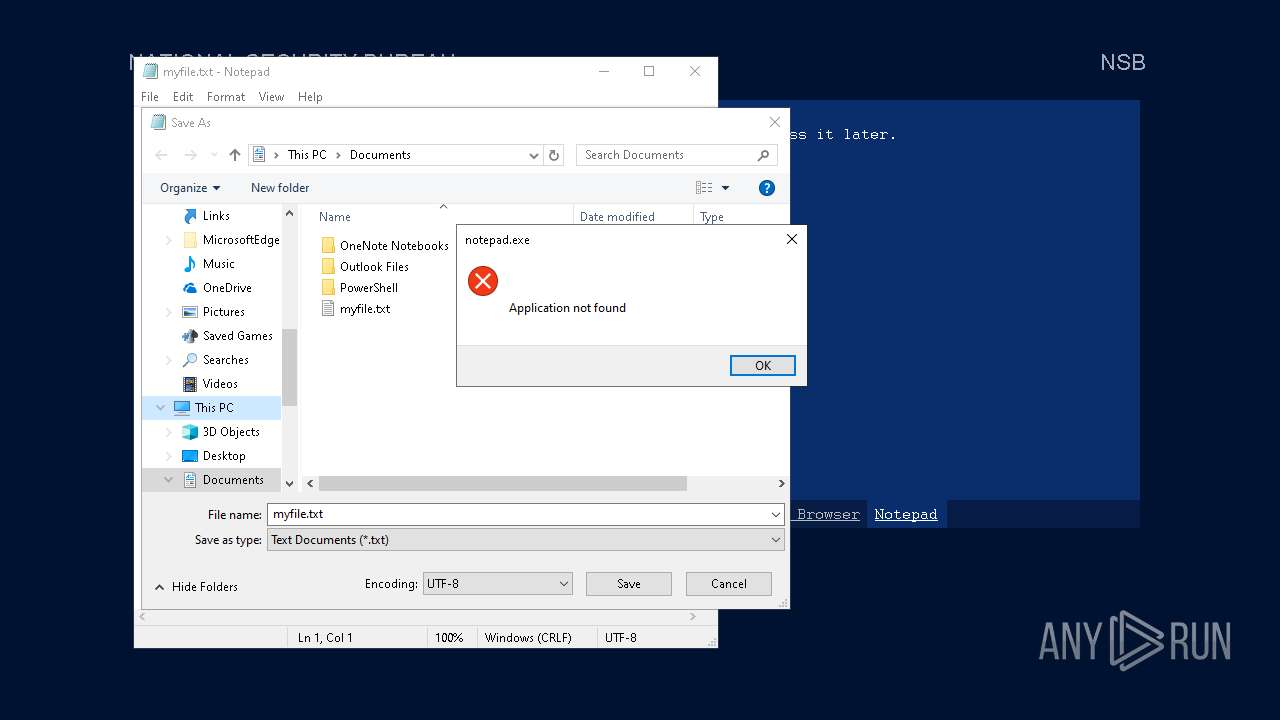
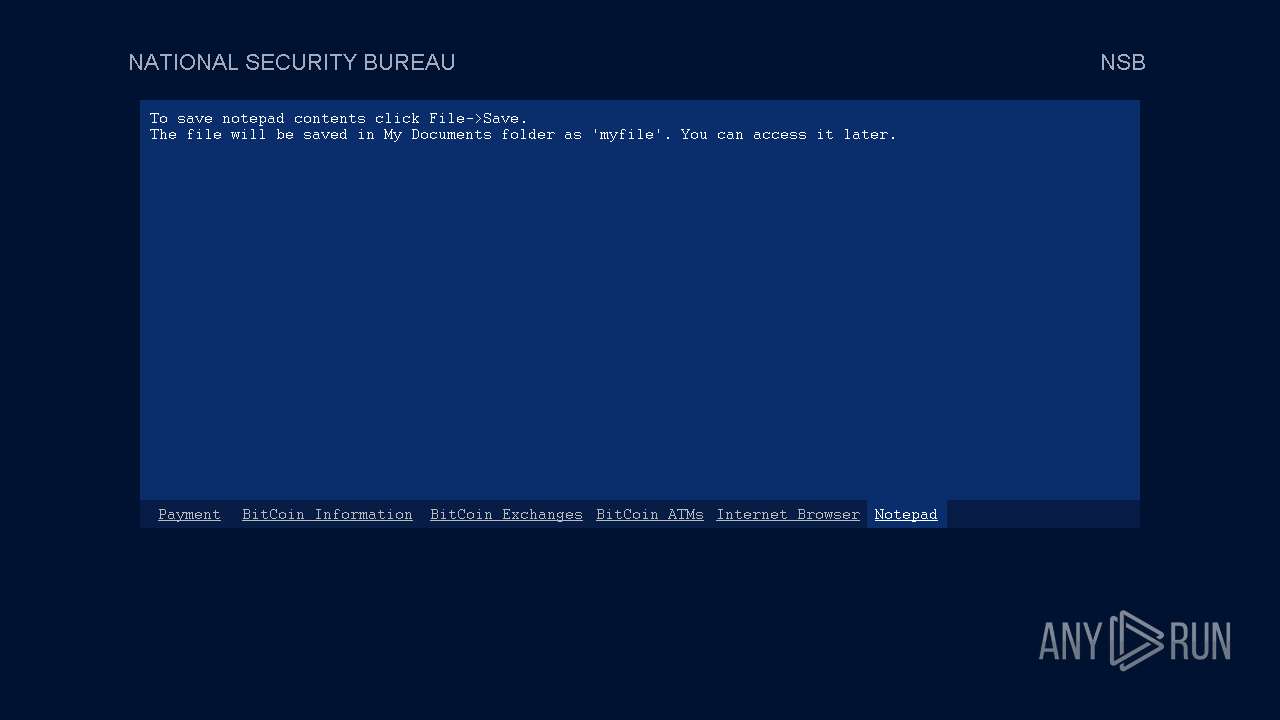
Start notepad (likely ransomware note)
- Week6.exe (PID: 5600)
INFO
Reads the computer name
- Week6.exe (PID: 5600)
- XWAQAQUE.exe (PID: 1940)
Checks supported languages
- Week6.exe (PID: 5600)
- XWAQAQUE.exe (PID: 1940)
Creates files in the program directory
- Week6.exe (PID: 5600)
- XWAQAQUE.exe (PID: 1940)
UPX packer has been detected
- Week6.exe (PID: 5600)
Create files in a temporary directory
- Week6.exe (PID: 5600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (64.2) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.6) |
| .exe | | | Win32 Executable (generic) (10.6) |
| .exe | | | Generic Win/DOS Executable (4.7) |
| .exe | | | DOS Executable Generic (4.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1970:01:01 00:02:03+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 5.12 |
| CodeSize: | 143360 |
| InitializedDataSize: | 72192 |
| UninitializedDataSize: | 73728 |
| EntryPoint: | 0x357e0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
147
Monitored processes
11
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 368 | "C:\WINDOWS\system32\control.exe" SYSTEM | C:\Windows\SysWOW64\control.exe | — | notepad.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1432 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1940 | "C:\ProgramData\usAgAgoI\XWAQAQUE.exe" | C:\ProgramData\usAgAgoI\XWAQAQUE.exe | Week6.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
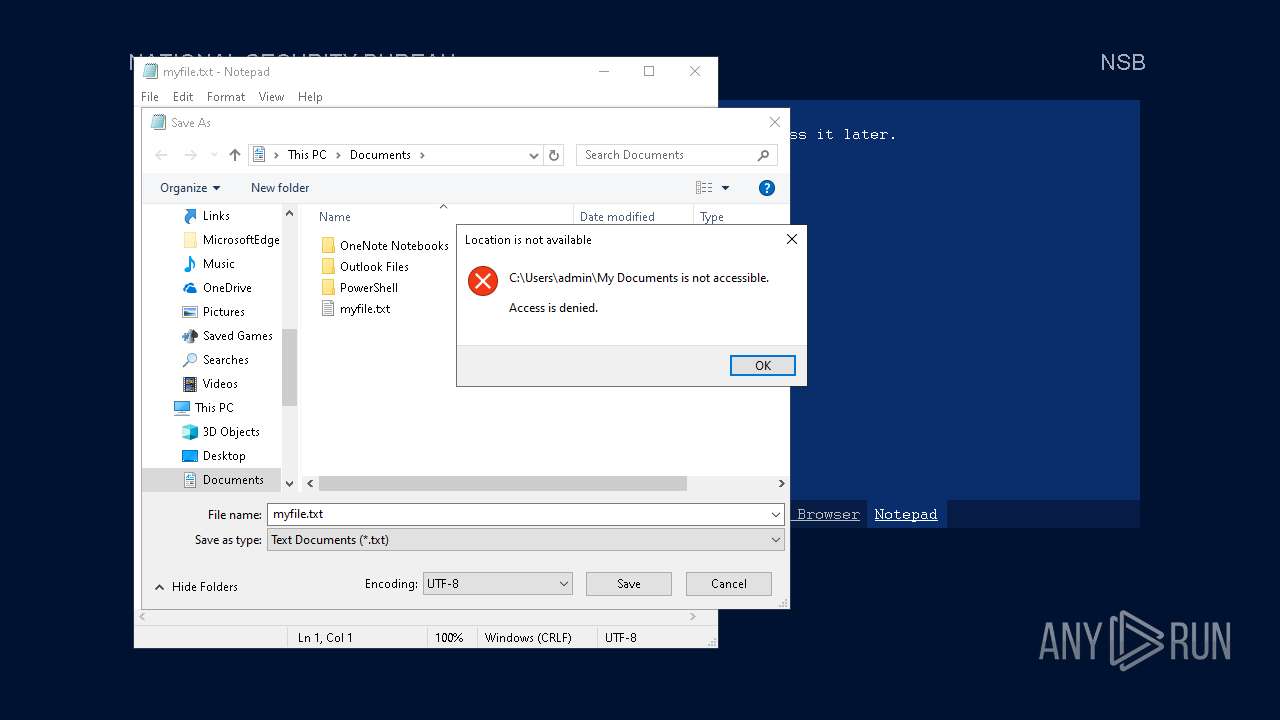
| 3588 | notepad.exe "C:\Users\admin\My Documents\myfile" | C:\Windows\SysWOW64\notepad.exe | — | Week6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4344 | "C:\WINDOWS\system32\systempropertiescomputername.exe" | C:\Windows\System32\SystemPropertiesComputerName.exe | sihost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change Computer Settings Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4600 | "C:\Windows\ImmersiveControlPanel\SystemSettings.exe" -ServerName:microsoft.windows.immersivecontrolpanel | C:\Windows\ImmersiveControlPanel\SystemSettings.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Settings Exit code: 1 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5464 | "C:\WINDOWS\system32\systempropertiescomputername.exe" | C:\Windows\System32\SystemPropertiesComputerName.exe | SystemSettings.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change Computer Settings Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5600 | "C:\Users\admin\AppData\Local\Temp\Week6.exe" | C:\Users\admin\AppData\Local\Temp\Week6.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6260 | "C:\WINDOWS\system32\control.exe" SYSTEM | C:\Windows\SysWOW64\control.exe | — | notepad.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 634
Read events
20 293
Write events
327
Delete events
14
Modification events
| (PID) Process: | (1940) XWAQAQUE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | XWAQAQUE.exe |
Value: C:\ProgramData\usAgAgoI\XWAQAQUE.exe | |||
| (PID) Process: | (3588) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3588) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 040000000E00000010000000030000000F000000000000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (3588) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (3588) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (3588) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (3588) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (3588) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | FFlags |
Value: | |||
| (PID) Process: | (3588) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | IconSize |
Value: 16 | |||
| (PID) Process: | (3588) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | Sort |
Value: 000000000000000000000000000000000100000030F125B7EF471A10A5F102608C9EEBAC0A00000001000000 | |||
Executable files
488
Suspicious files
8
Text files
129
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5600 | Week6.exe | C:\ProgramData\Adobe\ARM\S\388\AdobeARMHelper.exe | executable | |
MD5:75F19F65F1E6400D06221DB467F933E1 | SHA256:085E6088634876145C900617FC8F4F8E57323BAB23F0B3EEA0B43C3BBB6B72C0 | |||
| 5600 | Week6.exe | C:\Users\admin\AppData\Local\VirtualStore\RCX9F4A.tmp | executable | |
MD5:75F19F65F1E6400D06221DB467F933E1 | SHA256:085E6088634876145C900617FC8F4F8E57323BAB23F0B3EEA0B43C3BBB6B72C0 | |||
| 5600 | Week6.exe | C:\Users\admin\AppData\Local\Temp\BsAK.ico | image | |
MD5:B2A9E20F351B70B21469E4A4BA1D3506 | SHA256:0F015363E17B4320AA73BB7DB01A87773BB171120EF59CB9EBDC13C857DF1692 | |||
| 5600 | Week6.exe | C:\Users\admin\AppData\Local\Temp\Skws.exe | executable | |
MD5:E7B4738C7C93B8122372E1744D191853 | SHA256:8A655D7161F2834D3A2A78C462ECAA47D867A8A3F294D3A6144B48C73F5E9F8B | |||
| 5600 | Week6.exe | C:\Users\admin\AppData\Local\Temp\lgEg.exe | executable | |
MD5:C348F008B5F9E9C8D1F6D1A0676111D6 | SHA256:718C21A3FEFAEC4D0ECE97A3E570EADEA341755AC4387451915E1812B63659F2 | |||
| 5600 | Week6.exe | C:\Users\admin\AppData\Local\Temp\ywIq.exe | executable | |
MD5:52D6681485E335939E28E4EBF44ED2D9 | SHA256:B246EF97B6A7F7CDC7169656041DD524AAE42B705479DEA7A2FEABEB5DF08CCE | |||
| 5600 | Week6.exe | C:\ProgramData\usAgAgoI\XWAQAQUE.exe | executable | |
MD5:10AF81F798A72546510AB665BB508768 | SHA256:D8404DC359F5F340FF55DB4DDF90C634BAED5C05AEA017DC8ECE6407649832BF | |||
| 5600 | Week6.exe | C:\Users\admin\AppData\Local\VirtualStore\RCXA1BF.tmp | executable | |
MD5:82542D92F71E0EC6915F04B258DAAAB3 | SHA256:26BD67C42176EEB7A6EE0DF9B6D75E0966A62D3410F9C6E5B828F92C0FB029BB | |||
| 5600 | Week6.exe | C:\Users\admin\AppData\Local\Temp\pcUO.ico | image | |
MD5:B2A9E20F351B70B21469E4A4BA1D3506 | SHA256:0F015363E17B4320AA73BB7DB01A87773BB171120EF59CB9EBDC13C857DF1692 | |||
| 5600 | Week6.exe | C:\Users\admin\AppData\Local\VirtualStore\RCXA0C2.tmp | executable | |
MD5:039A0A2E22B1BBD3479FA032C5B23CD0 | SHA256:B91833C37810A88F6B9D1322350B3B7905C2E961DBB1B8222A7EC1CD90FDAC86 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
65
DNS requests
24
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1940 | XWAQAQUE.exe | GET | 302 | 142.250.185.206:80 | http://google.com/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6188 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2028 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1672 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6188 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5600 | Week6.exe | GET | 302 | 142.250.185.206:80 | http://google.com/ | unknown | — | — | whitelisted |
1028 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1028 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4288 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5600 | Week6.exe | 200.87.164.69:9999 | — | Entel S.A. - EntelNet | BO | unknown |
5600 | Week6.exe | 142.250.185.206:80 | google.com | GOOGLE | US | whitelisted |
1940 | XWAQAQUE.exe | 200.87.164.69:9999 | — | Entel S.A. - EntelNet | BO | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5600 | Week6.exe | A Network Trojan was detected | ET HUNTING Terse Unencrypted Request for Google - Likely Connectivity Check |
1940 | XWAQAQUE.exe | A Network Trojan was detected | ET HUNTING Terse Unencrypted Request for Google - Likely Connectivity Check |
1940 | XWAQAQUE.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Possible automated connectivity check (www.google.com) |
5600 | Week6.exe | A Network Trojan was detected | ET HUNTING Terse Unencrypted Request for Google - Likely Connectivity Check |