| File name: | 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin |
| Full analysis: | https://app.any.run/tasks/ffbc1986-9d7d-4184-8b8a-94fe8427fd4b |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2025, 09:58:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 1EBE81AA5E1FA13F8C5A5F0A54DD6B23 |
| SHA1: | 7DBFAD859C653997DD35BFAAEBD7F9BD368D35F1 |
| SHA256: | 1CFE4F92E281FDD504F5E9FFA9C10DDD781F52E20D128FBCB269FF9474D7257A |
| SSDEEP: | 49152:46VnvKZko85VNMA/qY+Vw8l9FD/NEYHRtBq/+uBXjPhcFcRTVfCg7AZdZAh1EHqW:46VnvK+V7B+VpFD/NnHRfq2uBzPhpV9M |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 6404)
SUSPICIOUS
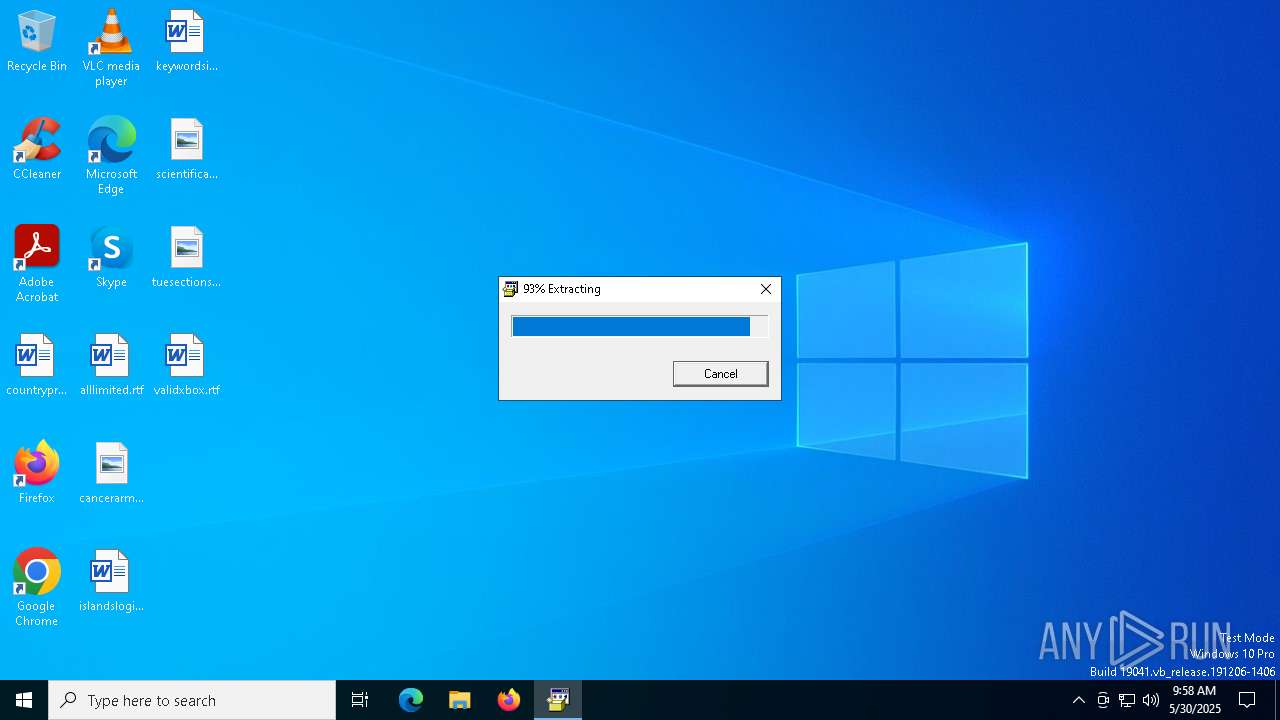
Drops 7-zip archiver for unpacking
- 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe (PID: 728)
Executable content was dropped or overwritten
- 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe (PID: 728)
- cmd.exe (PID: 6404)
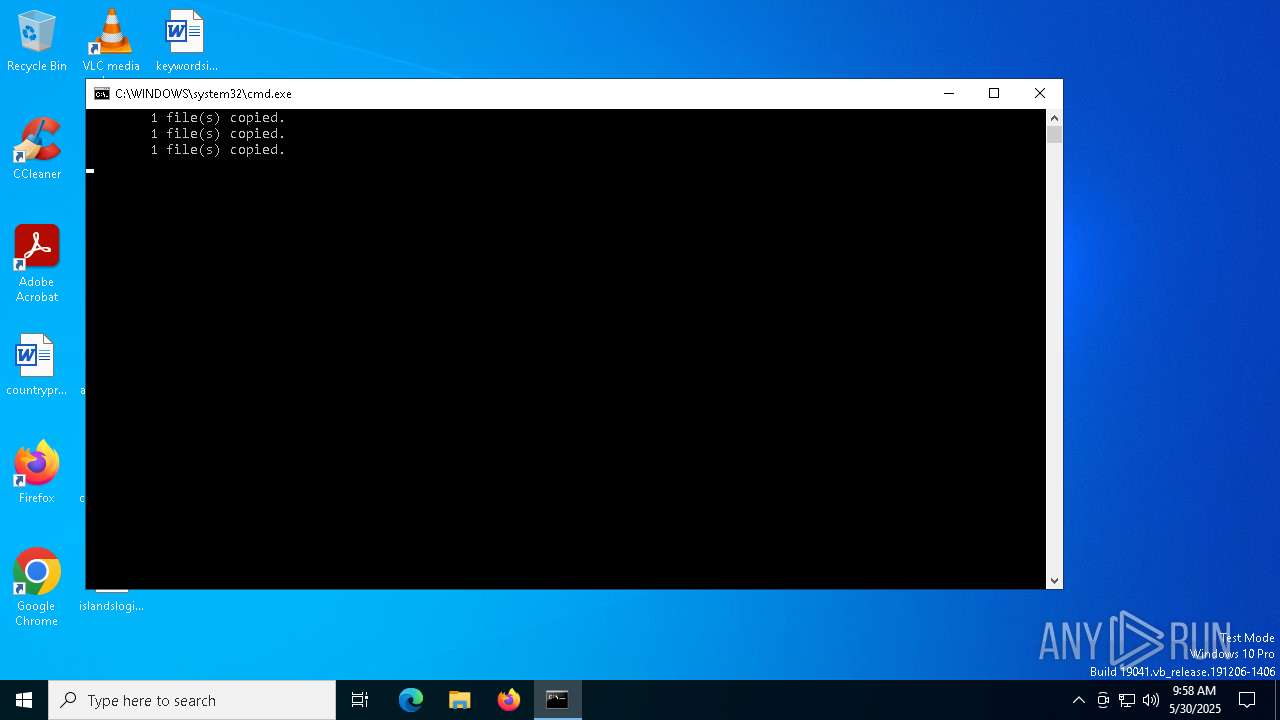
Starts CMD.EXE for commands execution
- 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe (PID: 728)
Process drops legitimate windows executable
- 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe (PID: 728)
- cmd.exe (PID: 6404)
Reads security settings of Internet Explorer
- 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe (PID: 728)
Executing commands from ".cmd" file
- 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe (PID: 728)
The executable file from the user directory is run by the CMD process
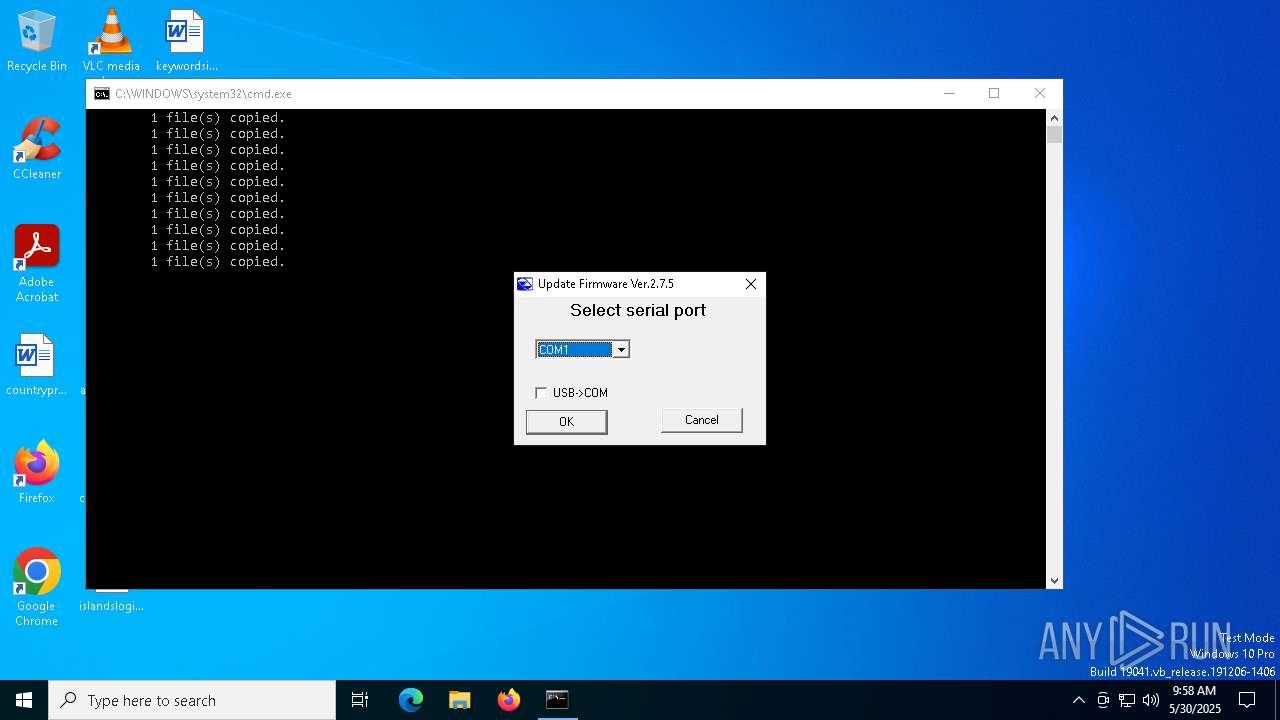
- Updatefw.exe (PID: 4164)
Creates/Modifies COM task schedule object
- Updatefw.exe (PID: 4164)
INFO
The sample compiled with english language support
- 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe (PID: 728)
- cmd.exe (PID: 6404)
Create files in a temporary directory
- 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe (PID: 728)
- Updatefw.exe (PID: 4164)
Reads the computer name
- 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe (PID: 728)
- Updatefw.exe (PID: 4164)
Checks supported languages
- 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe (PID: 728)
- Updatefw.exe (PID: 4164)
The sample compiled with Italian language support
- 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe (PID: 728)
- cmd.exe (PID: 6404)
Process checks computer location settings
- 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe (PID: 728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:04:18 18:54:06+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 104448 |
| InitializedDataSize: | 45056 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x148d4 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.22.0.0 |
| ProductVersionNumber: | 9.22.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Igor Pavlov |
| FileDescription: | 7z Setup SFX |
| FileVersion: | 9.22 beta |
| InternalName: | 7zS.sfx |
| LegalCopyright: | Copyright (c) 1999-2011 Igor Pavlov |
| OriginalFileName: | 7zS.sfx.exe |
| ProductName: | 7-Zip |
| ProductVersion: | 9.22 beta |
Total processes
143
Monitored processes
17
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | REGSVR32 /S C:\WINDOWS\SYSTEM32\DLLFILE\COMCT232.OCX | C:\Windows\SysWOW64\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | "C:\Users\admin\AppData\Local\Temp\1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe" | C:\Users\admin\AppData\Local\Temp\1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Setup SFX Version: 9.22 beta Modules
| |||||||||||||||
| 1532 | REGSVR32 /S C:\WINDOWS\SYSTEM32\DLLFILE\msvbvm50.dll | C:\Windows\SysWOW64\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2104 | REGSVR32 /S C:\WINDOWS\SYSTEM32\DLLFILE\comdlg32.dll | C:\Windows\SysWOW64\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2656 | REGSVR32 /S C:\WINDOWS\SYSTEM32\DLLFILE\COMCT332.OCX | C:\Windows\SysWOW64\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3884 | REGSVR32 /S C:\WINDOWS\SYSTEM32\DLLFILE\comdlg32.ocx | C:\Windows\SysWOW64\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4164 | Updatefw.exe C MOTFILE\Dgt06_07.13.01_ML_NL205.mot | C:\Users\admin\AppData\Local\Temp\7zS8D287191\Updatefw.exe | — | cmd.exe | |||||||||||
User: admin Company: DINI ARGEO s.r.l Integrity Level: HIGH Version: 2.07.0005 Modules
| |||||||||||||||
| 4220 | REGSVR32 /S C:\WINDOWS\SYSTEM32\DLLFILE\comctl32.dll | C:\Windows\SysWOW64\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4740 | REGSVR32 /S C:\WINDOWS\SYSTEM32\DLLFILE\vb5it.dll | C:\Windows\SysWOW64\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4844 | REGSVR32 /S C:\WINDOWS\SYSTEM32\DLLFILE\VB5STKIT.DLL | C:\Windows\SysWOW64\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 164
Read events
977
Write events
135
Delete events
52
Modification events
| (PID) Process: | (4164) Updatefw.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{58DA8D8A-9D6A-101B-AFC0-4210102A8DA7} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4164) Updatefw.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{58DA8D8A-9D6A-101B-AFC0-4210102A8DA7}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (4164) Updatefw.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{0713E8A2-850A-101B-AFC0-4210102A8DA7} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4164) Updatefw.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{0713E8A2-850A-101B-AFC0-4210102A8DA7}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (4164) Updatefw.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{0713E8A8-850A-101B-AFC0-4210102A8DA7} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4164) Updatefw.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{0713E8A8-850A-101B-AFC0-4210102A8DA7}\InprocServer32 |
| Operation: | delete value | Name: | ThreadingModel |
Value: | |||
| (PID) Process: | (4164) Updatefw.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{9ED94440-E5E8-101B-B9B5-444553540000} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4164) Updatefw.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{9ED94440-E5E8-101B-B9B5-444553540000}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (4164) Updatefw.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{9ED94444-E5E8-101B-B9B5-444553540000} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4164) Updatefw.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{9ED94444-E5E8-101B-B9B5-444553540000}\InprocServer32 |
| Operation: | delete value | Name: | ThreadingModel |
Value: | |||
Executable files
18
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 728 | 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe | C:\Users\admin\AppData\Local\Temp\7zS8D287191\MOTFILE\Dgt06_07.13.01_ML_NL205.mot | text | |
MD5:B3191FEB96BBC2F24FAA8E4A35ABDD38 | SHA256:83427F0C2DA4CC8C017855D48717B9ABF06D930077DBD8ECBB0DA1A23435B59C | |||
| 728 | 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe | C:\Users\admin\AppData\Local\Temp\7zS8D287191\DLLFILE\COMCT332.OCX | executable | |
MD5:821AB1F1CF9904CB9026C686F13F0F05 | SHA256:332E6A1CB4BF722092F9E774ECC14ACDDBF95A9655BEA021681B11AAC37AC716 | |||
| 728 | 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe | C:\Users\admin\AppData\Local\Temp\7zS8D287191\DLLFILE\comctl32.dll | executable | |
MD5:5DC6E15B3989AF66D09F39786FD7154E | SHA256:2A51EF254AC8E8332768B15B36205B690AC6C8C3EDB84E6903A4A812637B5512 | |||
| 728 | 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe | C:\Users\admin\AppData\Local\Temp\7zS8D287191\DLLFILE\comcat.dll | executable | |
MD5:961AE088EAB8E1A1F64F98713B4B41BD | SHA256:E83364165A4827662BF3B258FFB6232F6D3FF56AFFD9772E54145B7B5C485B2F | |||
| 728 | 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe | C:\Users\admin\AppData\Local\Temp\7zS8D287191\UPDATE.CMD | text | |
MD5:0052FAC1A8A59BC5EAB21FB6FDE2BA34 | SHA256:17EDF2375388C72DFB02606823DB7215402E89BED9489BB3E55C1B931416E57D | |||
| 6404 | cmd.exe | C:\Windows\SysWOW64\msvbvm50.dll | executable | |
MD5:AB2878B9CAC282129E8DBC83310920A7 | SHA256:DC5284B77E8ABD8A011D50075C94102F555105A7FEE5204E7A57F29BF1BC52DD | |||
| 6404 | cmd.exe | C:\Windows\SysWOW64\vb5it.dll | executable | |
MD5:AD1826AE0427BE4F65F2F41FE21735DE | SHA256:33831F45DC4EA749FCFB5CF59D45E2C0FF09FC814A52987D1EEEE563B6A37355 | |||
| 728 | 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe | C:\Users\admin\AppData\Local\Temp\7zS8D287191\Updatefw.exe | executable | |
MD5:77DAB9C66B14BFD99B46D76B6D25F78F | SHA256:0868B45D53E8B3A0FEA656F494C2C06E070963B358AA3B4DC12FFC5B10B1CBC8 | |||
| 6404 | cmd.exe | C:\Windows\SysWOW64\COMCTL32.OCX | executable | |
MD5:821511549E2AAF29889C7B812674D59B | SHA256:F59CDF89F0F522CE3662E09FA847BCA9B277B006C415DCC0029B416C347DB9C4 | |||
| 728 | 1cfe4f92e281fdd504f5e9ffa9c10ddd781f52e20d128fbcb269ff9474d7257a.bin.exe | C:\Users\admin\AppData\Local\Temp\7zS8D287191\DLLFILE\vb5it.dll | executable | |
MD5:AD1826AE0427BE4F65F2F41FE21735DE | SHA256:33831F45DC4EA749FCFB5CF59D45E2C0FF09FC814A52987D1EEEE563B6A37355 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
20
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4008 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4008 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6544 | svchost.exe | 20.190.159.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.32.238.107:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
6544 | svchost.exe | 40.126.31.73:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3140 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |