| File name: | loki.exe |
| Full analysis: | https://app.any.run/tasks/30a808d9-c7b9-4a6b-9587-9767fb13a1db |
| Verdict: | Malicious activity |
| Analysis date: | July 26, 2023, 22:31:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 90BAE9356DC021172D0FF06603E7A4CF |
| SHA1: | 7FD07C934CE9B7C4AD902408ED528ACF4CE32DDB |
| SHA256: | 1D2DB070008116A7A1992ED7DAD7E7F26A0BFEE3499338C3E603161E3F18DB2F |
| SSDEEP: | 12288:hh1Lk70TnvjcJ4+FtJY0W+MnoUfomBZOVWkpU5+yWV:9k70TrcHtYdoWBZOVNp0+h |
MALICIOUS
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 3808)
Starts Visual C# compiler
- loki.exe (PID: 992)
- loki.exe (PID: 2312)
Create files in the Startup directory
- loki.exe (PID: 992)
- loki.exe (PID: 2312)
Deletes shadow copies
- cmd.exe (PID: 3900)
- cmd.exe (PID: 3920)
- cmd.exe (PID: 4060)
- cmd.exe (PID: 1024)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 1408)
- cmd.exe (PID: 2092)
Disables Windows Defender
- loki.exe (PID: 2312)
Connects to the CnC server
- loki.exe (PID: 2312)
SUSPICIOUS
Reads the Internet Settings
- loki.exe (PID: 992)
- loki.exe (PID: 2312)
- WMIC.exe (PID: 1428)
Starts CMD.EXE for commands execution
- loki.exe (PID: 992)
- loki.exe (PID: 2312)
Executable content was dropped or overwritten
- loki.exe (PID: 992)
- csc.exe (PID: 2148)
- loki.exe (PID: 2312)
- csc.exe (PID: 2164)
Uses .NET C# to load dll
- loki.exe (PID: 992)
- loki.exe (PID: 2312)
Application launched itself
- loki.exe (PID: 992)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 820)
- cmd.exe (PID: 1576)
Executes as Windows Service
- wbengine.exe (PID: 4052)
- VSSVC.exe (PID: 2664)
- vds.exe (PID: 3952)
Write to the desktop.ini file (may be used to cloak folders)
- loki.exe (PID: 2312)
INFO
Reads the machine GUID from the registry
- loki.exe (PID: 992)
- csc.exe (PID: 2148)
- loki.exe (PID: 2312)
- csc.exe (PID: 2164)
- cvtres.exe (PID: 2068)
- cvtres.exe (PID: 3332)
Checks supported languages
- loki.exe (PID: 992)
- csc.exe (PID: 2148)
- cvtres.exe (PID: 2068)
- loki.exe (PID: 2312)
- csc.exe (PID: 2164)
- cvtres.exe (PID: 3332)
Reads the computer name
- loki.exe (PID: 992)
- loki.exe (PID: 2312)
Create files in a temporary directory
- loki.exe (PID: 992)
- cvtres.exe (PID: 2068)
- loki.exe (PID: 2312)
- cvtres.exe (PID: 3332)
Creates files in the program directory
- csc.exe (PID: 2148)
- loki.exe (PID: 992)
- loki.exe (PID: 2312)
- csc.exe (PID: 2164)
The process checks LSA protection
- csc.exe (PID: 2148)
- loki.exe (PID: 992)
- cvtres.exe (PID: 2068)
- loki.exe (PID: 2312)
- csc.exe (PID: 2164)
- wbadmin.exe (PID: 2964)
- vssadmin.exe (PID: 2032)
- netsh.exe (PID: 2420)
- cvtres.exe (PID: 3332)
- dllhost.exe (PID: 912)
- wbengine.exe (PID: 4052)
- VSSVC.exe (PID: 2664)
- vdsldr.exe (PID: 556)
- vds.exe (PID: 3952)
- netsh.exe (PID: 1592)
- WMIC.exe (PID: 1428)
Creates files or folders in the user directory
- loki.exe (PID: 992)
Checks proxy server information
- loki.exe (PID: 2312)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| AssemblyVersion: | 1.2.0.0 |
|---|---|
| ProductVersion: | 1.0.0.0 |
| ProductName: | svchost |
| OriginalFileName: | svchost.exe |
| LegalTrademarks: | - |
| LegalCopyright: | Copyright © 2021 |
| InternalName: | svchost.exe |
| FileVersion: | 1.0.0.0 |
| FileDescription: | svchost |
| CompanyName: | Microsoft |
| Comments: | - |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.0.0.0 |
| FileVersionNumber: | 1.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5 |
| ImageVersion: | - |
| OSVersion: | 5 |
| EntryPoint: | 0xcd2f |
| UninitializedDataSize: | - |
| InitializedDataSize: | 406016 |
| CodeSize: | 104448 |
| LinkerVersion: | 9 |
| PEType: | PE32 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware, 32-bit |
| TimeStamp: | 2012:07:13 22:47:16+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 13-Jul-2012 22:47:16 |
| Debug artifacts: | |
| Comments: | - |
| CompanyName: | Microsoft |
| FileDescription: | svchost |
| FileVersion: | 1.0.0.0 |
| InternalName: | svchost.exe |
| LegalCopyright: | Copyright © 2021 |
| LegalTrademarks: | - |
| OriginalFilename: | svchost.exe |
| ProductName: | svchost |
| ProductVersion: | 1.0.0.0 |
| Assembly Version: | 1.2.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 13-Jul-2012 22:47:16 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00019718 | 0x00019800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.74851 |
.rdata | 0x0001B000 | 0x00006DB4 | 0x00006E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.44296 |
.data | 0x00022000 | 0x000030C0 | 0x00001600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.26259 |
.rsrc | 0x00026000 | 0x0005ACF4 | 0x0005AE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.99901 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
__ | 7.99948 | 370342 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
~ | 4.875 | 32 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
Imports
KERNEL32.dll |
OLEAUT32.dll |
ole32.dll |
Total processes
83
Monitored processes
29
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 820 | "C:\Windows\System32\cmd.exe" /C netsh firewall set opmode mode=disable | C:\Windows\System32\cmd.exe | — | loki.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 912 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 992 | "C:\Users\admin\AppData\Local\Temp\loki.exe" | C:\Users\admin\AppData\Local\Temp\loki.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: svchost Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1024 | "C:\Windows\System32\cmd.exe" /C wbadmin delete catalog -quiet | C:\Windows\System32\cmd.exe | — | loki.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1248 | wbadmin DELETE SYSTEMSTATEBACKUP | C:\Windows\System32\wbadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® BLB Backup Exit code: 4294967293 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1408 | "C:\Windows\System32\cmd.exe" /C bcdedit /set {default} recoveryenabled no | C:\Windows\System32\cmd.exe | — | loki.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1428 | wmic shadowcopy delete | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 2147749890 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1576 | "C:\Windows\System32\cmd.exe" /C netsh advfirewall set currentprofile state off | C:\Windows\System32\cmd.exe | — | loki.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1592 | netsh advfirewall set currentprofile state off | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 253
Read events
4 054
Write events
199
Delete events
0
Modification events
| (PID) Process: | (992) loki.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (992) loki.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (992) loki.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (992) loki.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (992) loki.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2312) loki.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2312) loki.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 105 | |||
| (PID) Process: | (2312) loki.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2312) loki.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2312) loki.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
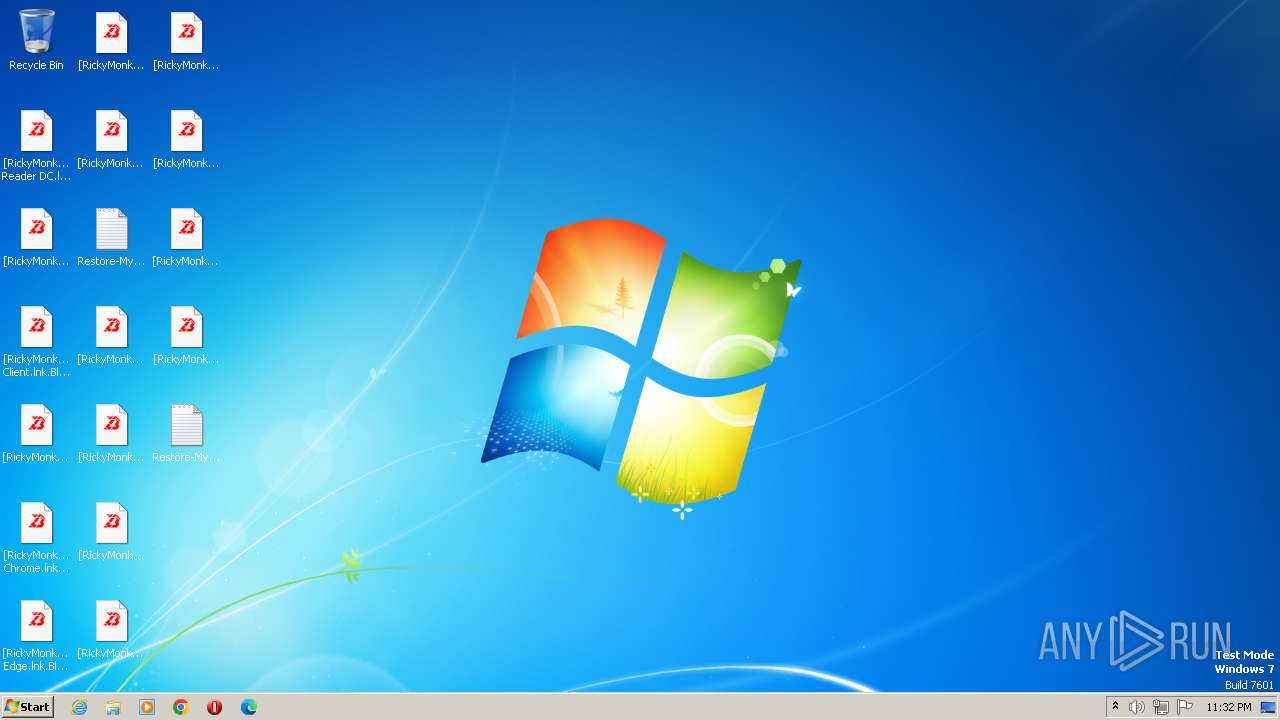
Executable files
7
Suspicious files
415
Text files
85
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 992 | loki.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\winlogon.exe | executable | |
MD5:90BAE9356DC021172D0FF06603E7A4CF | SHA256:1D2DB070008116A7A1992ED7DAD7E7F26A0BFEE3499338C3E603161E3F18DB2F | |||
| 992 | loki.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\wvtymcow.bat | text | |
MD5:3FC537B642D3756646715325299C6367 | SHA256:708511C356493E41CA103DB51B8DF3FB57898DDB2BB7CF4F11560FACDE9425ED | |||
| 2148 | csc.exe | C:\ProgramData\CSC2AE91A2FEE4044BEAE6899B94F9E1462.TMP | binary | |
MD5:1E8F256A2D5EE595443AB58E22C85128 | SHA256:C7FE23156D8C8639AF4458CA81BBCCC0C6E72806B2D2F675B758BE4EFB7145EC | |||
| 992 | loki.exe | C:\Users\admin\AppData\Roaming\winlogon.exe | executable | |
MD5:90BAE9356DC021172D0FF06603E7A4CF | SHA256:1D2DB070008116A7A1992ED7DAD7E7F26A0BFEE3499338C3E603161E3F18DB2F | |||
| 992 | loki.exe | C:\ProgramData\info.BlackBit | html | |
MD5:91B38D2F5A2DE17285F648AF1985AC1E | SHA256:3A927F87762934A80FBF75A2D262D85BE6EE3FDDA3584DC92429F3D9C26611C3 | |||
| 992 | loki.exe | C:\Users\admin\AppData\Local\Temp\qocpcagq.0.cs | text | |
MD5:D0E9C33D5B13003DE33E4A6BCCE3C90F | SHA256:A1AF8159882C4A80F6C6F7A532A0F116DD3F1BB56AF0B451F2432B8795265CA1 | |||
| 992 | loki.exe | C:\Users\admin\AppData\Local\Temp\whdoxpzi.ico | image | |
MD5:305C2042777E67710483E58ACC04AC2C | SHA256:F9DDF619CA0266055744C2BECA77673AA41702104B459A0F55DE3945196B6C50 | |||
| 992 | loki.exe | C:\Users\admin\AppData\Local\Temp\qocpcagq.cmdline | text | |
MD5:D71E2739E70A2398410F04D5AB139CE0 | SHA256:BF29FBF1F0020392D9BF5F4548517852C775C13E018257288F0953B929AB31A4 | |||
| 2148 | csc.exe | C:\ProgramData\yruvt1v4.exe | executable | |
MD5:5D77140D764FC4DAAD714AB55D33F84A | SHA256:C50DBA9D2672B4D299431A04D93067DA57C829D713859DFFC98A76C48C8DD748 | |||
| 2312 | loki.exe | C:\Windows\winlogon.exe | executable | |
MD5:90BAE9356DC021172D0FF06603E7A4CF | SHA256:1D2DB070008116A7A1992ED7DAD7E7F26A0BFEE3499338C3E603161E3F18DB2F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
27
DNS requests
2
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2312 | loki.exe | POST | 200 | 195.230.22.7:80 | http://application-api.xyz/api/index.php | BG | text | 568 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1084 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2720 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.1:445 | — | — | — | unknown |
4 | System | 192.168.100.100:445 | — | — | — | malicious |
4 | System | 192.168.100.121:137 | — | — | — | malicious |
4 | System | 192.168.100.100:137 | — | — | — | malicious |
2312 | loki.exe | 195.230.22.7:80 | application-api.xyz | Verdina Ltd. | BG | malicious |
4 | System | 192.168.100.121:445 | — | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
application-api.xyz |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2312 | loki.exe | A Network Trojan was detected | ET MALWARE Loki Locker Ransomware CnC Activity |
2312 | loki.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |