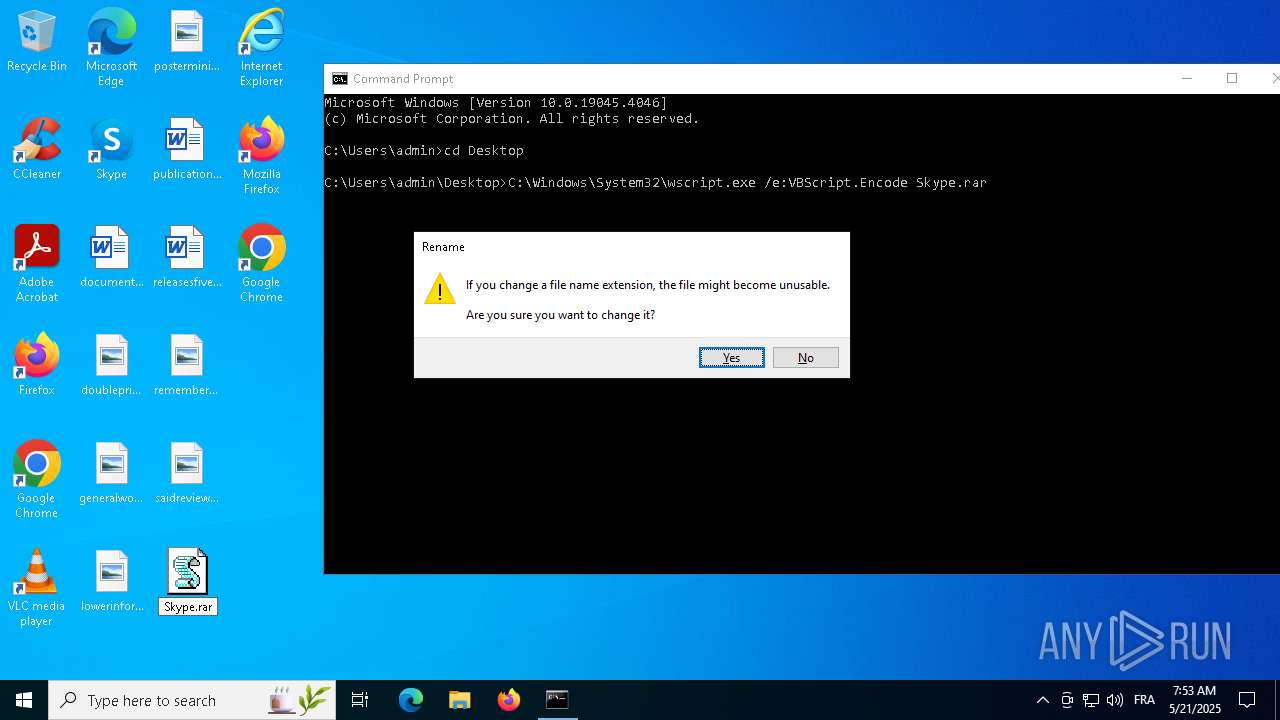
| File name: | Skype.rar |
| Full analysis: | https://app.any.run/tasks/cb534811-c0f6-4427-ad0e-9566a196a138 |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2025, 07:51:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | 12AF6B0F7D5850DDDE54708248C150CD |
| SHA1: | 30147AA093344099290A209D0962CB1B876B5113 |
| SHA256: | 1D13661D712CB20730A5FCFD1013B030DFBD88BC90296A0F03AE04652F21BC62 |
| SSDEEP: | 768:OTWxefR9XX7f6WDVpb9EGpFNx4WxbgZpAs8t++ji9F70jqn:OTYefR9XX7PBt4WRKpAsWxjO0A |
MALICIOUS
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 7432)
Creates a new registry key or changes the value of an existing one (SCRIPT)
- wscript.exe (PID: 7432)
Modifies registry startup key (SCRIPT)
- wscript.exe (PID: 7432)
Create files in the Startup directory
- wscript.exe (PID: 7432)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 7432)
Bypass User Account Control (fodhelper)
- fodhelper.exe (PID: 2656)
SUSPICIOUS
Runs shell command (SCRIPT)
- wscript.exe (PID: 7432)
Accesses current user name via WMI (SCRIPT)
- wscript.exe (PID: 7432)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 7432)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- wscript.exe (PID: 7432)
INFO
Manual execution by a user
- cmd.exe (PID: 7880)
Reads the software policy settings
- slui.exe (PID: 7624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .vbe | | | VBScript Encoded script (100) |
|---|
Total processes
147
Monitored processes
10
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2656 | C:\WINDOWS\System32\FodHelper.exe -Embedding | C:\Windows\System32\fodhelper.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Features On Demand Helper Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4880 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7432 | "C:\WINDOWS\System32\WScript.exe" C:\Users\admin\Desktop\Skype.rar.vbe | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7592 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7624 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7880 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8036 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
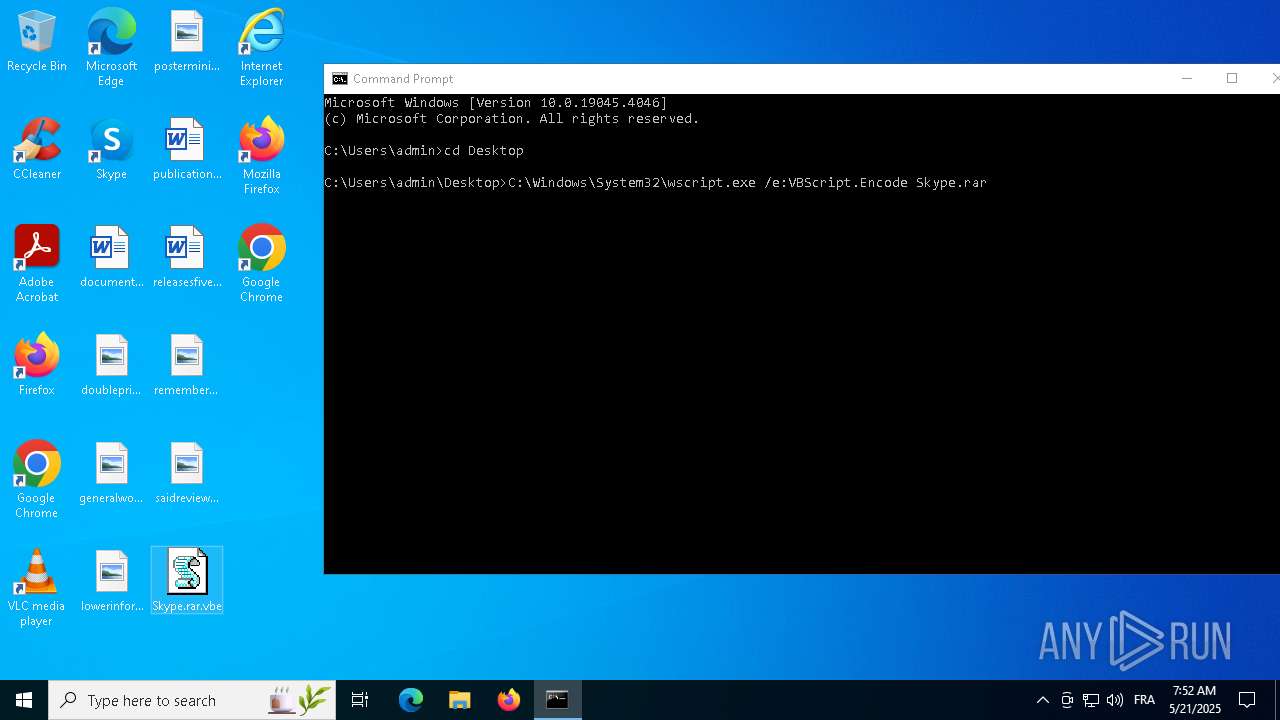
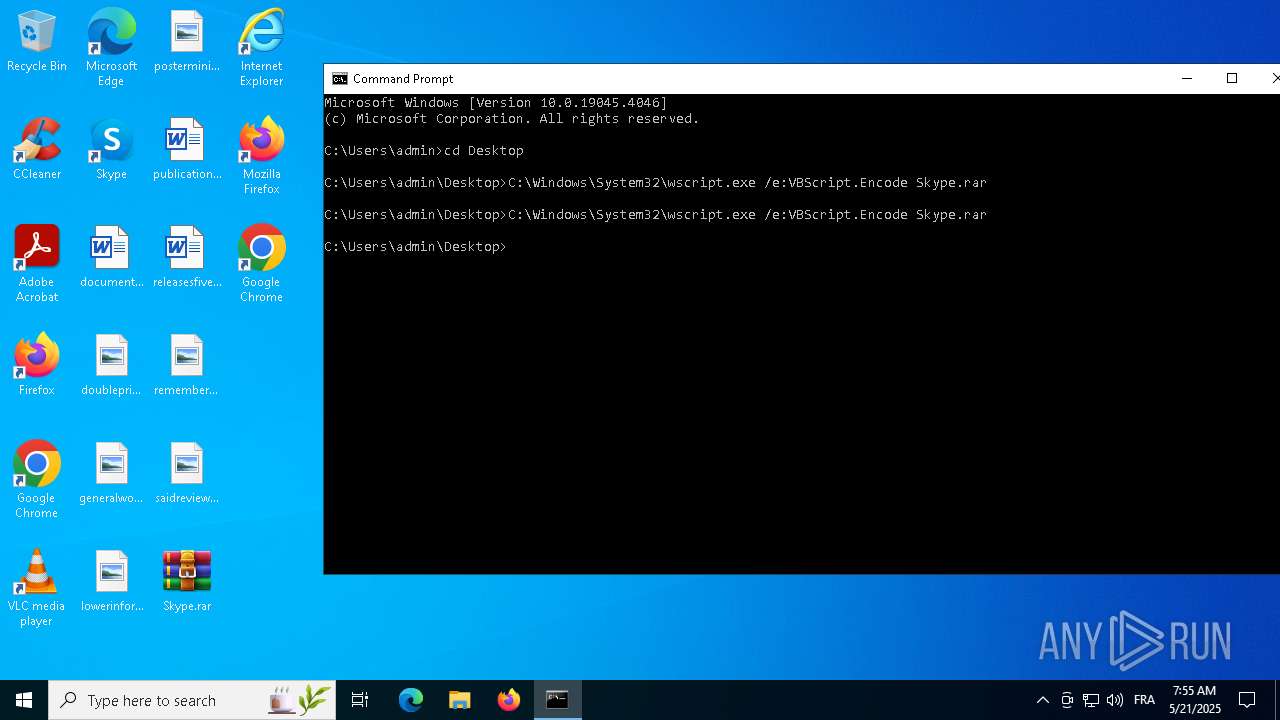
| 8100 | C:\Windows\System32\wscript.exe /e:VBScript.Encode Skype.rar | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 8152 | C:\Windows\System32\wscript.exe /e:VBScript.Encode Skype.rar | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
5 012
Read events
5 000
Write events
12
Delete events
0
Modification events
| (PID) Process: | (4880) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31181349 | |||
| (PID) Process: | (4880) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: 690855196 | |||
| (PID) Process: | (4880) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: 689435373 | |||
| (PID) Process: | (4880) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: 689435374 | |||
| (PID) Process: | (4880) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: 700681607 | |||
| (PID) Process: | (4880) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: 979151236 | |||
| (PID) Process: | (4880) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: 981492833 | |||
Executable files
0
Suspicious files
10
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7432 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Manualadmin.lnk | binary | |
MD5:2250D6BABA299179442104324CB655D2 | SHA256:AC9FAEFBAFA1620A4BABA10581AAA832FF6CCC6151D161BDCF610472660FE6A3 | |||
| 7432 | wscript.exe | C:\Users\admin\Desktop\Google Chrome.lnk | binary | |
MD5:361BABA400CF4B8CA47C44F8AD2373C3 | SHA256:39743056EFD586B1B85EFC011A692456061BB073FFCB8219AB080F69D1D116B7 | |||
| 7432 | wscript.exe | C:\Users\admin\Desktop\Mozilla Firefox.lnk | binary | |
MD5:8DD9DC758EB5E3E71460CF59A9AAF226 | SHA256:CDA99FDEBCE7B898408F75ADA5F3F988928E325607EFA4688EE686F363E23551 | |||
| 7432 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\Mozilla Firefox.LNK | binary | |
MD5:DD7336028D773A7F1437E72C31D84AAB | SHA256:AFC87E80D88BE3811CD831D30B0734430BFE6AA904047B681B1121488AFBCBE1 | |||
| 8152 | wscript.exe | C:\admin\01 | binary | |
MD5:12AF6B0F7D5850DDDE54708248C150CD | SHA256:1D13661D712CB20730A5FCFD1013B030DFBD88BC90296A0F03AE04652F21BC62 | |||
| 7432 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\Internet Explorer.LNK | binary | |
MD5:9552DC603C3430E5369C4C2B62A783A0 | SHA256:6CD4D73D91627662FFC48D9D4749638E3AFDD12F0C6E4EFB9B265A72707AFE52 | |||
| 7432 | wscript.exe | C:\Users\admin\Desktop\Internet Explorer.lnk | binary | |
MD5:A54A081B288A6F1904AA6FA30FF5C8B8 | SHA256:C5A0F884F27A7F7088DE2C6E0546C3085869EF7A8BC8B33CD6315EB1BC547213 | |||
| 8152 | wscript.exe | C:\admin\Skype.rar | binary | |
MD5:12AF6B0F7D5850DDDE54708248C150CD | SHA256:1D13661D712CB20730A5FCFD1013B030DFBD88BC90296A0F03AE04652F21BC62 | |||
| 7432 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Helpadmin.lnk | binary | |
MD5:7E8B10B64844442BA7D4015E1AC16600 | SHA256:A2B09E630A2B34775F069F5FD0963F49F9D49AB7BCE2A0B249D192CD45387E30 | |||
| 7432 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\chrome.LNK | binary | |
MD5:A1CD442AA7F0D4EEEE318EACBE0CC971 | SHA256:8F877DB6CC46868F15E34FD886A039FB5A4CA893583BF4E66DDCF9096DC46207 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
38
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4156 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4156 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1280 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1280 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
cxcs.microsoft.net |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |