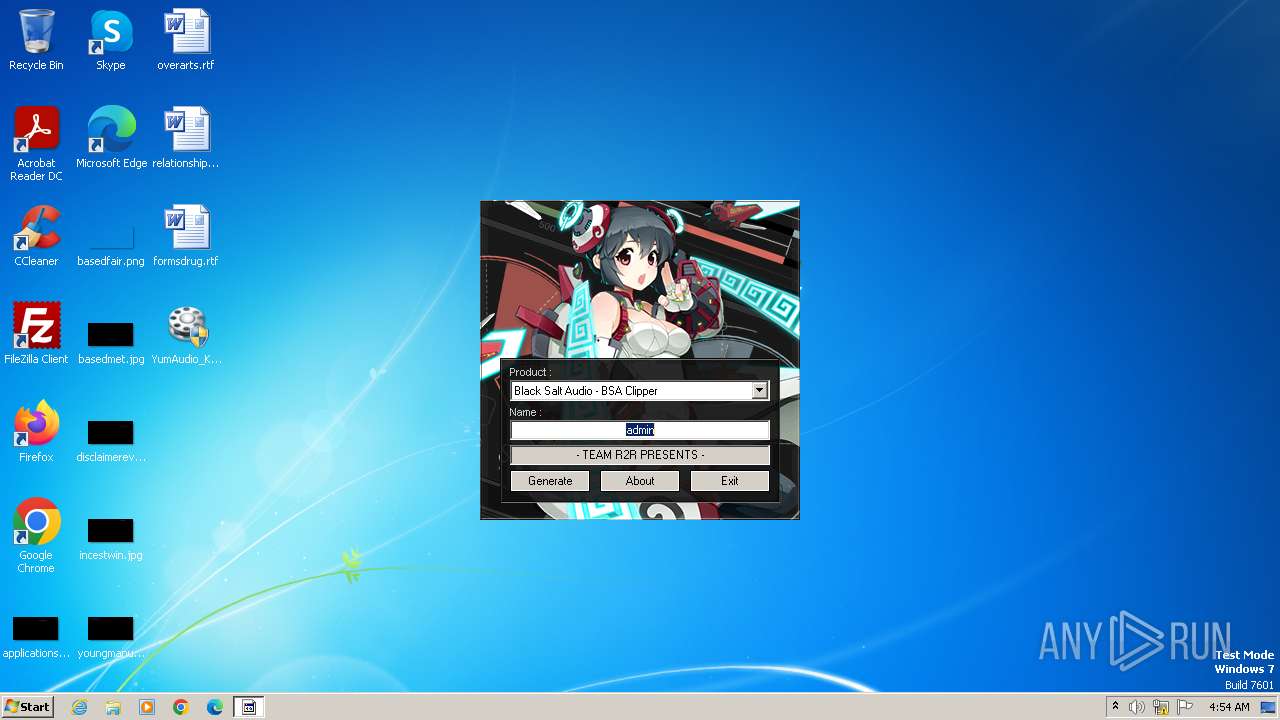
| File name: | YumAudio_KeyGen.exe |
| Full analysis: | https://app.any.run/tasks/73dc6c3e-dea5-481d-923a-e3e1f3db31a3 |
| Verdict: | Malicious activity |
| Analysis date: | May 09, 2024, 03:53:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 16FE5D6EB442672570AACC30CACB72C6 |
| SHA1: | 8F9266A0762A043DEBC59D170152DA731D7C91CC |
| SHA256: | 1D998A64065DA889E34CC63FA213FF5555D277C77704A0433E54706CF83E940C |
| SSDEEP: | 24576:hJ8m3sUkChJvT1rZmSAgEXaxofQS2h+SzfI01BlP+4sKQs7FVvbR+l+:hJ8m3sUkCLvT1rZmSAzXax6QS2h+SzfR |
MALICIOUS
Drops the executable file immediately after the start
- YumAudio_KeyGen.exe (PID: 2104)
SUSPICIOUS
Executable content was dropped or overwritten
- YumAudio_KeyGen.exe (PID: 2104)
Reads the Internet Settings
- keygen.exe (PID: 1116)
INFO
Checks supported languages
- keygen.exe (PID: 1116)
- YumAudio_KeyGen.exe (PID: 2104)
Reads the computer name
- YumAudio_KeyGen.exe (PID: 2104)
- keygen.exe (PID: 1116)
Create files in a temporary directory
- keygen.exe (PID: 1116)
- YumAudio_KeyGen.exe (PID: 2104)
Reads the machine GUID from the registry
- keygen.exe (PID: 1116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:56:47+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3640 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1116 | C:\Users\admin\AppData\Local\Temp\keygen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | — | YumAudio_KeyGen.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225547 Modules
| |||||||||||||||
| 2104 | "C:\Users\admin\Desktop\YumAudio_KeyGen.exe" | C:\Users\admin\Desktop\YumAudio_KeyGen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3976 | "C:\Users\admin\Desktop\YumAudio_KeyGen.exe" | C:\Users\admin\Desktop\YumAudio_KeyGen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
4 798
Read events
4 728
Write events
64
Delete events
6
Modification events
| (PID) Process: | (1116) keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (1116) keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | 0 |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C006B0065007900670065006E002E00650078006500000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070000000 | |||
| (PID) Process: | (1116) keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
| (PID) Process: | (1116) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (1116) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000070000000200000006000000000000000B0000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (1116) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1116) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | Mode |
Value: 6 | |||
| (PID) Process: | (1116) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | LogicalViewMode |
Value: 2 | |||
| (PID) Process: | (1116) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | FFlags |
Value: | |||
| (PID) Process: | (1116) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | IconSize |
Value: 48 | |||
Executable files
3
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2104 | YumAudio_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\bgm.xm | binary | |
MD5:0045C07DCB94D3A901B3777FF7E02B21 | SHA256:FB31D7534573DED625A28CBF3667BDA497565826D9F65047CB9704CA69E8C219 | |||
| 2104 | YumAudio_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\nsk3887.tmp | binary | |
MD5:24193769F5BAAADEF2AA53F4B19DC9E9 | SHA256:3C0DF13EF85AF5331D22023397E07F5F1078A9BA521DCB9E1929580525792193 | |||
| 2104 | YumAudio_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\BASSMOD.dll | executable | |
MD5:E4EC57E8508C5C4040383EBE6D367928 | SHA256:8AD9E47693E292F381DA42DDC13724A3063040E51C26F4CA8E1F8E2F1DDD547F | |||
| 2104 | YumAudio_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\R2RYUMKG.dll | executable | |
MD5:790E106F9D94DAA7DD0FC504F4088B9C | SHA256:ACD8134B870037BF36D2C4F9354B08B1C436AD6EFBADE603AEEDCB2B3CA64A7A | |||
| 1116 | keygen.exe | C:\Users\admin\AppData\Local\Temp\~DF4AA40D2897A5F7C8.TMP | binary | |
MD5:A51F0FF73670304124EFE31662E3ED6D | SHA256:FF6123E5EB6877850D68099B4A08A3C097A71EB9FEC74325D34A09317A6EF85F | |||
| 2104 | YumAudio_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | executable | |
MD5:7BF359E41950E8E8C9CC41A92102AE7C | SHA256:9286700907B3CA15D15FE92D3F8C1920F60F31E6190F57E6E6CE01C97AD1C569 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |