| File name: | 1dad6e730d5c249b9ed1217a4cc8e9b14efb9e3a8e12773bc6fea43760f8cc5b.exe |
| Full analysis: | https://app.any.run/tasks/5d4786bc-03ab-469e-81e5-a8b3193680bf |
| Verdict: | Malicious activity |
| Analysis date: | June 13, 2025, 11:02:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (DLL) (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 18656A812C03BE04E07DFD148F215B54 |
| SHA1: | 2582F567338B2FF417C162ACA295C1033CD1D173 |
| SHA256: | 1DAD6E730D5C249B9ED1217A4CC8E9B14EFB9E3A8E12773BC6FEA43760F8CC5B |
| SSDEEP: | 6144:43XT83g0d9HzlihtpT+FFAfqa9L8rqrG4qw:4nT83g0dm7T+FEqe8rMG4H |
MALICIOUS
Changes the autorun value in the registry
- CCleaner64.exe (PID: 3572)
SUSPICIOUS
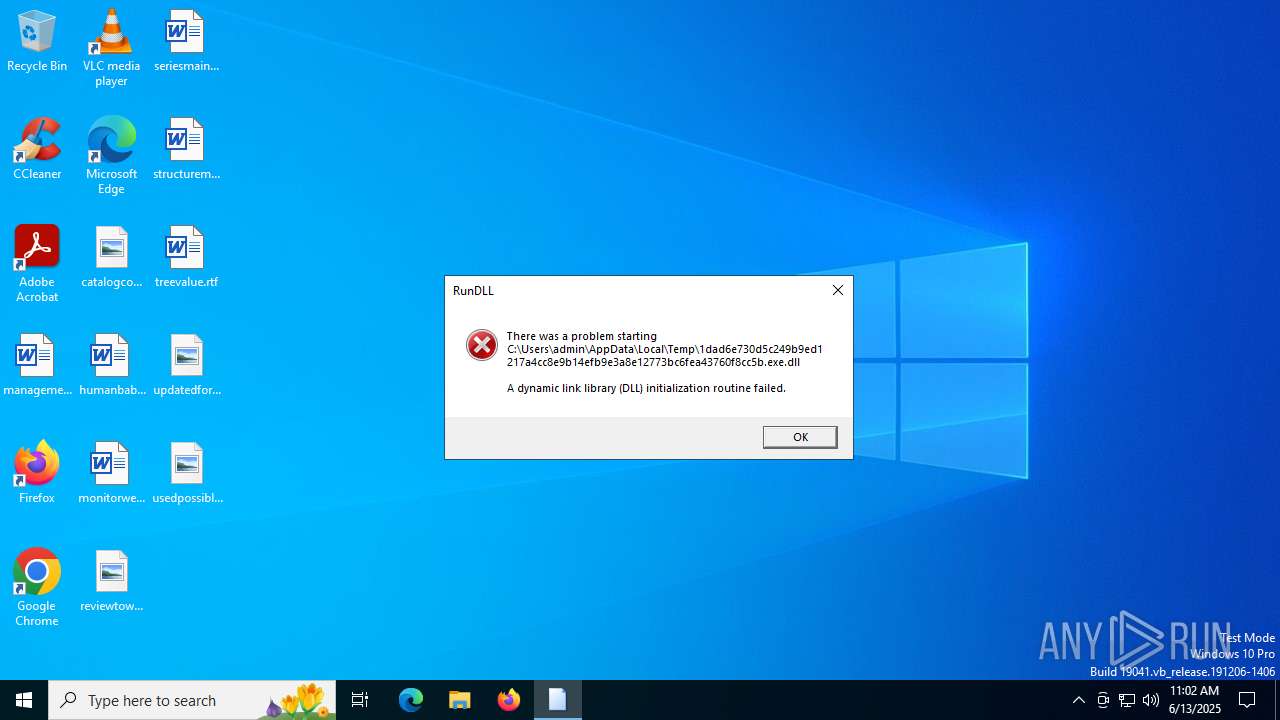
Executes application which crashes
- rundll32.exe (PID: 6188)
Reads the date of Windows installation
- CCleaner64.exe (PID: 3672)
- CCleaner64.exe (PID: 1068)
Reads security settings of Internet Explorer
- CCleaner64.exe (PID: 3672)
- CCleaner64.exe (PID: 1068)
- CCleaner64.exe (PID: 3572)
Application launched itself
- CCleaner64.exe (PID: 3672)
- CCleaner64.exe (PID: 1068)
Reads Internet Explorer settings
- CCleaner64.exe (PID: 1068)
- CCleaner64.exe (PID: 3572)
Executable content was dropped or overwritten
- CCleaner64.exe (PID: 1068)
- CCleaner64.exe (PID: 3572)
Checks for external IP
- CCleaner64.exe (PID: 1068)
The process verifies whether the antivirus software is installed
- CCleaner64.exe (PID: 3572)
Searches for installed software
- CCleaner64.exe (PID: 1068)
INFO
Manual execution by a user
- CCleaner64.exe (PID: 3672)
Creates files or folders in the user directory
- WerFault.exe (PID: 504)
- CCleaner64.exe (PID: 1068)
Checks supported languages
- CCleaner64.exe (PID: 3672)
- CCleaner64.exe (PID: 1068)
- CCleaner64.exe (PID: 3572)
Process checks computer location settings
- CCleaner64.exe (PID: 3672)
- CCleaner64.exe (PID: 1068)
Creates files in the program directory
- CCleaner64.exe (PID: 1068)
- CCleaner64.exe (PID: 3572)
Reads the computer name
- CCleaner64.exe (PID: 1068)
- CCleaner64.exe (PID: 3572)
Reads Environment values
- CCleaner64.exe (PID: 1068)
- CCleaner64.exe (PID: 3572)
The sample compiled with english language support
- CCleaner64.exe (PID: 1068)
- CCleaner64.exe (PID: 3572)
Reads CPU info
- CCleaner64.exe (PID: 1068)
- CCleaner64.exe (PID: 3572)
Reads the software policy settings
- CCleaner64.exe (PID: 1068)
- CCleaner64.exe (PID: 3572)
Reads product name
- CCleaner64.exe (PID: 1068)
- CCleaner64.exe (PID: 3572)
Checks proxy server information
- CCleaner64.exe (PID: 1068)
Launching a file from a Registry key
- CCleaner64.exe (PID: 3572)
Reads the machine GUID from the registry
- CCleaner64.exe (PID: 1068)
- CCleaner64.exe (PID: 3572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:12:29 02:43:28+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit, DLL |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 147456 |
| InitializedDataSize: | 61440 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1363a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
145
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 504 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6188 -s 616 | C:\Windows\SysWOW64\WerFault.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | "C:\Program Files\CCleaner\CCleaner64.exe" /uac | C:\Program Files\CCleaner\CCleaner64.exe | CCleaner64.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 6.20.0.10897 Modules
| |||||||||||||||
| 3572 | "C:\Program Files\CCleaner\CCleaner64.exe" /monitor | C:\Program Files\CCleaner\CCleaner64.exe | CCleaner64.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Version: 6.20.0.10897 Modules
| |||||||||||||||
| 3672 | "C:\Program Files\CCleaner\CCleaner64.exe" | C:\Program Files\CCleaner\CCleaner64.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 6.20.0.10897 Modules
| |||||||||||||||
| 6188 | "C:\WINDOWS\SysWOW64\rundll32.exe" C:\Users\admin\AppData\Local\Temp\1dad6e730d5c249b9ed1217a4cc8e9b14efb9e3a8e12773bc6fea43760f8cc5b.exe.dll, #1 | C:\Windows\SysWOW64\rundll32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 898
Read events
18 755
Write events
90
Delete events
53
Modification events
| (PID) Process: | (1068) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | DAST |
Value: 06/13/2025 11:03:21 | |||
| (PID) Process: | (1068) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | T8062 |
Value: 0 | |||
| (PID) Process: | (1068) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | UpdateBackground |
Value: 1 | |||
| (PID) Process: | (1068) CCleaner64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore |
| Operation: | write | Name: | SystemRestorePointCreationFrequency |
Value: 0 | |||
| (PID) Process: | (1068) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | NumOfOutdatedDrivers |
Value: 0 | |||
| (PID) Process: | (1068) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | delete value | Name: | GUID |
Value: | |||
| (PID) Process: | (1068) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | delete value | Name: | GD |
Value: | |||
| (PID) Process: | (1068) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | delete value | Name: | SetupGD |
Value: | |||
| (PID) Process: | (1068) CCleaner64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Piriform\CCleaner |
| Operation: | delete value | Name: | (Cfg)TTL |
Value: 86400 | |||
| (PID) Process: | (1068) CCleaner64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Piriform\CCleaner |
| Operation: | delete value | Name: | (Cfg)TTL-Spread |
Value: 43200 | |||
Executable files
5
Suspicious files
14
Text files
7
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 504 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_rundll32.exe_c9b05c5ec3b5431eec4ae531f55fc17c4c79e212_67c333ae_a1dd692e-7c1f-46d8-a700-d26e589b45a3\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1068 | CCleaner64.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ccc0fa1b9f86f7b3.customDestinations-ms~RF17fb38.TMP | binary | |
MD5:715D03F2C851242AE02F082C92170337 | SHA256:52F9047E9A072554A68045FD0215B8484C2D6D758FEE82543FBAA7C7F7D163D9 | |||
| 504 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5B7F.tmp.WERInternalMetadata.xml | xml | |
MD5:4164E7ECFE19DF8CF63775B1EEFE6363 | SHA256:C47AFE407569AF2D02041932FC70232450E370CE123BE56B664EF91A126186E2 | |||
| 504 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\rundll32.exe.6188.dmp | binary | |
MD5:733A25F8834224FC6BFC6291FE1B6958 | SHA256:9FD450995B54F679EF4CB490EDFEC4FBCA137EBFEFED60045356005EAA5AFD85 | |||
| 1068 | CCleaner64.exe | C:\Program Files\CCleaner\gcapi_17498126011068.dll | executable | |
MD5:F17F96322F8741FE86699963A1812897 | SHA256:8B6CE3A640E2D6F36B0001BE2A1ABB765AE51E62C314A15911E75138CBB544BB | |||
| 1068 | CCleaner64.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\ccupdate636_free[1].exe | — | |
MD5:— | SHA256:— | |||
| 1068 | CCleaner64.exe | C:\Program Files\CCleaner\temp_ccupdate\ccupdate636_free.exe | — | |
MD5:— | SHA256:— | |||
| 504 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5B9F.tmp.xml | xml | |
MD5:4720A2852CF65391010C4FD4FD83E02E | SHA256:ABB92467CB170C5B3C8BA08DB81528D423182EFFE3EA99FF0596B174B55BFC1D | |||
| 1068 | CCleaner64.exe | C:\Program Files\CCleaner\gcapi_dll.dll | executable | |
MD5:F17F96322F8741FE86699963A1812897 | SHA256:8B6CE3A640E2D6F36B0001BE2A1ABB765AE51E62C314A15911E75138CBB544BB | |||
| 504 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5B01.tmp.dmp | binary | |
MD5:7DE61412915E1FD9DEE9D765762DF8FF | SHA256:F66B63C1F046ECED3C10C5882A1DA760CACFD5D37DBE96AC920F8DD125CD6BF1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
36
DNS requests
25
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3768 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4460 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4460 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1068 | CCleaner64.exe | GET | 200 | 2.16.168.113:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | whitelisted |
1068 | CCleaner64.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
1068 | CCleaner64.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
1068 | CCleaner64.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEAXfj0A2M0oL7zuU%2F%2F2jetU%3D | unknown | — | — | whitelisted |
1068 | CCleaner64.exe | GET | 200 | 216.58.212.131:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1564 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3768 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3768 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
1068 | CCleaner64.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
Process | Message |
|---|---|
CCleaner64.exe | [2025-06-13 11:03:21.399] [error ] [ini_access ] [ 1068: 4224] [000000: 0] Incorrect ini_accessor configuration! Fixing relative input path to avoid recursion. Input was: Setup
|
CCleaner64.exe | [2025-06-13 11:03:21.399] [error ] [settings ] [ 1068: 4224] [000000: 0] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner64.exe | Failed to open log file 'C:\Program Files\CCleaner' |
CCleaner64.exe | OnLanguage - en
|
CCleaner64.exe | [2025-06-13 11:03:21.914] [error ] [settings ] [ 1068: 4372] [D2EC45: 356] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner64.exe | [2025-06-13 11:03:21.930] [error ] [Burger ] [ 1068: 4372] [904E07: 253] [23.2.1118.0] [BurgerReporter.cpp] [253] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner64.exe | [2025-06-13 11:03:21.930] [error ] [Burger ] [ 1068: 4372] [904E07: 253] [23.2.1118.0] [BurgerReporter.cpp] [253] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner64.exe | file:///tis/optimizer.tis(1131) : warning :'await' should be used only inside 'async' or 'event'
|
CCleaner64.exe | file:///tis/optimizer.tis(1288) : warning :'async' does not contain any 'await'
|
CCleaner64.exe | OnLanguage - en
|