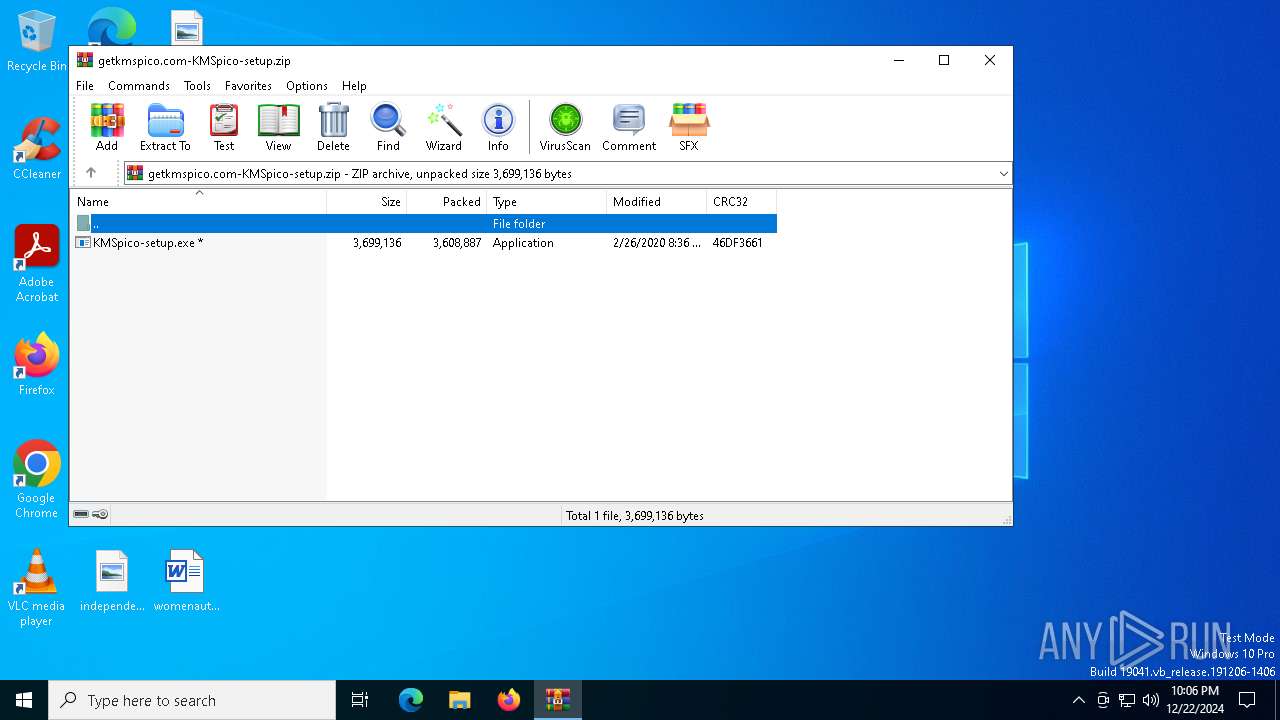
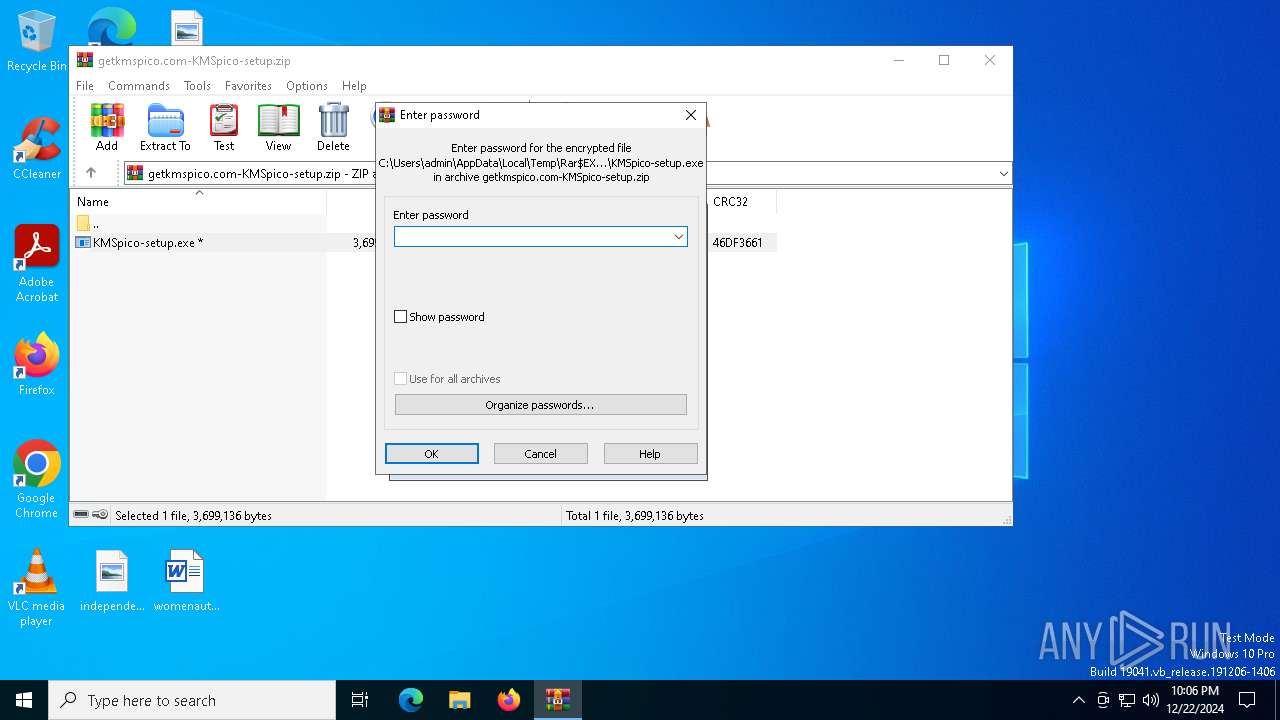
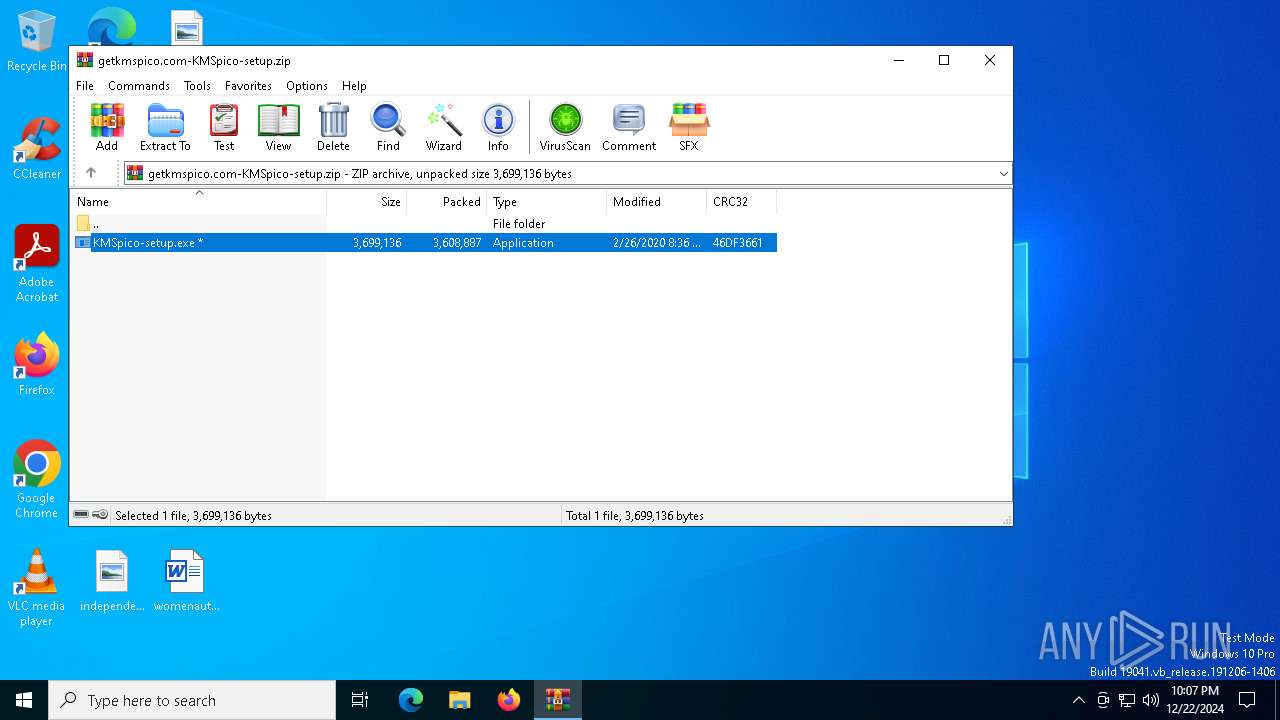
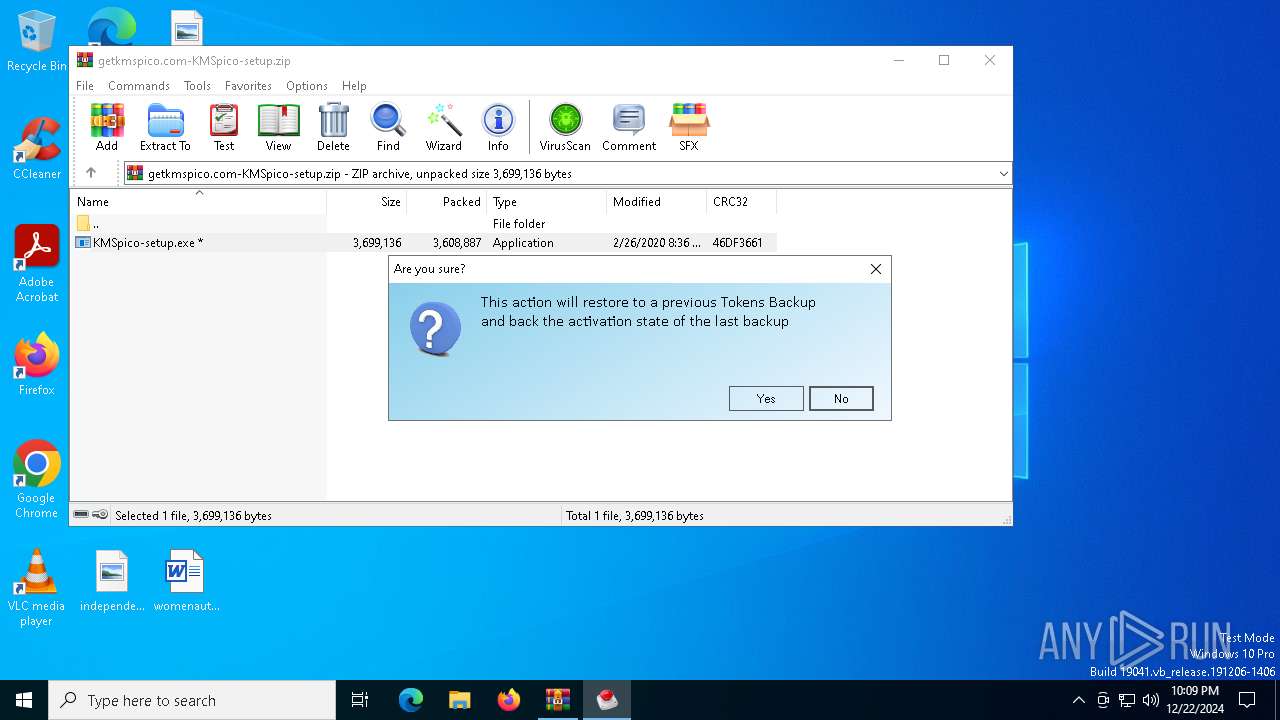
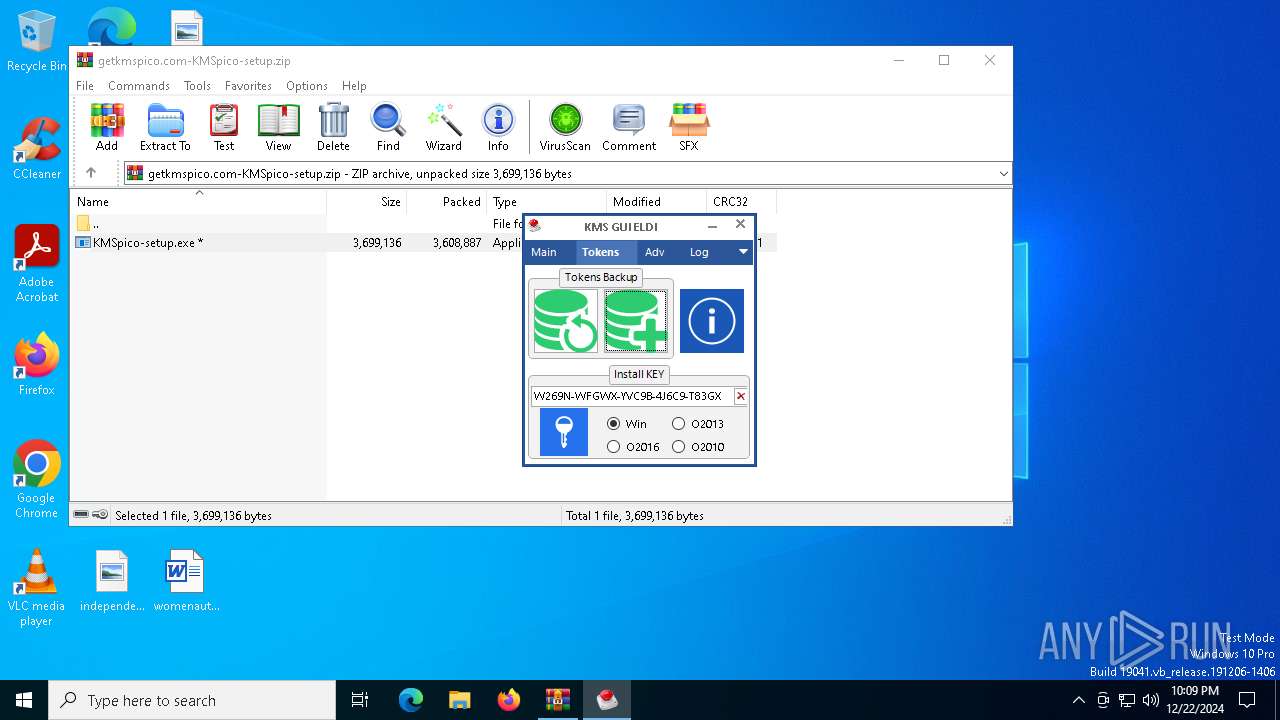
| File name: | getkmspico.com-KMSpico-setup.zip |
| Full analysis: | https://app.any.run/tasks/1ecd14ce-e3fc-4d42-96d3-05e6d10376e3 |
| Verdict: | Malicious activity |
| Analysis date: | December 22, 2024, 22:06:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 2E286F3F68A215B58D134A22C3A36766 |
| SHA1: | 872783B04855DE3681813A645872B694F803A23A |
| SHA256: | 1E0321278152004BD4A93E6CF70DF30282BF3DE3BDAC4F5A43314891C233FC8D |
| SSDEEP: | 98304:sZrxTFnAsxOEZJkPqdETqDk5hClGuc2V/N4+lWe42HzriI8FlWE7KZ6ntCQoLl6K:sisxWKvQGp |
MALICIOUS
Executing a file with an untrusted certificate
- KMSpico-setup.exe (PID: 7156)
- KMSpico-setup.exe (PID: 6300)
- KMSpico-setup.exe (PID: 6484)
- _setup.exe (PID: 5640)
- KMSELDI.exe (PID: 5696)
- AutoPico.exe (PID: 6480)
- KMSELDI.exe (PID: 6316)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3140)
Uses Task Scheduler to autorun other applications
- KMSpico-setup.tmp (PID: 4932)
Changes image file execution options
- KMSELDI.exe (PID: 5696)
- AutoPico.exe (PID: 6480)
- KMSELDI.exe (PID: 6316)
- KMSELDI.exe (PID: 6572)
- AutoPico.exe (PID: 6740)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6352)
- KMSpico-setup.tmp (PID: 3488)
- KMSpico-setup.tmp (PID: 4008)
Executable content was dropped or overwritten
- KMSpico-setup.exe (PID: 7156)
- KMSpico-setup.exe (PID: 6300)
- KMSpico-setup.tmp (PID: 4008)
- KMSpico-setup.exe (PID: 6484)
- KMSpico-setup.tmp (PID: 4932)
- _setup.exe (PID: 5640)
- _setup.tmp (PID: 5728)
- KMSELDI.exe (PID: 5696)
Reads the Windows owner or organization settings
- KMSpico-setup.tmp (PID: 4008)
- KMSpico-setup.tmp (PID: 4932)
- _setup.tmp (PID: 5728)
Process drops legitimate windows executable
- _setup.tmp (PID: 5728)
Modifies the phishing filter of IE
- _setup.tmp (PID: 5728)
Starts SC.EXE for service management
- cmd.exe (PID: 4548)
Uses TASKKILL.EXE to kill process
- KMSpico-setup.tmp (PID: 4932)
Executing commands from ".cmd" file
- _setup.tmp (PID: 5728)
Starts CMD.EXE for commands execution
- _setup.tmp (PID: 5728)
Creates a new Windows service
- sc.exe (PID: 4996)
Uses ICACLS.EXE to modify access control lists
- KMSELDI.exe (PID: 6316)
Connects to unusual port
- KMSELDI.exe (PID: 6316)
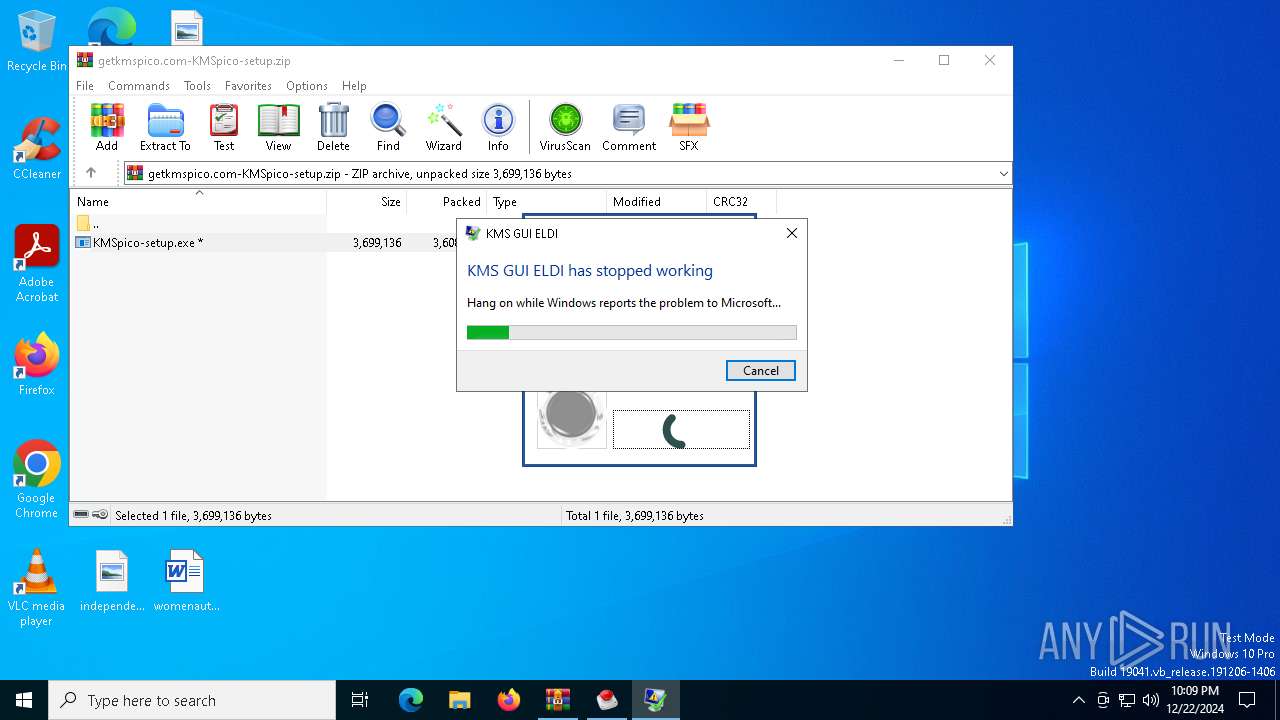
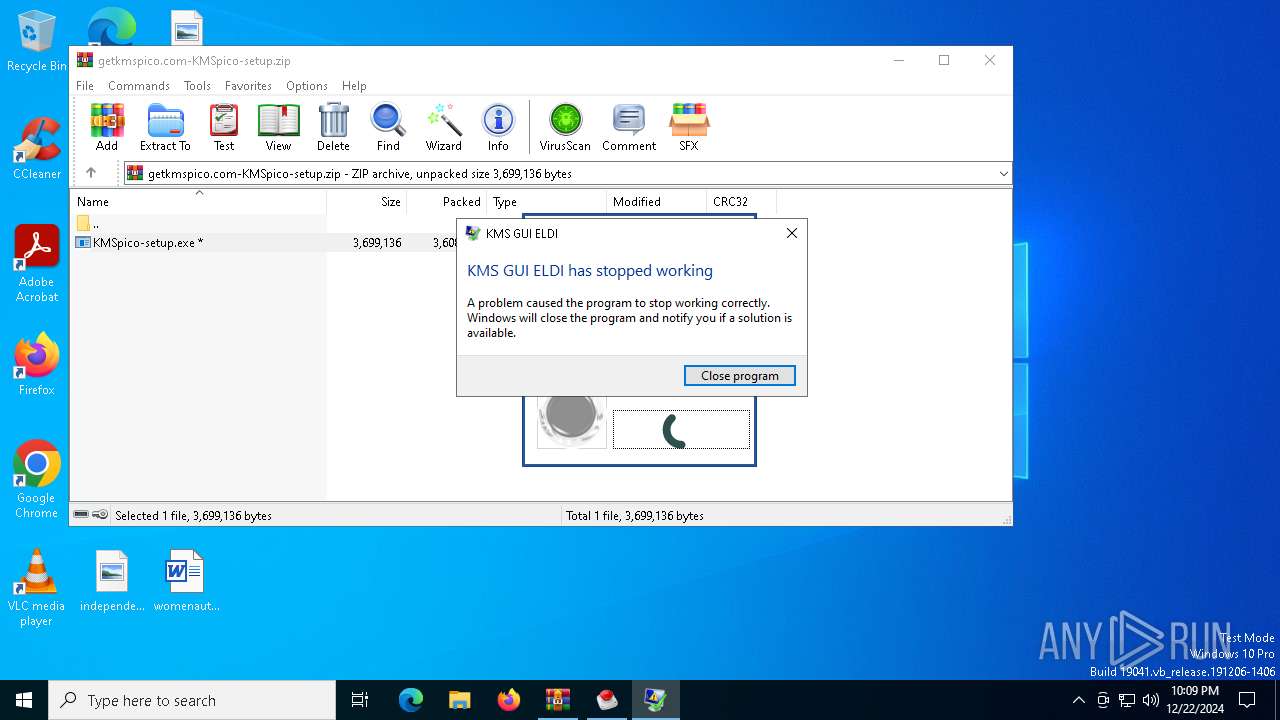
Executes application which crashes
- KMSELDI.exe (PID: 6316)
Takes ownership (TAKEOWN.EXE)
- KMSELDI.exe (PID: 6316)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6352)
- KMSpico-setup.tmp (PID: 4008)
Checks supported languages
- SearchApp.exe (PID: 5064)
- KMSpico-setup.tmp (PID: 3488)
- KMSpico-setup.exe (PID: 7156)
- KMSpico-setup.tmp (PID: 4008)
- KMSpico-setup.exe (PID: 6300)
- KMSpico-setup.exe (PID: 6484)
- KMSpico-setup.tmp (PID: 4932)
- _setup.exe (PID: 5640)
- _setup.tmp (PID: 5728)
- UninsHs.exe (PID: 396)
- KMSELDI.exe (PID: 5696)
- AutoPico.exe (PID: 6480)
- SECOH-QAD.exe (PID: 5432)
- KMSELDI.exe (PID: 6572)
- KMSELDI.exe (PID: 6316)
- AutoPico.exe (PID: 6740)
- SECOH-QAD.exe (PID: 6056)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6352)
Create files in a temporary directory
- KMSpico-setup.exe (PID: 7156)
- KMSpico-setup.exe (PID: 6300)
- KMSpico-setup.tmp (PID: 4008)
- KMSpico-setup.exe (PID: 6484)
- KMSpico-setup.tmp (PID: 4932)
- _setup.tmp (PID: 5728)
- _setup.exe (PID: 5640)
Reads the computer name
- KMSpico-setup.tmp (PID: 3488)
- KMSpico-setup.tmp (PID: 4008)
- KMSpico-setup.tmp (PID: 4932)
- _setup.tmp (PID: 5728)
- KMSELDI.exe (PID: 5696)
- AutoPico.exe (PID: 6480)
- KMSELDI.exe (PID: 6572)
- KMSELDI.exe (PID: 6316)
- AutoPico.exe (PID: 6740)
Process checks computer location settings
- KMSpico-setup.tmp (PID: 3488)
- KMSpico-setup.tmp (PID: 4008)
- SearchApp.exe (PID: 5064)
Creates files in the program directory
- KMSpico-setup.tmp (PID: 4932)
- _setup.tmp (PID: 5728)
- KMSELDI.exe (PID: 5696)
- AutoPico.exe (PID: 6480)
- KMSELDI.exe (PID: 6572)
- KMSELDI.exe (PID: 6316)
- AutoPico.exe (PID: 6740)
Creates a software uninstall entry
- _setup.tmp (PID: 5728)
The sample compiled with english language support
- _setup.tmp (PID: 5728)
Reads the machine GUID from the registry
- KMSELDI.exe (PID: 5696)
- AutoPico.exe (PID: 6480)
- SearchApp.exe (PID: 5064)
- KMSELDI.exe (PID: 6572)
- KMSELDI.exe (PID: 6316)
- AutoPico.exe (PID: 6740)
Reads product name
- KMSELDI.exe (PID: 5696)
- AutoPico.exe (PID: 6480)
- KMSELDI.exe (PID: 6572)
- KMSELDI.exe (PID: 6316)
- AutoPico.exe (PID: 6740)
Reads Environment values
- KMSELDI.exe (PID: 5696)
- AutoPico.exe (PID: 6480)
- KMSELDI.exe (PID: 6316)
- KMSELDI.exe (PID: 6572)
- AutoPico.exe (PID: 6740)
Reads Microsoft Office registry keys
- KMSELDI.exe (PID: 5696)
- AutoPico.exe (PID: 6480)
- KMSELDI.exe (PID: 6572)
- KMSELDI.exe (PID: 6316)
- AutoPico.exe (PID: 6740)
Reads the software policy settings
- SearchApp.exe (PID: 5064)
- WerFault.exe (PID: 3000)
Manual execution by a user
- KMSELDI.exe (PID: 6696)
- KMSELDI.exe (PID: 6572)
- KMSELDI.exe (PID: 5876)
- KMSELDI.exe (PID: 6316)
- AutoPico.exe (PID: 372)
- AutoPico.exe (PID: 6740)
Creates files or folders in the user directory
- WerFault.exe (PID: 3000)
Checks proxy server information
- WerFault.exe (PID: 3000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:02:26 20:36:14 |
| ZipCRC: | 0x46df3661 |
| ZipCompressedSize: | 3608887 |
| ZipUncompressedSize: | 3699136 |
| ZipFileName: | KMSpico-setup.exe |
Total processes
312
Monitored processes
177
Malicious processes
11
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\WINDOWS\system32\CheckNetIsolation.exe" LoopbackExempt -a -n=Microsoft.Windows.ShellExperienceHost_cw5n1h2txyewy | C:\Windows\SysWOW64\CheckNetIsolation.exe | — | KMSpico-setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: AppContainer Network Isolation Diagnostic Tool Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 128 | "C:\WINDOWS\System32\icacls.exe" C:\WINDOWS\System32\spp\store\2.0\cache\cache.dat /grant :r administrators:(d,f) | C:\Windows\System32\icacls.exe | — | KMSELDI.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 132 | "C:\WINDOWS\system32\CheckNetIsolation.exe" LoopbackExempt -a -n=NcsiUwpApp_8wekyb3d8bbwe | C:\Windows\SysWOW64\CheckNetIsolation.exe | — | KMSpico-setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: AppContainer Network Isolation Diagnostic Tool Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 188 | "C:\WINDOWS\system32\CheckNetIsolation.exe" LoopbackExempt -a -n=Microsoft.XboxGamingOverlay_8wekyb3d8bbwe | C:\Windows\SysWOW64\CheckNetIsolation.exe | — | KMSpico-setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: AppContainer Network Isolation Diagnostic Tool Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 204 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | SECOH-QAD.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | CheckNetIsolation.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 244 | "C:\WINDOWS\System32\SLUI.exe" RuleId=379cccfb-d4e0-48fe-b0f2-0136097be147;Action=CleanupState;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 372 | "C:\Program Files\KMSpico\AutoPico.exe" | C:\Program Files\KMSpico\AutoPico.exe | — | explorer.exe | |||||||||||
User: admin Company: @ByELDI Integrity Level: MEDIUM Description: AutoPico Exit code: 3221226540 Version: 16.1.0.0 Modules
| |||||||||||||||
| 396 | "C:\Program Files\KMSpico\UninsHs.exe" /r0=KMSpico,default,C:\Users\admin\AppData\Local\Temp\is-HITGO.tmp\_setup.exe | C:\Program Files\KMSpico\UninsHs.exe | — | _setup.tmp | |||||||||||
User: admin Company: Han-soft Integrity Level: HIGH Description: Uninstall for InnoSetup by Han-soft Exit code: 0 Version: 2.1.0.283 Modules
| |||||||||||||||
| 444 | "C:\WINDOWS\system32\CheckNetIsolation.exe" LoopbackExempt -a -n=Microsoft.549981C3F5F10_8wekyb3d8bbwe | C:\Windows\SysWOW64\CheckNetIsolation.exe | — | KMSpico-setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: AppContainer Network Isolation Diagnostic Tool Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
26 765
Read events
26 374
Write events
366
Delete events
25
Modification events
| (PID) Process: | (6352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\getkmspico.com-KMSpico-setup.zip | |||
| (PID) Process: | (6352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicText |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicTextTruncated |
Value: | |||
Executable files
39
Suspicious files
53
Text files
741
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{b8b1e24f-2898-44c4-861b-2c1a0edd7edd}\0.1.filtertrie.intermediate.txt | text | |
MD5:34BD1DFB9F72CF4F86E6DF6DA0A9E49A | SHA256:8E1E6A3D56796A245D0C7B0849548932FEE803BBDB03F6E289495830E017F14C | |||
| 4008 | KMSpico-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-934UI.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6484 | KMSpico-setup.exe | C:\Users\admin\AppData\Local\Temp\is-K299B.tmp\KMSpico-setup.tmp | executable | |
MD5:9220AABFA74A0D9ACCFEC48F5B668A41 | SHA256:305C3D26326BFC3582B4056C20F31819E6F4B95A54A3BC5A7971ECBB86F00BD7 | |||
| 6300 | KMSpico-setup.exe | C:\Users\admin\AppData\Local\Temp\is-BE8F4.tmp\KMSpico-setup.tmp | executable | |
MD5:9220AABFA74A0D9ACCFEC48F5B668A41 | SHA256:305C3D26326BFC3582B4056C20F31819E6F4B95A54A3BC5A7971ECBB86F00BD7 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{b8b1e24f-2898-44c4-861b-2c1a0edd7edd}\Apps.ft | binary | |
MD5:AB5CF5D309581951ACE7978FF8DF0FF0 | SHA256:CA45CAA7DE38CB805EC43EDC8B9332E1E95124A27FBB6E5BD3DDD5E8A526AFC7 | |||
| 4008 | KMSpico-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-934UI.tmp\idp.dll | executable | |
MD5:8F995688085BCED38BA7795F60A5E1D3 | SHA256:203D7B61EAC96DE865AB3B586160E72C78D93AB5532B13D50EF27174126FD006 | |||
| 4932 | KMSpico-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-HITGO.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 7156 | KMSpico-setup.exe | C:\Users\admin\AppData\Local\Temp\is-9GN6H.tmp\KMSpico-setup.tmp | executable | |
MD5:9220AABFA74A0D9ACCFEC48F5B668A41 | SHA256:305C3D26326BFC3582B4056C20F31819E6F4B95A54A3BC5A7971ECBB86F00BD7 | |||
| 5728 | _setup.tmp | C:\Users\admin\AppData\Local\Temp\is-H5B8Q.tmp\_isetup\_setup64.tmp | executable | |
MD5:526426126AE5D326D0A24706C77D8C5C | SHA256:B20A8D88C550981137ED831F2015F5F11517AEB649C29642D9D61DEA5EBC37D1 | |||
| 4932 | KMSpico-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-HITGO.tmp\idp.dll | executable | |
MD5:8F995688085BCED38BA7795F60A5E1D3 | SHA256:203D7B61EAC96DE865AB3B586160E72C78D93AB5532B13D50EF27174126FD006 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
54
DNS requests
37
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3508 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3508 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3000 | WerFault.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3224 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3224 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3508 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3508 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.140:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |