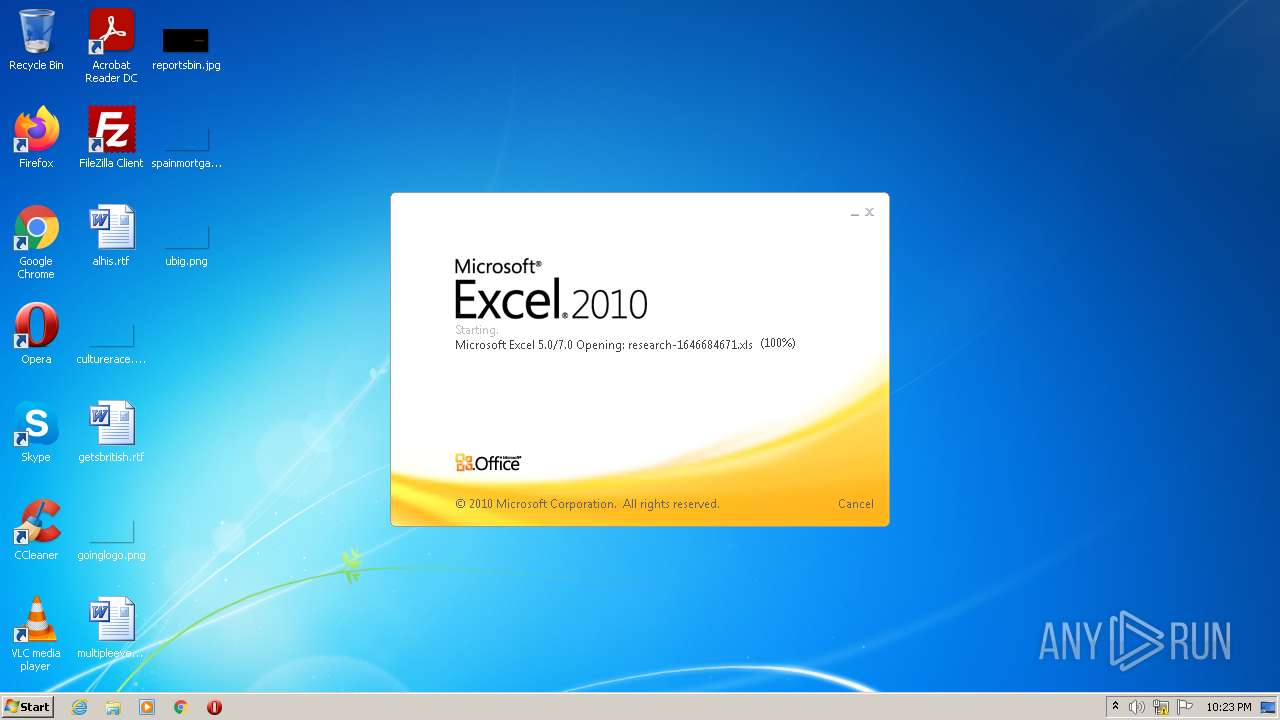
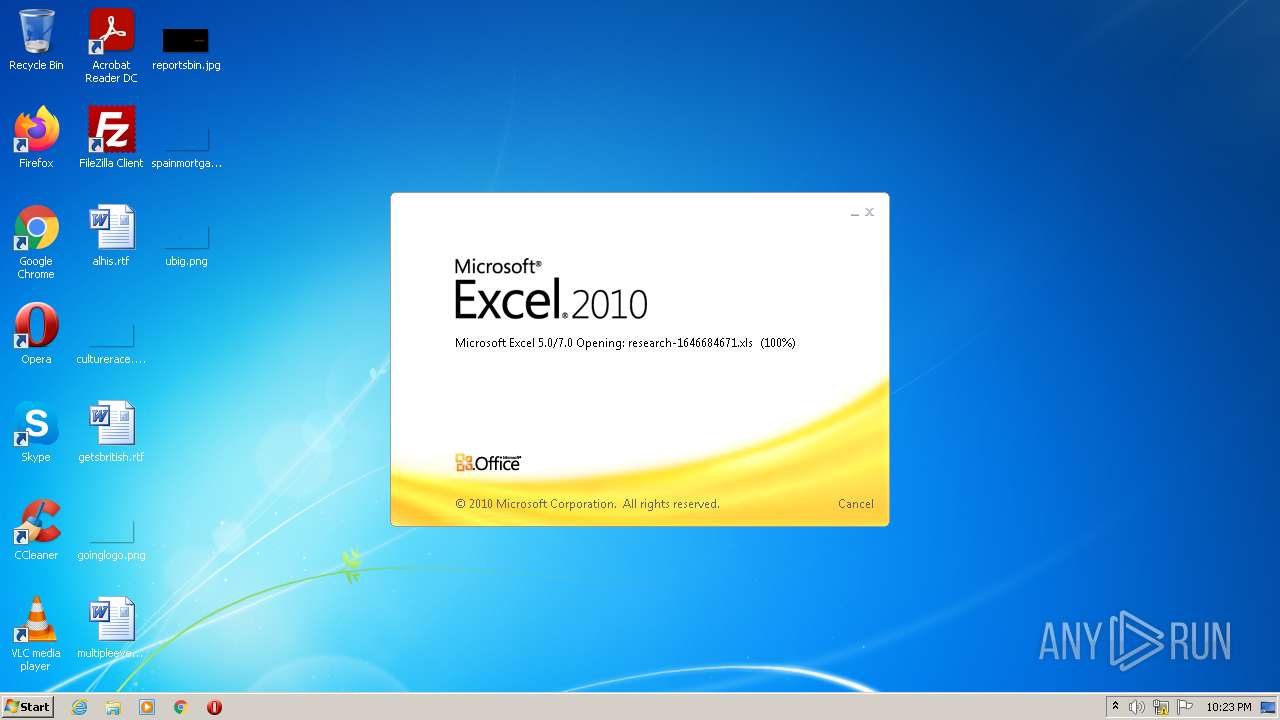
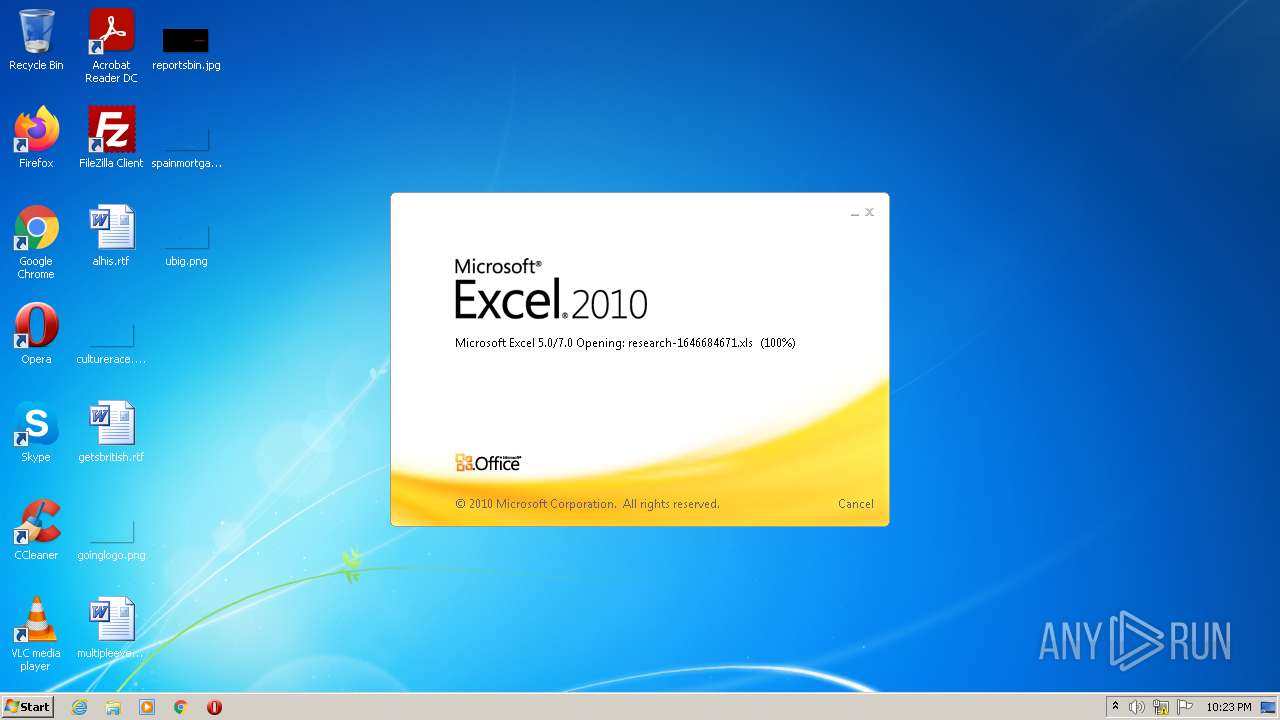
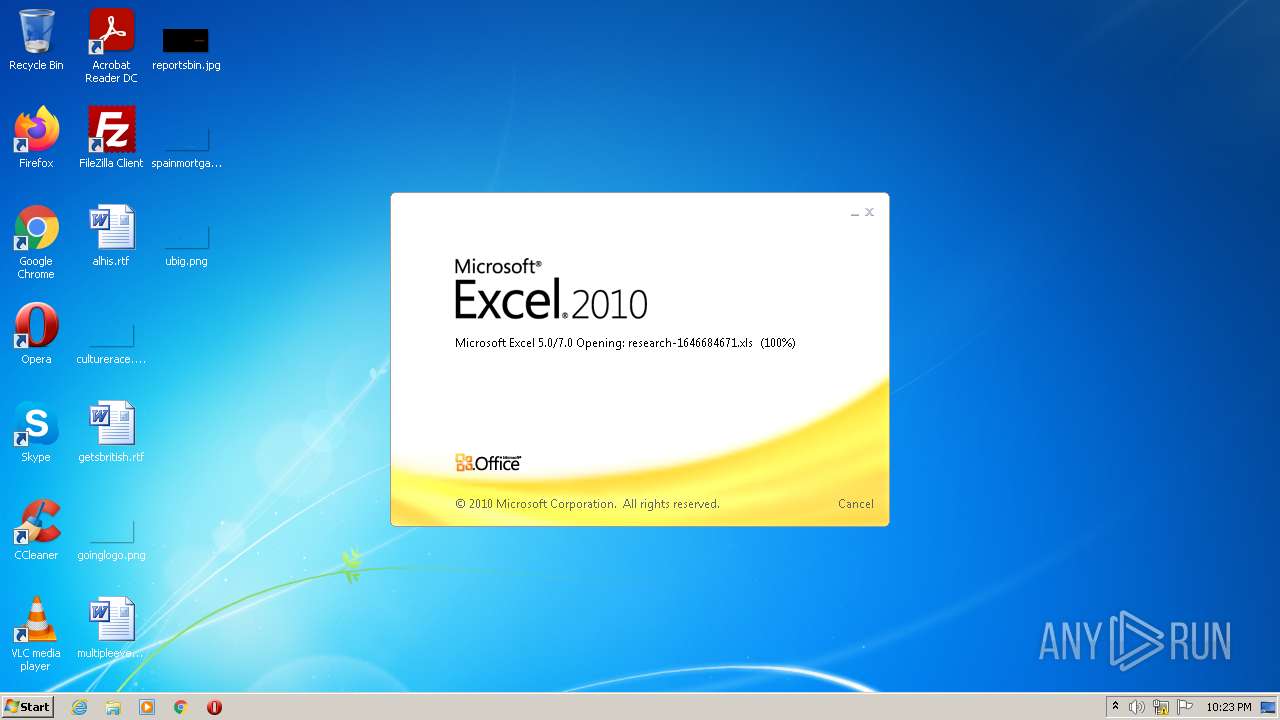
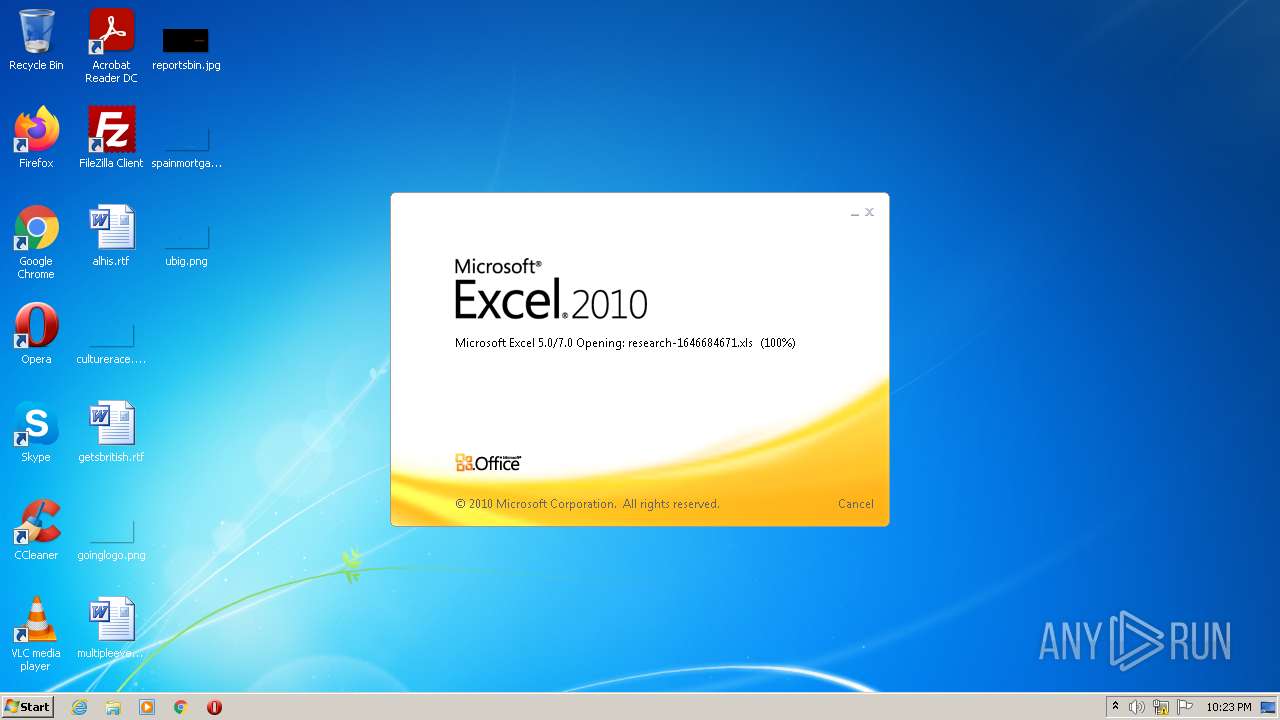
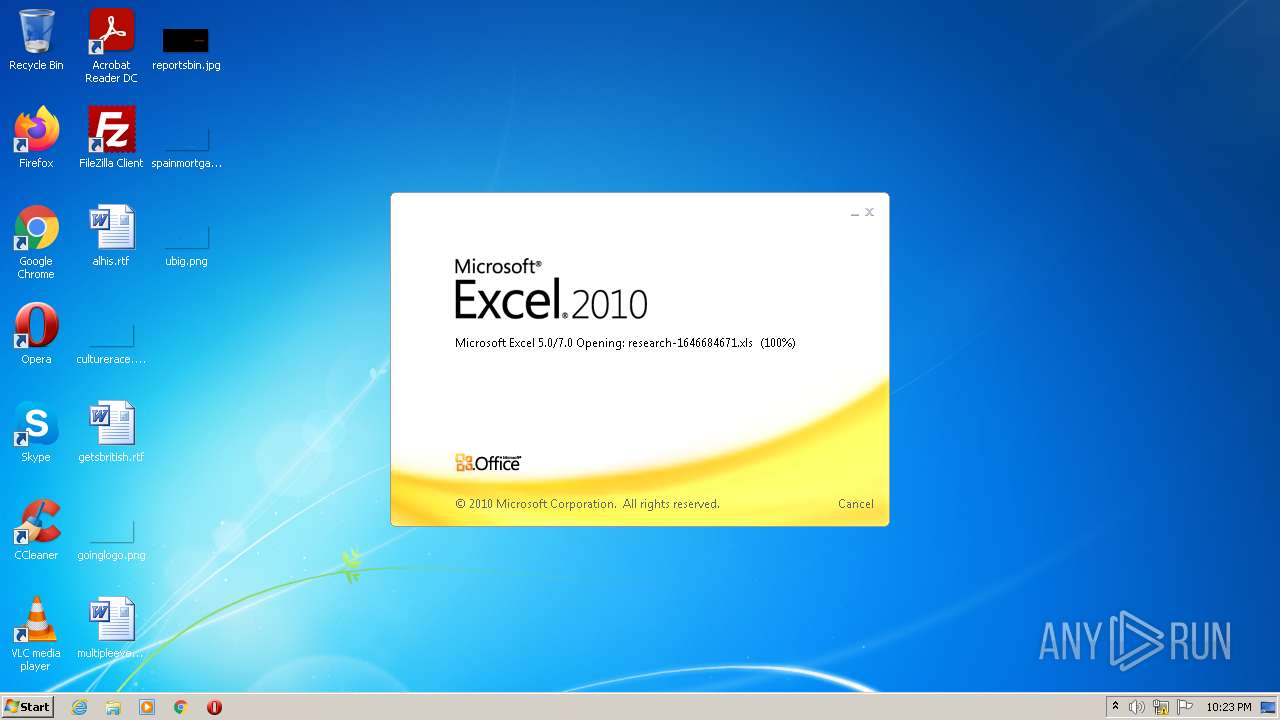
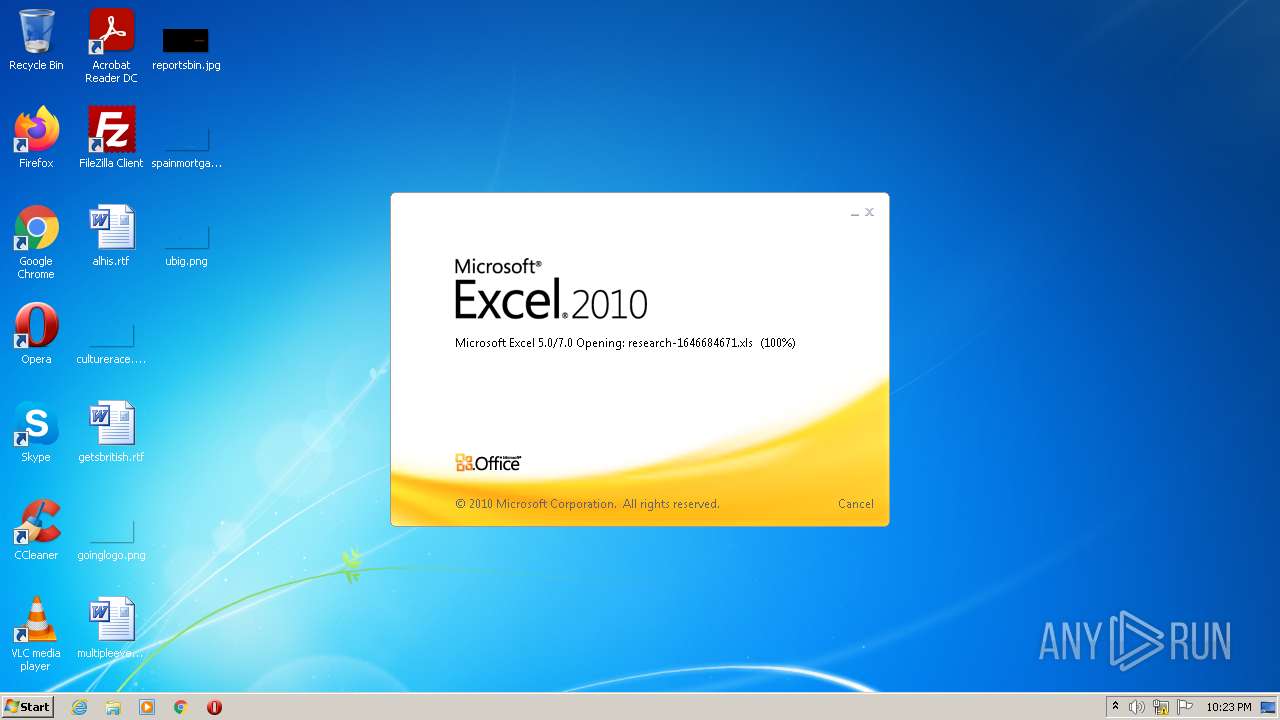
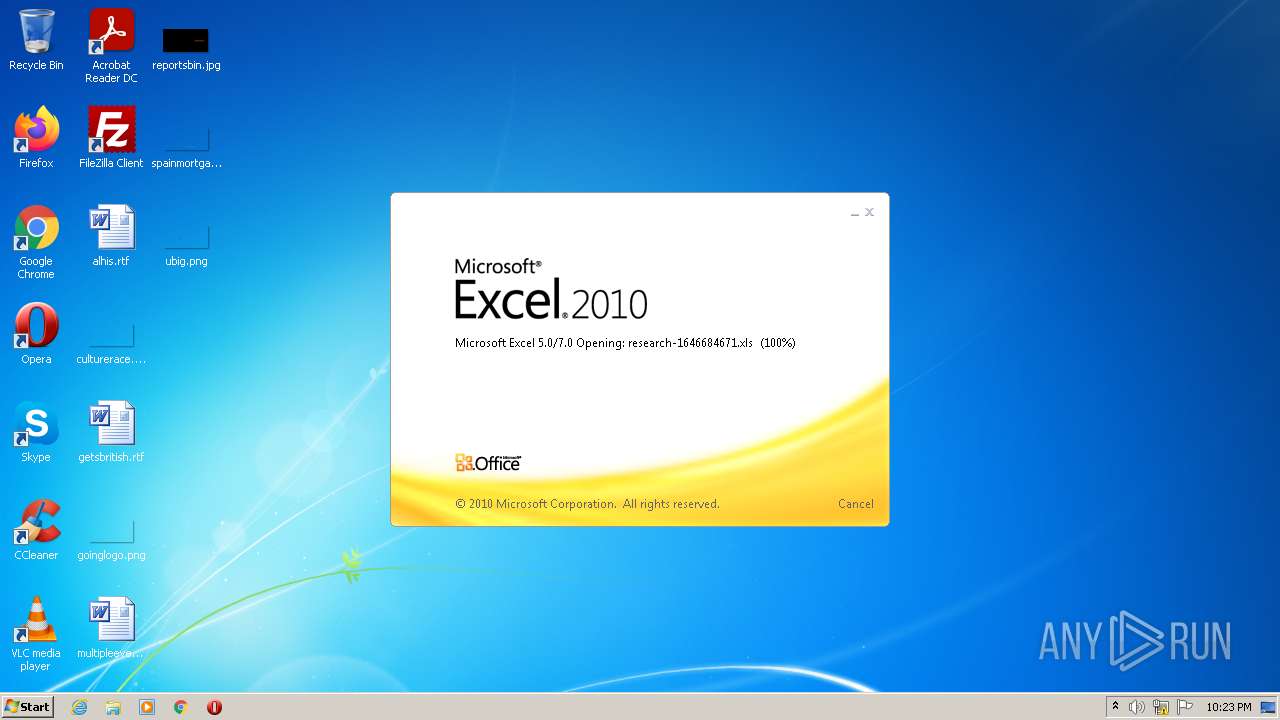
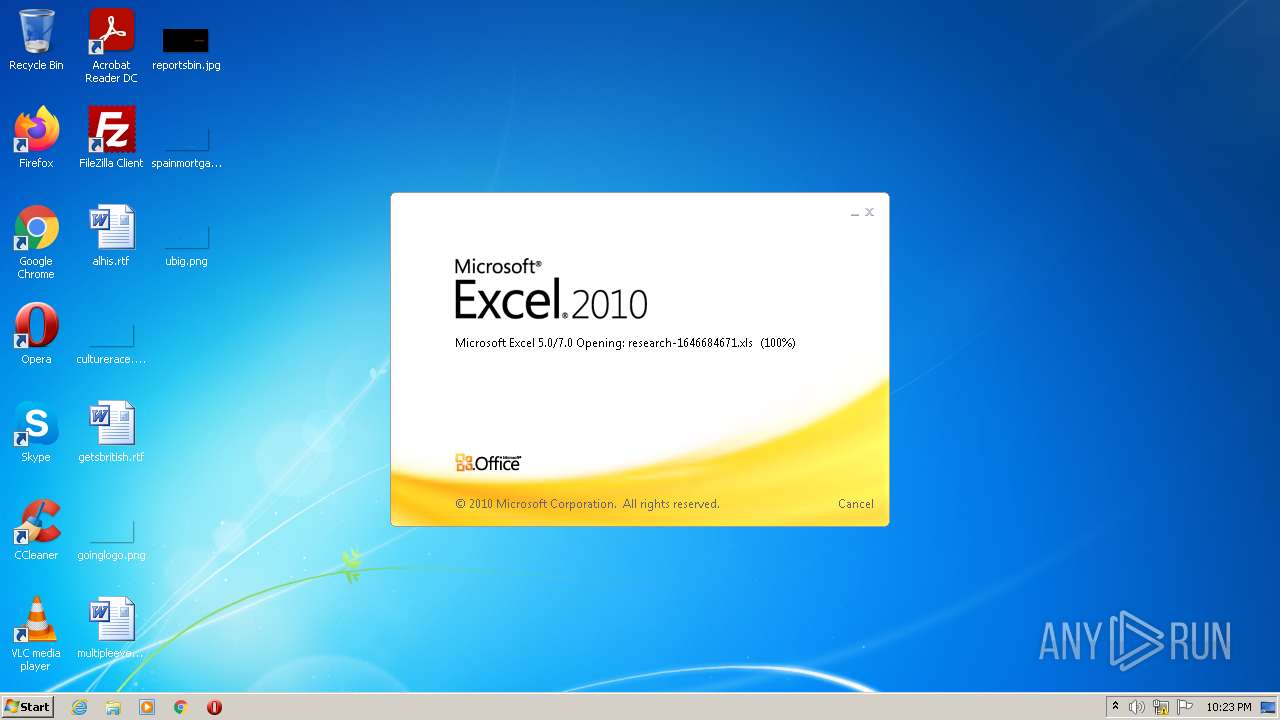
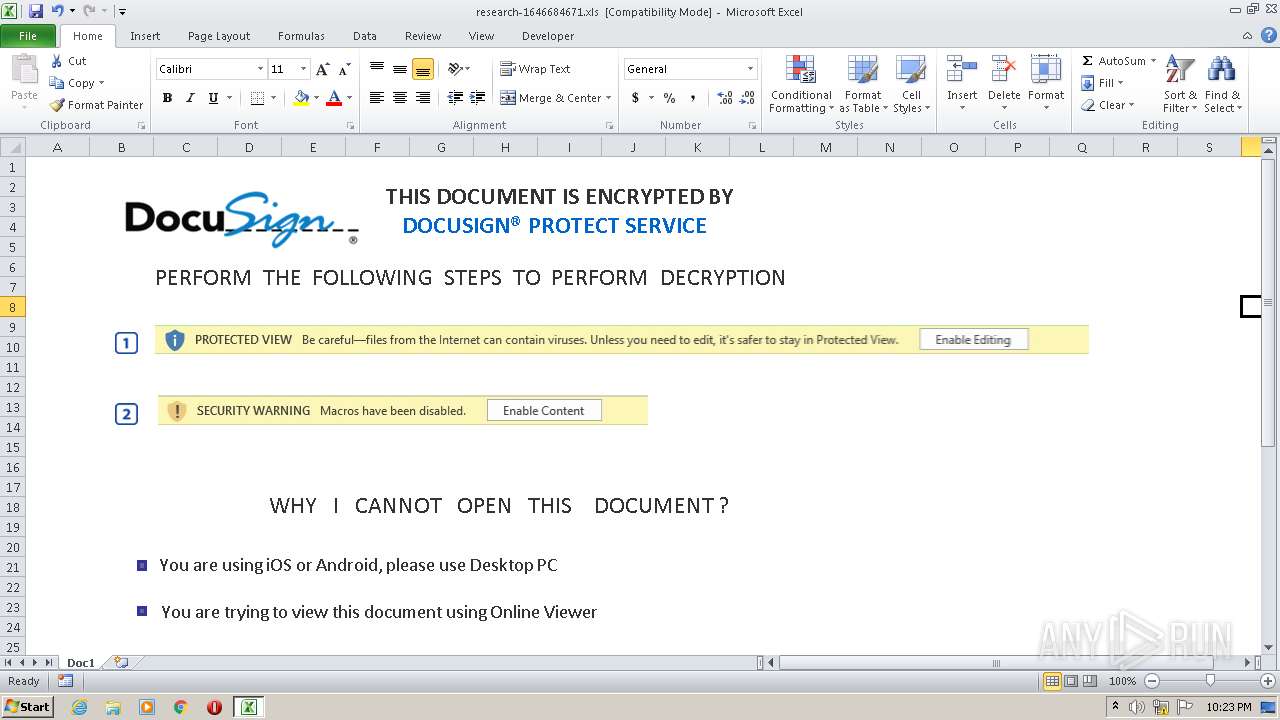
| File name: | research-1646684671.xls |
| Full analysis: | https://app.any.run/tasks/c4210bc2-1ada-411f-a98f-040ac7f3a6f6 |
| Verdict: | Suspicious activity |
| Analysis date: | January 15, 2022, 22:23:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Last Saved By: Amanda, Name of Creating Application: Microsoft Excel, Create Time/Date: Fri Jun 5 19:17:20 2015, Last Saved Time/Date: Sun Jun 13 10:24:55 2021, Security: 0 |
| MD5: | B775CD8BE83696CA37B2FE00BCB40574 |
| SHA1: | 60C8A9FDF2B24F8FB4913D4745A8557DF5FF8E07 |
| SHA256: | 1DF68D55968BB9D2DB4D0D18155188A03A442850FF543C8595166AC6987DF820 |
| SSDEEP: | 6144:Hknl9oBdySAx76F6XeyTVtW/9Ny9ABnl5/PBgxOHjuM9Mn:jl5/WxIji |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- EXCEL.EXE (PID: 1988)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 1988)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- EXCEL.EXE (PID: 1988)
- regsvr32.exe (PID: 2744)
- regsvr32.exe (PID: 1696)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 1988)
Reads the computer name
- EXCEL.EXE (PID: 1988)
Checks Windows Trust Settings
- EXCEL.EXE (PID: 1988)
Reads settings of System Certificates
- EXCEL.EXE (PID: 1988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| HeadingPairs: |
|
|---|---|
| TitleOfParts: |
|
| LinksUpToDate: | No |
| ScaleCrop: | No |
| Company: | - |
| CodePage: | Windows Latin 1 (Western European) |
| Security: | None |
| ModifyDate: | 2021:06:13 09:24:55 |
| CreateDate: | 2015:06:05 18:17:20 |
| Software: | Microsoft Excel |
| LastModifiedBy: | Amanda |
| Author: | - |
Total processes
38
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1696 | regsvr32 -s ..\iroto1.dll | C:\Windows\system32\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1988 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2744 | regsvr32 -s ..\iroto.dll | C:\Windows\system32\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 860
Read events
5 782
Write events
67
Delete events
11
Modification events
| (PID) Process: | (1988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | h4< |
Value: 68343C00C4070000010000000000000000000000 | |||
| (PID) Process: | (1988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
4
Text files
2
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1988 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRE468.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1988 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 1988 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 1988 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7D050A5DEFFE6693AC415A8090B3CB9C | binary | |
MD5:— | SHA256:— | |||
| 1988 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\suspendedpage[1].htm | html | |
MD5:1842EED13FDDC700A50ADADA08A0F84D | SHA256:47AC9EEF48022403111F9CEF6871AF594079ACDD88DA83E7D2B2A92FA47F7368 | |||
| 1988 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1988 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:54E9306F95F32E50CCD58AF19753D929 | SHA256:45F94DCEB18A8F738A26DA09CE4558995A4FE02B971882E8116FC9B59813BB72 | |||
| 1988 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7D050A5DEFFE6693AC415A8090B3CB9C | der | |
MD5:— | SHA256:— | |||
| 1988 | EXCEL.EXE | C:\Users\admin\iroto1.dll | html | |
MD5:1842EED13FDDC700A50ADADA08A0F84D | SHA256:47AC9EEF48022403111F9CEF6871AF594079ACDD88DA83E7D2B2A92FA47F7368 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
10
DNS requests
7
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1988 | EXCEL.EXE | GET | 200 | 95.101.89.75:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgSTEyvN51KAbxDQ9iQfKIWreQ%3D%3D | unknown | der | 503 b | shared |
1988 | EXCEL.EXE | GET | 200 | 23.45.105.185:80 | http://x1.c.lencr.org/ | NL | der | 717 b | whitelisted |
1988 | EXCEL.EXE | GET | 200 | 2.16.186.56:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?cb926953e41013fd | unknown | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1988 | EXCEL.EXE | 188.213.19.81:443 | nws.visionconsulting.ro | Voxility S.R.L. | RO | suspicious |
1988 | EXCEL.EXE | 23.45.105.185:80 | x1.c.lencr.org | Akamai International B.V. | NL | unknown |
1988 | EXCEL.EXE | 192.232.219.67:443 | royalpalm.sparkblue.lk | Unified Layer | US | malicious |
1988 | EXCEL.EXE | 2.16.186.56:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | whitelisted |
— | — | 95.101.89.75:80 | r3.o.lencr.org | Akamai International B.V. | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
nws.visionconsulting.ro |
| suspicious |
dns.msftncsi.com |
| shared |
royalpalm.sparkblue.lk |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1988 | EXCEL.EXE | Potentially Bad Traffic | ET INFO TLS Handshake Failure |