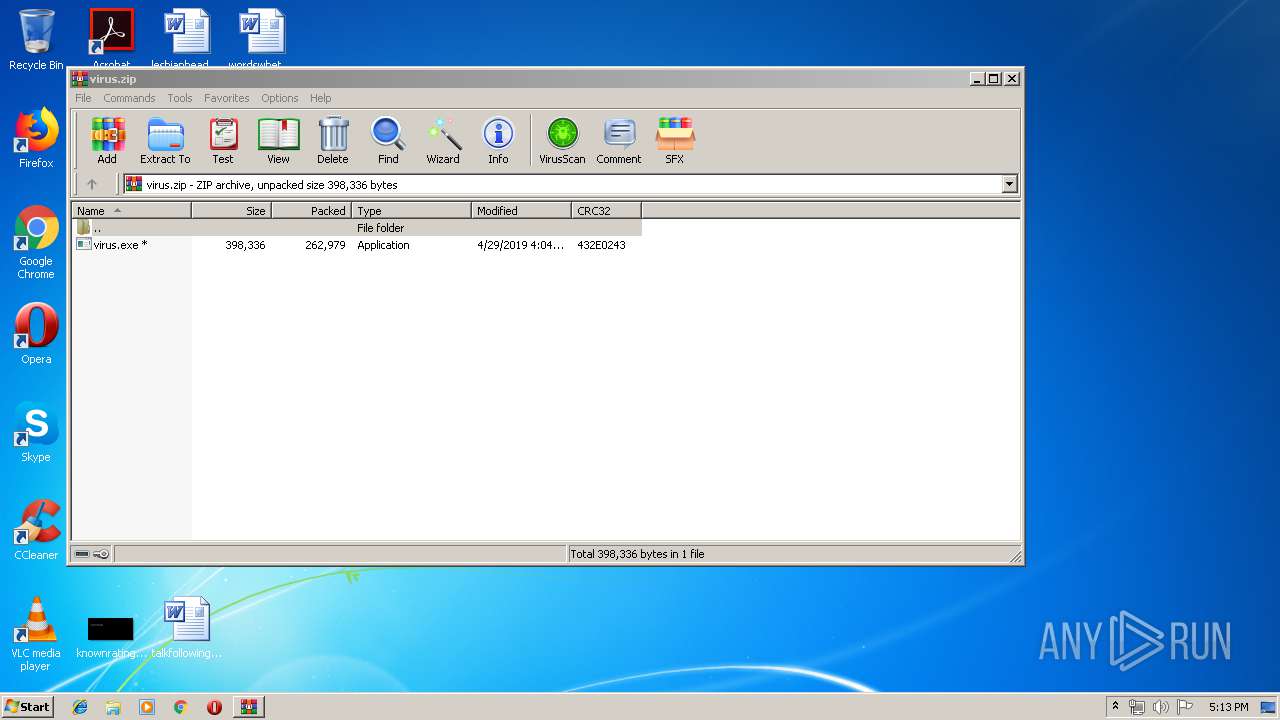
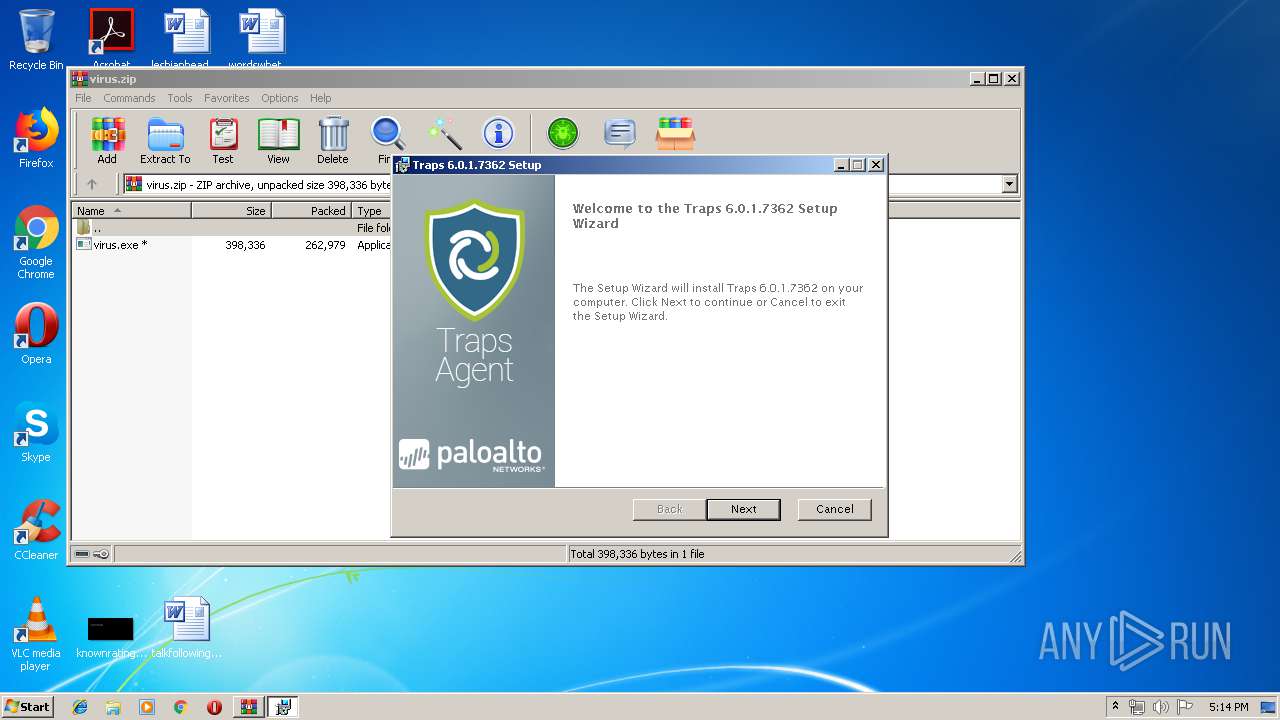
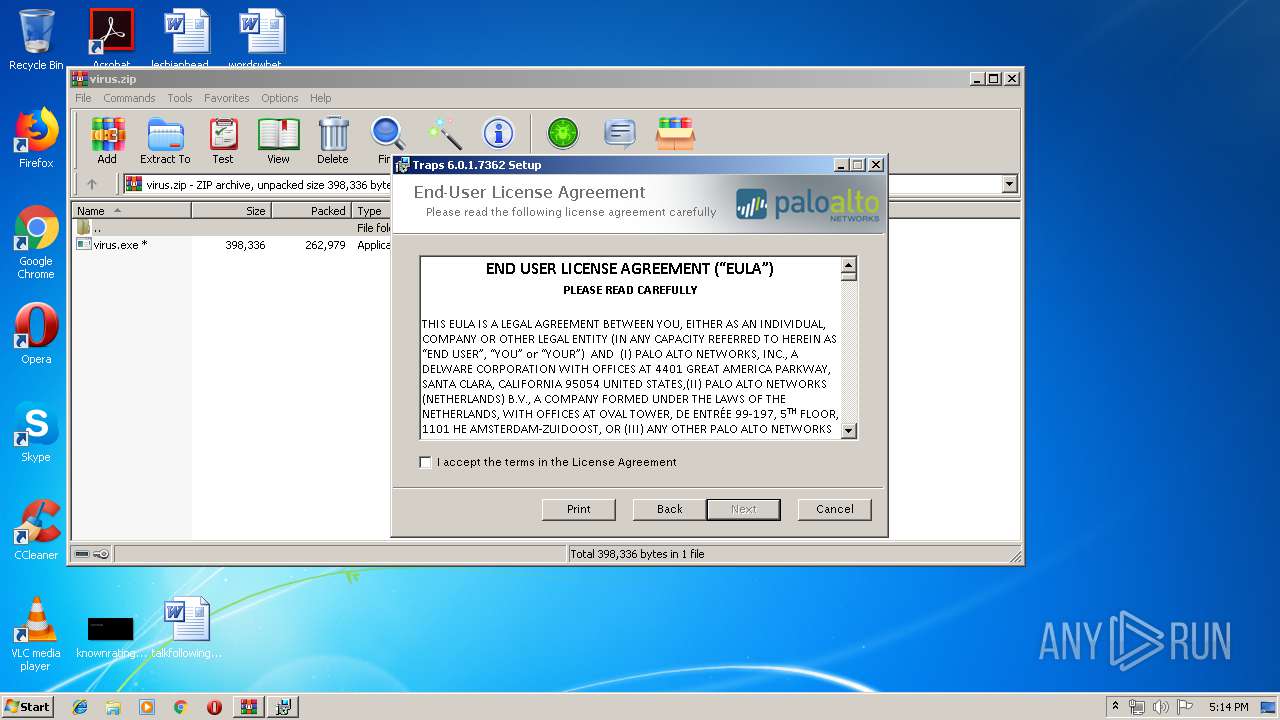
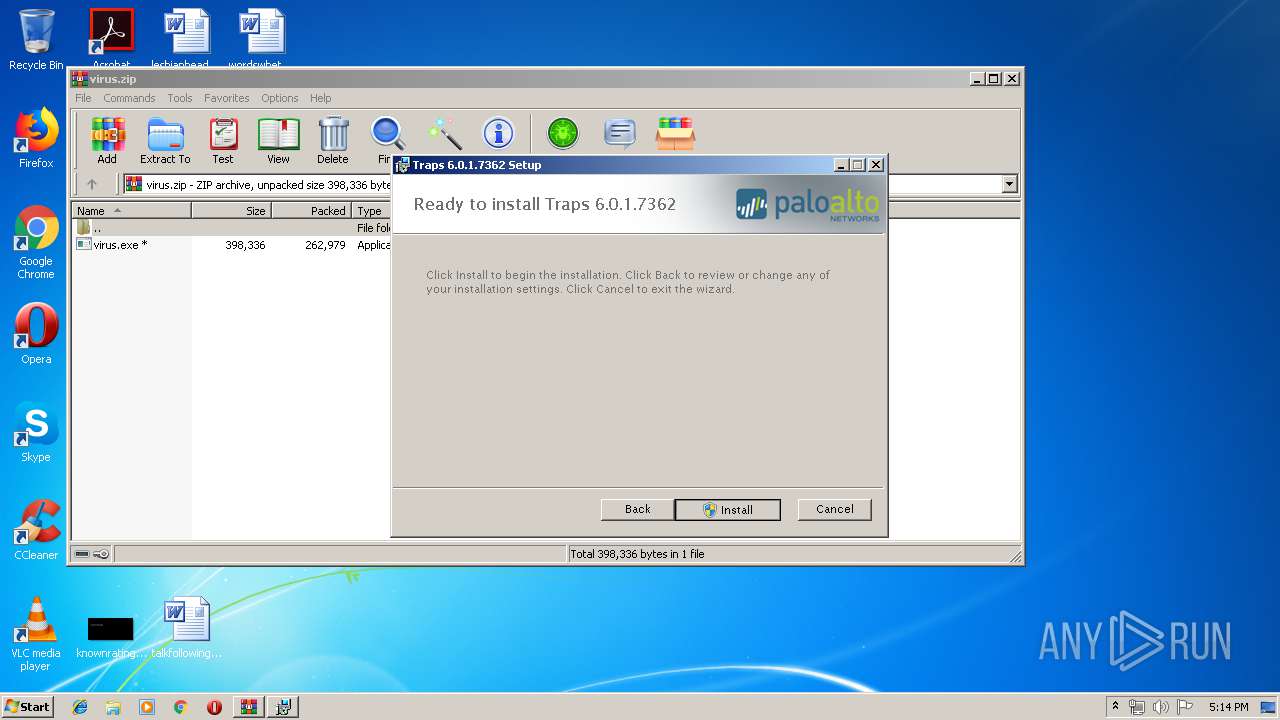
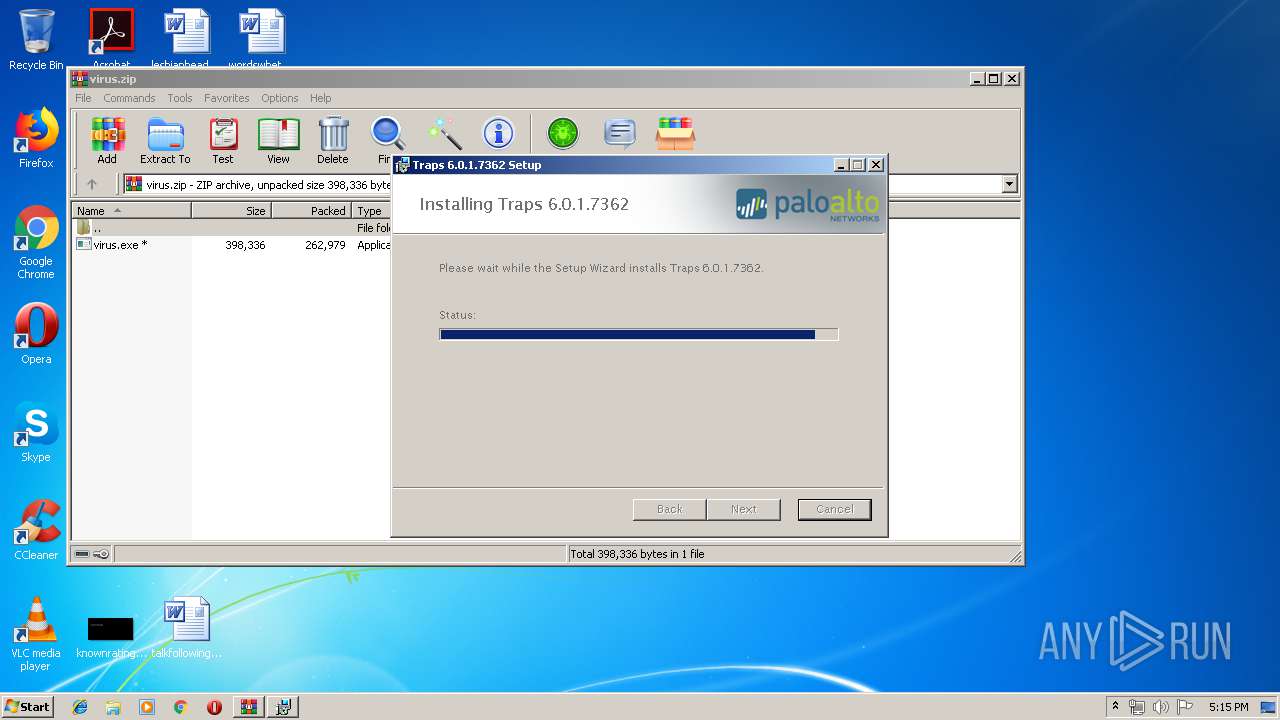
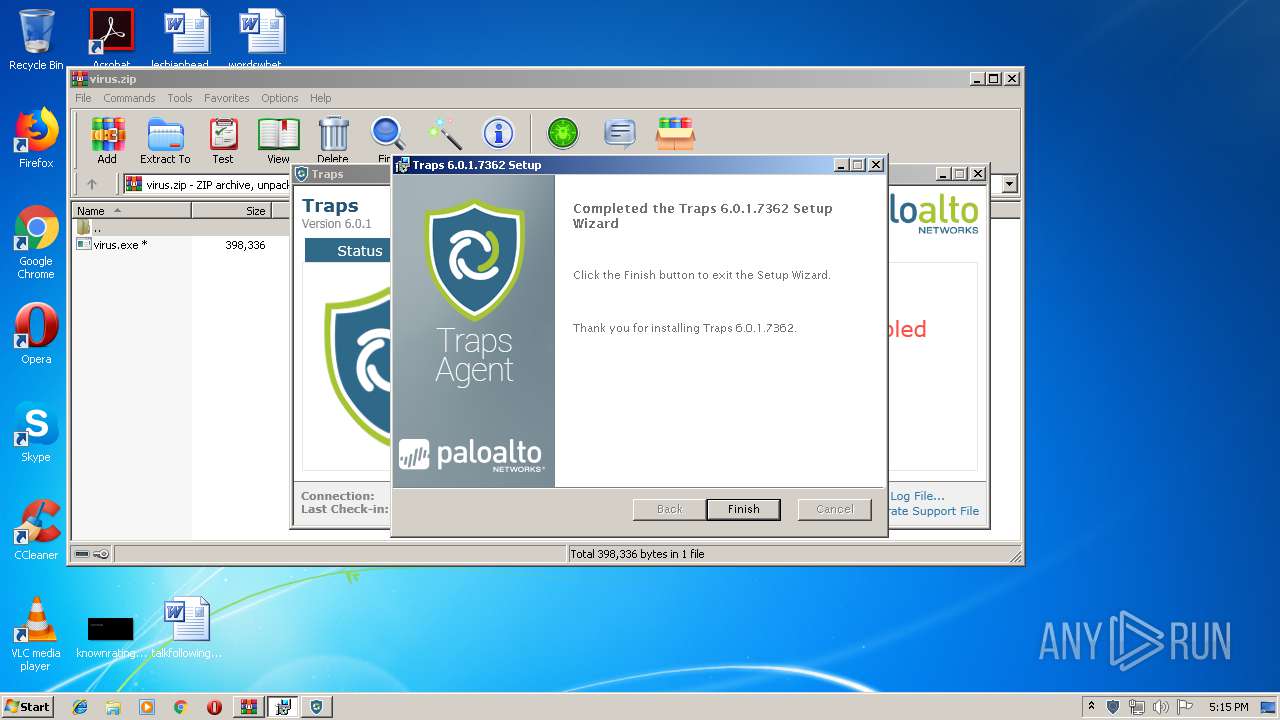
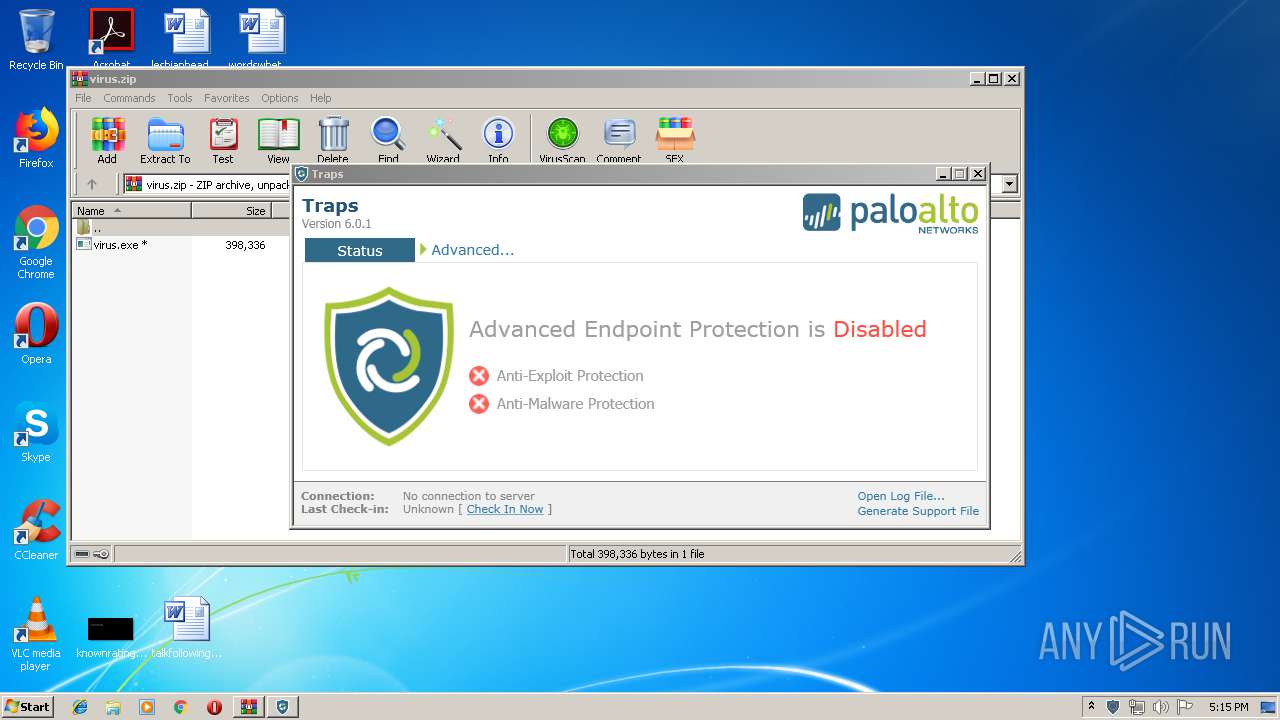
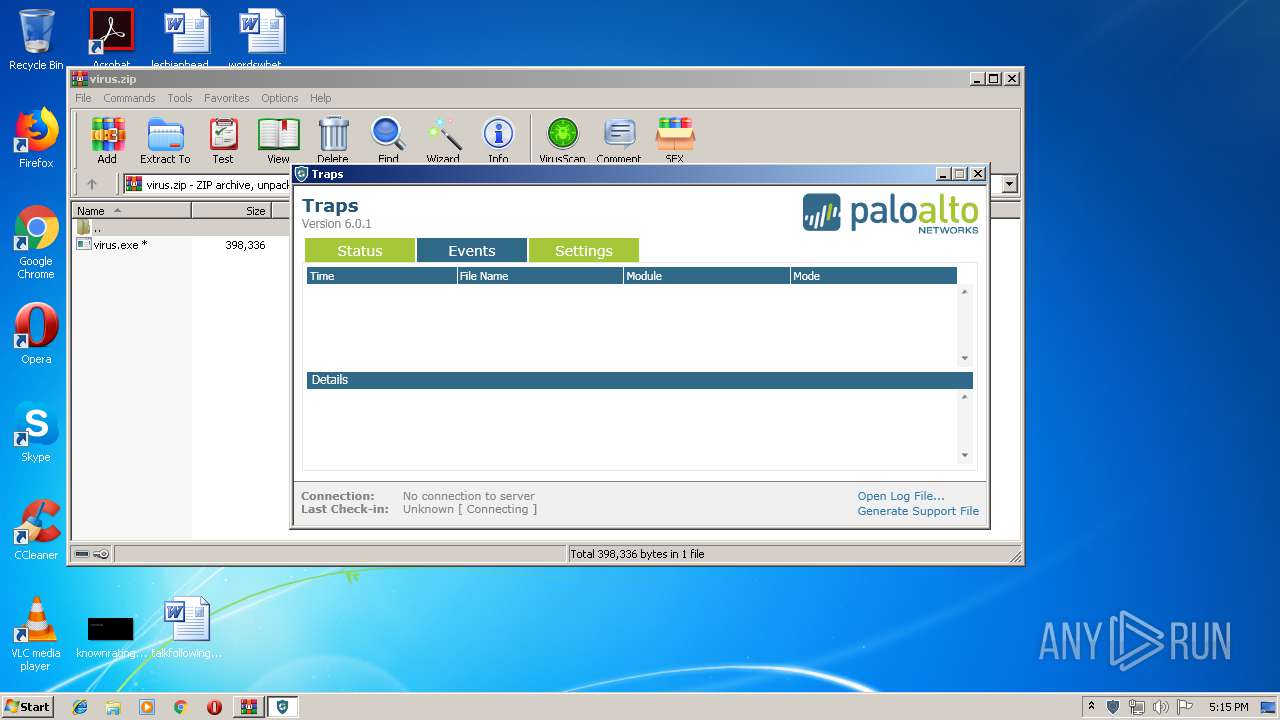
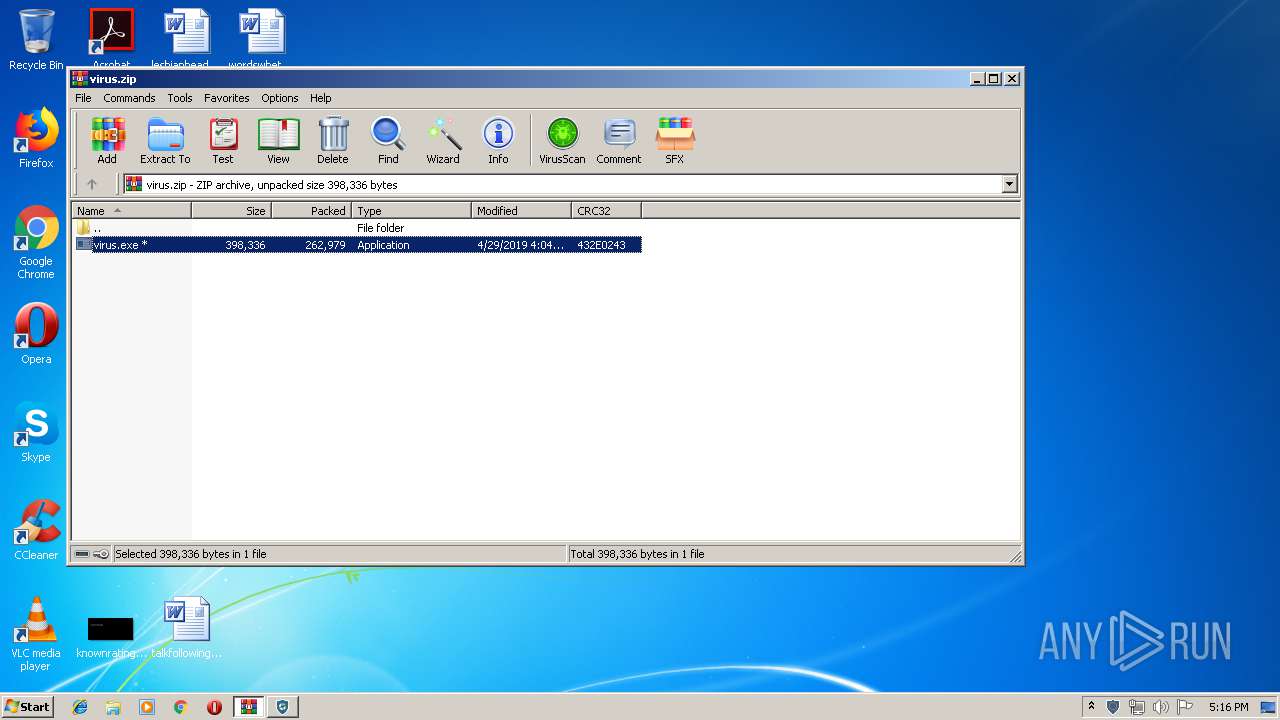
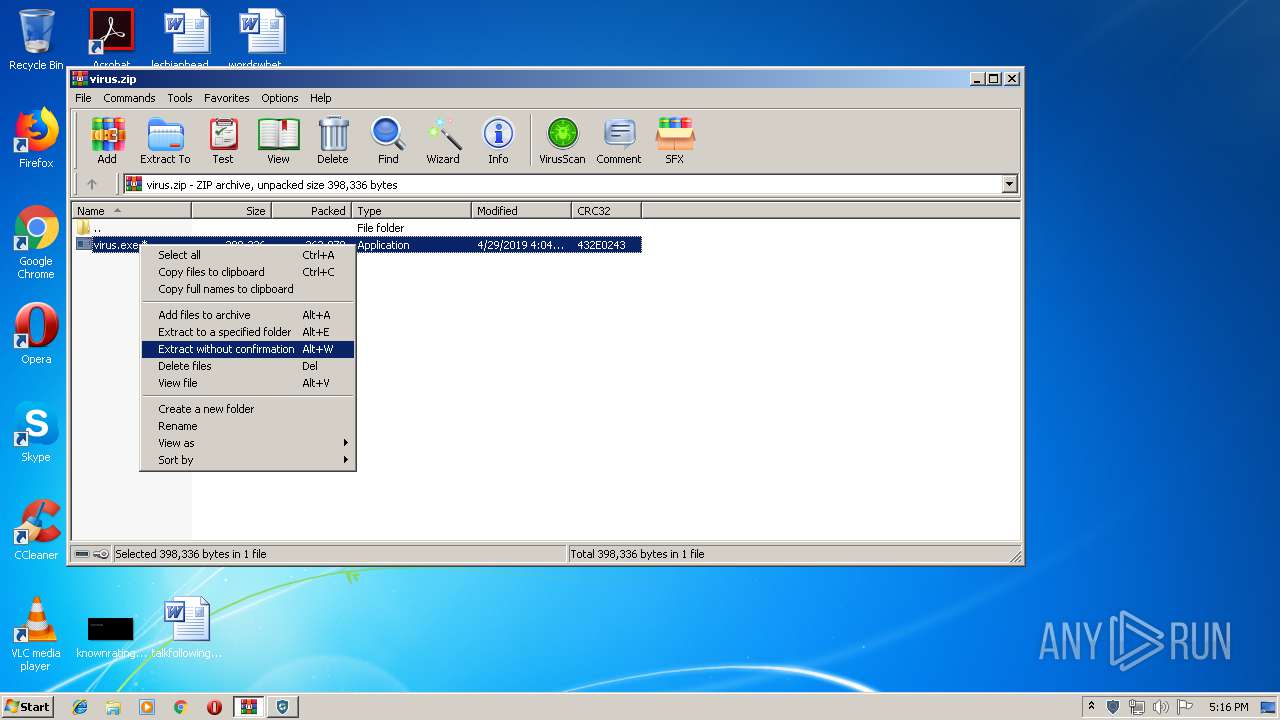
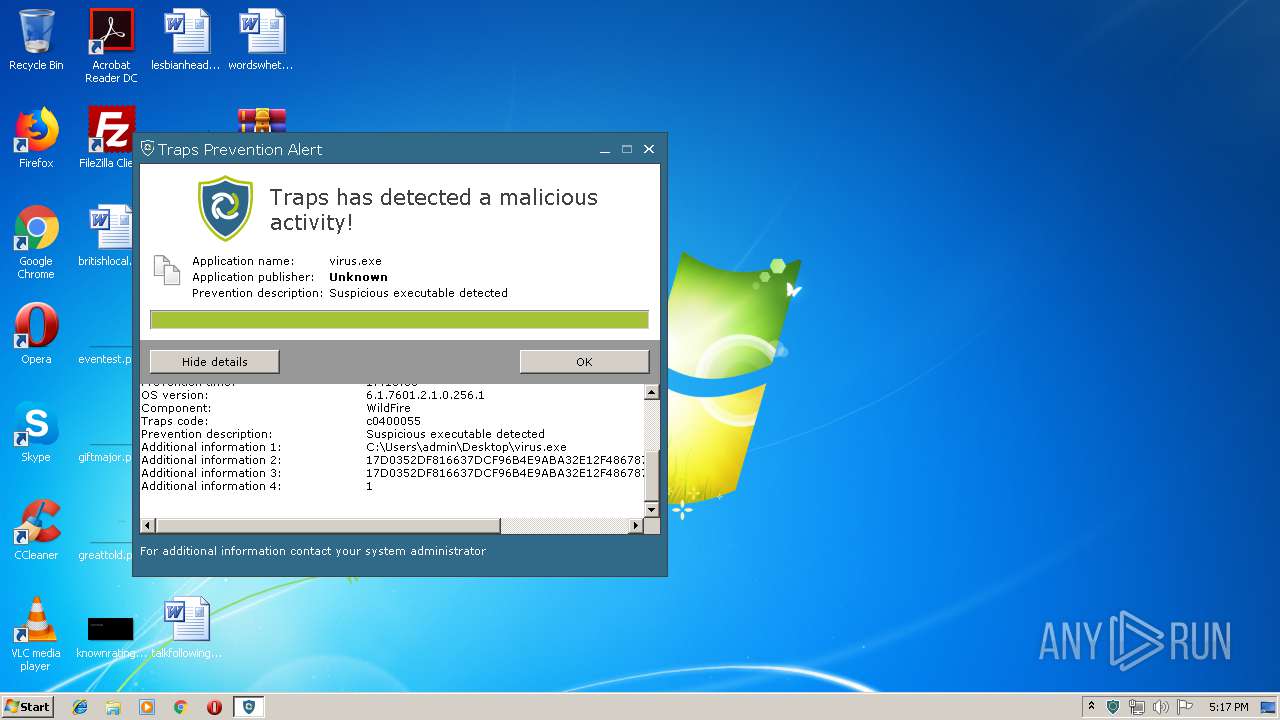
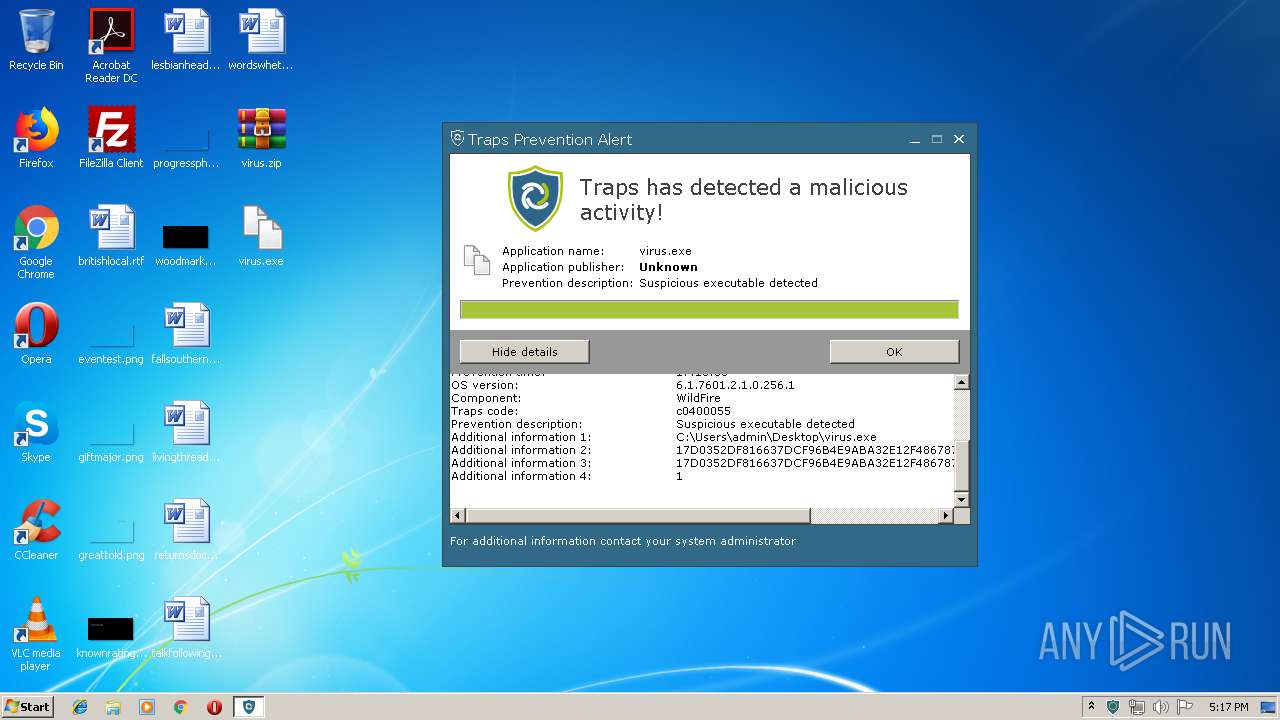
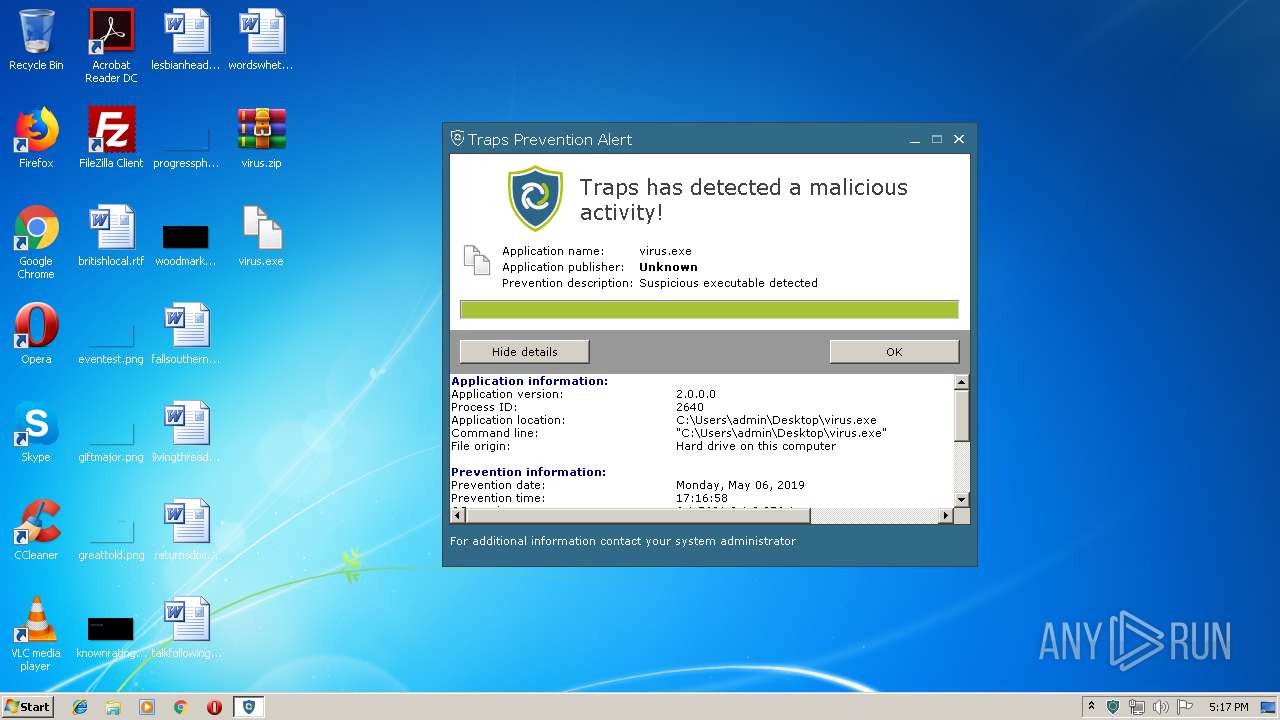
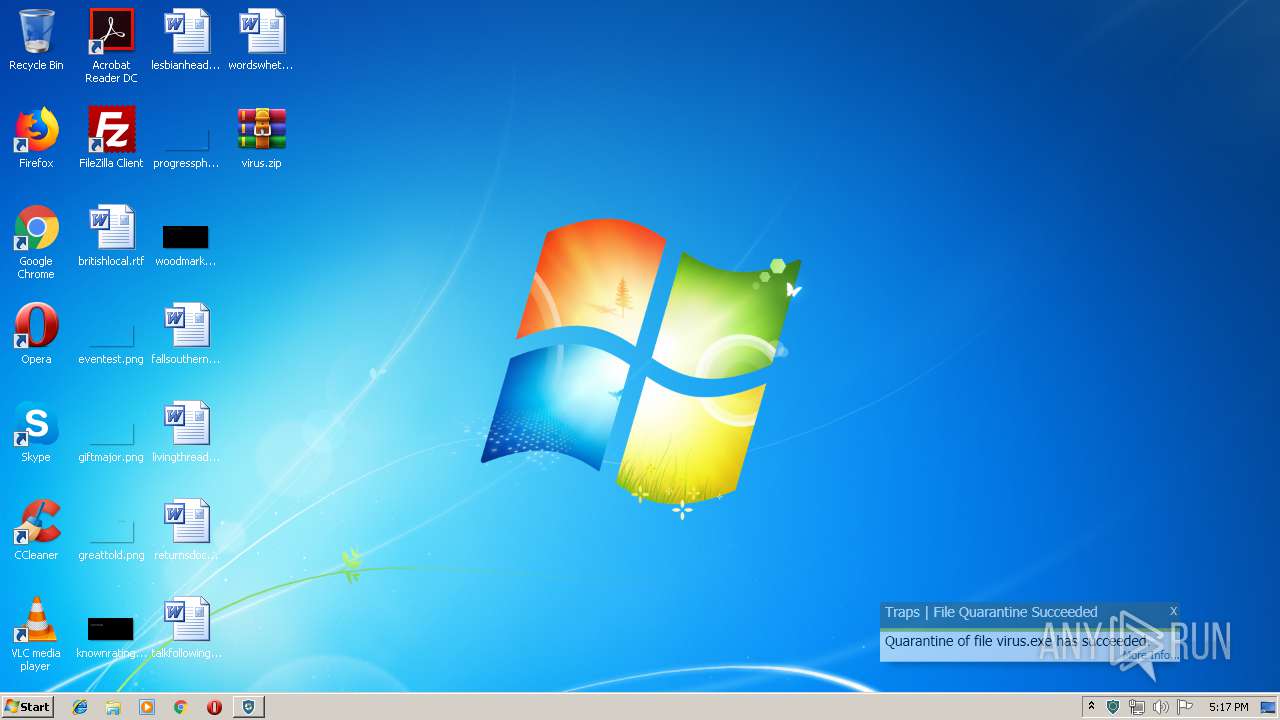
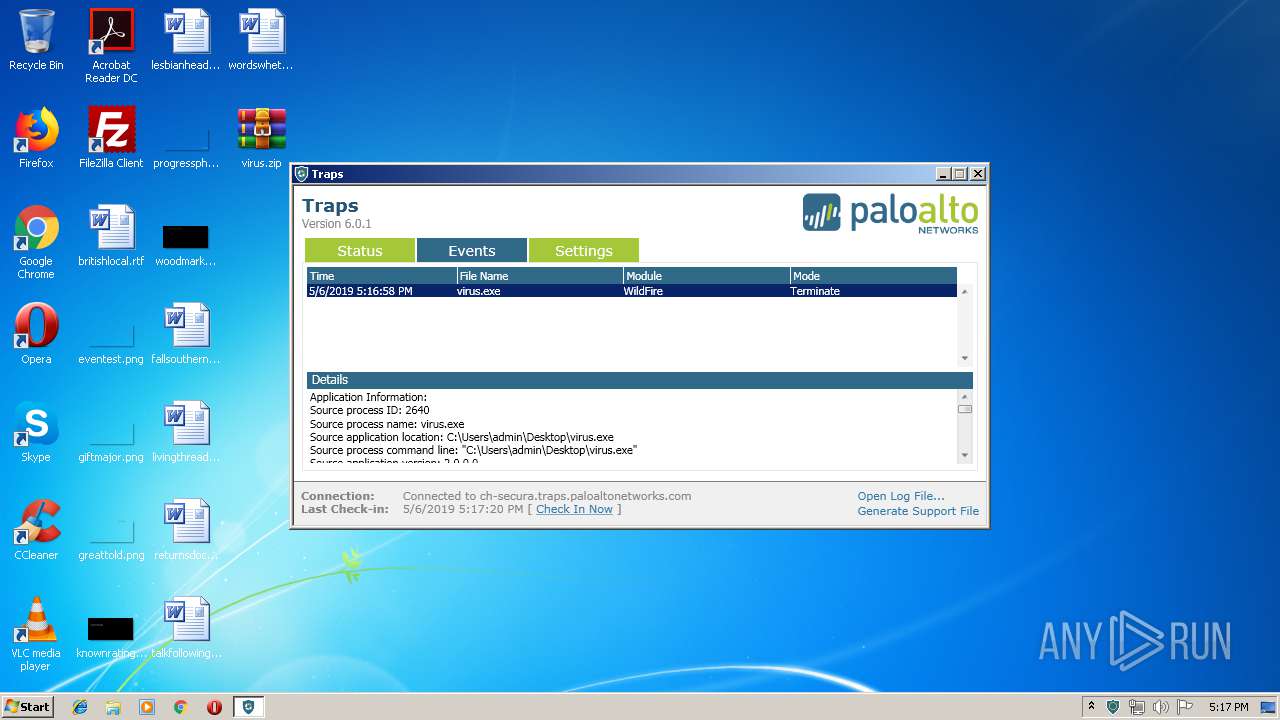
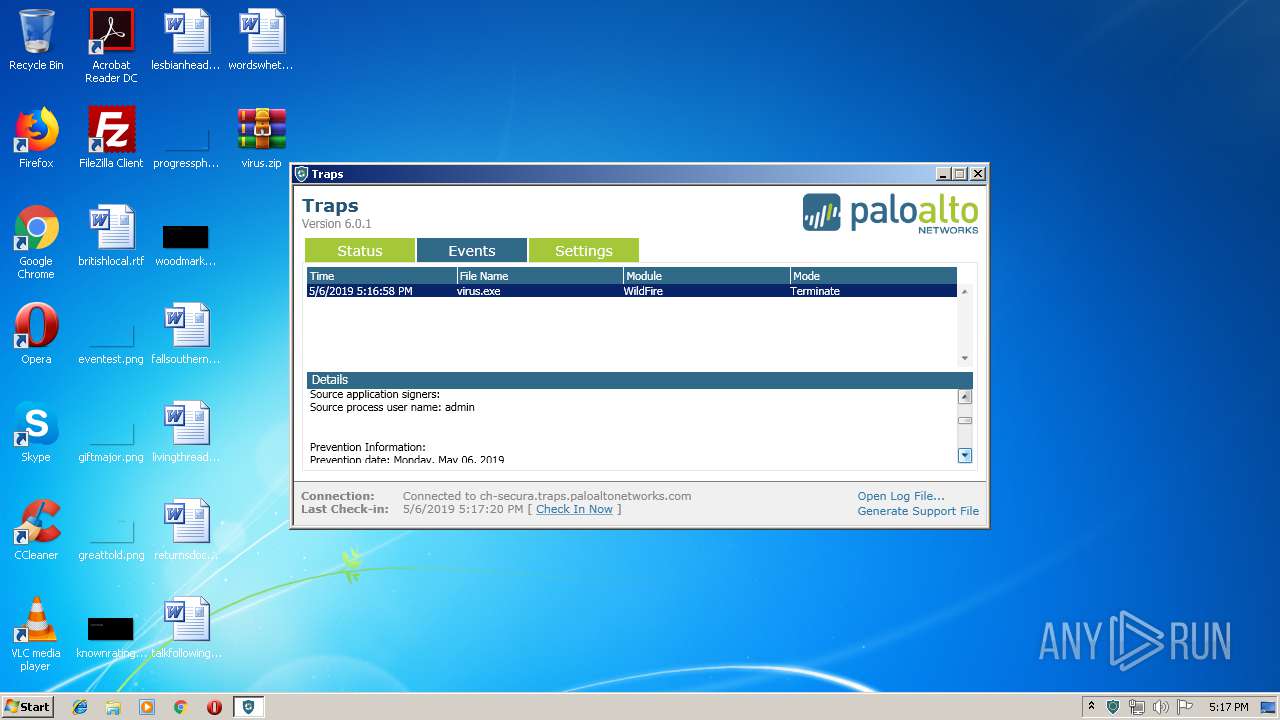
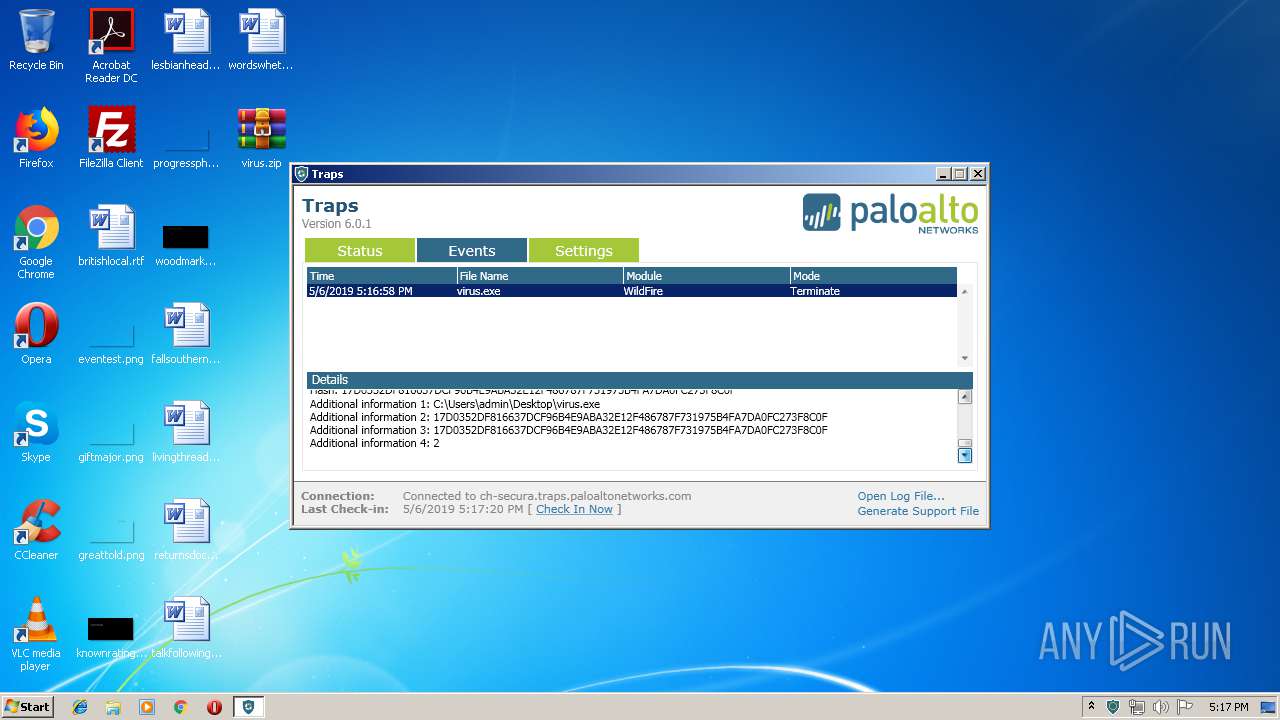
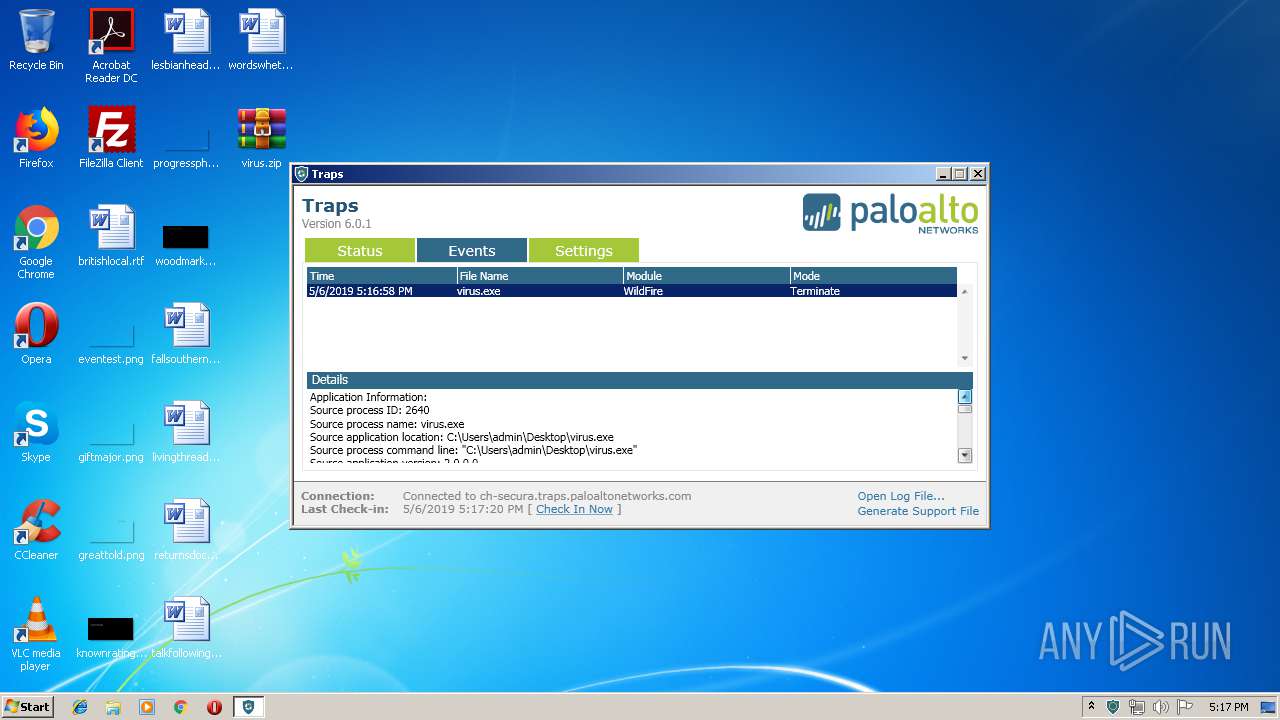
| File name: | virus.zip |
| Full analysis: | https://app.any.run/tasks/d49b4de0-d9b6-411c-ab54-c8abd746c0a9 |
| Verdict: | Malicious activity |
| Analysis date: | May 06, 2019, 16:13:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | E2FA9935CADB068C0357BAF20674380B |
| SHA1: | 1DDC65D33A0BC2A1DD562AC382C66B5FD92C79A4 |
| SHA256: | 1D1CEF5533208E6F54E849B08FE4C7A9AD7A90216C014B95889AEB5730318893 |
| SSDEEP: | 6144:F7odAFWtW0eijSjUtISl6Ji1zyS8LifkuSLIclBT+Qd7UWL5ZP:Fk20tW0rf10+zLfk3LdlBT+QdUW1ZP |
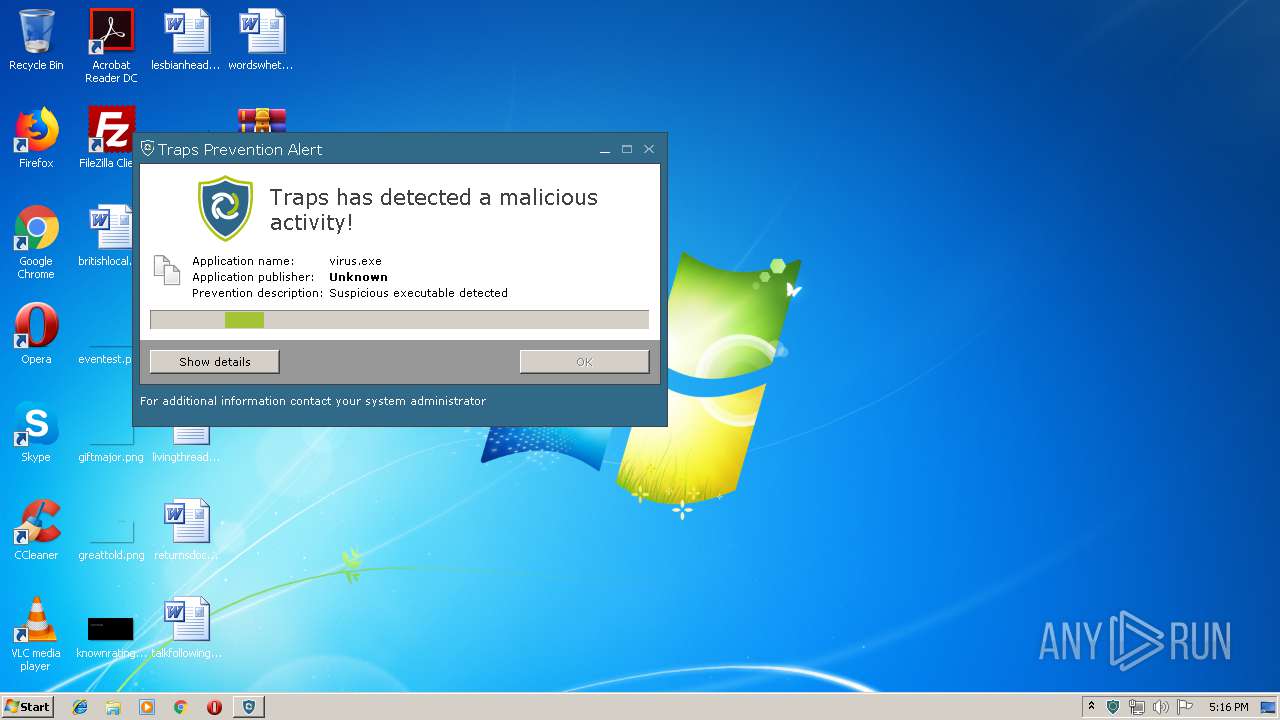
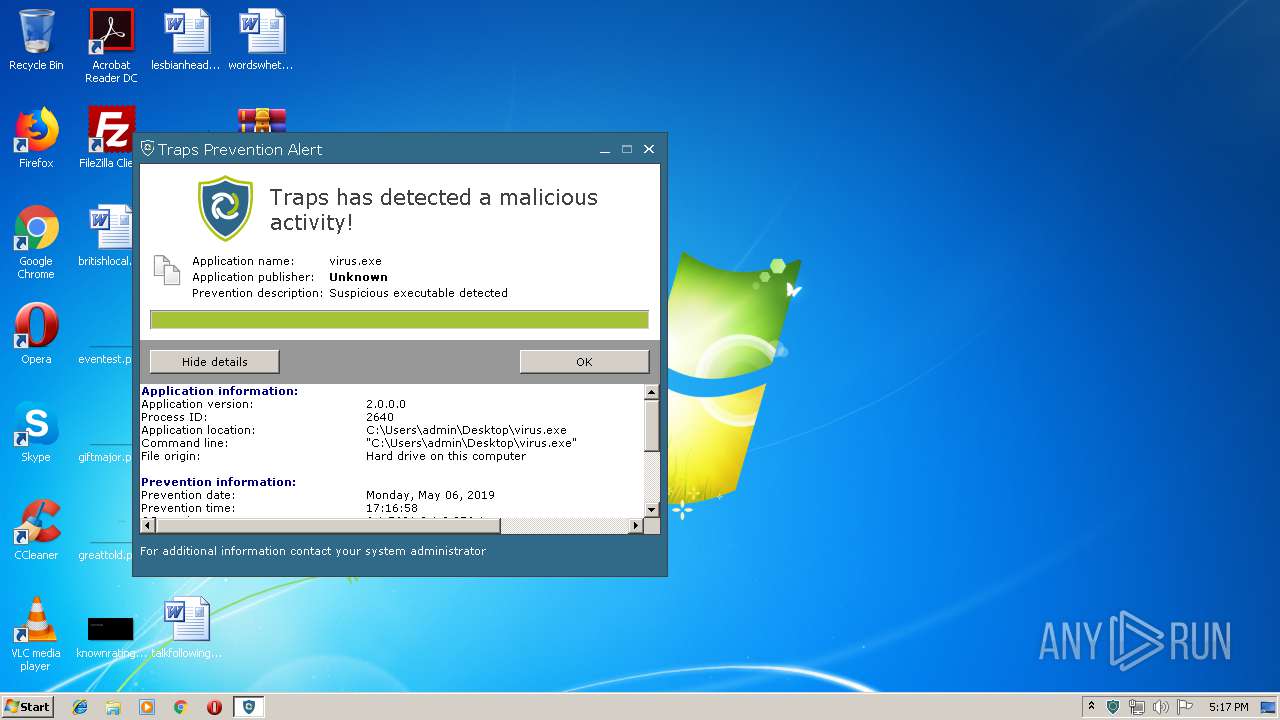
MALICIOUS
Loads dropped or rewritten executable
- rundll32.exe (PID: 4092)
- rundll32.exe (PID: 3424)
- rundll32.exe (PID: 980)
- rundll32.exe (PID: 2384)
- rundll32.exe (PID: 2492)
- rundll32.exe (PID: 1936)
- rundll32.exe (PID: 592)
- rundll32.exe (PID: 2528)
- rundll32.exe (PID: 388)
- rundll32.exe (PID: 2540)
- rundll32.exe (PID: 2788)
- rundll32.exe (PID: 2664)
- cytray.exe (PID: 3108)
- rundll32.exe (PID: 2380)
- rundll32.exe (PID: 2312)
- rundll32.exe (PID: 556)
- twdservice.exe (PID: 3772)
- rundll32.exe (PID: 3004)
- CyveraService.exe (PID: 3000)
- cyserver.exe (PID: 3064)
- rundll32.exe (PID: 292)
- tlaworker.exe (PID: 1656)
- tlaworker.exe (PID: 2808)
- tlaworker.exe (PID: 2372)
- tlaworker.exe (PID: 2116)
- rundll32.exe (PID: 1184)
- CyveraConsole.exe (PID: 1476)
- explorer.exe (PID: 2044)
- regsvr32.exe (PID: 3004)
- svchost.exe (PID: 848)
- CyveraConsole.exe (PID: 3956)
- regsvr32.exe (PID: 1336)
- CyveraConsole.exe (PID: 3612)
- CyveraConsole.exe (PID: 1436)
- cyreport.exe (PID: 2292)
- CyveraConsole.exe (PID: 2772)
- CyveraConsole.exe (PID: 3560)
- CyveraConsole.exe (PID: 3260)
- CyveraConsole.exe (PID: 3700)
- tlaservice.exe (PID: 3168)
- cyrprtui.exe (PID: 2916)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 3100)
- cmd.exe (PID: 2632)
Runs injected code in another process
- rundll32.exe (PID: 2540)
Application was injected by another process
- explorer.exe (PID: 2044)
Application was dropped or rewritten from another process
- cyserver.exe (PID: 3064)
- CyveraConsole.exe (PID: 1476)
- tlaworker.exe (PID: 2808)
- tlaworker.exe (PID: 1656)
- tlaworker.exe (PID: 2372)
- twdservice.exe (PID: 3772)
- tlaworker.exe (PID: 2116)
- tlaservice.exe (PID: 3168)
- CyveraService.exe (PID: 3000)
- CyveraConsole.exe (PID: 3612)
- cytray.exe (PID: 3108)
- CyveraConsole.exe (PID: 3956)
- virus.exe (PID: 2640)
- cyreport.exe (PID: 2292)
- cyrprtui.exe (PID: 2916)
- CyveraConsole.exe (PID: 1436)
- explorer.exe (PID: 2044)
- CyveraConsole.exe (PID: 2772)
- CyveraConsole.exe (PID: 3260)
- CyveraConsole.exe (PID: 3560)
- CyveraConsole.exe (PID: 3700)
Changes settings of System certificates
- CyveraService.exe (PID: 3000)
SUSPICIOUS
Creates files in the user directory
- explorer.exe (PID: 2044)
- CyveraConsole.exe (PID: 1476)
Reads Internet Cache Settings
- explorer.exe (PID: 2044)
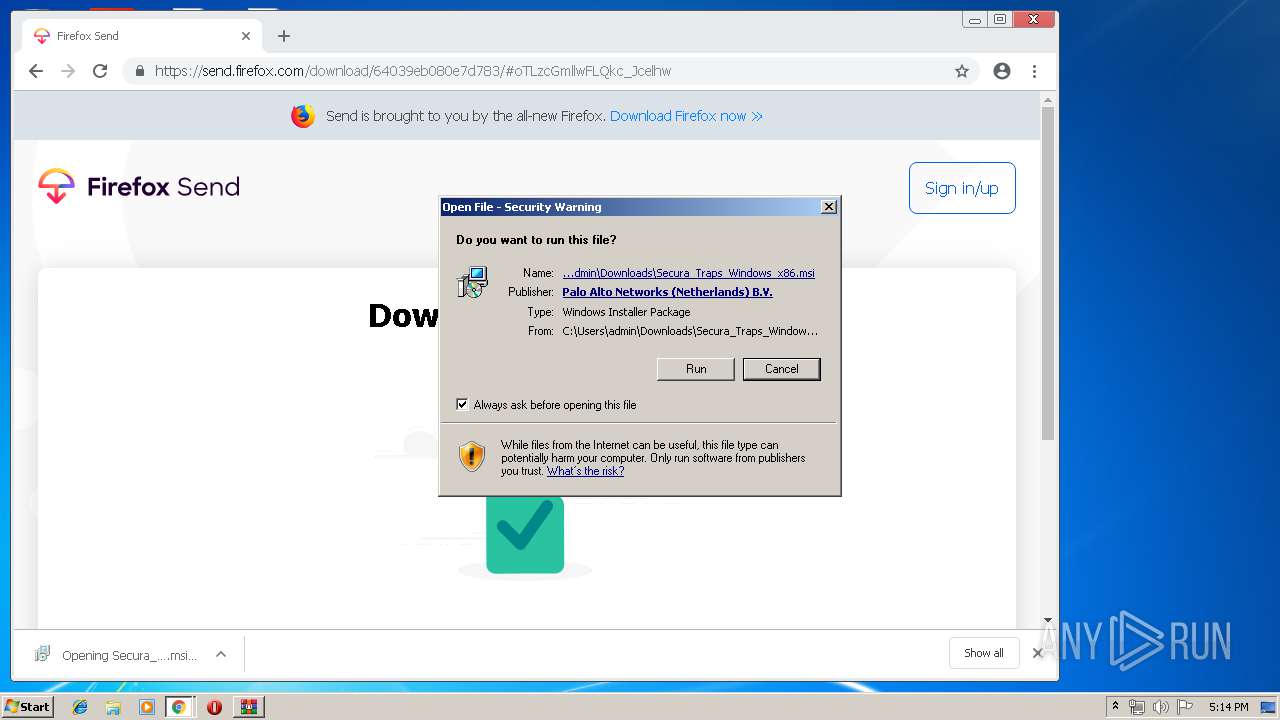
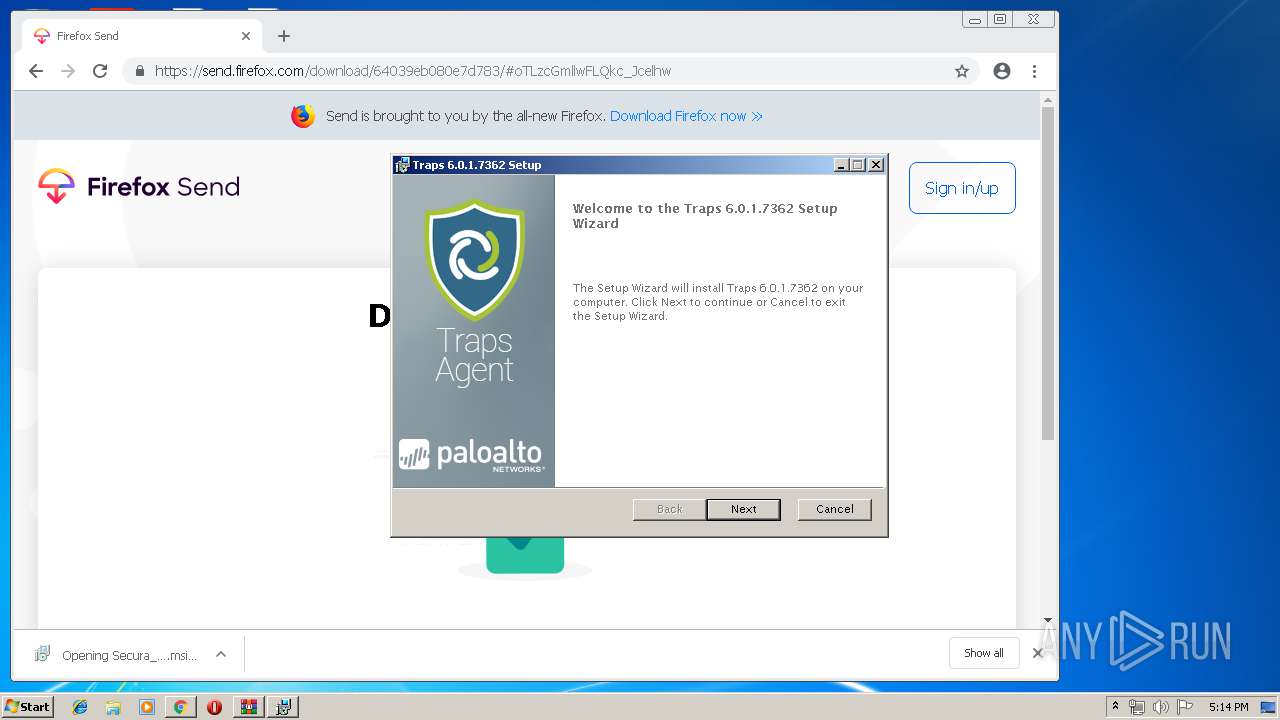
Starts Microsoft Installer
- chrome.exe (PID: 3692)
Uses RUNDLL32.EXE to load library
- MsiExec.exe (PID: 3528)
- MsiExec.exe (PID: 480)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3692)
Executable content was dropped or overwritten
- rundll32.exe (PID: 4092)
- rundll32.exe (PID: 980)
- rundll32.exe (PID: 2492)
- rundll32.exe (PID: 2528)
- msiexec.exe (PID: 2176)
- rundll32.exe (PID: 2540)
- rundll32.exe (PID: 2788)
- rundll32.exe (PID: 2312)
- rundll32.exe (PID: 2380)
- rundll32.exe (PID: 556)
- rundll32.exe (PID: 3004)
- rundll32.exe (PID: 1184)
- WinRAR.exe (PID: 2616)
- cyreport.exe (PID: 2292)
Starts CMD.EXE for commands execution
- MsiExec.exe (PID: 3528)
- twdservice.exe (PID: 3772)
Creates files in the Windows directory
- msiexec.exe (PID: 2176)
- CyveraService.exe (PID: 3000)
- tlaservice.exe (PID: 3168)
Creates COM task schedule object
- regsvr32.exe (PID: 3004)
Changes the autorun value in the registry
- msiexec.exe (PID: 2176)
Creates files in the program directory
- rundll32.exe (PID: 2540)
- rundll32.exe (PID: 2664)
- CyveraConsole.exe (PID: 1476)
- CyveraService.exe (PID: 3000)
- CyveraConsole.exe (PID: 1436)
- cyreport.exe (PID: 2292)
- CyveraConsole.exe (PID: 3260)
- CyveraConsole.exe (PID: 2772)
- tlaservice.exe (PID: 3168)
Starts SC.EXE for service management
- cmd.exe (PID: 2620)
Removes files from Windows directory
- CyveraService.exe (PID: 3000)
- tlaservice.exe (PID: 3168)
Adds / modifies Windows certificates
- CyveraService.exe (PID: 3000)
INFO
Reads settings of System Certificates
- chrome.exe (PID: 3692)
- CyveraService.exe (PID: 3000)
- tlaservice.exe (PID: 3168)
Reads Internet Cache Settings
- chrome.exe (PID: 3692)
Adds / modifies Windows certificates
- DrvInst.exe (PID: 1260)
Creates files in the user directory
- opera.exe (PID: 1088)
Application launched itself
- chrome.exe (PID: 3692)
- msiexec.exe (PID: 2176)
Searches for installed software
- msiexec.exe (PID: 2176)
Changes settings of System certificates
- DrvInst.exe (PID: 1260)
Dropped object may contain Bitcoin addresses
- rundll32.exe (PID: 4092)
- rundll32.exe (PID: 2492)
- rundll32.exe (PID: 980)
- rundll32.exe (PID: 2528)
- msiexec.exe (PID: 2176)
- rundll32.exe (PID: 2540)
- rundll32.exe (PID: 2788)
- rundll32.exe (PID: 2380)
- rundll32.exe (PID: 2312)
- rundll32.exe (PID: 556)
- rundll32.exe (PID: 1184)
- CyveraService.exe (PID: 3000)
Low-level read access rights to disk partition
- vssvc.exe (PID: 2768)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 480)
Creates or modifies windows services
- msiexec.exe (PID: 2176)
Creates files in the program directory
- msiexec.exe (PID: 2176)
Creates a software uninstall entry
- msiexec.exe (PID: 2176)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:04:29 17:04:06 |
| ZipCRC: | 0x432e0243 |
| ZipCompressedSize: | 262979 |
| ZipUncompressedSize: | 398336 |
| ZipFileName: | virus.exe |
Total processes
118
Monitored processes
80
Malicious processes
33
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | rundll32.exe "C:\Windows\Installer\MSID29A.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1233781 1 Cyvera.Client.CustomActions!Cyvera.Client.CustomActions.Sessions.GetNtVersion | C:\Windows\system32\rundll32.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 388 | rundll32.exe "C:\Windows\Installer\MSIF032.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1241140 177 Cyvera.Client.CustomActions!Cyvera.Client.CustomActions.Services.InstallService | C:\Windows\system32\rundll32.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 480 | C:\Windows\system32\MsiExec.exe -Embedding AAD93424DCE17D29C7B2AE24200EF86E | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 556 | rundll32.exe "C:\Windows\Installer\MSI3330.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1258296 252 Cyvera.Client.CustomActions!Cyvera.Client.CustomActions.Services.StartService | C:\Windows\system32\rundll32.exe | MsiExec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 592 | rundll32.exe "C:\Windows\Installer\MSIEC57.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1240156 159 Cyvera.Client.CustomActions!Cyvera.Client.CustomActions.Services.InstallService | C:\Windows\system32\rundll32.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,16459374194525471050,15626566159301180985,131072 --enable-features=PasswordImport --service-pipe-token=9762679547080834876 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9762679547080834876 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1968 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 836 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,16459374194525471050,15626566159301180985,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=16119437451924673527 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16119437451924673527 --renderer-client-id=18 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3756 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 848 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 940 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Downloads\Secura_Traps_Windows_x86.msi" | C:\Windows\System32\msiexec.exe | — | chrome.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 980 | rundll32.exe "C:\Windows\Installer\MSIE01F.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1237281 141 Cyvera.Client.CustomActions!Cyvera.Client.CustomActions.Services.CopyPathToTemp | C:\Windows\system32\rundll32.exe | MsiExec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
17 684
Read events
5 690
Write events
9 031
Delete events
2 963
Modification events
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2044) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {7P5N40RS-N0SO-4OSP-874N-P0S2R0O9SN8R}\Bcren\bcren.rkr |
Value: 00000000010000000000000000000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF6007EFA22604D50100000000 | |||
| (PID) Process: | (2044) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000050000000300000076A000000200000002000000724300004D006900630072006F0073006F00660074002E004100750074006F00470065006E006500720061007400650064002E007B00310035003900360032003100370035002D0037004400460043002D0042003100440037002D0042003000440031002D004500420034004300300038004600460044003700350034007D000000120200000000CC0B120200000000CC0B12020400050005001F02280C12020800050005001F026CE71F020100000154001F0200000100B8139D75444812020C0003000300000000000500280C12020000000005000000CC0B120201000000C8E91F02C0E91F0200000000C8FDDE02C0FCDE0244E71F023DA9457600000000FBFFFF7F68E71F02987880574F8C6244BB6371042380B1090000000001100211FFFFFFFF00000000000000000000000035EE190651EE190635EE1906000000000000000000000000080000002E006C006E006B0000005300630068006500640075006C00650072002E006C006E006B00000014000000140050000000070000000200060026030200A5863C750800000064021400E72F1B77B5863C753F030000CC04140000001400A86D150011000000B8451700B045170005000000F8F3DD0270E80000F28635BB20E81F028291457670E81F0224E81F022795457600000000ECD2DD024CE81F02CD944576ECD2DD02F8E81F0260CEDD02E19445760000000060CEDD02F8E81F0254E81F020200000002000000724300004D006900630072006F0073006F00660074002E004100750074006F00470065006E006500720061007400650064002E007B00310035003900360032003100370035002D0037004400460043002D0042003100440037002D0042003000440031002D004500420034004300300038004600460044003700350034007D000000120200000000CC0B120200000000CC0B12020400050005001F02280C12020800050005001F026CE71F020100000154001F0200000100B8139D75444812020C0003000300000000000500280C12020000000005000000CC0B120201000000C8E91F02C0E91F0200000000C8FDDE02C0FCDE0244E71F023DA9457600000000FBFFFF7F68E71F02987880574F8C6244BB6371042380B1090000000001100211FFFFFFFF00000000000000000000000035EE190651EE190635EE1906000000000000000000000000080000002E006C006E006B0000005300630068006500640075006C00650072002E006C006E006B00000014000000140050000000070000000200060026030200A5863C750800000064021400E72F1B77B5863C753F030000CC04140000001400A86D150011000000B8451700B045170005000000F8F3DD0270E80000F28635BB20E81F028291457670E81F0224E81F022795457600000000ECD2DD024CE81F02CD944576ECD2DD02F8E81F0260CEDD02E19445760000000060CEDD02F8E81F0254E81F020200000002000000724300004D006900630072006F0073006F00660074002E004100750074006F00470065006E006500720061007400650064002E007B00310035003900360032003100370035002D0037004400460043002D0042003100440037002D0042003000440031002D004500420034004300300038004600460044003700350034007D000000120200000000CC0B120200000000CC0B12020400050005001F02280C12020800050005001F026CE71F020100000154001F0200000100B8139D75444812020C0003000300000000000500280C12020000000005000000CC0B120201000000C8E91F02C0E91F0200000000C8FDDE02C0FCDE0244E71F023DA9457600000000FBFFFF7F68E71F02987880574F8C6244BB6371042380B1090000000001100211FFFFFFFF00000000000000000000000035EE190651EE190635EE1906000000000000000000000000080000002E006C006E006B0000005300630068006500640075006C00650072002E006C006E006B00000014000000140050000000070000000200060026030200A5863C750800000064021400E72F1B77B5863C753F030000CC04140000001400A86D150011000000B8451700B045170005000000F8F3DD0270E80000F28635BB20E81F028291457670E81F0224E81F022795457600000000ECD2DD024CE81F02CD944576ECD2DD02F8E81F0260CEDD02E19445760000000060CEDD02F8E81F0254E81F02 | |||
| (PID) Process: | (2044) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Bcren12.15 1748.yax |
Value: 00000000010000000000000000000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF6007EFA22604D50100000000 | |||
| (PID) Process: | (2044) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000000400000000000000030000000200000000000000020000007B00300031003300390044003400340045002D0036004100460045002D0034003900460032002D0038003600390030002D003300440041004600430041004500360046004600420038007D005C004100630063006500730073006F0072006900650073005C00530079007300740065006D00200054006F006F006C0073005C005400610073006B0020005300630068006500640075006C00650072002E006C006E006B0000006C006E006B0000008006EDE0177749713800FEFFFFFFE72F1B77822E1B77B8F944763302000086000000B5B9A3710000000008E1F00520661400F8671400D891FE05987D1400AC3600378CD6800648DE800654F98006EDE01777497138000000000030D78006399C26762062D802800200008000000031000000A064D8022062D80254D78006DE9C26762062D80200000000B102000008000000B90200005CD78006330200001862D80284D78006431945764B64D802489F1D00860000001862D8022094FE0533020000B8F94476541E0000C8B0D102A0D7800633AB1B77C880C7C6000C00001027000012000000AC540200D4D78006F8AA1B77AC540200C8B0D102F4D78006B0B7DE0274D8800600000000A301000034D8000036B9AABFE4D780068291457634D88006E8D7800627954576000000003CBCDE0210D88006CD9445763CBCDE02BCD88006B0B7DE02E194457600000000B0B7DE02BCD8800618D880060200000000000000020000007B00300031003300390044003400340045002D0036004100460045002D0034003900460032002D0038003600390030002D003300440041004600430041004500360046004600420038007D005C004100630063006500730073006F0072006900650073005C00530079007300740065006D00200054006F006F006C0073005C005400610073006B0020005300630068006500640075006C00650072002E006C006E006B0000006C006E006B0000008006EDE0177749713800FEFFFFFFE72F1B77822E1B77B8F944763302000086000000B5B9A3710000000008E1F00520661400F8671400D891FE05987D1400AC3600378CD6800648DE800654F98006EDE01777497138000000000030D78006399C26762062D802800200008000000031000000A064D8022062D80254D78006DE9C26762062D80200000000B102000008000000B90200005CD78006330200001862D80284D78006431945764B64D802489F1D00860000001862D8022094FE0533020000B8F94476541E0000C8B0D102A0D7800633AB1B77C880C7C6000C00001027000012000000AC540200D4D78006F8AA1B77AC540200C8B0D102F4D78006B0B7DE0274D8800600000000A301000034D8000036B9AABFE4D780068291457634D88006E8D7800627954576000000003CBCDE0210D88006CD9445763CBCDE02BCD88006B0B7DE02E194457600000000B0B7DE02BCD8800618D880060200000000000000020000007B00300031003300390044003400340045002D0036004100460045002D0034003900460032002D0038003600390030002D003300440041004600430041004500360046004600420038007D005C004100630063006500730073006F0072006900650073005C00530079007300740065006D00200054006F006F006C0073005C005400610073006B0020005300630068006500640075006C00650072002E006C006E006B0000006C006E006B0000008006EDE0177749713800FEFFFFFFE72F1B77822E1B77B8F944763302000086000000B5B9A3710000000008E1F00520661400F8671400D891FE05987D1400AC3600378CD6800648DE800654F98006EDE01777497138000000000030D78006399C26762062D802800200008000000031000000A064D8022062D80254D78006DE9C26762062D80200000000B102000008000000B90200005CD78006330200001862D80284D78006431945764B64D802489F1D00860000001862D8022094FE0533020000B8F94476541E0000C8B0D102A0D7800633AB1B77C880C7C6000C00001027000012000000AC540200D4D78006F8AA1B77AC540200C8B0D102F4D78006B0B7DE0274D8800600000000A301000034D8000036B9AABFE4D780068291457634D88006E8D7800627954576000000003CBCDE0210D88006CD9445763CBCDE02BCD88006B0B7DE02E194457600000000B0B7DE02BCD8800618D88006 | |||
| (PID) Process: | (2044) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Bcren12.15 1748.yax |
Value: 00000000010000000000000001000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF6007EFA22604D50100000000 | |||
| (PID) Process: | (2044) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000000400000000000000040000000200000000000000020000007B00300031003300390044003400340045002D0036004100460045002D0034003900460032002D0038003600390030002D003300440041004600430041004500360046004600420038007D005C004100630063006500730073006F0072006900650073005C00530079007300740065006D00200054006F006F006C0073005C005400610073006B0020005300630068006500640075006C00650072002E006C006E006B0000006C006E006B0000008006EDE0177749713800FEFFFFFFE72F1B77822E1B77B8F944763302000086000000B5B9A3710000000008E1F00520661400F8671400D891FE05987D1400AC3600378CD6800648DE800654F98006EDE01777497138000000000030D78006399C26762062D802800200008000000031000000A064D8022062D80254D78006DE9C26762062D80200000000B102000008000000B90200005CD78006330200001862D80284D78006431945764B64D802489F1D00860000001862D8022094FE0533020000B8F94476541E0000C8B0D102A0D7800633AB1B77C880C7C6000C00001027000012000000AC540200D4D78006F8AA1B77AC540200C8B0D102F4D78006B0B7DE0274D8800600000000A301000034D8000036B9AABFE4D780068291457634D88006E8D7800627954576000000003CBCDE0210D88006CD9445763CBCDE02BCD88006B0B7DE02E194457600000000B0B7DE02BCD8800618D880060200000000000000020000007B00300031003300390044003400340045002D0036004100460045002D0034003900460032002D0038003600390030002D003300440041004600430041004500360046004600420038007D005C004100630063006500730073006F0072006900650073005C00530079007300740065006D00200054006F006F006C0073005C005400610073006B0020005300630068006500640075006C00650072002E006C006E006B0000006C006E006B0000008006EDE0177749713800FEFFFFFFE72F1B77822E1B77B8F944763302000086000000B5B9A3710000000008E1F00520661400F8671400D891FE05987D1400AC3600378CD6800648DE800654F98006EDE01777497138000000000030D78006399C26762062D802800200008000000031000000A064D8022062D80254D78006DE9C26762062D80200000000B102000008000000B90200005CD78006330200001862D80284D78006431945764B64D802489F1D00860000001862D8022094FE0533020000B8F94476541E0000C8B0D102A0D7800633AB1B77C880C7C6000C00001027000012000000AC540200D4D78006F8AA1B77AC540200C8B0D102F4D78006B0B7DE0274D8800600000000A301000034D8000036B9AABFE4D780068291457634D88006E8D7800627954576000000003CBCDE0210D88006CD9445763CBCDE02BCD88006B0B7DE02E194457600000000B0B7DE02BCD8800618D880060200000000000000020000007B00300031003300390044003400340045002D0036004100460045002D0034003900460032002D0038003600390030002D003300440041004600430041004500360046004600420038007D005C004100630063006500730073006F0072006900650073005C00530079007300740065006D00200054006F006F006C0073005C005400610073006B0020005300630068006500640075006C00650072002E006C006E006B0000006C006E006B0000008006EDE0177749713800FEFFFFFFE72F1B77822E1B77B8F944763302000086000000B5B9A3710000000008E1F00520661400F8671400D891FE05987D1400AC3600378CD6800648DE800654F98006EDE01777497138000000000030D78006399C26762062D802800200008000000031000000A064D8022062D80254D78006DE9C26762062D80200000000B102000008000000B90200005CD78006330200001862D80284D78006431945764B64D802489F1D00860000001862D8022094FE0533020000B8F94476541E0000C8B0D102A0D7800633AB1B77C880C7C6000C00001027000012000000AC540200D4D78006F8AA1B77AC540200C8B0D102F4D78006B0B7DE0274D8800600000000A301000034D8000036B9AABFE4D780068291457634D88006E8D7800627954576000000003CBCDE0210D88006CD9445763CBCDE02BCD88006B0B7DE02E194457600000000B0B7DE02BCD8800618D88006 | |||
| (PID) Process: | (2044) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (2044) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
880
Suspicious files
299
Text files
511
Unknown types
130
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1088 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr4EC9.tmp | — | |
MD5:— | SHA256:— | |||
| 1088 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr4F08.tmp | — | |
MD5:— | SHA256:— | |||
| 1088 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00001.tmp | — | |
MD5:— | SHA256:— | |||
| 1088 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\BFBJGPF5ET6TCEE68J93.temp | — | |
MD5:— | SHA256:— | |||
| 1088 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr9BD2.tmp | — | |
MD5:— | SHA256:— | |||
| 1088 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\typed_history.xml | xml | |
MD5:— | SHA256:— | |||
| 1088 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\icons\https%3A%2F%2Fsend.firefox.com%2Ffavicon-16x16.dd949bf3.png | — | |
MD5:— | SHA256:— | |||
| 1088 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 1088 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
| 2044 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\virus.zip.lnk | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
128
TCP/UDP connections
100
DNS requests
59
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3000 | CyveraService.exe | GET | — | 188.121.36.237:80 | http://crl.godaddy.com/gdroot-g2.crl | NL | — | — | whitelisted |
1088 | opera.exe | GET | 200 | 216.58.205.238:80 | http://clients1.google.com/complete/search?q=tiny&client=opera-suggest-omnibox&hl=de | US | text | 107 b | whitelisted |
1088 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertGlobalRootCA.crl | US | der | 581 b | whitelisted |
1088 | opera.exe | GET | 200 | 192.35.177.64:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 896 b | whitelisted |
1088 | opera.exe | GET | 200 | 66.225.197.197:80 | http://crl4.digicert.com/DigiCertGlobalRootCA.crl | US | der | 581 b | whitelisted |
1088 | opera.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYdUvKOeNRji0LOHG2eICEA0TqIq5koce%2BY%2BAtbAl2U8%3D | US | der | 471 b | whitelisted |
1088 | opera.exe | GET | 200 | 216.58.205.238:80 | http://clients1.google.com/complete/search?q=tin&client=opera-suggest-omnibox&hl=de | US | text | 96 b | whitelisted |
1088 | opera.exe | GET | 200 | 66.225.197.197:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 543 b | whitelisted |
3000 | CyveraService.exe | GET | 200 | 188.121.36.239:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | NL | der | 1.66 Kb | whitelisted |
1088 | opera.exe | GET | 200 | 216.58.205.238:80 | http://clients1.google.com/complete/search?q=abo&client=opera-suggest-omnibox&hl=de | US | text | 108 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1088 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
1088 | opera.exe | 66.225.197.197:80 | crl4.digicert.com | CacheNetworks, Inc. | US | whitelisted |
1088 | opera.exe | 216.58.205.238:80 | clients1.google.com | Google Inc. | US | whitelisted |
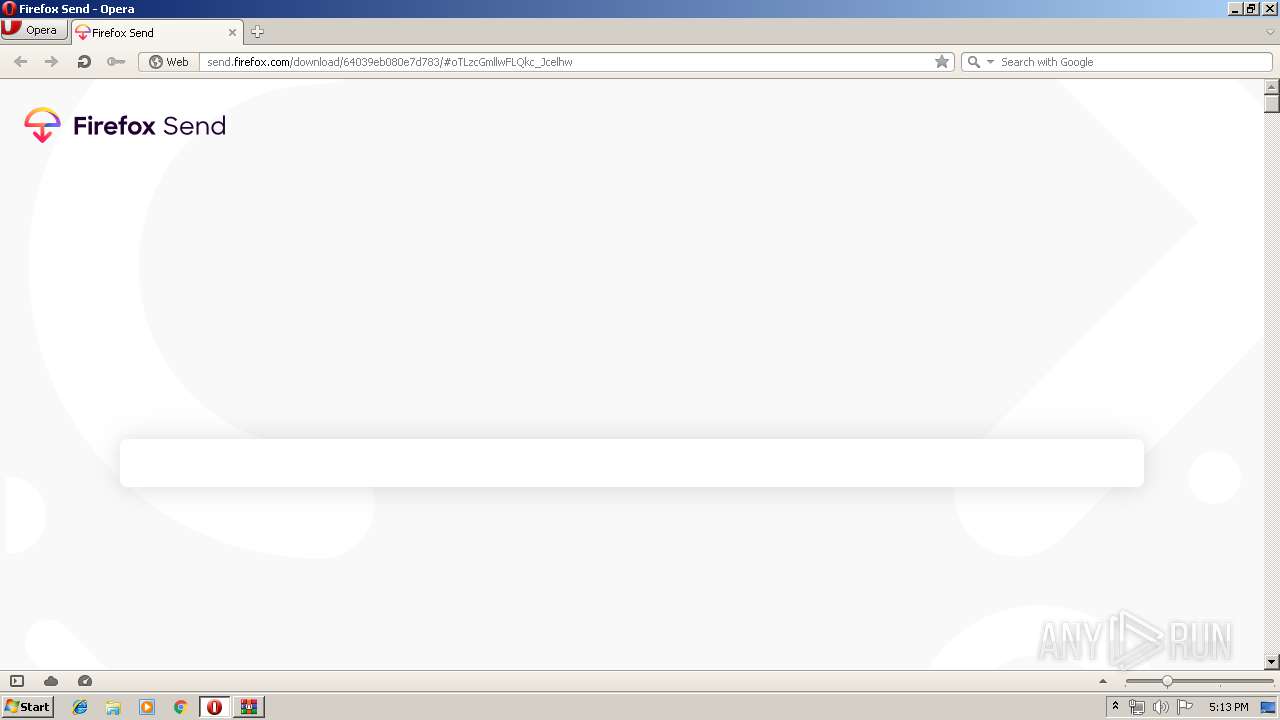
1088 | opera.exe | 35.186.224.242:443 | send.firefox.com | Google Inc. | US | suspicious |
3692 | chrome.exe | 172.217.18.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1088 | opera.exe | 93.184.220.29:80 | crl3.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3692 | chrome.exe | 216.58.208.35:443 | www.google.com.ua | Google Inc. | US | whitelisted |
3692 | chrome.exe | 216.58.206.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3692 | chrome.exe | 172.217.23.129:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
3692 | chrome.exe | 172.217.16.142:443 | apis.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
clients1.google.com |
| whitelisted |
tiny.cc |
| malicious |
sitecheck2.opera.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
crl.identrust.com |
| whitelisted |
send.firefox.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1068 | svchost.exe | A Network Trojan was detected | ET POLICY URL Shortener Service Domain in DNS Lookup (tiny .cc) |
1088 | opera.exe | A Network Trojan was detected | ET POLICY Observed SSL Cert (URL Shortener Service - tiny .cc) |
3692 | chrome.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
3692 | chrome.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
3000 | CyveraService.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
3000 | CyveraService.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
3000 | CyveraService.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |