| File name: | file.exe |
| Full analysis: | https://app.any.run/tasks/66bed568-4325-465a-ae4e-55e6d5a924a1 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 22:10:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 40F295E386339B4AE02193F5EA48FB17 |
| SHA1: | 1EA83AFAD29AC862DC32B8CF5510CDE15CFCDABC |
| SHA256: | 1DA36EE155F0D54953C50AC5E1289685E19FB7A7DE3980AD2CF3B0DFB36FFAD1 |
| SSDEEP: | 98304:aUH1VXh9YeK+vwW6V/g/vhgvDkuJbv1bmtR+wwrDLLXcAtPM3ghc7tHFFWCd1/ua:w2U11zLEz8MAKHIQHtRDzgwSzJ1jG |
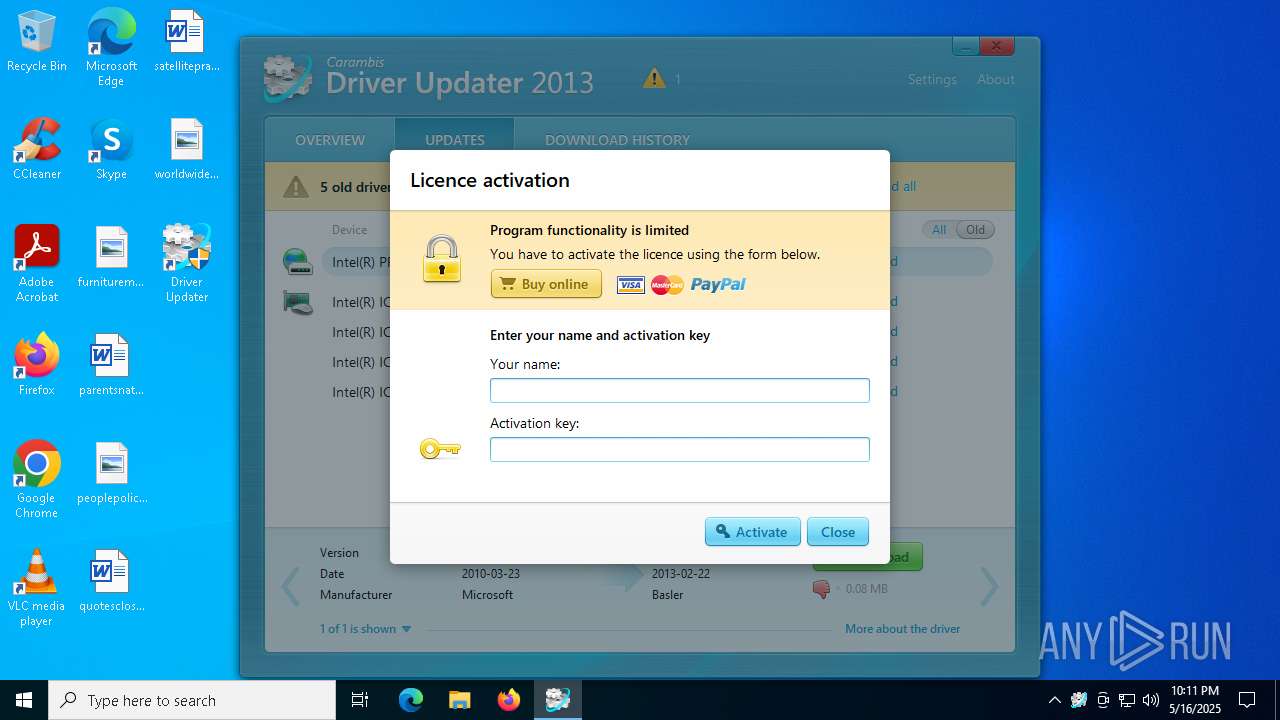
MALICIOUS
Executing a file with an untrusted certificate
- file.exe (PID: 864)
- file.exe (PID: 6640)
- vcredist_x86.exe (PID: 5384)
- Setup.exe (PID: 1328)
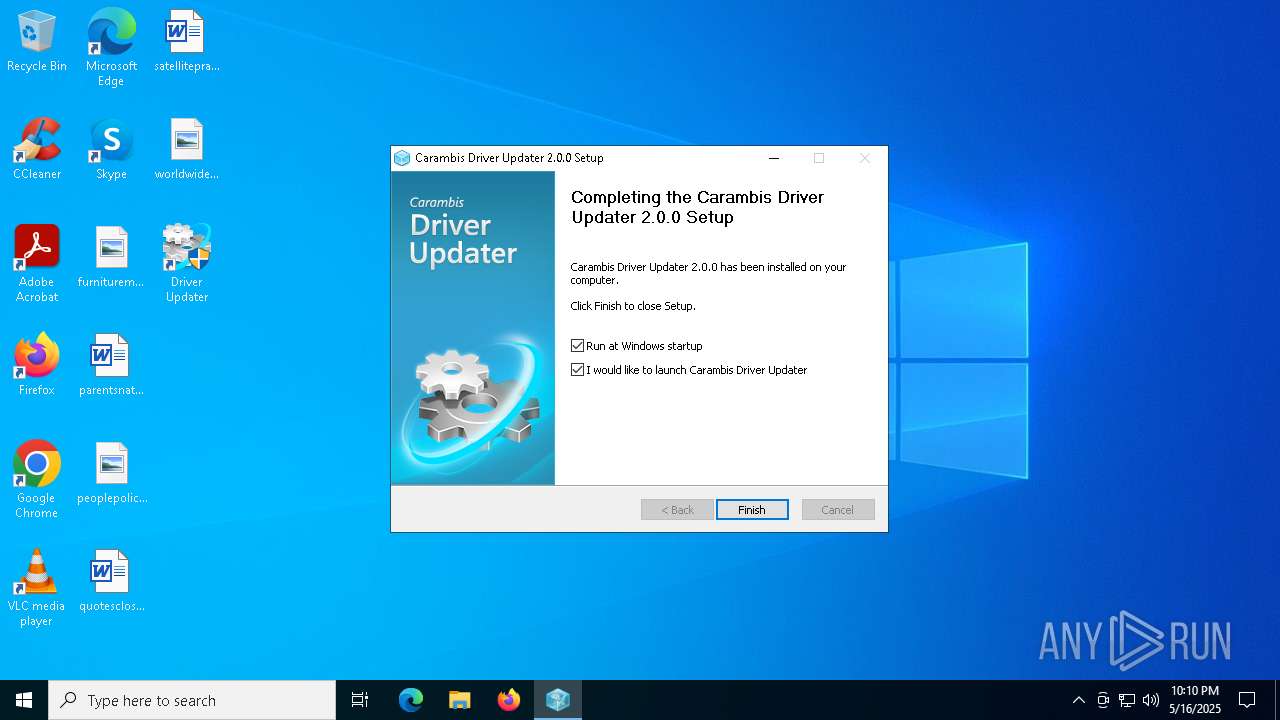
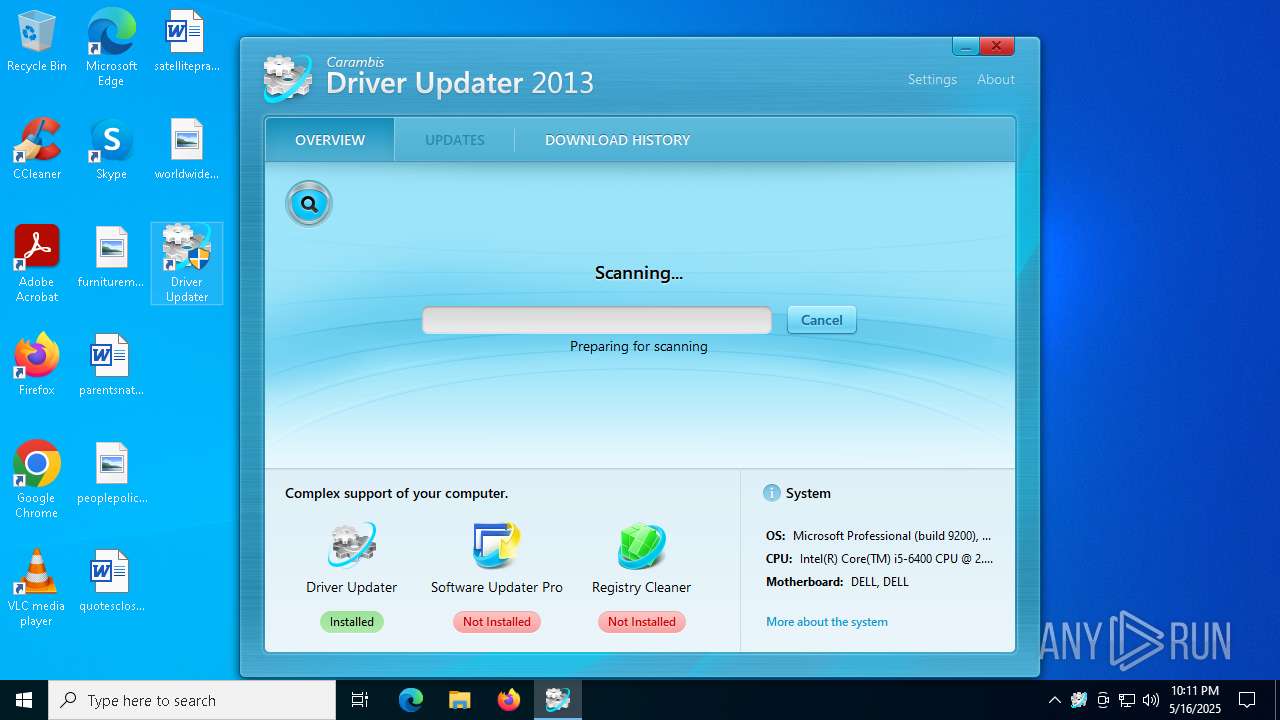
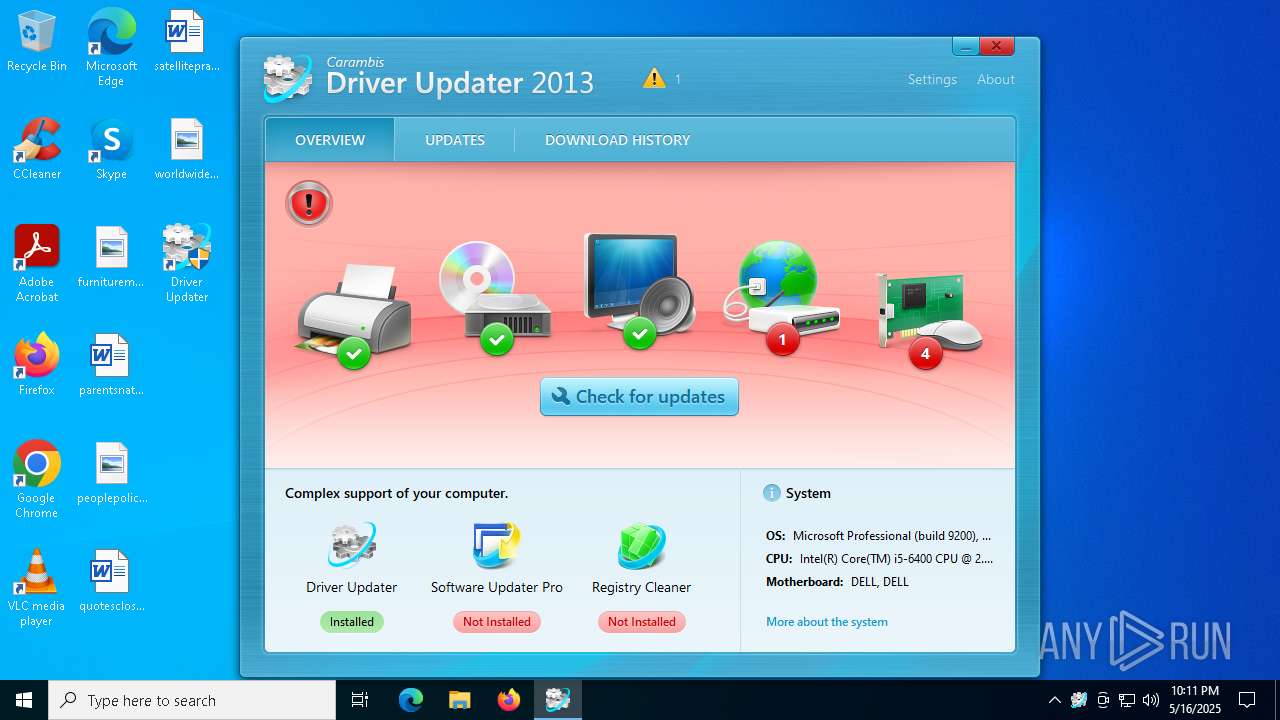
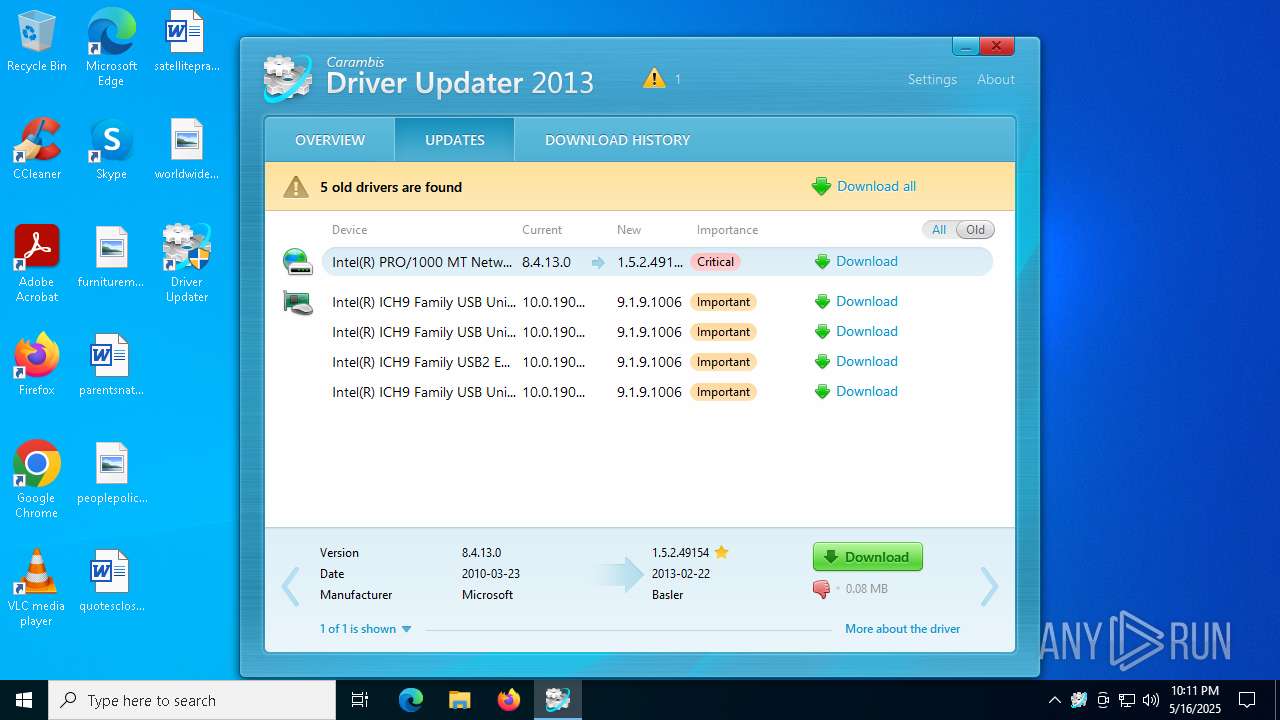
- dupdater.exe (PID: 5112)
- dupdater.exe (PID: 6164)
- Installer.exe (PID: 6732)
- Installer.exe (PID: 6856)
- Installer.exe (PID: 6972)
- Installer.exe (PID: 7020)
Changes the autorun value in the registry
- file.exe (PID: 864)
SUSPICIOUS
The process creates files with name similar to system file names
- file.exe (PID: 864)
Executable content was dropped or overwritten
- vcredist_x86.exe (PID: 5384)
- file.exe (PID: 864)
Creates file in the systems drive root
- vcredist_x86.exe (PID: 5384)
Process drops legitimate windows executable
- vcredist_x86.exe (PID: 5384)
- msiexec.exe (PID: 4188)
- file.exe (PID: 864)
Reads security settings of Internet Explorer
- Setup.exe (PID: 1328)
- CrashSender.exe (PID: 2904)
- dupdater.exe (PID: 5112)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 4188)
The process drops C-runtime libraries
- msiexec.exe (PID: 4188)
Creates a software uninstall entry
- file.exe (PID: 864)
Reads the BIOS version
- dupdater.exe (PID: 5112)
There is functionality for taking screenshot (YARA)
- dupdater.exe (PID: 5112)
- file.exe (PID: 864)
Malware-specific behavior (creating "System.dll" in Temp)
- file.exe (PID: 864)
INFO
Checks supported languages
- file.exe (PID: 864)
- vcredist_x86.exe (PID: 5384)
- Setup.exe (PID: 1328)
- msiexec.exe (PID: 4188)
- dupdater.exe (PID: 5112)
- CrashSender.exe (PID: 2904)
Creates files in the program directory
- file.exe (PID: 864)
- dupdater.exe (PID: 5112)
Creates files or folders in the user directory
- file.exe (PID: 864)
- msiexec.exe (PID: 4188)
- dupdater.exe (PID: 5112)
Reads the machine GUID from the registry
- vcredist_x86.exe (PID: 5384)
- Setup.exe (PID: 1328)
- msiexec.exe (PID: 4188)
- dupdater.exe (PID: 5112)
The sample compiled with japanese language support
- vcredist_x86.exe (PID: 5384)
- msiexec.exe (PID: 4188)
Reads the computer name
- vcredist_x86.exe (PID: 5384)
- Setup.exe (PID: 1328)
- msiexec.exe (PID: 4188)
- dupdater.exe (PID: 5112)
- CrashSender.exe (PID: 2904)
- file.exe (PID: 864)
The sample compiled with english language support
- vcredist_x86.exe (PID: 5384)
- msiexec.exe (PID: 4188)
- file.exe (PID: 864)
The sample compiled with korean language support
- vcredist_x86.exe (PID: 5384)
- msiexec.exe (PID: 4188)
Create files in a temporary directory
- file.exe (PID: 864)
- Setup.exe (PID: 1328)
The sample compiled with Italian language support
- vcredist_x86.exe (PID: 5384)
- msiexec.exe (PID: 4188)
The sample compiled with chinese language support
- vcredist_x86.exe (PID: 5384)
- msiexec.exe (PID: 4188)
The sample compiled with spanish language support
- vcredist_x86.exe (PID: 5384)
- msiexec.exe (PID: 4188)
The sample compiled with french language support
- vcredist_x86.exe (PID: 5384)
- msiexec.exe (PID: 4188)
The sample compiled with german language support
- vcredist_x86.exe (PID: 5384)
- msiexec.exe (PID: 4188)
The sample compiled with russian language support
- vcredist_x86.exe (PID: 5384)
- msiexec.exe (PID: 4188)
Reads CPU info
- Setup.exe (PID: 1328)
- dupdater.exe (PID: 5112)
Reads the software policy settings
- msiexec.exe (PID: 4188)
- Setup.exe (PID: 1328)
- dupdater.exe (PID: 5112)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4188)
Creates a software uninstall entry
- msiexec.exe (PID: 4188)
Process checks whether UAC notifications are on
- dupdater.exe (PID: 5112)
Process checks computer location settings
- dupdater.exe (PID: 5112)
Manual execution by a user
- notepad++.exe (PID: 6604)
- Installer.exe (PID: 6732)
- Installer.exe (PID: 7020)
- dupdater.exe (PID: 6164)
- Installer.exe (PID: 6856)
- Installer.exe (PID: 6972)
- notepad++.exe (PID: 4748)
Themida protector has been detected
- dupdater.exe (PID: 5112)
UPX packer has been detected
- dupdater.exe (PID: 5112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:24 19:19:59+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 28672 |
| InitializedDataSize: | 445952 |
| UninitializedDataSize: | 16896 |
| EntryPoint: | 0x39e3 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
283
Monitored processes
15
Malicious processes
4
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | "C:\Users\admin\AppData\Local\Temp\file.exe" | C:\Users\admin\AppData\Local\Temp\file.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1328 | c:\a8faf183ba014f1b5d\Setup.exe /q /norestart | C:\a8faf183ba014f1b5d\Setup.exe | — | vcredist_x86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Installer Exit code: 0 Version: 10.0.30319.1 built by: RTMRel Modules
| |||||||||||||||
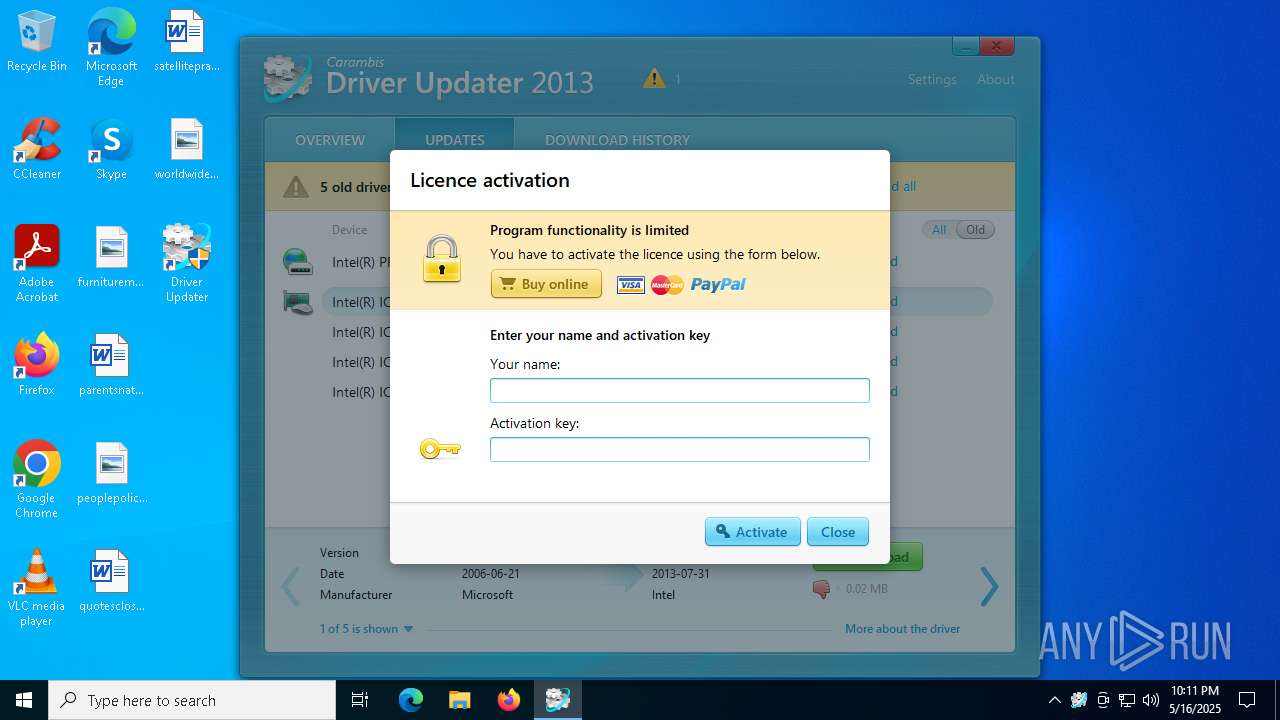
| 2904 | "C:\Users\admin\AppData\Roaming\Carambis\Driver Updater\crashereports\d20a335c-1287-454f-98ad-7038b671906d.xml" "C:\Users\admin\AppData\Roaming\Carambis\Driver Updater\crashereports\d20a335c-1287-454f-98ad-7038b671906d.xml" | C:\Program Files (x86)\Carambis\Driver Updater\CrashSender.exe | — | dupdater.exe | |||||||||||
User: admin Integrity Level: HIGH Description: CrashSender Module Exit code: 0 Version: 1, 2, 0, 7 Modules
| |||||||||||||||
| 4188 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
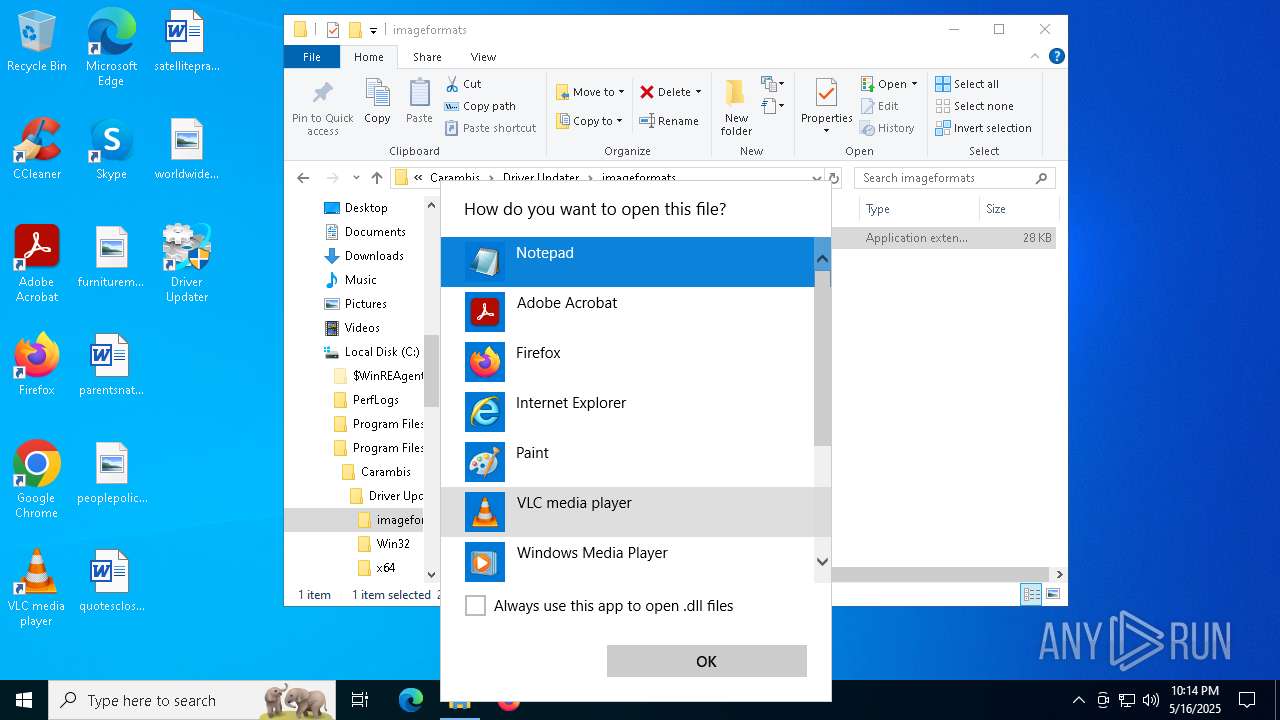
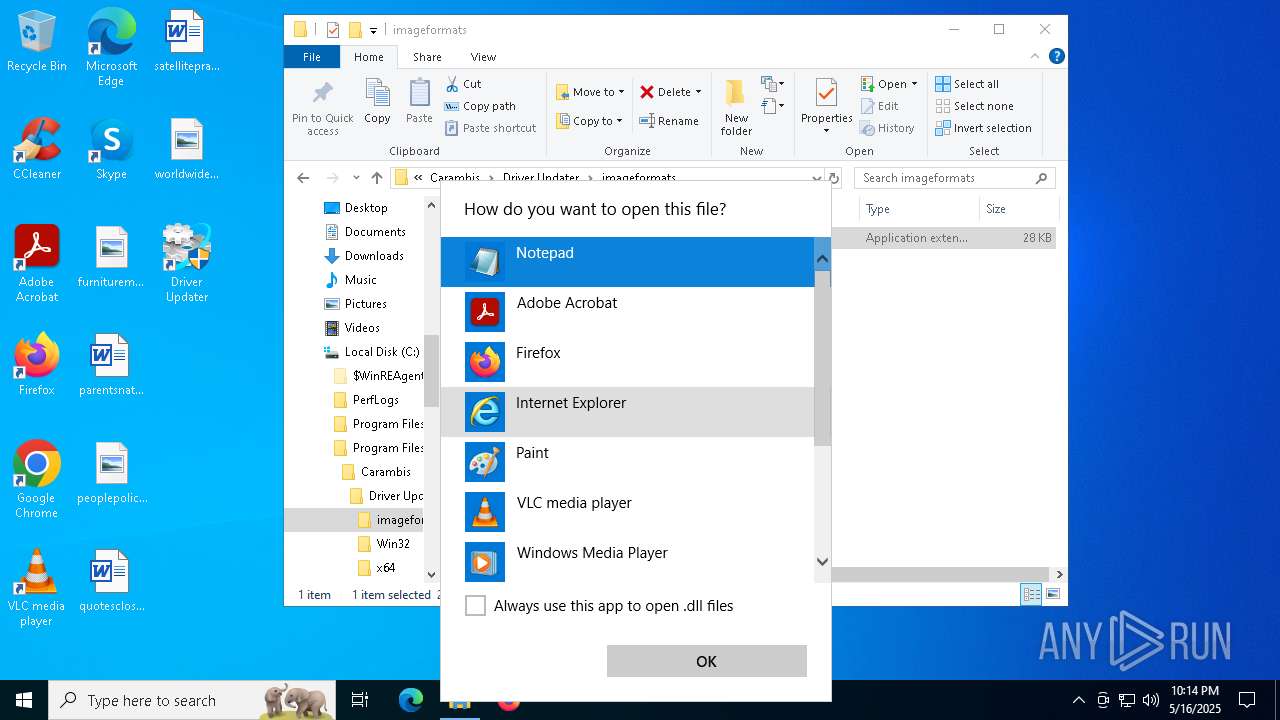
| 4748 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Program Files (x86)\Carambis\Driver Updater\imageformats\qico4.dll" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
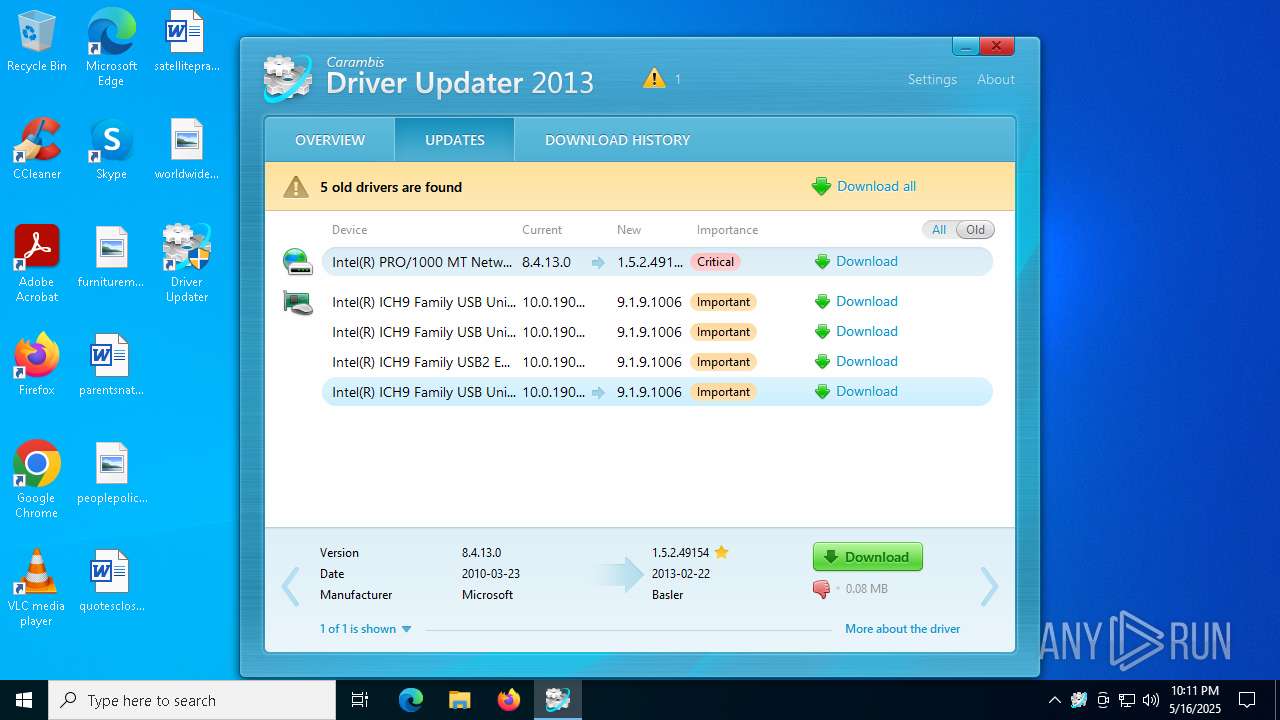
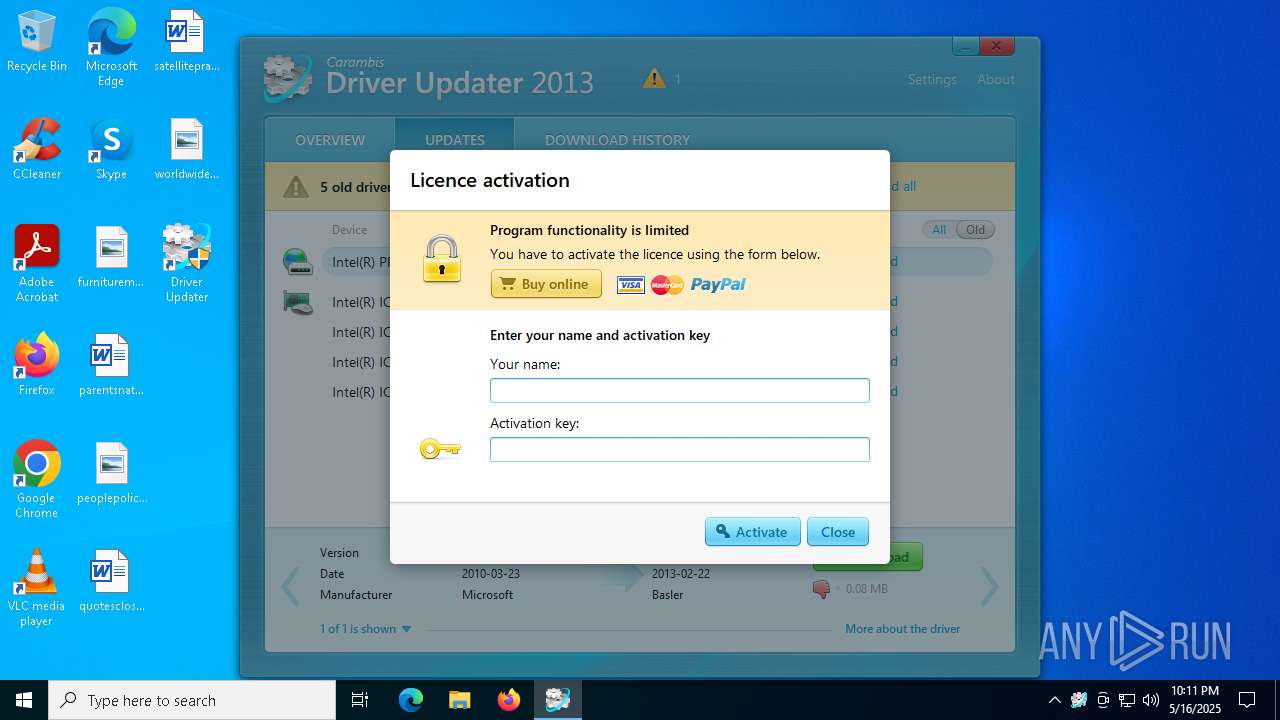
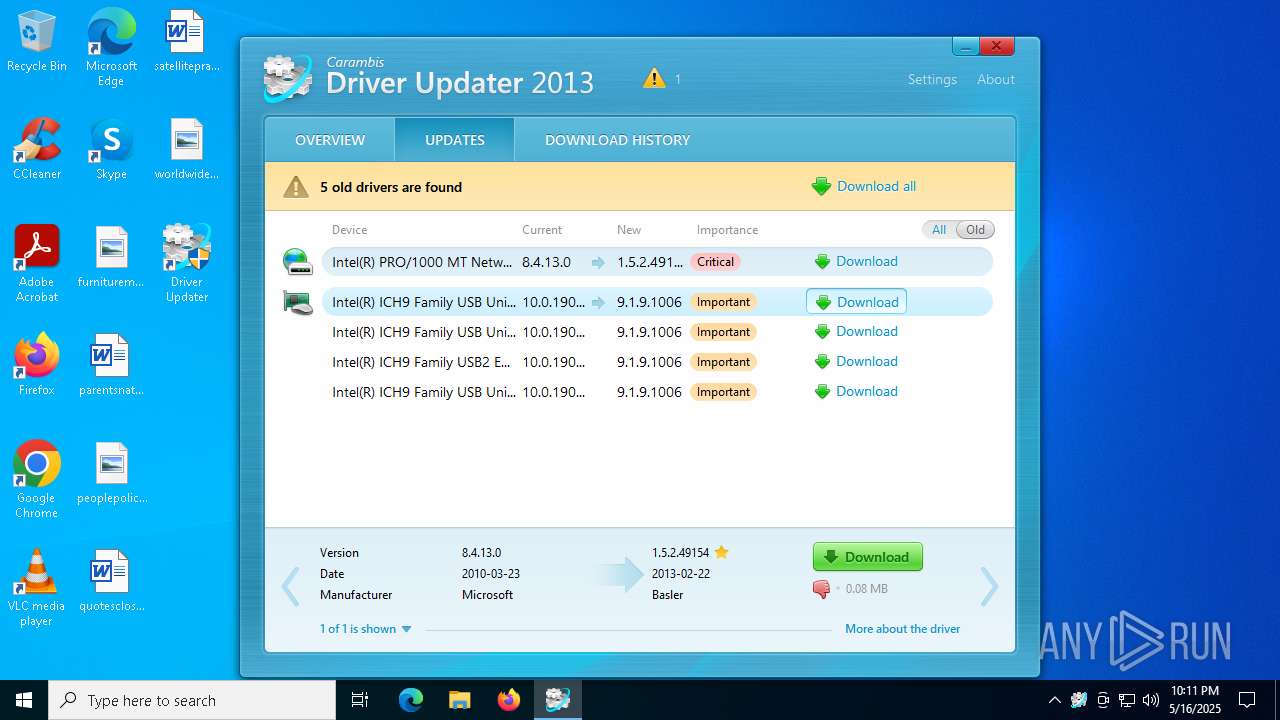
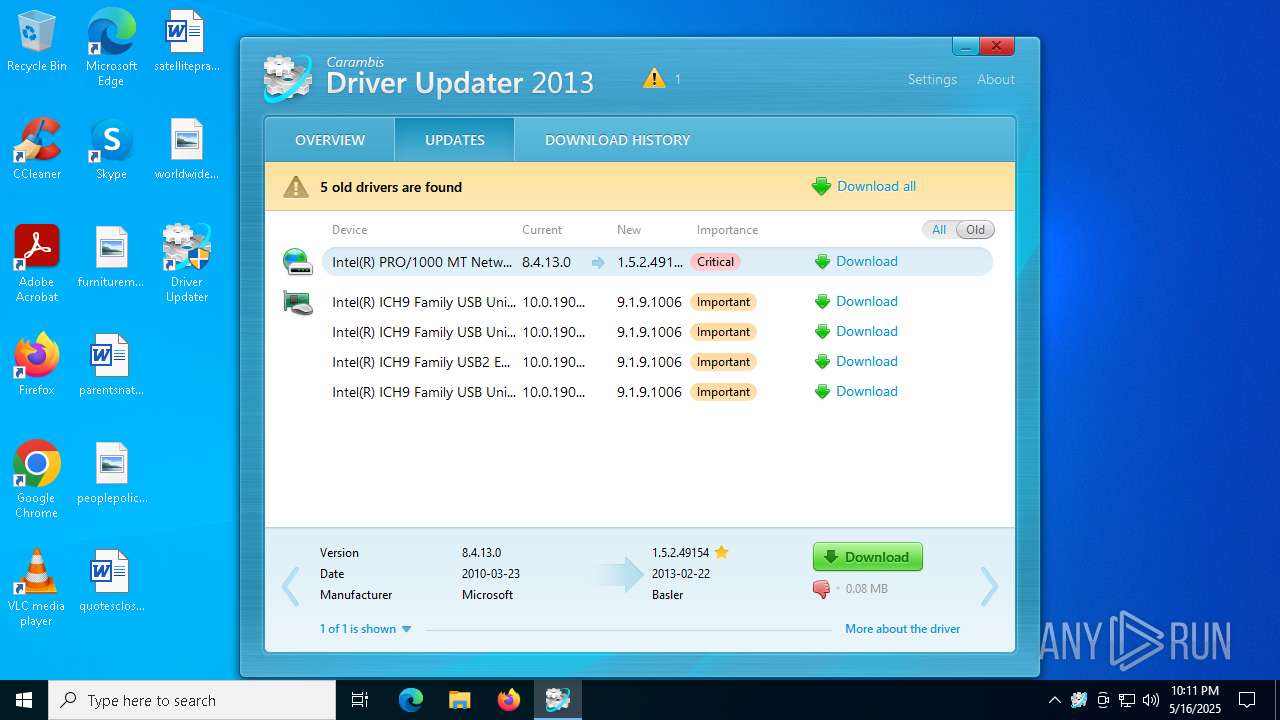
| 5112 | "C:\Program Files (x86)\Carambis\Driver Updater\dupdater.exe" | C:\Program Files (x86)\Carambis\Driver Updater\dupdater.exe | file.exe | ||||||||||||
User: admin Company: MEDIA FOG LTD. Integrity Level: HIGH Description: Driver Updater Exit code: 0 Version: 2.0.0.6004 Modules
| |||||||||||||||
| 5384 | vcredist_x86.exe /q /norestart | C:\Users\admin\AppData\Local\TempDIR\vcredist_x86.exe | file.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2010 x86 Redistributable Setup Exit code: 0 Version: 10.0.30319.01 Modules
| |||||||||||||||
| 6164 | "C:\Program Files (x86)\Carambis\Driver Updater\dupdater.exe" -minimized | C:\Program Files (x86)\Carambis\Driver Updater\dupdater.exe | — | explorer.exe | |||||||||||
User: admin Company: MEDIA FOG LTD. Integrity Level: MEDIUM Description: Driver Updater Exit code: 3221226540 Version: 2.0.0.6004 Modules
| |||||||||||||||
| 6564 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 1073807364 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6604 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Program Files (x86)\Carambis\Driver Updater\htmlayout.dll" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
Total events
19 606
Read events
19 391
Write events
205
Delete events
10
Modification events
| (PID) Process: | (864) file.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Carambis\Driver Updater\generalSettings |
| Operation: | write | Name: | language |
Value: EN | |||
| (PID) Process: | (4188) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 5C100000BB800263AFC6DB01 | |||
| (PID) Process: | (4188) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 74A1E150976618BC689A03A97B0B94FF5A8FDC22EE62A99C9BF06D7C52CD57DD | |||
| (PID) Process: | (4188) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (4188) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | c:\Config.Msi\11463f.rbs |
Value: 31180463 | |||
| (PID) Process: | (4188) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | c:\Config.Msi\11463f.rbsLow |
Value: | |||
| (PID) Process: | (4188) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\7E4C35488E6280433B4A9504AC59CB06 |
| Operation: | write | Name: | D04BB691875110D32B98EBCF771AA1E1 |
Value: 02:\SOFTWARE\Microsoft\VisualStudio\10.0\VC\VCRedist\x86\Version | |||
| (PID) Process: | (4188) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\48DB41415A9D5EE3AA3711D8C7703207 |
| Operation: | write | Name: | D04BB691875110D32B98EBCF771AA1E1 |
Value: 02:\SOFTWARE\Microsoft\DevDiv\vc\Servicing\10.0\red\x86\1033\Install | |||
| (PID) Process: | (4188) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | c:\Program Files (x86)\Common Files\Microsoft Shared\VC\msdia100.dll |
Value: 1 | |||
| (PID) Process: | (4188) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\33964F2EF4FF0E649B796FD4C2D6F41A |
| Operation: | write | Name: | D04BB691875110D32B98EBCF771AA1E1 |
Value: c:\?Program Files (x86)\Common Files\Microsoft Shared\VC\msdia100.dll | |||
Executable files
57
Suspicious files
33
Text files
66
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 864 | file.exe | C:\Users\admin\AppData\Local\Temp\nsvB8A5.tmp\installer_translate.ini | text | |
MD5:27D382008CBED622E61C00FB7ABA6DFF | SHA256:0D6BD1E4EA9E20E28E2BDBA2F1413B9AF184676761967D25598C67DEB5938A11 | |||
| 864 | file.exe | C:\Users\admin\AppData\Local\Temp\nsvB8A5.tmp\LangDLL.dll | executable | |
MD5:A1CD3F159EF78D9ACE162F067B544FD9 | SHA256:47B9E251C9C90F43E3524965AECC07BD53C8E09C5B9F9862B44C306667E2B0B6 | |||
| 864 | file.exe | C:\Users\admin\AppData\Local\Temp\nsvB8A5.tmp\modern-header.bmp | image | |
MD5:7F38B3536EA0D8F8403A7DC03E81CB69 | SHA256:5C01BA60C2CDE934F7AE84849A7BD3FA70BB71EE5A670E3336313A9A76BFD9AE | |||
| 864 | file.exe | C:\Users\admin\AppData\Local\Temp\nsvB8A5.tmp\ioSpecial.ini | text | |
MD5:6F98FCDA445825382121E480A64AE24C | SHA256:689A67B30946CBE12DCE92D17207EC0488E850A806BE608E6FB174F853F86B57 | |||
| 864 | file.exe | C:\Program Files (x86)\Carambis\Driver Updater\dbghelp.dll | executable | |
MD5:5C5E3AFD499E5146FEF1DA5EF8A23205 | SHA256:9A26FFAFFB26FA6549C6DA75F76238A903CA723F9DAD356FBA8D91067FE312FD | |||
| 864 | file.exe | C:\Users\admin\AppData\Local\Temp\nsvB8A5.tmp\System.dll | executable | |
MD5:BF712F32249029466FA86756F5546950 | SHA256:7851CB12FA4131F1FEE5DE390D650EF65CAC561279F1CFE70AD16CC9780210AF | |||
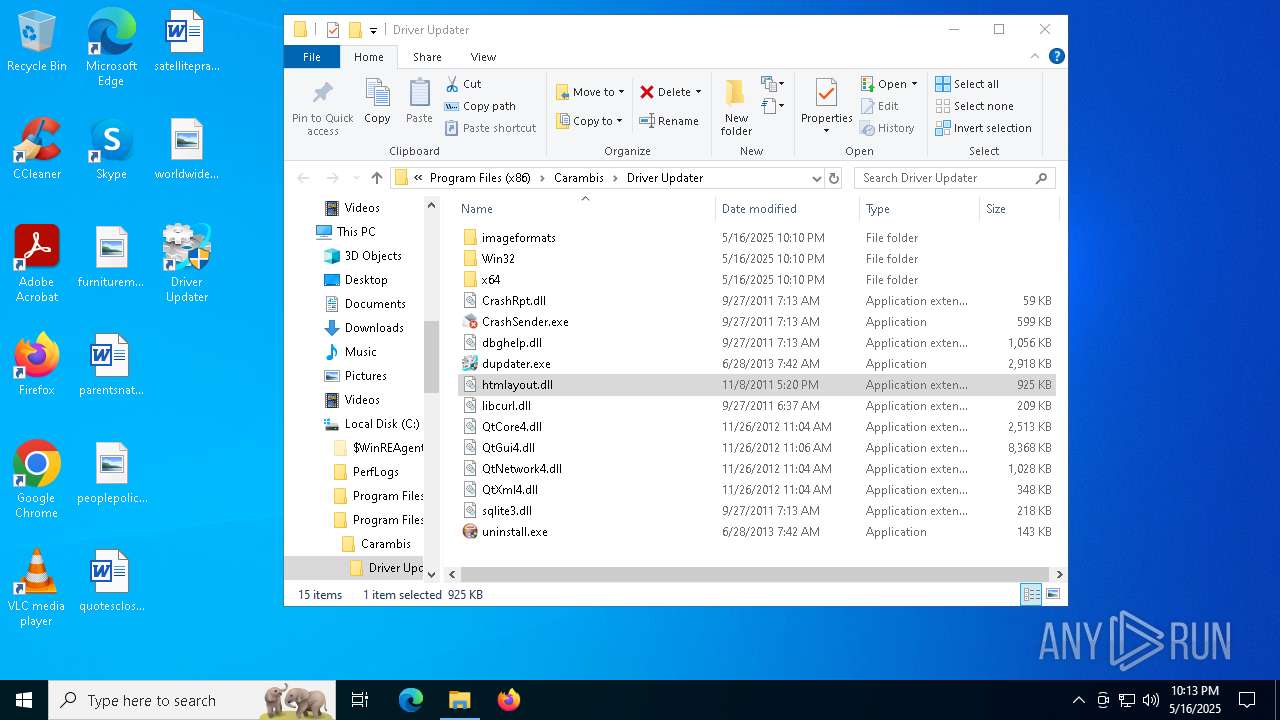
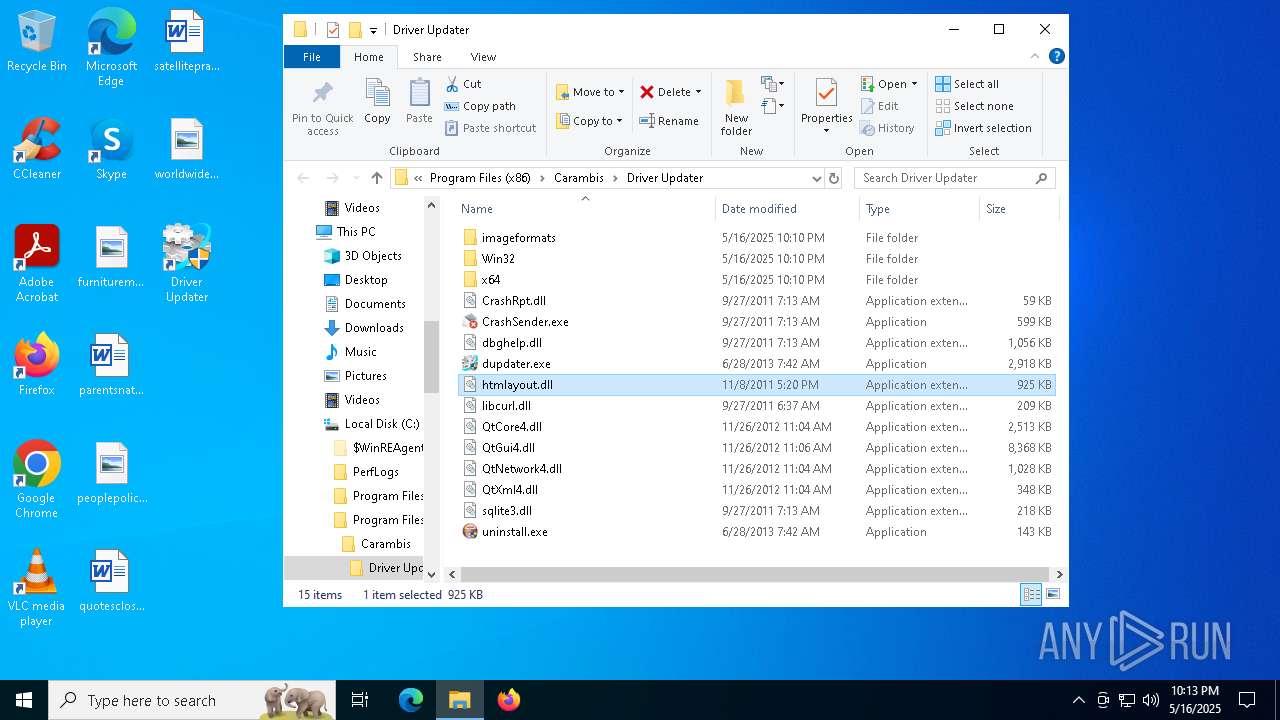
| 864 | file.exe | C:\Program Files (x86)\Carambis\Driver Updater\htmlayout.dll | executable | |
MD5:76F6BFA7C57ACD6C83FAEA94B150E974 | SHA256:1F367B648323780E6295D15E1230BBF5626EFD2D3D5442C7B7D361CC236A9872 | |||
| 864 | file.exe | C:\Program Files (x86)\Carambis\Driver Updater\Win32\Installer.exe | executable | |
MD5:F9EBF8E6BE7CC3A9C19B9C7AF722CA64 | SHA256:52CCE95608BC37927C4B2B425305509F1F3D40F07321D0B27E825F9E41942D17 | |||
| 864 | file.exe | C:\Program Files (x86)\Carambis\Driver Updater\sqlite3.dll | executable | |
MD5:3CB54463EA2C41B8203EB604BAF09577 | SHA256:F5218B0B2ADBE43DC65EF213F5447FA27273AE2DA6F32CCE8D9EBDB887AFCB26 | |||
| 864 | file.exe | C:\Program Files (x86)\Carambis\Driver Updater\QtGui4.dll | executable | |
MD5:960BC206B92EF49EEDE264547A946872 | SHA256:C8A8AD79A1F88ED7E19A2EFC67B98EF2F90296D12FD9E664D3B93E8632EA8FC0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
56
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5892 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4188 | msiexec.exe | GET | 200 | 23.48.23.153:80 | http://crl.microsoft.com/pki/crl/products/CSPCA.crl | unknown | — | — | whitelisted |
5892 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5292 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5112 | dupdater.exe | PUT | 200 | 188.130.153.33:80 | http://a.carambis.com/du_settings.php | unknown | — | — | unknown |
6488 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5112 | dupdater.exe | PUT | 200 | 188.130.153.33:80 | http://a.carambis.com/du_scan.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2432 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
a.carambis.com |
| unknown |